Risk Based Methodology To Cyber And Information Security Powerpoint Presentation Slides
As IT organizations strive for digitization, many face significant cybersecurity challenges. Here is an efficiently designed template on Risk Based Methodology to Cyber and Information Security that will benefit the companies that want to introduce an information security program for effectively handling cybersecurity risks across their digital landscape. The presentation starts with the global market insights slide a company can use this slide to address the global market summary of cybersecurity. Market insights slide is followed by declines such as the companys digitalization levels, priority requirements for buying IoT products, threat drivers, and emerging technologies impact cybersecurity. To ensure information security, the company may use defining business priorities slide, focusing on effective risk and incident management. With the gap identification slide, the company may highlight its current approach and the details of its process, significant flaws, and risk management cost. A communication plan for cyber breaches will assist the company in maintaining effective communication between different team owners and coordinators, which will aid in the efficient handling of risk events. Finally, metrics to track the program effectiveness section will help the company track security risk events. Get access to this powerful template now.
As IT organizations strive for digitization, many face significant cybersecurity challenges. Here is an efficiently designe..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Risk Based Methodology To Cyber And Information Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty four slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Risk-Based Methodology to Cyber and Information Security. State Your Company Name and begin.
Slide 2: This is an Agenda slide. State your agendas here.
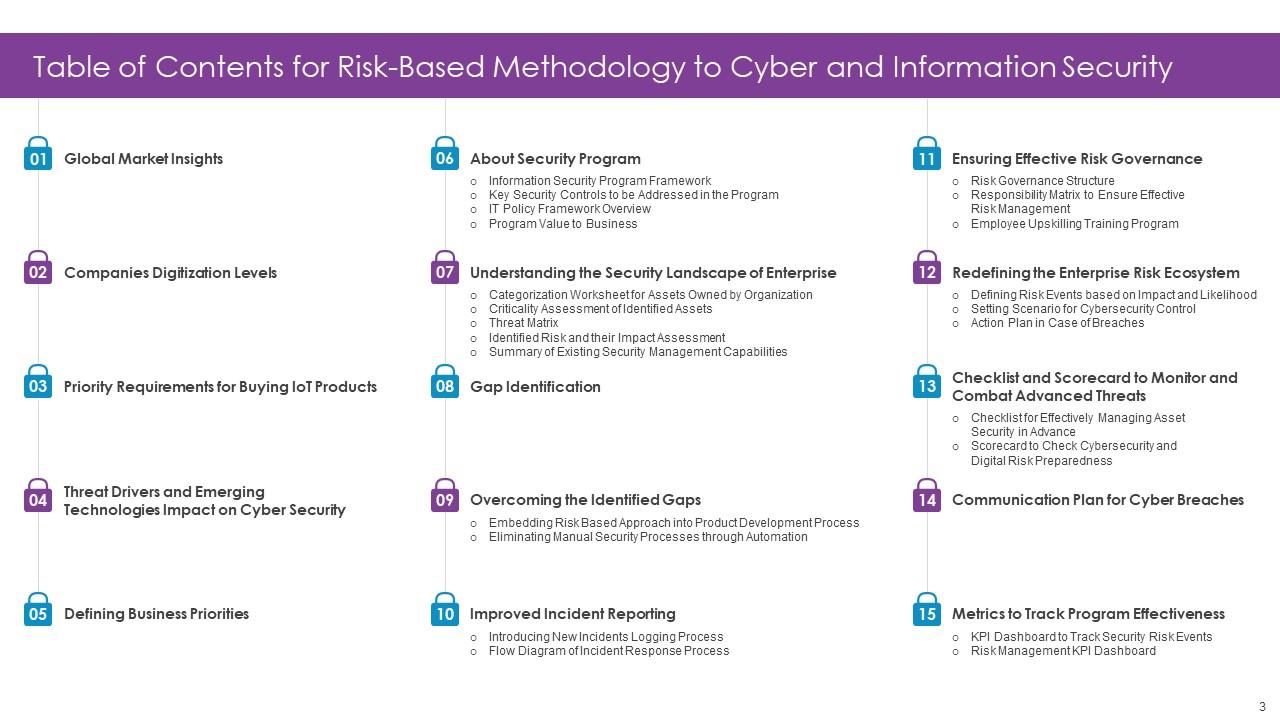
Slide 3: This slide presents Table of Content for the presentation.
Slide 4: This slide highlights title for topics that are to be covered next in the template.
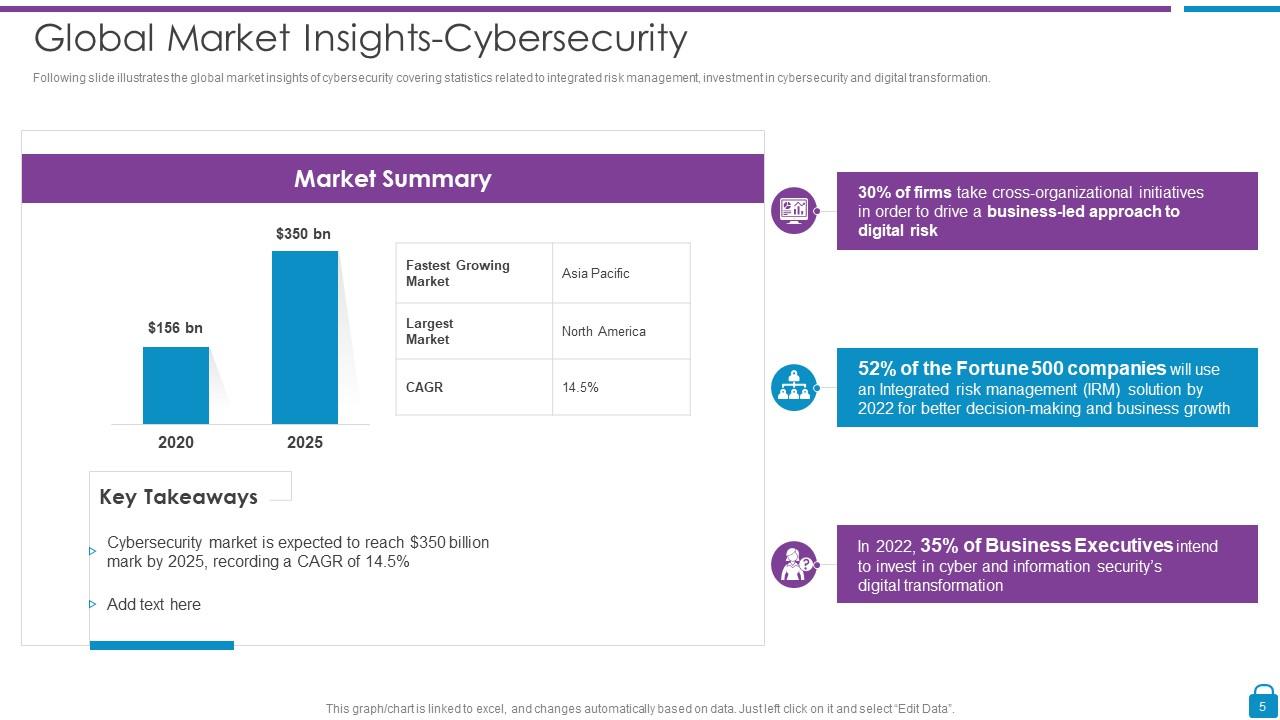
Slide 5: This slide shows global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation.
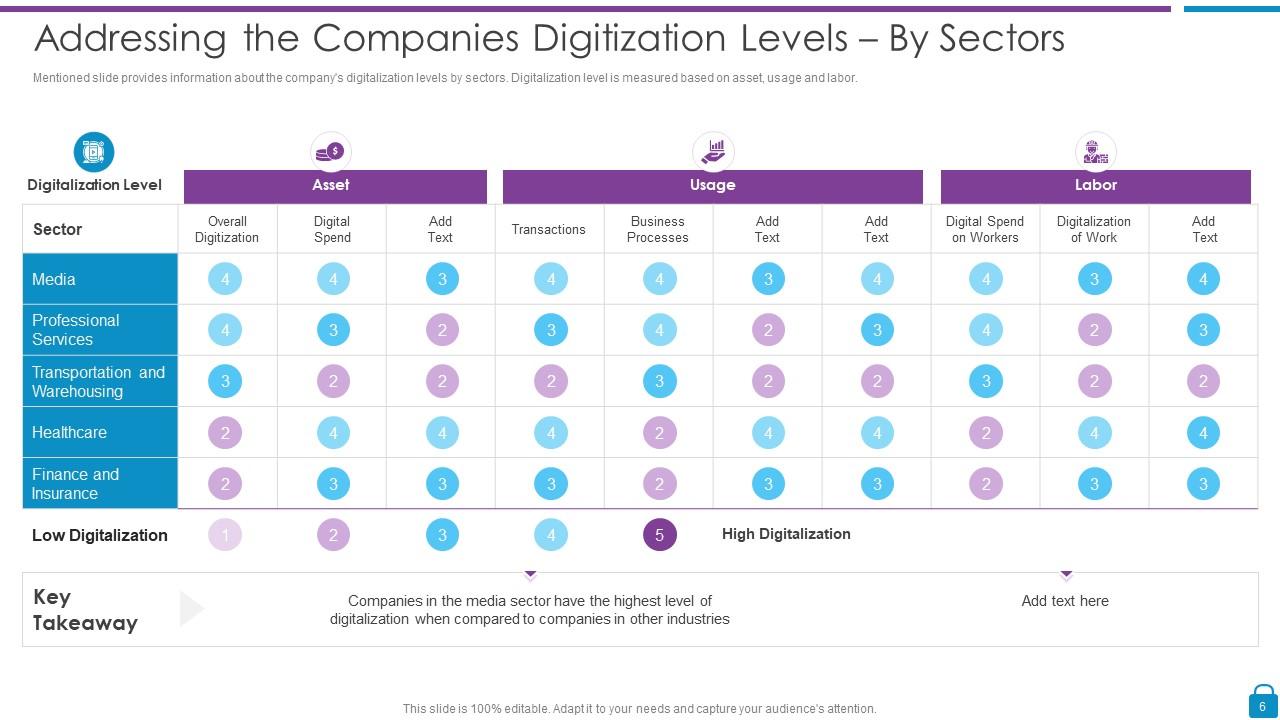
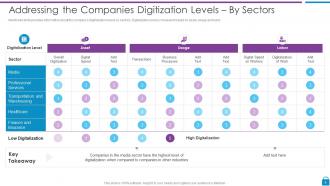
Slide 6: This slide displays Addressing the Companies Digitization Levels – By Sectors.
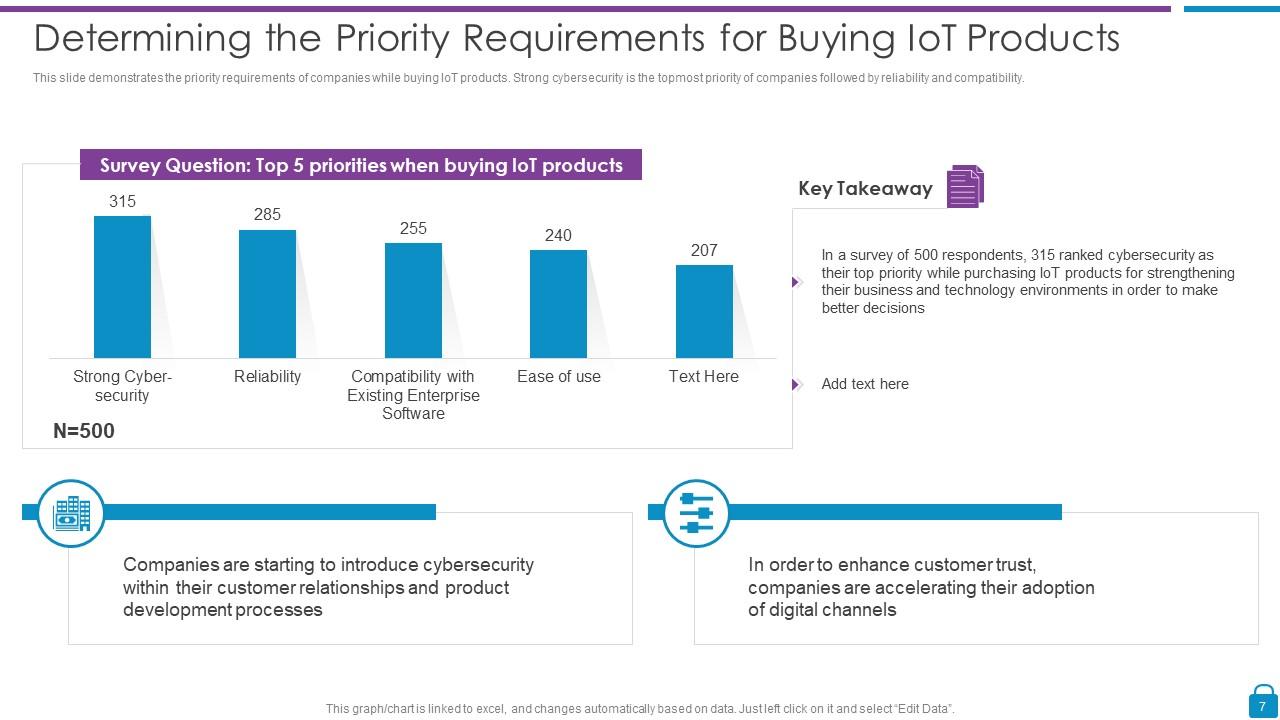
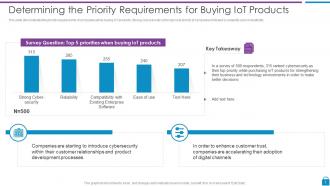
Slide 7: This slide represents Determining the Priority Requirements for Buying IoT Products.
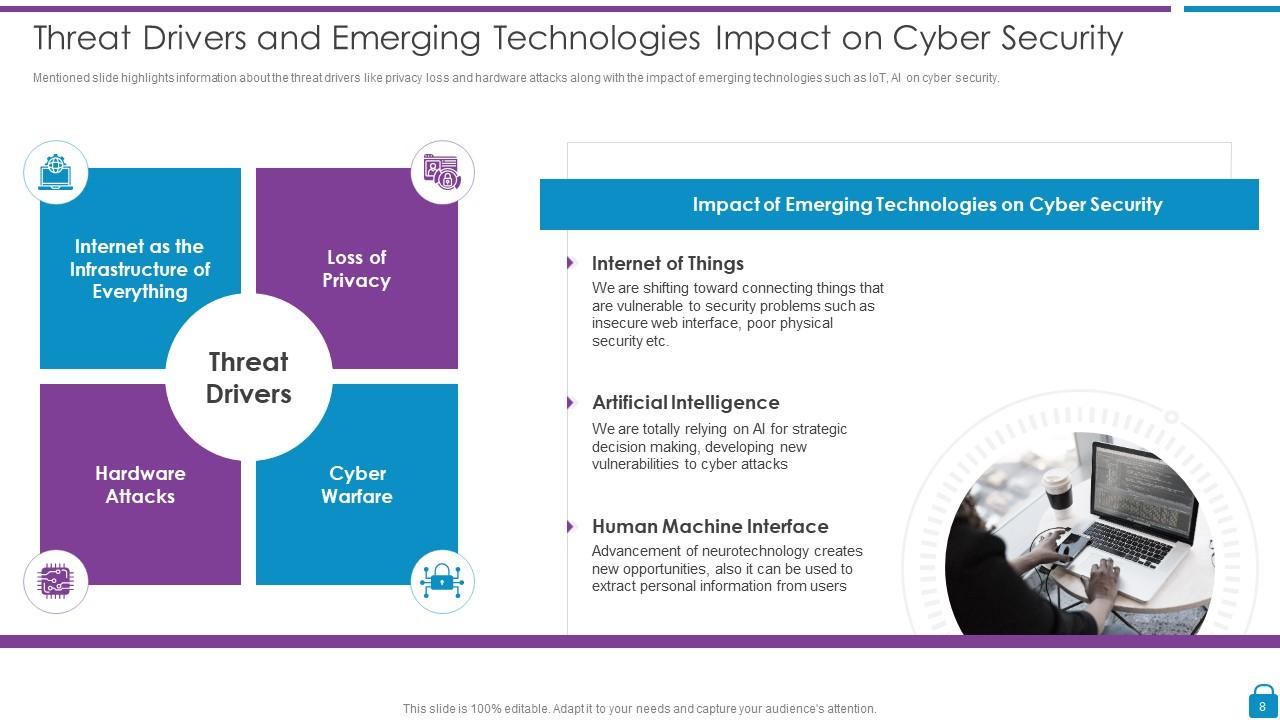
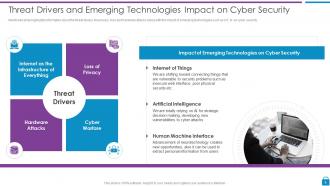
Slide 8: This slide shows Threat Drivers and Emerging Technologies Impact on Cyber Security.
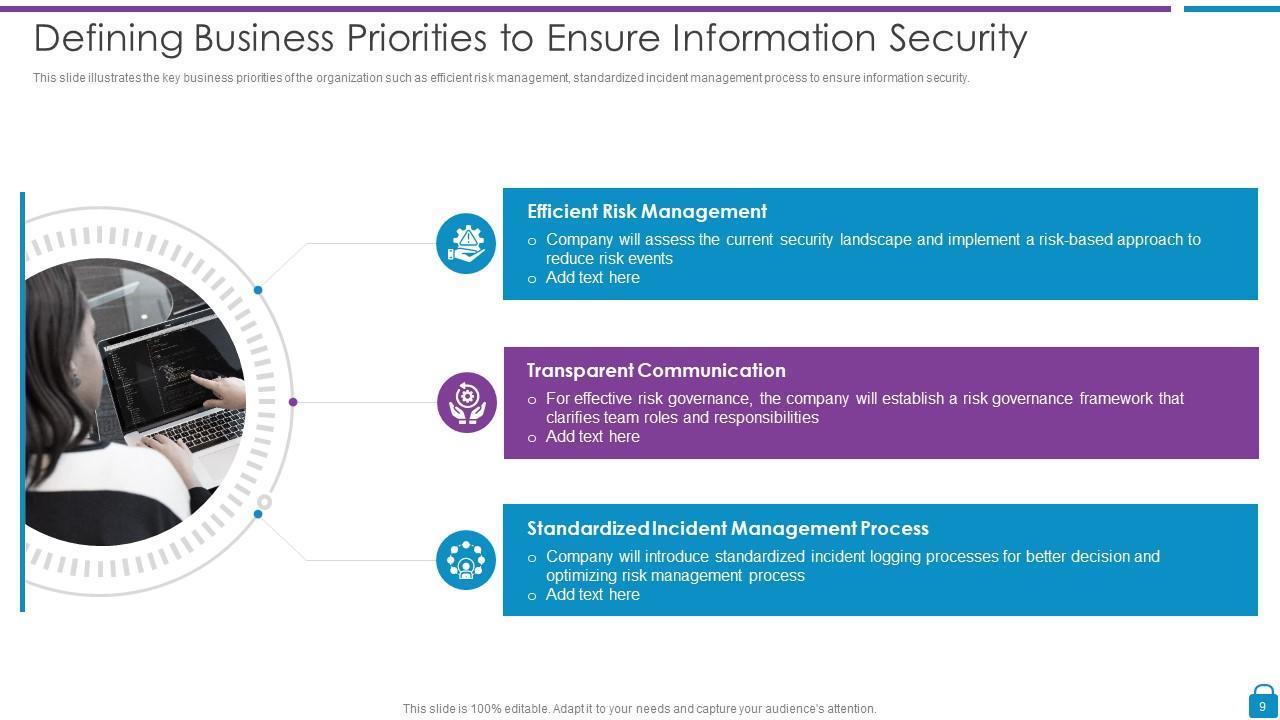
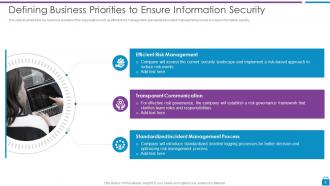
Slide 9: This slide presents Defining Business Priorities to Ensure Information Security.
Slide 10: This slide highlights title for topics that are to be covered next in the template.
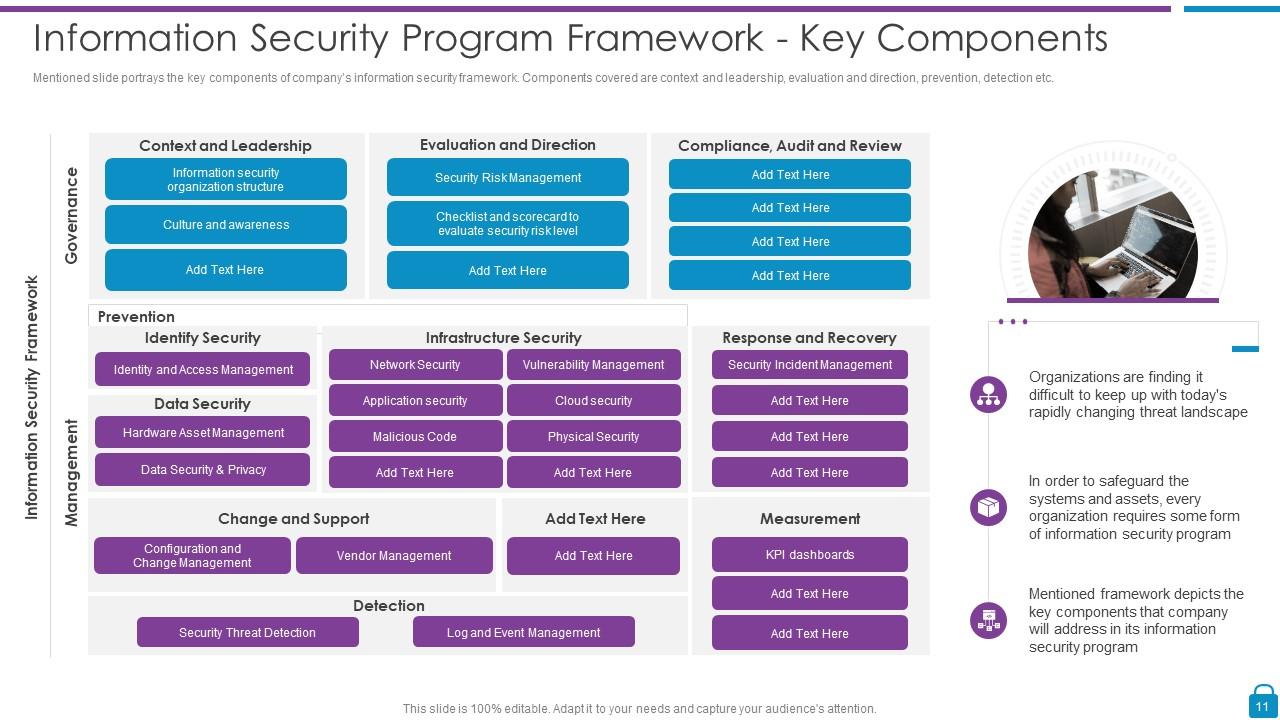
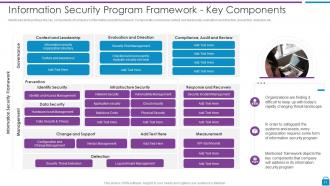
Slide 11: This slide displays key components of company’s information security framework.
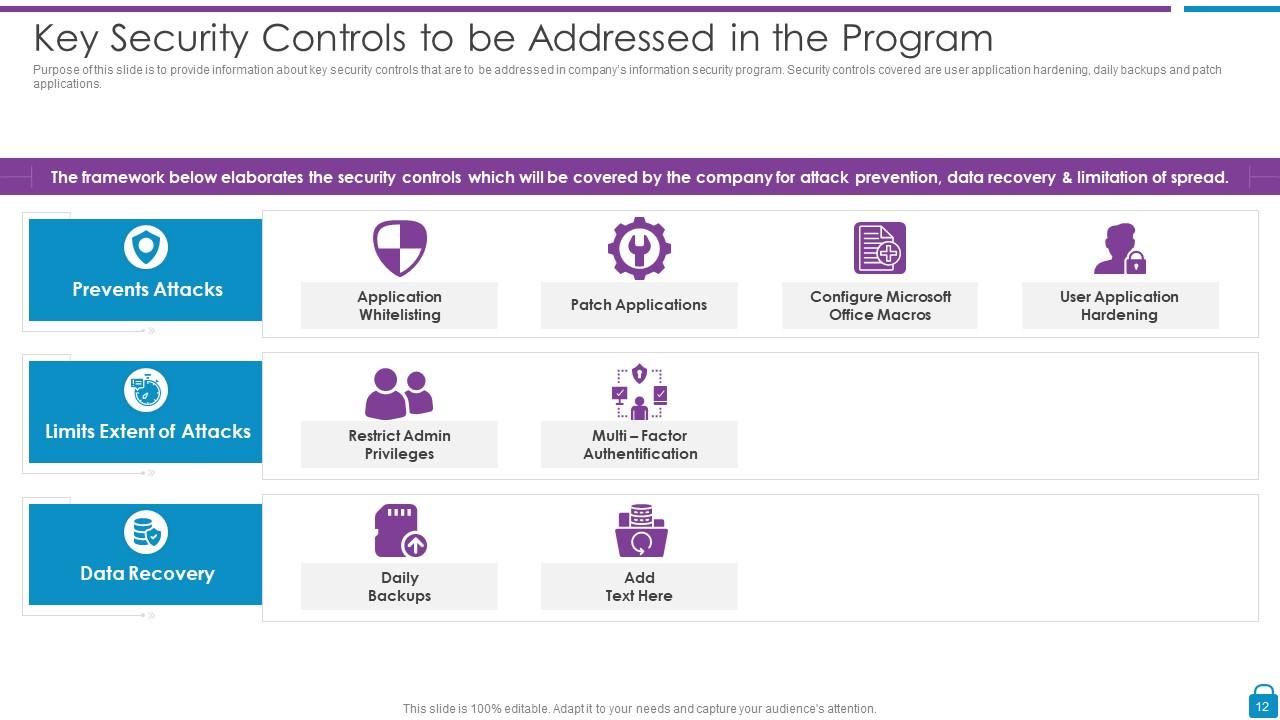
Slide 12: This slide represents Key Security Controls to be Addressed in the Program.
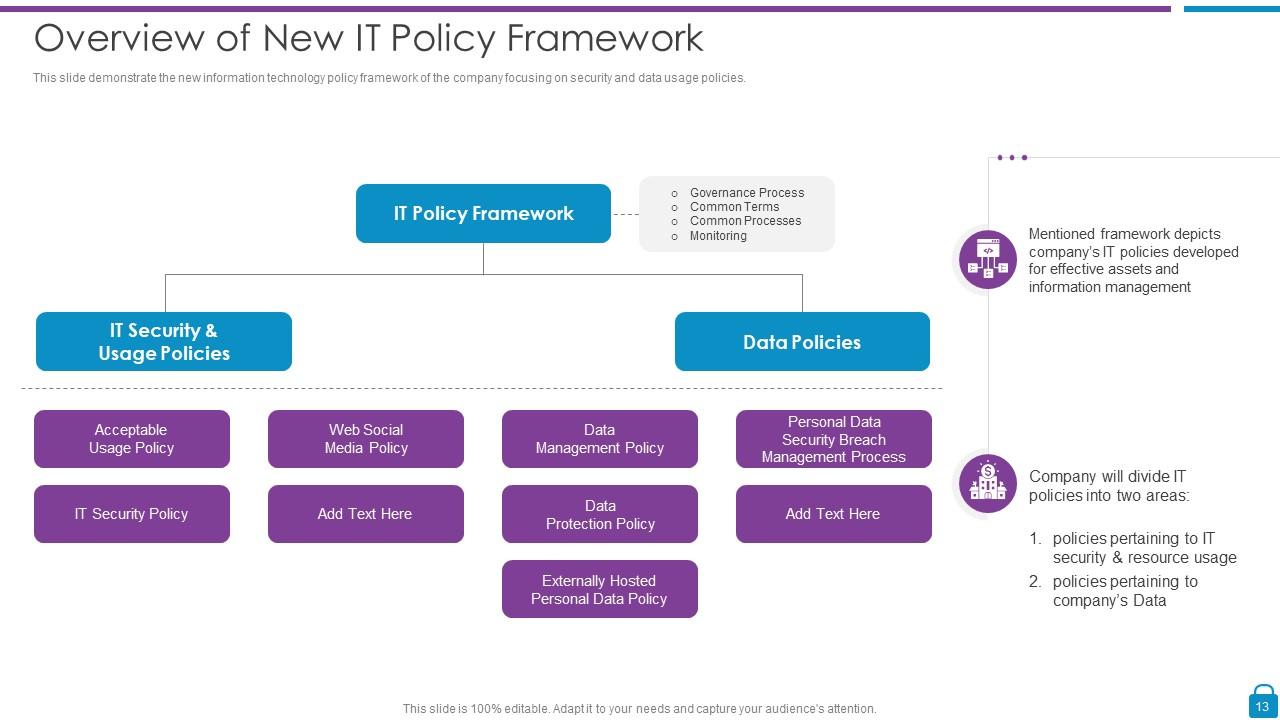
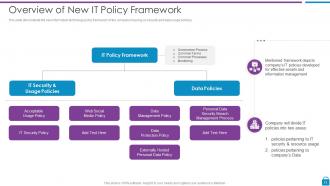
Slide 13: This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies.
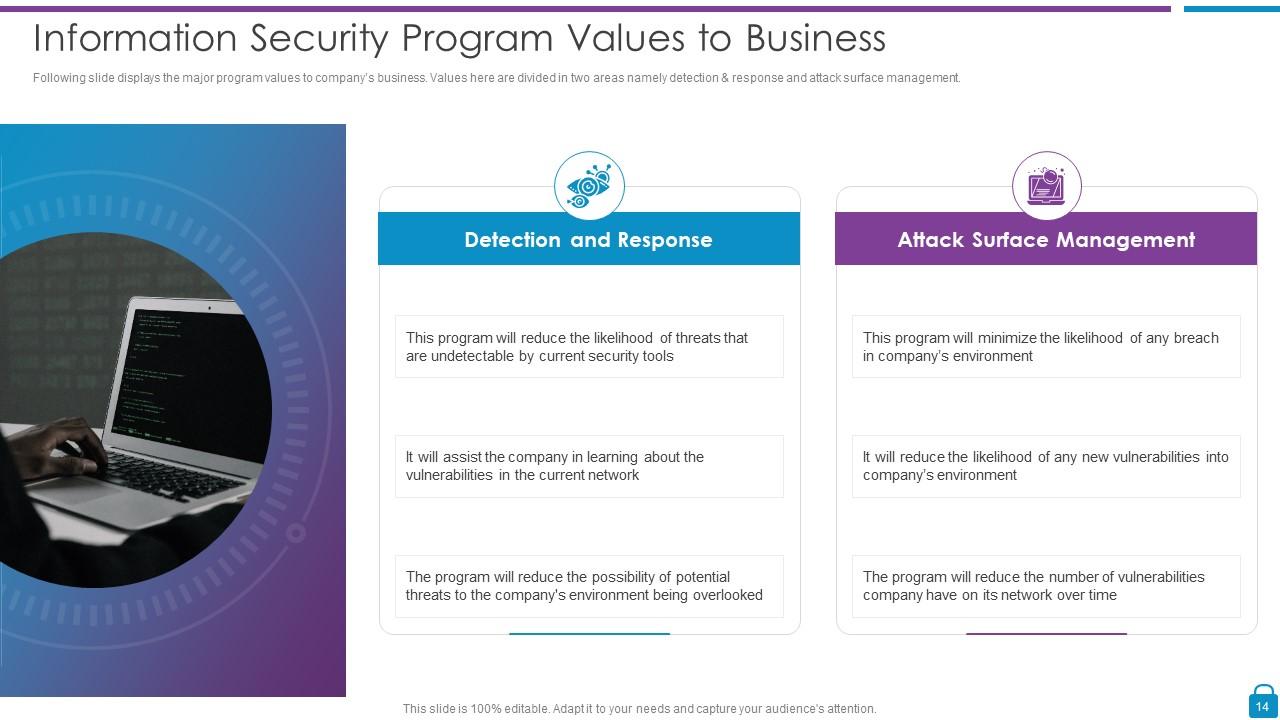
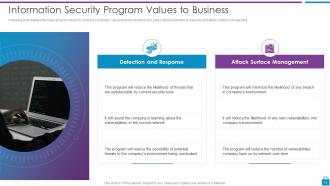
Slide 14: This slide presents Information Security Program Values to Business.
Slide 15: This slide highlights title for topics that are to be covered next in the template.
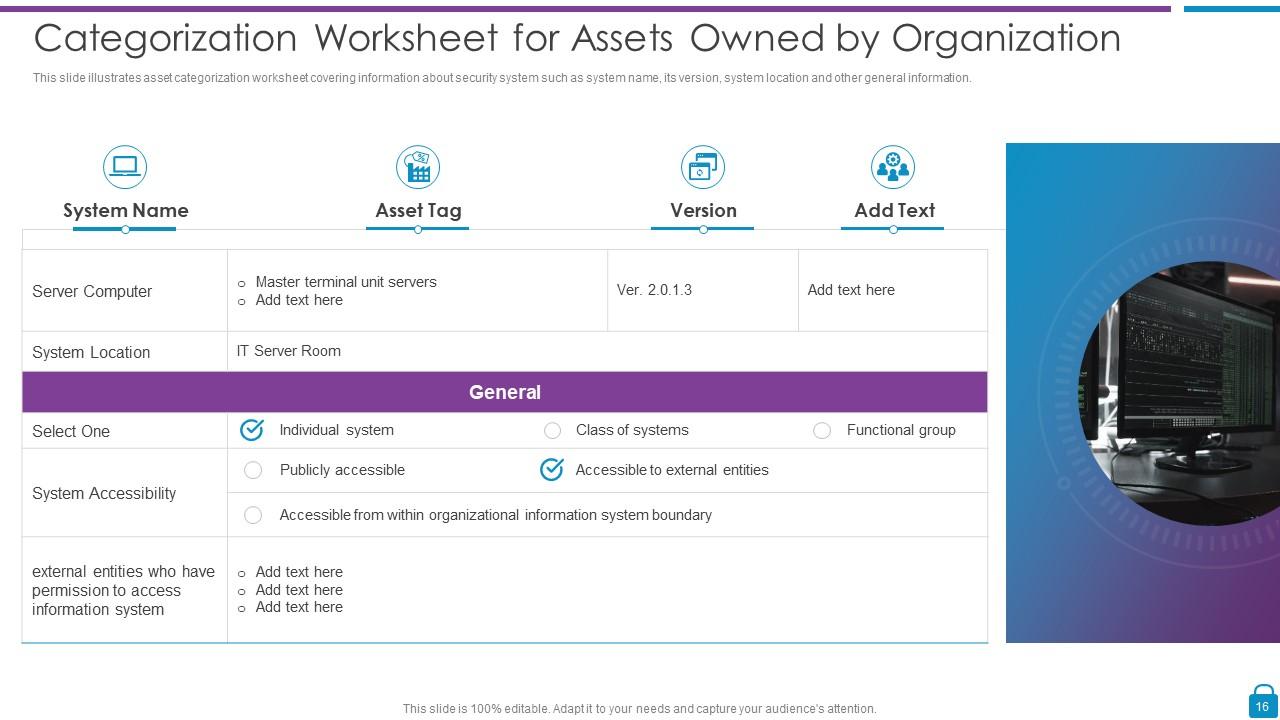
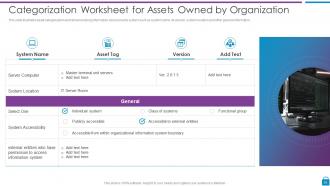
Slide 16: This slide displays Categorization Worksheet for Assets Owned by Organization.
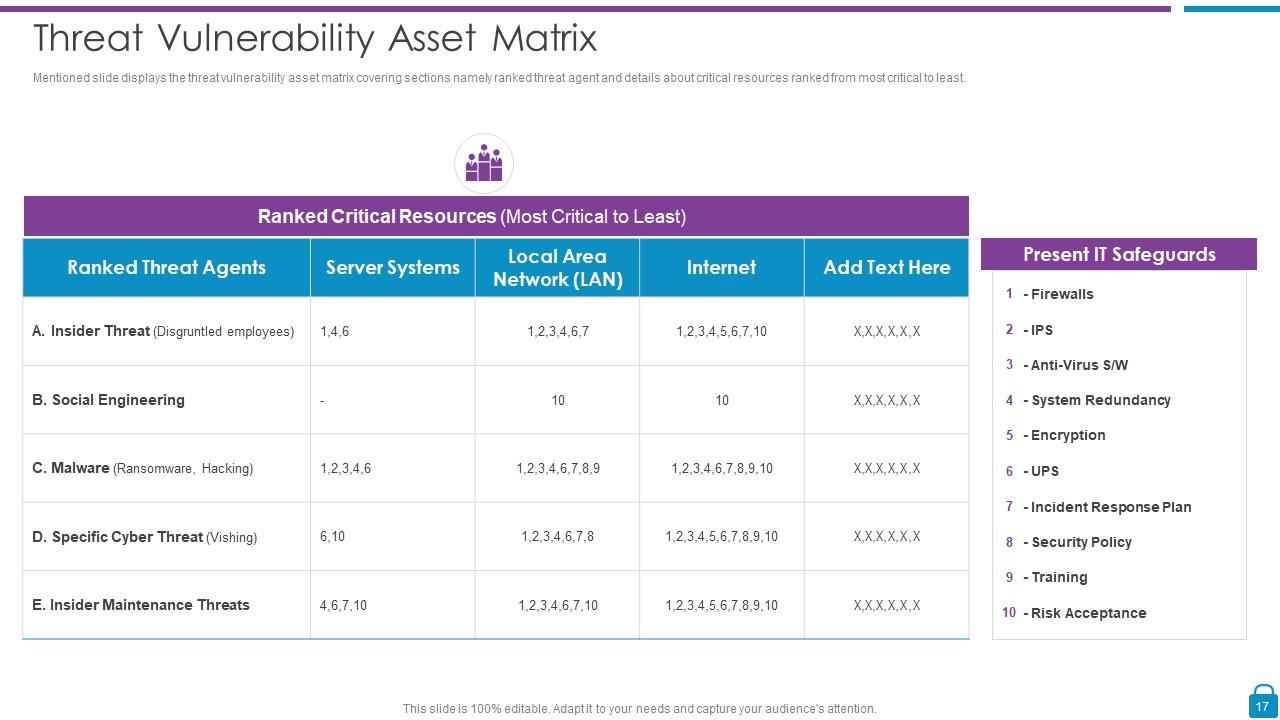
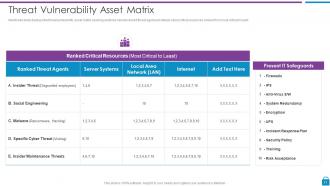
Slide 17: This slide represents threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources.
Slide 18: This slide shows Summary- Existing Security Management Capabilities.
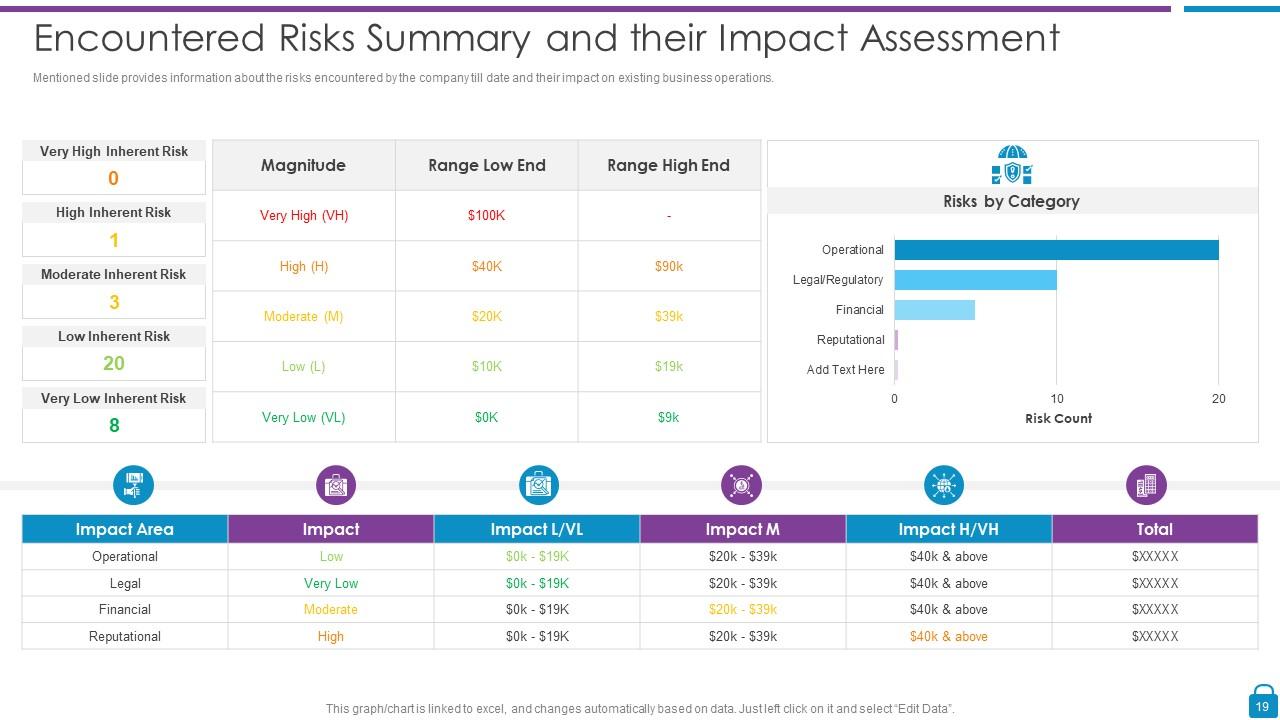
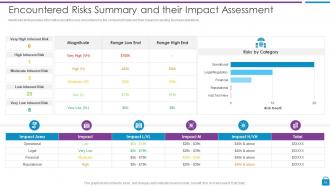
Slide 19: This slide presents Encountered Risks Summary and their Impact Assessment.
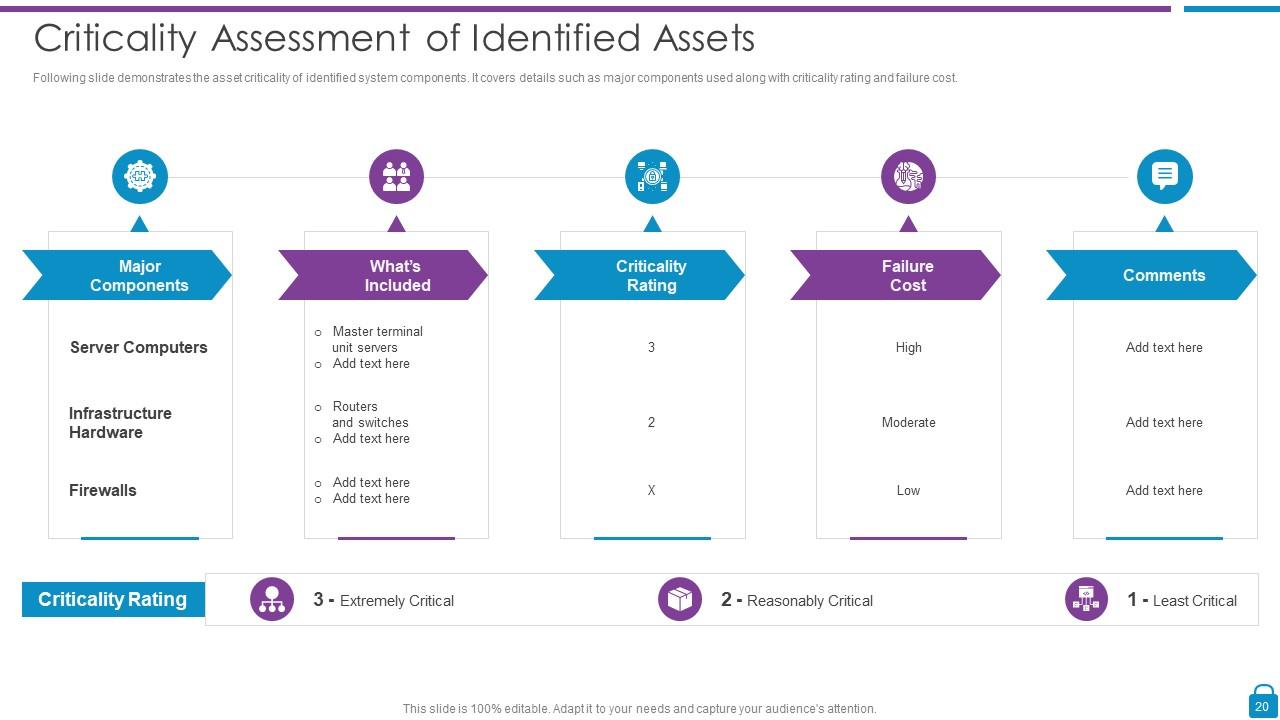
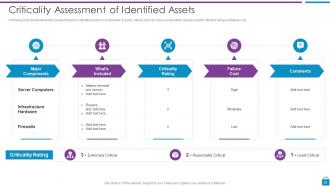
Slide 20: This slide shows asset criticality of identified system components.
Slide 21: This slide highlights title for topics that are to be covered next in the template.
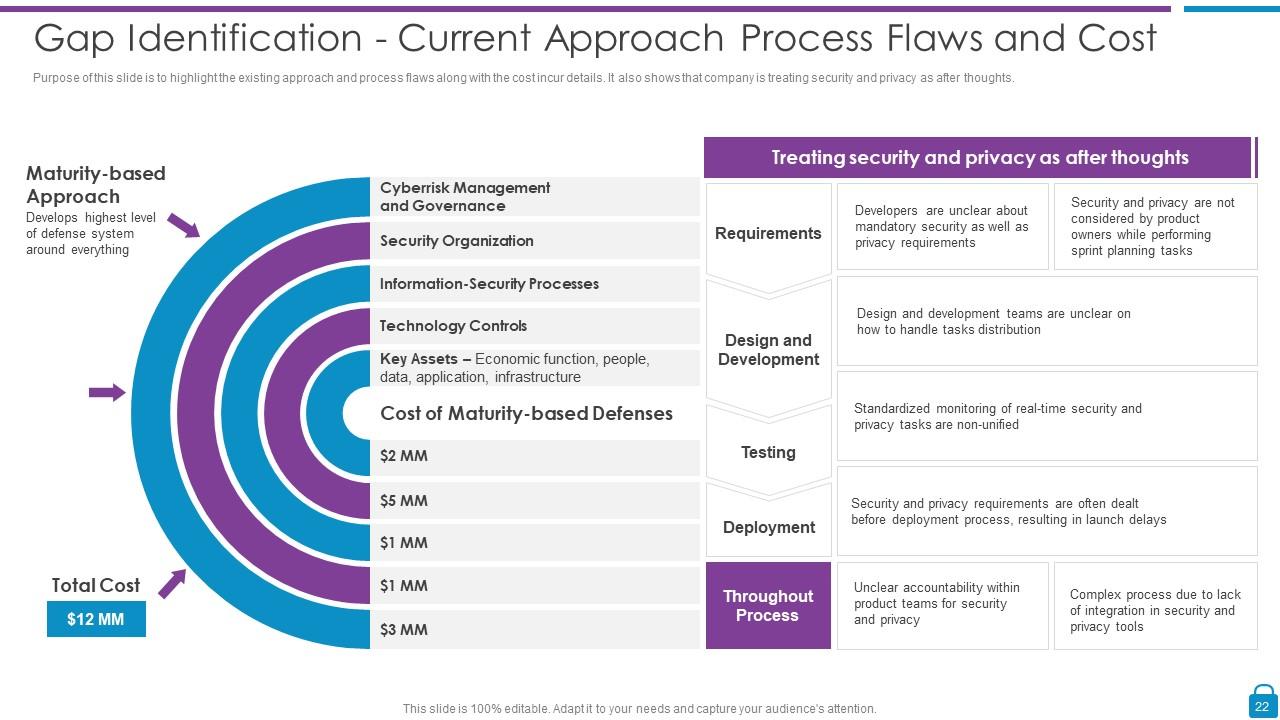
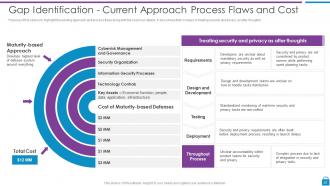
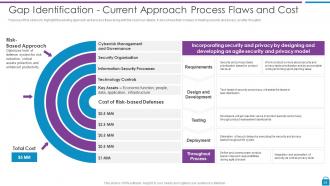
Slide 22: This slide represents Gap Identification - Current Approach Process Flaws and Cost.
Slide 23: This slide highlights title for topics that are to be covered next in the template.
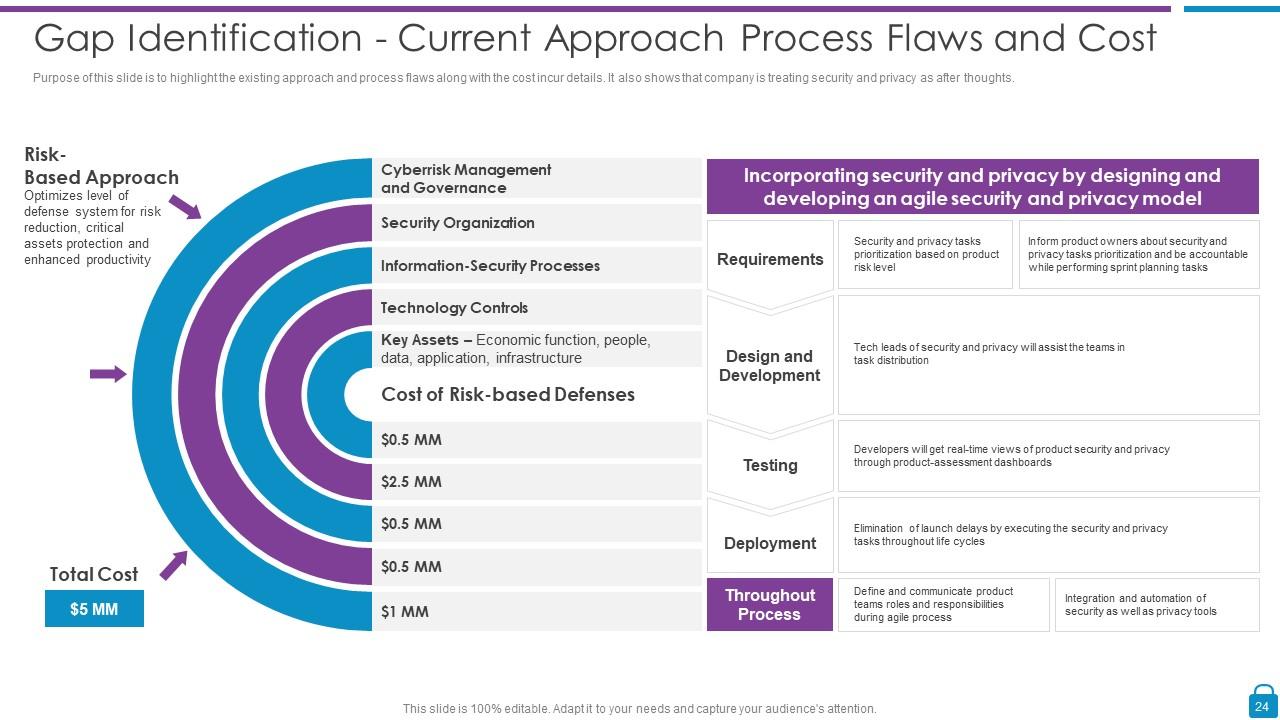
Slide 24: This slide presents risk-based approach and process efficiency along with the cost incur details.
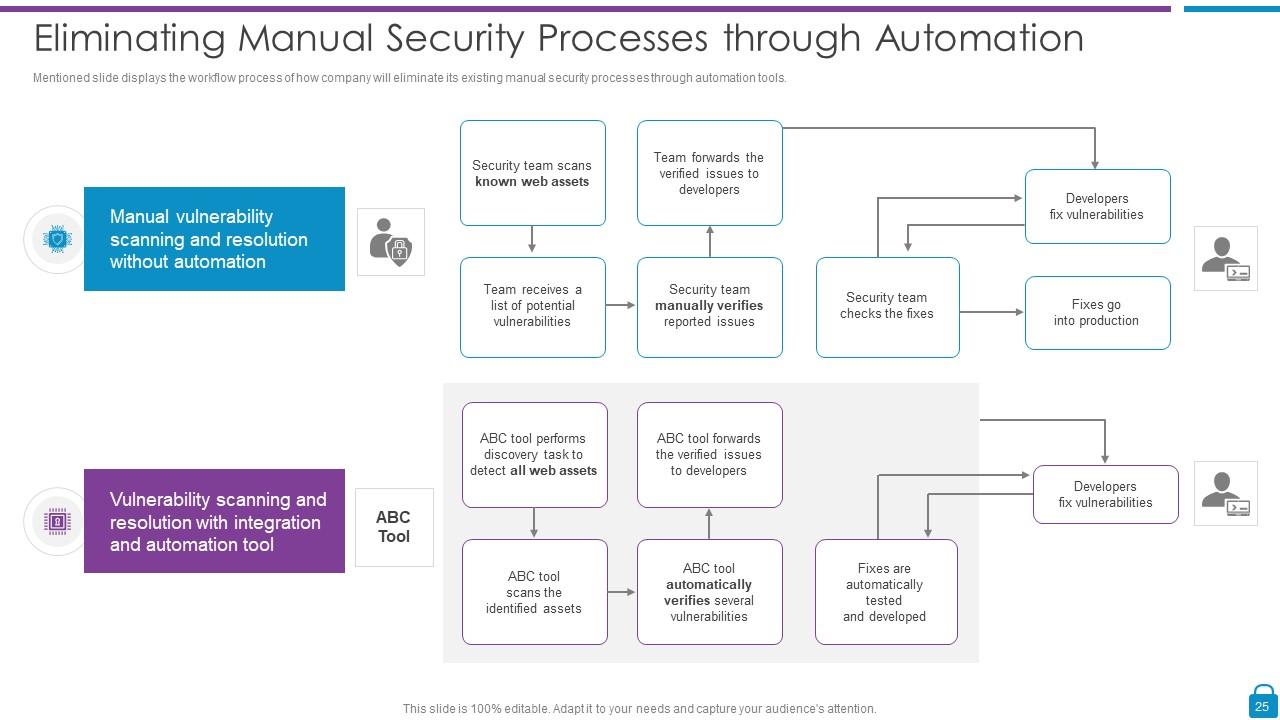
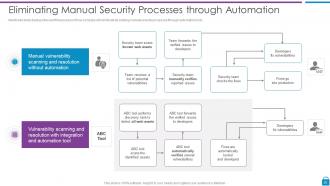
Slide 25: This slide shows Eliminating Manual Security Processes through Automation.
Slide 26: This slide highlights title for topics that are to be covered next in the template.
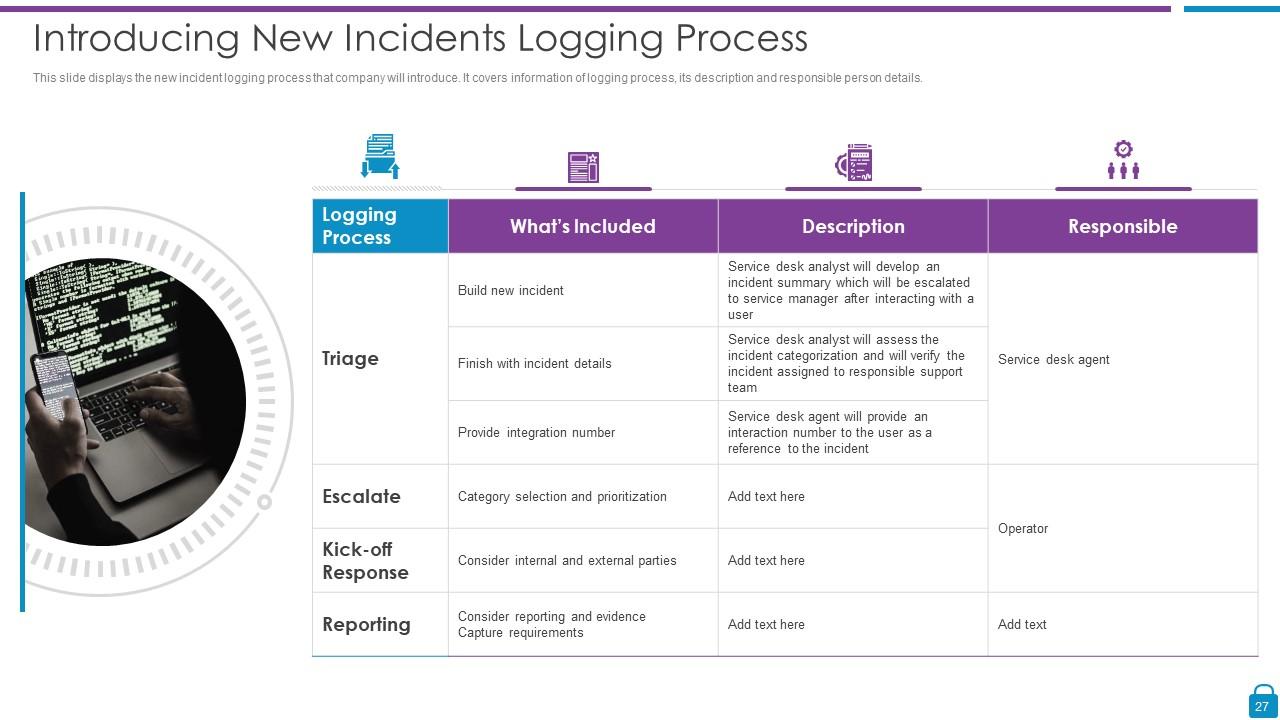
Slide 27: This slide represents the new incident logging process that company will introduce.
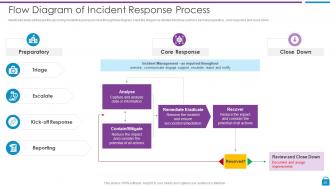
Slide 28: This slide shows upcoming incident response process through flow diagram.
Slide 29: This slide highlights title for topics that are to be covered next in the template.
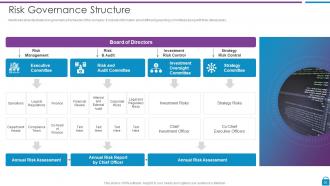
Slide 30: This slide shows risk governance framework of the company.
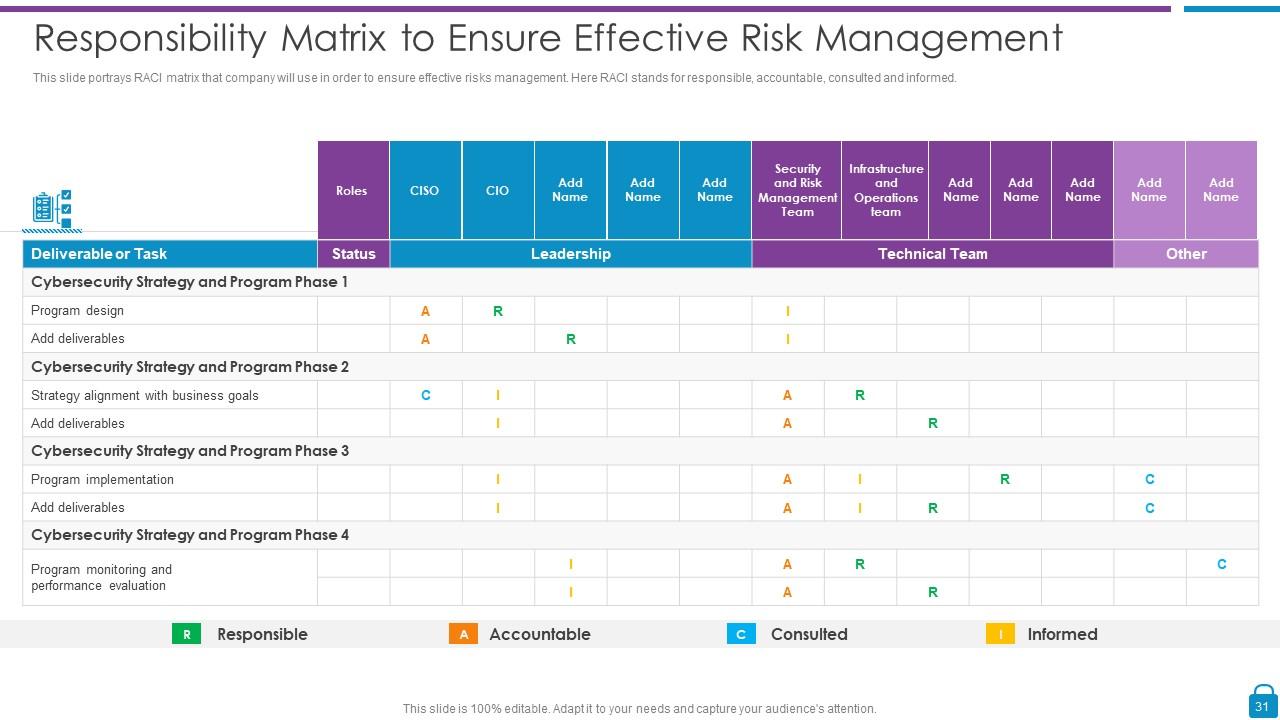
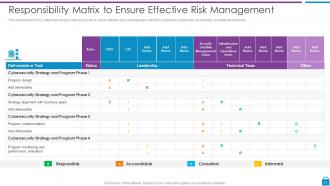
Slide 31: This slide displays RACI matrix that company will use in order to ensure effective risks management.
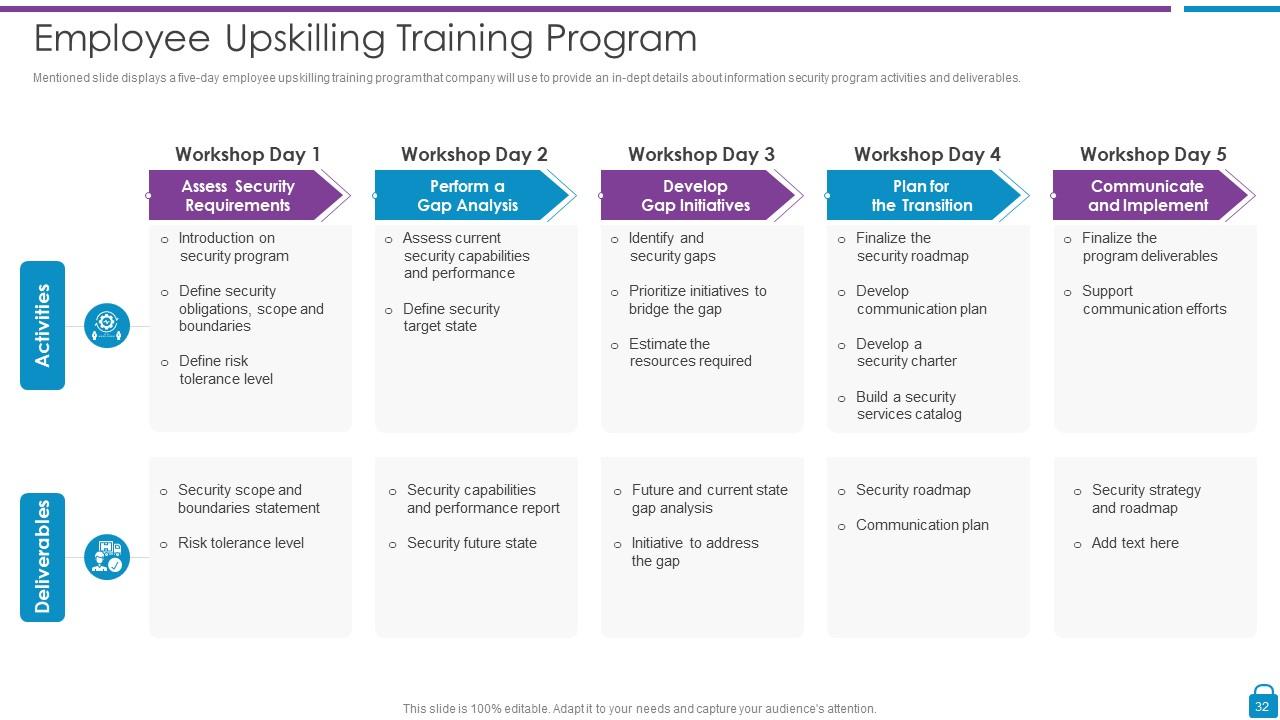
Slide 32: This slide represents five-day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables.
Slide 33: This slide highlights title for topics that are to be covered next in the template.
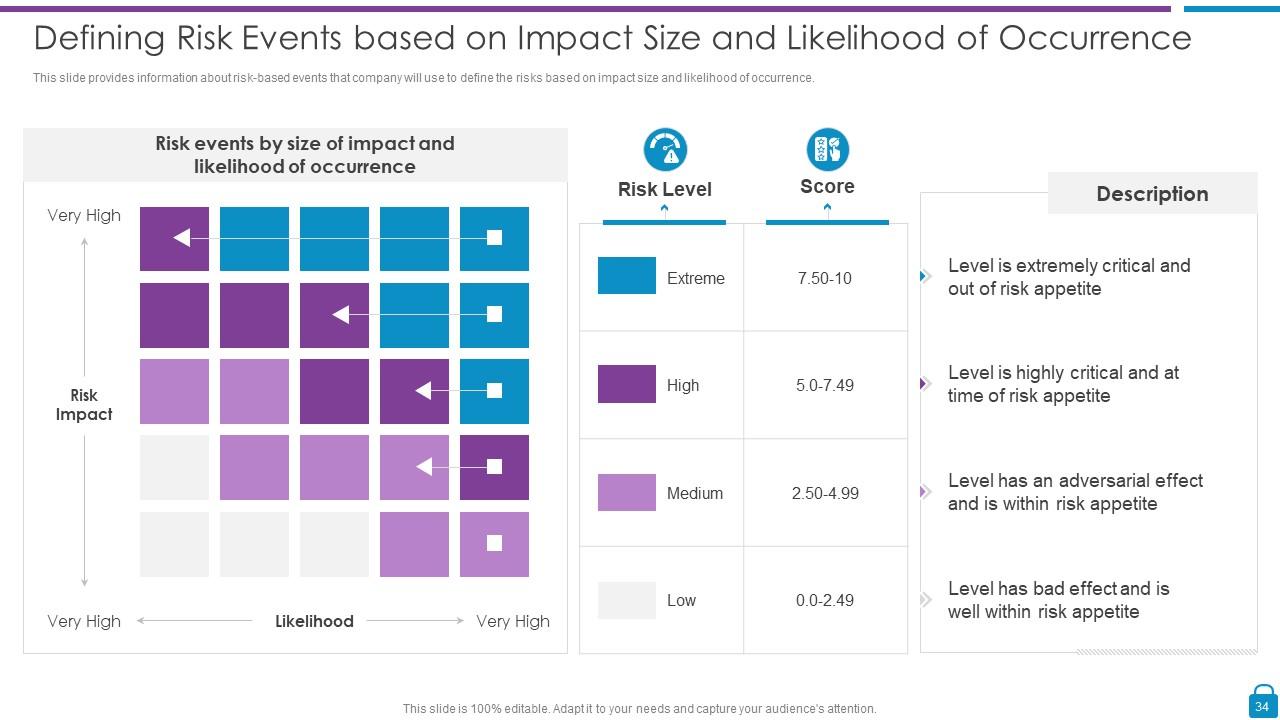
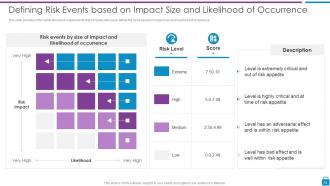
Slide 34: This slide presents Defining Risk Events based on Impact Size and Likelihood of Occurrence.
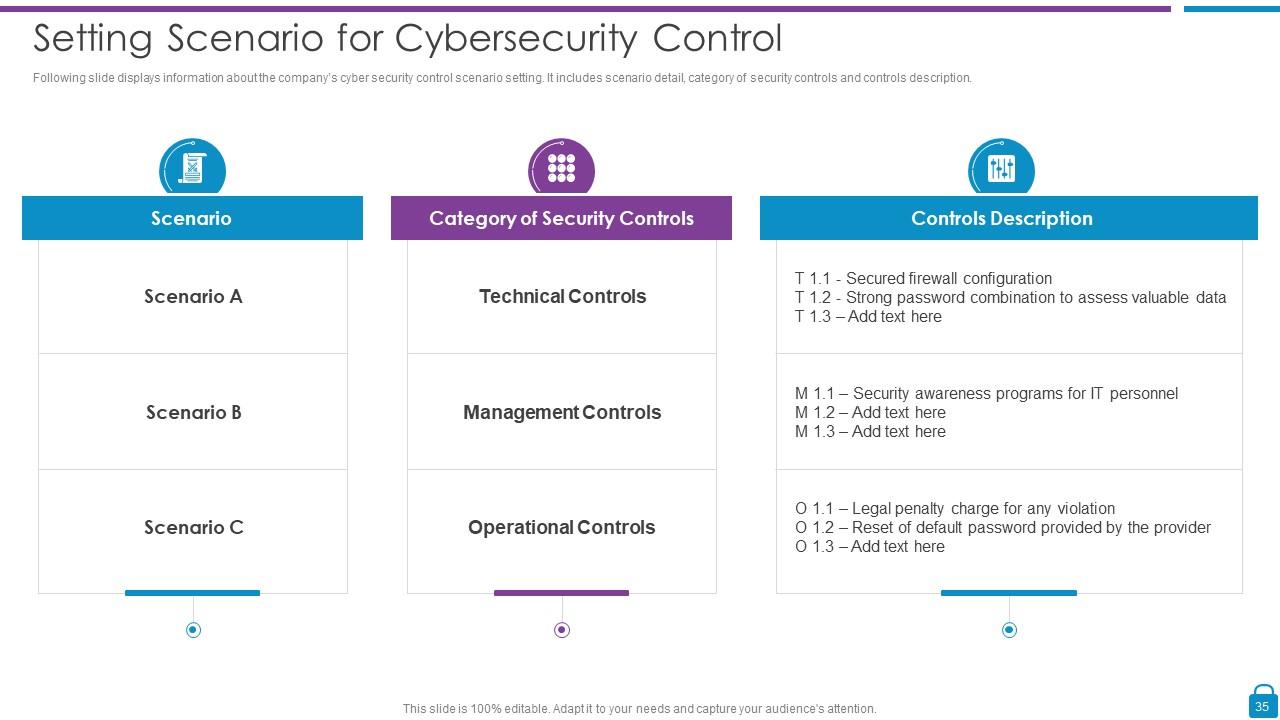
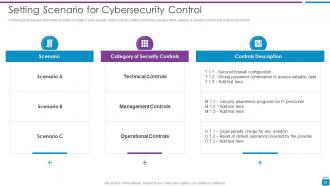
Slide 35: This slide shows information about the company’s cyber security control scenario setting.
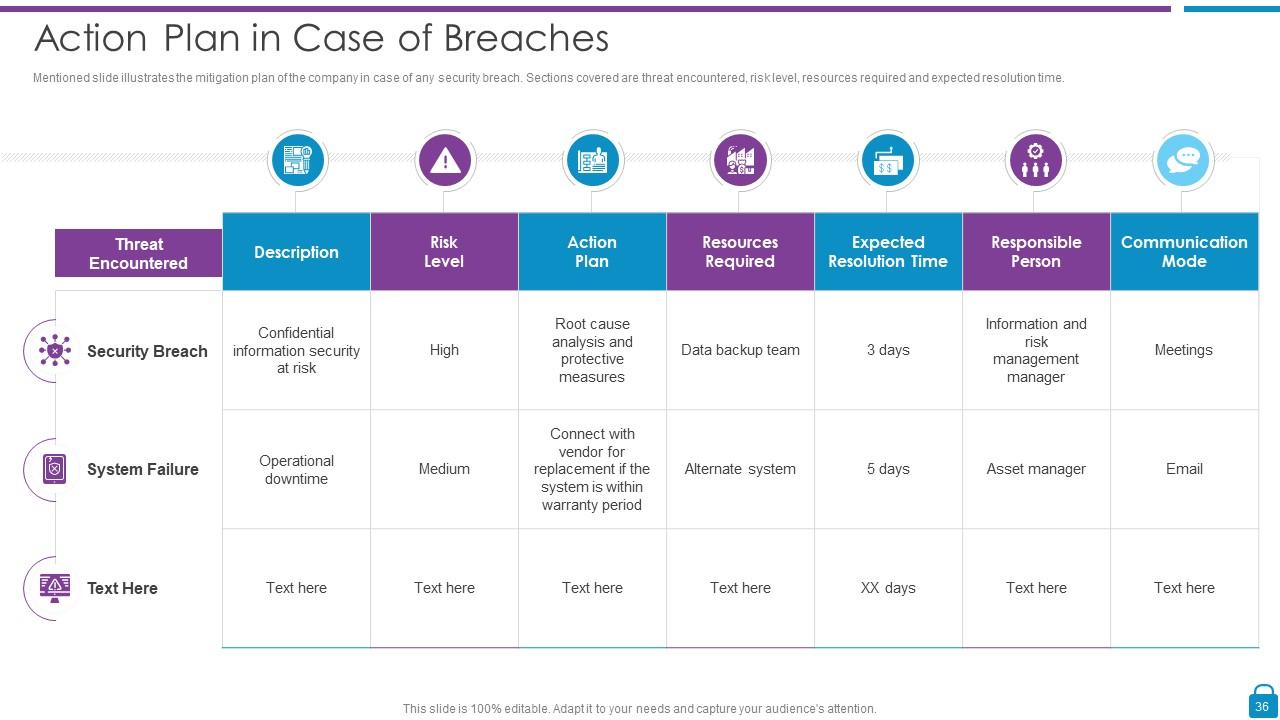
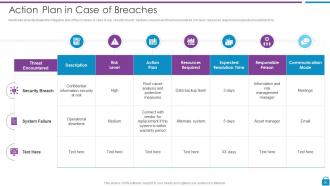
Slide 36: This slide displays mitigation plan of the company in case of any security breach.
Slide 37: This slide highlights title for topics that are to be covered next in the template.
Slide 38: This slide shows Checklist for Effectively Managing Asset Security.
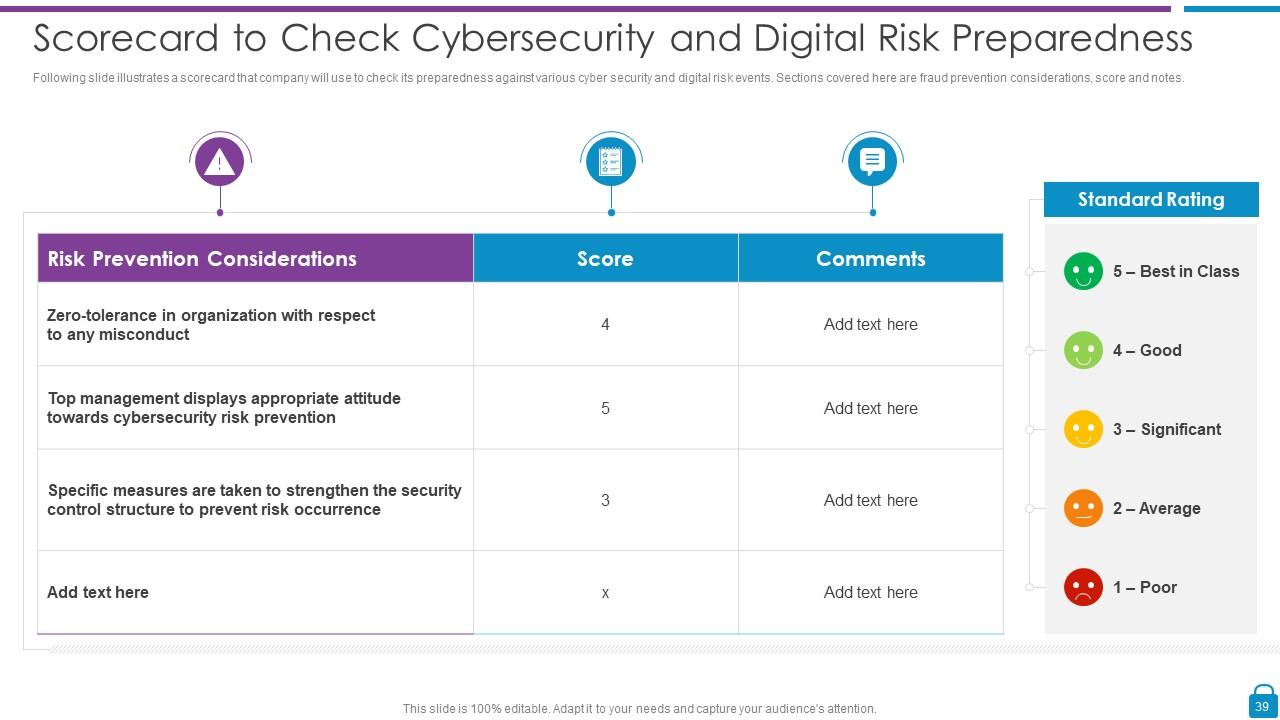
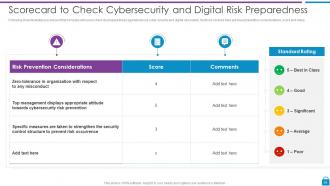
Slide 39: This slide presents Scorecard to Check Cybersecurity and Digital Risk Preparedness.
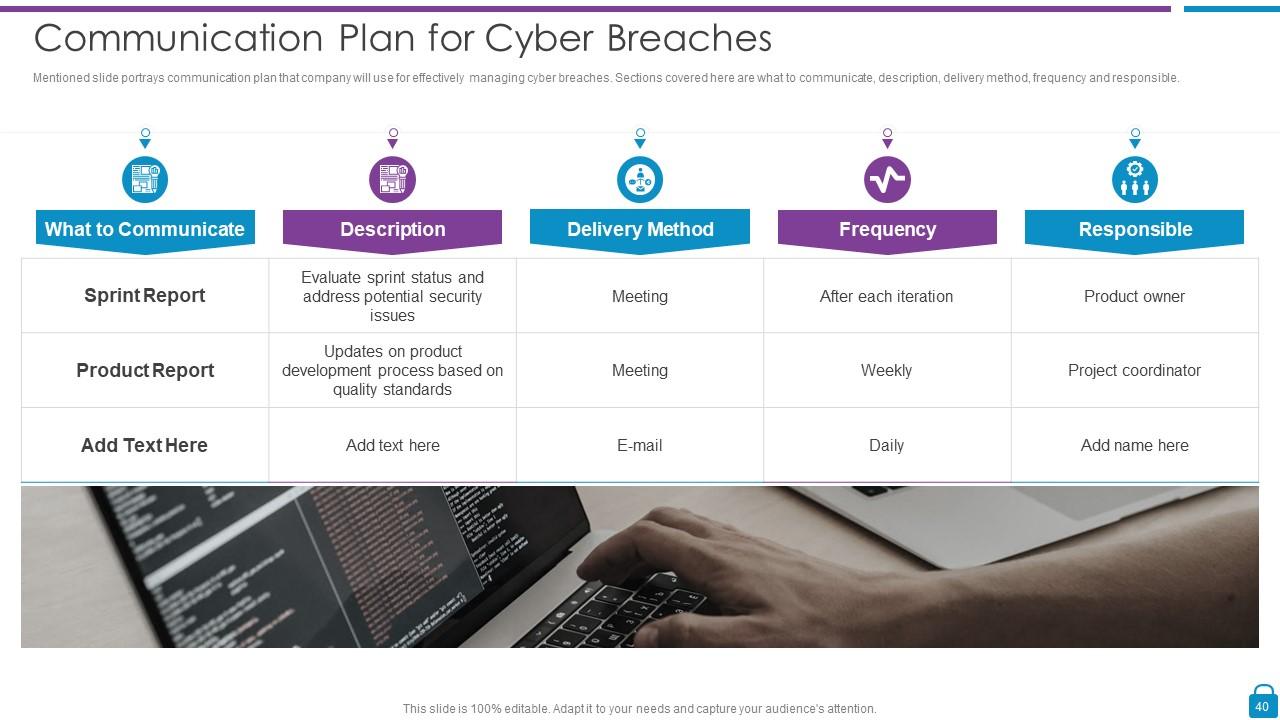
Slide 40: This slide shows communication plan that company will use for effectively managing cyber breaches.
Slide 41: This slide highlights title for topics that are to be covered next in the template.
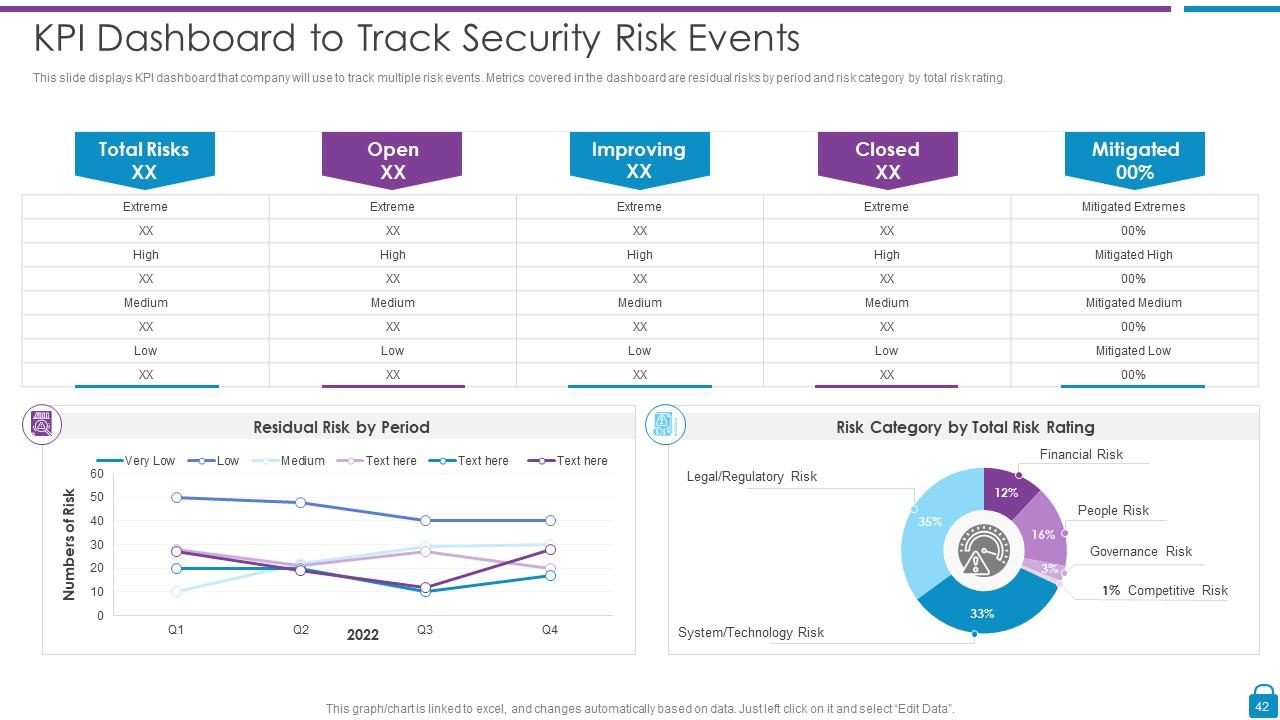
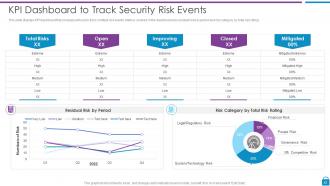
Slide 42: This slide displays KPI dashboard that company will use to track multiple risk events.
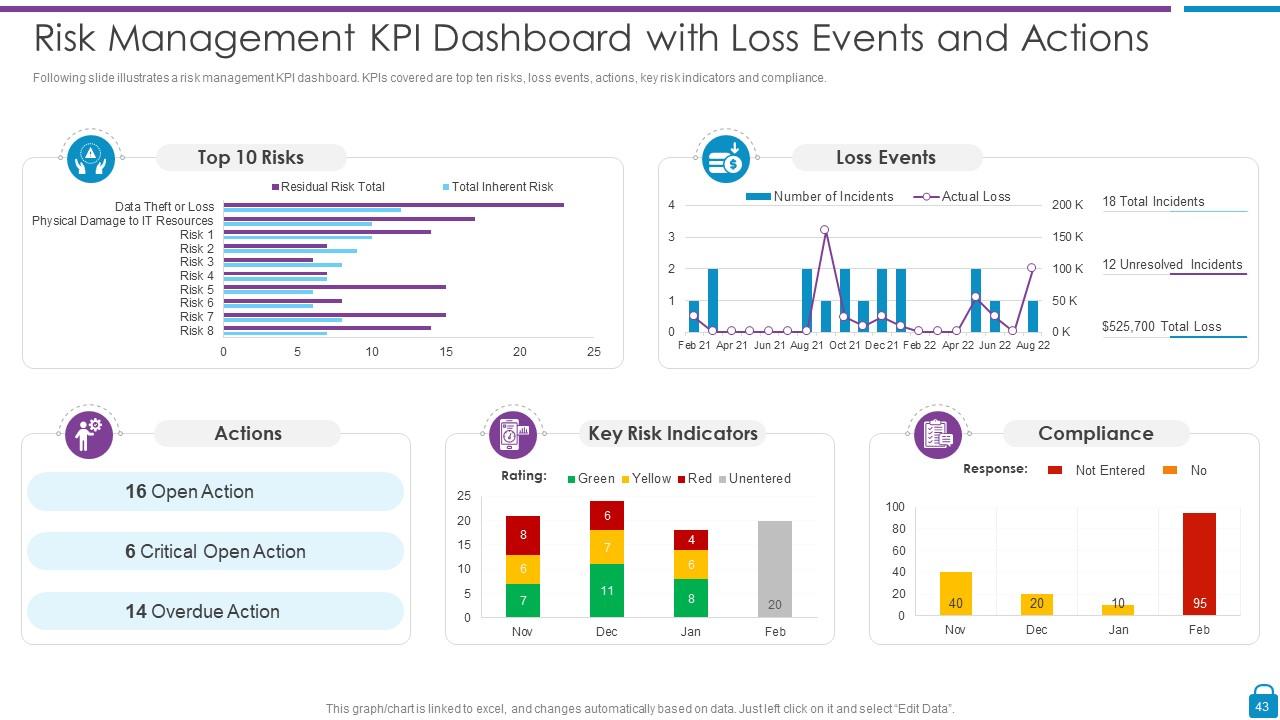
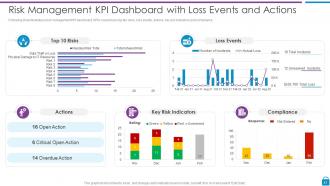
Slide 43: This slide shows Risk Management KPI Dashboard with Loss Events and Actions.
Slide 44: This slide displays Icons for Risk-Based Methodology to Cyber and Information Security.
Slide 45: This slide is titled as Additional Slides for moving forward.
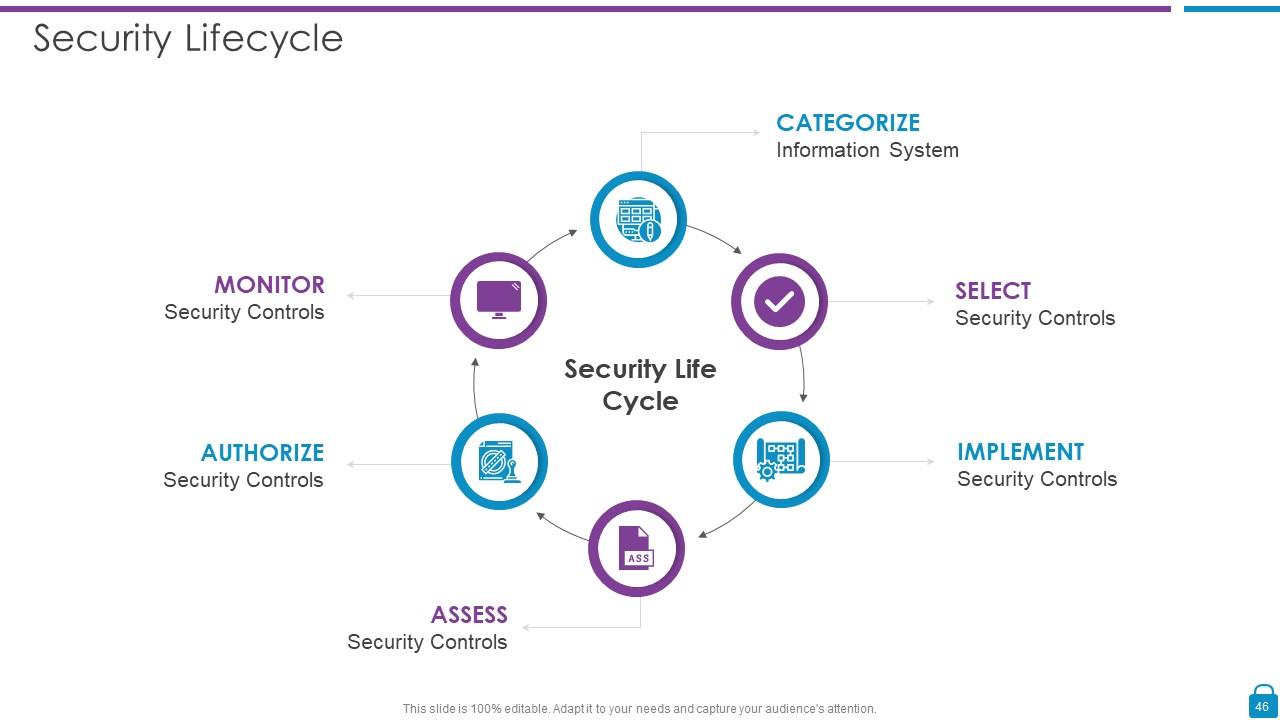
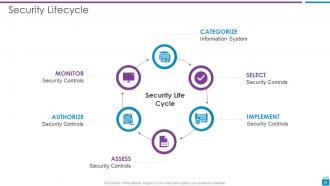
Slide 46: This slide displays Security Life Cycle describing- Information System, Security Controls, etc.
Slide 47: This is a Timeline slide. Show data related to time intervals here.
Slide 48: This is an Idea Generation slide to state a new idea or highlight information, specifications etc.
Slide 49: This slide contains Puzzle with related icons and text.
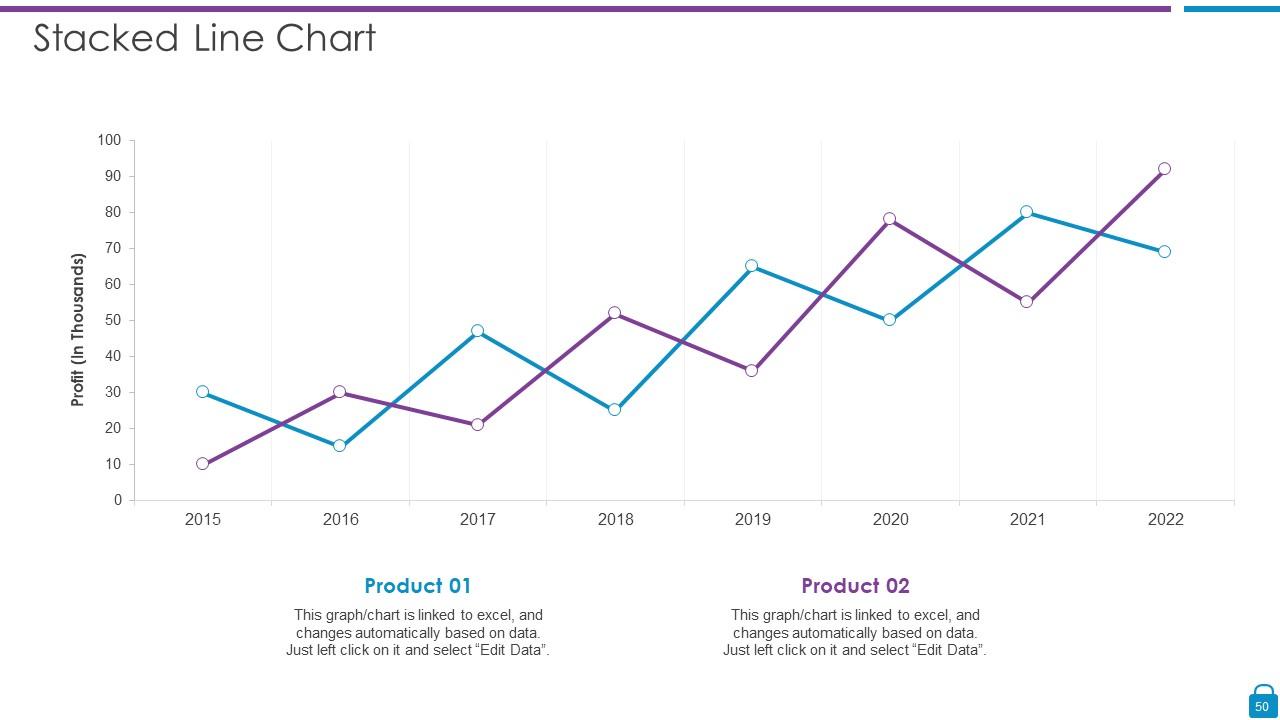
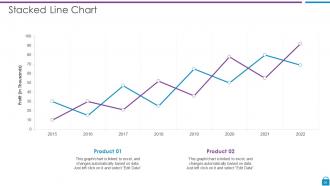
Slide 50: This slide represents Stacked line chart with two products comparison.
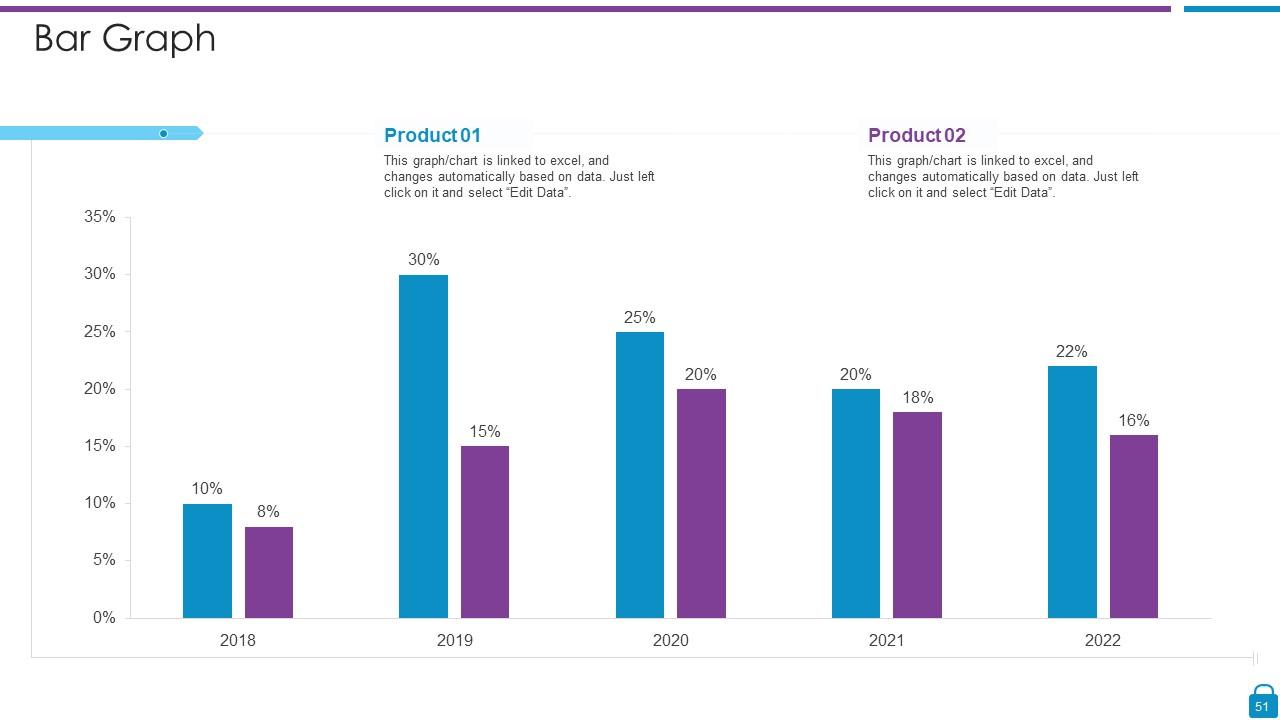
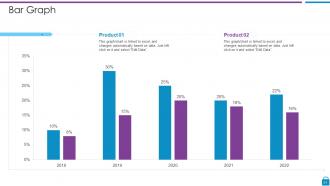
Slide 51: This slide presents Bar chart with two products comparison.
Slide 52: This is Our Goal slide. State your firm's goals here.
Slide 53: This slide provides 30 60 90 Days Plan with text boxes.
Slide 54: This is a Thank You slide with address, contact numbers and email address.
Risk Based Methodology To Cyber And Information Security Powerpoint Presentation Slides with all 59 slides:
Use our Risk Based Methodology To Cyber And Information Security Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Definitely a time saver! Predesigned and easy-to-use templates just helped me put together an amazing presentation.
-
Unique design & color.