Executing security management plan to minimize threats powerpoint presentation slides
Strategic plans for the management of security integrate data security in businesses that ensure risk assessment. Also, it provides mitigation strategies for minimizing the effects of threats. Mitigating these challenges is the new normal for companies to protect their IT operations and create a security policy to enforce it correctly. Here is an efficiently designed proposal on Executing a Security Management Plan to Minimize Threats that will reduce the risk of crisis in your company and the effects of threats occurring from outside. This template aims to identify high safety risks, enable IT security to protect the company from threats, and set up safety plans to reduce such risks. One can display their current security plans critical success factors and significant reasons for poor security to know the company's challenges. Security tasks require organizations to show the elements with their status that affect the operations and overcome them by setting an advanced safety plan for IT. Businesses evaluate information processing assets for analyzing the risk and clearly define the security management system through adopting high-tech assessment controls for themselves. Book a free demo with our research team and talk to our experts for customizing this 100 percent editable proposal based on your needs. Get access to the market's best template now.
Strategic plans for the management of security integrate data security in businesses that ensure risk assessment. Also, it ..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver an informational PPT on various topics by using this Executing Security Management Plan To Minimize Threats Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds eye view of the topic. Encompassed with fourty two slides, designed using high quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
Content of this Powerpoint Presentation
Slide 1: This is the cover slide of Executing Security Management Plan to Minimize Threats PowerPoint presentation.
Slide 2: This is the Agenda slide for Executing Security Management Plan to minimize Threats
Slide 3: This is a table of contents slide that lists out all the essential elements covered in the deck.
Slide 4: This slide introduces Current security management critical success factors and reasons for poor security management.
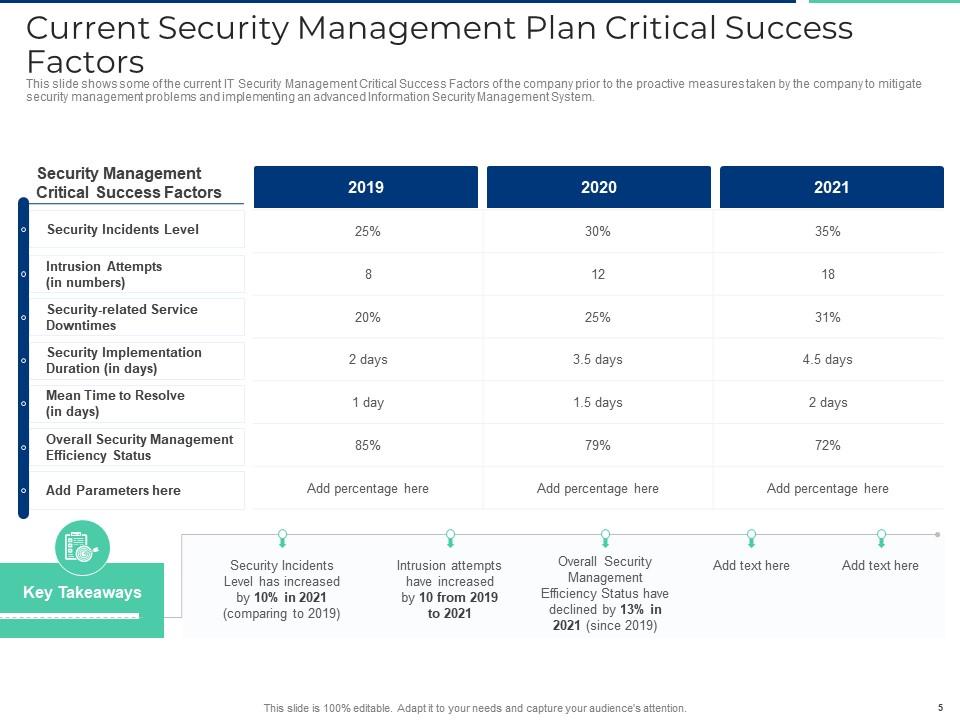
Slide 5: This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.
Slide 6: This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue.
Slide 7: This slide intoduces current security management challenges and ways to mitigate the challenges.
Slide 8: This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers.
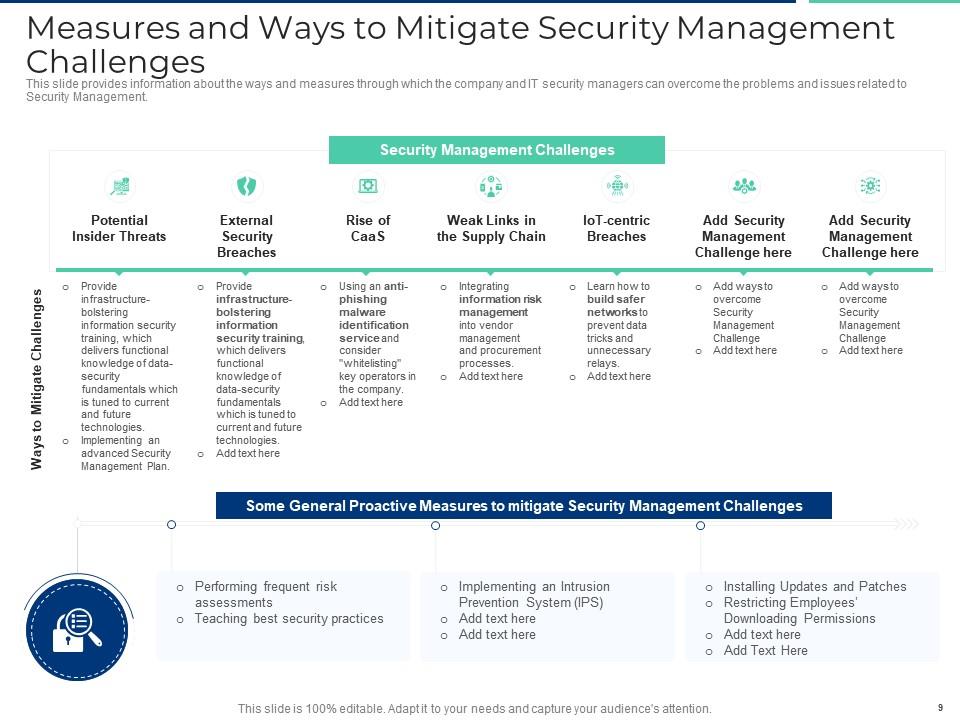
Slide 9: This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.
Slide 10: This slide shows essential elements to be included in a security management plan.
Slide 11: This slide provides information about the essential elements/parts that must be included in security management plan by the company and IT security manager.
Slide 12: This slide shows ways to overcome security management challenges.
Slide 13: This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge/problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.
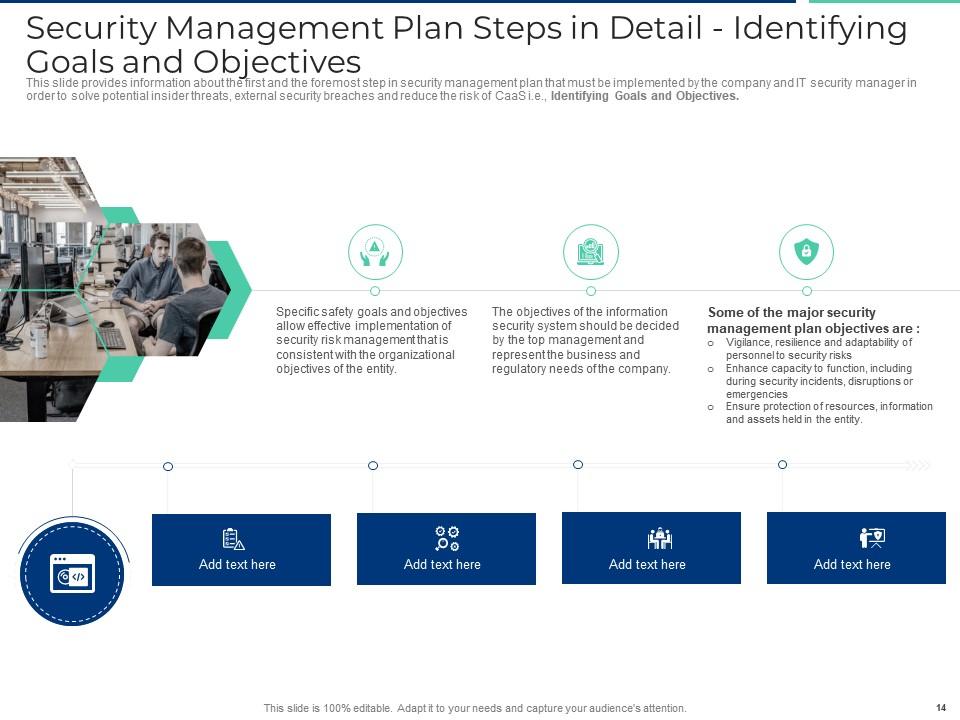
Slide 14: This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives.
Slide 15: This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets.
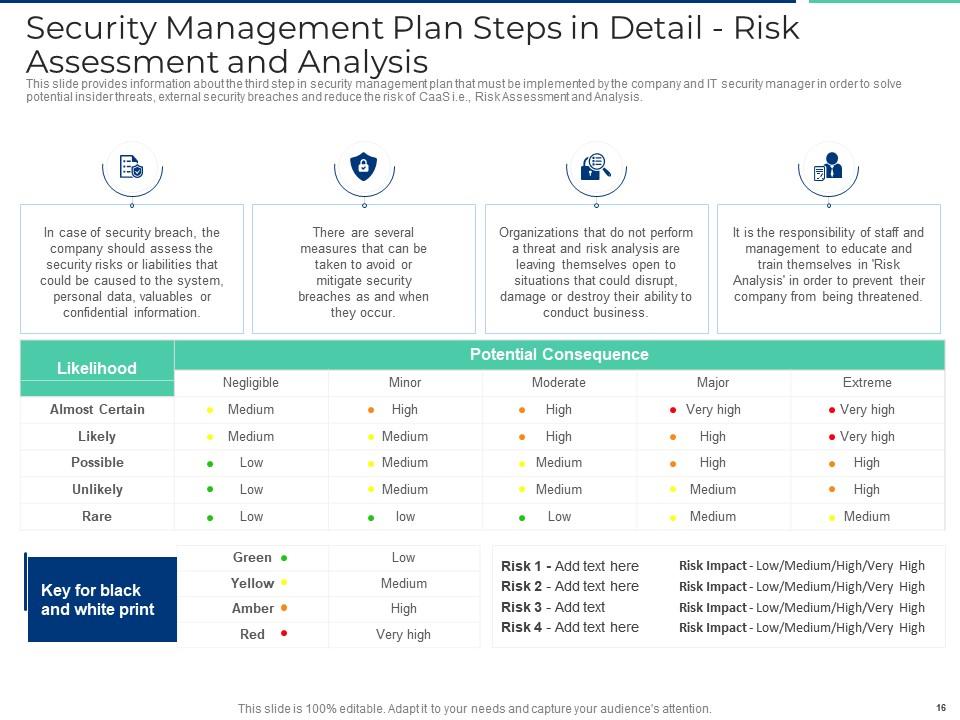
Slide 16: This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis.
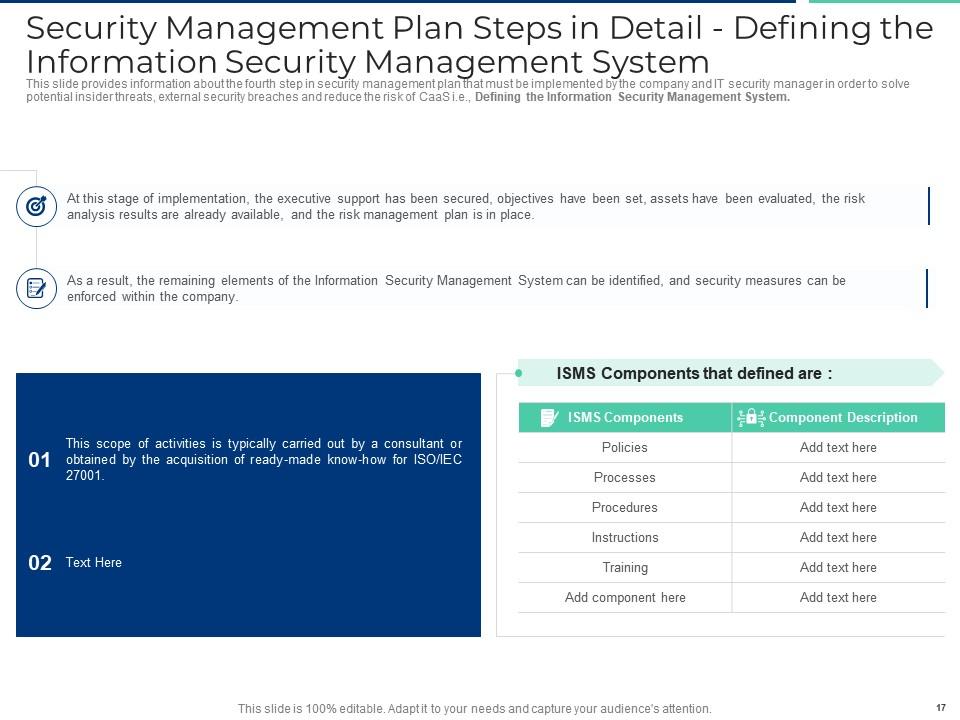
Slide 17: This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System.
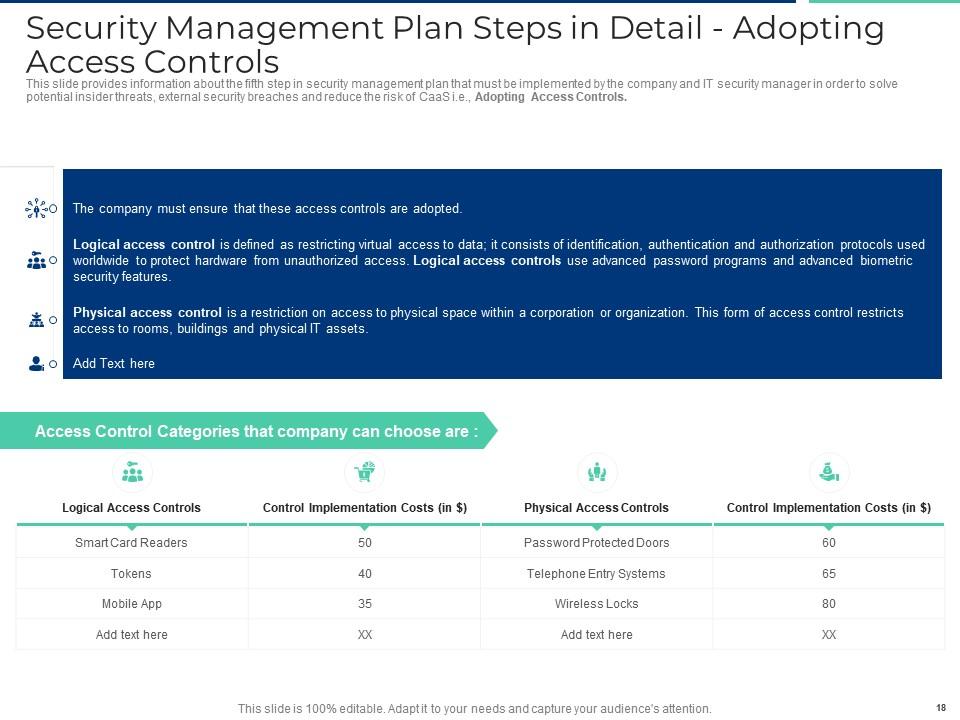
Slide 18: This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Adopting Access Controls.
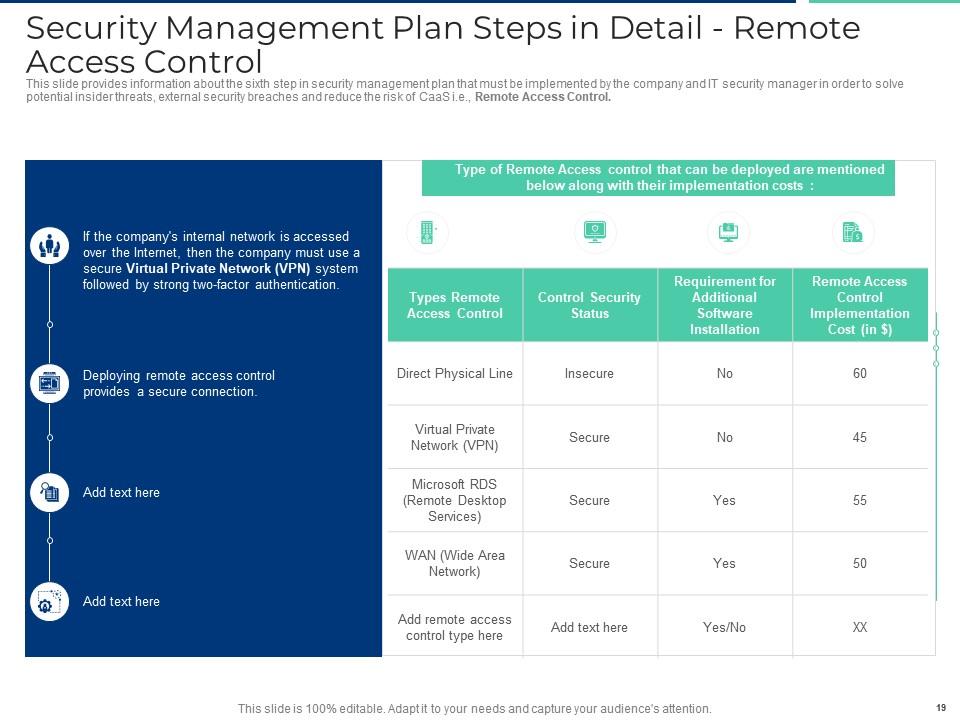
Slide 19: This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control.
Slide 20: This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies.
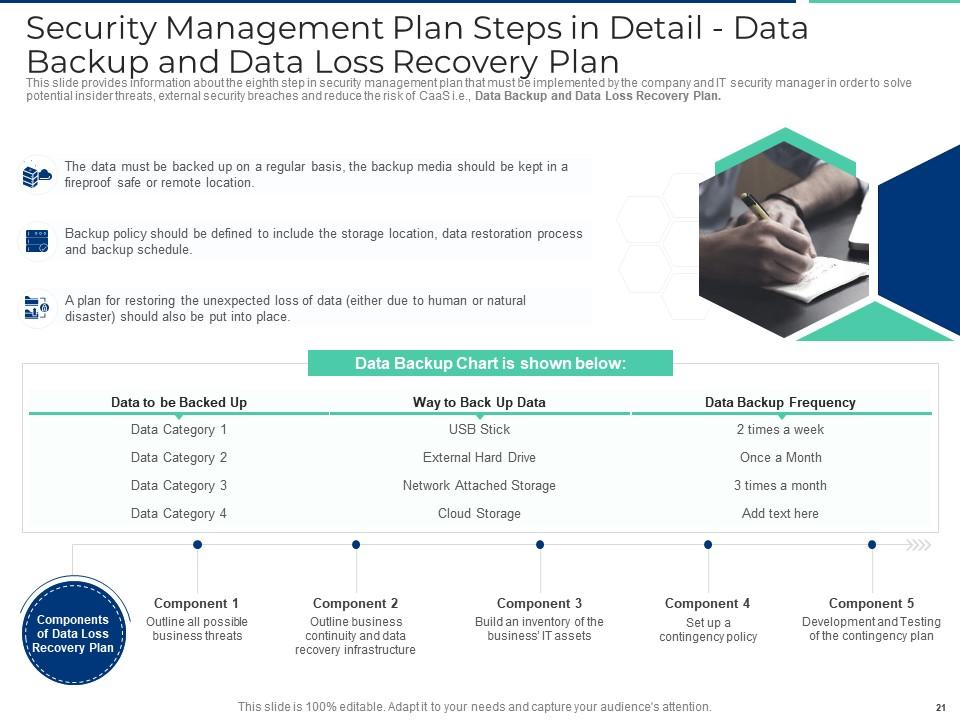
Slide 21: This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Data Backup and Data Loss Recovery Plan.
Slide 22: This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring.
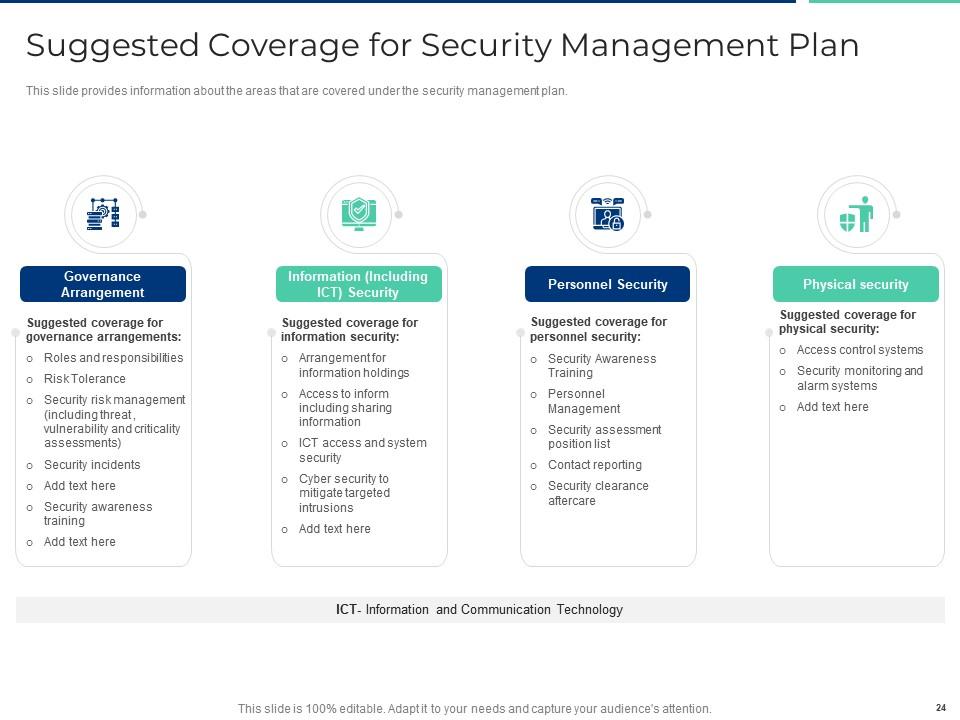
Slide 23: This slide shows suggested coverage for security management plan.
Slide 24: This slide provides information about the areas that are covered under the security management plan.
Slide 25: This slide shows security risk management process and security risk management checklist.
Slide 26: This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk.
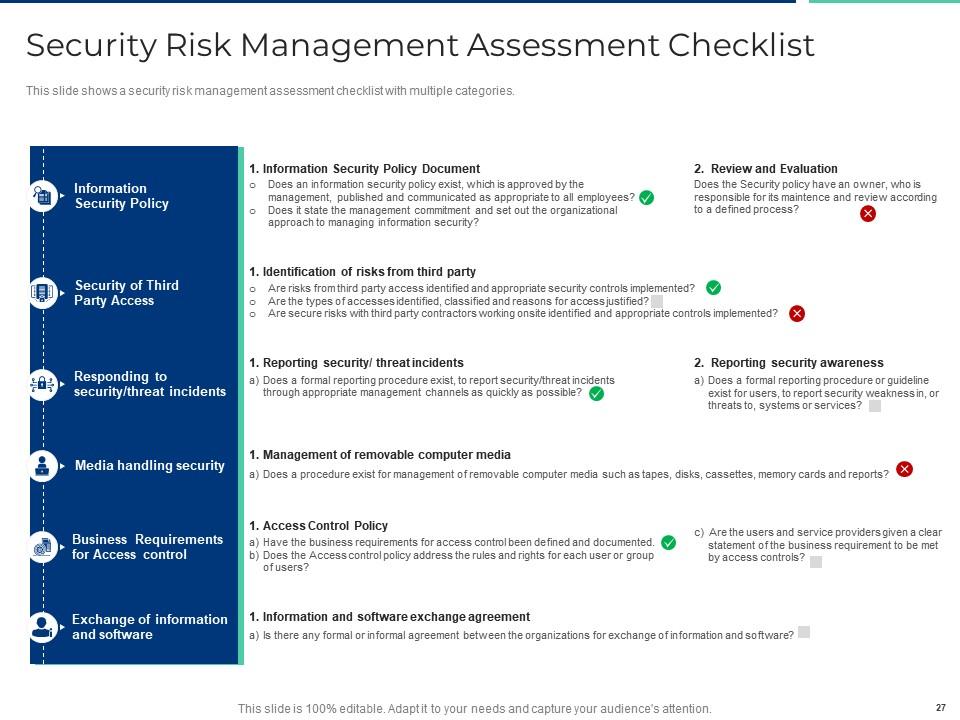
Slide 27: This slide shows a security risk management assessment checklist with multiple categories.
Slide 28: Estimated Security Management Plan Critical Success Factors and Security Management Dashboard
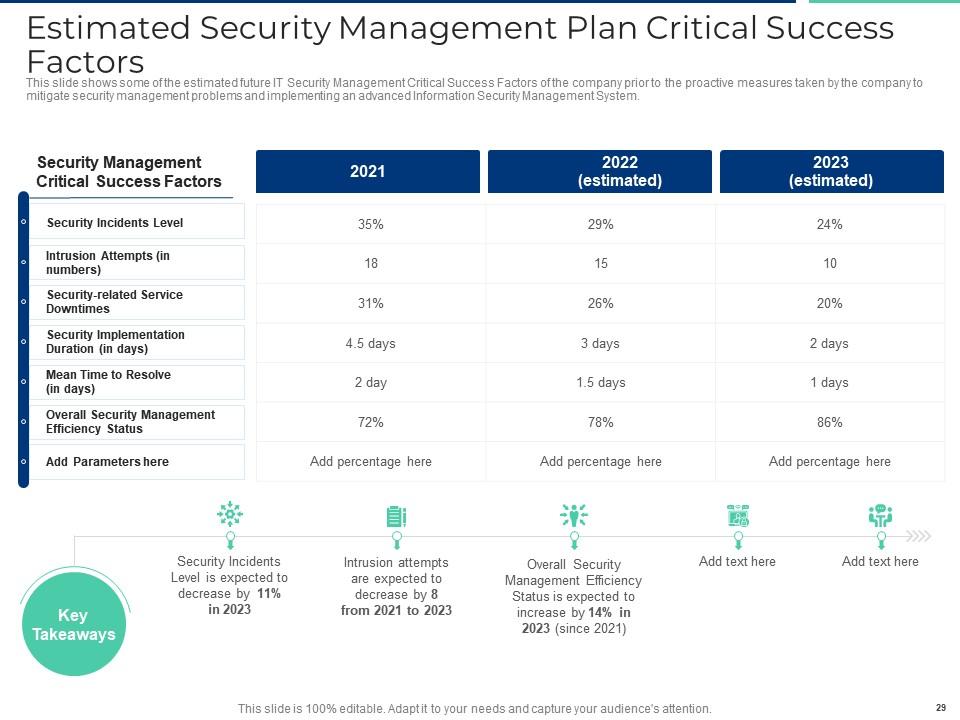
Slide 29: This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.
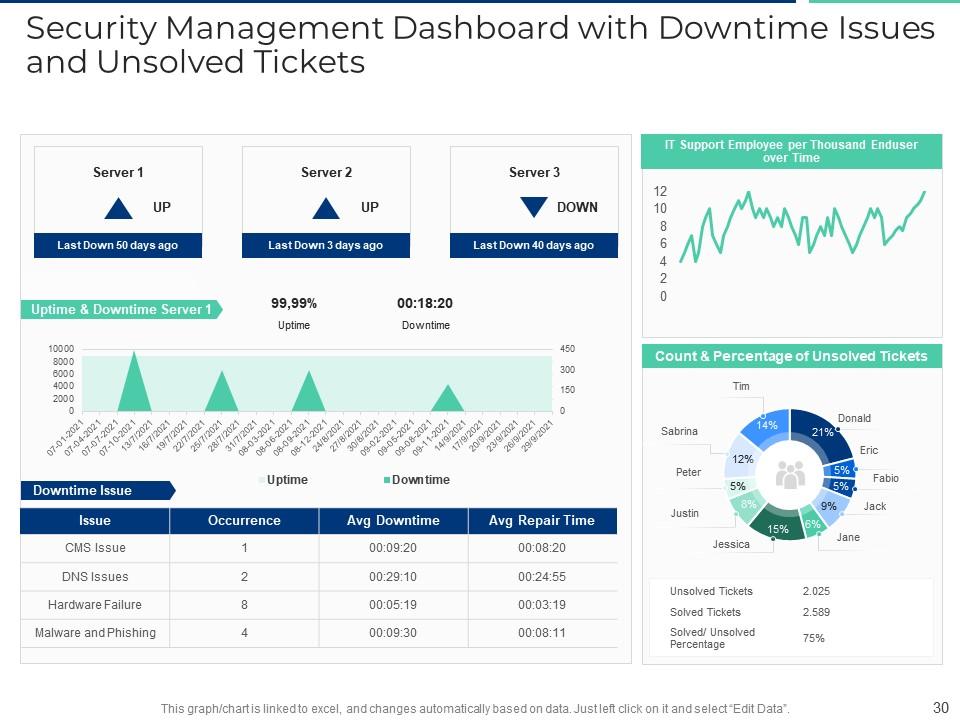
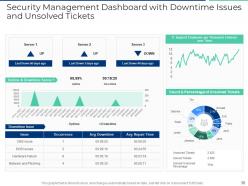
Slide 30: This slide shows security management dashboard with downtime issues and unsloved tickets.
Slide 31: Executing Security Management Plan to minimize Threats Icons Slide
Slide 32: This is an Additional Slide
Slide 33: This is Our Mission slide to state your mission and vision.
Slide 34: This is a Post It Notes slide that can be used to keep the important data at one place.
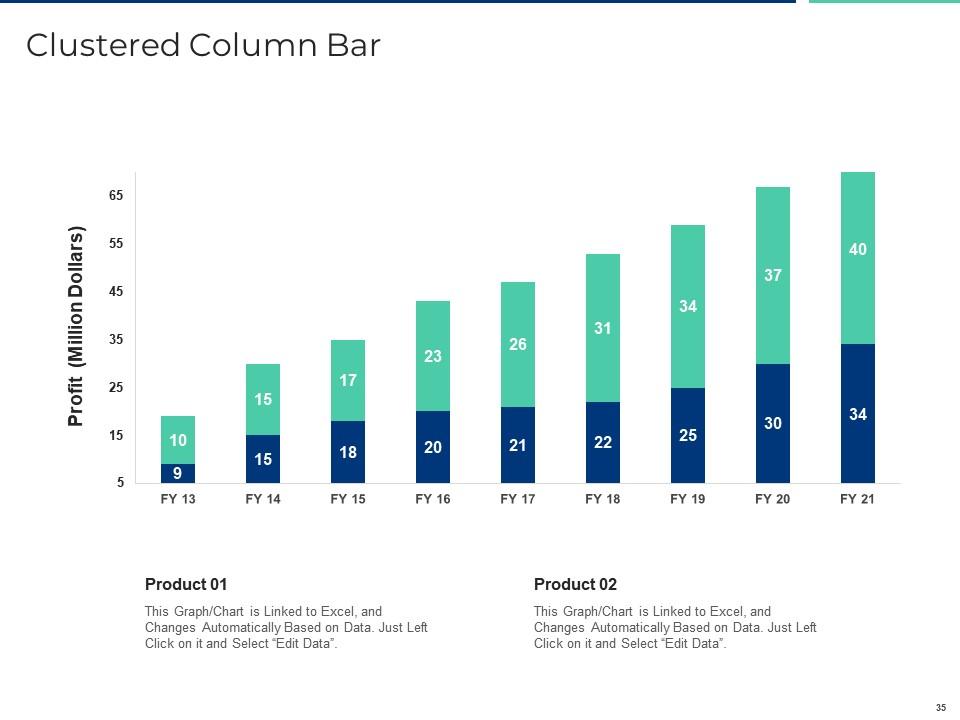
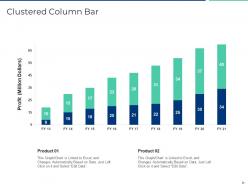
Slide 35: This is a Clustered Column Bar chart slide that can be used to compare different elements.
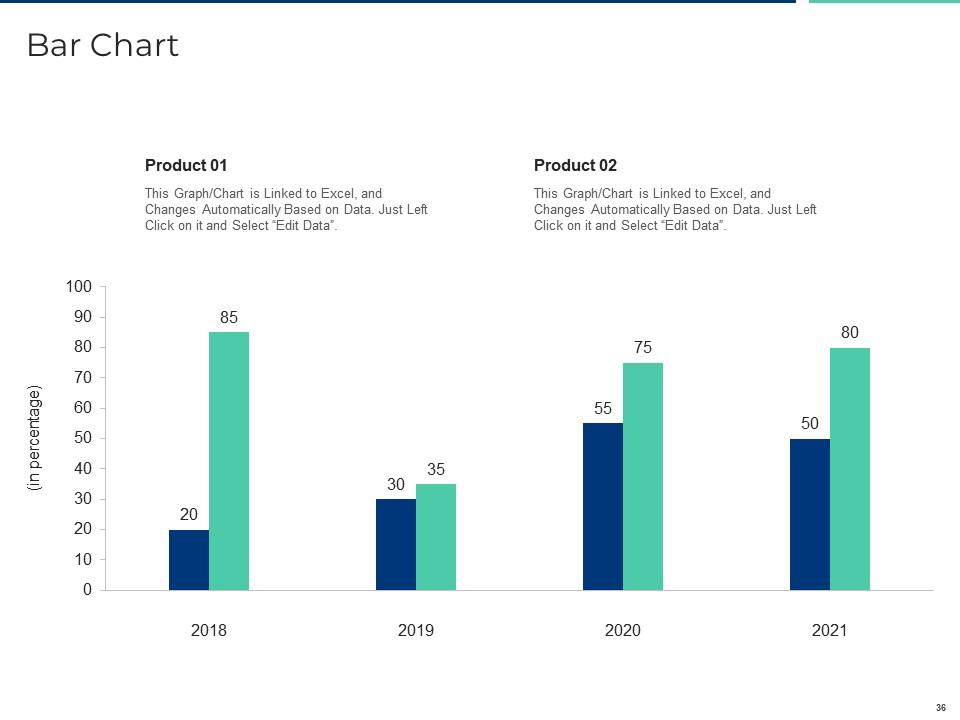
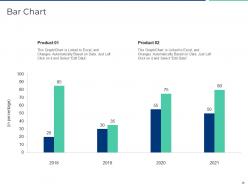
Slide 36: This is a Bar Chart slide that can be used to conduct comparative analysis between different products.
Slide 37: This is a Venn diagram slide that can be used to compare three different elements,
Slide 38: This is a Financial score slide to state your company's financial aspects.
Slide 39: This is a creative Puzzle image slide to state information, specifications etc.
Slide 40: This is a Timeline slide that can be used to showcase chronological sequence of events.
Slide 41: This is a Roadmap slide that can be used to present series of events.
Slide 42: This is a thankyou slide for acknowledgment. You can share your contact details here.
Executing security management plan to minimize threats powerpoint presentation slides with all 42 slides:
Use our Executing Security Management Plan To Minimize Threats Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
No Reviews