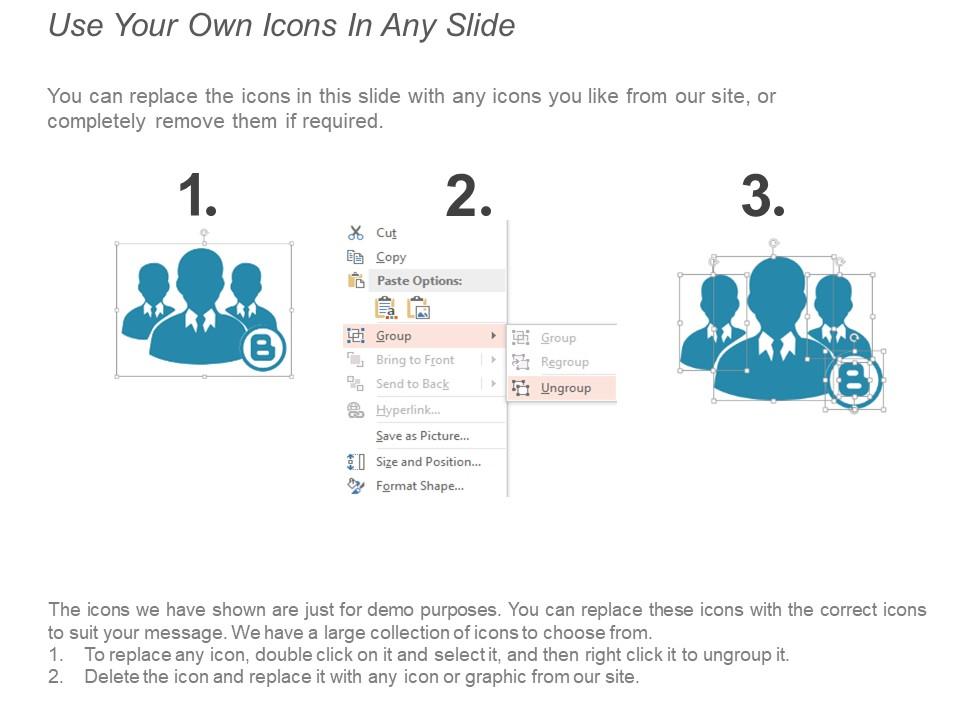
Five ways to prevent social engineering attacks
Handle irresponsible conduct with our Five Ways To Prevent Social Engineering Attacks. Elaborate on the importance of displaying commitment.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
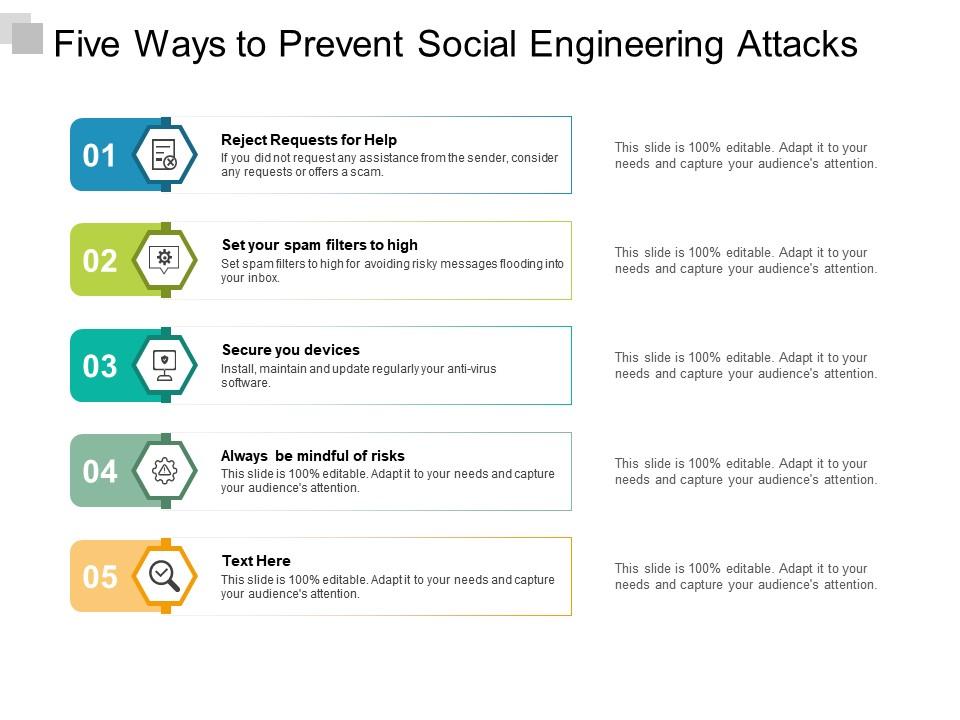
Presenting this set of slides with name Five Ways To Prevent Social Engineering Attacks. This is a five process. The stages in this process are stages Social Engineering, Technology, Social, Network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Description:
The image presents a slide titled "Five Ways to Prevent Social Engineering Attacks" and is designed to inform about best practices in cybersecurity. It contains five numbered items, each providing a distinct tip on how to counteract social engineering threats:
1. Reject Requests for Help -
The slide instructs viewers to disregard unsolicited assistance offers which might be scams, particularly if the aid wasn't sought. This is a critical first line of defense in cybersecurity.
2. Set your spam filters to high -
To prevent phishing or fraudulent emails from reaching your inbox, configuring high spam filters is recommended.
3. Secure your devices -
Regular installation, maintenance, and updating of antivirus software safeguards against malicious software infiltrations.
4. Always be mindful of risks -
This placeholder suggests maintaining a constant awareness of potential security threats, although the specific content is missing and the slide notes it is 100% editable.
5. Text Here -
The fifth point is left as a placeholder for the presenter to customize with additional content, which shows the slide is adaptable for different contexts.
Use Cases:
The slide can be applied across a range of industries that require awareness and practices to safeguard against social engineering. Here are seven such industries:
1. Financial Services:
Use: Cybersecurity training for staff and clients
Presenter: Cybersecurity experts or trainers
Audience: Employees and clients
2. Healthcare:
Use: Protecting patient information and hospital systems
Presenter: IT security teams
Audience: Medical and administrative staff
3. Government:
Use: Strengthening national and local cyber defense mechanisms
Presenter: Cybersecurity agency personnel
Audience: Government officials and IT staff
4. Education:
Use: Educating students and faculty on data security
Presenter: IT administrators or cybersecurity guest lecturers
Audience: Students, teachers, and administrative staff
5. Retail:
Use: Safeguarding customer data and preventing fraud
Presenter: Security consultants or internal IT teams
Audience: Customer service representatives and store managers
6. Technology:
Use: Internal security protocol training
Presenter: Chief Information Security Officer (CISO) or IT team
Audience: Developers, engineers, and all company staff
7. Telecommunications:
Use: Preventing fraudulent activities over networks
Presenter: Telecommunications security specialists
Audience: Network engineers and customer-facing staff
Five ways to prevent social engineering attacks with all 5 slides:
Elaborate on the importance of displaying commitment with our Five Ways To Prevent Social Engineering Attacks. Handle irresponsible conduct.
No Reviews