The average yearly data breach cost in 2022 in the US was nearly $4.4 million, a 3% increase over 2021.
Running a business is like flying a plane. Just as a pilot relies on flight plans and regular updates on weather and air traffic, a business owner must remain ever-vigilant of potential security threats and have a plan in place to address them. Security reports are imperative for evaluating a business’s security strength. Without these reports, you risk leaving gaping holes in your company’s defenses that (cyber)criminals can exploit with ridiculous ease, destroying the business you built over decades within seconds.
Regular and relevant security reports that portray threat in the required, clear format allow organizations to detect and respond to security threats before these can cause irreparable harm.
SlideTeam’s Security Report PPT Templates make it easy to showcase the health of your cybersecurity systems to stakeholders. With clear, concise slides and eye-catching graphics, you can communicate the steps you’re taking to keep your business safe. Download our Security Report PPT Templates now and ensure your business fortress remains unbreachable.
The 100% customizable nature of the templates provides you with the desired flexibility to edit your presentations. The content ready slides give you the much-needed structure.
To write inclusive security reports, you don’t just need a pre-designed format but a strategic manual as well to ensure no element of substance and merit is left out (in this case, security incidents). Here’s an exclusive collection of the top security incident report templates that are a prerequisite for drafting workable security reports. Click here to explore.
Template 1: Security Report PowerPoint Bundle
Cyber security and data integrity is top priority for businesses in today's digital age. As cyber threats become more sophisticated, it's critical to have a clear and comprehensive understanding of your organization's security status. That's where our Security PPT Layout comes in. Designed to help you communicate your security insights and plans, this template helps you create impactful security reports. With its focus on server security threat reports, business incident reports, and cyber security evaluation reports, our PowerPoint Template provides key insights and actionable plans to help you always stay one step ahead. Whether you're a seasoned security professional or a rookie, our template makes it easy to write engaging and informative security reports that make a difference. One of the slides gives your clients (and you) a comparative view of cybersecurity software in terms of features, compatibility, price and ratings. This is a priceless piece of presentation input that saves your time and is hugely convenient. In the slide on tips to create cyber security evaluation report, help your clients master the four steps of a general approach, analyze, scope assessment and conclusion to have that flawless document ready within minutes. Lean how to use the KPI metrics of cyber security reporting as well.
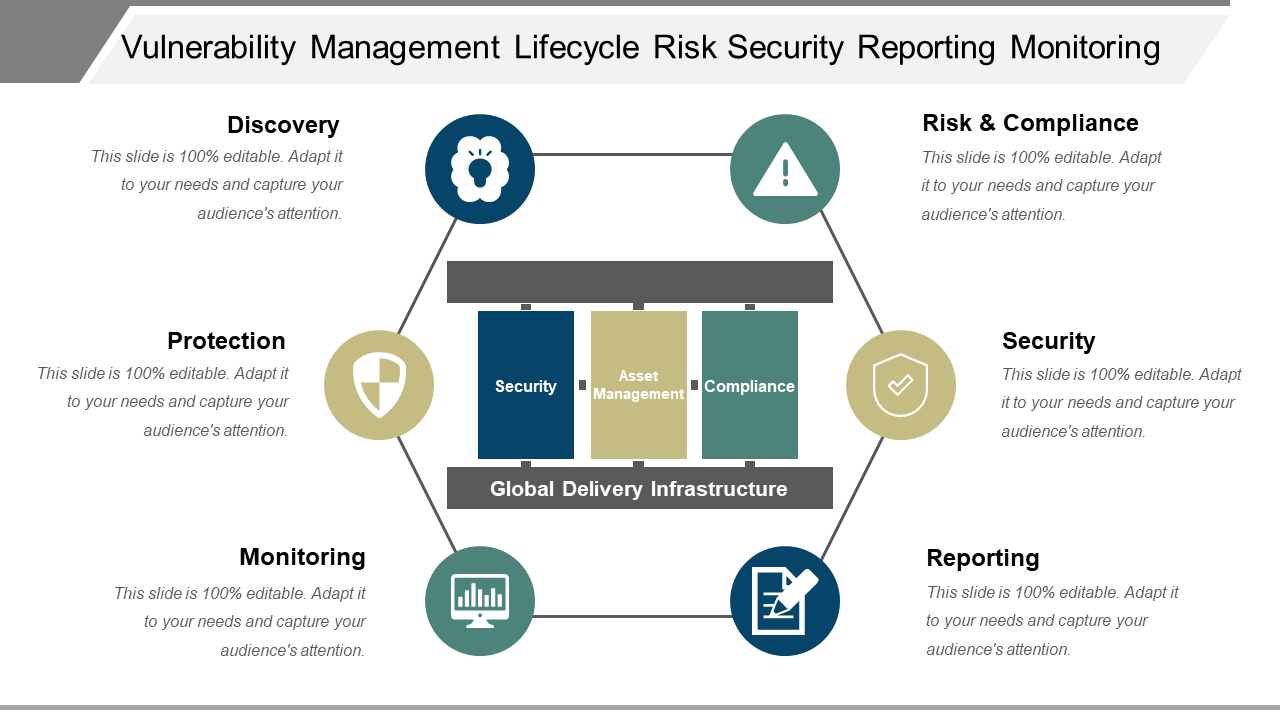
Template 2: Vulnerability Management Lifecycle & Risk Security Reporting
This PPT Template is a comprehensive tool for building a robust vulnerability management program. This template is designed to help you draft a strategic plan that covers vulnerability management, including Discovery, Risk and Compliance, Security, Reporting, Monitoring, and Protection. With this slide, you will have access to insights and actionable strategies for managing vulnerabilities and ensuring the security of your systems. Use this slide to showcase your expertise in monitoring, reporting and protecting your data and servers against cyber threats.
Template 3: Rent Sublease Agreement Security Report PPT Template
Looking to streamline the process of drafting a sublease agreement? Look no further! Our PPT Preset is designed to help you create a comprehensive agreement that covers all aspects of a sublease transaction. With key insights for drafting an agreement that eliminates friction between parties, this template is a must-have for anyone looking to secure a seamless sublease. This template offers the tools you need to draft this rent agreement that protects your interests.
Risks Are Inevitable, But Avoidable
Security reports have become a vital component of successful operations in today's fast-paced and constantly evolving business landscape. They help organizations stay ahead of the curve and navigate the risks that come with growth. By downloading our security report PPT Templates, you're not just investing in a tool; you're investing in the future of your business. With their user-friendly design and functionality, our security report templates are the perfect way to ensure that your security reports are always on point.
FAQs on Security Reports
What is a security report?
A security report is a document that outlines an organization's security landscape, detailing the measures and controls in place to protect its assets, data, and systems from potential threats. Security reports often include information on the risk assessment, vulnerability management, incident response plans, and the overall effectiveness of the security measures implemented. These reports play a crucial role in ensuring the security and privacy of information and help organizations make informed decisions to strengthen their security position.
How do you write an information security report?
Writing a good information security report requires a thorough understanding of the company's security needs and the ability to evaluate current security practices against industry standards and best practices.
To write an information security report, follow these steps:
- Identify the scope of the report: Determine what aspects of the company's security you will cover in the report, such as network security, physical security, and data protection.
- Gather data: Collect relevant data such as security logs, network scans, and vulnerability assessments.
- Evaluate the data: Analyze the data you have collected and determine the strengths and weaknesses of the company's current security measures.
- Report findings: Present your findings in a clear and concise manner, highlighting areas of concern, and making recommendations for improvement.
- Recommendations: Offer concrete and practical recommendations on how the company can improve its security level, such as updating the software, implementing stronger passwords, or conducting regular security training for employees.
- Conclusions: Sum up your findings and recommendations in an organized fashion.
- Review and approval: Have relevant stakeholders, including management and technical staff review the report before finalizing and distributing it.
What are the two types of security reports?
There are two main types of security reports:
Technical Security Report: This type of report focuses on the technical information of a security assessment, including details on vulnerabilities and threats, and recommendations for mitigation or remediation. It is usually written for technical stakeholders such as security professionals and IT teams.
Management Security Report: This type of report is designed for non-technical stakeholders such as executives, managers, and business owners. It presents the security assessment findings in a simpler and user-friendly manner, highlighting the most important risks and providing recommendations for improvement.
What is a cyber security report?
A cyber security report is a document that provides information about the current state of an organization’s cyber security. It covers the aspects of an organization's digital security, such as the current threat landscape, vulnerabilities and exposures, cyber-attacks and incidents, and risk management strategies.
Cyber security reports can be used for internal decision-making and planning, regulatory compliance, or demonstrating an organization’s security footing to stakeholders. The objective of a cyber security report is to provide a comprehensive overview of the organization's cyber security posture and to help stakeholders respond effectively to potential security risks.





 Customer Reviews
Customer Reviews