Attractive Security Technology Slides and Design
-
 Digital security lock to prevent cyber attacks
Digital security lock to prevent cyber attacksPresenting our set of slides with Shopping Web Portal For Online Purchases. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Shopping Web Portal For Online Purchases.
-
 Loss Prevention Icon With Security System
Loss Prevention Icon With Security SystemIntroducing our premium set of slides with Loss Prevention Icon With Security System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Loss Prevention Icon With Security System. So download instantly and tailor it with your information.
-
 Key icon with employee having authority
Key icon with employee having authorityPresenting this set of slides with name Key Icon With Employee Having Authority. This is a three stage process. The stages in this process are Key Icon With Employee Having Authority. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Approval sign for enhanced credibility
Approval sign for enhanced credibilityPresenting this set of slides with name Approval Sign For Enhanced Credibility. This is a three stage process. The stages in this process are Approval Sign For Enhanced Credibility. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security shield expressing degree of credibility
Security shield expressing degree of credibilityPresenting this set of slides with name Security Shield Expressing Degree Of Credibility. This is a three stage process. The stages in this process are Security Shield Expressing Degree Of Credibility. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 16768345 style technology 2 security 3 piece powerpoint presentation diagram infographic slide
16768345 style technology 2 security 3 piece powerpoint presentation diagram infographic slideOur presentation on “Key Messages To Communicate PowerPoint Slide Template” is adaptable to all software for easy running. It can be converted to JPG and PDF conveniently. It is also compatible with Google slides and can be conveniently viewed in different screens. It is easy to insert company logo, name and trademark. Highly customizable layout including font, text, color and design makes it a ready to use presentation. High resolution PPT graphic is incorporated for better clarity. Use our remarkable presentation at ease and lessen your burden.
-
 Image of internet security with a lock
Image of internet security with a lockPresenting this set of slides with name Image Of Internet Security With A Lock. This is a one stage process. The stages in this process are Internet, Marketing, Internet Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cloud computing data protection binary security codes
Cloud computing data protection binary security codesPresenting this set of slides with name Cloud Computing Data Protection Binary Security Codes. This is a three stage process. The stages in this process are Cloud Computing Data Protection Binary Security Codes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Securing privacy policy on computer
Securing privacy policy on computerIntroducing our premium set of slides with Securing Privacy Policy On Computer. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Securing Privacy Policy On Computer. So download instantly and tailor it with your information.
-
 Setting password on laptop for privacy icon
Setting password on laptop for privacy iconIntroducing our premium set of slides with Setting Password On Laptop For Privacy Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Setting Password On Laptop For Privacy Icon. So download instantly and tailor it with your information.
-
 46874343 style essentials 1 agenda 6 piece powerpoint presentation diagram infographic slide
46874343 style essentials 1 agenda 6 piece powerpoint presentation diagram infographic slidePresenting lc six staged business staircase diagram and icons powerpoint template. Six staged staircase diagram and icons has been used to craft this Power Point template diagram. This PPT diagram contains the concept of business success representation. Use this PPT diagram for business and marketing related presentations.
-
 53027922 style technology 2 security 5 piece powerpoint presentation diagram infographic slide
53027922 style technology 2 security 5 piece powerpoint presentation diagram infographic slidePresenting a five staged key of success for financial analysis flat powerpoint design. This Power Point template diagram has been crafted with graphic of five staged key diagram. This PPT diagram contains the concept of success for financial analysis. Use this PPT diagram for business and finance related presentations.
-
 Security gate pass icon
Security gate pass iconPresenting this set of slides with name Security Gate Pass Icon. This is a three stage process. The stages in this process are Security Icon, Camera Security, Money Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Antivirus protect icon with tick mark
Antivirus protect icon with tick markPresenting this set of slides with name Antivirus Protect Icon With Tick Mark. This is a three stage process. The stages in this process are Antivirus Protect Icon With Tick Mark. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Mobile protect icon for internet security
Mobile protect icon for internet securityPresenting this set of slides with name Mobile Protect Icon For Internet Security. This is a one stage process. The stages in this process are Mobile Protect Icon For Internet Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Confidential document icon with protect guard
Confidential document icon with protect guardPresenting this set of slides with name Confidential Document Icon With Protect Guard. This is a three stage process. The stages in this process are Confidential Document Icon With Protect Guard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Survey Insights On Data Breach Risk Incidents Icon
Survey Insights On Data Breach Risk Incidents IconPresenting our set of slides with name Survey Insights On Data Breach Risk Incidents Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Survey Insights, Data Breach, Risk Incidents Icon.
-
 38679283 style technology 1 servers 2 piece powerpoint presentation diagram infographic slide
38679283 style technology 1 servers 2 piece powerpoint presentation diagram infographic slidePresenting code window and laptop icon with brackets. This is a code window and laptop icon with brackets. This is a two stage process. The stages in this process are code, programming, script, brackets.
-
 30287496 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
30287496 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting Search Code Icon Slide. It is also compatible with Google Slides and MS PowerPoint.Add this PPT into common images or document formats like JPEG and PDF. The PPT also supports the standard (4:3) and widescreen (16:9) sizes. Modify the style, size, background, etc. High-quality graphics ensures that there is no room for distortion.
-
 1260799 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
1260799 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting shield with tick mark and ribbon icon. This is a shield with tick mark and ribbon icon. This is a one stage process. The stages in this process are shield icon, protection icon, safety icon.
-
 75033139 style technology 2 security 4 piece powerpoint presentation diagram infographic slide
75033139 style technology 2 security 4 piece powerpoint presentation diagram infographic slidePresenting hotel safety and security icon 3. This is a hotel safety and security icon 3. This is a four stage process. The stages in this process are hotel safety and security, guest house safety, lodge safety.
-
 Key cyber security threat to organizations
Key cyber security threat to organizationsThis slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Introducing our premium set of slides with Key Cyber Security Threat To Organizations. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Malware, Phishing, SQL Injection. So download instantly and tailor it with your information.
-
 10805957 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
10805957 style technology 2 security 1 piece powerpoint presentation diagram infographic slideWe are proud to present our solution indication for business flat powerpoint design. Concept of solution indication has been explained in this power point template diagram with suitable graphics. This PPT diagram contains the graphic of key hole and man with key. Use this PPT diagram for business and marketing related presentations and display solutions.
-
 90915144 style technology 2 security 2 piece powerpoint presentation diagram infographic slide
90915144 style technology 2 security 2 piece powerpoint presentation diagram infographic slidePresenting Lock Puzzle With Keys To Open. The template is available in both standard and widescreen. It is compatible with Google Slides, which makes it accessible at once. It can be transformed into various formats like PDF, JPG, and PNG. You can modify the color, font, font type, and font size of the slide as per the requirements. All the elements of this slide are under your control. Get this ready to use the template in just one click.
-
 94839152 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
94839152 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting White Lock Icon With Circular Arrow which is completely editable. It is available in both 4:3 and 16:9 aspect ratio. It can be converted into various formats like PDF, JPG, and PNG. You can customize the color, font, font types, and font size of the slides as per your requirements. This template is adaptable with Google Slides which makes it easily accessible at once.
-
 28109586 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
28109586 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting door lock key icon. This is a door lock key icon. This is a one stage process. The stages in this process are key icon, lock icon.
-
 89111674 style technology 2 security 4 piece powerpoint presentation diagram infographic slide
89111674 style technology 2 security 4 piece powerpoint presentation diagram infographic slidePresenting keys icon. This is a keys icon. This is a four stage process. The stages in this process are key icon, lock icon.
-
 Application user interface authentication login
Application user interface authentication loginPresenting this set of slides with name Application User Interface Authentication Login. This is a three stage process. The stages in this process are Application User Interface Authentication Login. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
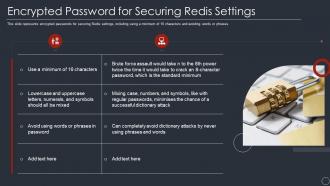 Encrypted password for securing redis settings ppt powerpoint presentation ideas show
Encrypted password for securing redis settings ppt powerpoint presentation ideas showThis slide represents encrypted passwords for securing Redis settings, including using a minimum of 16 characters and avoiding words or phrases. Increase audience engagement and knowledge by dispensing information using Encrypted Password For Securing Redis Settings Ppt Powerpoint Presentation Ideas Show. This template helps you present information on two stages. You can also present information on Encrypted Password For Securing Redis Settings using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managing critical threat vulnerabilities and security threats determine sequence phases
Managing critical threat vulnerabilities and security threats determine sequence phasesThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Managing Critical Threat Vulnerabilities And Security Threats Determine Sequence Phases to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Weaponization, Delivery, Exploitation, using this template. Grab it now to reap its full benefits.
-
 Data Security And Storage Environment Icon
Data Security And Storage Environment IconPresenting our set of slides with Data Security And Storage Environment Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Storage Environment Icon.
-
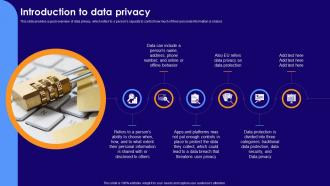 Introduction To Data Privacy Ppt Powerpoint Presentation Slides Background Designs
Introduction To Data Privacy Ppt Powerpoint Presentation Slides Background DesignsThis slide provides a quick overview of data privacy, which refers to a persons capacity to control how much of their personal information is shared. Increase audience engagement and knowledge by dispensing information using Introduction To Data Privacy Ppt Powerpoint Presentation Slides Background Designs. This template helps you present information on six stages. You can also present information on Personal Information, Apps And Platforms, Data Privacy, Data Protection using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations.
-
 Lock icon on clipboard
Lock icon on clipboardPresenting this set of slides with name Lock Icon On Clipboard. This is a three stage process. The stages in this process are Lock Icon On Clipboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Traditional Vs Cloud Information Security Icon
Traditional Vs Cloud Information Security IconPresenting our set of slides with name Traditional Vs Cloud Information Security Icon. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Traditional, Cloud Information Security, Icon.
-
 93737649 style technology 2 security 4 piece powerpoint presentation diagram infographic slide
93737649 style technology 2 security 4 piece powerpoint presentation diagram infographic slidePresenting this set of slides with name - Onboarding Best Practices Ppt Powerpoint Presentation Gallery Example Cpb. This is an editable four stages graphic that deals with topics like Onboarding Best Practices to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Privacy key to unlock image
Privacy key to unlock imagePresenting this set of slides with name Privacy Key To Unlock Image. This is a two stage process. The stages in this process are Privacy, Data Lock, Keyboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security icon for establishing employee belief in governance system
Security icon for establishing employee belief in governance systemPresenting this set of slides with name Security Icon For Establishing Employee Belief In Governance System. This is a two stage process. The stages in this process are Security Icon For Establishing Employee Belief In Governance System. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Warehouse icon with security camera for 24 hours surveillance
Warehouse icon with security camera for 24 hours surveillanceIntroducing our premium set of slides with Warehouse Icon With Security Camera For 24 Hours Surveillance. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Warehouse Icon With Security Camera For 24 Hours Surveillance. So download instantly and tailor it with your information.
-
 Data security it implementation of strong password policy
Data security it implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Data Security IT Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Special Characters, Employees, Protected Accounts, using this template. Grab it now to reap its full benefits.
-
 Data Governance Strategic Data Protection Icon
Data Governance Strategic Data Protection IconIntroducing our premium set of slides with Data Governance Strategic Data Protection Icon. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Governance, Strategic, Data Protection, Icon. So download instantly and tailor it with your information.
-
 5489434 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
5489434 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting security of internet of things powerpoint slide deck. This is a security of internet of things powerpoint slide deck. This is a one stage process. The stages in this process are device connectivity and management, analytics and operationalized insights, presentation and business connectivity, cloud based iot solutions, easy to provision, use and manage, end to end security and privacy, global reach.
-
 18746548 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
18746548 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting this set of slides with name - Login Page Icon With Lock And Password Field. This is a one stage process. The stages in this process are Login Page, Sign In Page, Register Page.
-
 53308855 style technology 2 security 3 piece powerpoint presentation diagram infographic slide
53308855 style technology 2 security 3 piece powerpoint presentation diagram infographic slidePresenting this set of slides with name - Authentication Icon Displaying Secured Connection. This is a three stages process. The stages in this process are Password, Authentication Icon, Access Approval.
-
 Key criteria for selecting business intelligence solution
Key criteria for selecting business intelligence solutionPresenting this set of slides with name Key Criteria For Selecting Business Intelligence Solution. This is a four stage process. The stages in this process are Technology, Infrastructure, Service. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Icon showing database server security from cyber threat
Icon showing database server security from cyber threatPresenting this set of slides with name Icon Showing Database Server Security From Cyber Threat. This is a three stage process. The stages in this process are Icon Showing Database Server Security From Cyber Threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Automation Icon To Improve Cyber Security
Automation Icon To Improve Cyber SecurityPresenting our set of slides with name Automation Icon To Improve Cyber Security. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Automation Icon, Improve Cyber Security.
-
 Security Automation System Icon With Gear
Security Automation System Icon With GearIntroducing our premium set of slides with Security Automation System Icon With Gear. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Automation System Icon, Gear. So download instantly and tailor it with your information.
-
 93841209 style technology 2 security 2 piece powerpoint presentation diagram infographic slide
93841209 style technology 2 security 2 piece powerpoint presentation diagram infographic slidePresenting Lock Password Icons slide. The slide is easy to download and can be transformed into a number of images or document formats such as JPEG, PNG or PDF. It is compatible with Google Slides and fully editable in PowerPoint. The slideshow supports both the standard(4:3) and widescreen(16:9) sizes. You can modify the style, size, color, background, and other attributes according to your needs. Moreover, high-quality images ensure that pixelation does not occur.
-
 30830893 style technology 2 security 2 piece powerpoint presentation diagram infographic slide
30830893 style technology 2 security 2 piece powerpoint presentation diagram infographic slidePresenting durability lock icon with round directed arrow. This is a durability lock icon with round directed arrow. This is a two stage process. The stages in this process are durability, durable, design lifetime, goods quality.
-
 6186124 style technology 2 security 4 piece powerpoint presentation diagram infographic slide
6186124 style technology 2 security 4 piece powerpoint presentation diagram infographic slidePresenting Key Icon in Circle Template. The template is available in both standard and widescreen. It is compatible with Google Slides, which makes it accessible at once. It can be transformed into various formats like PDF, JPG, and PNG. You can modify the color, font, font type, and font size of the slide as per the requirements. All the elements of this slide are under your control. Get this ready to use the template in just one click.
-
 46260059 style technology 2 security 1 piece powerpoint presentation diagram template slide
46260059 style technology 2 security 1 piece powerpoint presentation diagram template slidePresenting Black And White Shield Icon slideshow. Alter the font style, font color, and other components with ease. Make as many changes as you want on the slide Transform this template into various document or image formats like PDF or JPEG. The slide is fully customizable in PowerPoint and other office suites. The slide is also compatible with Google Slides. High-quality graphics ensure that quality is always maintained.
-
 8451352 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
8451352 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting padlock inside lighting bulb idea protection hand drawn. This is a padlock inside lighting bulb idea protection hand drawn. This is a one stage process. The stages in this process are padlock, lock, locker.
-
 7124126 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
7124126 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting incentive policy chart icon powerpoint slide. This is a incentive policy chart icon powerpoint slide. This is a one stage process. The stages in this process are incentive policy chart, incentive structures, profit motive.
-
 Virtual private network vpn security icon with lock
Virtual private network vpn security icon with lockPresenting Virtual Private Network VPN Security Icon With Lock slide. You can edit the slide as per your requirements. This slide can be downloaded into formats like PDF, JPG, and PNG with ease. It is adaptable with Google Slides which makes it accessible at once. This slide is available in both the standard and widescreen aspect ratios. High-quality graphics ensures that there is no room for deterioration.
-
 Folder access through digital identity finger print scanning icon
Folder access through digital identity finger print scanning iconPresenting our set of slides with Folder Access Through Digital Identity Finger Print Scanning Icon. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Folder Access Through Digital Identity Finger Print Scanning Icon.
-
 Scanning and storing digital identity for face recognition icon
Scanning and storing digital identity for face recognition iconIntroducing our premium set of slides with Scanning And Storing Digital Identity For Face Recognition Icon. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Scanning And Storing Digital Identity For Face Recognition Icon. So download instantly and tailor it with your information.
-
 82223192 style technology 2 security 1 piece powerpoint presentation diagram infographic slide
82223192 style technology 2 security 1 piece powerpoint presentation diagram infographic slidePresenting “Point To Point Security Solutions Ppt Infographic Template” which is 100% editable. This PPT template is crafted professionally by SlideTeam designers. This PPT slide is easy to customize and enables you to personalize it as per your own criteria. The presentation slide is fully compatible with Google slides, multiple format and software options.Instructions can be easily followed in case of any help. It is easy to download in a very short span of time. The images, layouts, designs are of high quality and ensures quality in widescreen. Generally, students, IT professionals and financialists makes the use of this PowerPoint presentation.
-
 85811338 style technology 2 security 6 piece powerpoint presentation diagram infographic slide
85811338 style technology 2 security 6 piece powerpoint presentation diagram infographic slidePresenting this set of slides with name - Content Management Business Process Overview Customer Management Strategy Cpb. This is an editable six graphic that deals with topics like Content Management, Business Process Overview, Customer Management Strategy to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Technological Strategies In Powerpoint And Google Slides Cpb
Technological Strategies In Powerpoint And Google Slides CpbPresenting Technological Strategies In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Technological Strategies. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
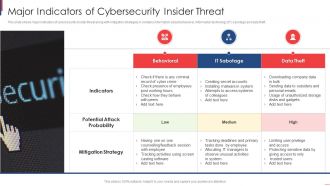 Major Indicators Of Cybersecurity Insider Threat
Major Indicators Of Cybersecurity Insider ThreatThis slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Introducing our premium set of slides with Major Indicators Of Cybersecurity Insider Threat. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Indicators, Potential Attack Probability, Mitigation Strategy. So download instantly and tailor it with your information.





