Powerpoint Templates and Google slides for Protection From Cyber Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Protecting Your Organizations From Cyber Risks Training Ppt
Protecting Your Organizations From Cyber Risks Training PptPresenting Protecting Your Organizations from Cyber Risks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
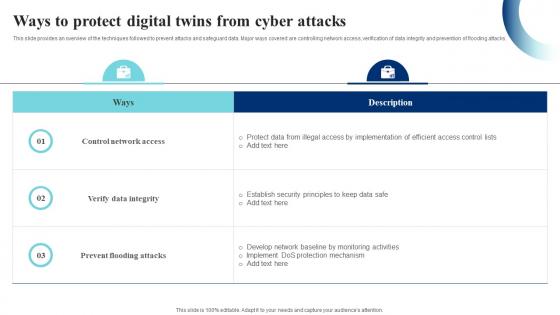 Ways To Protect Digital Twins From Cyber Attacks IoT Digital Twin Technology IOT SS
Ways To Protect Digital Twins From Cyber Attacks IoT Digital Twin Technology IOT SSThis slide provides an overview of the techniques followed to prevent attacks and safeguard data. Major ways covered are controlling network access, verification of data integrity and prevention of flooding attacks. Present the topic in a bit more detail with this Ways To Protect Digital Twins From Cyber Attacks IoT Digital Twin Technology IOT SS. Use it as a tool for discussion and navigation on Control Network Access, Prevent Flooding Attacks, Verify Data Integrity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Key Approaches To Protect From Honeypot Scams BCT SS V
Cyber Threats In Blockchain Key Approaches To Protect From Honeypot Scams BCT SS VThe following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. Introducing Cyber Threats In Blockchain Key Approaches To Protect From Honeypot Scams BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on No Dead Coins, Check Social Media, Scrutinize Website using this template. Grab it now to reap its full benefits.
-
 How To Protect Company From Trojan Attacks Cyber Terrorism Attacks
How To Protect Company From Trojan Attacks Cyber Terrorism AttacksThis slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. Increase audience engagement and knowledge by dispensing information using How To Protect Company From Trojan Attacks Cyber Terrorism Attacks. This template helps you present information on five stages. You can also present information on Antivirus Programm, Application Firewall, Reliable Sources, Avoid Third Party Downloads using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
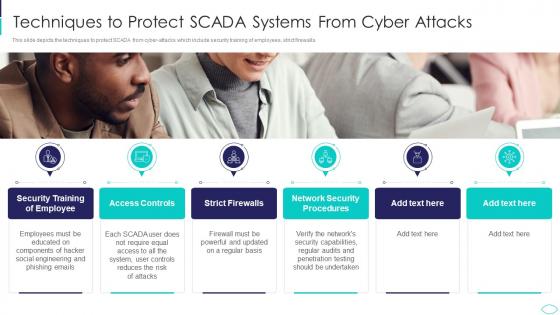 Techniques To Protect SCADA Systems From Cyber Terrorism Attacks
Techniques To Protect SCADA Systems From Cyber Terrorism AttacksThis slide depicts the techniques to protect SCADA from cyber attacks which include security training of employees, strict firewalls. Increase audience engagement and knowledge by dispensing information using Techniques To Protect SCADA Systems From Cyber Terrorism Attacks. This template helps you present information on six stages. You can also present information on Security Training, Access Controls, Strict Firewalls, Security Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
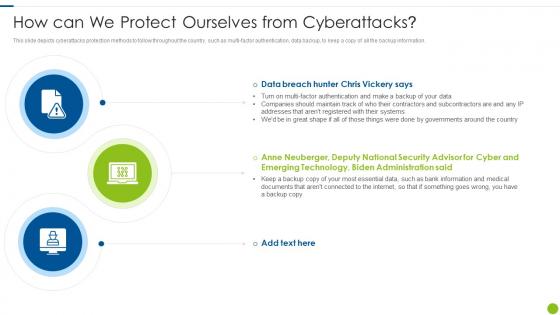 Cyber Attacks On Ukraine How Can We Protect Ourselves From Cyberattacks
Cyber Attacks On Ukraine How Can We Protect Ourselves From CyberattacksThis slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. Introducing Cyber Attacks On Ukraine How Can We Protect Ourselves From Cyberattacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on How Can We Protect Ourselves From Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks On Ukraine How To Protect Yourself From Ongoing Cybersecurity
Cyber Attacks On Ukraine How To Protect Yourself From Ongoing CybersecurityThis slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Increase audience engagement and knowledge by dispensing information using Cyber Attacks On Ukraine How To Protect Yourself From Ongoing Cybersecurity. This template helps you present information on six stages. You can also present information on Suspicious, Individuals, Adequately, Programmed using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
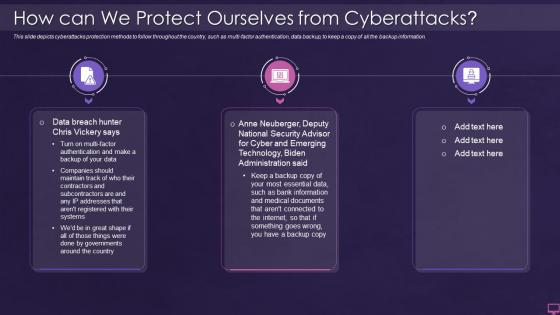 How can we protect ourselves from cyberattacks ukraine and russia cyber warfare it
How can we protect ourselves from cyberattacks ukraine and russia cyber warfare itThis slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. Increase audience engagement and knowledge by dispensing information using How Can We Protect Ourselves From Cyberattacks Ukraine And Russia Cyber Warfare It. This template helps you present information on three stages. You can also present information on How CAN We Protect Ourselves FROM Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
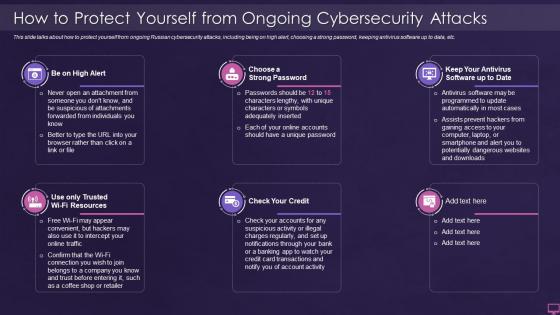 Ukraine and russia cyber warfare it how to protect yourself from ongoing cybersecurity attacks
Ukraine and russia cyber warfare it how to protect yourself from ongoing cybersecurity attacksThis slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Introducing Ukraine And Russia Cyber Warfare It How To Protect Yourself From Ongoing Cybersecurity Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Resources, Antivirus, Software, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it techniques to protect scada systems from cyber attacks
Cyberterrorism it techniques to protect scada systems from cyber attacksThis slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Techniques To Protect SCADA Systems From Cyber Attacks. Dispense information and present a thorough explanation of Security Training, Employee, Access Controls, Strict Firewalls, Network Security Procedures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
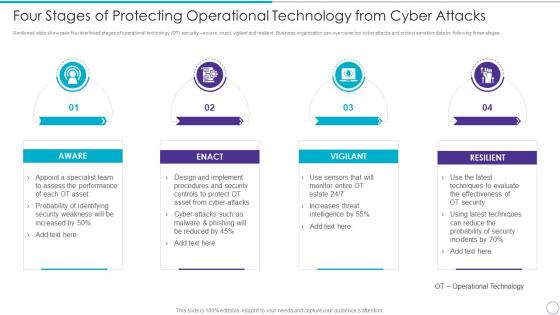 Four Stages Of Protecting Operational Technology From Cyber Attacks
Four Stages Of Protecting Operational Technology From Cyber AttacksMentioned slide showcase four interlinked stages of operational technology OT security aware, enact, vigilant and resilient. Business organization can overcome top cyber attacks and protect sensitive data by following these stages. Increase audience engagement and knowledge by dispensing information using four Stages Of Protecting Operational Technology From Cyber Attacks. This template helps you present information on four stages. You can also present information on Aware, Enact, Vigilant, Resilient using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist To Ensure Asset Protection From Internal Upgrading Cybersecurity With Incident Response Playbook
Checklist To Ensure Asset Protection From Internal Upgrading Cybersecurity With Incident Response PlaybookFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present the topic in a bit more detail with this Checklist To Ensure Asset Protection From Internal Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Protection, Measures, Ensure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And Vulnerability
Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And VulnerabilityFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Introducing Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Email, Mobile Devices, using this template. Grab it now to reap its full benefits.
-
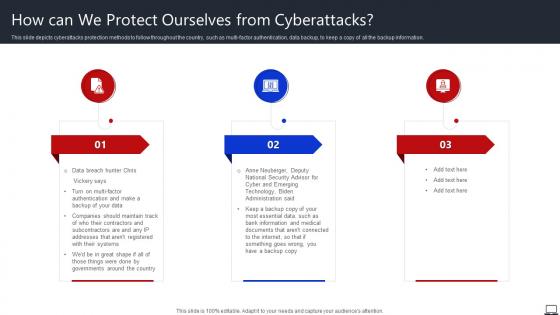 How Can We Protect Ourselves From Cyberattacks String Of Cyber Attacks Against
How Can We Protect Ourselves From Cyberattacks String Of Cyber Attacks AgainstThis slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. Increase audience engagement and knowledge by dispensing information using How Can We Protect Ourselves From Cyberattacks String Of Cyber Attacks Against. This template helps you present information on three stages. You can also present information on Governments, Backup Copy, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
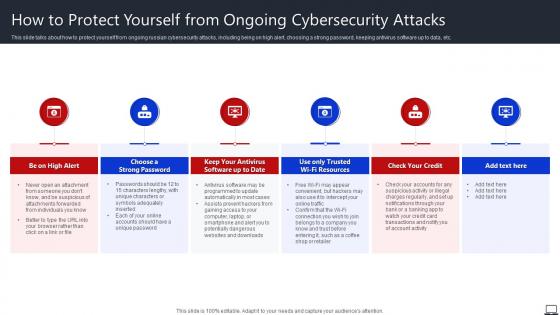 How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber Attacks
How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber AttacksThis slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Introducing How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Choose A Strong Password, Check Your Credit, Unique Password, using this template. Grab it now to reap its full benefits.
-
 Protection from cyber attacks ppt slide examples
Protection from cyber attacks ppt slide examplesPresenting protection from cyber attacks ppt slides examples PPT slide. The tension-free download is possible. Once downloaded, the presentation can be modified to any format like JPG, JPEG, PDF, etc. It’s also compatible with multiple software and Google Slides. The provided executive summary PPT presentation template can easily be used solely or as part of your pre-built presentation. Be happy to customize and personalize the presentation with company specifications.There is no hassle when any facts, figures or text is to be included or excluded in the presentation. Picture quality compatible with widescreen exposure.
-
 Icon of laptop protected with security software from cyber threat
Icon of laptop protected with security software from cyber threatPresenting this set of slides with name Icon Of Laptop Protected With Security Software From Cyber Threat. This is a three stage process. The stages in this process are Icon Of Laptop Protected With Security Software From Cyber Threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

