Implementing Cyber Security Incident Management Powerpoint Presentation Slides
Cyber security is essential to identify, record, and analyze cyber security threats instantaneously. Grab our professionally designed deck for Implementing cybersecurity incident management for a complete and comprehensive view of security issues within an IT infrastructure. It utilizes a combination of appliances, software systems, and human-driven investigation and analysis. Our Cyber attacks management PPT showcases the critical cyber security challenges faced by the enterprise and includes its management process. It further contains a response checklist, best practices to manage cyber security risks, and its events flow diagram. It also covers a cyber security incident response plan, and critical lessons the incident management team learned after mitigating cyber security incidents. Lastly, our Phishing attack administration module covers the roles and responsibilities of the cyber security team, the budget allocated for it, and its impact on business operations. Get access to this powerful template now
Cyber security is essential to identify, record, and analyze cyber security threats instantaneously. Grab our professionall..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver an informational PPT on various topics by using this Implementing Cyber Security Incident Management Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with sixty nine slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Implementing Cyber Security Incident Management. Commence by stating Your company name.
Slide 2: This slide depicts the Agenda of the presentation.
Slide 3: This slide incorporates the Table of Contents.
Slide 4: This slide elucidates the Title for the Topics to be covered in the upcoming template.
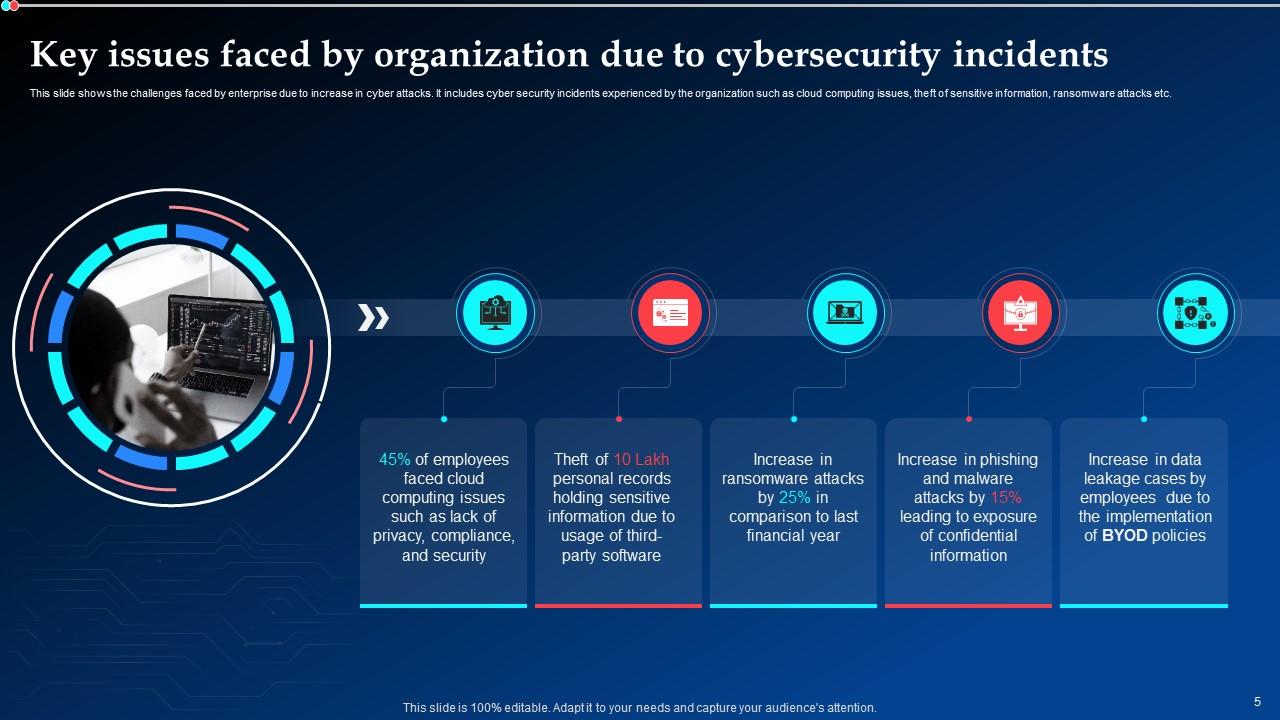
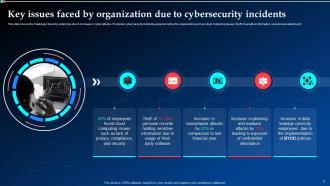
Slide 5: This slide shows the challenges faced by enterprise due to increase in cyber attacks.
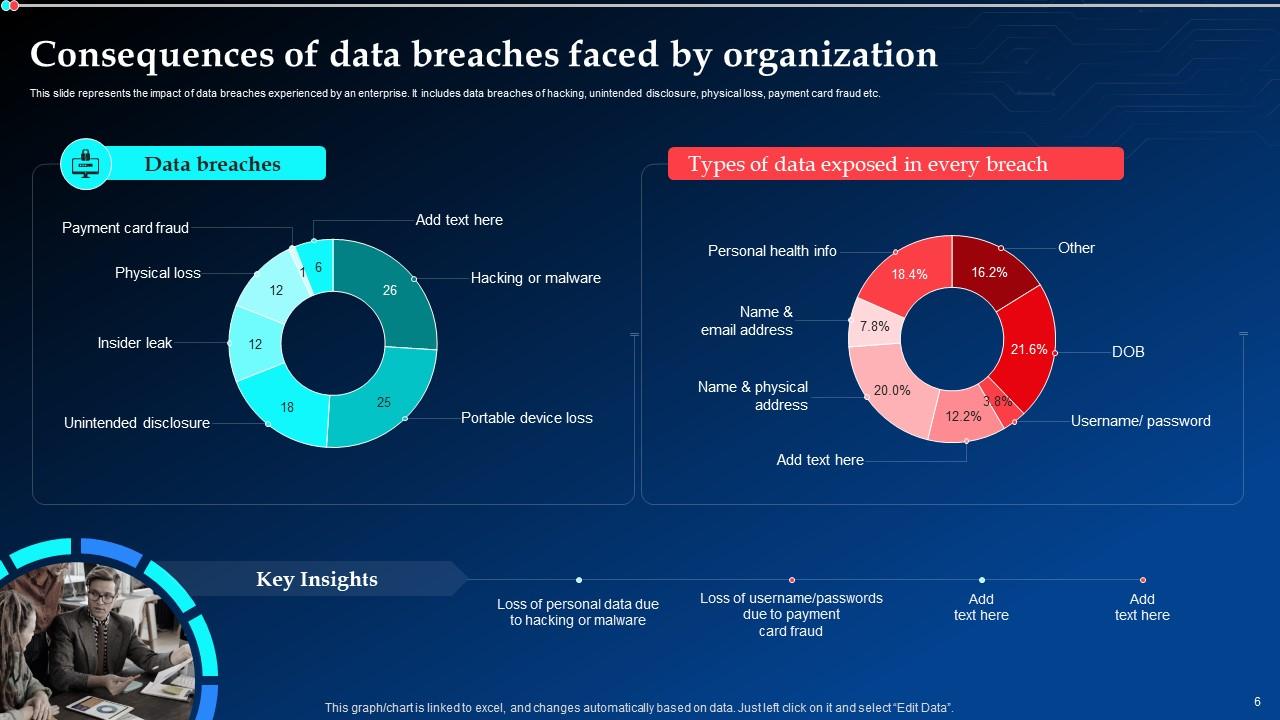
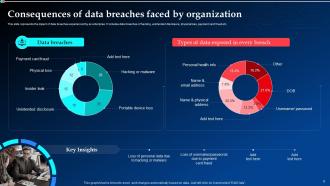
Slide 6: This slide represents the consequences of data breaches experienced by an enterprise.
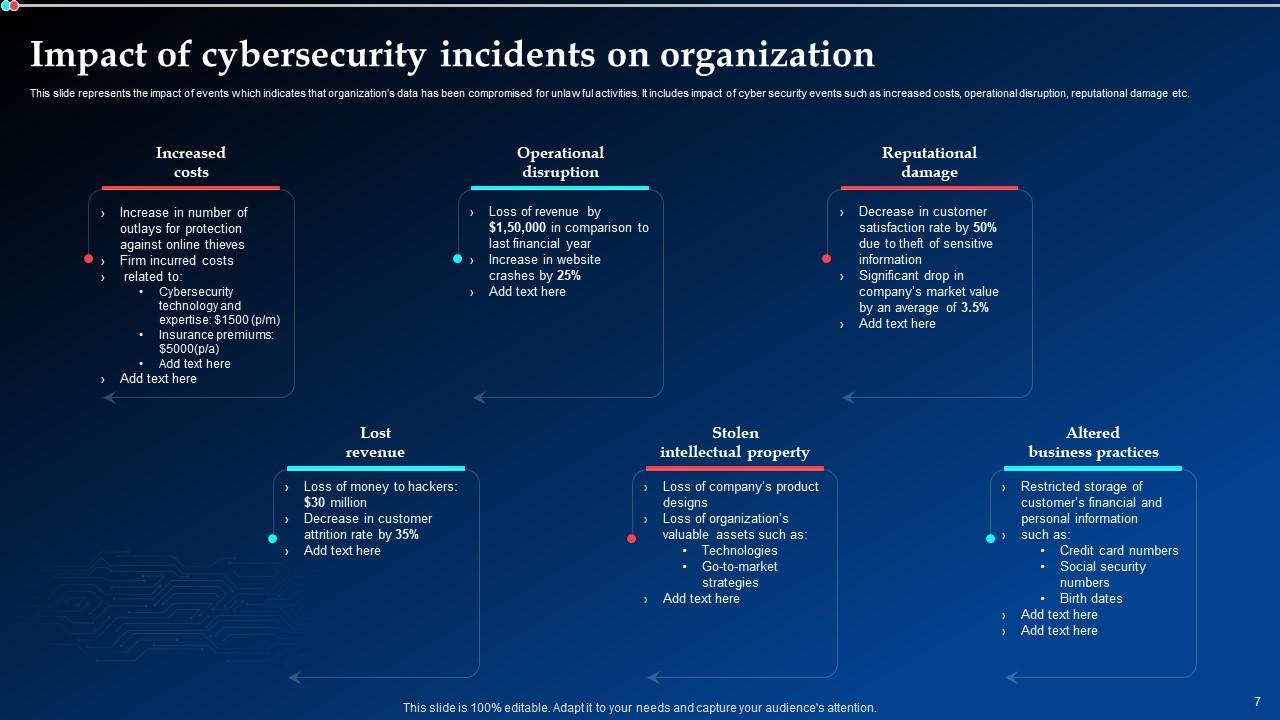
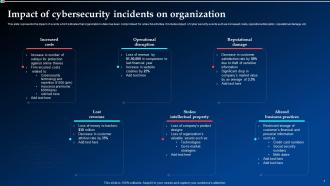
Slide 7: This slide highlights the impact of events which indicates that organization’s data has been compromised for unlawful activities.
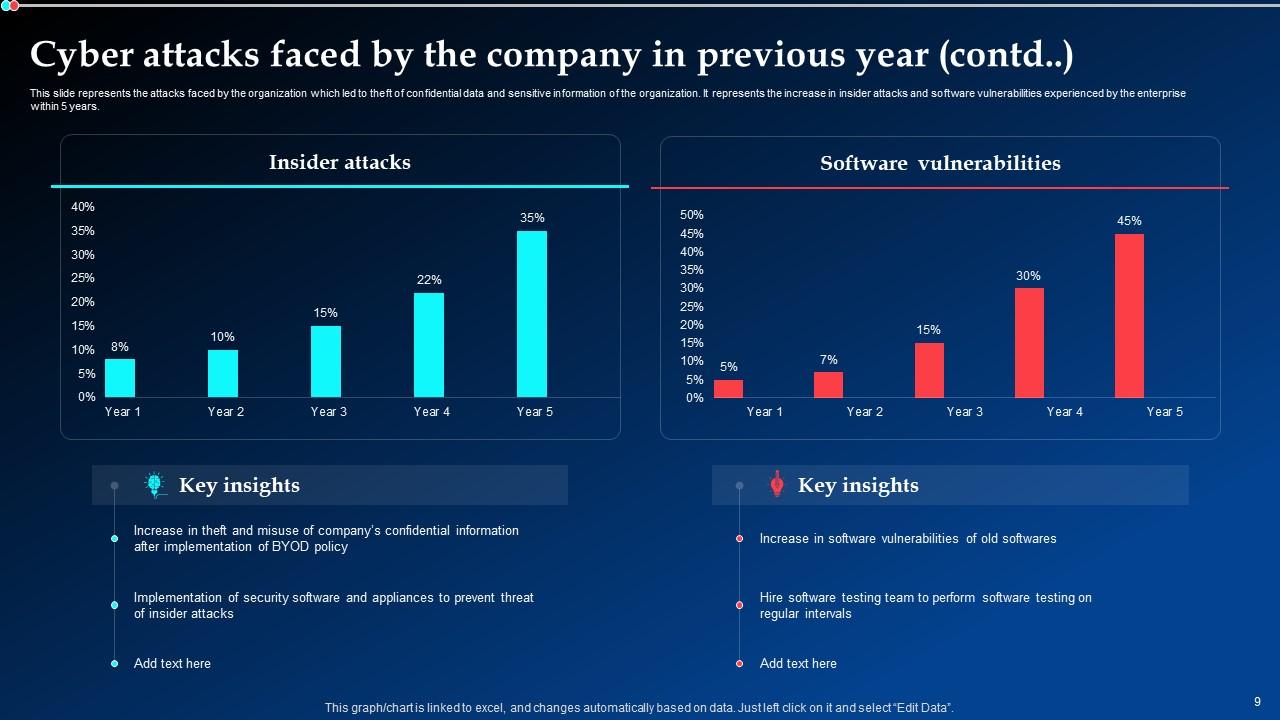
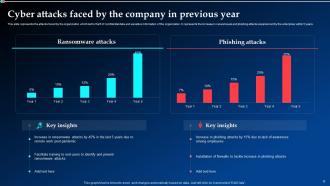
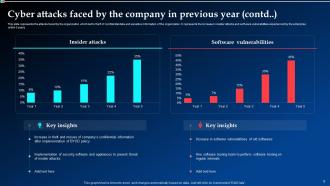
Slide 8: This slide illustrates the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization.
Slide 9: This is yet another slide continuing the attacks faced by the organization.
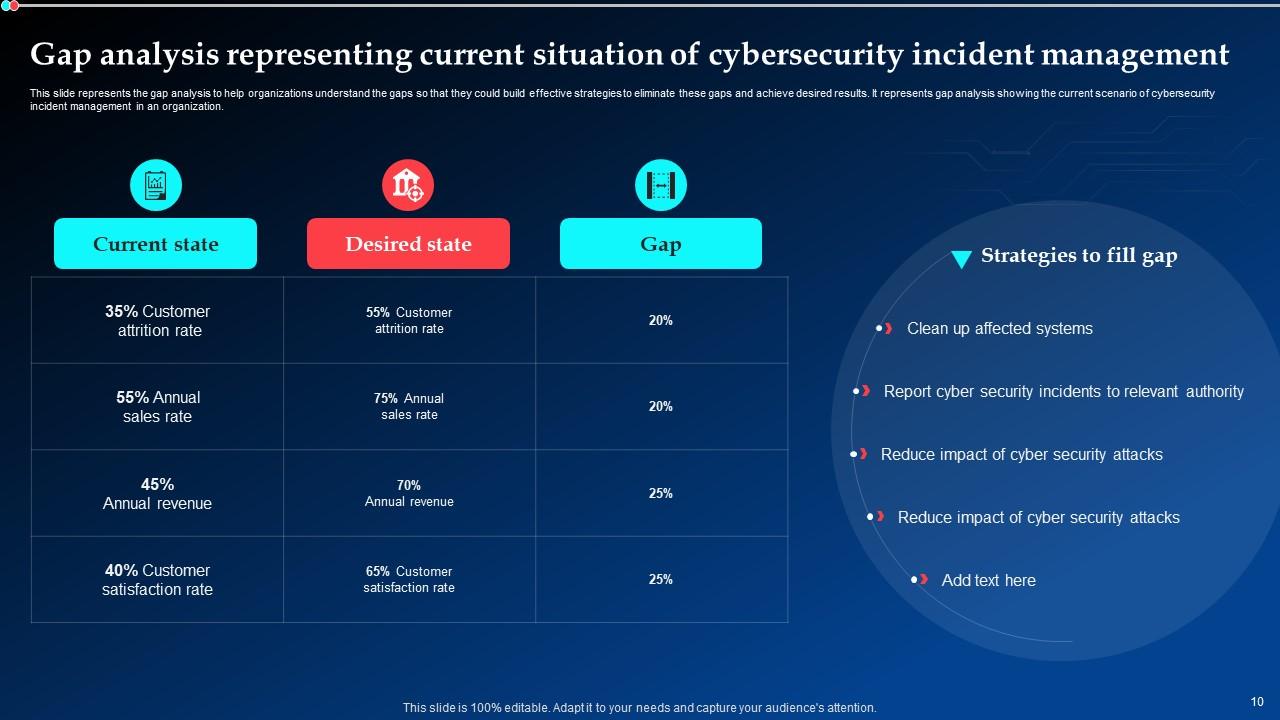
Slide 10: This slide reveals the gap analysis to help organizations understand the gaps for building effective strategies to eliminate these gaps and achieve desired results.
Slide 11: This slide presents the Heading for the Contents to be discussed next.
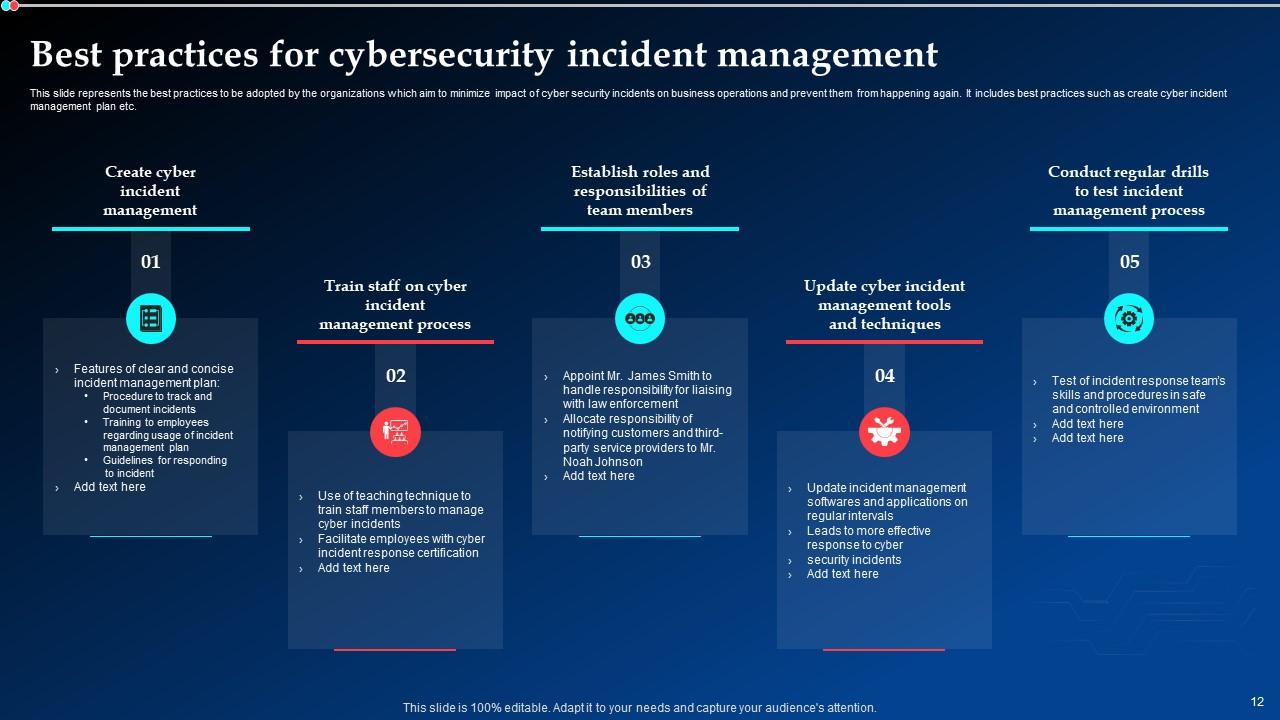
Slide 12: This slide exhibits the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again.
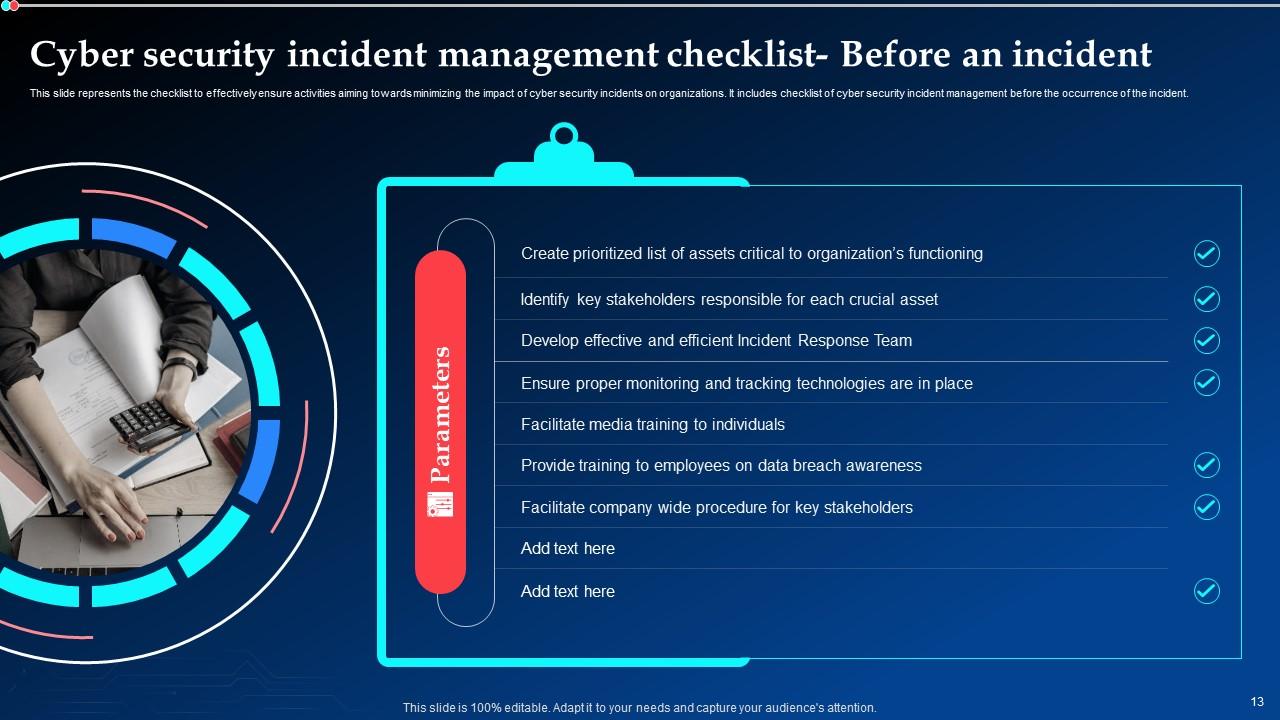
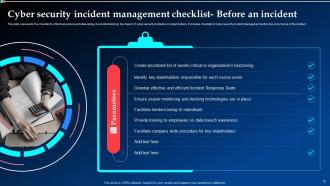
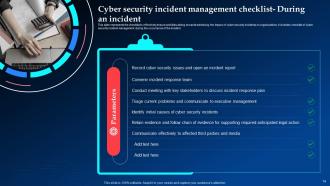
Slide 13: This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations.
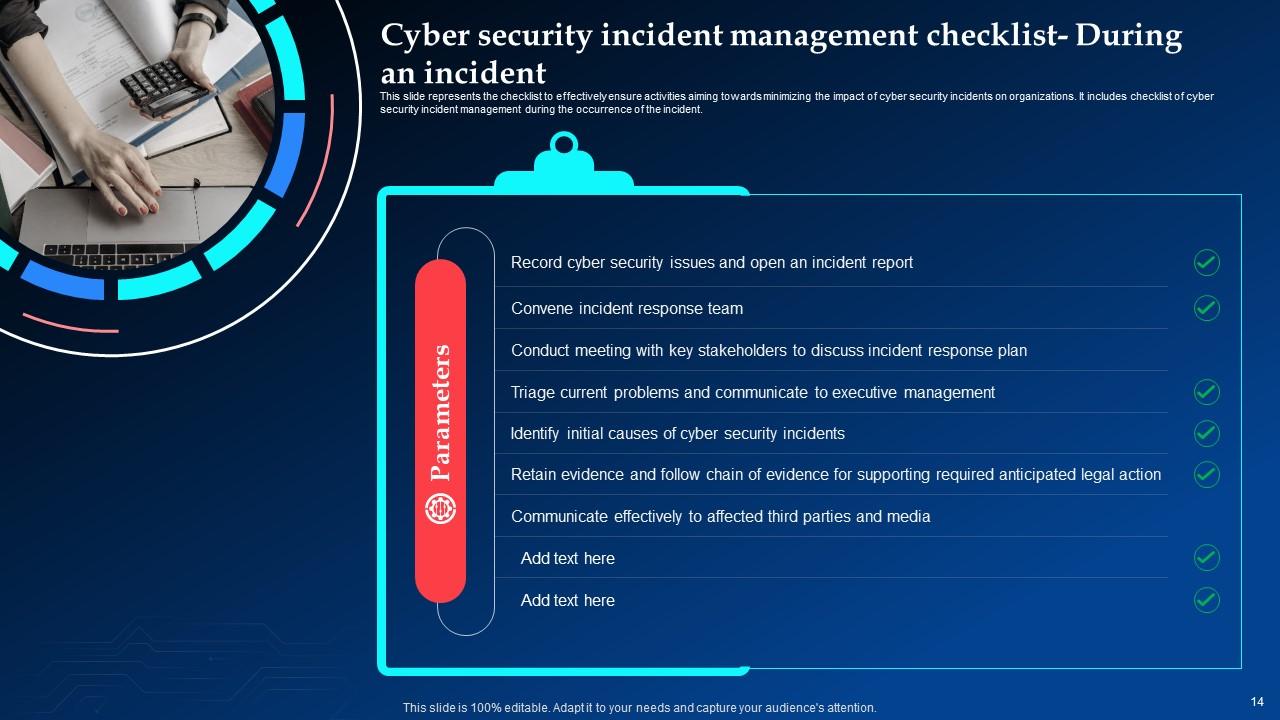
Slide 14: This slide elucidates the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations.
Slide 15: This slide shows the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents.
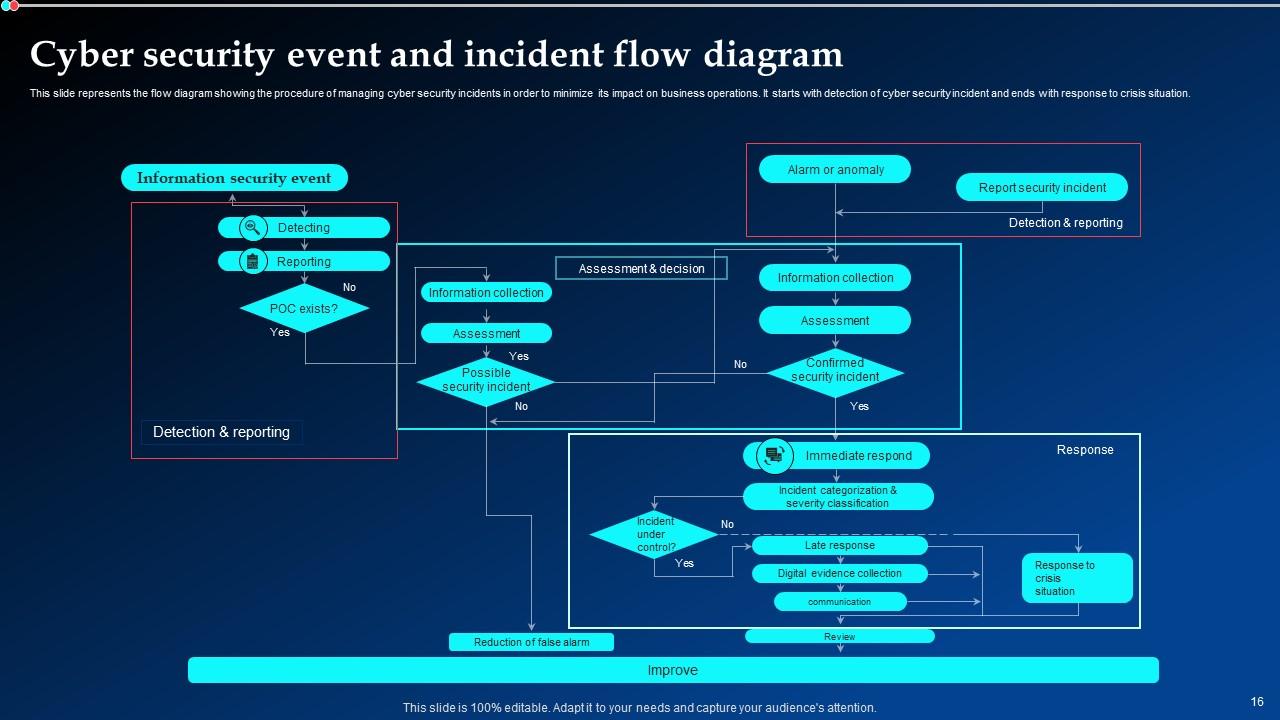
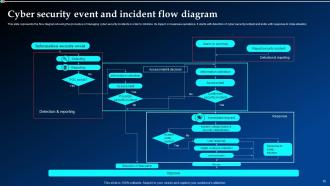
Slide 16: This slide illustrates the Cyber security event and incident flow diagram.
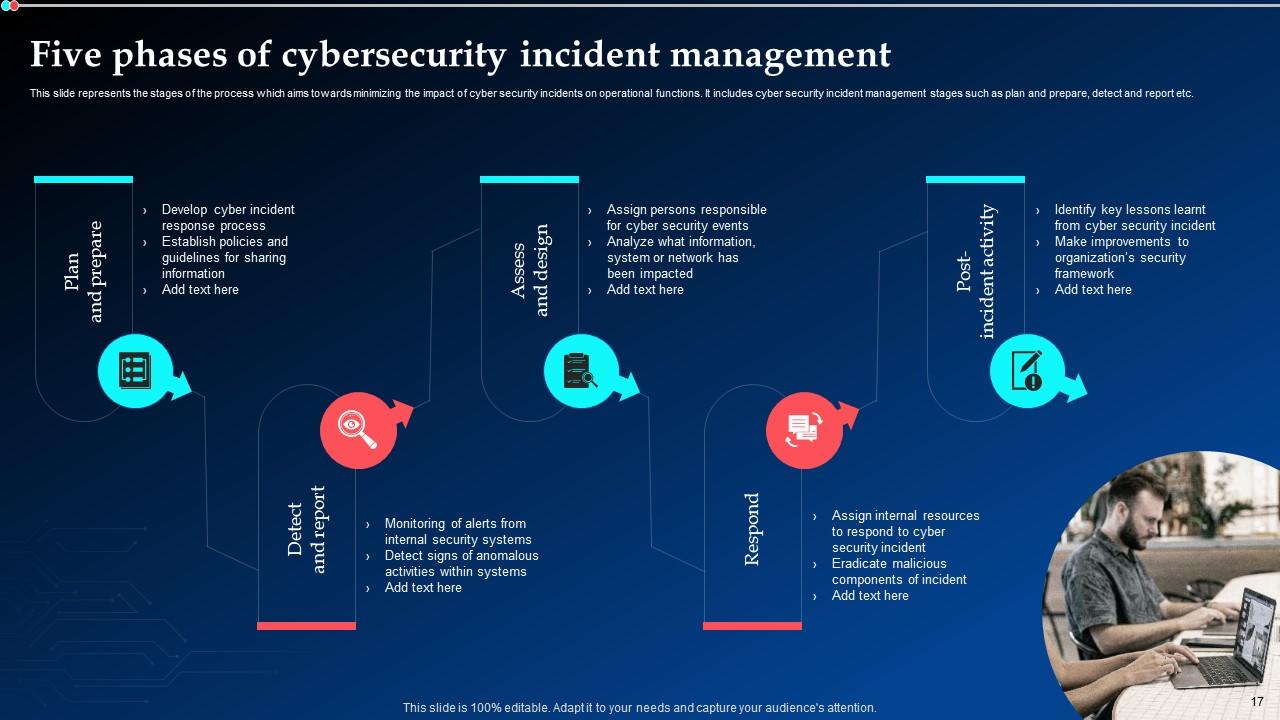
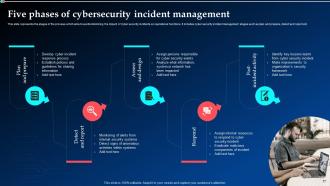
Slide 17: This slide states the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions.
Slide 18: This slide contains the Heading for the Ideas to be discussed further.
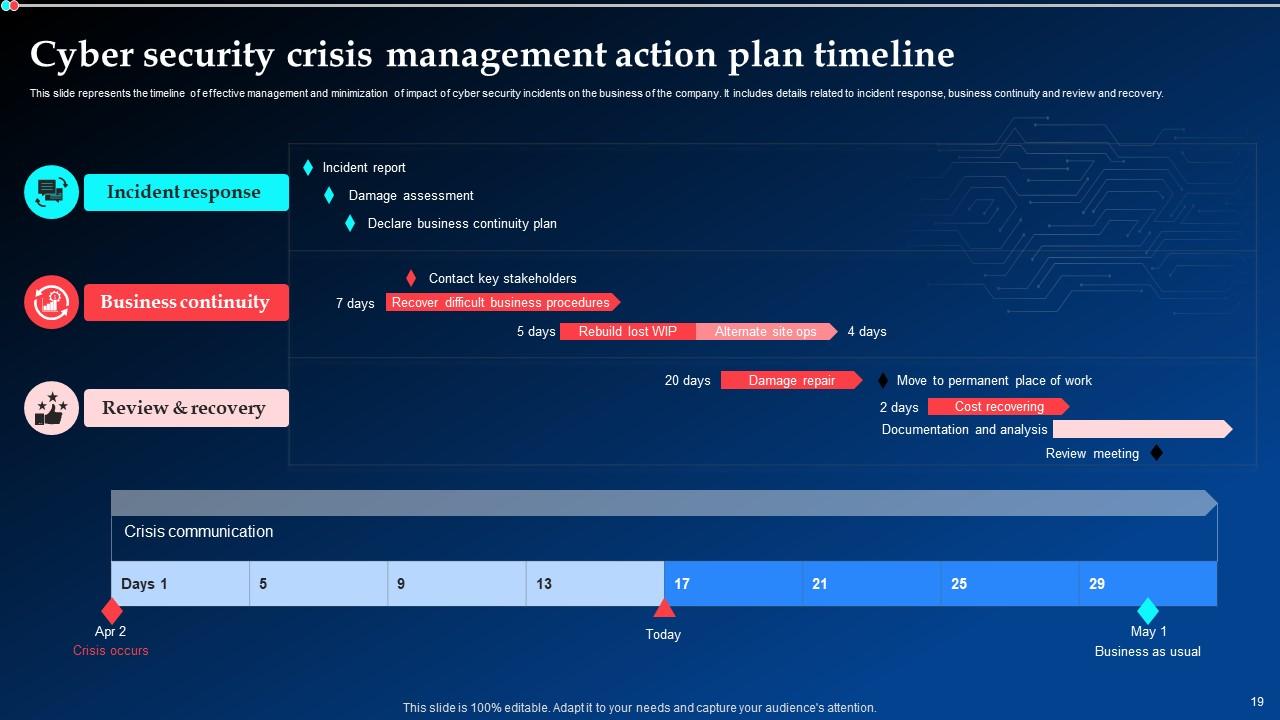
Slide 19: This slide reveals the timeline of effective management and minimization of impact of cyber security incidents on the company.
Slide 20: This slide elucidates the Title for the Topics to be covered in the forth-coming template.
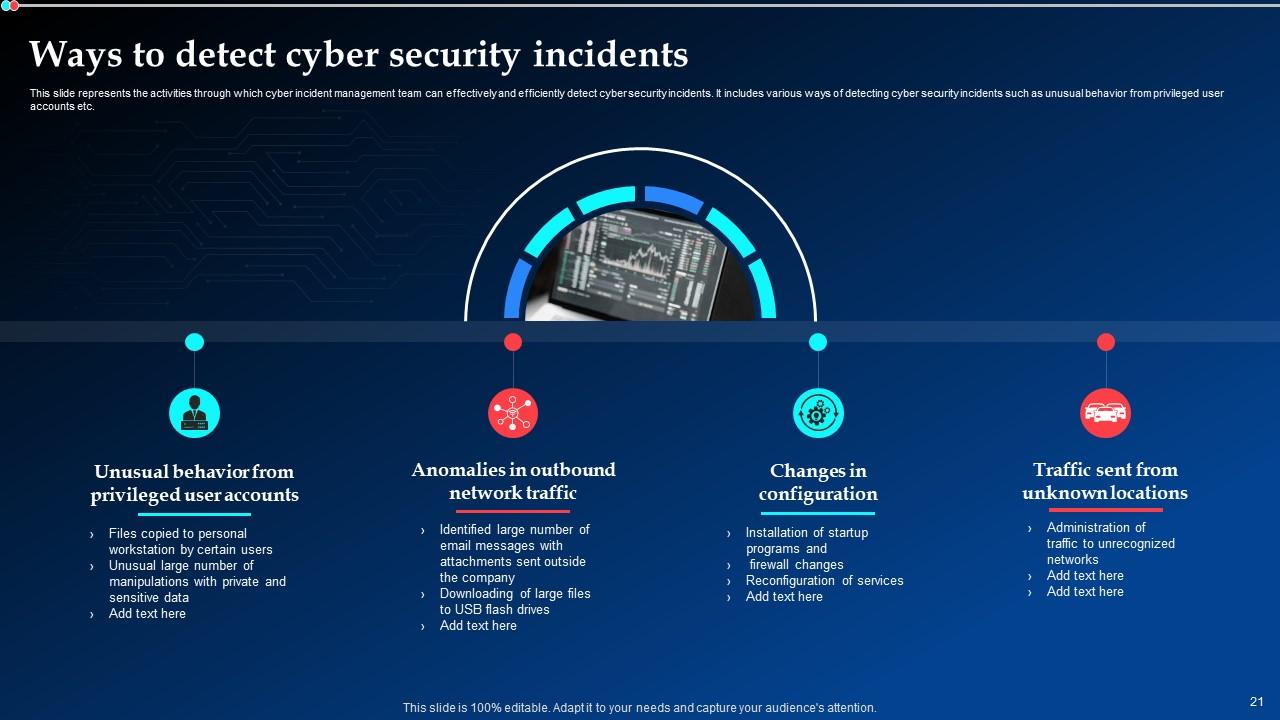
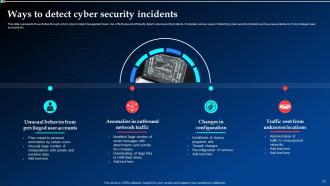
Slide 21: This slide showcases the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents.
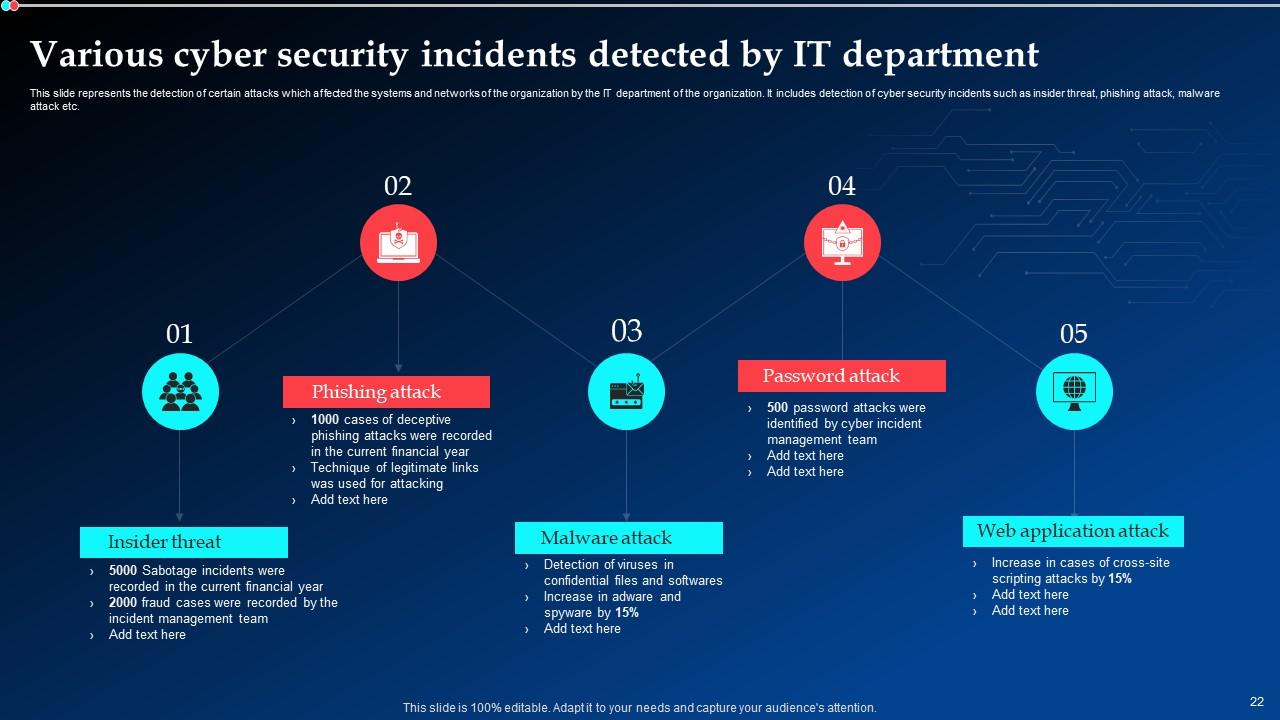
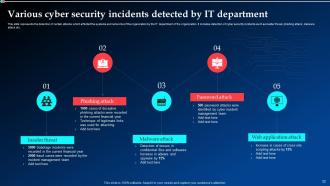
Slide 22: This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization.
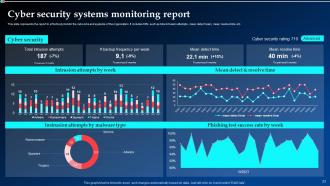
Slide 23: This slide illustrates the report to effectively monitor the networks and systems of the organization.
Slide 24: This slide exhibits the Heading for the Ideas to be covered further.
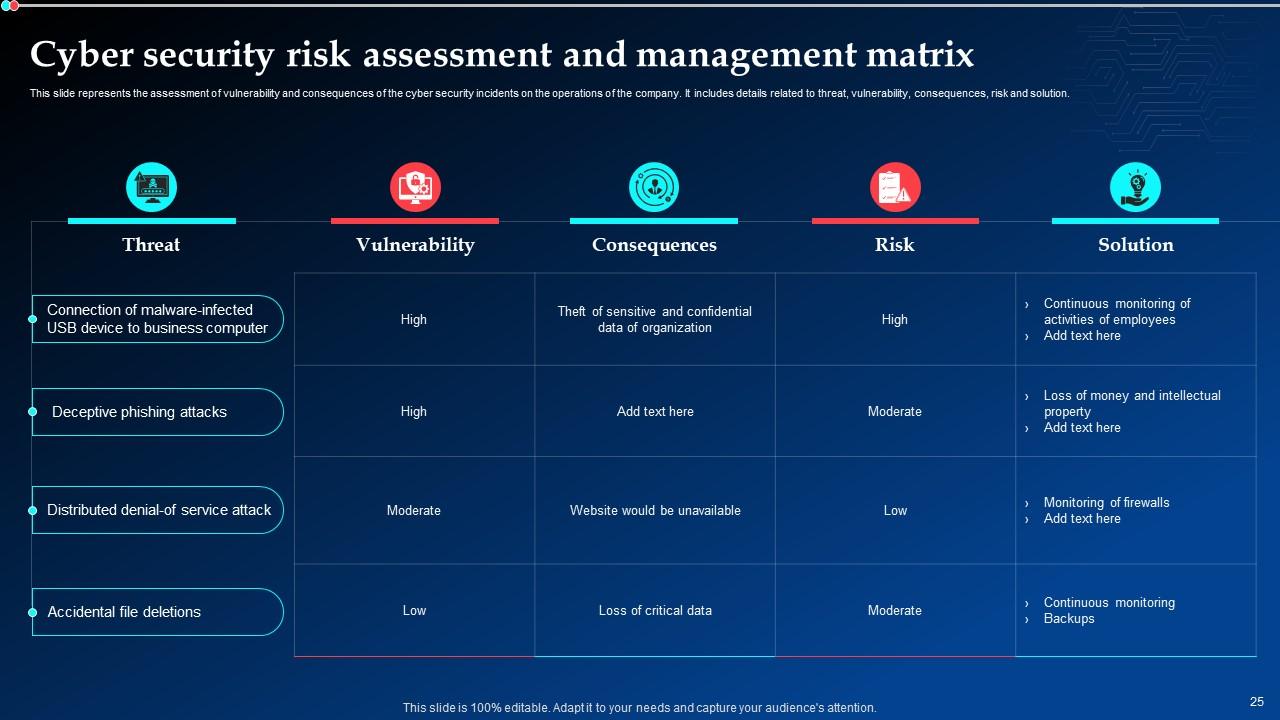
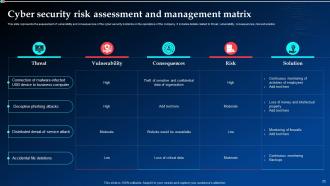
Slide 25: This slide displays the Cyber security risk assessment and management matrix.
Slide 26: This slide mentions the Title for the Ideas to be discussed in the upcoming template.
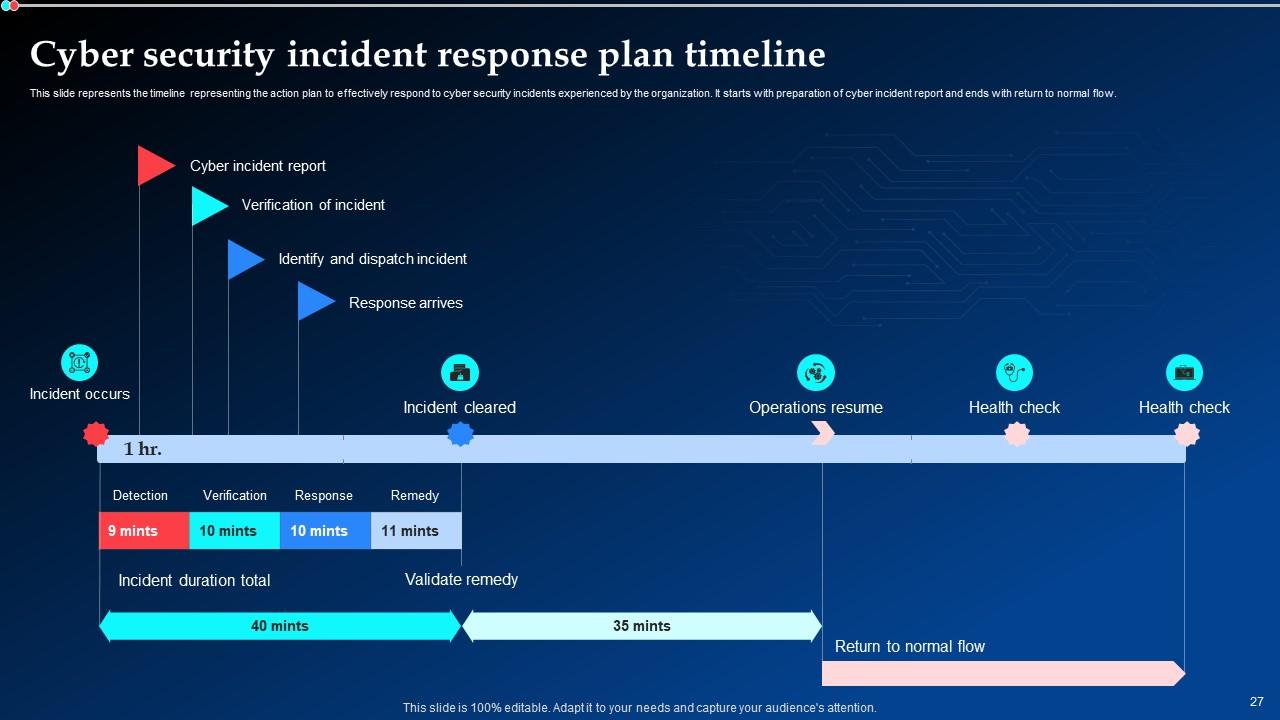
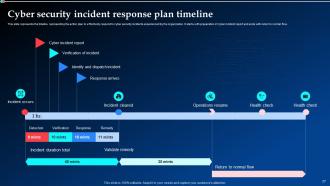
Slide 27: This slide shows the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization.
Slide 28: This slide includes the Heading for the Components to be discussed in the upcoming template.
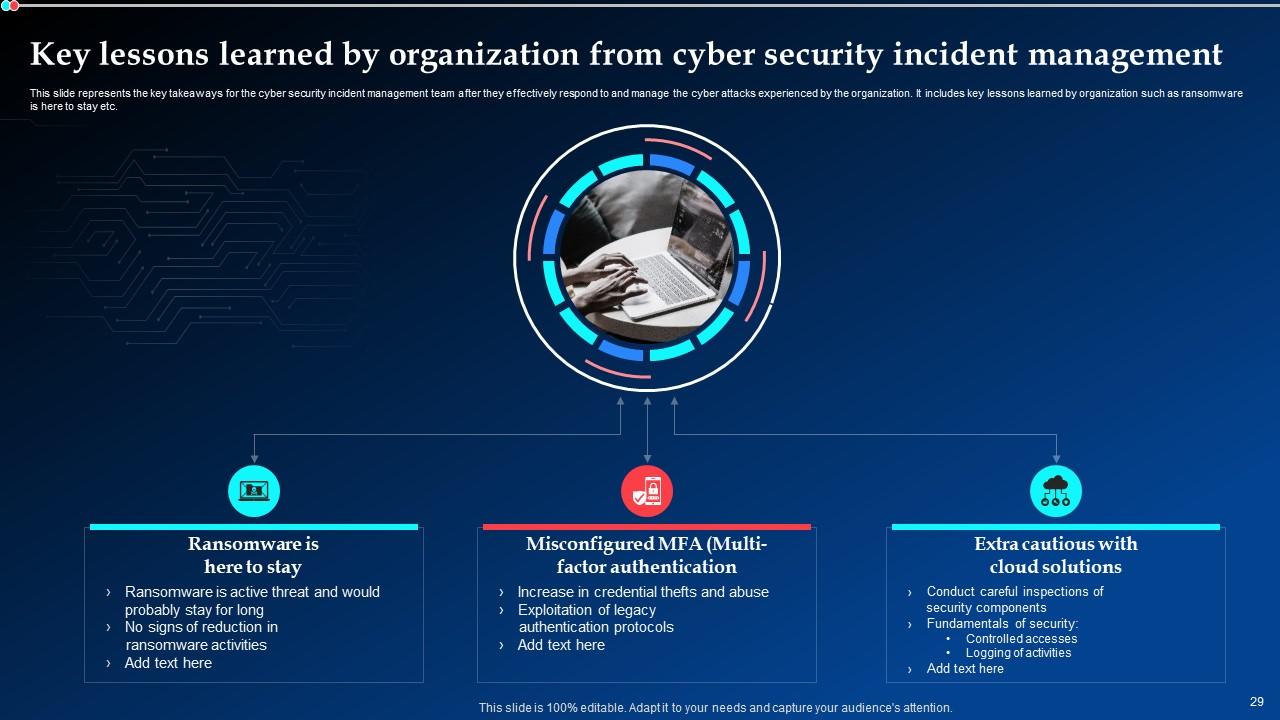
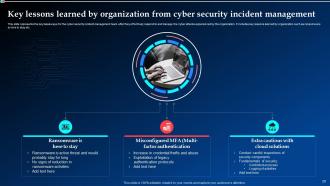
Slide 29: This slide talks about the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization.
Slide 30: This slide incorporates the Title for the Topics to be covered further.
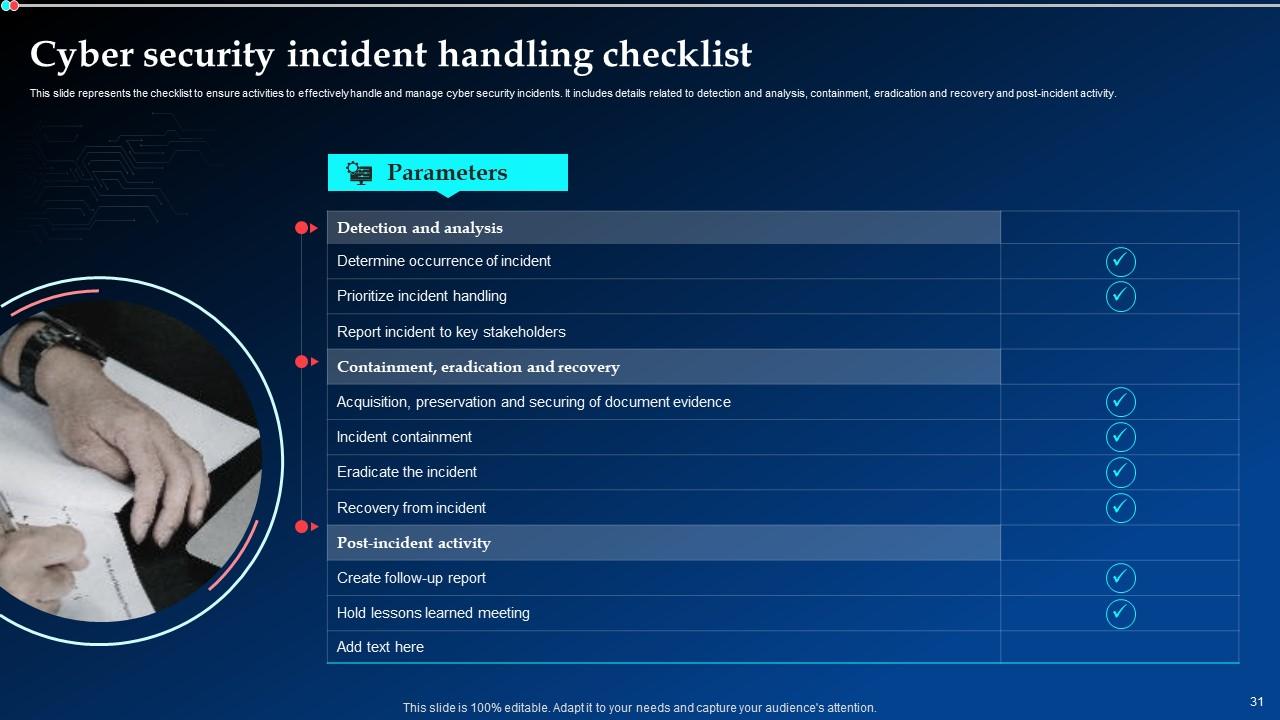
Slide 31: This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents.
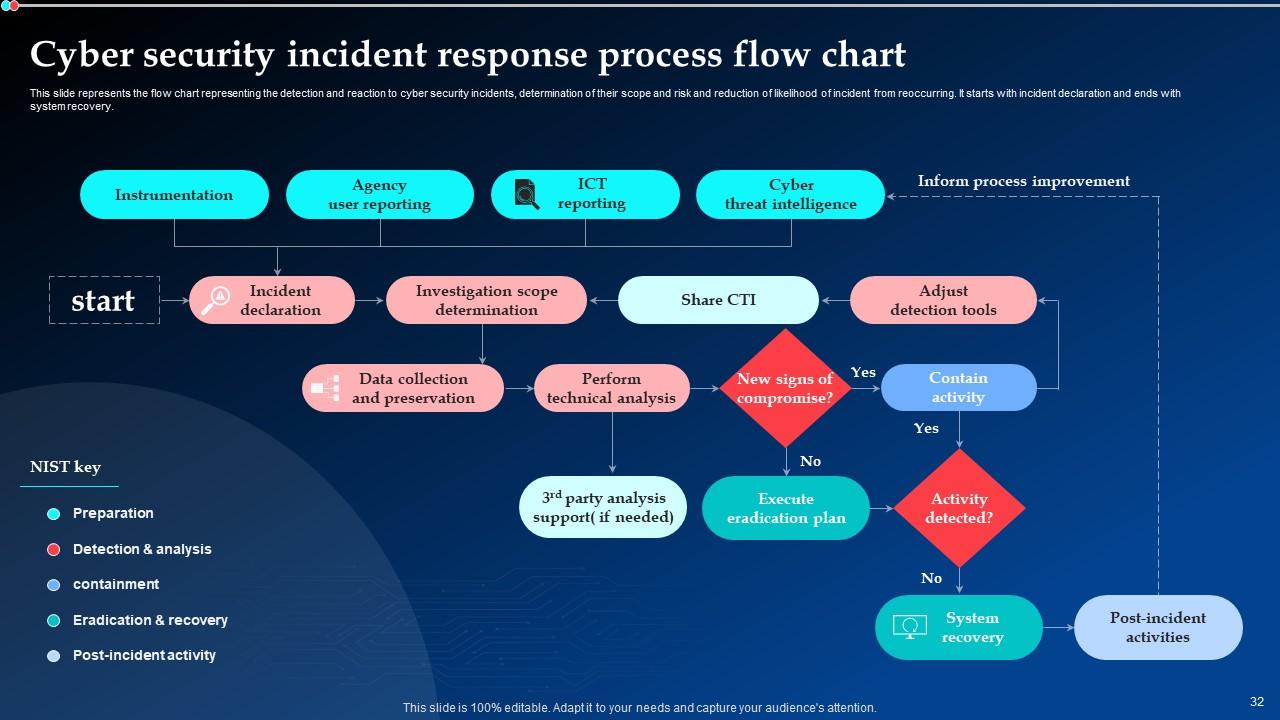
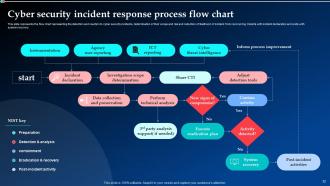
Slide 32: This slide displays the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring.
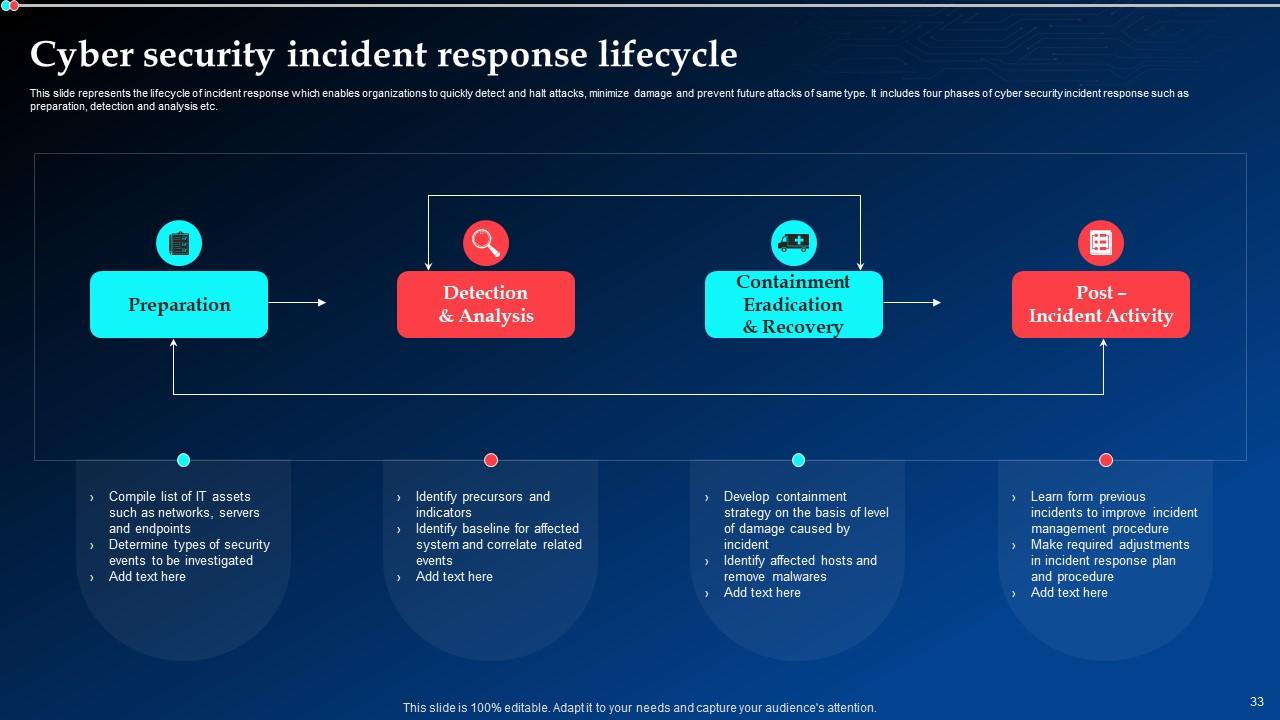
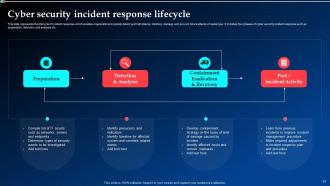
Slide 33: This slide elucidates the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type.
Slide 34: This slide reveals the Heading for the Ideas to be discsused next.
Slide 35: This slide deals with the Cyber security incident handler contact information.
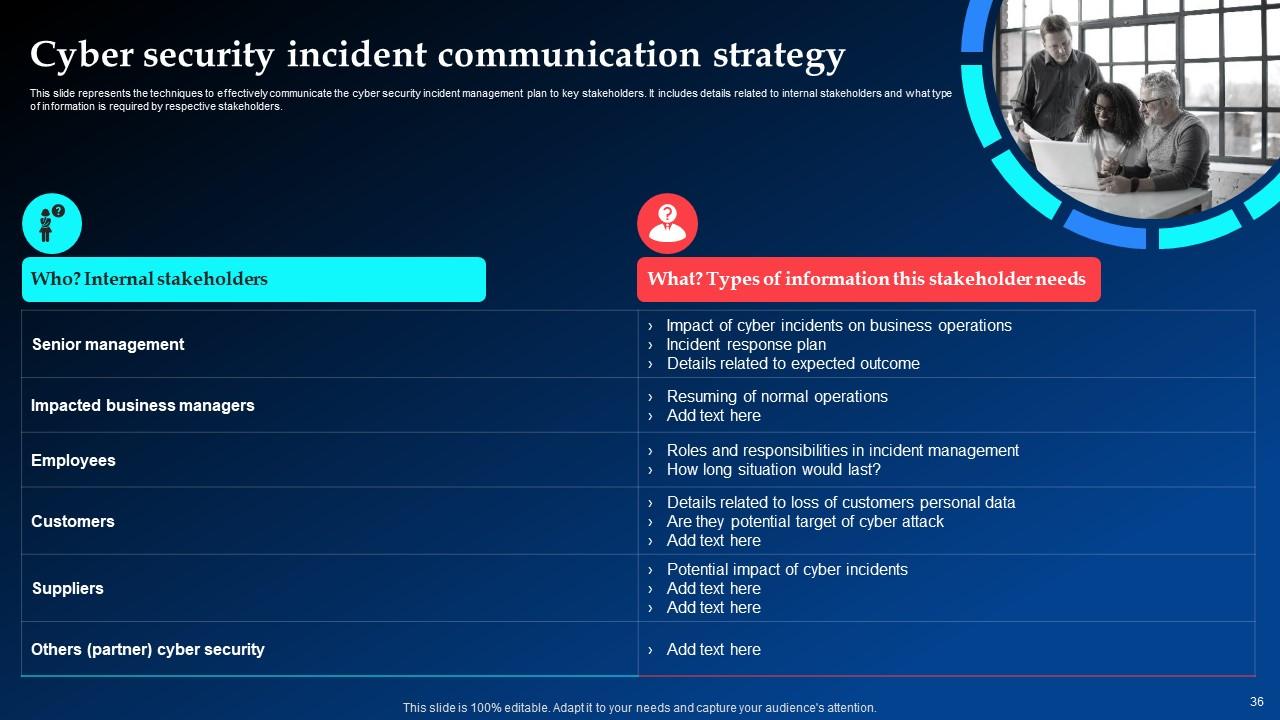
Slide 36: This slide highlights the Cyber security incident communication strategy.
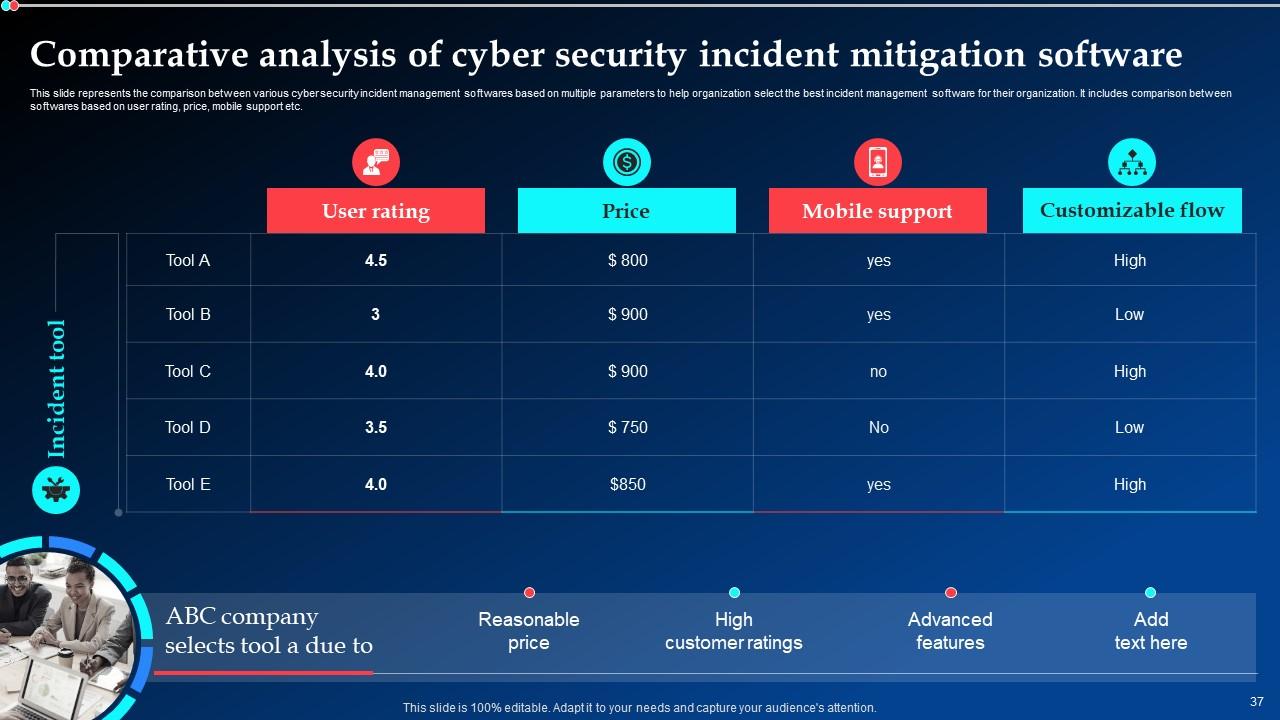
Slide 37: This slide deals with the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization.
Slide 38: This slide reveals the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur.
Slide 39: This slide mentions the Title for the Topics to be discussed further.
Slide 40: This slide focuses on the Cyber security threats detection techniques.
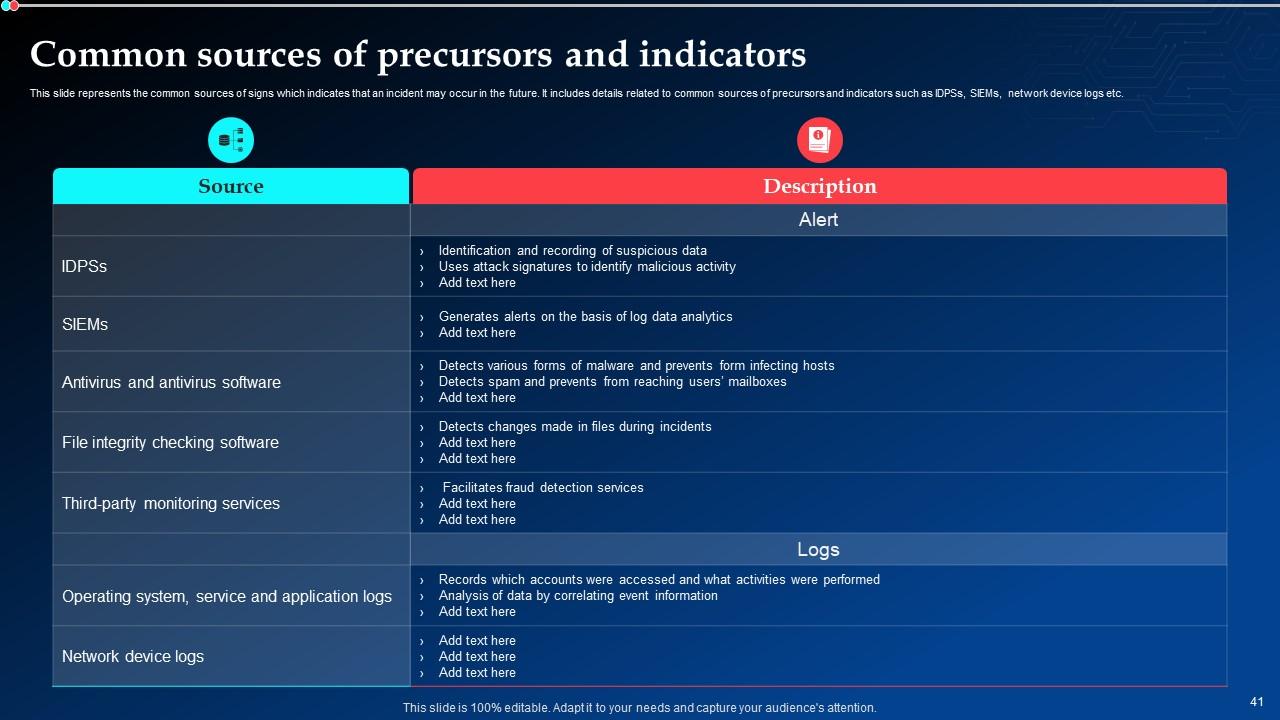
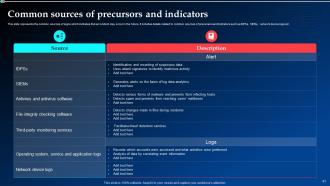
Slide 41: This slide presents the common sources of signs which indicates that an incident may occur in the future.
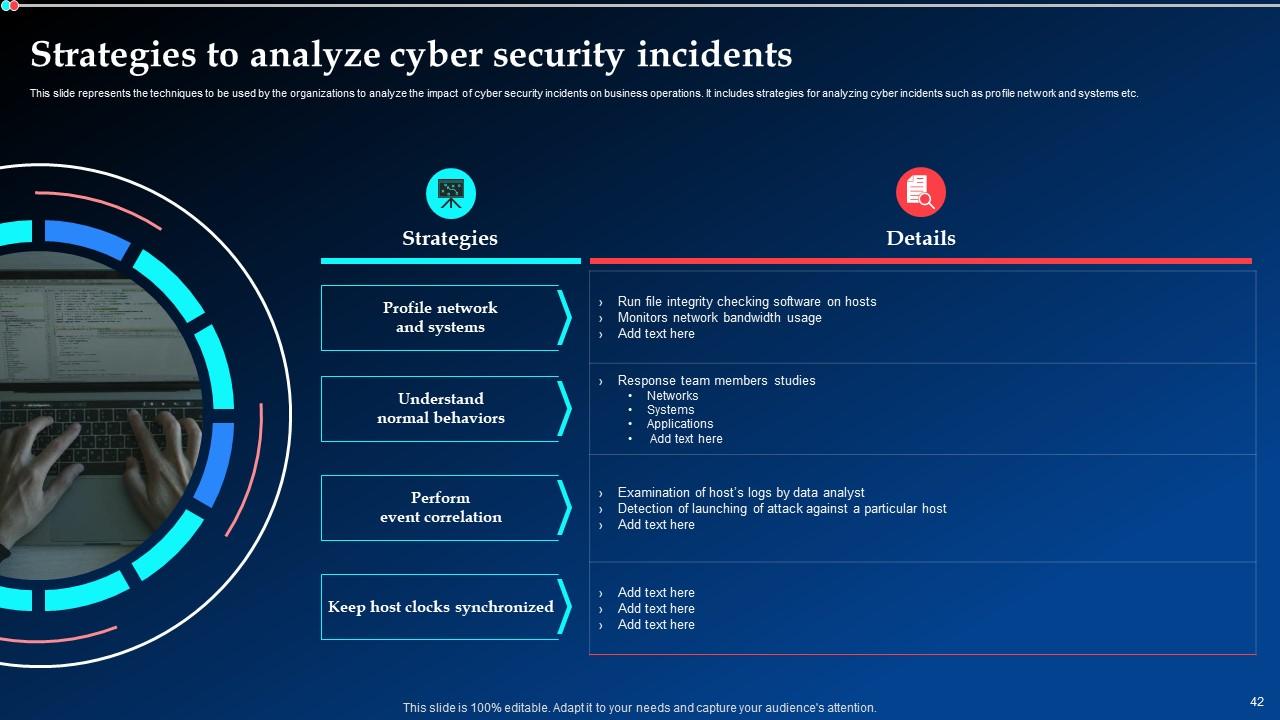
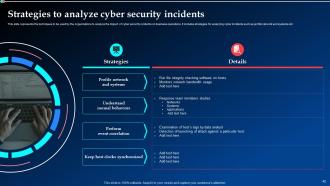
Slide 42: This slide depicts the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations.
Slide 43: This slide covers the Title for the Ideas to be discussed further.
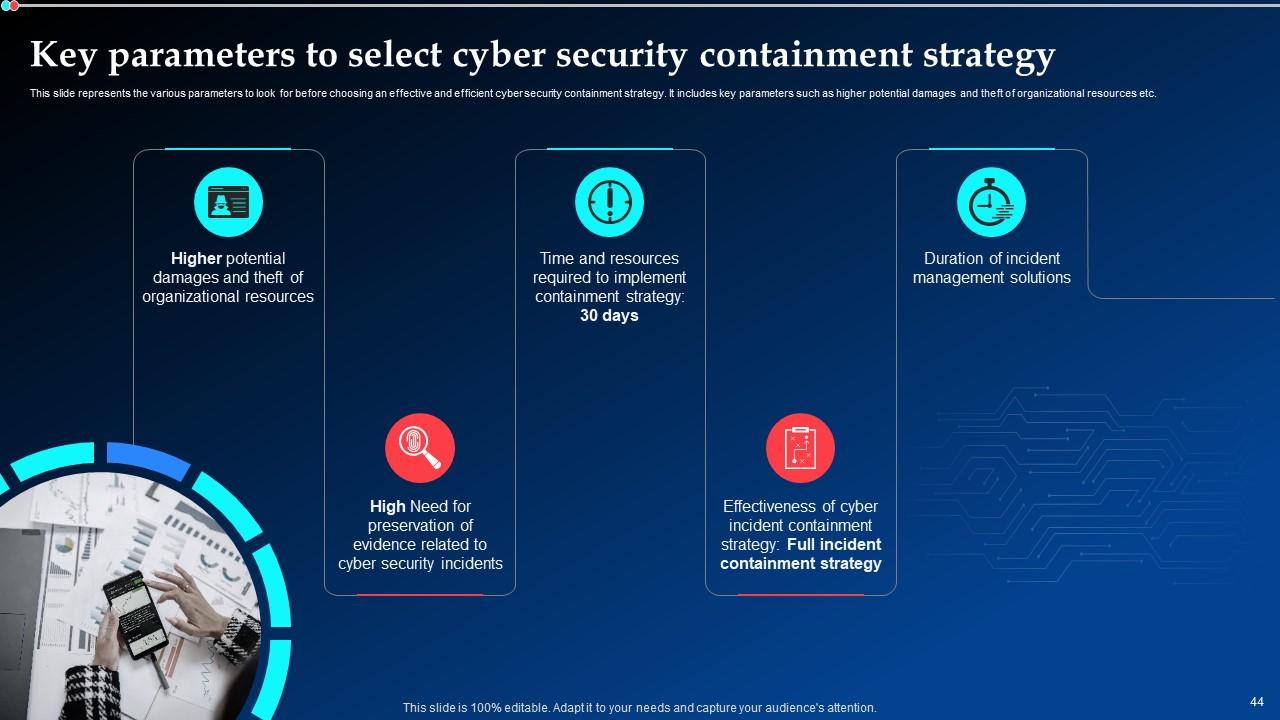
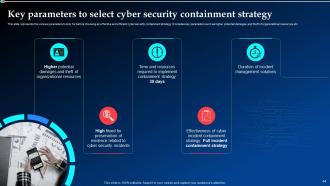
Slide 44: This slide showcases the various parameters to look for before choosing an effective and efficient cyber security containment strategy.
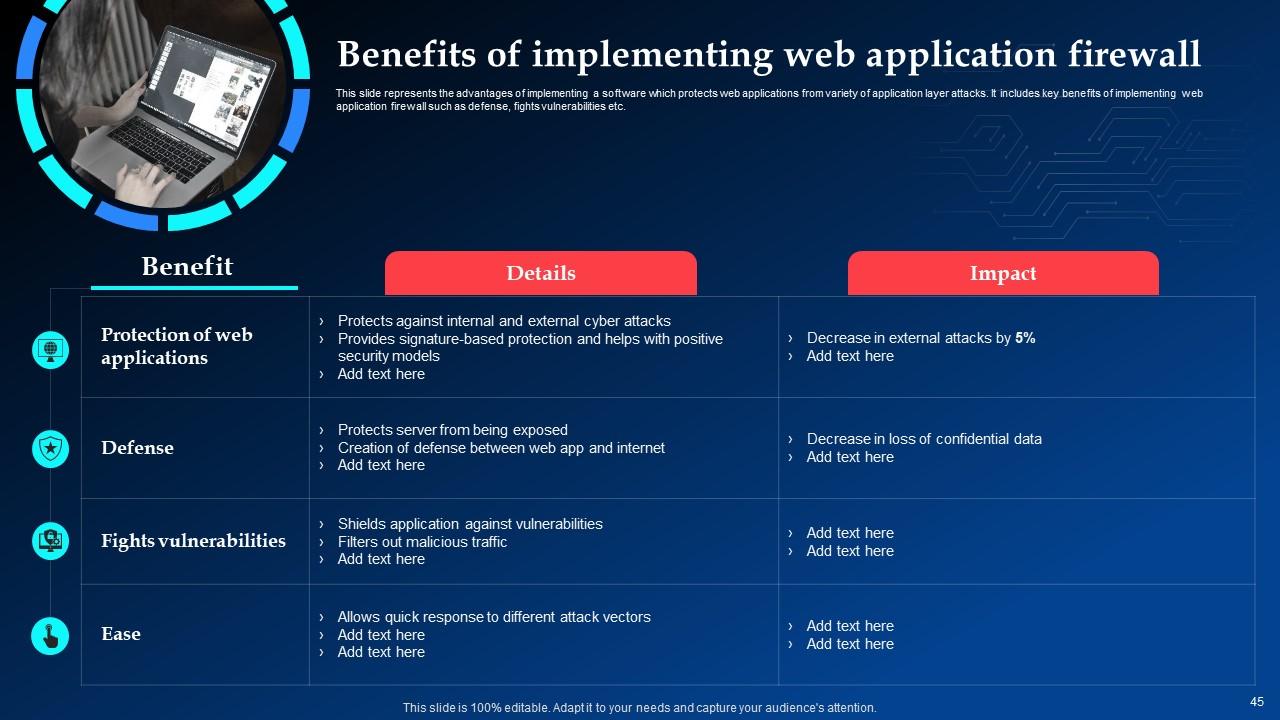
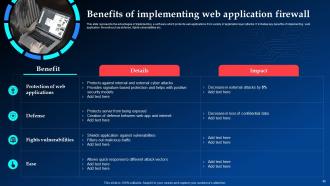
Slide 45: This slide elucidates the advantages of implementing a software which protects web applications from variety of application layer attacks.
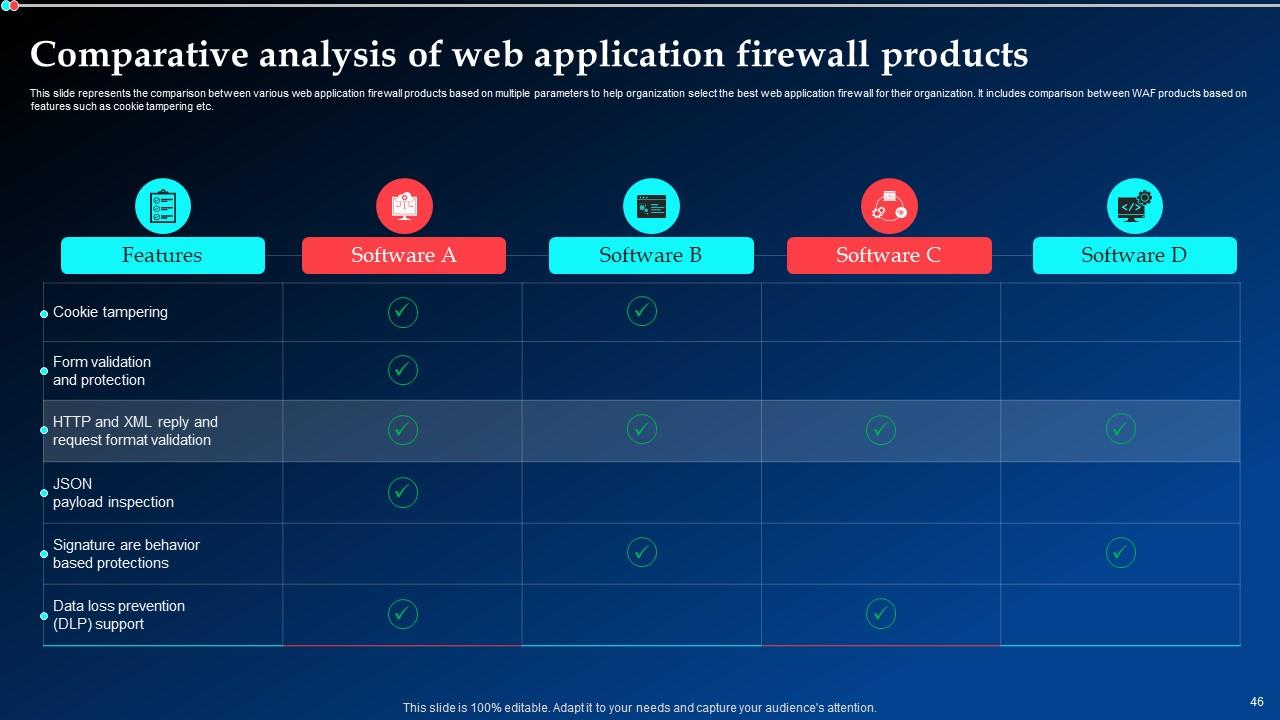
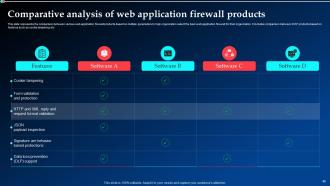
Slide 46: This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best from these.
Slide 47: This slide includes the Heading for the Topics to be covered in the upcoming template.
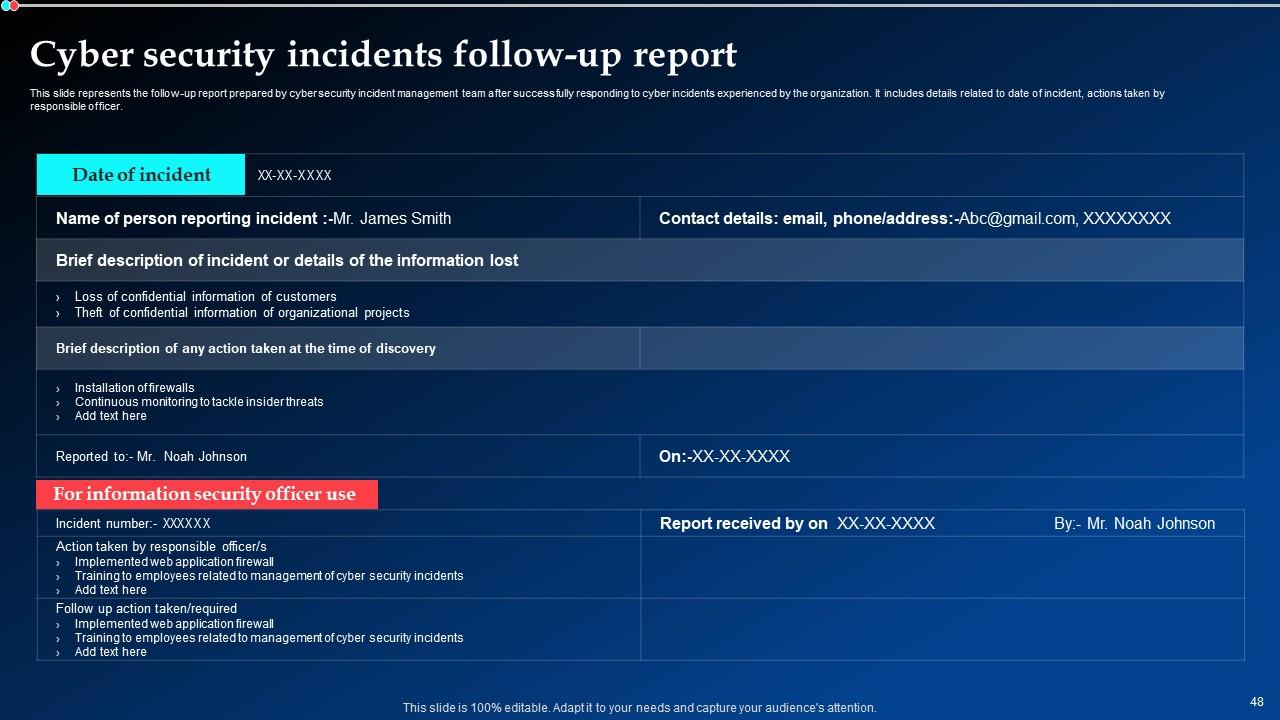
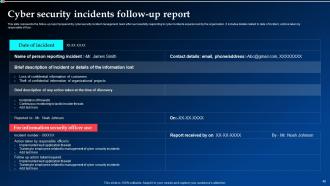
Slide 48: This slide indicates the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization.
Slide 49: This slide highlights the Heading for the Components to be discussed in the forth-coming template.
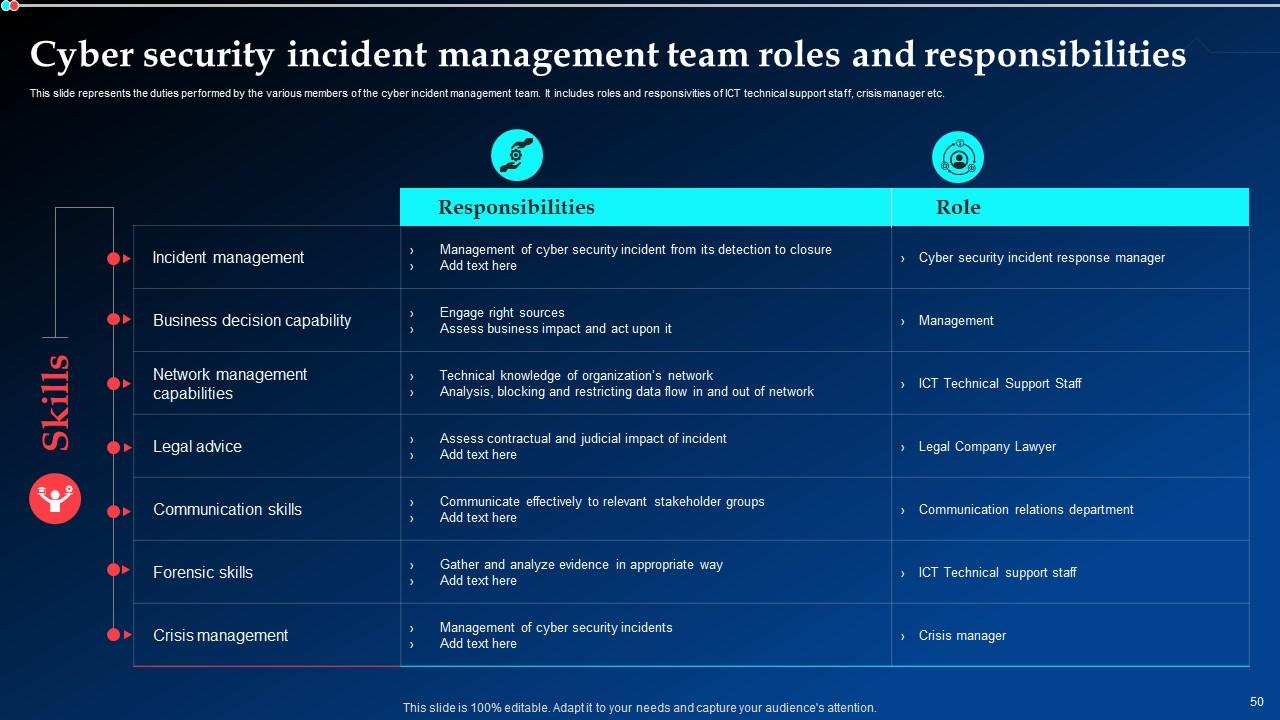
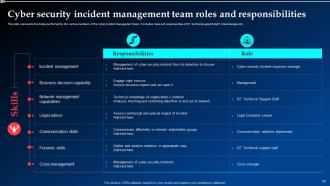
Slide 50: This slide mentions the duties performed by the various members of the cyber incident management team.
Slide 51: This slide potrays the Title for the Components to be covered further.
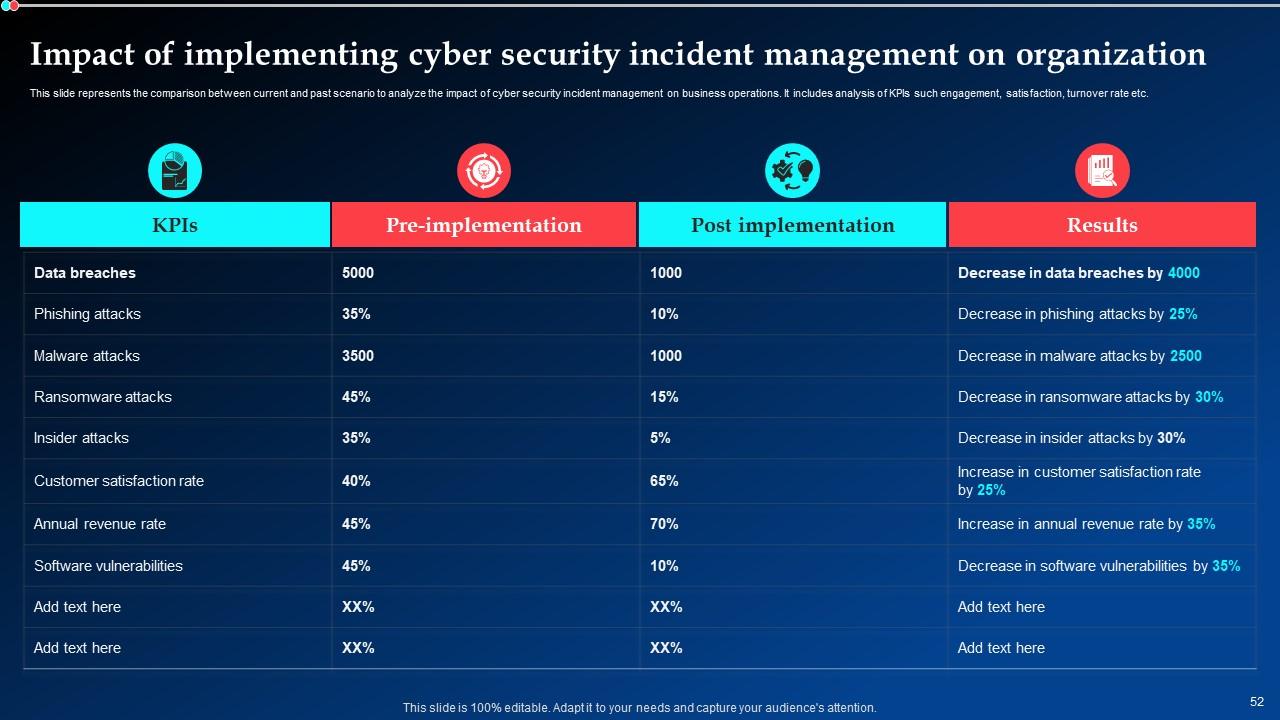
Slide 52: This slide shows the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations.
Slide 53: This slide highlights the Title for the Ideas to be covered further.
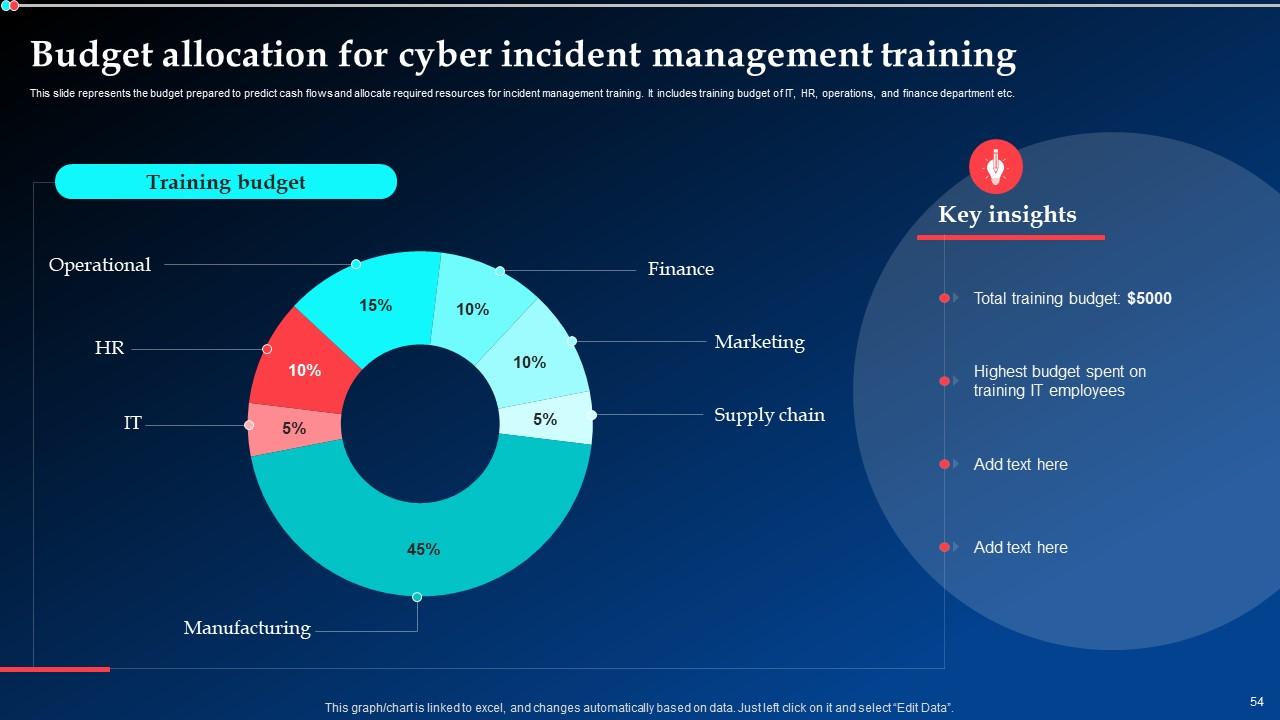
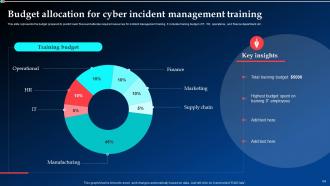
Slide 54: This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training.
Slide 55: This slide exhibits the Heading for the Topics to be discussed next.
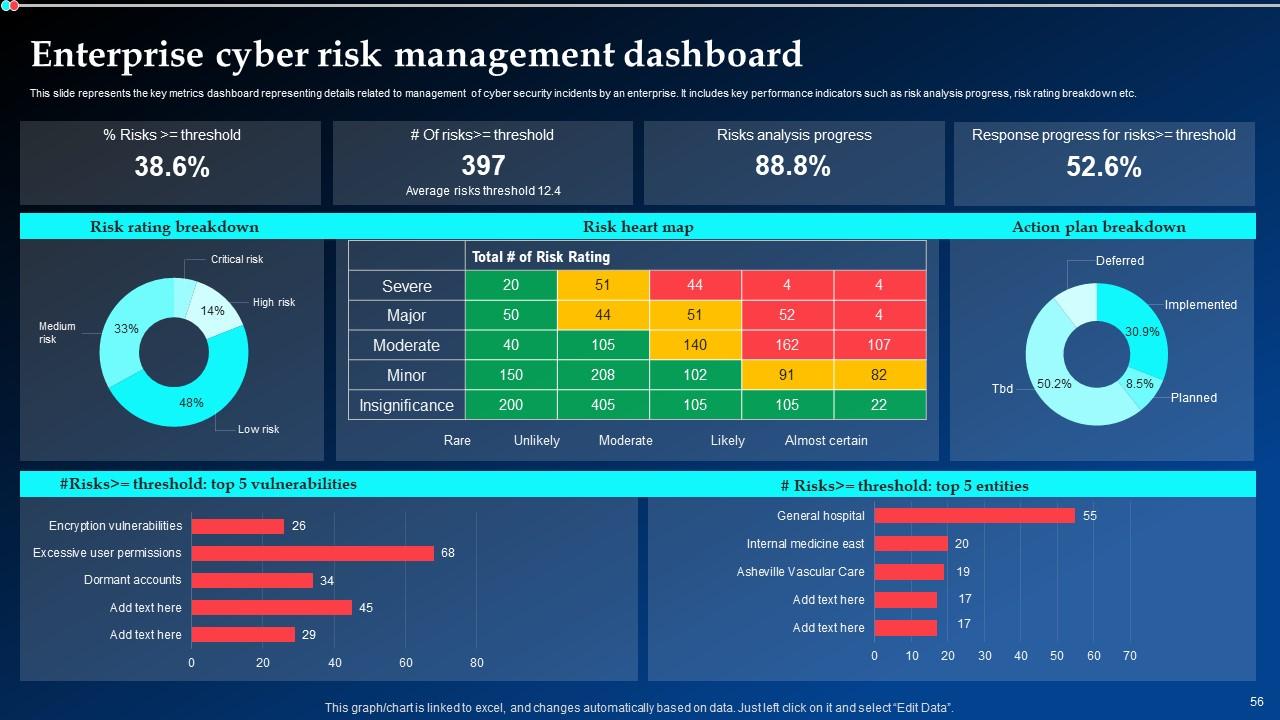
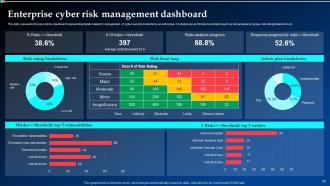
Slide 56: This slide deals with the key metrics dashboard representing details related to management of cyber security incidents by an enterprise.
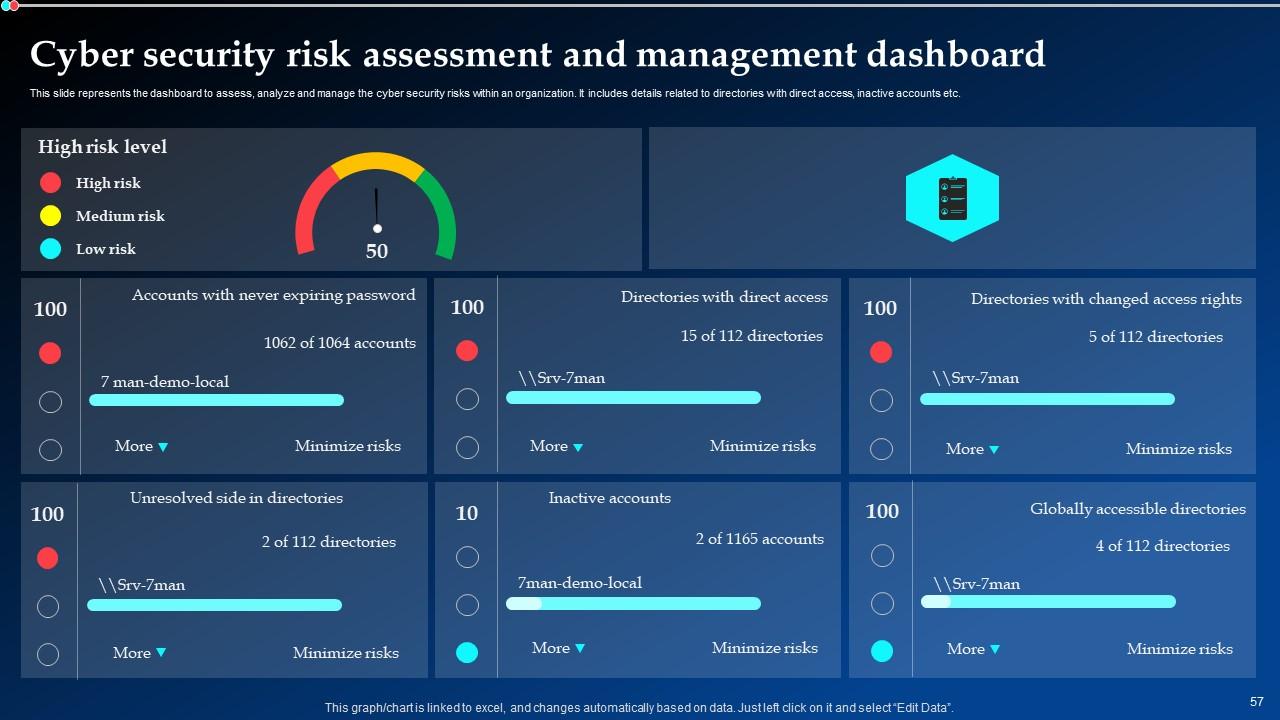
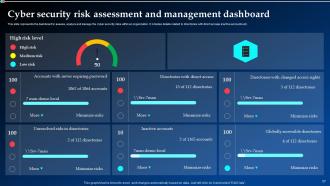
Slide 57: This slide depicts the dashboard to assess, analyze and manage the cyber security risks within an organization.
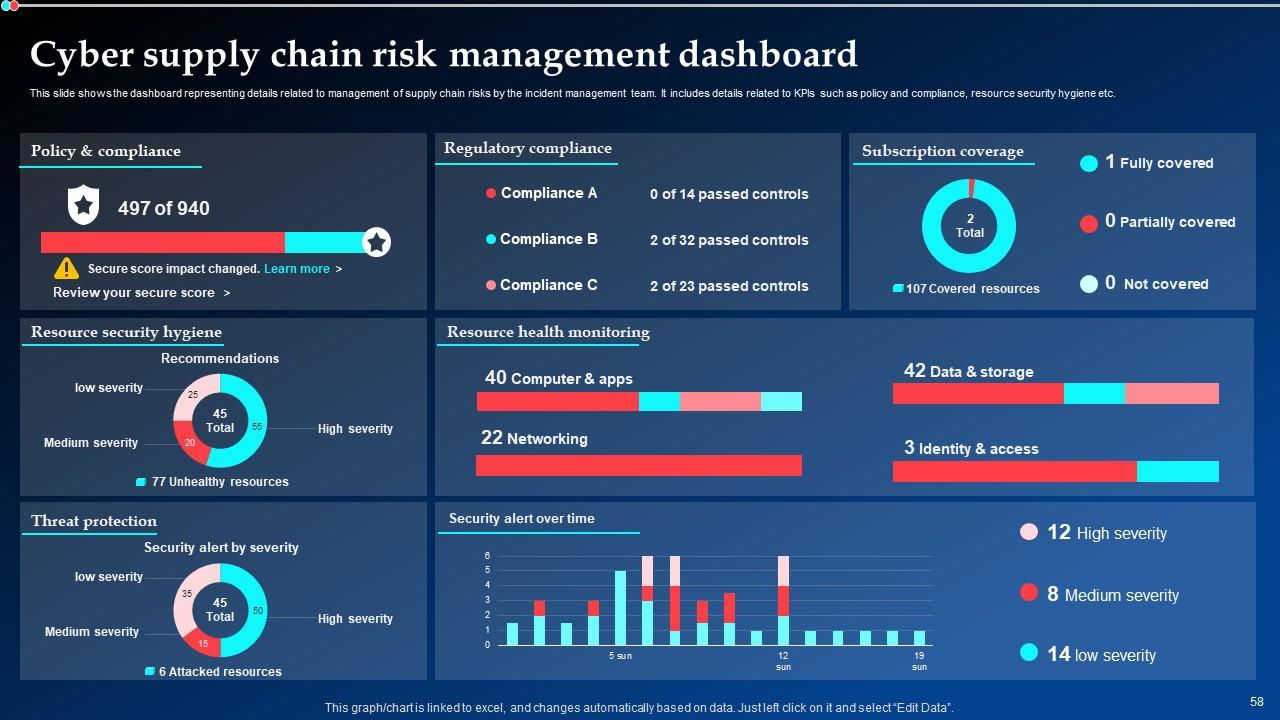
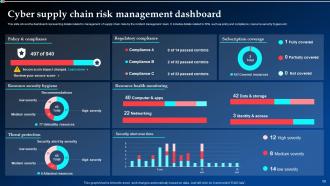
Slide 58: This slide illustrates the dashboard representing details related to management of supply chain risks by the incident management team.
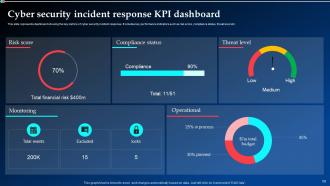
Slide 59: This slide represents dashboard showing the key metrics of cyber security incident response.
Slide 60: This is the Icons slide containing all the Icons used in the plan.
Slide 61: This slide is used for depicting some Additional information.
Slide 62: This is Our Mission slide. State your organization's mission, vision, and goals here.
Slide 63: This is the About Us slide for showcasing company related information.
Slide 64: This slide highlights the organization's Timeline.
Slide 65: This slide elucidates the SWOT analysis.
Slide 66: This template incorporates the 30 60 90 days plan for efficient planning.
Slide 67: This is the Puzzle slide with related imagery.
Slide 68: This slide sowcases information related to the Financial topic.
Slide 69: This is the Thank You slide for acknowledgement.
Implementing Cyber Security Incident Management Powerpoint Presentation Slides with all 74 slides:
Use our Implementing Cyber Security Incident Management Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Attractive design and informative presentation.
-
Illustrative design with editable content. Exceptional value for money. Highly pleased with the product.