An IBM survey shows that security breaches cost around $4.24 million globally, with a 10% yearly increase in cost. It takes (on average) 278 days to detect and contain a security breach.
Since the advent of the new normal, privacy breaches and data leaks have become so common that all have been affected by them unknowingly. With technological advancements, security breaches are more effortless, and hacking tools are more readily available. That is why a brand like Apple used the word 'privacy' as its unique selling point.
The massive success of apple products is a real-world example of how vital [data] privacy and security are for the consumers. Therefore, it is necessary for brands' to offer Z-class protection. The only way to achieve the expected level of data privacy and security is through a well-planned security management system.
But…
How to Build a Security Management System?
And how to make security and privacy a critical and automated part of your business?
This is what you will learn through the well-defined and comprehensive steps mentioned in this blog post. Along with each step, we included expert-designed decks/templates to help you build a proactive security management plan.
Let's begin. Shall we?
1. Program management
You need a team of leaders to discuss, define, and run a security management program smoothly. This team will be responsible for assessing needs, making decisions, and implementing security protocols. A suggestion here is to include top or middle-level management personnel from each department to understand the risk factors and find a solution that can be implemented throughout the organization.
You can use these PowerPoint templates to suggest security management opportunities for each department.
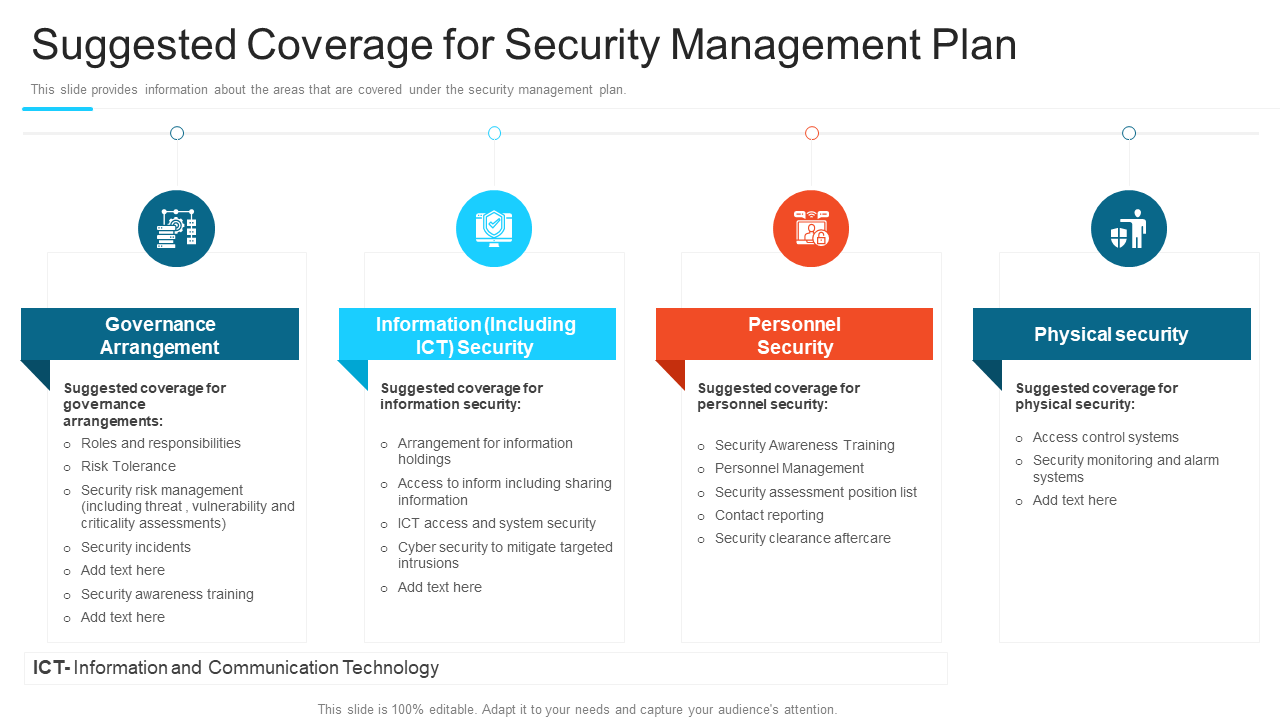
Template 1: Coverage for Security Management Plan PowerPoint Template
This template can help you cover the roles and needs of the security department of the organization. You can use it to define topics like governance arrangements, information, and personal and physical security plans. This will also help you keep transparency among leadership members. Download it now!
Template 2: Security Information and Event Management PowerPoint Presentation Slide
Utilize this PPT set for real-time analysis of security alerts generated by the applications and network hardware. This deck will give you 62 slides that help address challenges, solutions, and the need for security information and event management in the company. It will help you share the advantage and evolution of SIEM software and the security operations models. You can also share the budget of the security management plan with this template. Get access to it now!
2. Prevention
Define prevention measures after a thoughtful risk and business impact analysis. Simply put, these are documented security checks at different levels in an organization. They can be as simple as checking IDs (physical security) of the person entering office premises or as advanced as blocking sites (IT security) at your company's internal server.
These templates will help you enlist these prevention measures for a security management plan with ease.
Template 1: Security Management Plan Measures PPT Template
Deploy this PowerPoint deck to conduct risk factor analysis for various online and offline operations. This deck will give you 12 slides comprising risk analysis, defining metrics, mitigation plans, and more. Besides, all these PPT layouts are entirely customizable. Grab it now!
Template 2: Technology Security Process Framework PPT Template
If you are looking for something to explain the basics of technology security to your team, then this PPT template is an ideal choice for you. It gives you 12 slides to explain various aspects of technology security like cyber security framework, IT security assessment, security development lifecycle, types of security models, data protection technology, etc. Download this now!
3. Preparedness
Hope for the best and prepare for the worst — are the basics of a security management plan. In this step, you will prepare a list of actions deployed in case of any security breach or emergency incident. For example, in case of theft, the building will be ceased, while if it is an emergency like a fire, it will be evacuated. Furthermore, expert teams are formed or hired to handle these situations.
Here are a few templates to help you with this:
Template 1: Security Management Plan PowerPoint Template
Check out this efficiently designed deck on security management plans to protect sensitive data. Use this to define how the organization will establish and maintain a safe physical environment and monitor staff operations to limit the risk of personal injury and property loss. Additionally, a security risk management assessment checklist and dashboard are included in this PPT layout. Download and get access now!
Template 2: Corporate Security Management Plan PowerPoint Template
This template aims to identify high safety risks, enable management for corporate security to protect the company from fears, and set up safety plans to reduce risks. You can use this PPT slide to display critical success factors of current security plans and significant reasons for the poor security. Utilize this to manage security tasks for smooth operations and set an advanced safety plan. Grab it now!
4. Response
This step takes into consideration — when a real-time incident happens then how well the contingent steps will be executed. A checklist of actions will be prepared and performed by the response teams (IT, security, fire team, or others) during the containment procedures of a breach. For example, the IT team will restart the systems/servers to break the online hack. Similarly, the security team checks camera recordings and increases security on exits while handling a physical security breach.
Pro Tip: Always try to administer these steps calmly and share the required information with others to prevent any panic. You can call a quick meeting/huddle to make others aware of the situation.
Use these templates to share the steps with teams.
Template 1: Executing Security Management Plan PPT Slide
Here is an efficiently designed proposal to execute a security management plan. You can use it to minimize threats and reduce the risk of crisis in your company. This PPT template aims to identify high safety risks, enable IT security to protect the company from threats, and set up safety plans to reduce such risks. You can use it to display current security plans, critical success factors, and significant reasons for poor security to know the company's challenges. Besides, this PowerPoint set is 100 percent editable. Get access to this now!
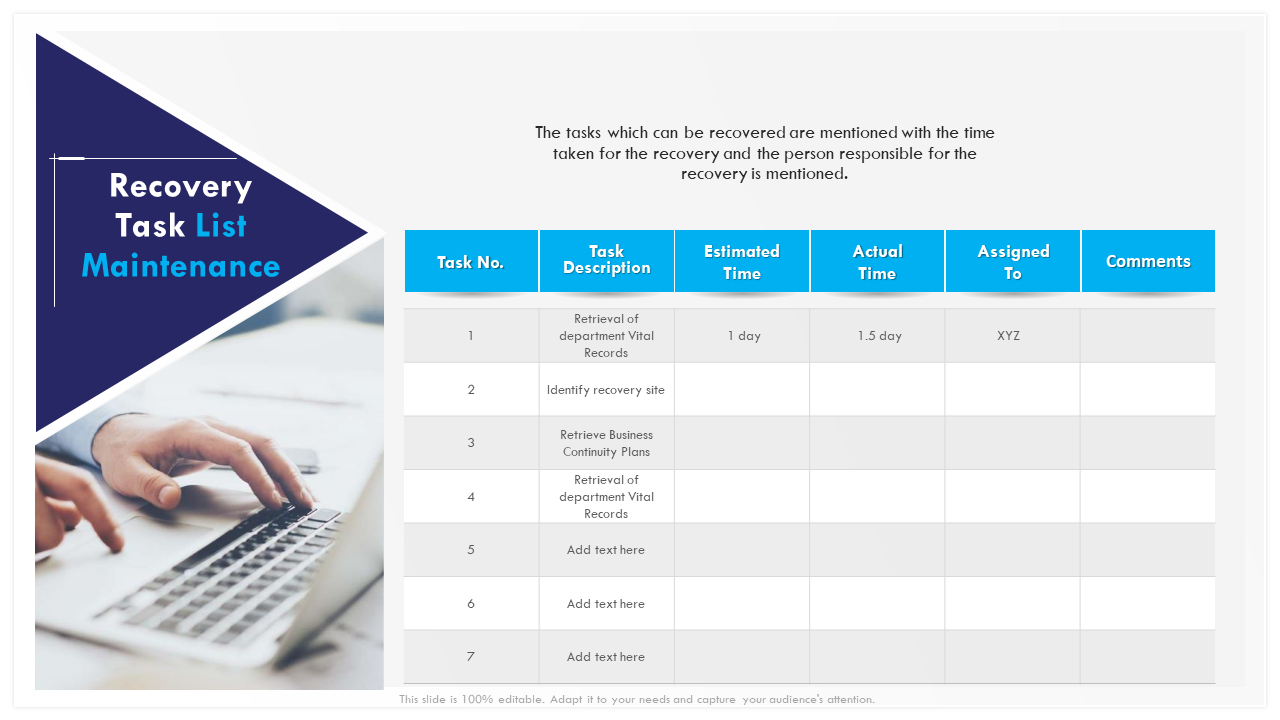
Template 2: Recovery Task list Security Management PPT Slide
Employ this template to share the list of tasks to perform while undergoing a security breach. You can use it to create a priority list and share each activity's estimated time and details with the responsible person. You can use this PPT template can be used to monitor the progress. Download this now!
5. Recovery
This step holds significant value for security management and business. Although it depends on teams' response/damage control (Step 4) during an incident, the business should restore its normal functions and operations as soon as possible. Calculation of loss or damage and finding ways to recover that loss is part of this. Recovery can be assets, data, communications, business operations, and more. For example, after a system has been hacked, the IT department will check how much data has been lost. Do they have a backup for it.? If yes, then how much time will it take to restore. And if not, will it be possible to proceed without that data. It will also define the value that information holds for your business and its operations.
Try these templates to set a recovery path post the traumatic incident.
Template 1: Effective Information Security Risk Management PPT Slide
Check out this competently designed template to implement an information security risk management program. You can use this to effectively manage organizational risks caused by incidents, threats, and vulnerabilities. It can be used to show scenarios addressing the present security management capabilities and infrastructure. You can present an in-depth overview of the security risk assessment workflow in asset identification, incident management, threat and vulnerability management, and mitigation stages. Besides, training, budget, system checklists, infrastructure performance, and dashboard slides are in this PowerPoint design to help you monitor business performance while protecting confidential data. Download it now!
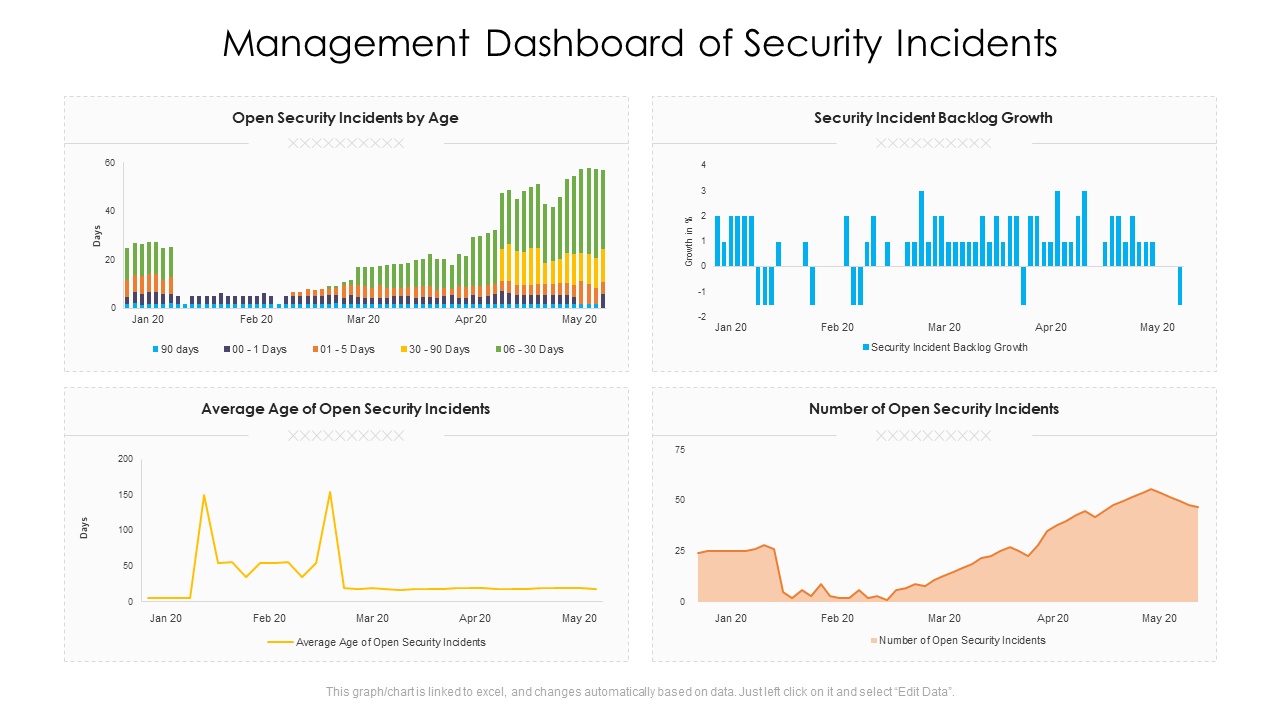
Template 2: Security Management Dashboard PowerPoint Template
Incorporate this template into your presentation to show the performance of the incident management team. It can help you compare the historical data of security incidents and time taken for recovery, backlog growth, when the incident happen, and more. The team of our expert designers has crafted this template to meet the security dashboard requirements. So grab it now without ado!
6. Training
Master Shifu (Kungfu Panda) said, "There is always something more to learn, even for a master." Therefore training is the most integral part of the security management plan. Without it, other steps can be merely academic and might never be put into action.
It can include integrating new knowledge, historical case studies, practical drills, familiarizing the team with recent trends and technologies, and other methods. Specific hours of training need to complete by each team member in a day/week/month. It will also enhance the team's performance and coordination.
Here are PowerPoint templates to help you with the training of the team!
Template 1: Advanced Security Management Plan PowerPoint Presentation Slide
Explore our expert-designed template on steps to set up an advanced security management plan. This template can help you describe the reasons for poor security and the current challenges that your organization is facing. It can also be used to present a roadmap for setting up an advanced security plan and describe the goals and objectives associated with it. You can evaluate the information processing assets periodically for analyzing and assessing the risk with this PPT template. Adopt this complete deck for protecting sensitive data using the steps mentioned. Grab it now!
Template 2: Industrial Security Management Plan PPT Template
Utilize this template to manage the security and equipment of your industrial hardware. It can help you to share and regularise the training program for your security team. This deck includes a slide for a 3-step process for industrial security management, a 4-stage industrial model, industrial cloud security management, IoT security, automation management, and more. Besides, all slides are completely customizable. Get it now!
These steps will help you design a security plan for any industry — IT, corporate, finance, healthcare, etc. But one thing about the security management plan is that it is mostly reactive. Organizations or teams respond after the incident happens. Like service engineers will rectify a bug or study a hack after it has hit the business. To save yourself from the impact of a security breach, you need to take some proactive steps. Here we are sharing a few extra tips to structure a proactive security management program for your organization and customers:
Regularize Risk assessment: conduct risk assessment regularly and check the risk associated with every asset of the company. This will help you stay ahead of breachers.
Teach security practices: Educate your peers on the best security practices. Investment in security management classes and assignments, and check their knowledge about security practices through these assignments.
Intrusion management system: Most companies have intrusion detection systems as a part of security management tools. Fix this with an intrusion prevention system, which will stop intruders rather than just showing red flags post intrusion.
System updates: Advanced technology is another thing that can keep you ahead of hackers. Update your systems regularly and install new technologies on-premises, especially essential for security management.
Permeability: One of the most critical parts of the information security system is that you can share the data with the selective and required people of the organization. Make it a cardinal rule to honor the privacy of your clients/customers.
In the end
The world and technology are undoubtedly changing very quickly. As the ways to strengthen the security increase, so does ways to breach it. Nowadays, data and information hold and drive the marketplace. That is why an industry invests millions of dollars in designing a proper security management system. You can save a lot on these unnecessary activities by investing in our tailor-made templates. Each one will help you develop, execute, and improve the security management plan with ease. So what are you waiting for? Go ahead and download these now!
PS: Want to learn how to keep your workplace safe for employees? Check out this guide with the best safety management plan templates to design an appropriate program for your organization.





 Customer Reviews
Customer Reviews













![Top 10 Templates to Fabricate a Powerful Cyber Security Roadmap [Free PDF Attached]](https://www.slideteam.net/wp/wp-content/uploads/2022/05/Cyber-Security-Roadmap-Templates_1-1013x441.png)












