Types of social engineering attack with pretexting
Allow for a few distractions to crop up with our Types Of Social Engineering Attack With Pretexting. Be able to cater for irritants.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting this set of slides with name Types Of Social Engineering Attack With Pretexting. This is a six process. The stages in this process are stages Social Engineering, Technology, Social, Network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Description:
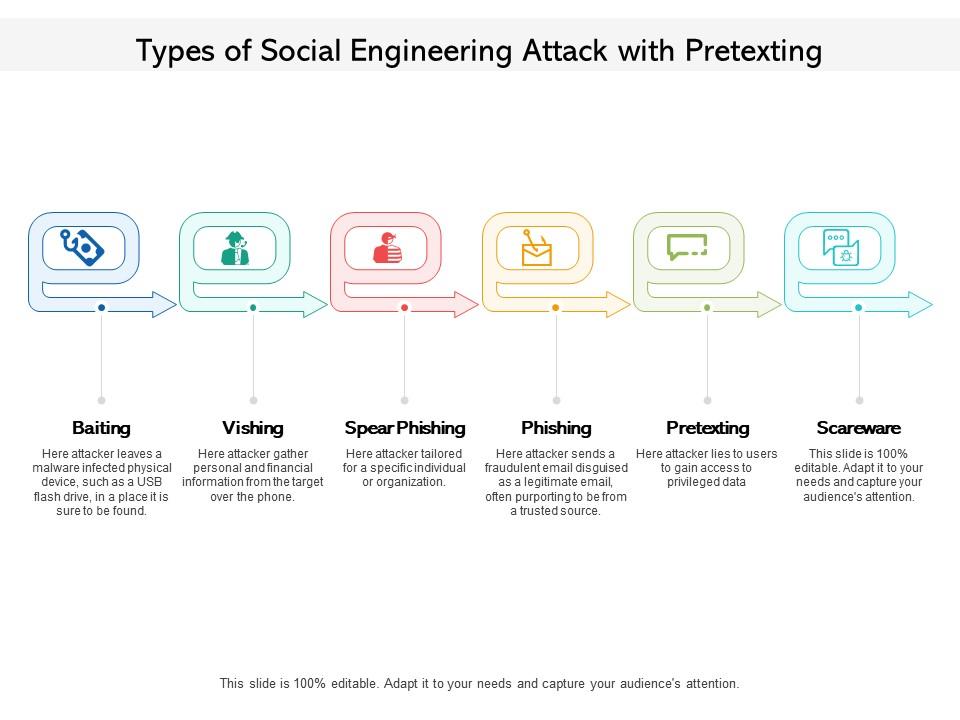
The image shows a PowerPoint slide titled "Types of Social Engineering Attack with Pretexting." It outlines various methods by which malicious actors manipulate individuals into divulging confidential information:
1. Baiting:
Similar to phishing, baiting involves offering something enticing to the victim, such as a malware-infected USB drive left in a place where it is sure to be found.
2. Vishing:
A method where attackers gather personal and financial information from the target over the phone by pretending to be a legitimate institution or authority.
3. Spear Phishing:
Unlike phishing, which targets large groups, spear phishing is tailored for specific individuals or organizations to trick them into revealing sensitive information or installing malware.
4. Phishing:
This well-known attack sends a fraudulent email disguised as legitimate, often purporting to be from a trusted source, to steal personal data or login credentials.
5. Pretexting:
Here, an attacker lies to users, creating a fabricated scenario, or pretext, to gain access to privileged data.
6. Scareware:
This involves tricking the victim into thinking their system is infected with malware prompting them to install malicious software.
Use Cases:
This type of slide can be used across a variety of industries for educational and awareness purposes:
1. Financial Services:
Use: Educating customers on safe online banking practices.
Presenter: Cybersecurity Expert
Audience: Bank customers, employees
2. Healthcare:
Use: Training staff to protect patient data.
Presenter: Information Security Officer
Audience: Healthcare professionals, administrative staff
3. Education:
Use: Teaching about cybersecurity and information integrity.
Presenter: IT Instructor
Audience: Students, faculty
4. Retail:
Use: Instructing employees on safeguarding customer information.
Presenter: Compliance Manager
Audience: Retail employees, management
5. Technology:
Use: Discussing security threats in software development and IT services.
Presenter: Chief Information Security Officer
Audience: IT staff, developers
6. Government:
Use: Training for protecting against espionage and information leaks.
Presenter: Security Analyst
Audience: Government employees, contractors
7. Hospitality:
Use: Ensuring staff understand the importance of protecting guest information.
Presenter: Risk Management Leader
Audience: Hotel staff, customer service agents
Types of social engineering attack with pretexting with all 5 slides:
Handle irritants with our Types Of Social Engineering Attack With Pretexting. Counter the impact of any distractions.
No Reviews