Improve it security with vulnerability management powerpoint presentation slides
Vulnerability management improves IT security and provides real-time analysis of security alerts generated by the applications and network hardware. Here is a competently designed Improve IT Security with Vulnerability Management template that will give various SIEM services to the customers and the costs of the services offered. A company overview has been provided, focusing on our company, mission, vision, etc. Challenges and solutions have been covered here, which will help the customers to understand the need for IT security identification strategies in their company. Automatings competitive advantage has been focused on our companys services, such as SIEM strategies, etc. SIEM architecture focuses on the logging process, flow, sources, etc. Hosting models are shared in this template, covering the traditional model, cloud IT security identification, hybrid managed, fully managed model and the key points to consider while choosing the suitable model. The next evolution of IT security identification is discussed for advancing SIEM technology. The costs of the IT security services offered by the company are shared in this deck. Get access now.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Improve IT Security With Vulnerability Management Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Improve IT Security with Vulnerability Management. State Your Company Name and begin.
Slide 2: This slide shows Agenda of Improve IT Security with Vulnerability Management.
Slide 3: This slide presents Table of Content for the presentation.
Slide 4: This slide depicts title for 'Company Overview'.
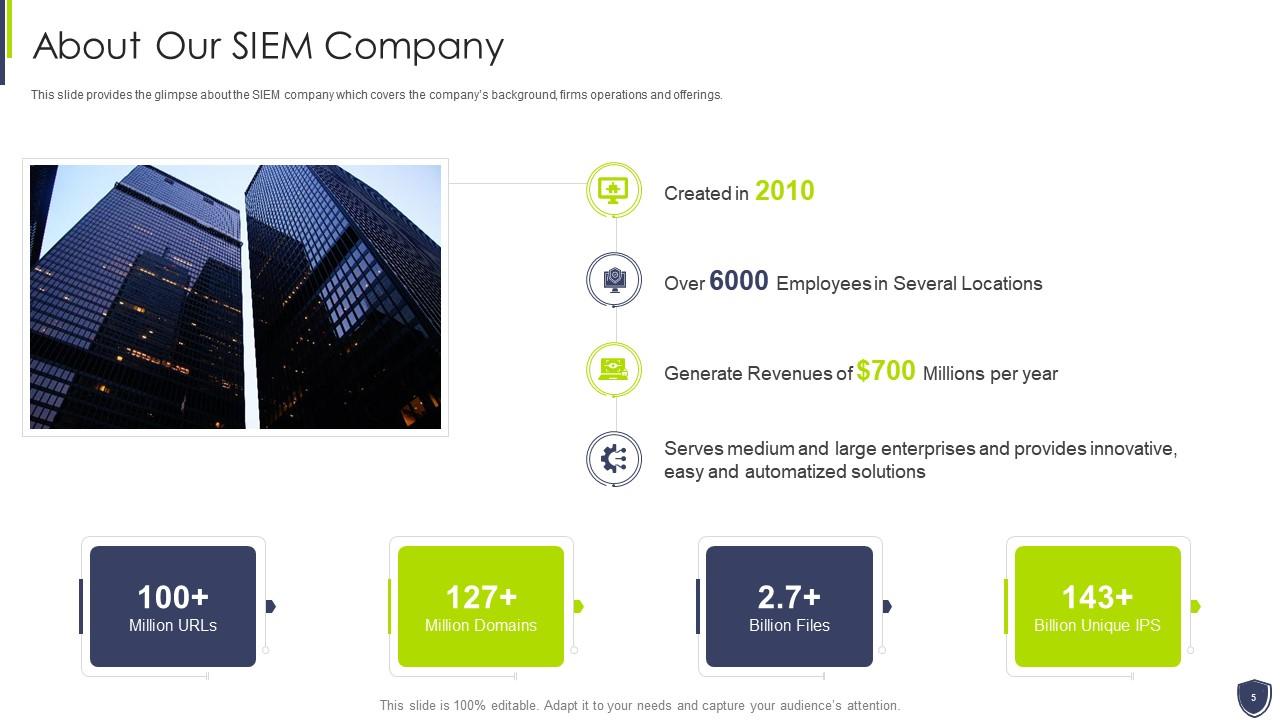
Slide 5: This slide provides the glimpse about the SIEM company which covers the company’s background, firms operations and offerings.
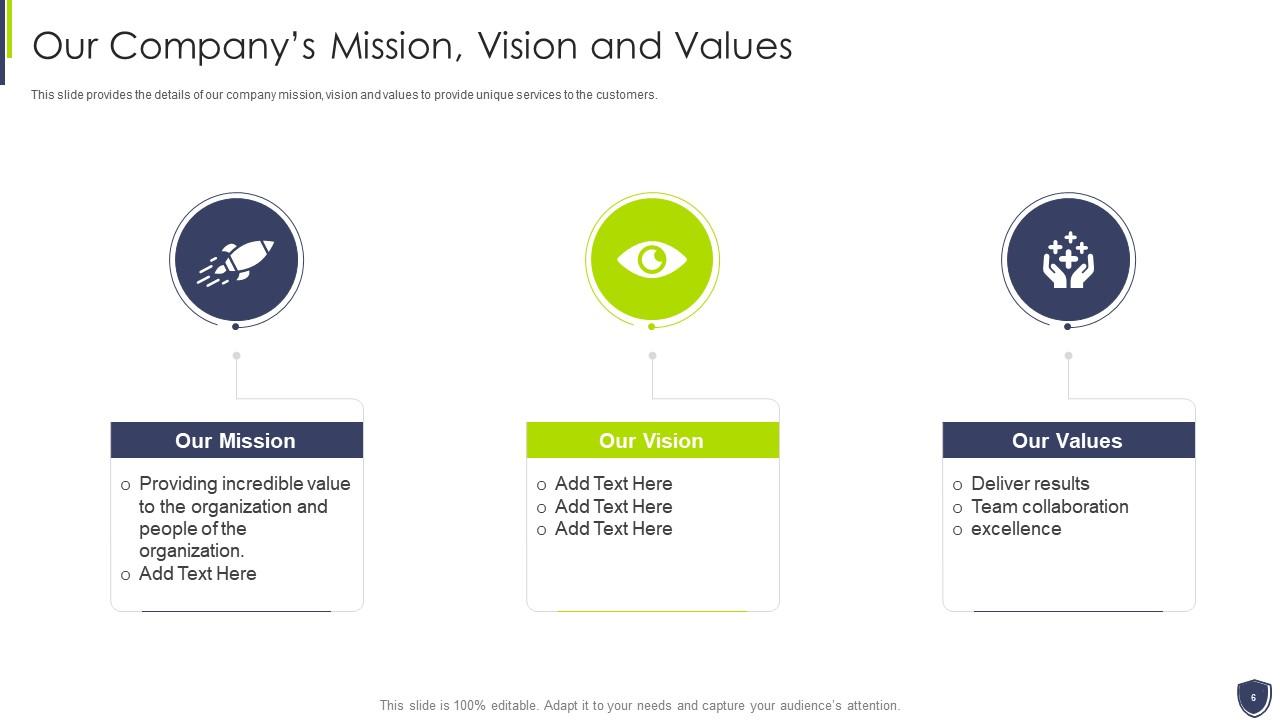
Slide 6: This slide provides the details of our company mission, vision and values to provide unique services to the customers.
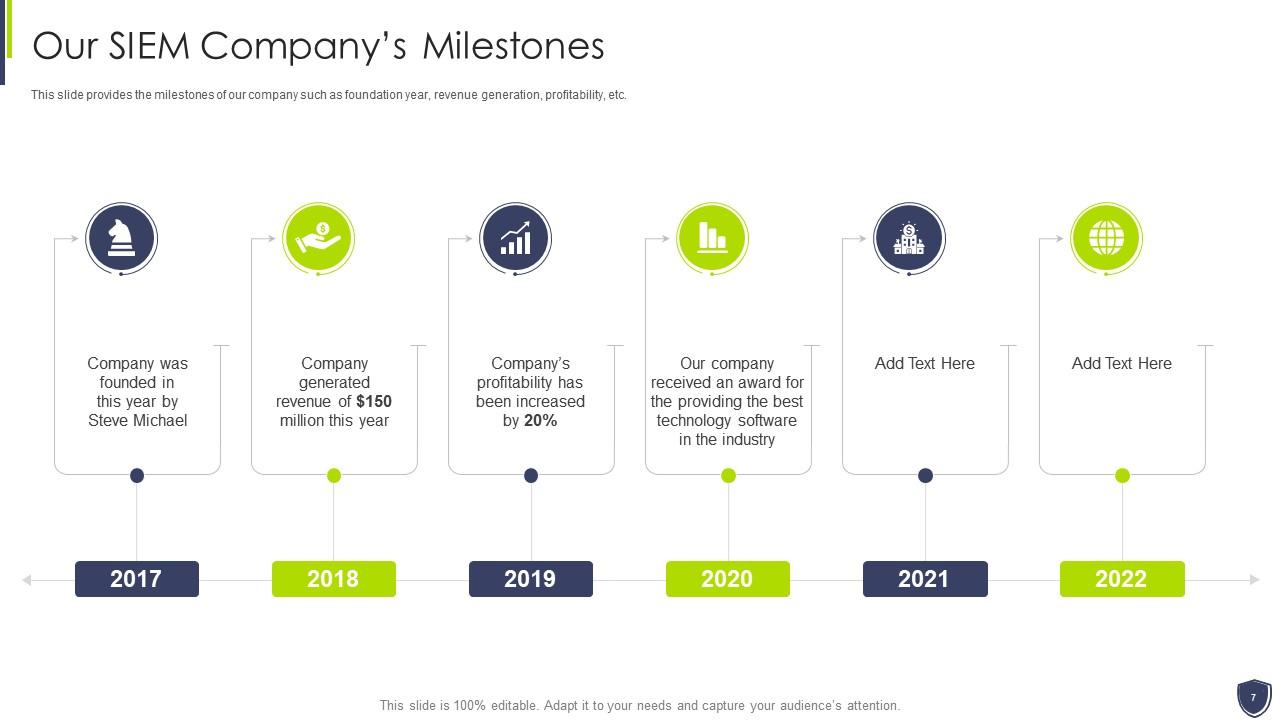
Slide 7: This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc.
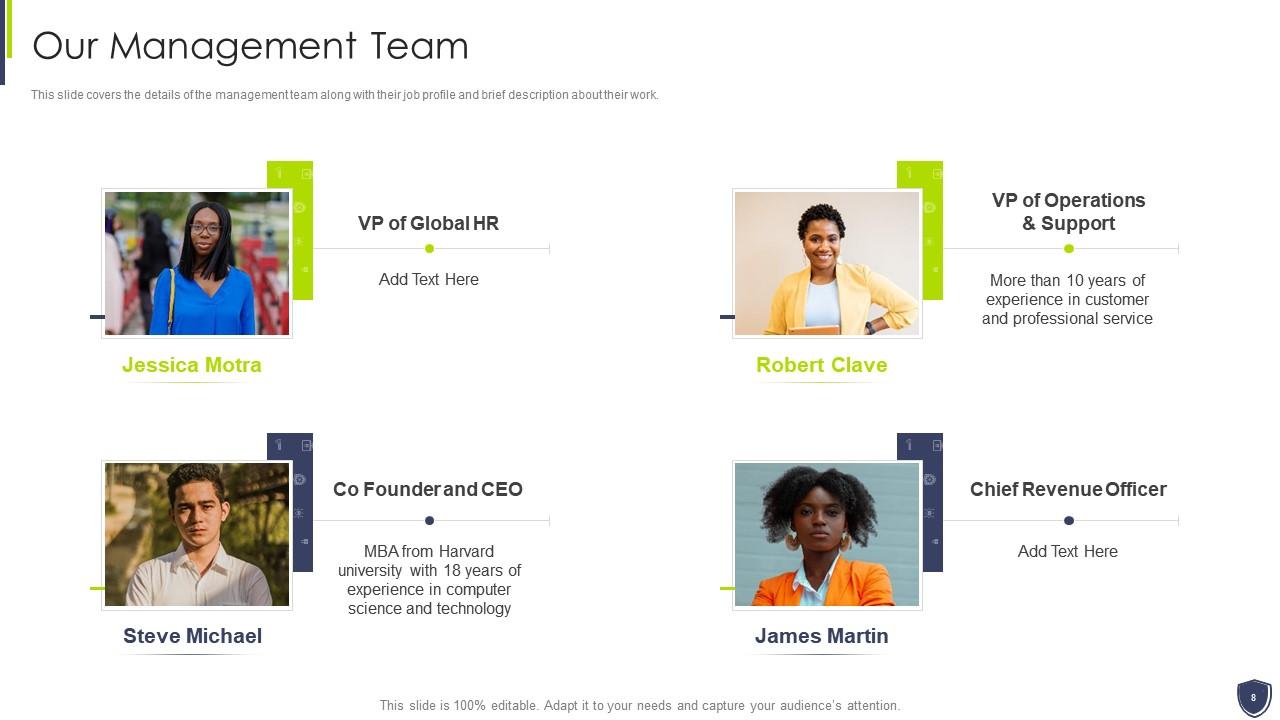
Slide 8: This slide covers the details of the management team along with their job profile and brief description about their work.
Slide 9: This slide shows title for 'Challenges and Solutions'.
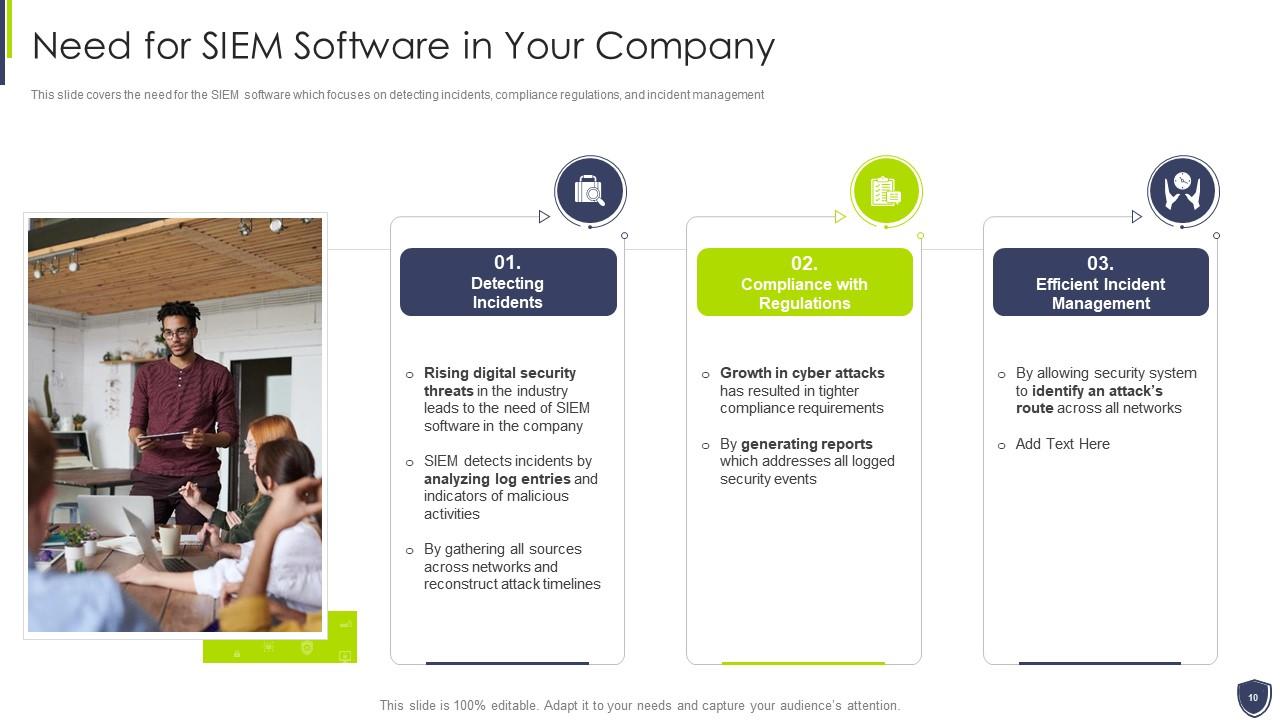
Slide 10: This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, etc.
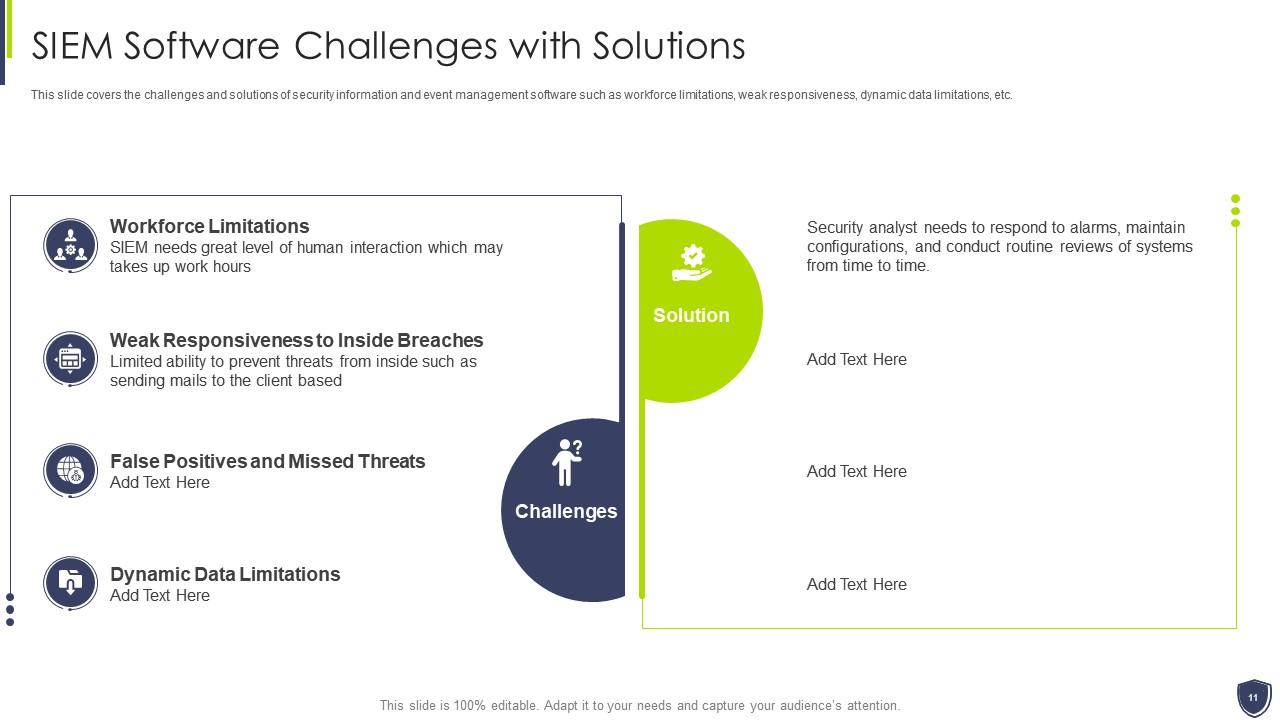
Slide 11: This slide covers the challenges and solutions of security information and event management software.
Slide 12: This slide displays title for 'SIEM Competitive Advantage'.
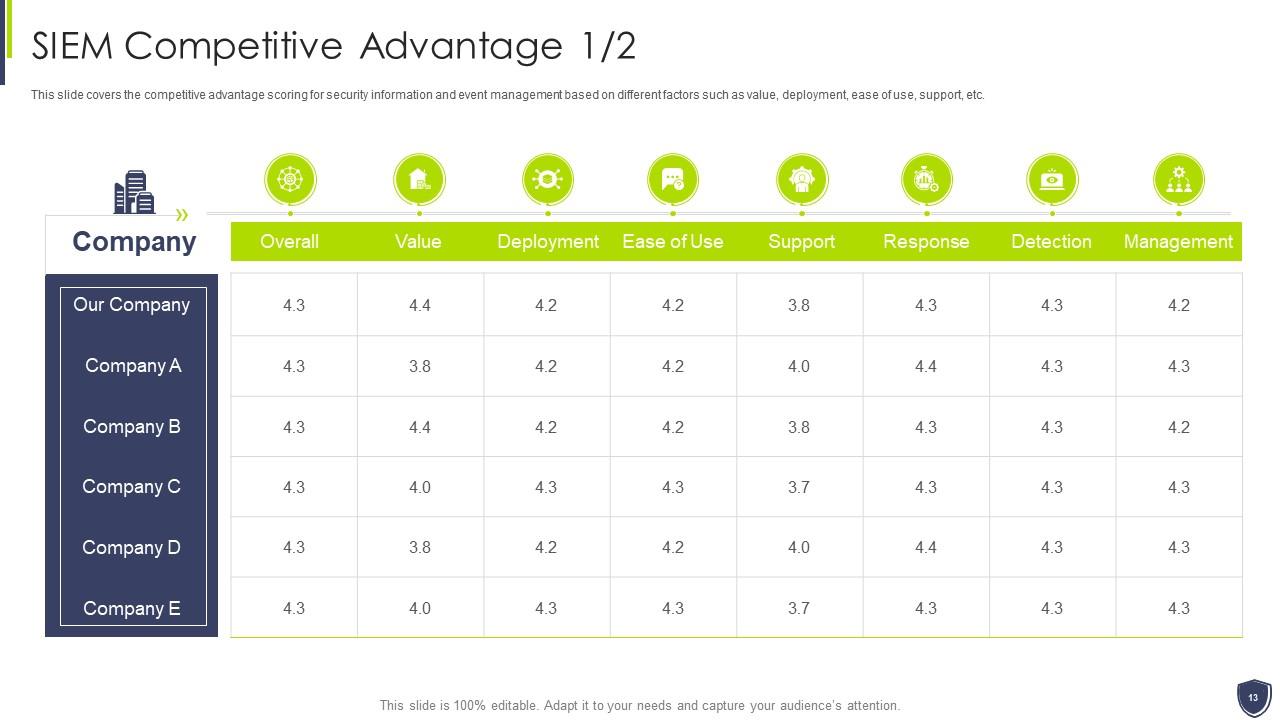
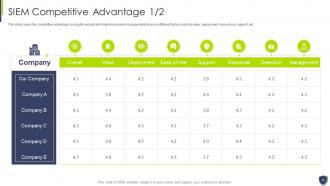
Slide 13: This slide covers the competitive advantage scoring for security information and event management.
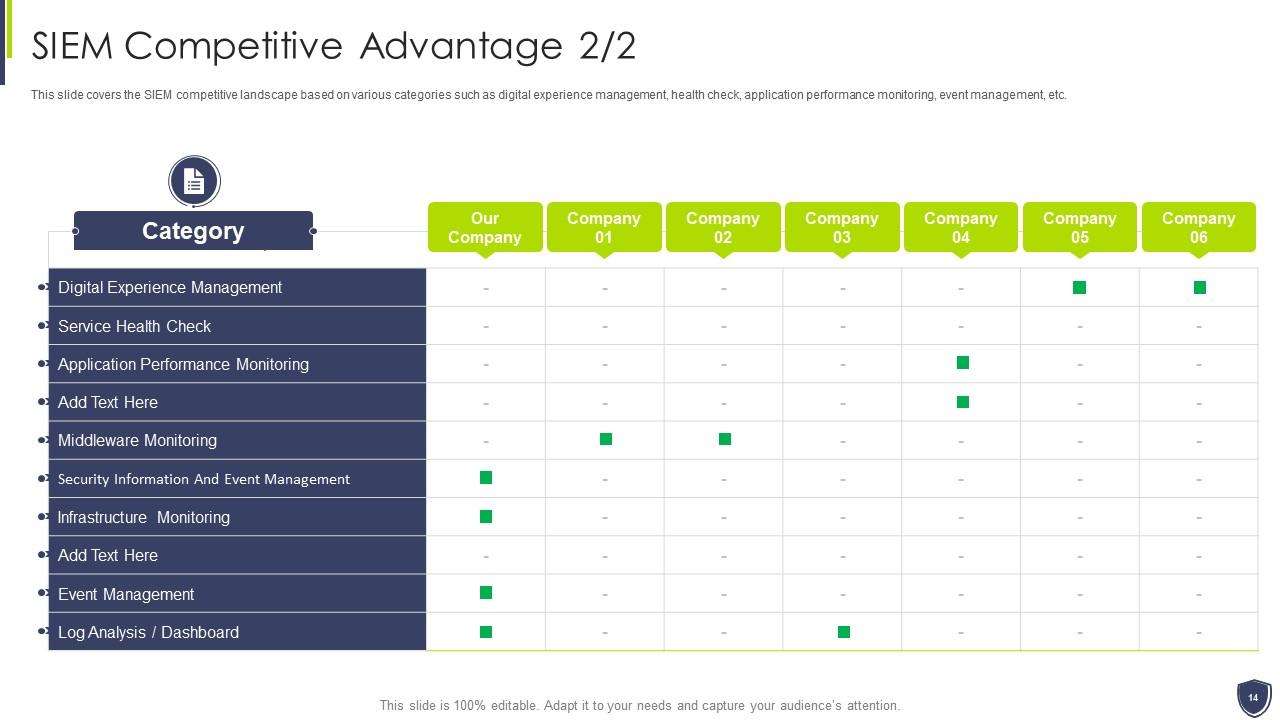
Slide 14: This slide covers the SIEM competitive landscape based on various categories such as digital experience management, etc.
Slide 15: This slide presents title for 'Services offered'.
Slide 16: This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, etc.
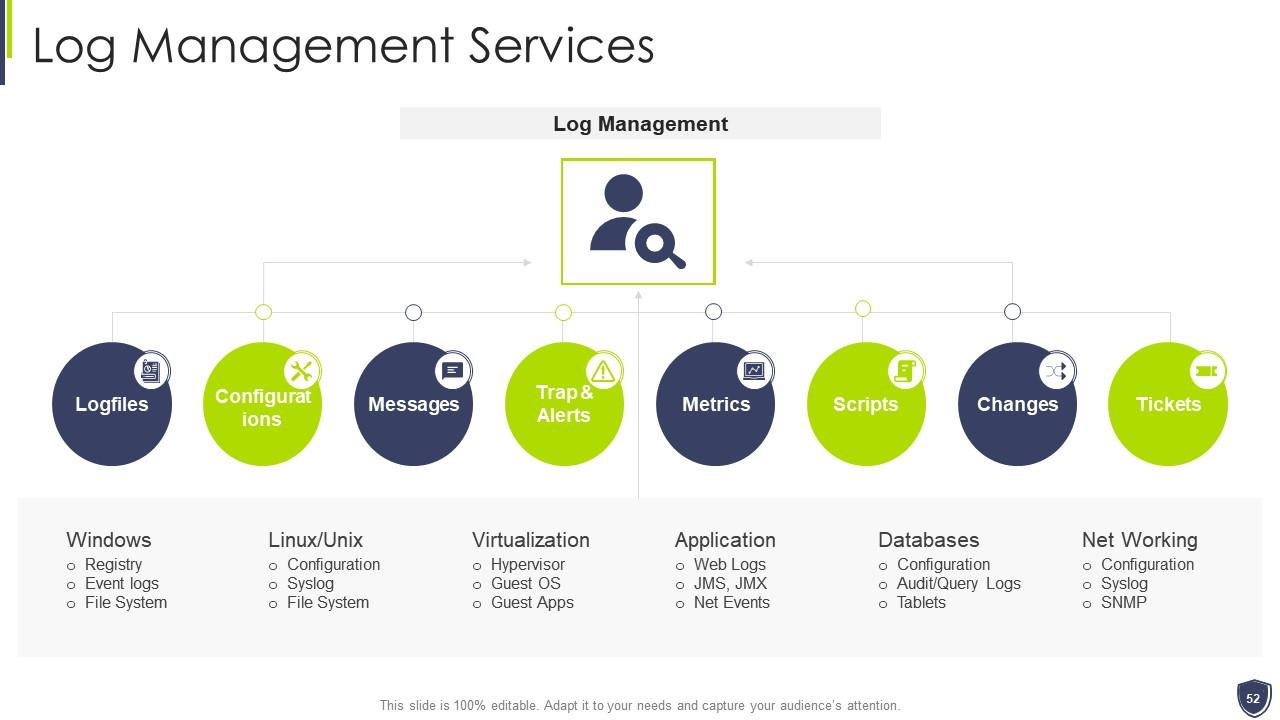
Slide 17: This slide covers the log management services offered by our company such as collection & normalization, search speed, etc.
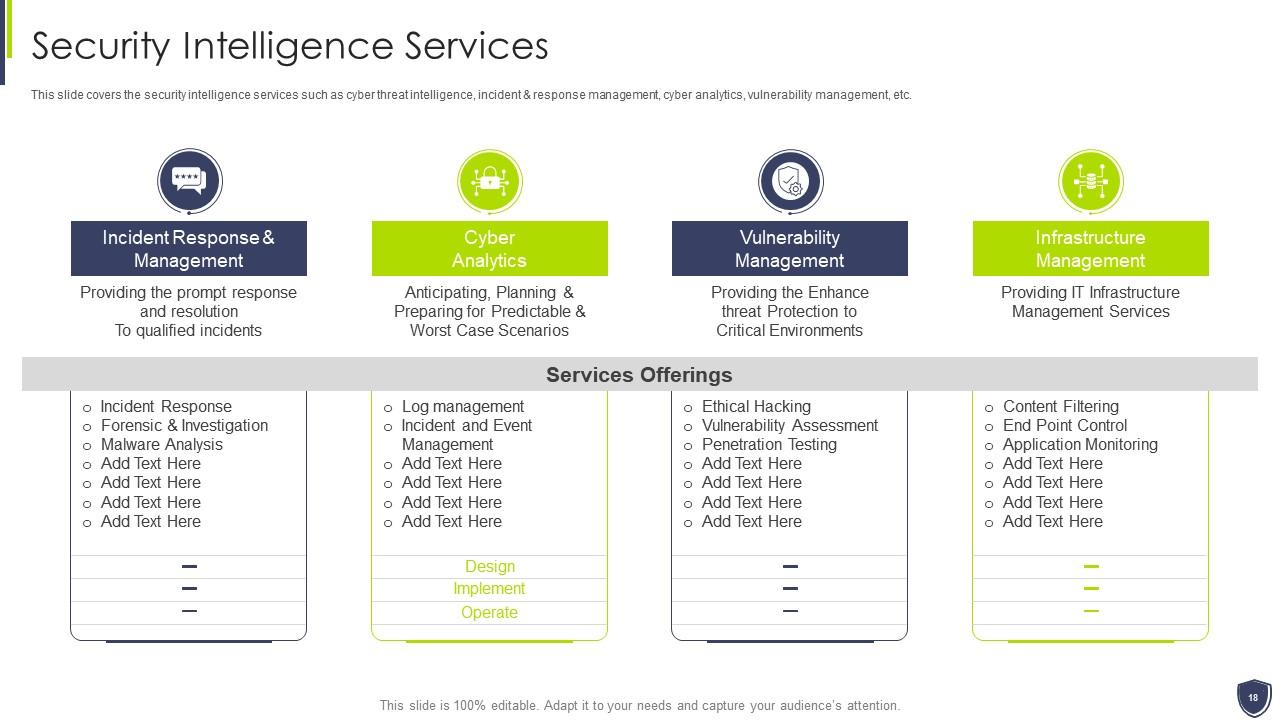
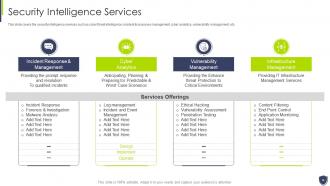
Slide 18: This slide covers the security intelligence services such as cyber threat intelligence, incident & response management, etc.
Slide 19: This slide covers the threat intelligence services such as global intelligence, local intelligence, etc.
Slide 20: This slide exhibits title for 'Features and Benefits'.
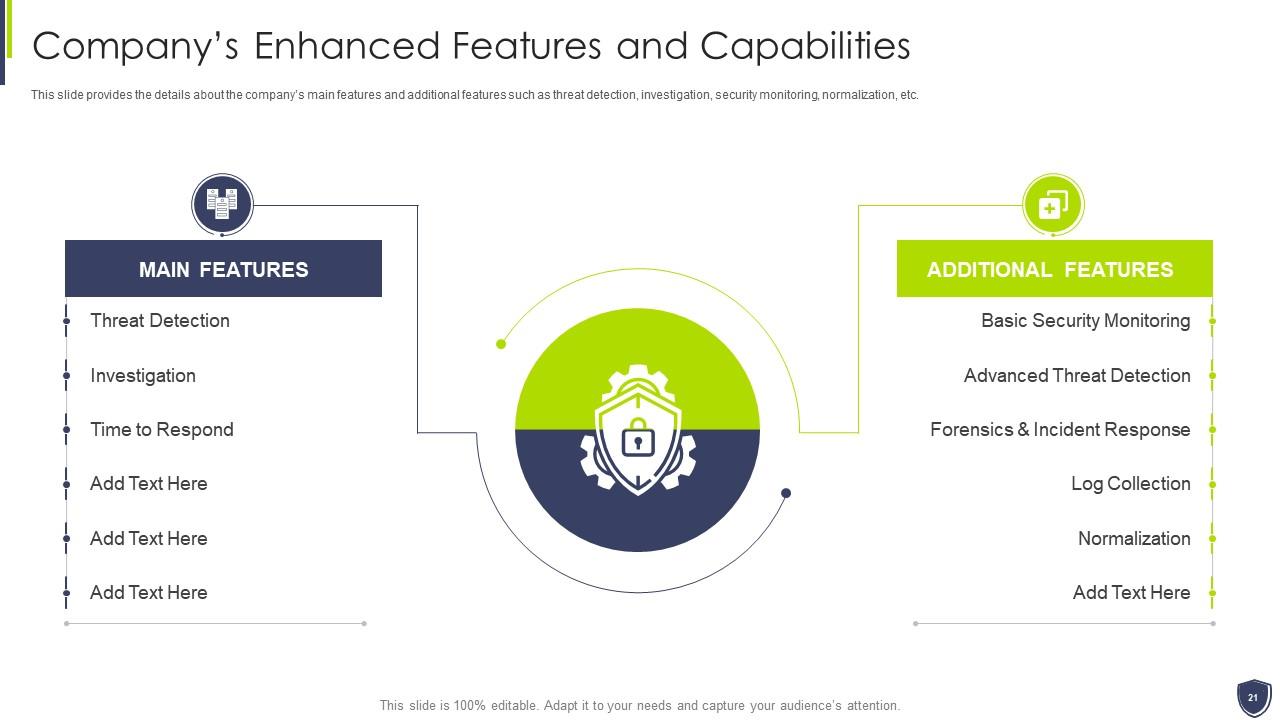
Slide 21: This slide provides the details about the company’s main features and additional features.
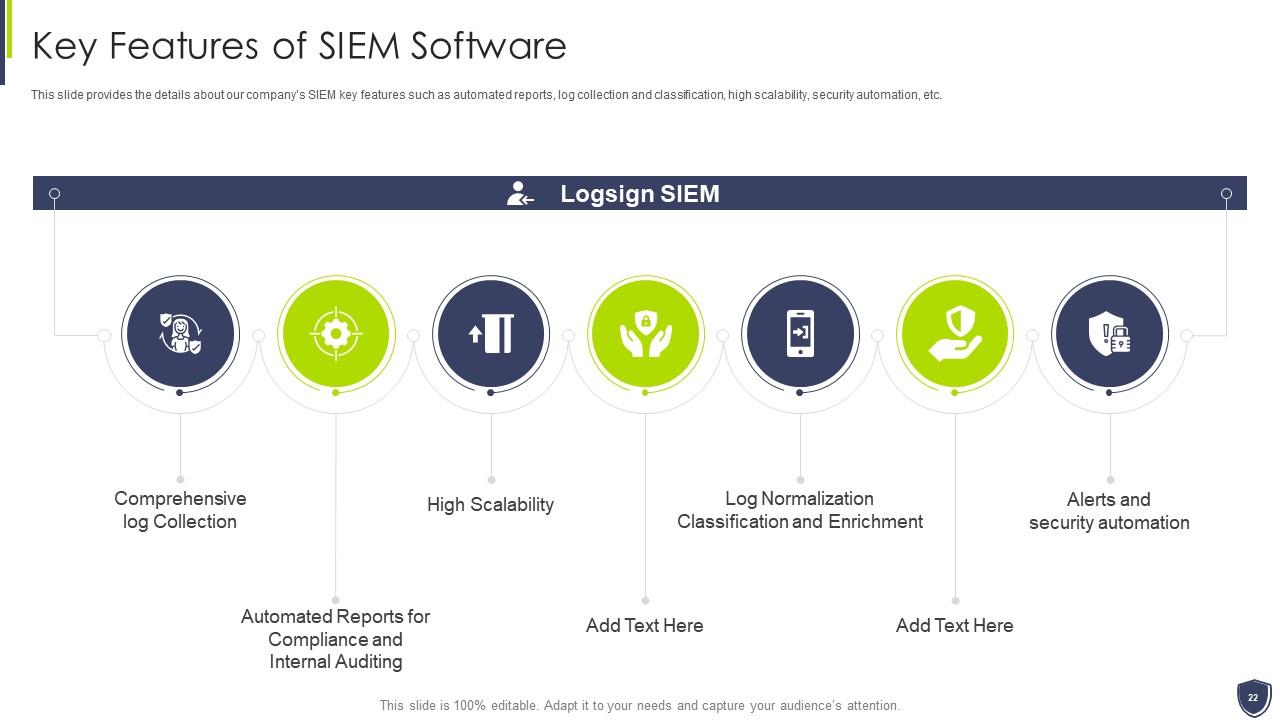
Slide 22: This slide provides the details about our company’s SIEM key features such as automated reports, log collection, etc.
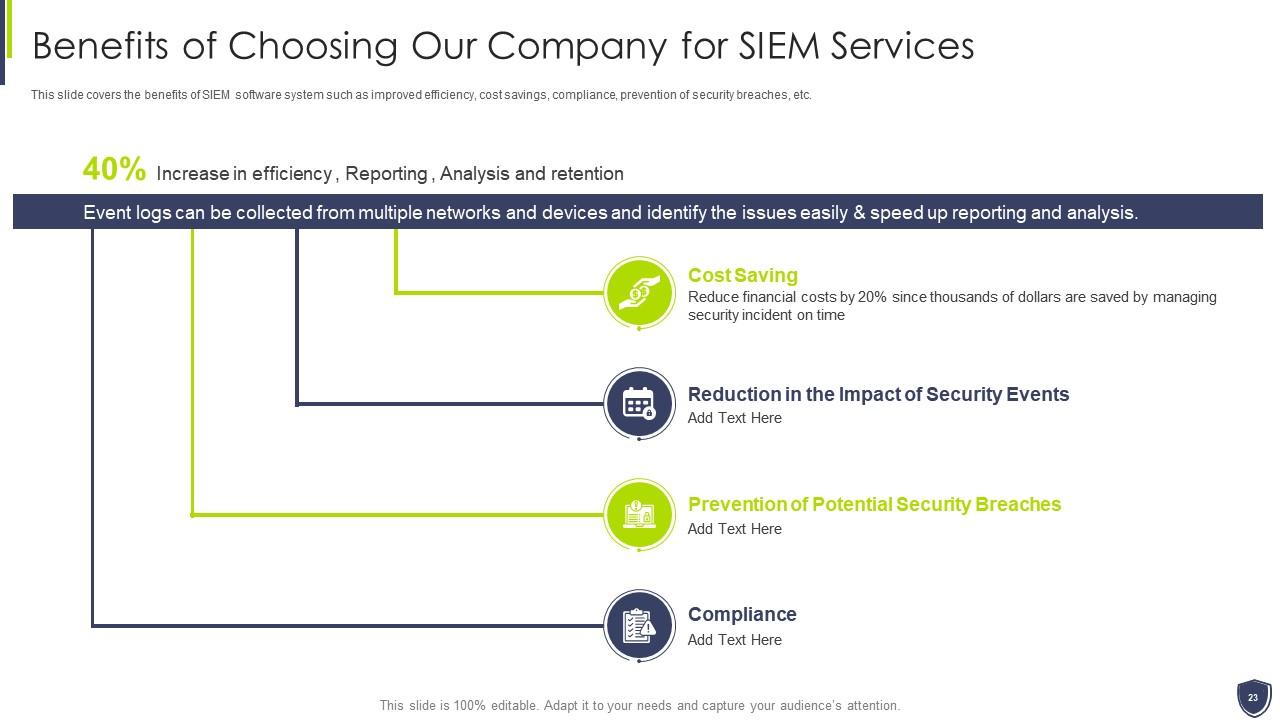
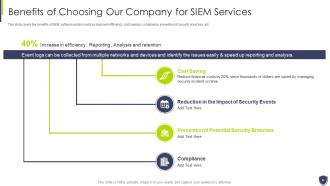
Slide 23: This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, etc.
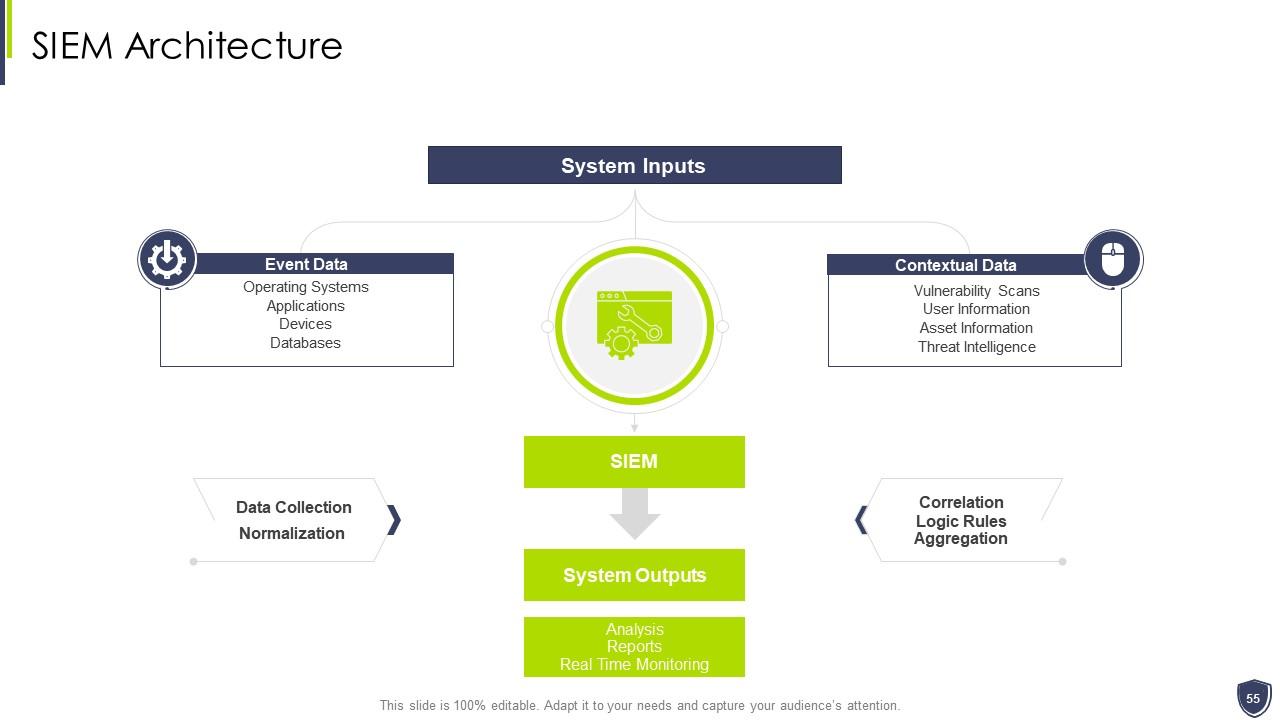
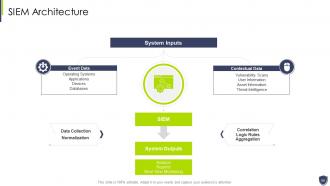
Slide 24: This slide shows title for 'SIEM Architecture'.
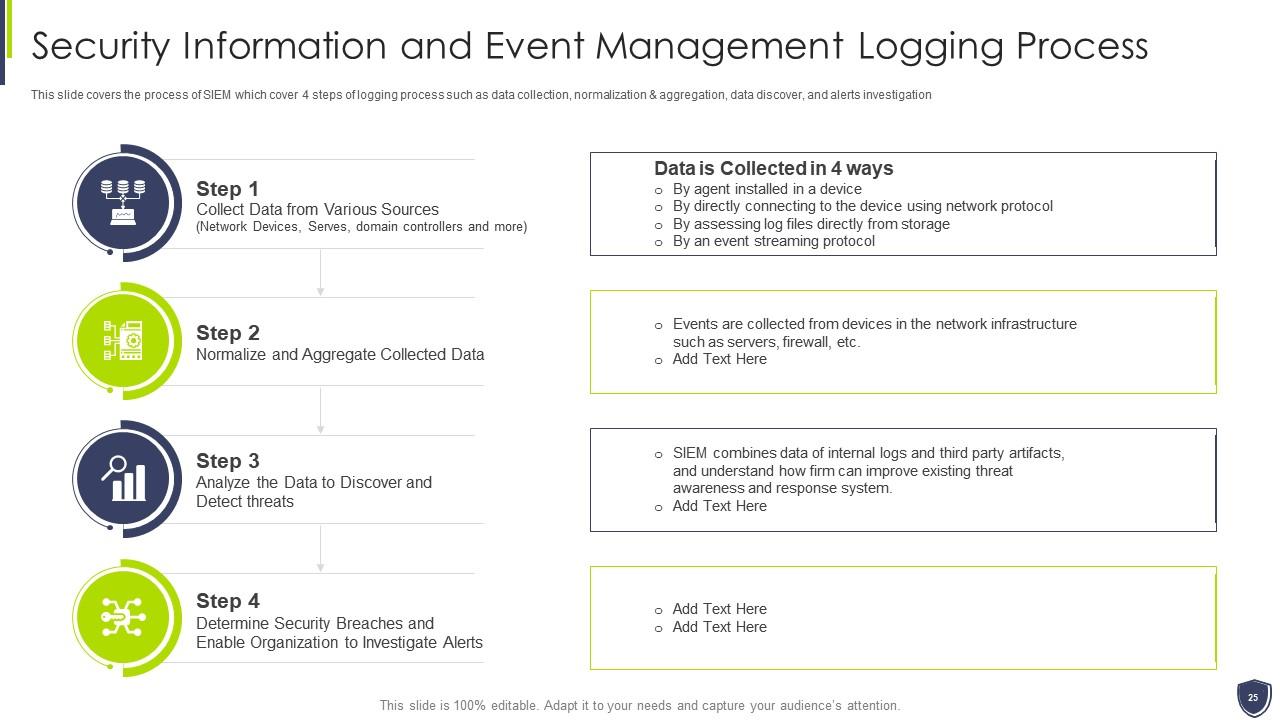
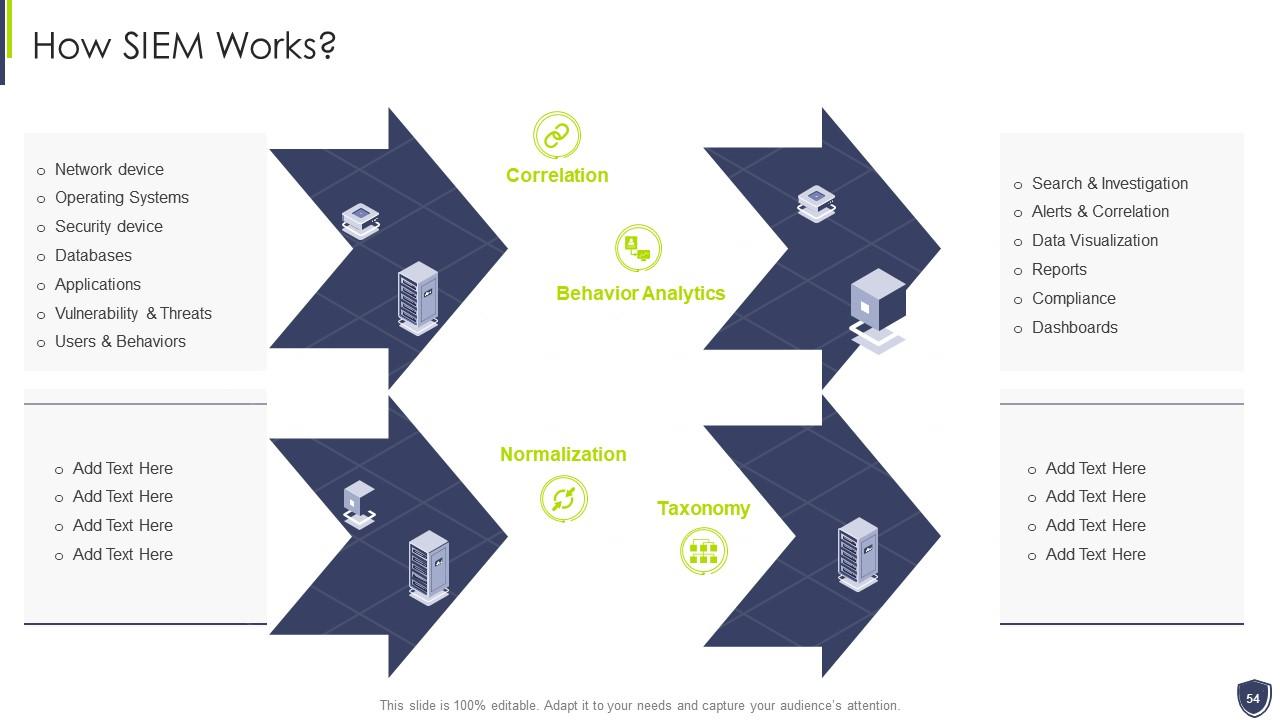
Slide 25: This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, etc.
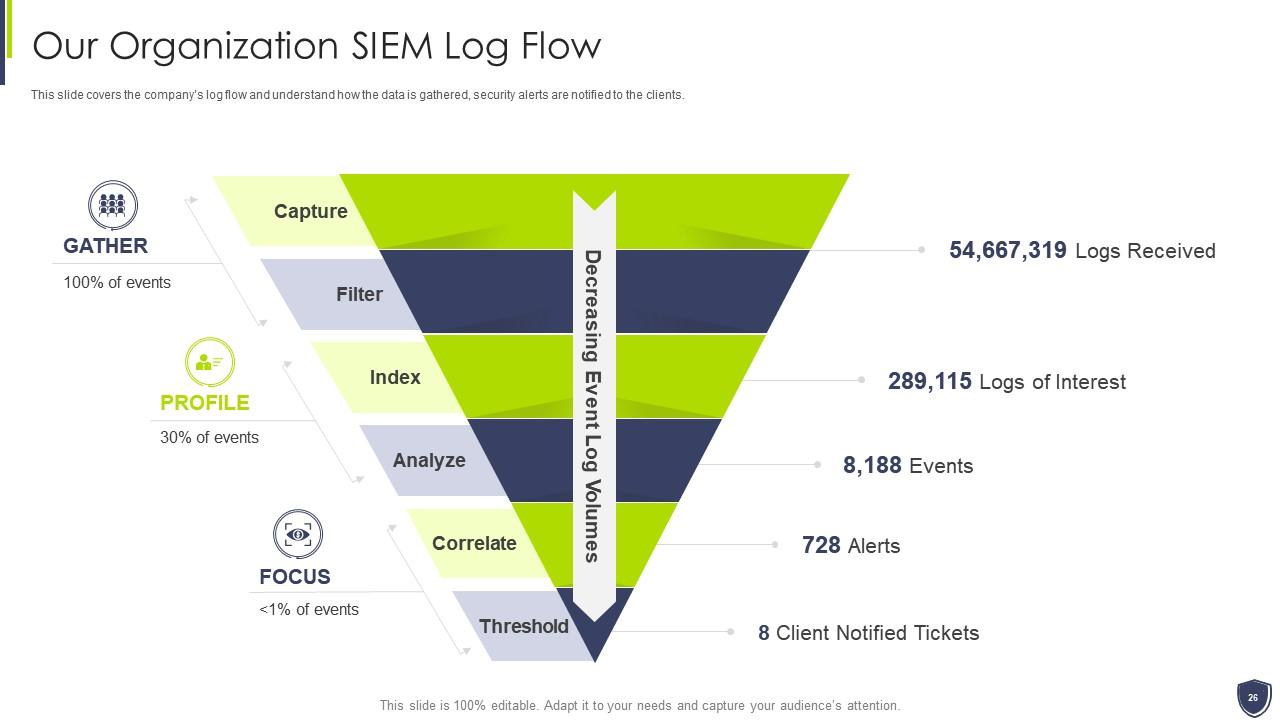
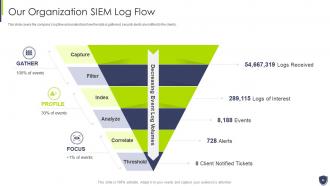
Slide 26: This slide covers the company’s log flow and understand how the data is gathered, security alerts are notified to the clients.
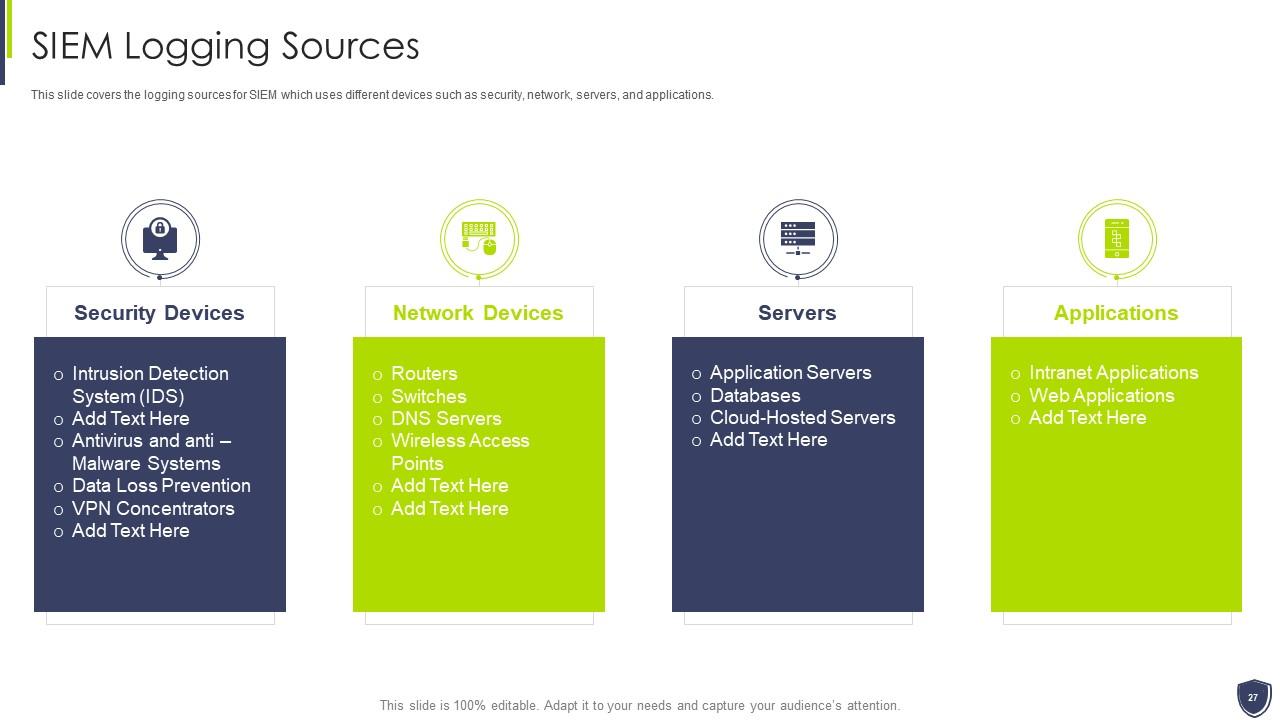
Slide 27: This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications.
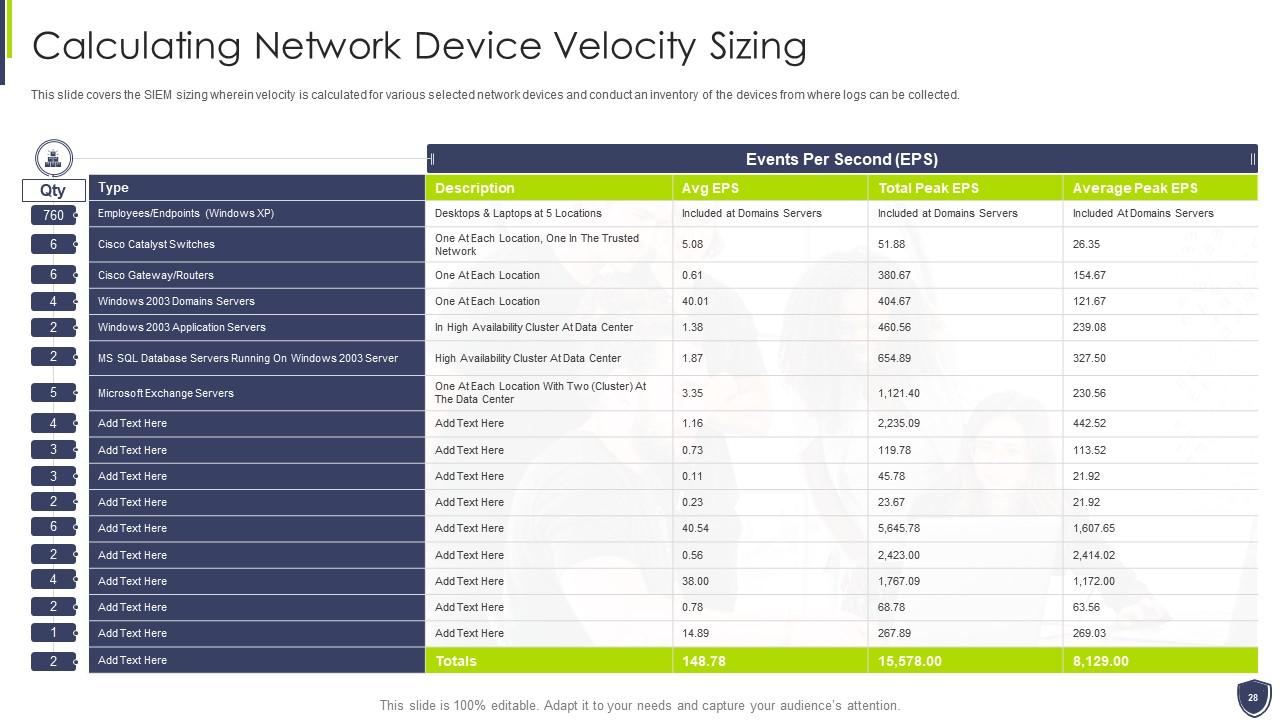
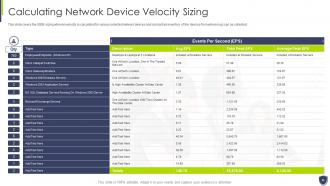
Slide 28: This slide covers the SIEM sizing wherein velocity is calculated for various selected network devices.
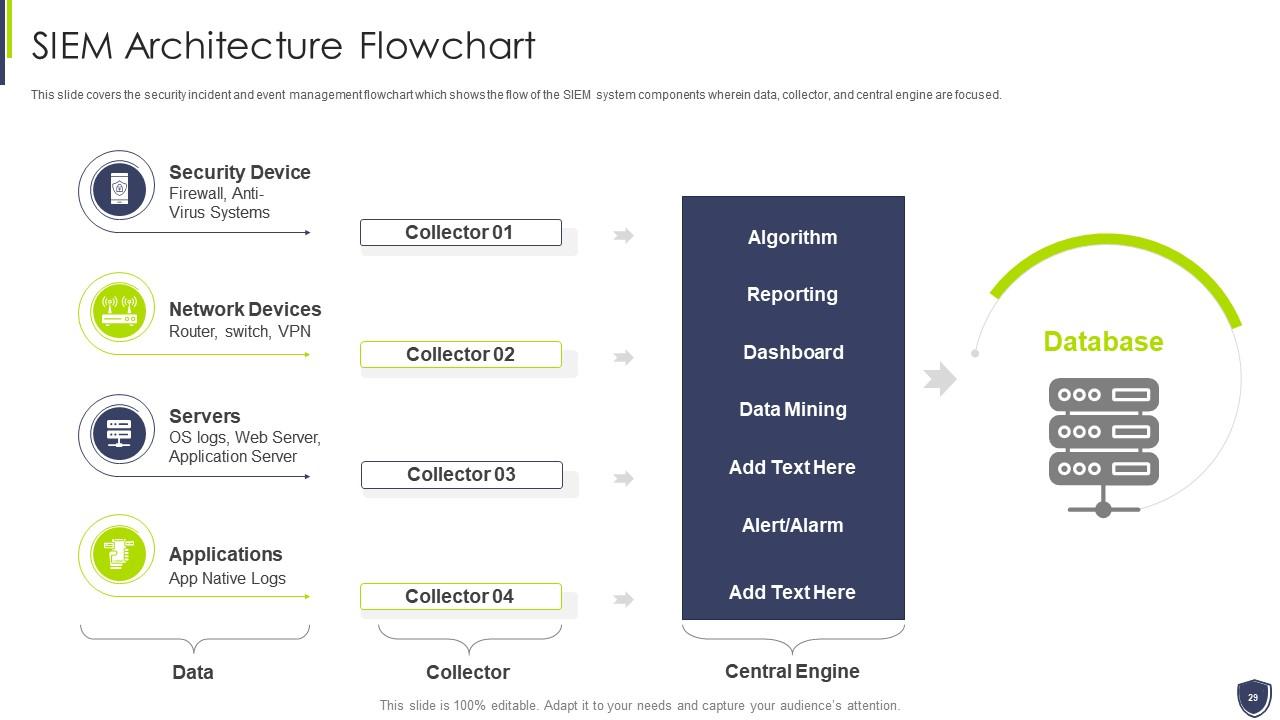
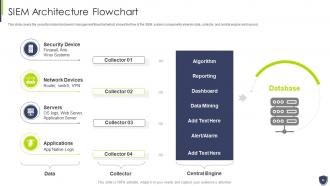
Slide 29: This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components.
Slide 30: This slide depicts title for 'SIEM Hosting Models'.
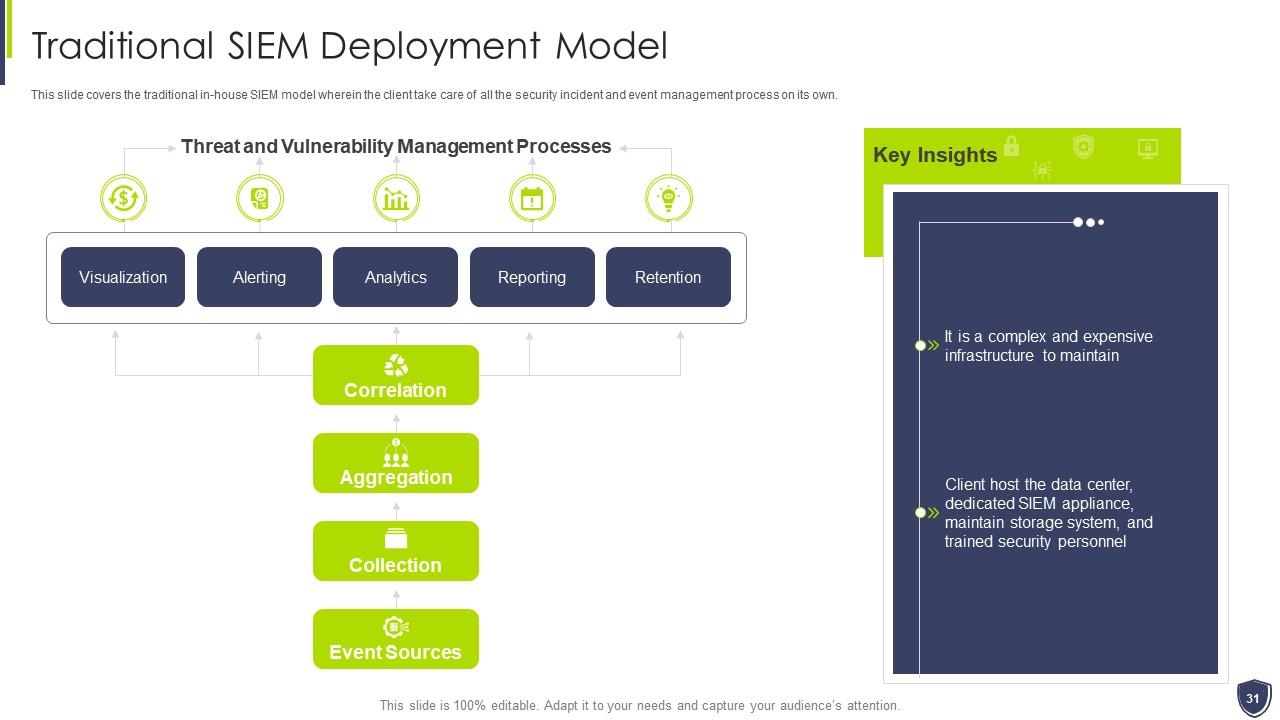
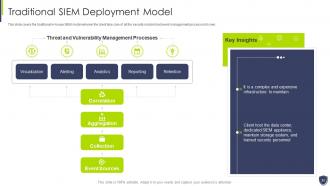
Slide 31: This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident.
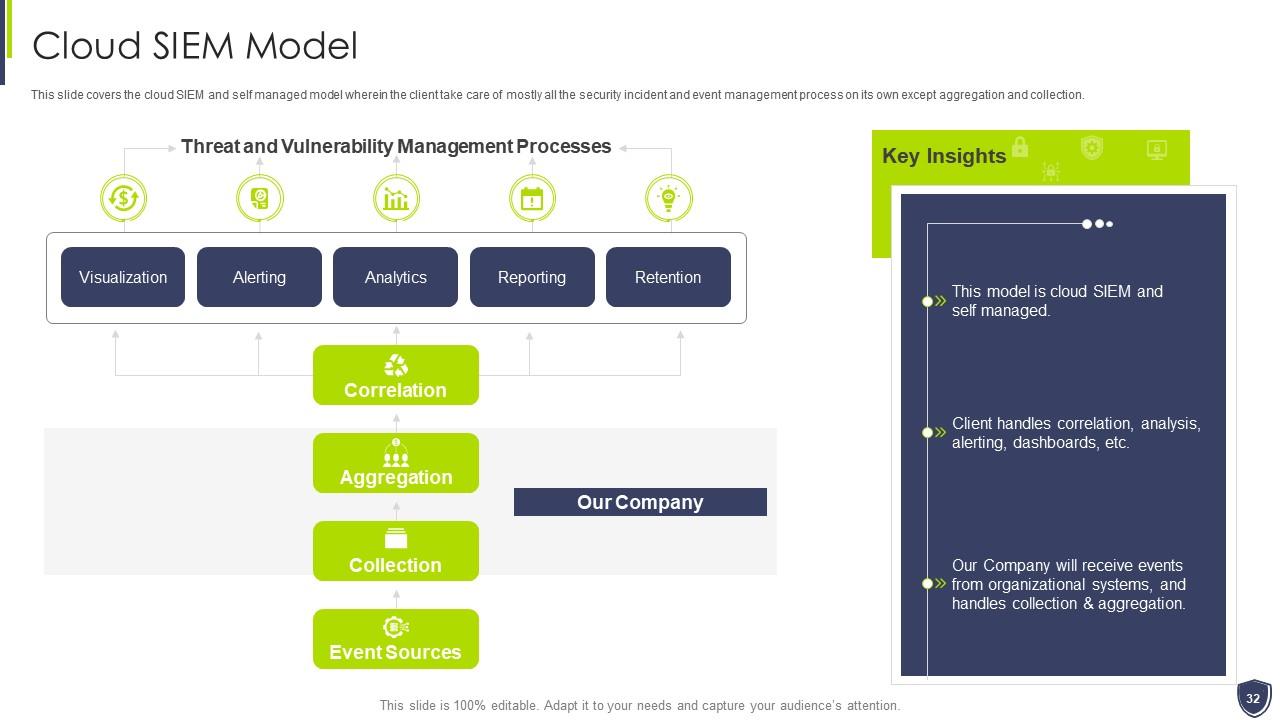
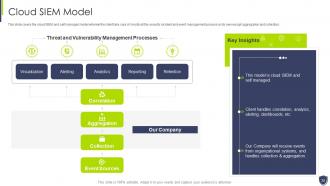
Slide 32: This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident.
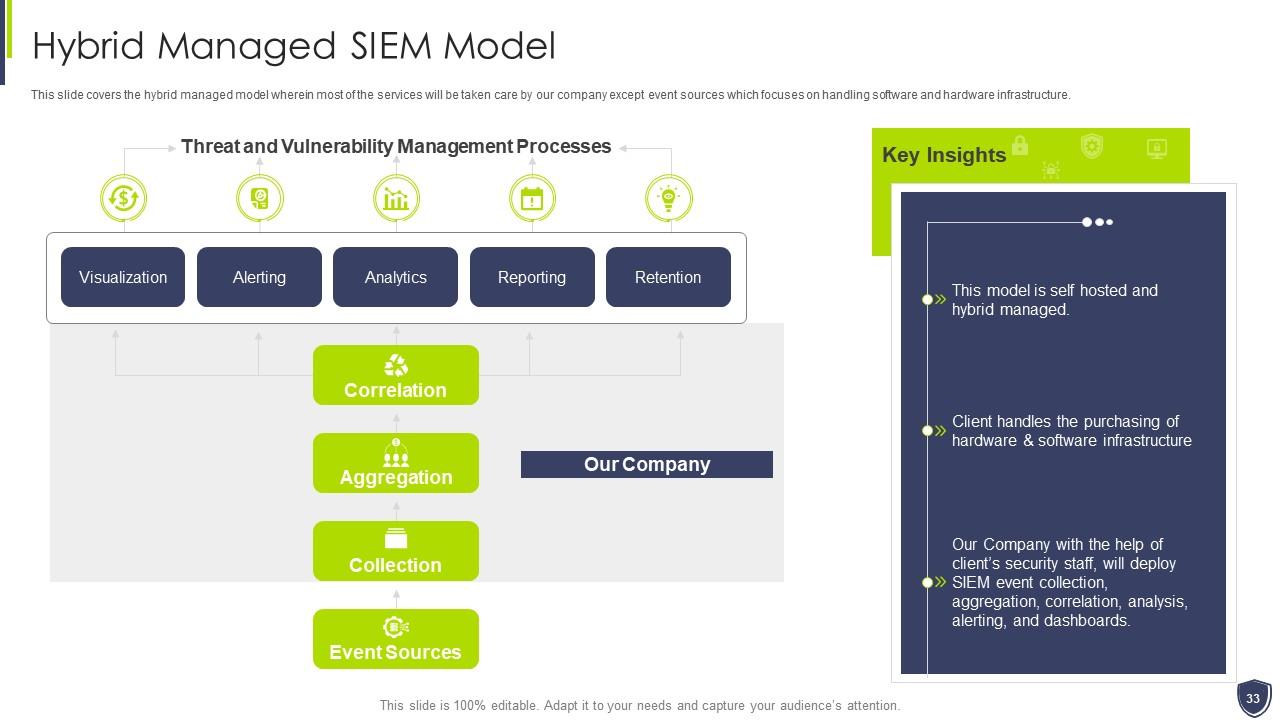
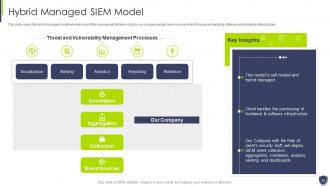
Slide 33: This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources.
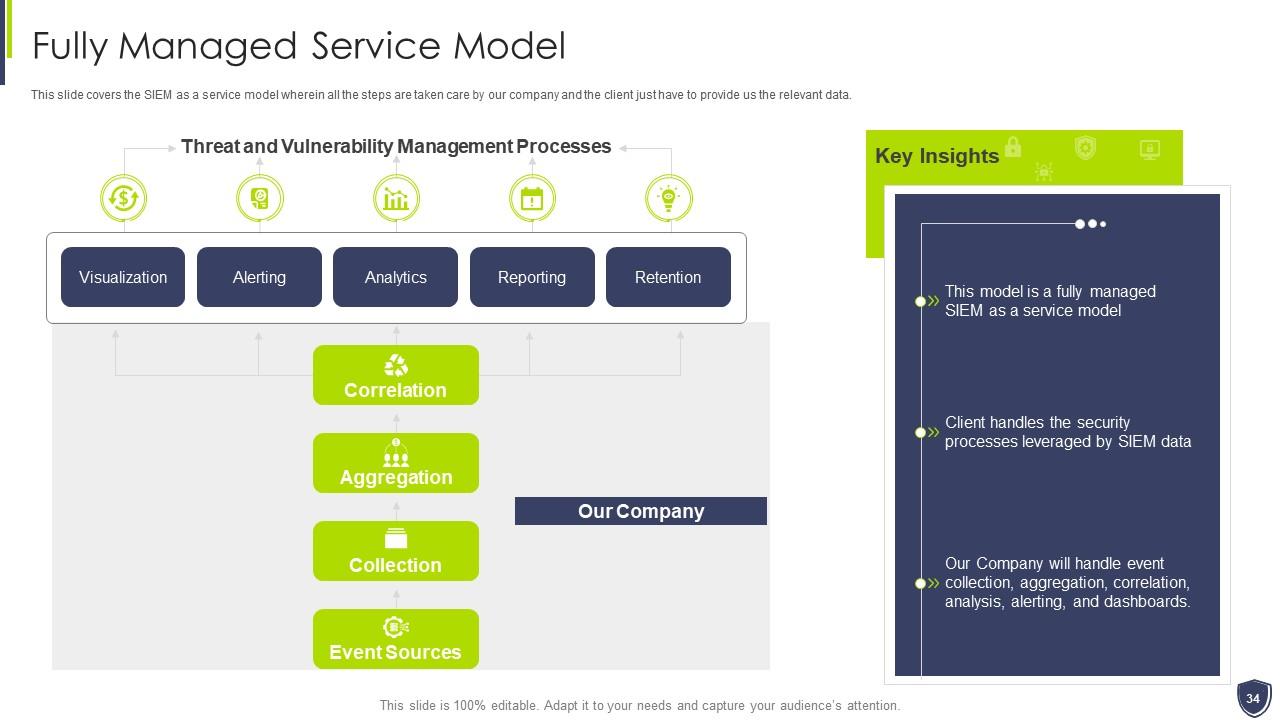
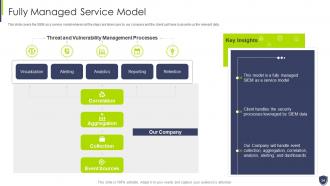
Slide 34: This slide covers the SIEM as a service model wherein all the steps are taken care by our company.
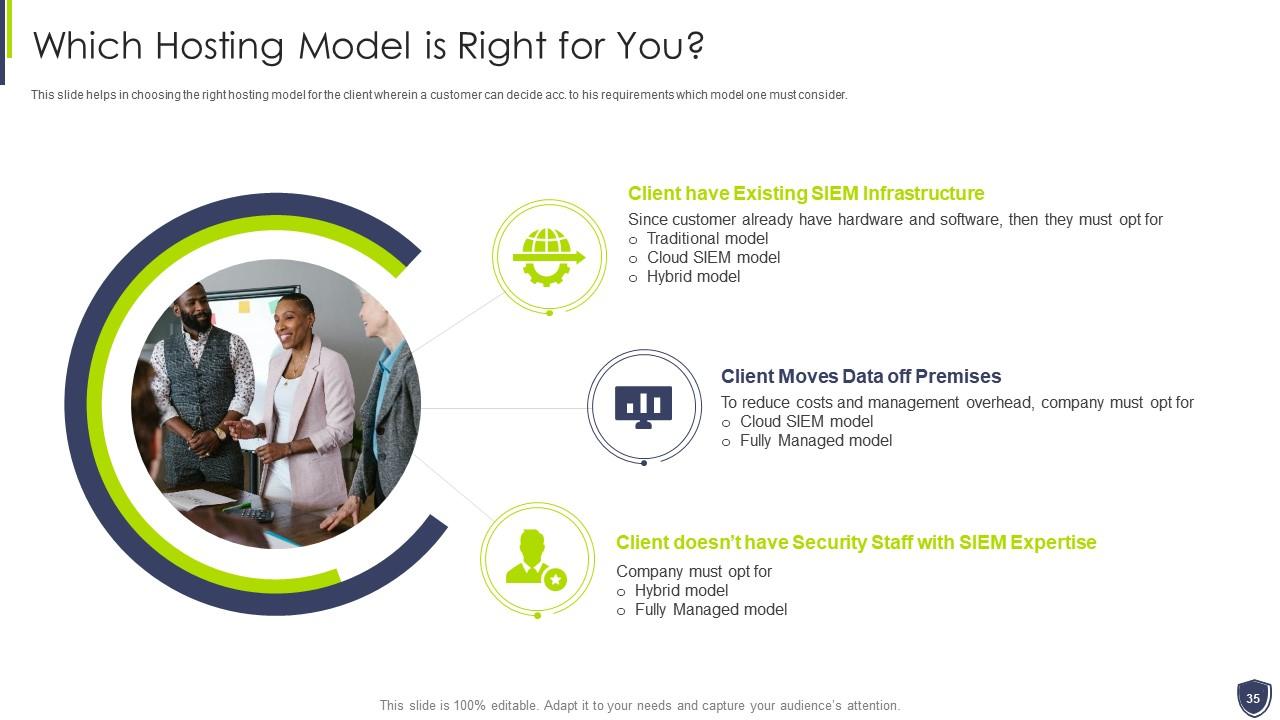
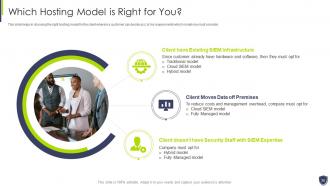
Slide 35: This slide helps in choosing the right hosting model for the client.
Slide 36: This slide displays title for 'Advancing our SIEM Technology'.
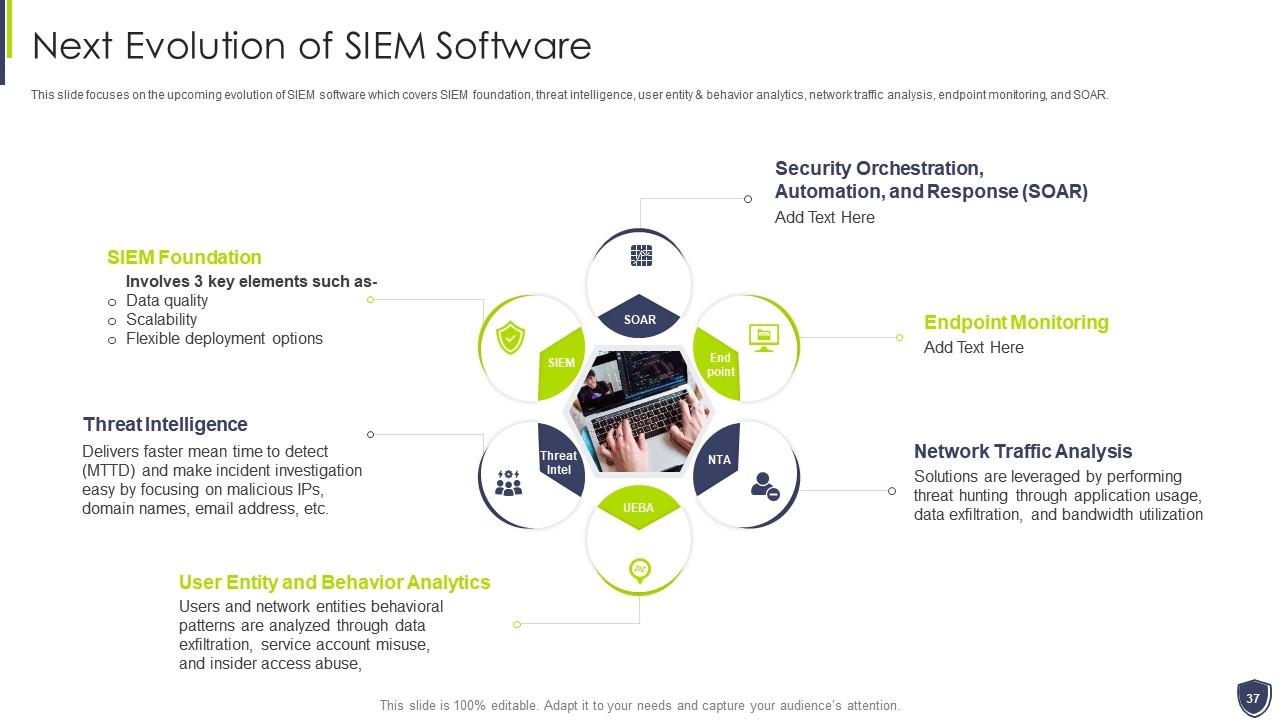
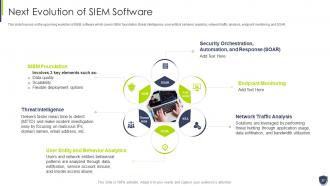
Slide 37: This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, etc.
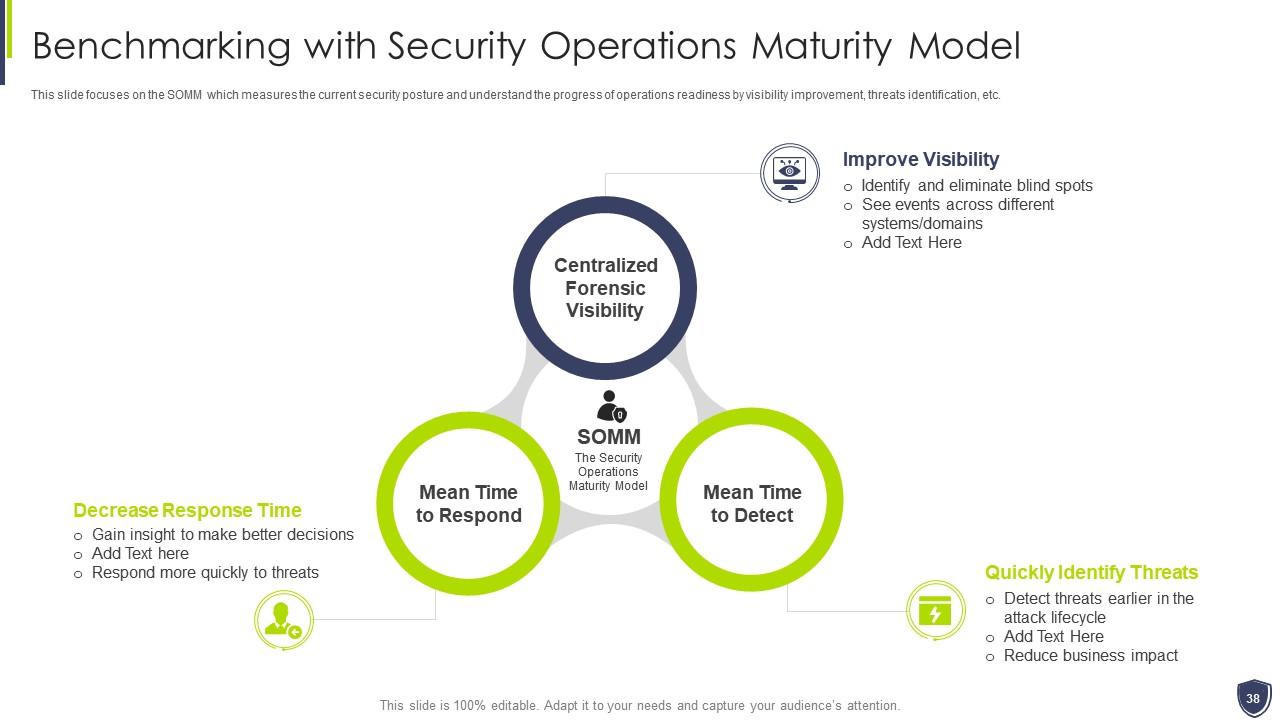
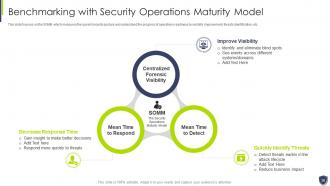
Slide 38: This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness.
Slide 39: This slide presents title for 'Costs of SIEM Services Offered by Our Company'.
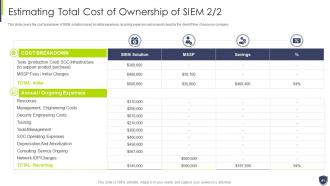
Slide 40: This slide covers the total cost of ownership incurred by SIEM services.
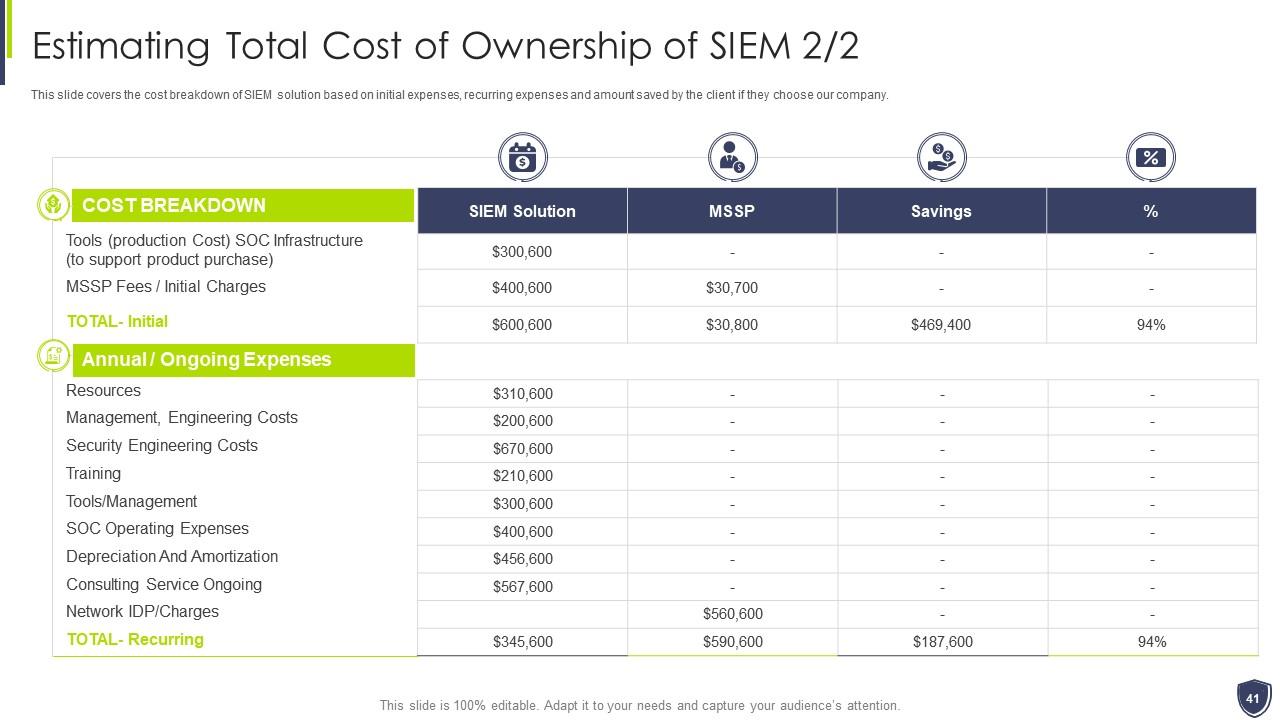
Slide 41: This slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses etc.
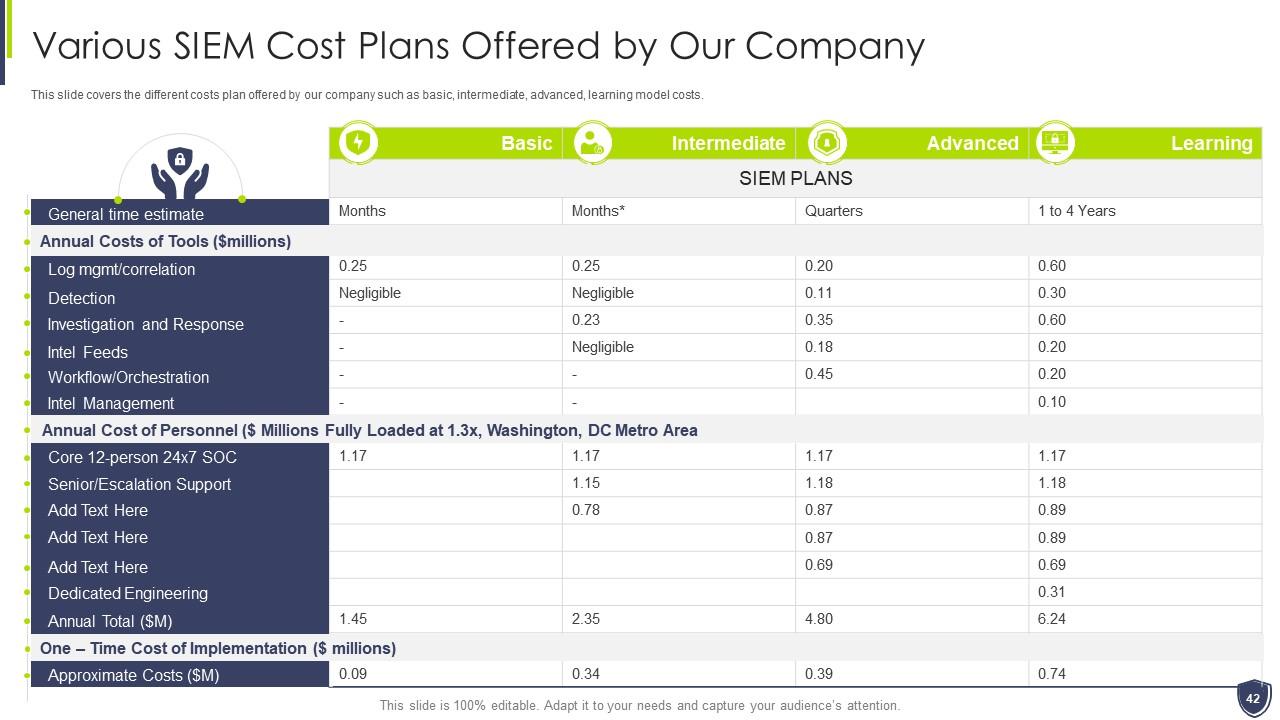
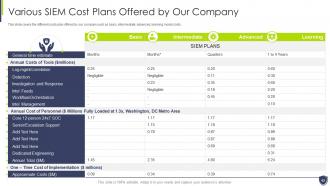
Slide 42: This slide covers the different costs plan offered by our company such as basic, intermediate, advanced, etc.
Slide 43: This slide exhibits title for 'Why to Choose Our Company'.
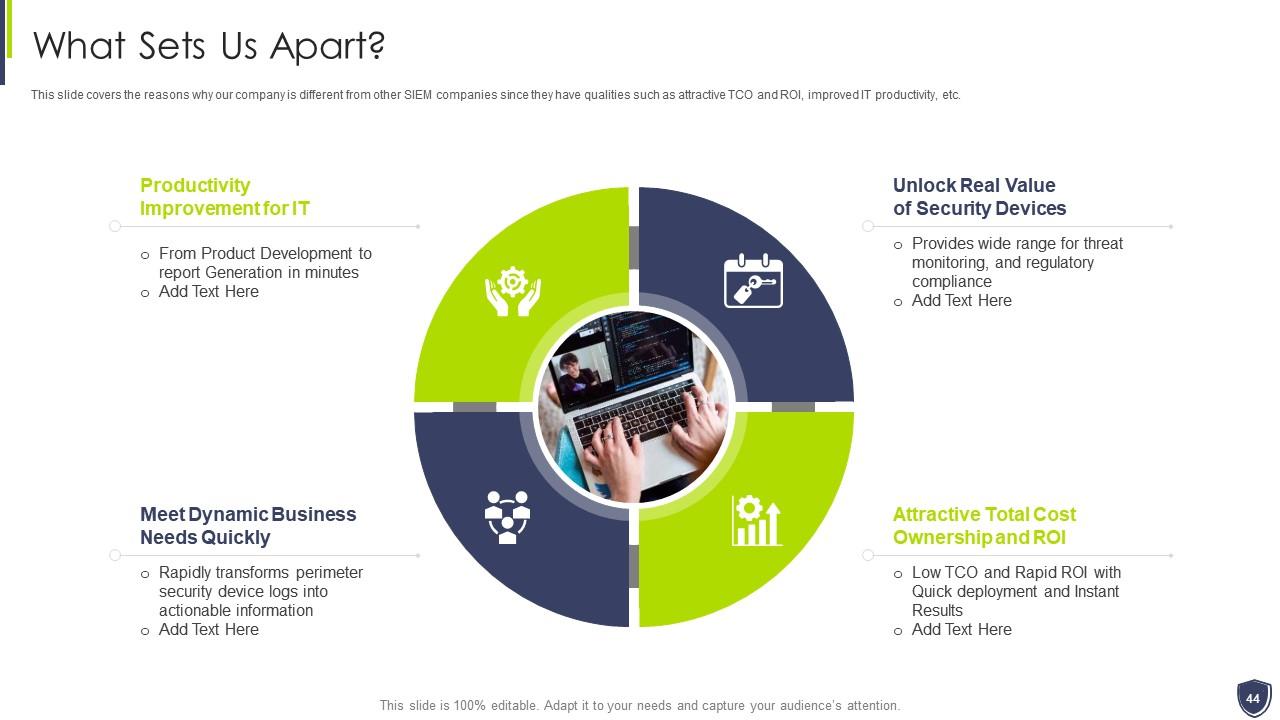
Slide 44: This slide covers the reasons why our company is different from other SIEM companies.
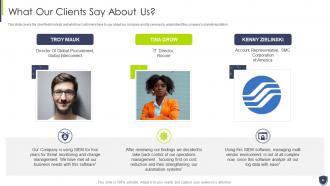
Slide 45: This slide covers the client testimonials and what our customers have to say about our company and its services.
Slide 46: This slide depicts title for 'SIEM Dashboard'.
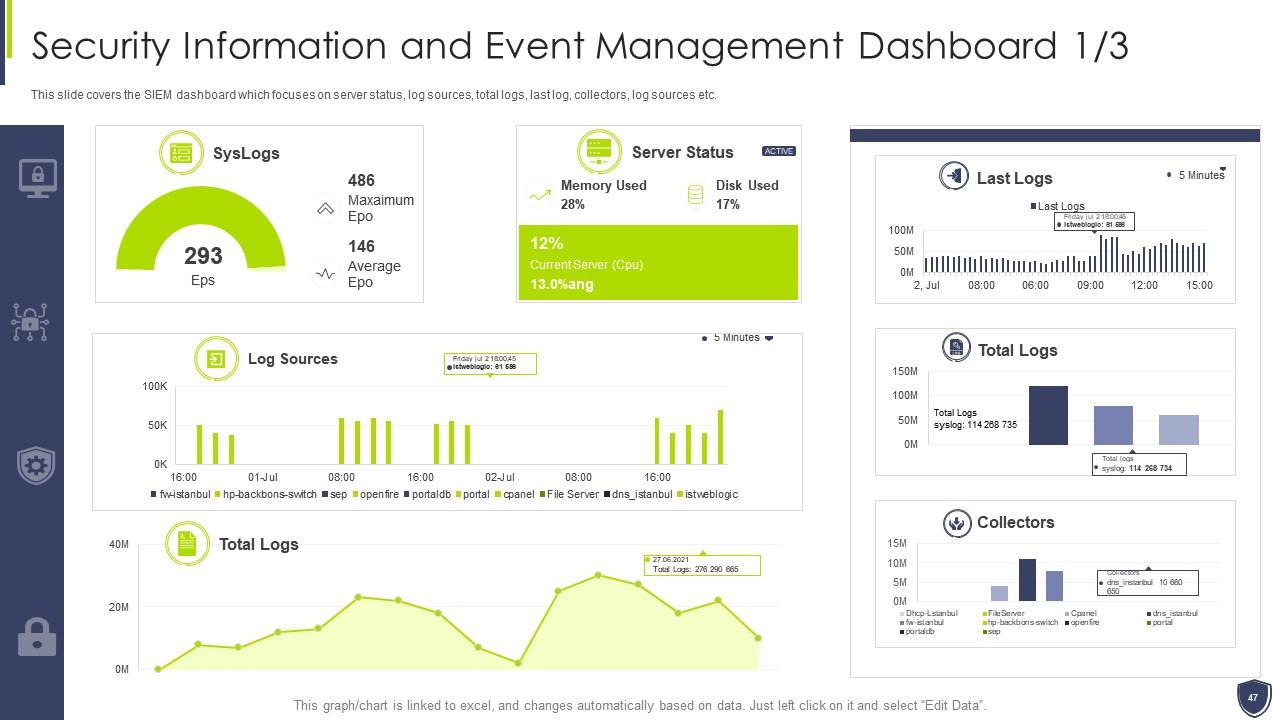
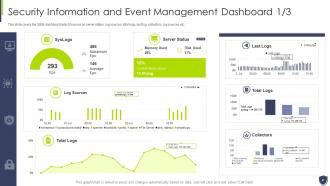
Slide 47: This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, etc.
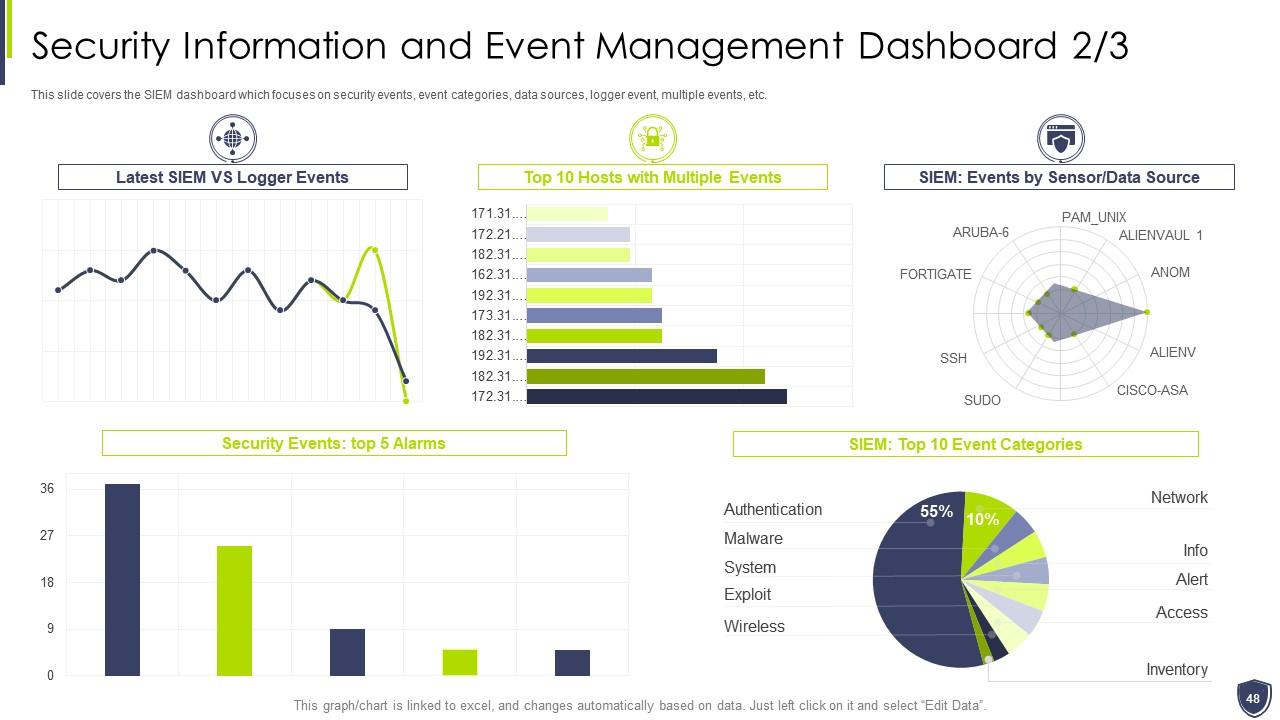
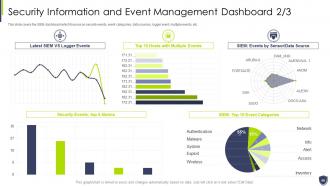
Slide 48: This slide covers the SIEM dashboard which focuses on security events, event categories, etc.
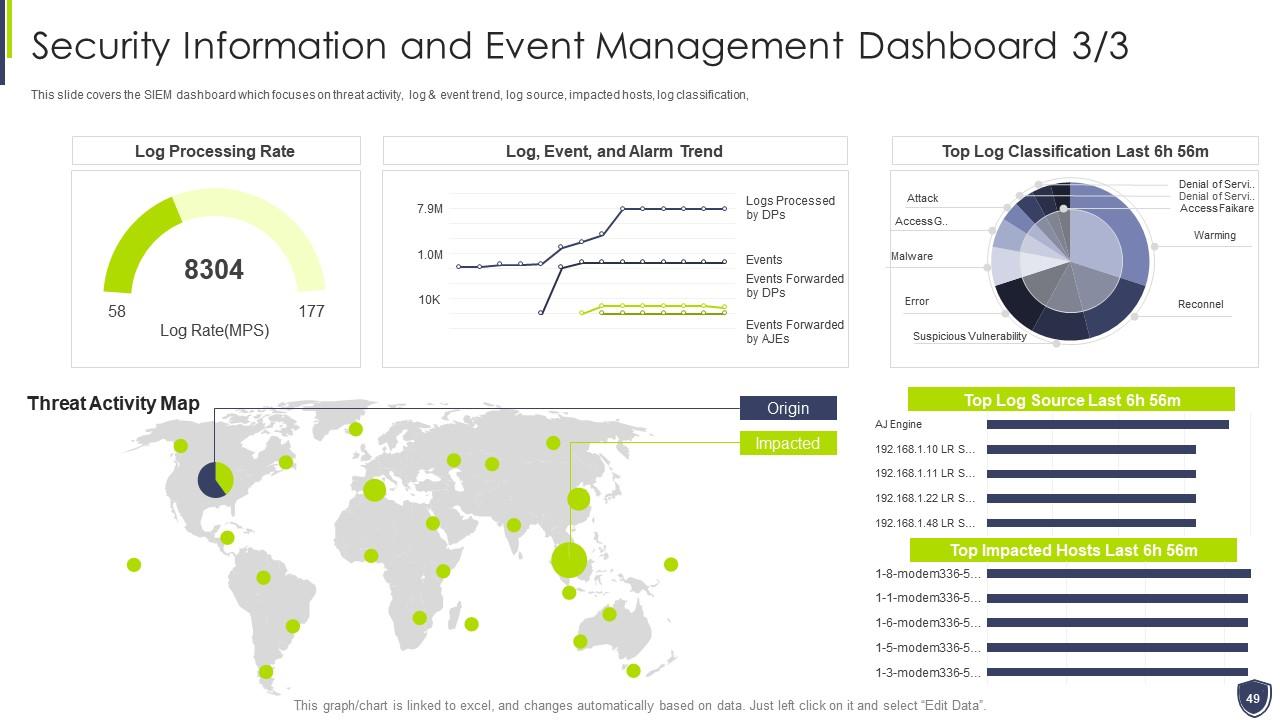
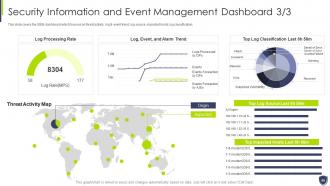
Slide 49: This slide covers the SIEM dashboard which focuses on threat activity, log & event trend, log source, etc.
Slide 50: This slide displays Icons for Improve IT Security with Vulnerability Management.
Slide 51: This slide is titled as Additional Slides for moving forward.
Slide 52: This slide shows Log Management Services.
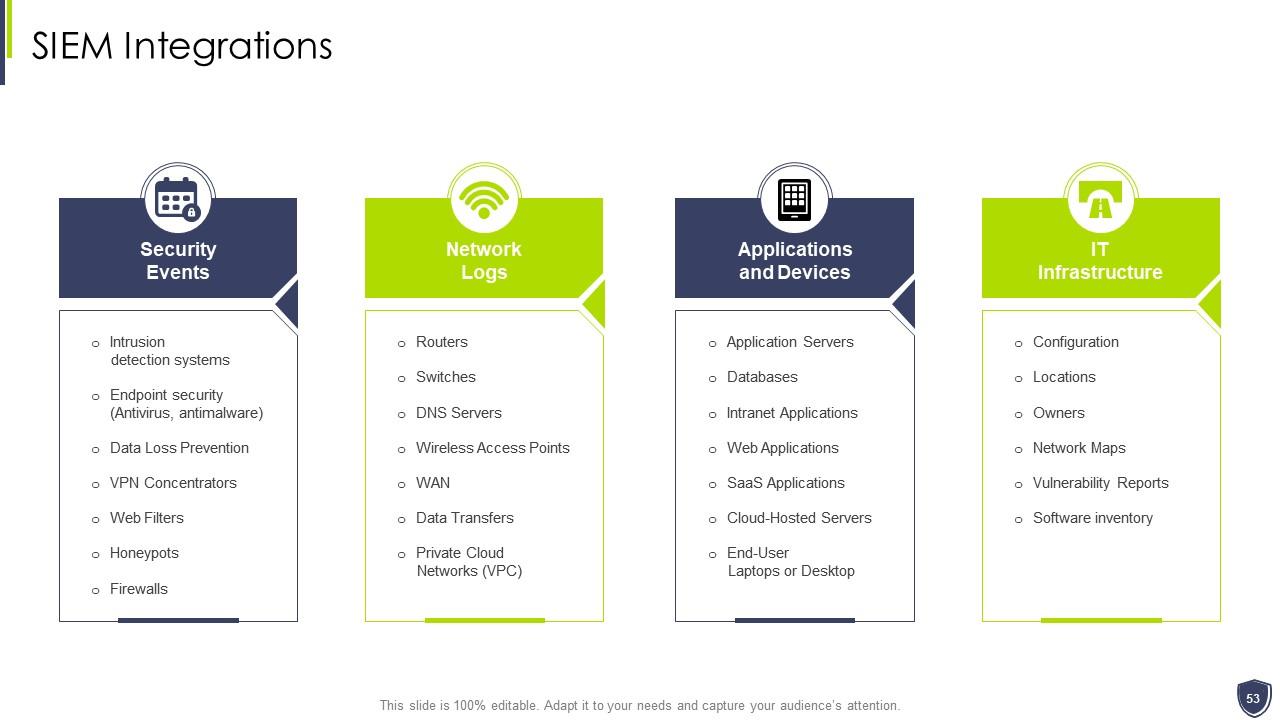
Slide 53: This slide displays SIEM Integrations.
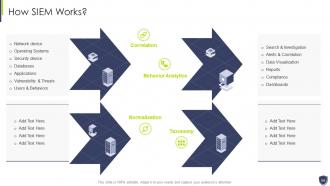
Slide 54: This slide presents 'How SIEM Works'?
Slide 55: This slide exhibits SIEM Architecture.
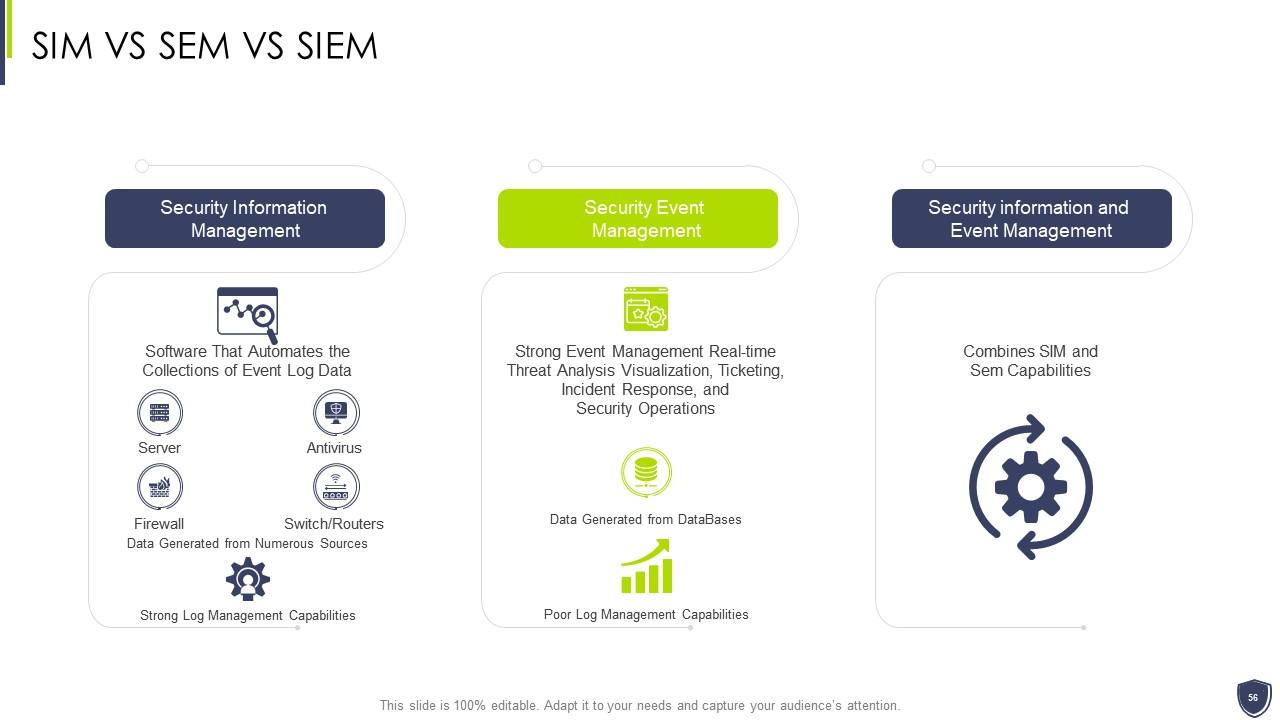
Slide 56: This slide depicts SIM VS SEM VS SIEM.
Slide 57: This is About Us slide to show company specifications etc.
Slide 58: This is a Timeline slide. Show data related to time intervals here.
Slide 59: This slide shows Post It Notes. Post your important notes here.
Slide 60: This slide contains Puzzle with related icons and text.
Slide 61: This is a Thank You slide with address, contact numbers and email address.
Improve it security with vulnerability management powerpoint presentation slides with all 66 slides:
Use our Improve IT Security With Vulnerability Management Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Easily Editable.
-
Topic best represented with attractive design.