Cyber security it powerpoint presentation slides
Cyber Security is the process of protecting electronic devices such as computers, servers, mobile gadgets, data, electronic systems, and networks from cyber-attacks. This PowerPoint presentation illustrates significant details about cybersecurity. Incorporating this PPT, you can present and share details on the common threats against data and information systems and the process to identify the information that needs to be protected. This network security PowerPoint presentation will be helpful to throw light on the current scenario of the organization, the requirement of cybersecurity in different sectors, and it's working. In addition, computer security PPT contains the critical elements of cybersecurity, cyber risk identification and assessment, steps to mitigate those risks, and benefits of cybersecurity, along with automation's role in cybersecurity. Further, this data security presentation comes with a checklist to implement cybersecurity in the organization, a 30-60-90-day plan to manage cybersecurity, and the budget to implement the same. The Information Security deck also showcases a roadmap to monitor cybersecurity and a timeline to implement cybersecurity in the organization. Lastly, this electronic information security PPT shows the effects of cybersecurity implementation on the organization and dashboard for threat tracking in cybersecurity. Talk to our expert and get access to our cybersecurity ppt template for generating a security framework for yourself. Download it now.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cyber Security It Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
Content of this Powerpoint Presentation
Slide 1: This slide displays the title i.e. ‘Cyber Security’ and your company name.
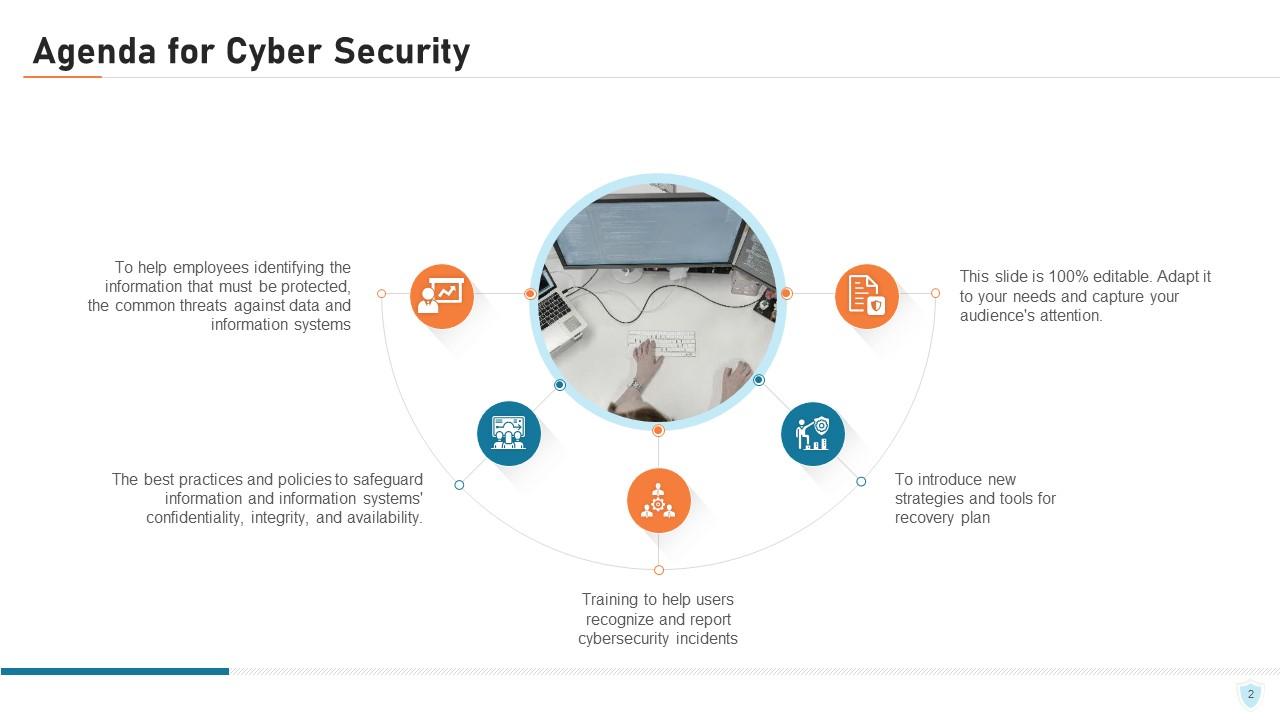
Slide 2: This slide explains the agenda of the for the project.
Slide 3: This slide demonstrates the table of contents for the project.
Slide 4: This slide presents the continued table of contents for the project.
Slide 5: This slide exhibits the title for overview of cyber security.
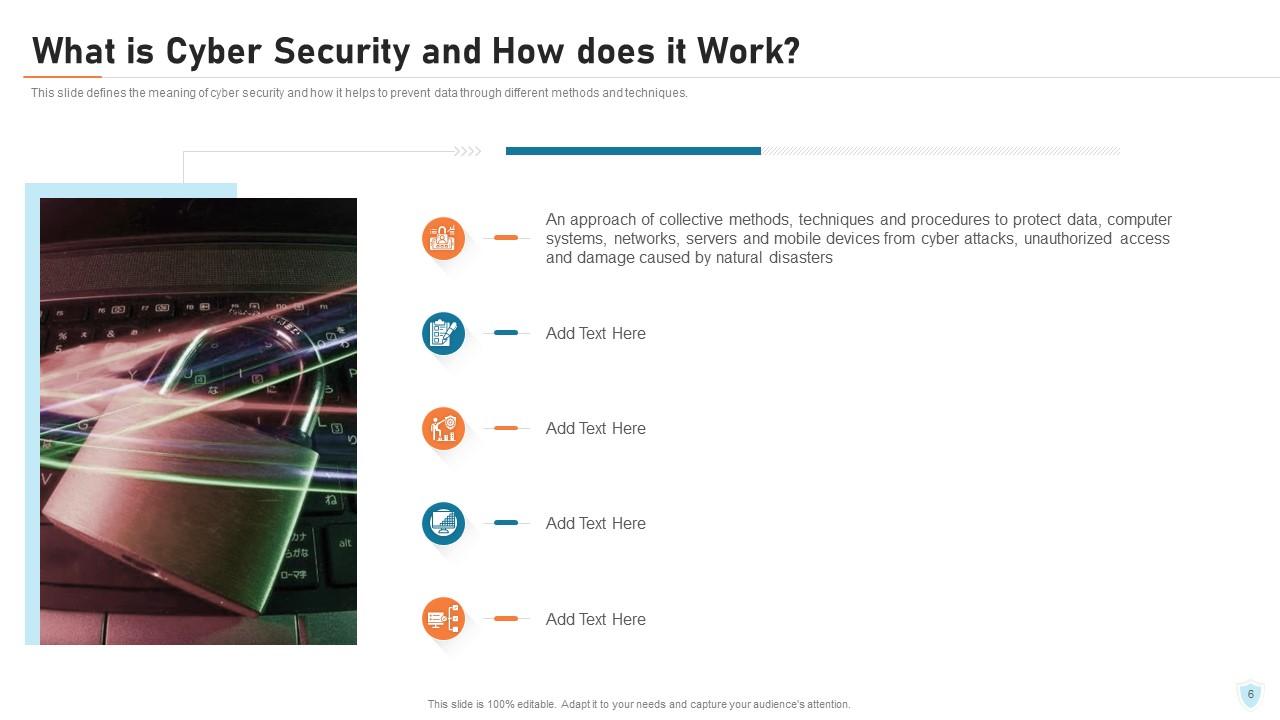
Slide 6: This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques.
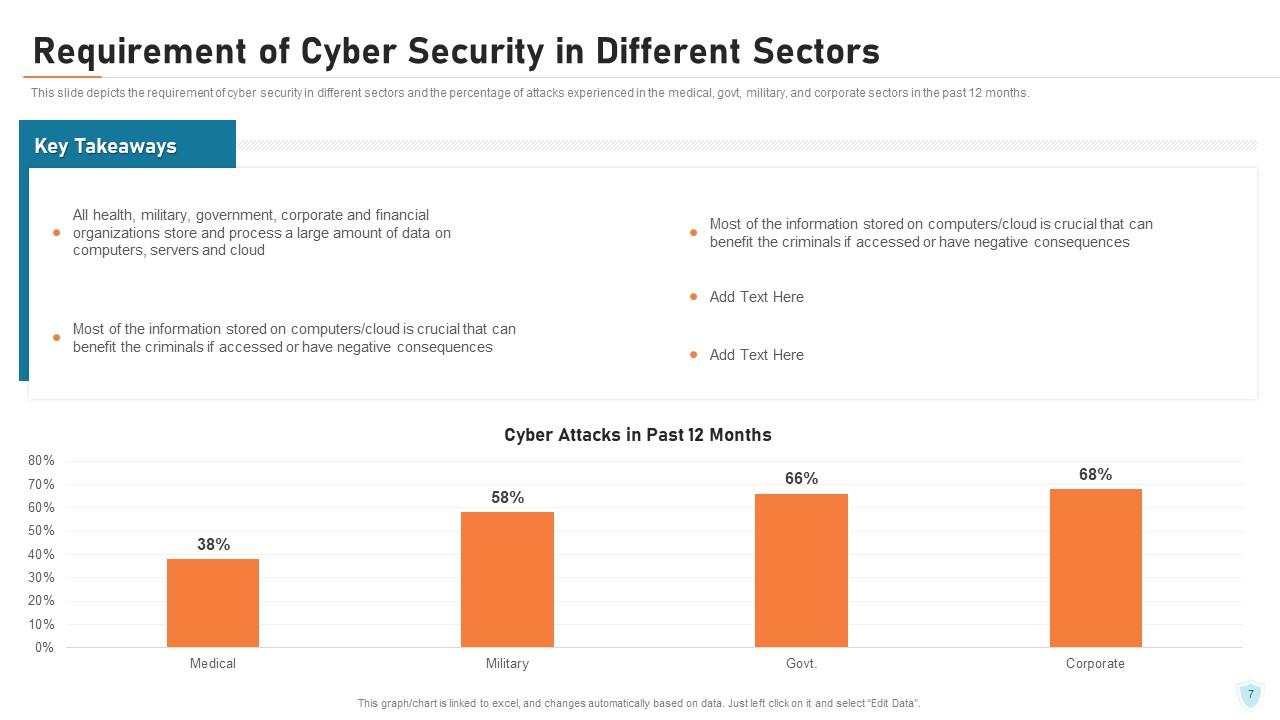
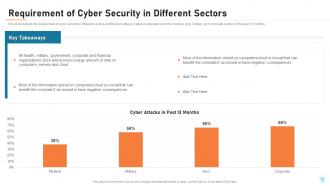
Slide 7: This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months.
Slide 8: This slide displays the title for current scenario of the organization.
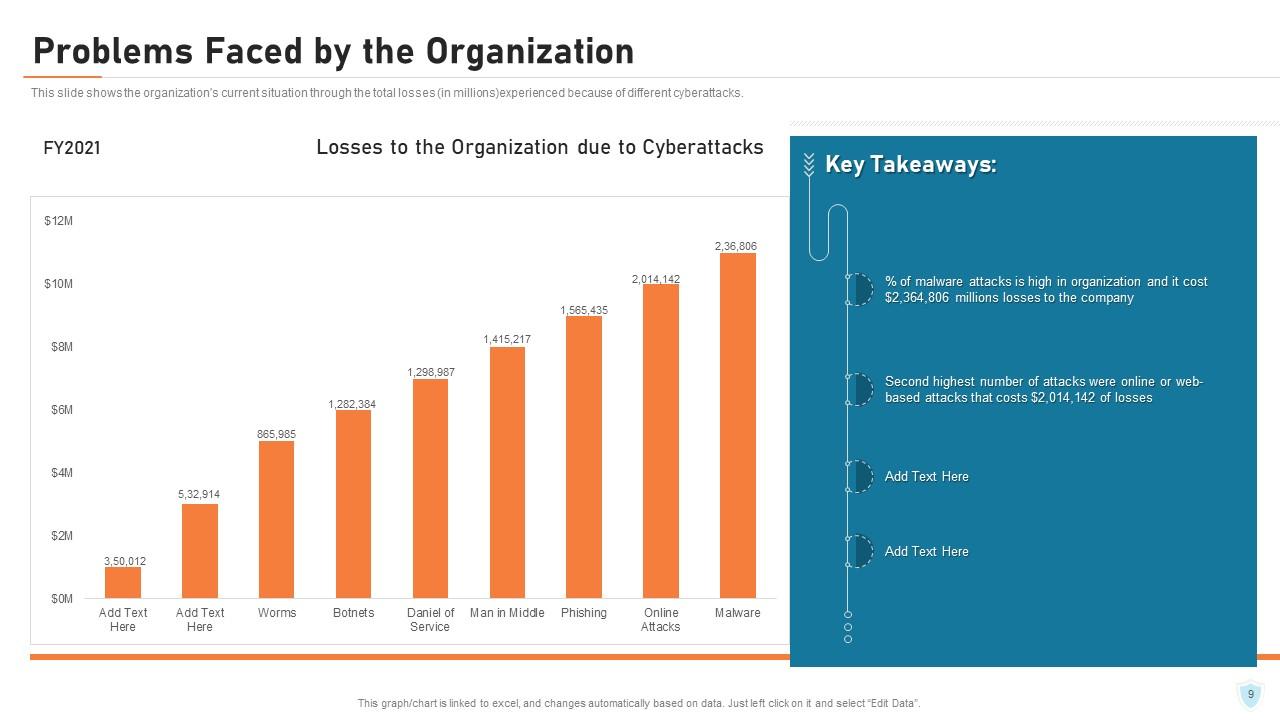
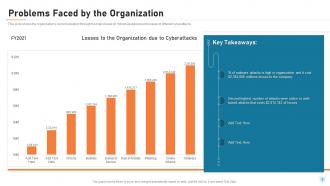
Slide 9: This slide shows the organization's current situation through the total losses experienced because of different cyberattacks.
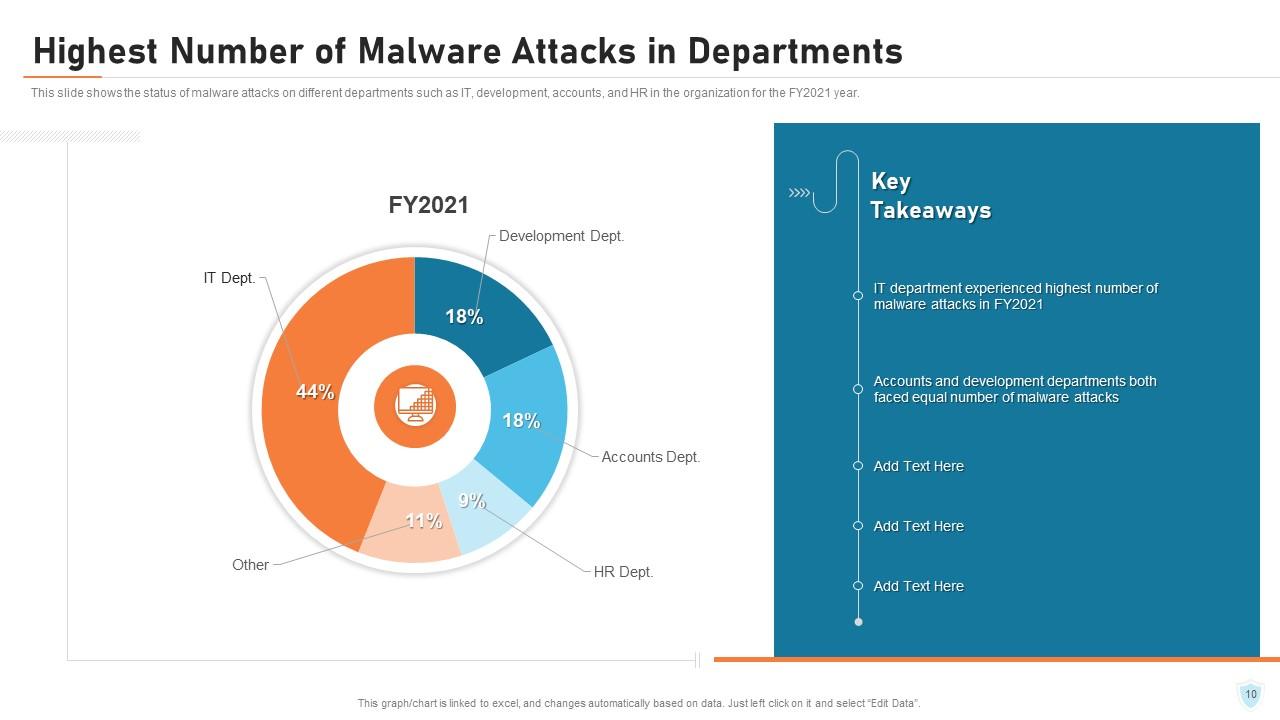
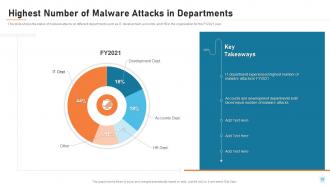
Slide 10: This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year.
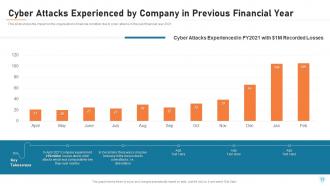
Slide 11: This slide shows the impact on the organization's financial condition due to cyber-attacks in the past financial year 2021.
Slide 12: This slide presents the title for key elements of cyber security.
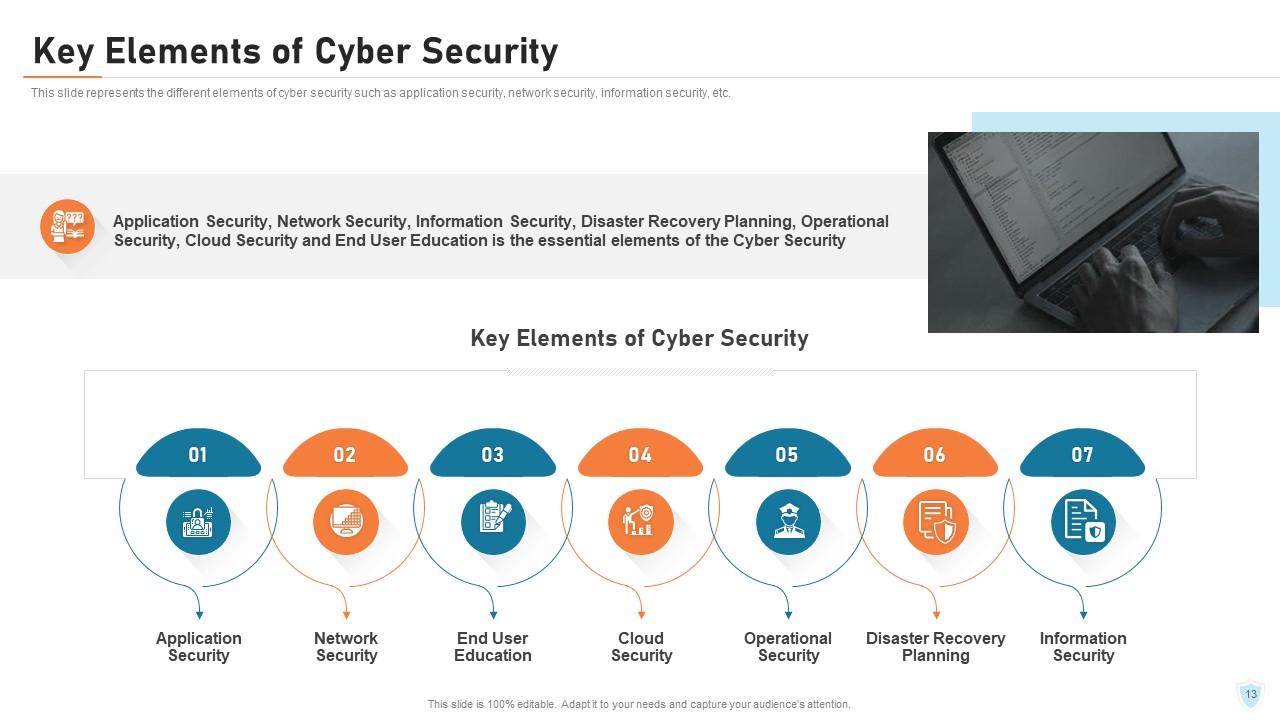
Slide 13: This slide represents the different elements of cyber security such as application security, network security, information security, etc.
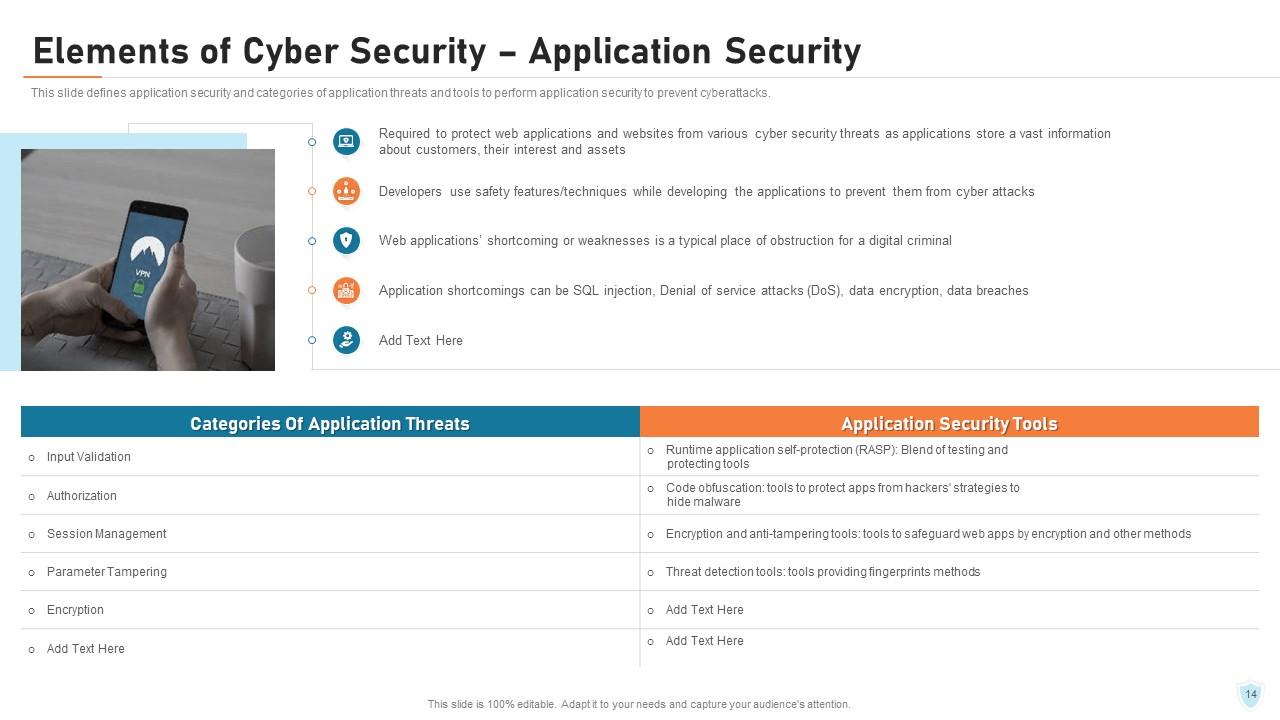
Slide 14: This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks.
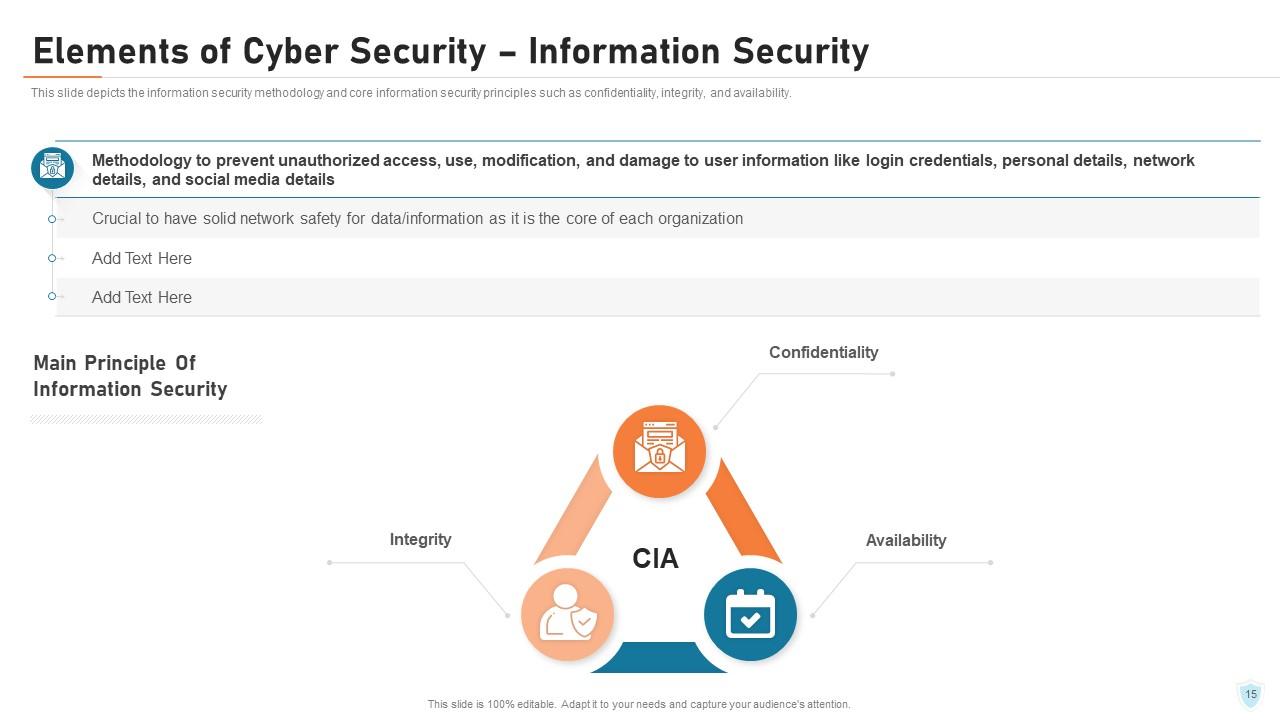
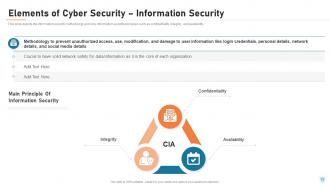
Slide 15: This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability.
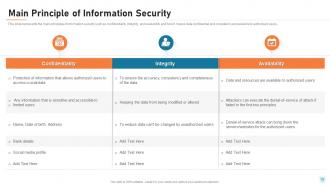
Slide 16: This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users.
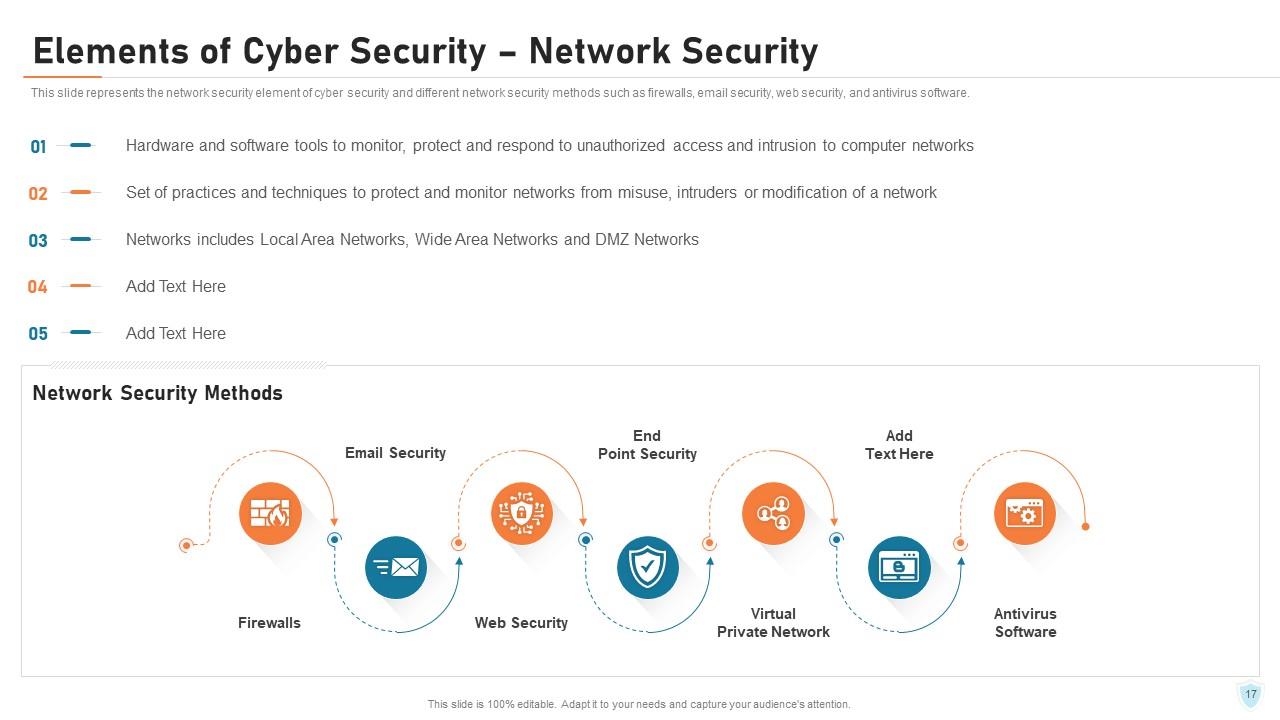
Slide 17: This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software.
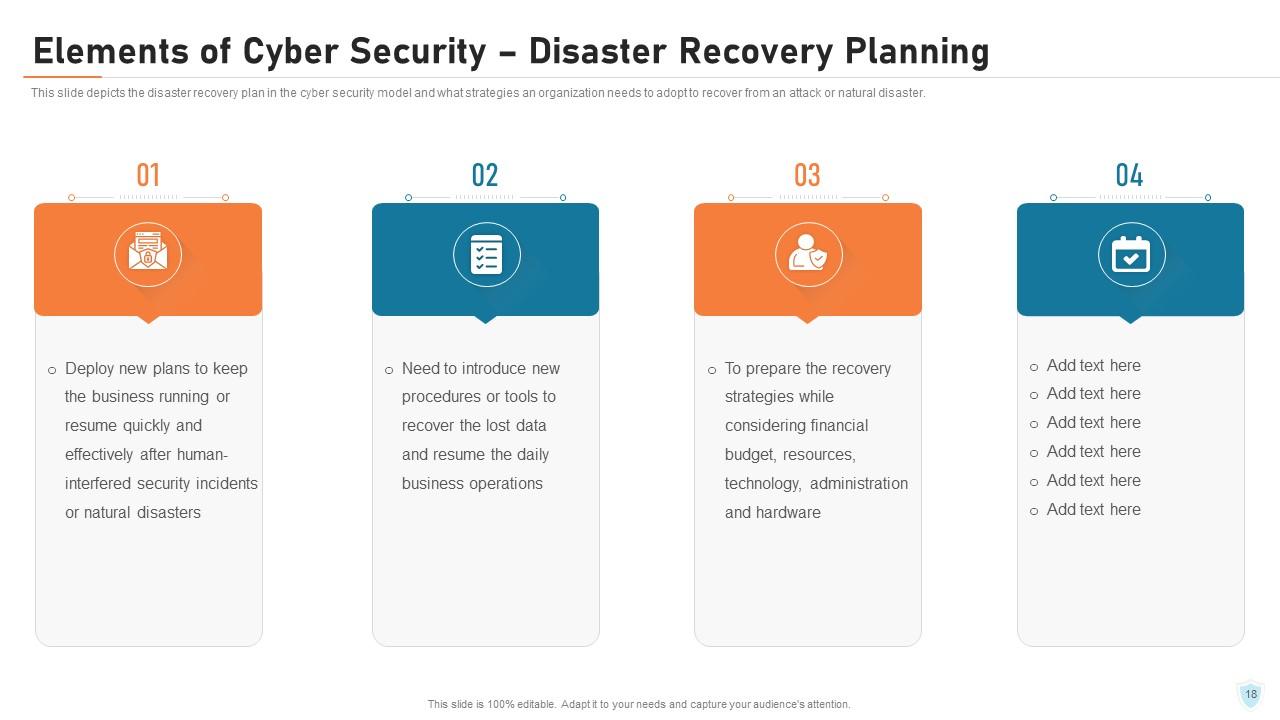
Slide 18: This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster.
Slide 19: This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc.
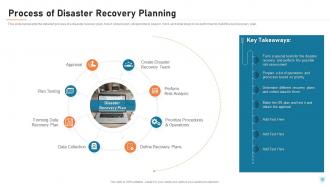
Slide 20: This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan.
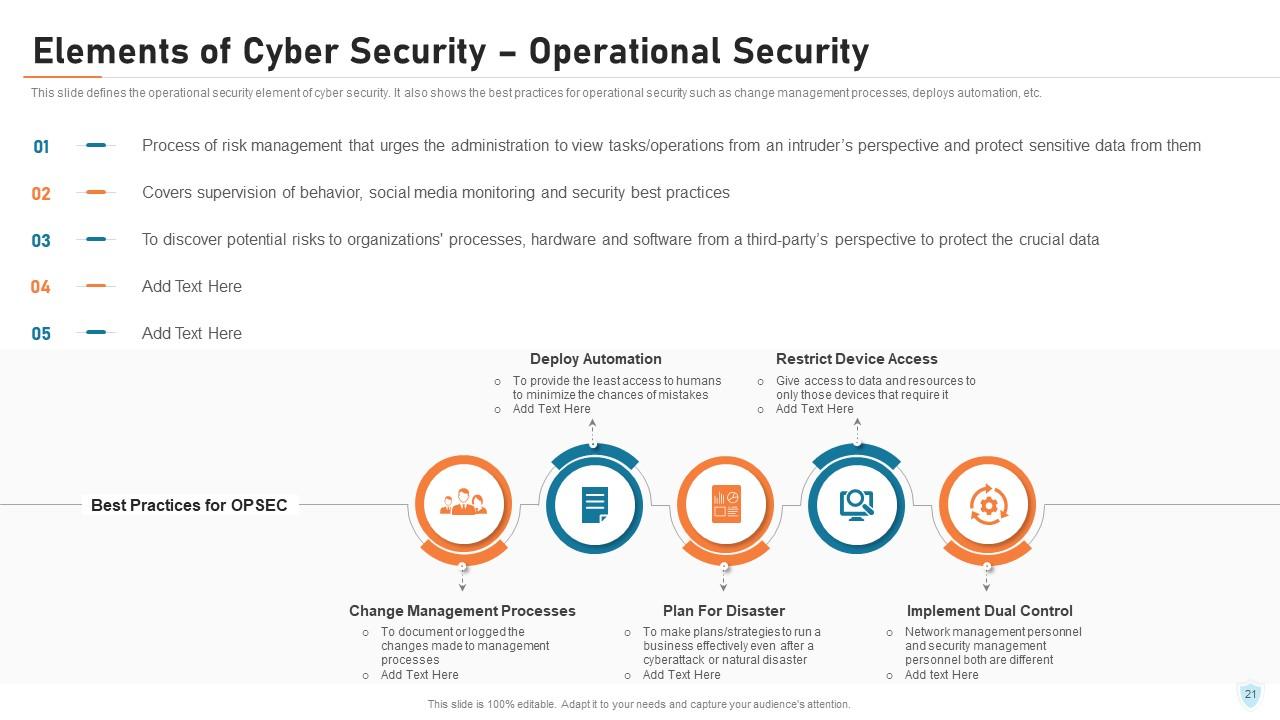
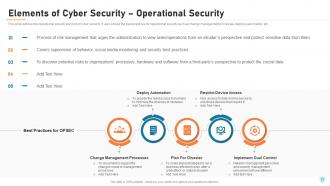
Slide 21: This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc.
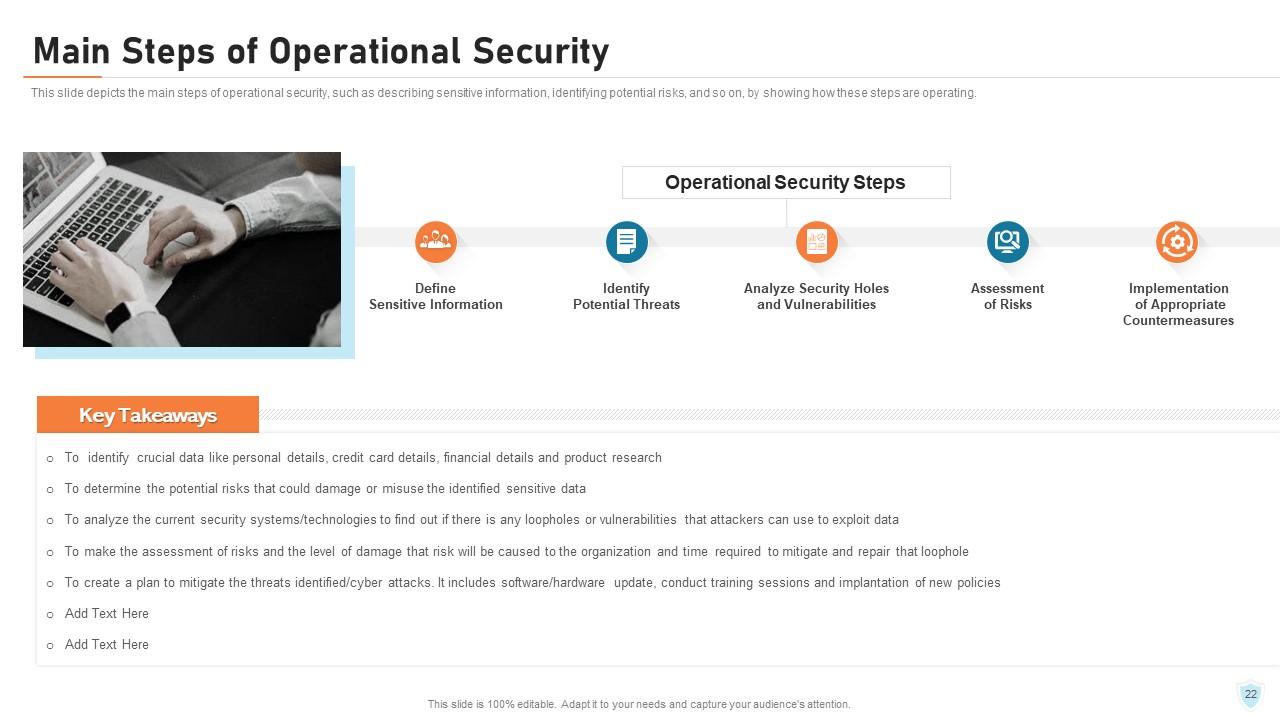
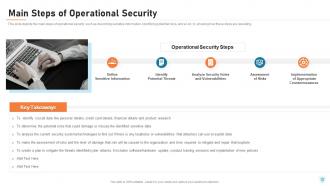
Slide 22: This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating.
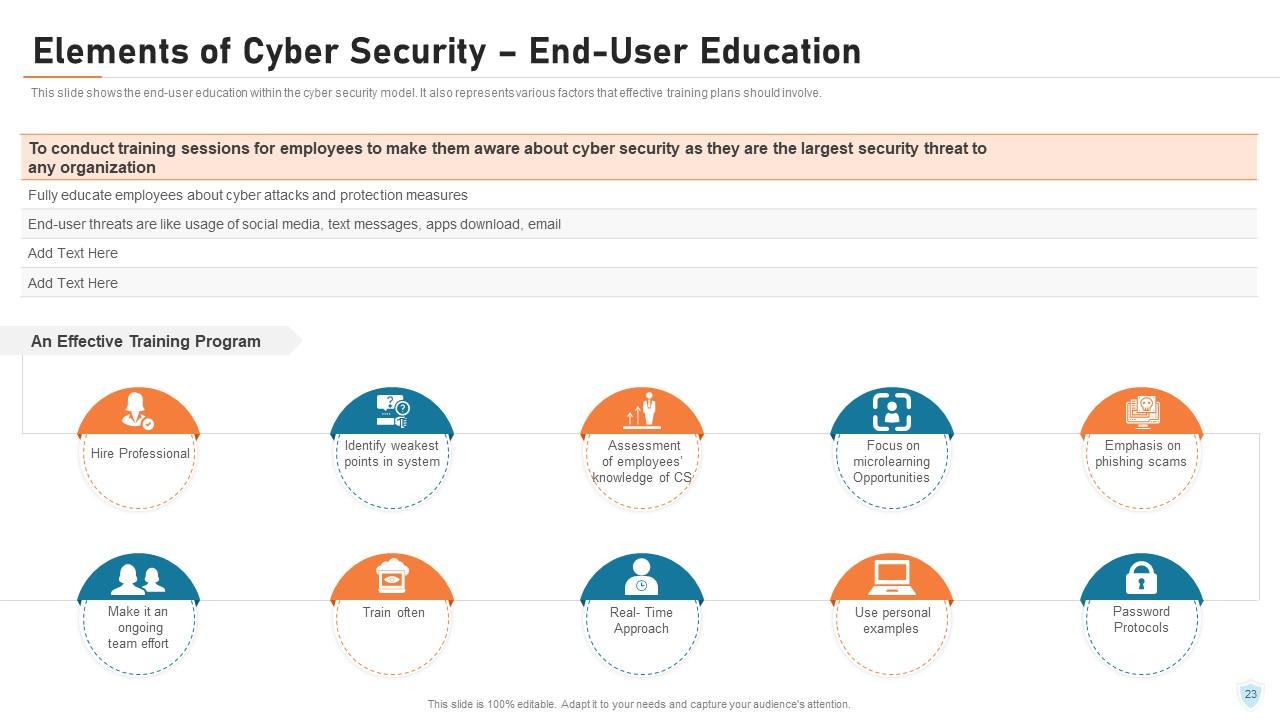
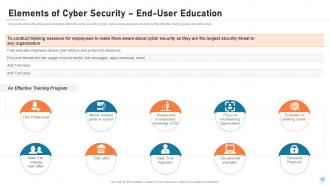
Slide 23: This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve.
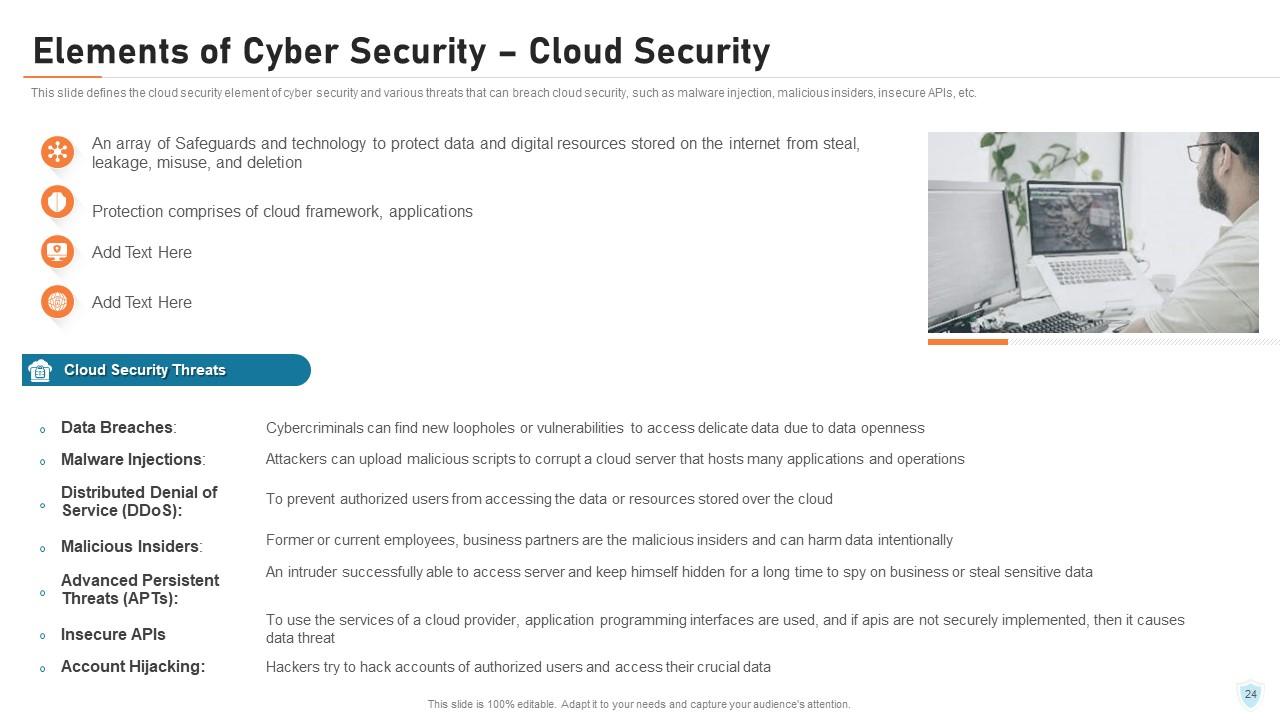
Slide 24: This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc.
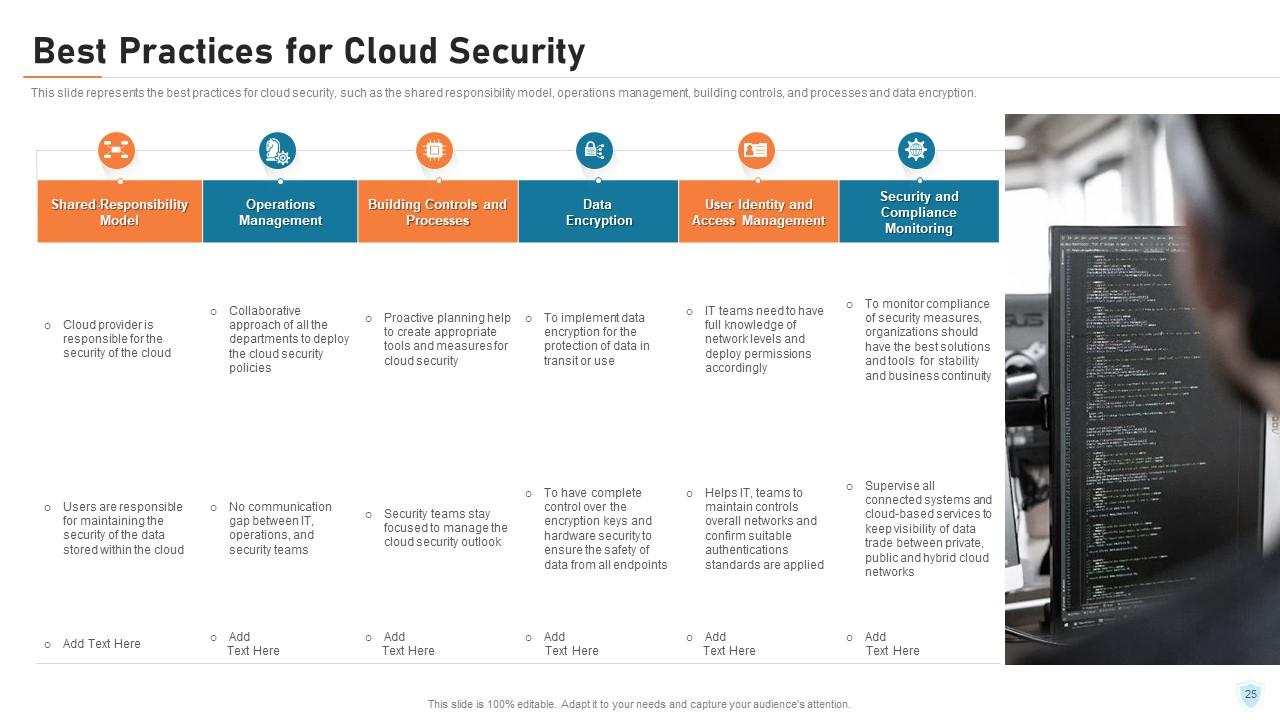
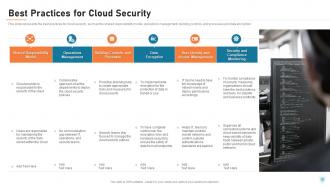
Slide 25: This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption.
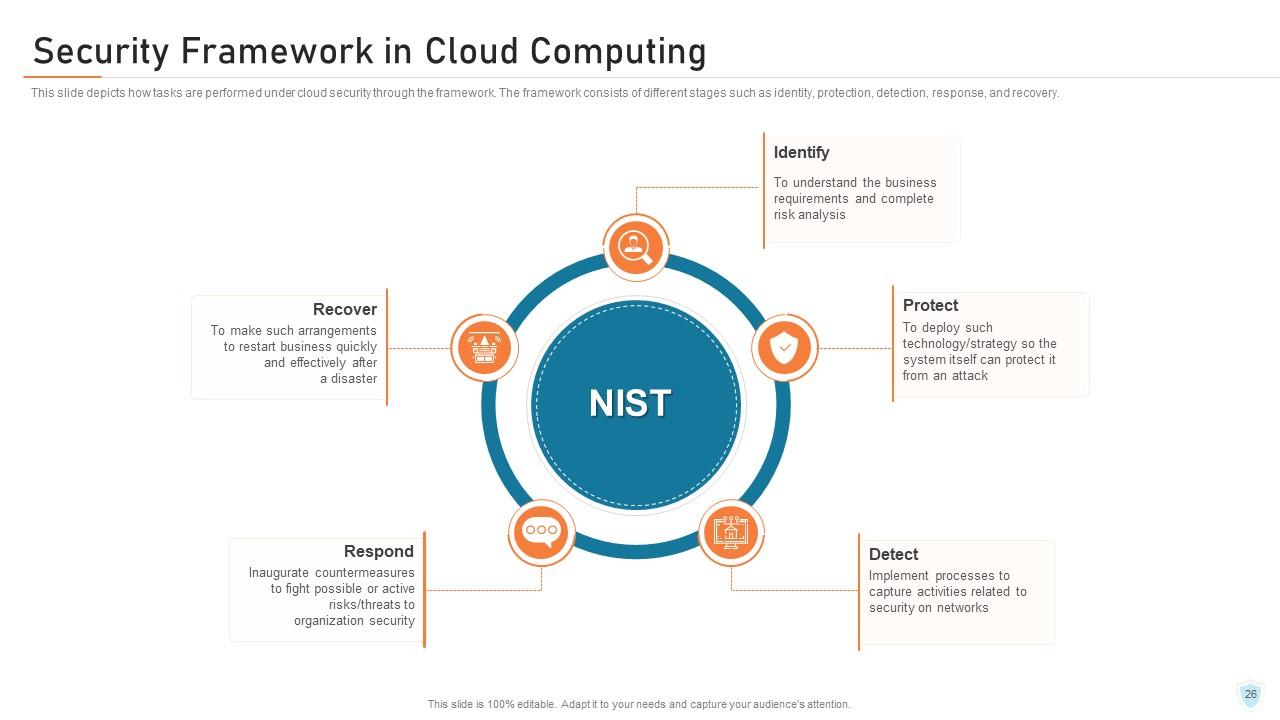
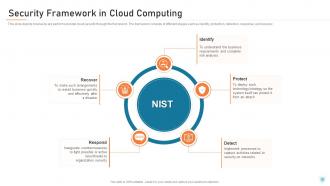
Slide 26: This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery.
Slide 27: This slide exhibits the title for cyber risk identification.
Slide 28: This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat.
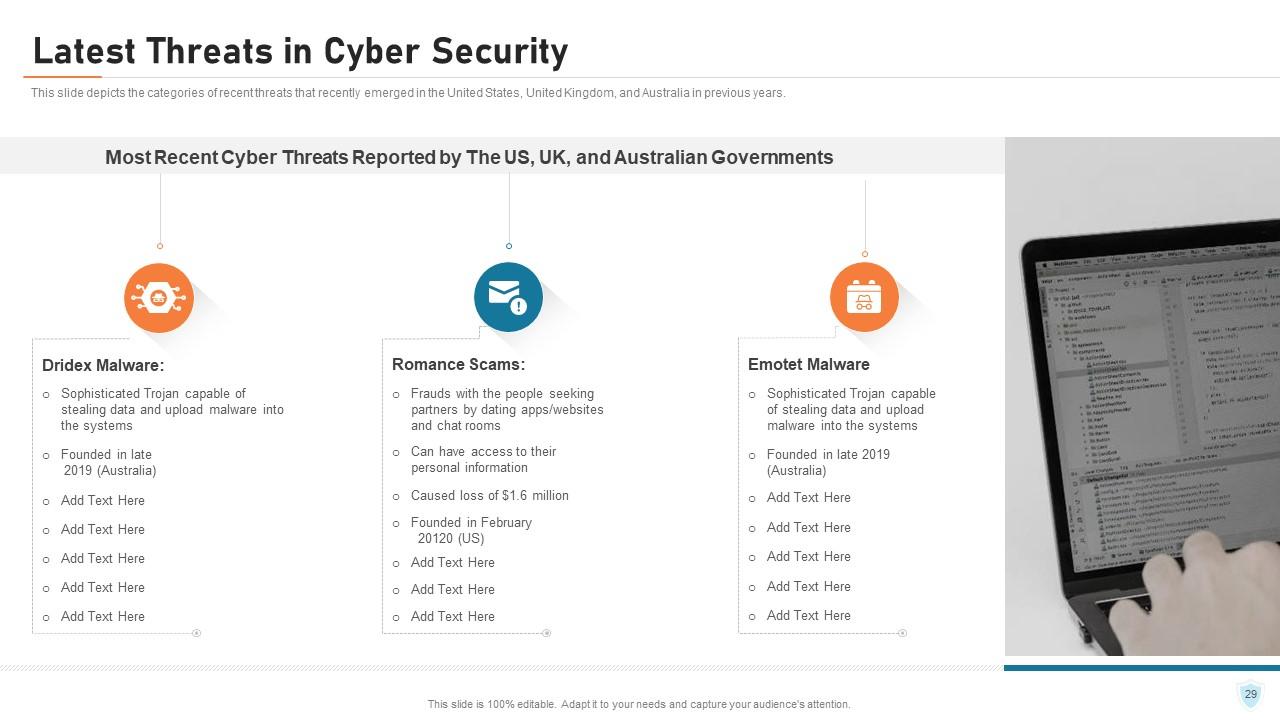
Slide 29: This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years.
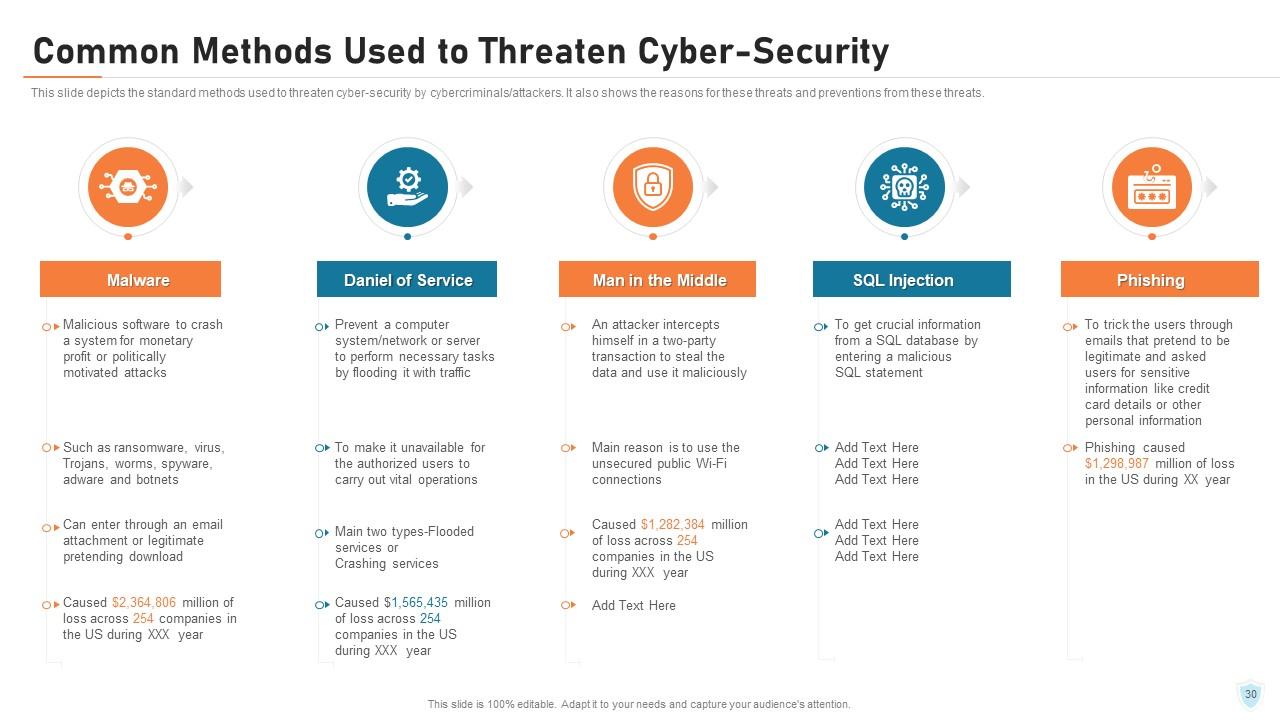
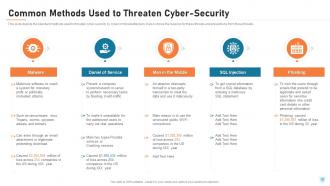
Slide 30: This slide depicts the standard methods used to threaten cyber-security by cybercriminals/attackers. It also shows the reasons for these threats and preventions from these threats.
Slide 31: This slide displays the title for cyber risk assessment.
Slide 32: This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web/mobile applications, online payments, employee devices.
Slide 33: This slide depicts the cyber threat landscape based on cybercriminal roles/actors and the impacts of successful cyberattacks on business.
Slide 34: This slide presents the title for steps for mitigation.
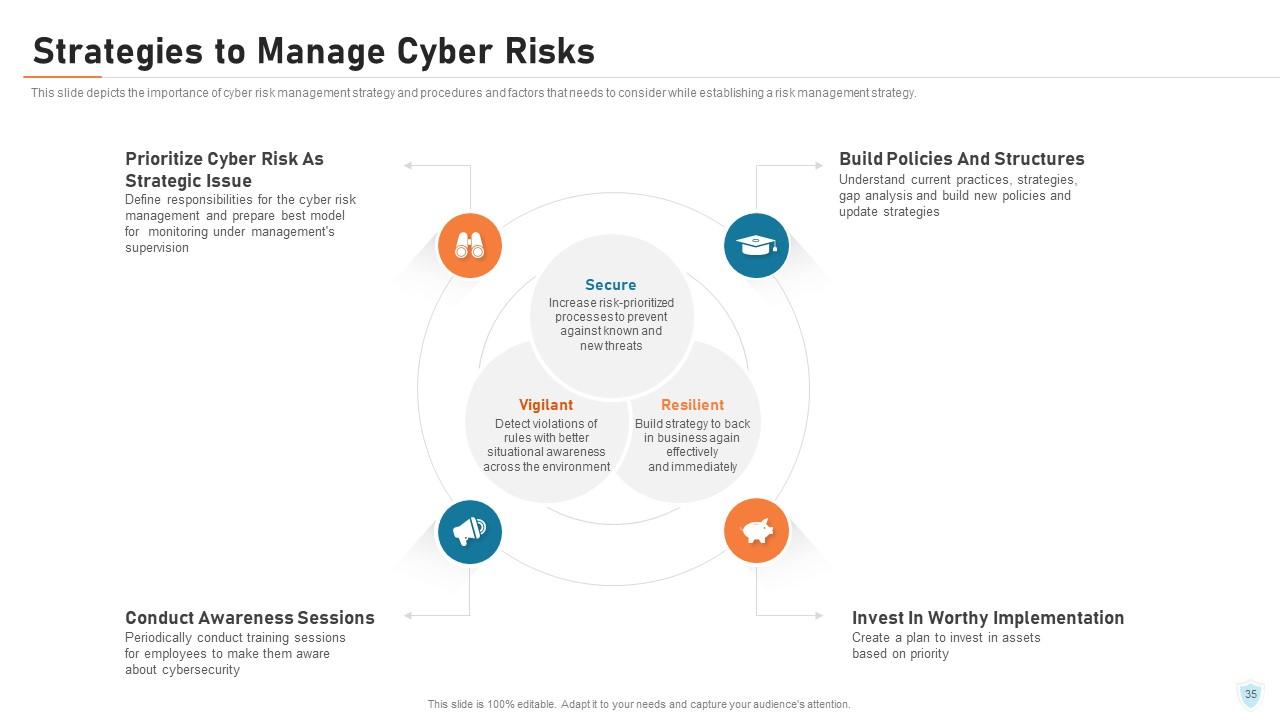
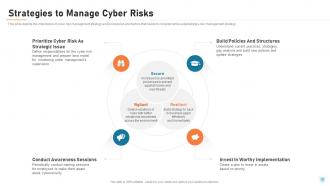
Slide 35: This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy.
Slide 36: This slide represents various tips or procedures that can be followed to prevent an organization's cyber security from cyberattacks or cybercriminals.
Slide 37: This slide exhibits the title for benefits of cybersecurity.
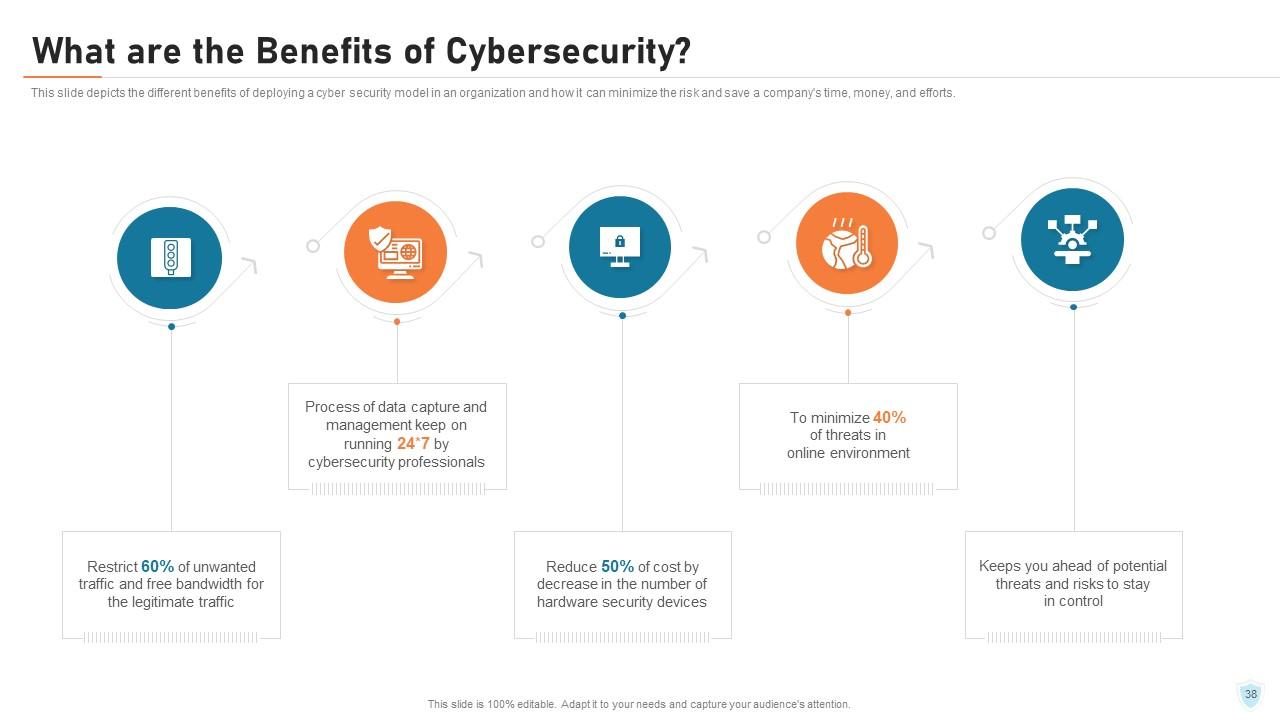
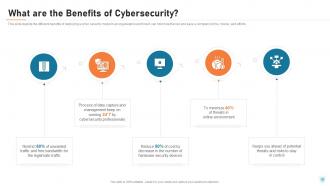
Slide 38: This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a company's time, money, and efforts.
Slide 39: This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a company's time, money, and efforts.
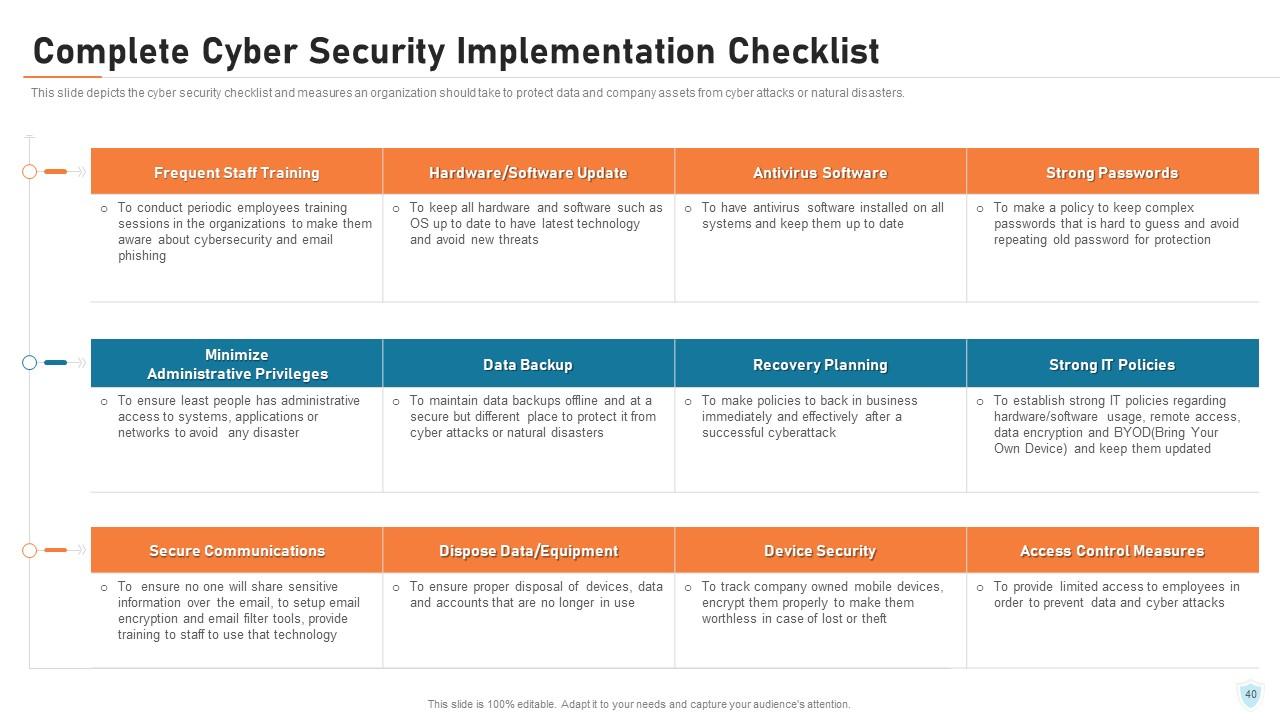
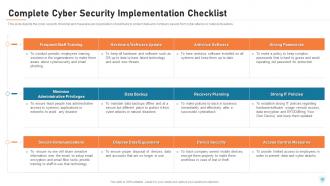
Slide 40: This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber-attacks or natural disasters.
Slide 41: This slide presents the title for cyber security implementation.
Slide 42: This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily.
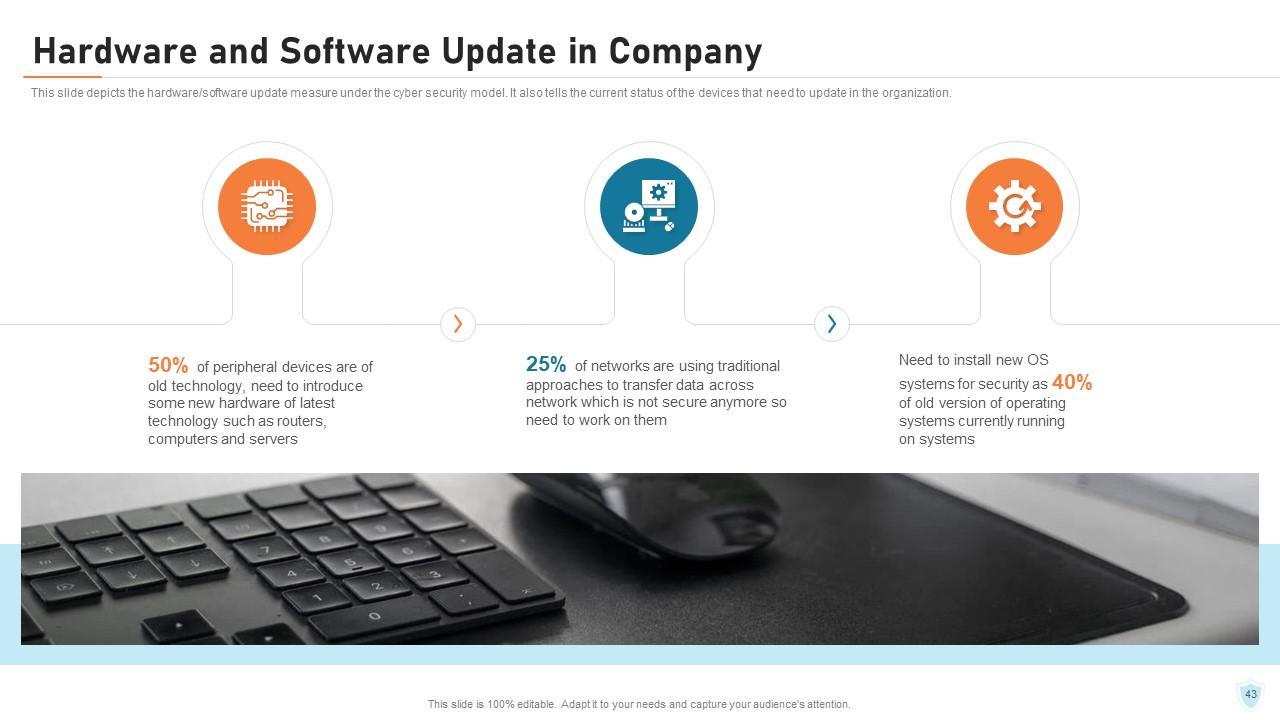
Slide 43: This slide depicts the hardware/software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization.
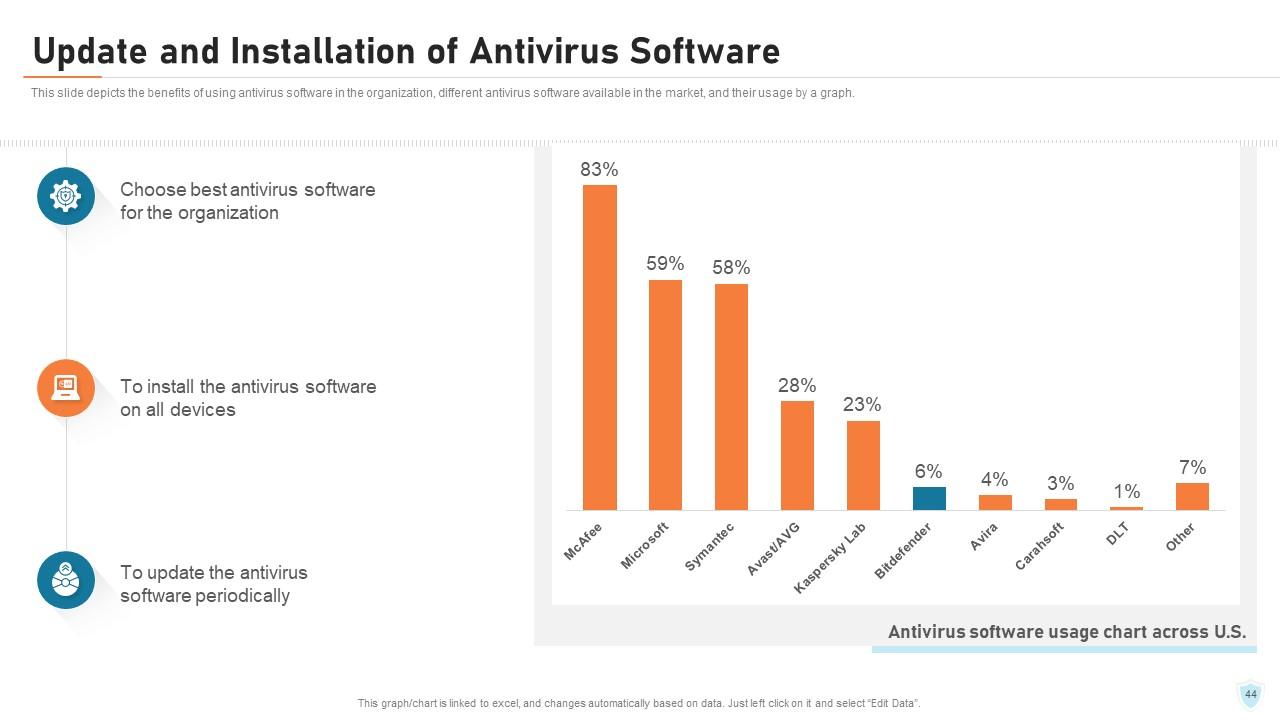
Slide 44: This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph.
Slide 45: This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts.
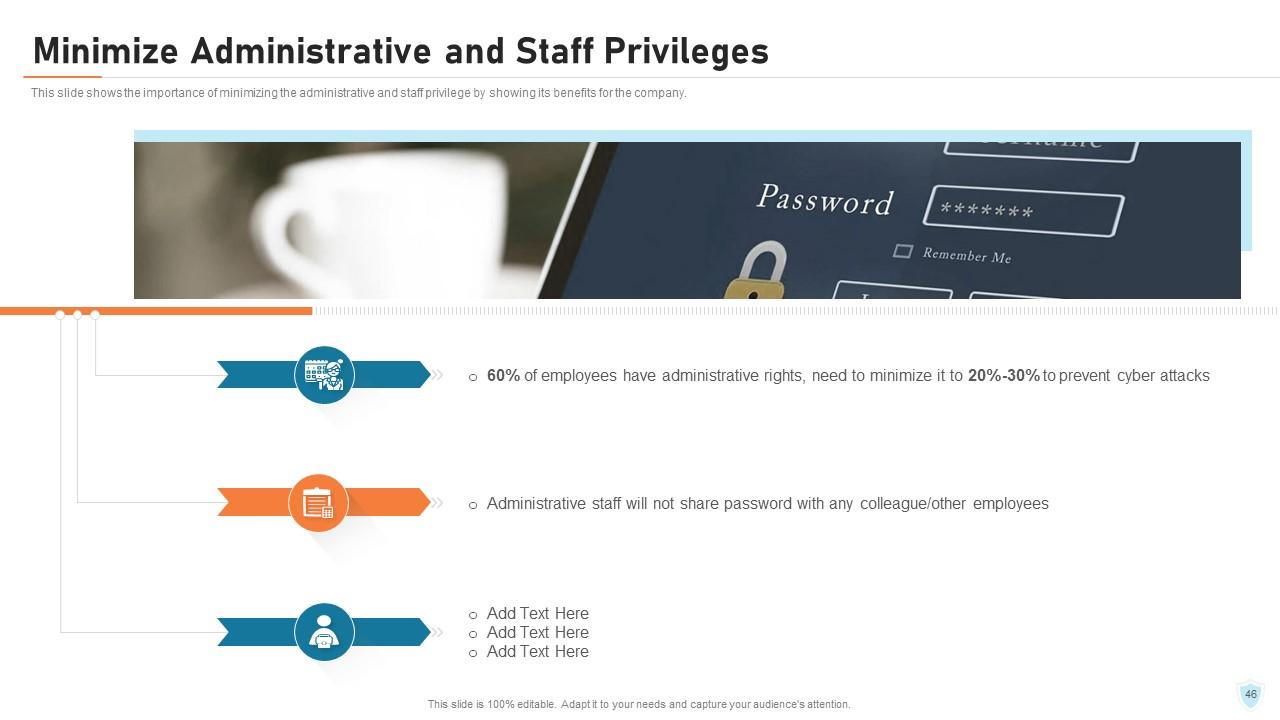
Slide 46: This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company.
Slide 47: This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization.
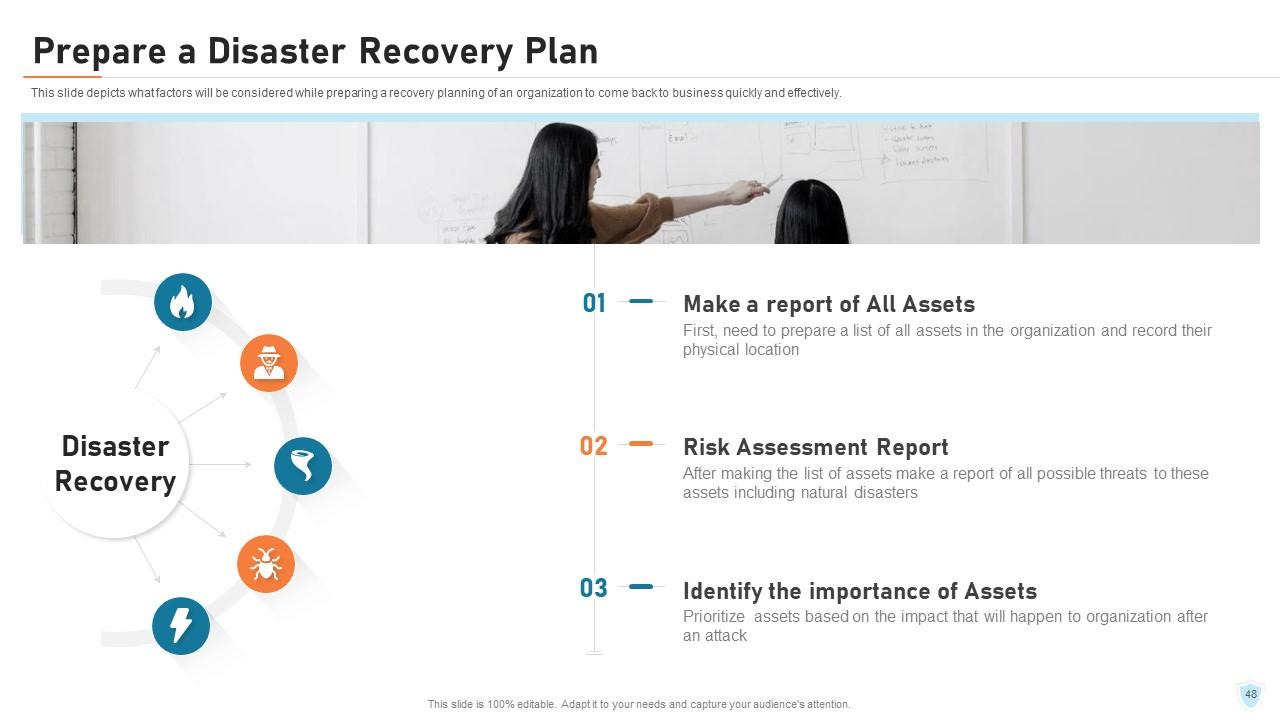
Slide 48: This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively.
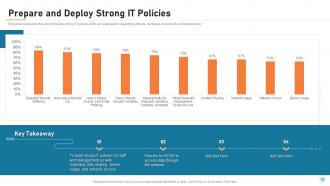
Slide 49: This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer.
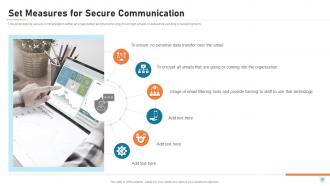
Slide 50: This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them.
Slide 51: This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization.
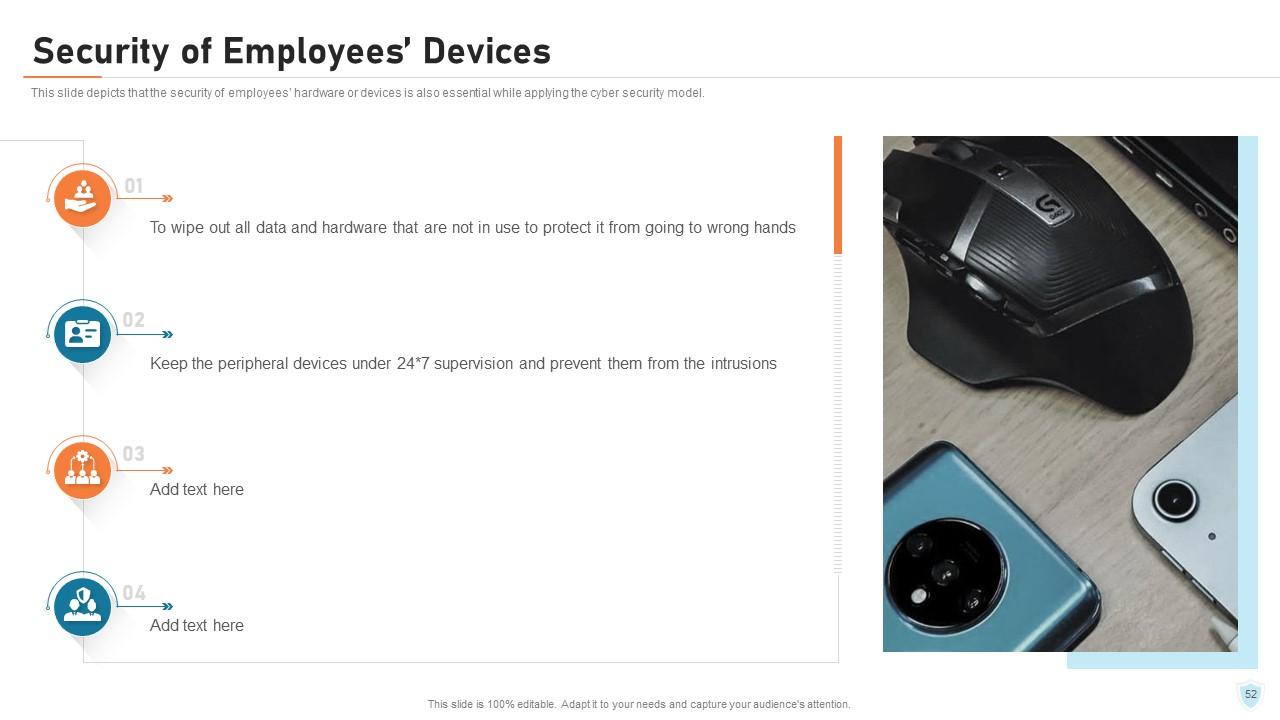
Slide 52: This slide depicts that the security of employees’ hardware or devices is also essential while applying the cyber security model.
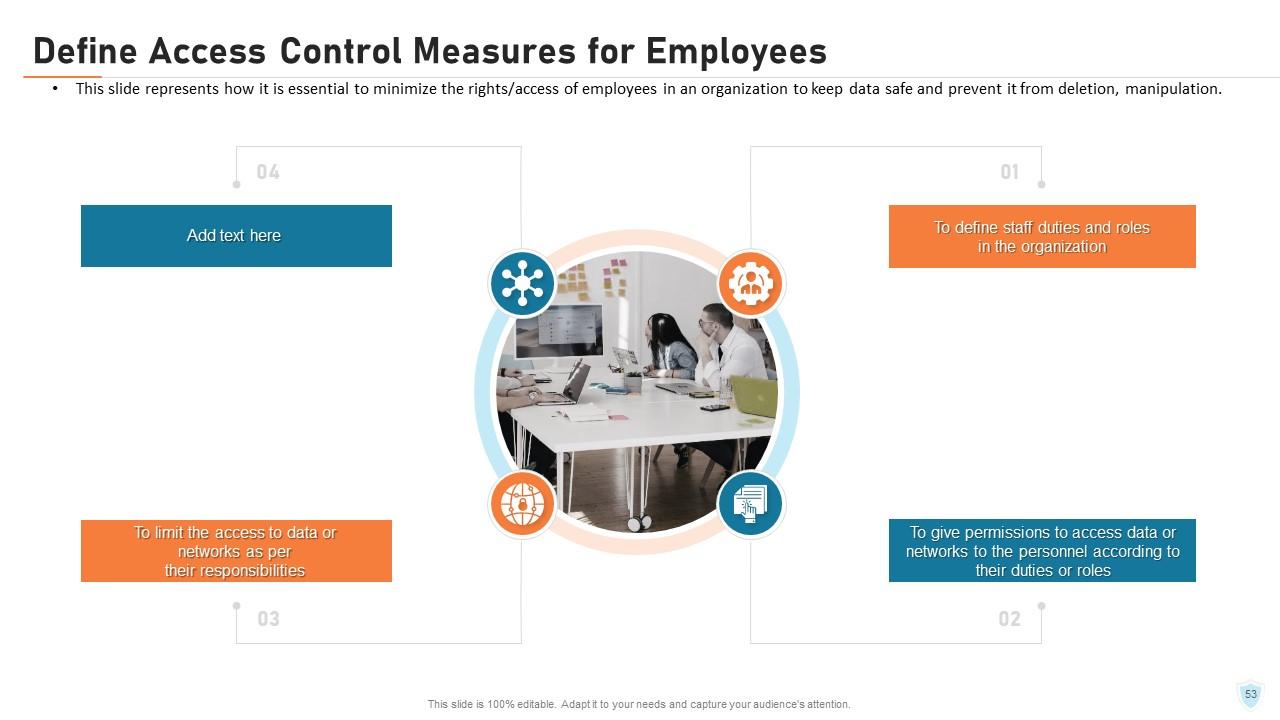
Slide 53: This slide represents how it is essential to minimize the rights/access of employees in an organization to keep data safe and prevent it from deletion, manipulation.
Slide 54: This slide presents the title for managing cyber security.
Slide 55: This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on.
Slide 56: This slide represents the plan for 60 days after implementing the cyber security model in the organization.
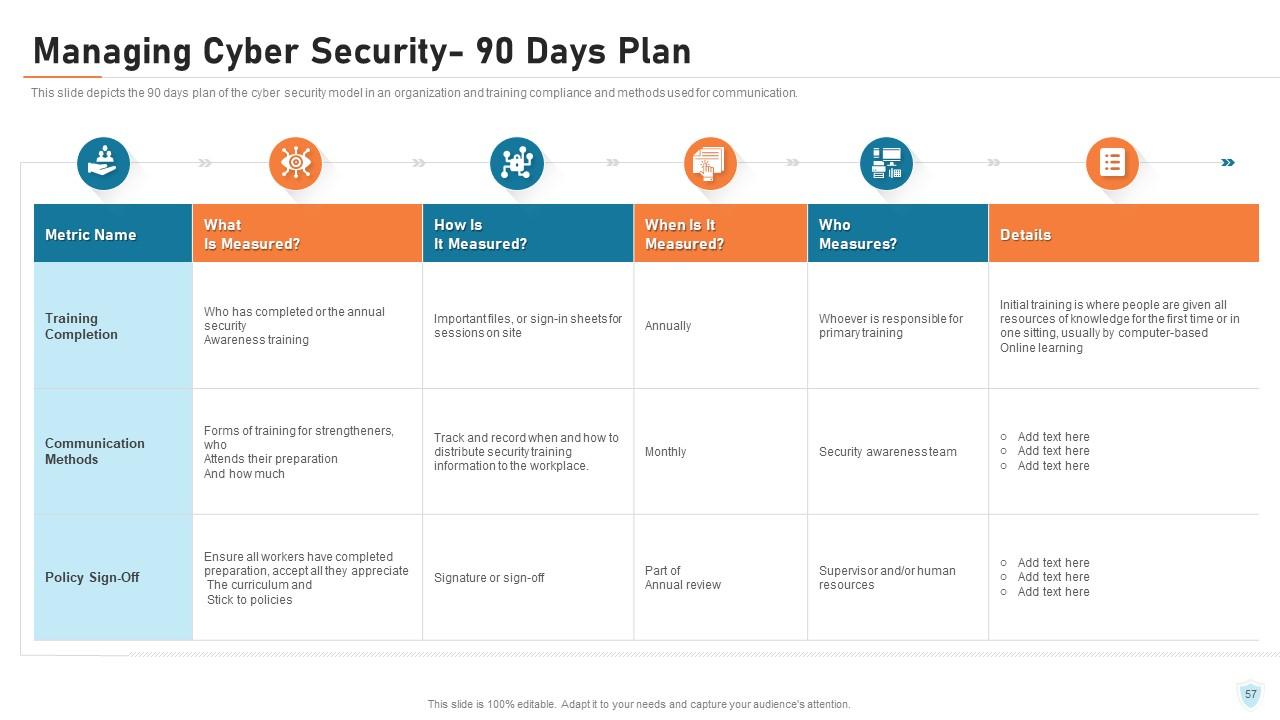
Slide 57: This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication.
Slide 58: This slide exhibits the title for cyber security budget.
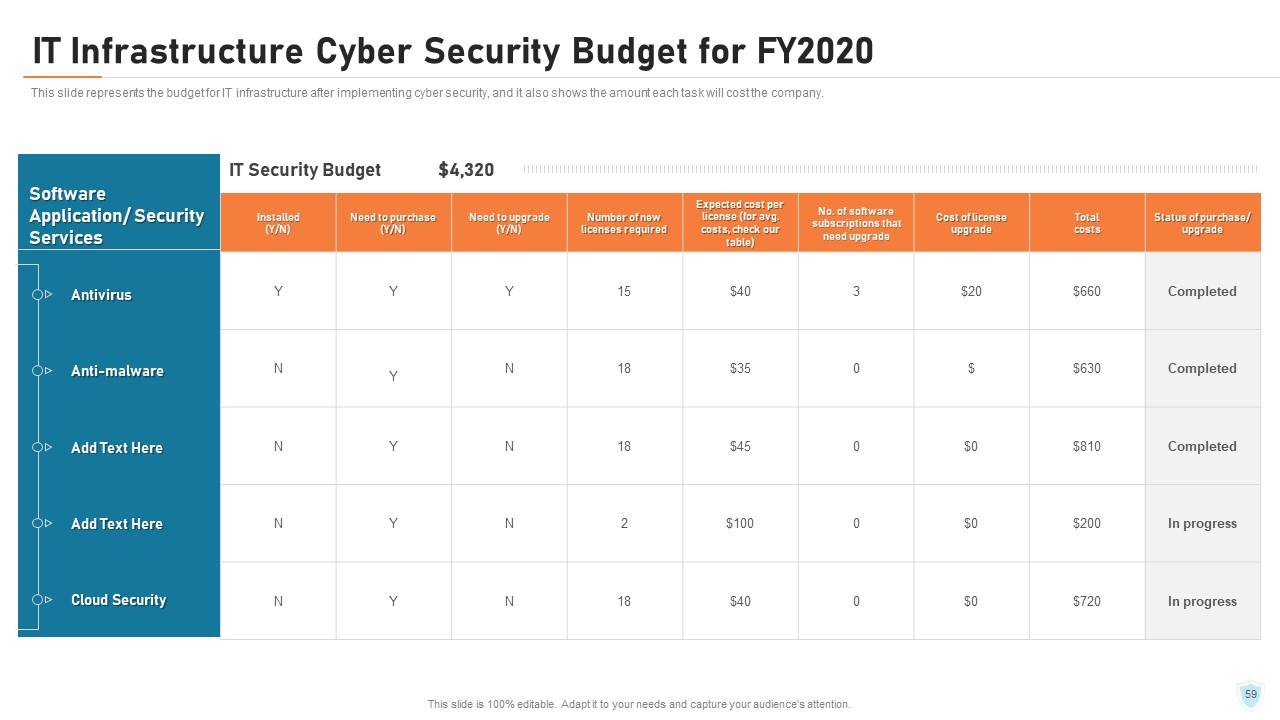
Slide 59: This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company.
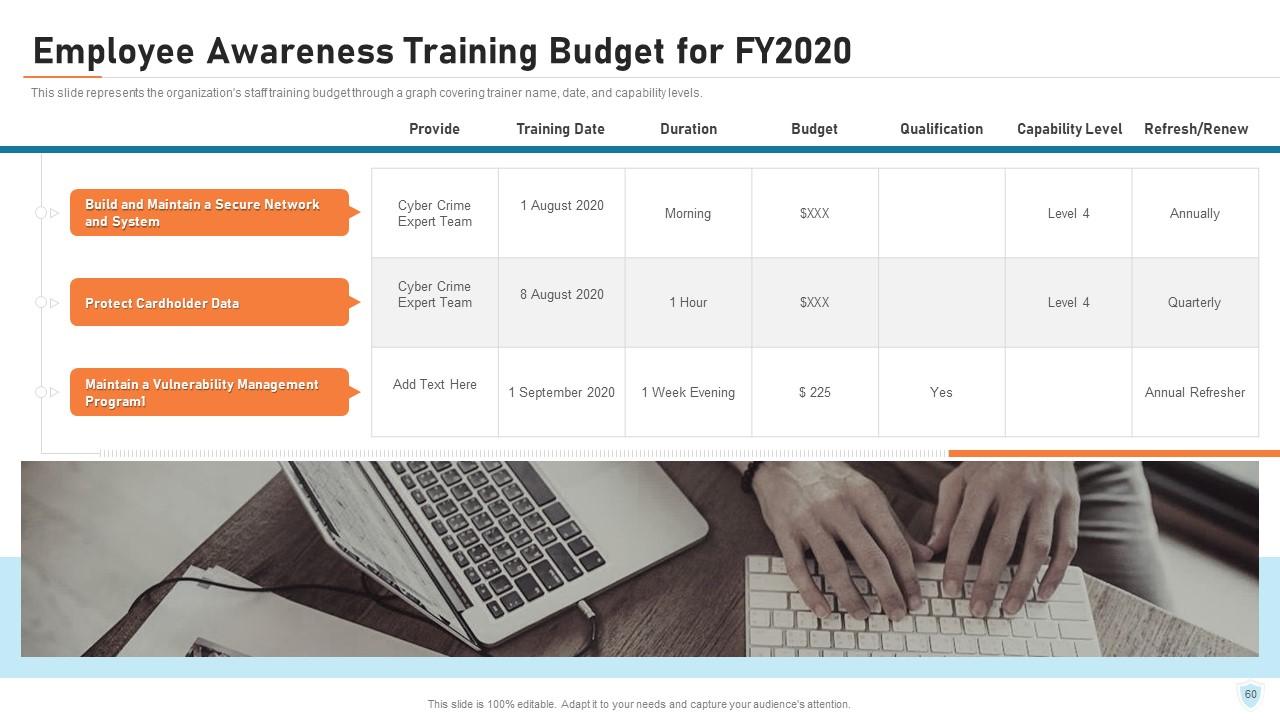
Slide 60: This slide represents the organization's staff training budget through a graph covering trainer name, date, and capability levels.
Slide 61: This slide displays the title for cyber security roadmap.
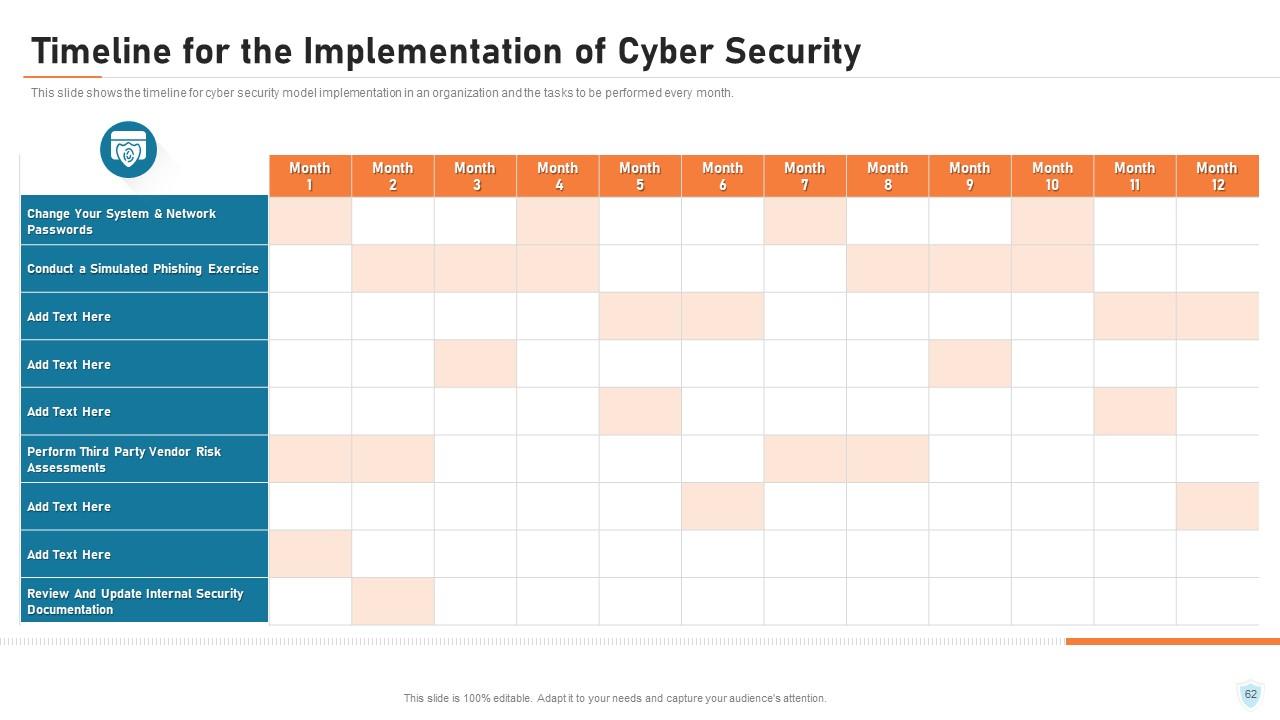
Slide 62: This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month.
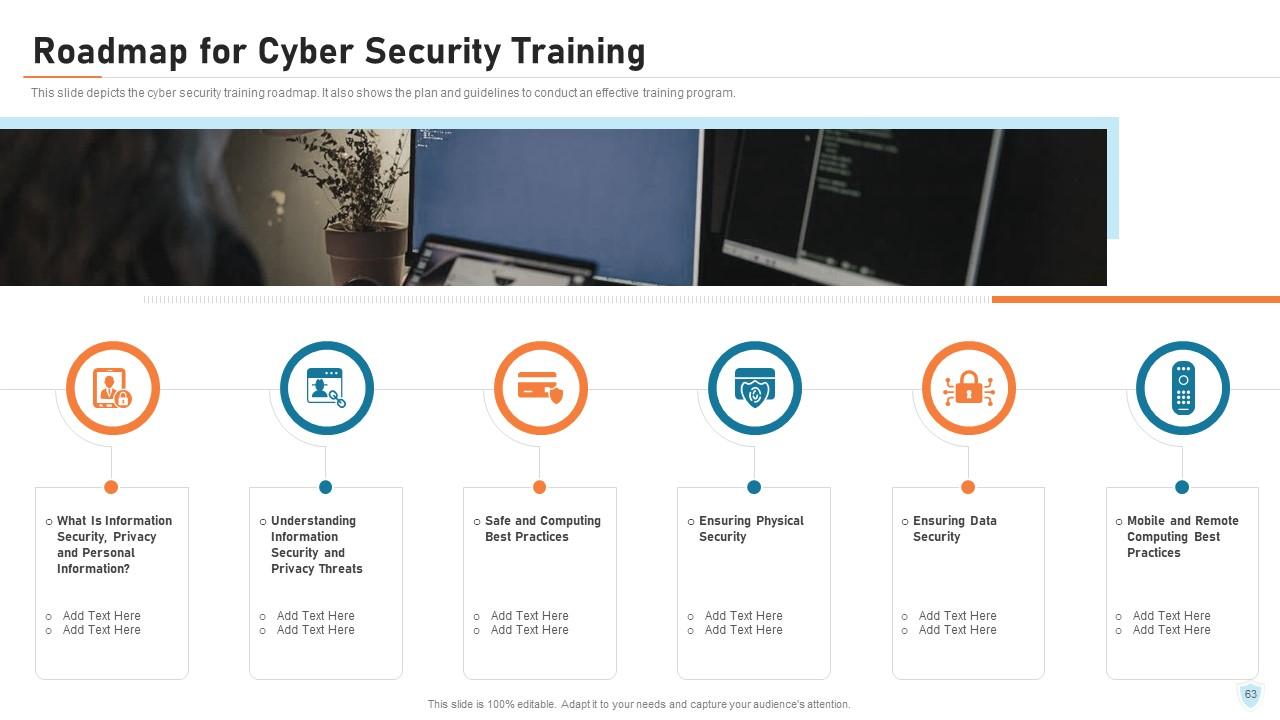
Slide 63: This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program.
Slide 64: This slide presents the title for effect of implementing cyber security in business
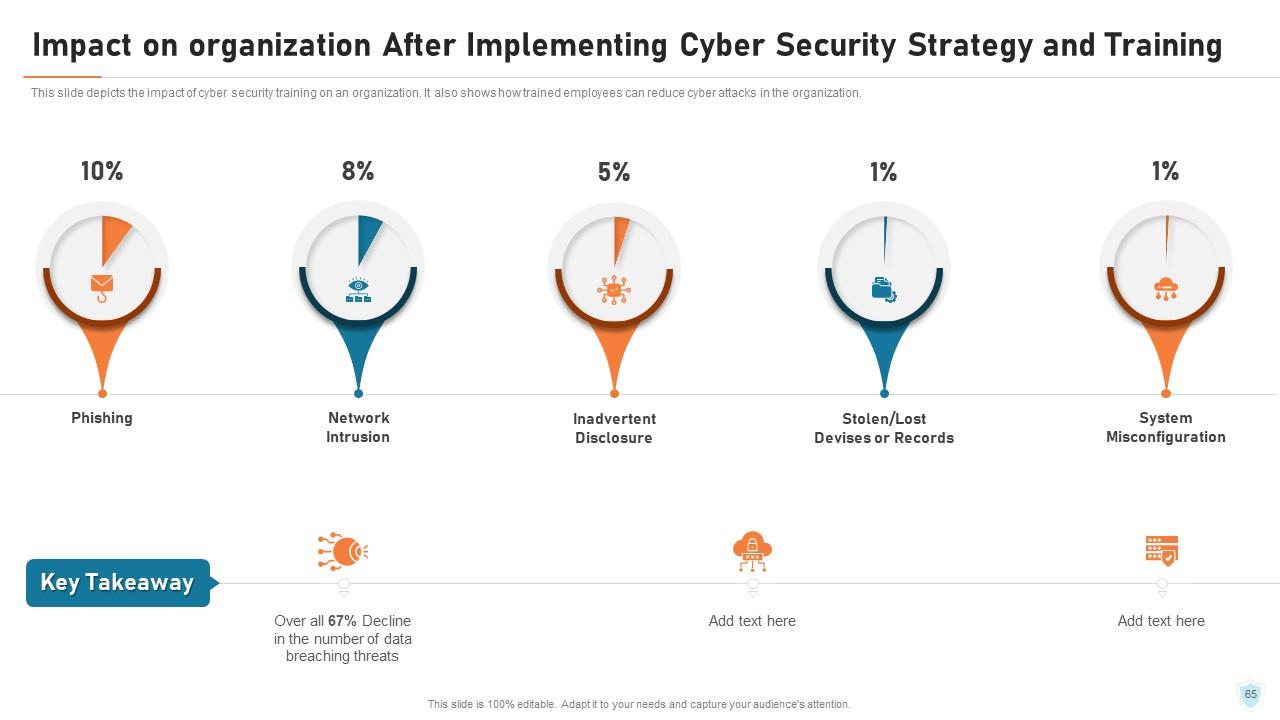
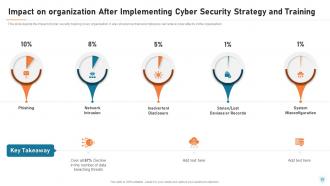
Slide 65: This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber-attacks in the organization.
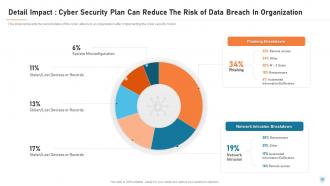
Slide 66: This slide represents the status of the cyber-attacks in an organization after implementing the cyber security model.
Slide 67: This slide exhibits the title for dashboards for cyber security tracking.
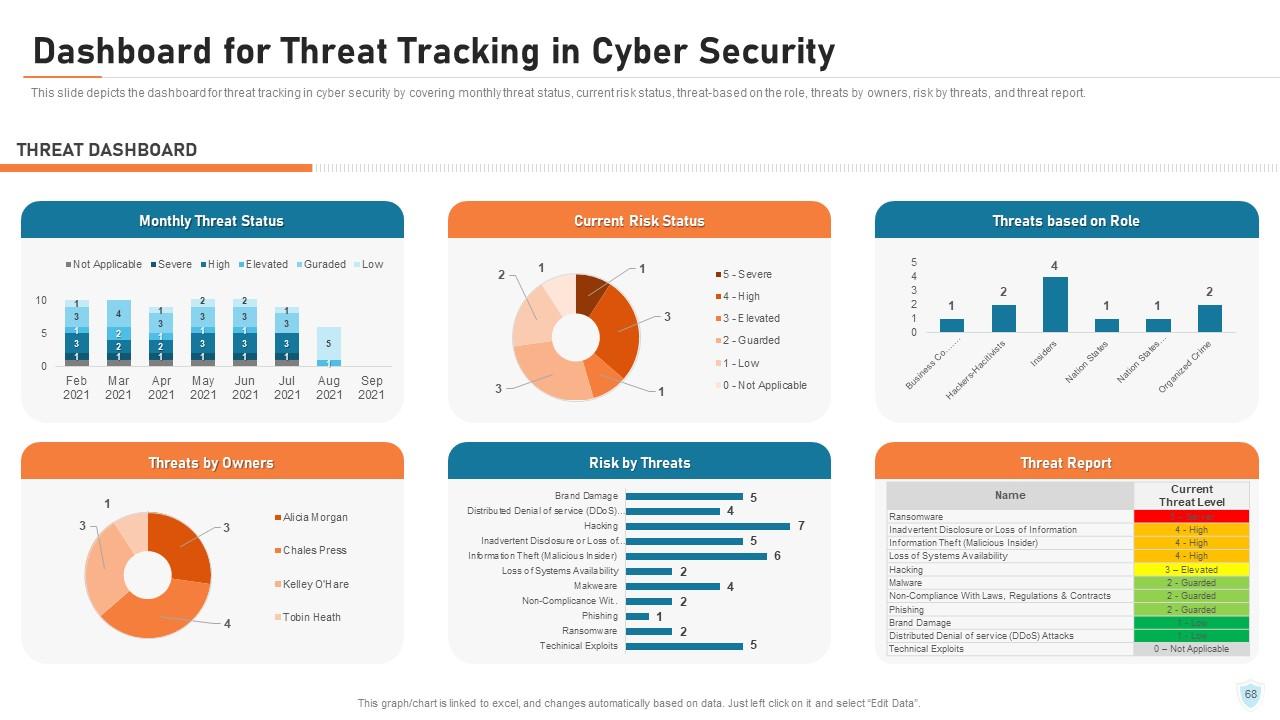
Slide 68: This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.
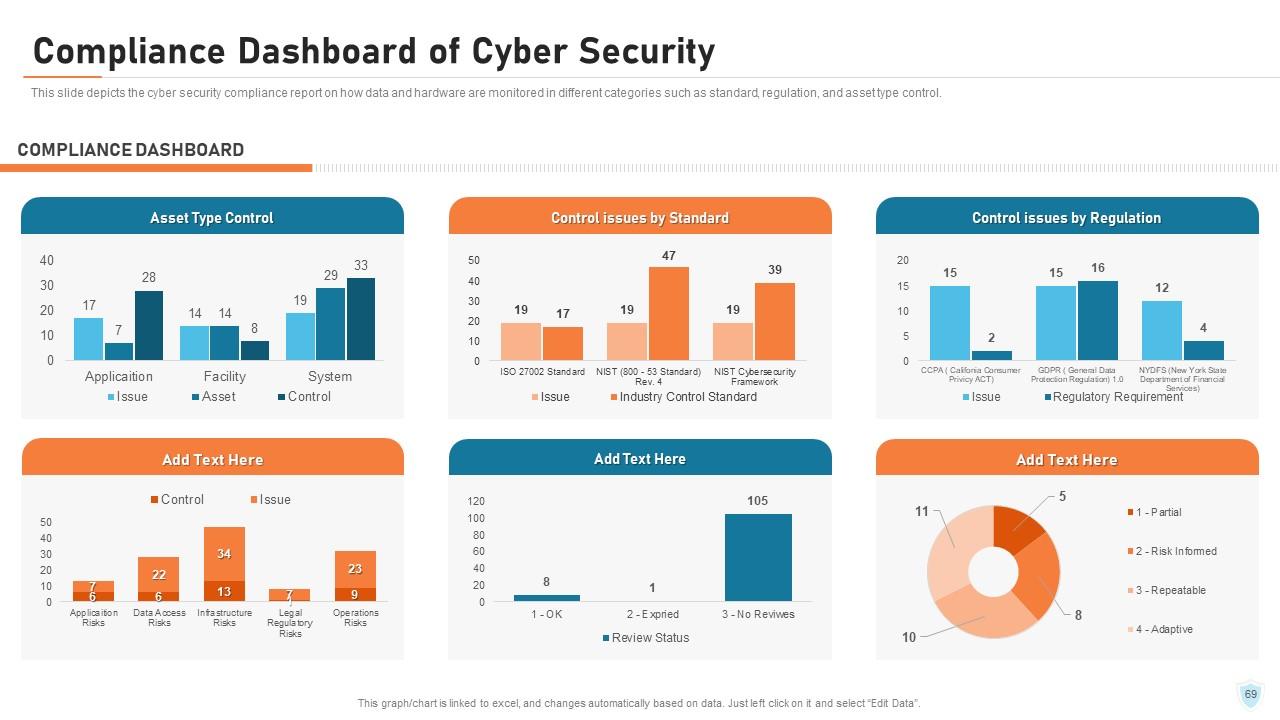
Slide 69: This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control.
Slide 70: This is the icons slide for cyber security.
Slide 71: This slide presents the title for additional slides.
Slide 72: This slide showcases about the company, target audience, client’s values, etc.
Slide 73: This slide demonstrates the details of the team members, their name and designation.
Slide 74: This slide displays the vision, mission, and goal of the company.
Slide 75: This slide showcases the posts for past feedbacks and experiences of the clients.
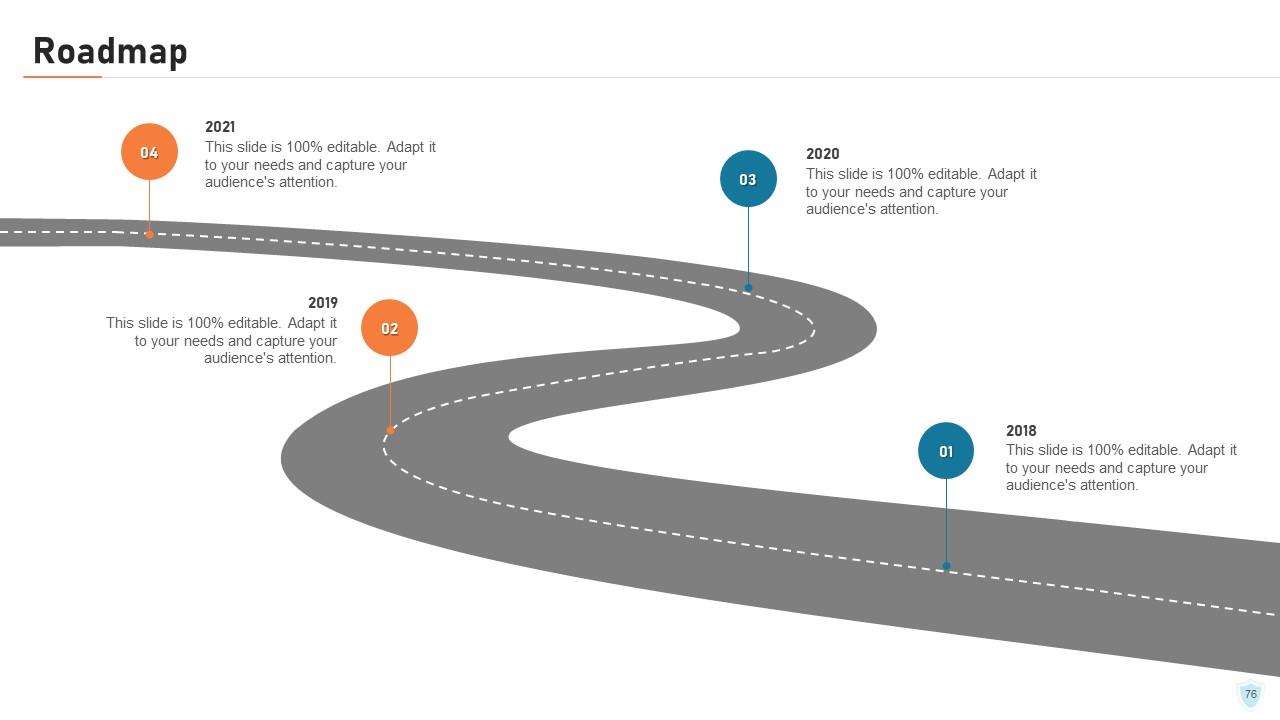
Slide 76: This slide presents the roadmap of the company over the years.
Slide 77: This slide displays the 30-60-90 days plan of the project.
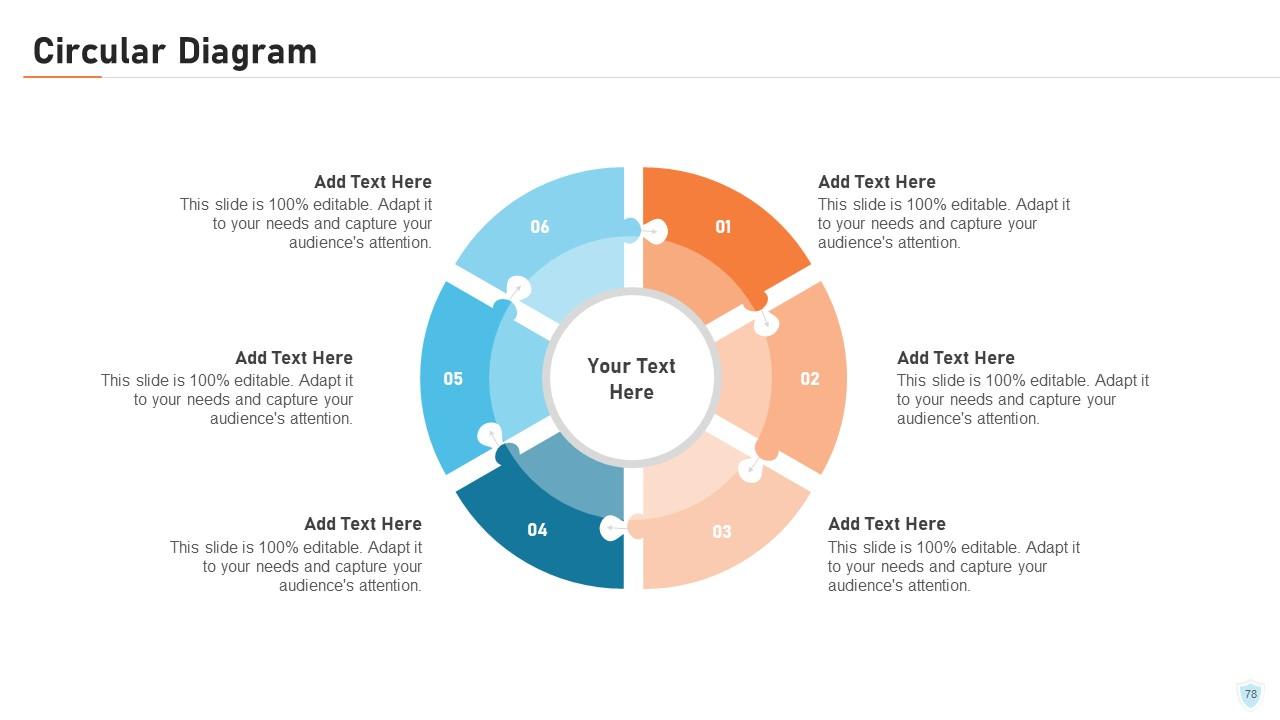
Slide 78: This slide showcases the circular diagram of the project.
Slide 79: This slide exhibits the goal of the company.
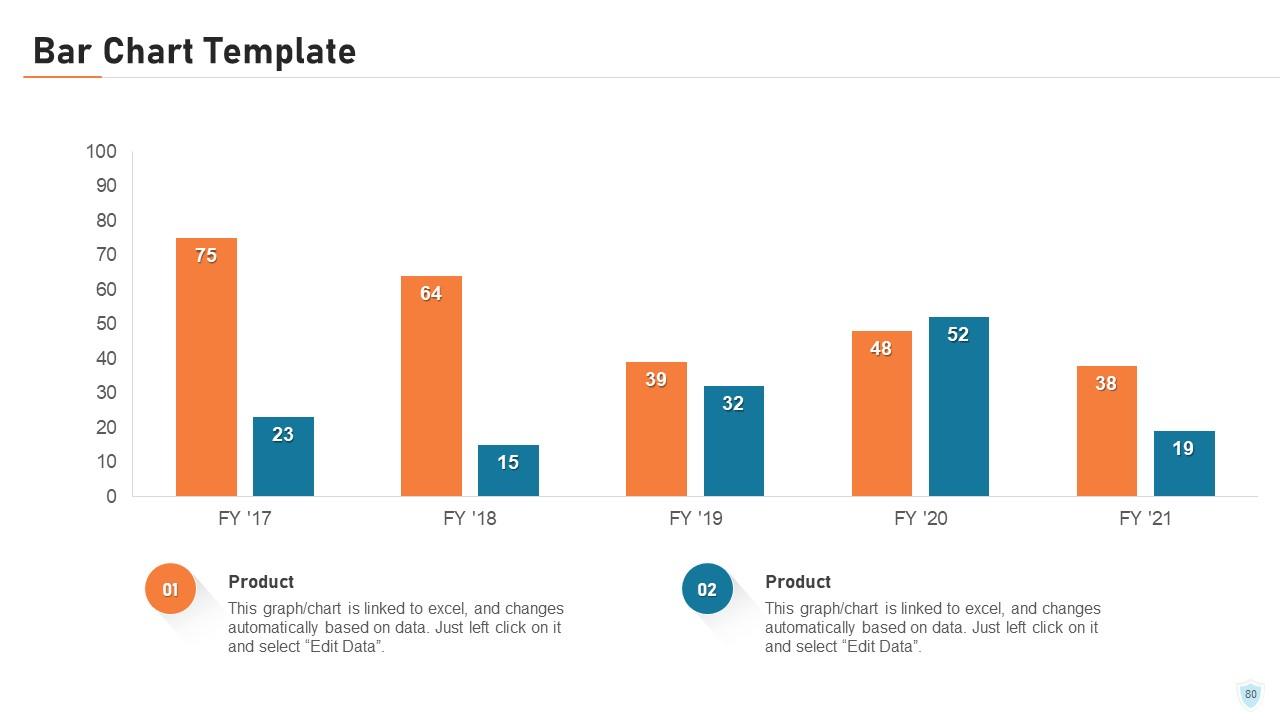
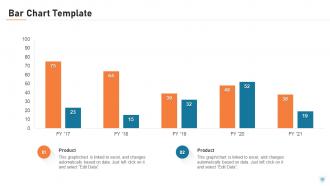
Slide 80: This slide presents the yearly bar charts for the products. The charts are linked to Excel.
Slide 81: This is the thank you slide and contains contact details of the company like phone no., address, etc.
Cyber security it powerpoint presentation slides with all 81 slides:
Use our Cyber Security It Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
FAQs
Cyber security is important for organizations as it helps prevent data breaches through different methods and techniques. Different sectors have experienced cyber attacks in the past, causing total losses to organizations.
The key elements of cyber security include application security, network security, information security, disaster recovery plan, operational security, end-user education, and cloud security.
The best practices for cloud security include the shared responsibility model, operations management, building controls and processes, and data encryption.
Deploying a cyber security model in an organization can minimize risk and save time, money, and efforts. It can prevent data breaches, protect company assets, and ensure business continuity.
An organization can take various measures to protect data and company assets, including establishing a cyber risk management strategy, following cybersecurity best practices, conducting cyber risk assessment, and implementing a disaster recovery plan. A cyber security checklist can also be used to ensure the protection of data and company assets.
No Reviews