Powerpoint Templates and Google slides for Data Encryption
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Encryption For Data Privacy In Digital Age IT Powerpoint Presentation Slides
Encryption For Data Privacy In Digital Age IT Powerpoint Presentation SlidesEnthrall your audience with this Encryption For Data Privacy In Digital Age IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising two hundred fourty one slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Cloud Data Encryption Implementation Plan Powerpoint Presentation Slides
Cloud Data Encryption Implementation Plan Powerpoint Presentation SlidesEnthrall your audience with this Cloud Data Encryption Implementation Plan Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising sixty eight slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
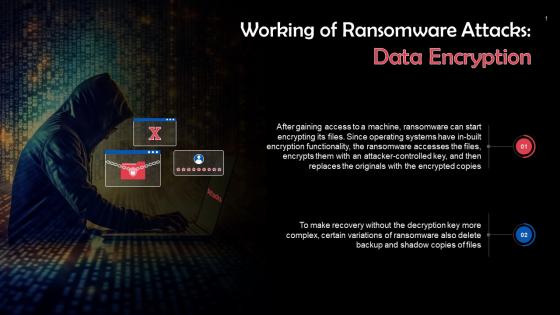 Data Encryption In Ransomware Attacks Training Ppt
Data Encryption In Ransomware Attacks Training PptPresenting Data Encryption in Ransomware Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
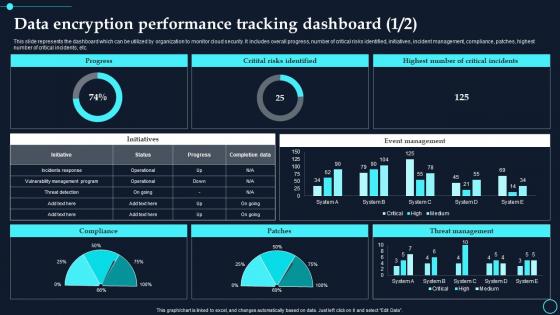 Data Encryption Performance Tracking Dashboard Cloud Data Encryption
Data Encryption Performance Tracking Dashboard Cloud Data EncryptionThis slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Deliver an outstanding presentation on the topic using this Data Encryption Performance Tracking Dashboard Cloud Data Encryption. Dispense information and present a thorough explanation of Progress, Critital Risks Identified using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
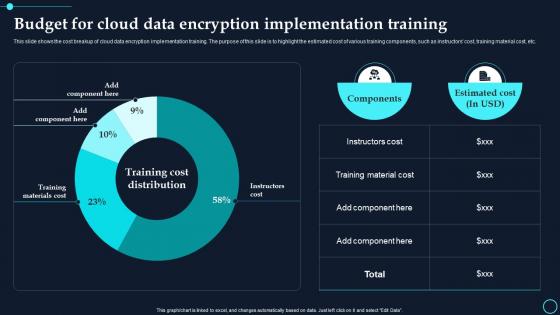 Budget For Cloud Data Encryption Implementation Training Cloud Data Encryption
Budget For Cloud Data Encryption Implementation Training Cloud Data EncryptionThis slide shows the cost breakup of cloud data encryption implementation training. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Deliver an outstanding presentation on the topic using this Budget For Cloud Data Encryption Implementation Training Cloud Data Encryption. Dispense information and present a thorough explanation of Components, Estimated Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
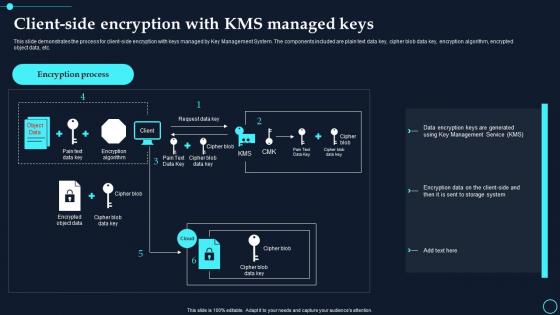 Client Side Encryption With Kms Managed Keys Cloud Data Encryption
Client Side Encryption With Kms Managed Keys Cloud Data EncryptionThis slide demonstrates the process for client side encryption with keys managed by Key Management System. The components included are plain text data key, cipher blob data key, encryption algorithm, encrypted object data, etc. Deliver an outstanding presentation on the topic using this Client Side Encryption With Kms Managed Keys Cloud Data Encryption. Dispense information and present a thorough explanation of Encryption Process, Encryption Algorithm using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
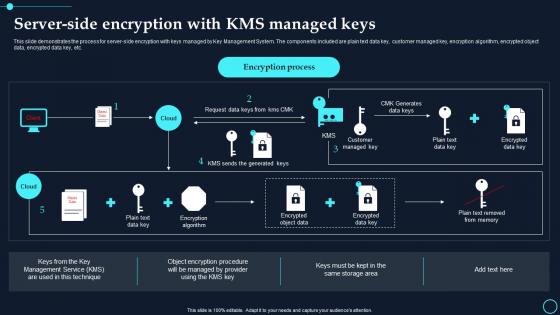 Server Side Encryption With Kms Managed Keys Cloud Data Encryption
Server Side Encryption With Kms Managed Keys Cloud Data EncryptionThis slide demonstrates the process for server side encryption with keys managed by Key Management System. The components included are plain text data key, customer managed key, encryption algorithm, encrypted object data, encrypted data key, etc. Present the topic in a bit more detail with this Server Side Encryption With Kms Managed Keys Cloud Data Encryption. Use it as a tool for discussion and navigation on Encryption Process, Customer Managed Key. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
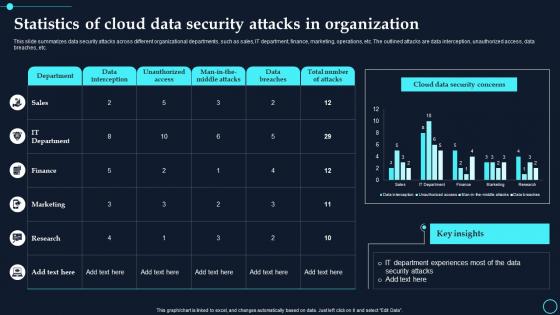 Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption
Statistics Of Cloud Data Security Attacks In Organization Cloud Data EncryptionThis slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. Deliver an outstanding presentation on the topic using this Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption. Dispense information and present a thorough explanation of Data Interception, Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
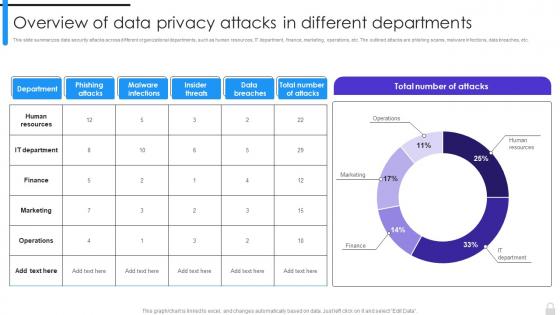 Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments
Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different DepartmentsThis slide summarizes data security attacks across different organizational departments, such as human resources, IT department, finance, marketing, operations, etc. The outlined attacks are phishing scams, malware infections, data breaches, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments. Use it as a tool for discussion and navigation on Human Resources, IT Department, Finance, Marketing, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
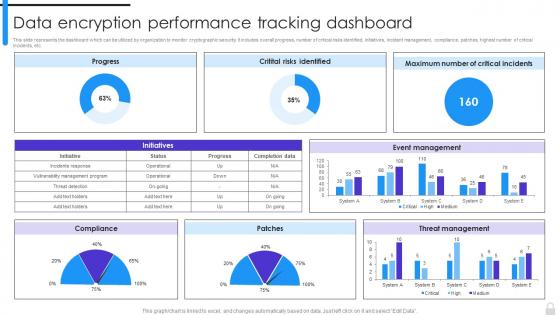 Encryption Implementation Strategies Data Encryption Performance Tracking Dashboard
Encryption Implementation Strategies Data Encryption Performance Tracking DashboardThis slide represents the dashboard which can be utilized by organization to monitor cryptographic security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Encryption Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Data Encryption Performance, Tracking Dashboard, Critical Incidents, Incident Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Applications As A Service In Organizations Encryption For Data Privacy In Digital Age It
Applications As A Service In Organizations Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the major uses of Encryption-as-Service method in different domains. The key applications discussed in this slide are all-time security assurance, secure sensitive information and maintaining regulatory compliance. Introducing Applications As A Service In Organizations Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Maintaining Regulatory Compliance, Secure Sensitive Information, Security Assurance, using this template. Grab it now to reap its full benefits.
-
 Comparison Symmetric And Asymmetric Encryption Encryption For Data Privacy In Digital Age It
Comparison Symmetric And Asymmetric Encryption Encryption For Data Privacy In Digital Age ItThis slide outlines the differences between symmetric and asymmetric encryption methods. The purpose of this slide is to compare the two main data encryption techniques known as symmetric key cryptography and asymmetric key cryptography. Present the topic in a bit more detail with this Comparison Symmetric And Asymmetric Encryption Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric, Encryption, Comparison. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
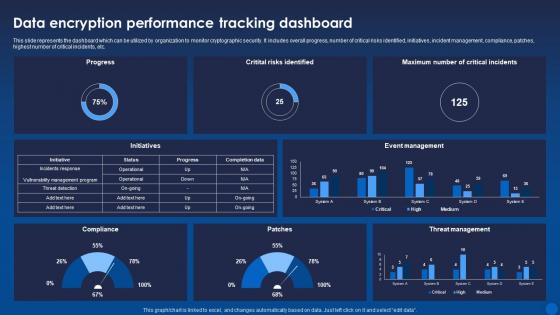 Data Encryption Performance Tracking Dashboard Encryption For Data Privacy In Digital Age It
Data Encryption Performance Tracking Dashboard Encryption For Data Privacy In Digital Age ItThis slide represents the dashboard which can be utilized by organization to monitor cryptographic security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. Deliver an outstanding presentation on the topic using this Data Encryption Performance Tracking Dashboard Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Performance, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
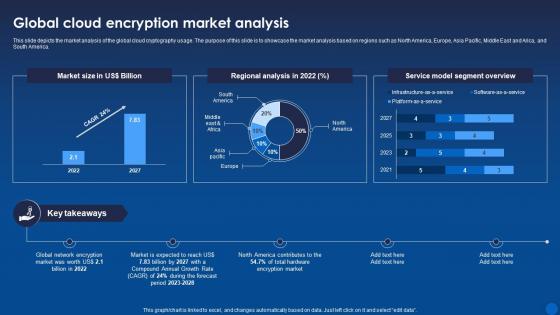 Global Cloud Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Cloud Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global cloud cryptography usage. The purpose of this slide is to showcase the market analysis based on regions such as North America, Europe, Asia Pacific, Middle East and Arica, and South America. Present the topic in a bit more detail with this Global Cloud Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Regional Analysis, Segment Overview, Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
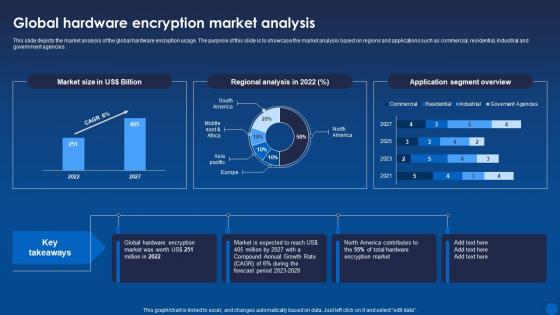 Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global hardware encryption usage. The purpose of this slide is to showcase the market analysis based on regions and applications such as commercial, residential, industrial and government agencies. Deliver an outstanding presentation on the topic using this Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Hardware, Encryption, Analysisusing the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
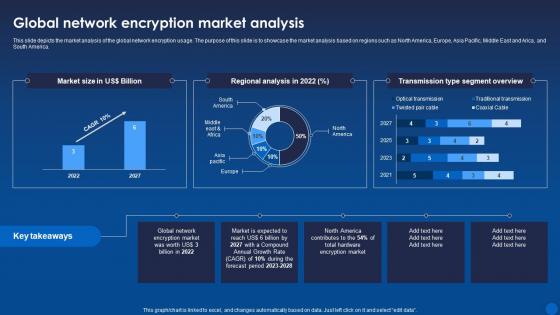 Global Network Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Network Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global network encryption usage. The purpose of this slide is to showcase the market analysis based on regions such as North America, Europe, Asia Pacific, Middle East and Arica, and South America. Present the topic in a bit more detail with this Global Network Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Global Network, Encryption, Market Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
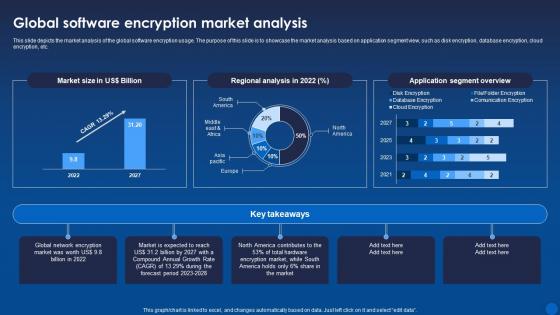 Global Software Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Software Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global software encryption usage. The purpose of this slide is to showcase the market analysis based on application segment view, such as disk encryption, database encryption, cloud encryption, etc. Deliver an outstanding presentation on the topic using this Global Software Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Software, Encryption, Market Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
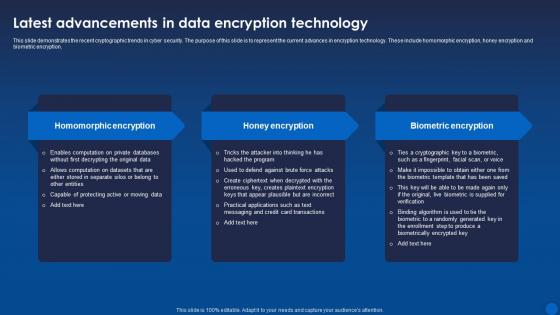 Latest Advancements In Data Encryption Technology Encryption For Data Privacy In Digital Age It
Latest Advancements In Data Encryption Technology Encryption For Data Privacy In Digital Age ItThis slide demonstrates the recent cryptographic trends in cyber security. The purpose of this slide is to represent the current advances in encryption technology. These include homomorphic encryption, honey encryption and biometric encryption. Increase audience engagement and knowledge by dispensing information using Latest Advancements In Data Encryption Technology Encryption For Data Privacy In Digital Age It. This template helps you present information on three stages. You can also present information on Homomorphic Encryption, Honey Encryption, Biometric Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
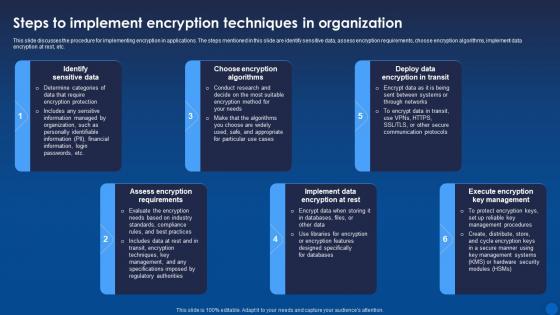 Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age It
Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age ItThis slide discusses the procedure for implementing encryption in applications. The steps mentioned in this slide are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Identify Sensitive Data, Choose Encryption Algorithms, Deploy Data Encryption In Transit, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Encryption For Data Privacy In Digital Age
Table Of Contents For Encryption For Data Privacy In Digital AgeDeliver an outstanding presentation on the topic using this Table Of Contents For Encryption For Data Privacy In Digital Age. Dispense information and present a thorough explanation of Encryption Overview, Importance Of Encryption, Encryption Market And Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
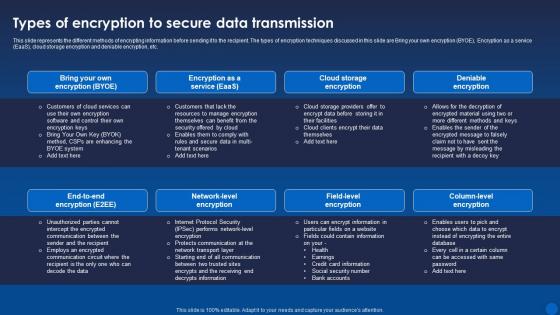 Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age It
Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age ItThis slide represents the different methods of encrypting information before sending it to the recipient. The types of encryption techniques discussed in this slide are Bring your own encryption BYOE, Encryption as a service EaaS, cloud storage encryption and deniable encryption, etc. Present the topic in a bit more detail with this Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Data Transmission, Encryption, Deniable Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
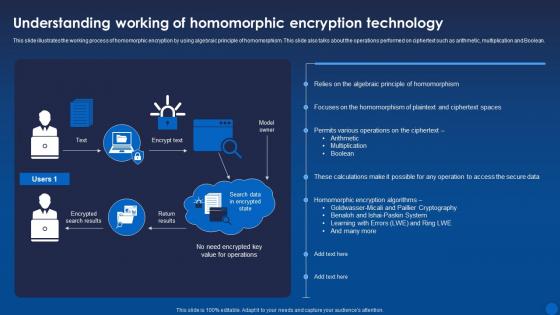 Understanding Homomorphic Encryption Technology Encryption For Data Privacy In Digital Age It
Understanding Homomorphic Encryption Technology Encryption For Data Privacy In Digital Age ItThis slide illustrates the working process of homomorphic encryption by using algebraic principle of homomorphism. This slide also talks about the operations performed on ciphertext such as arithmetic, multiplication and Boolean. Present the topic in a bit more detail with this Understanding Homomorphic Encryption Technology Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Homomorphic, Encryption, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
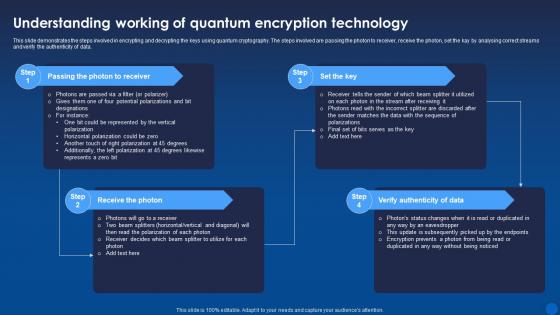 Understanding Working Of Quantum Encryption Technology Encryption For Data Privacy In Digital Age It
Understanding Working Of Quantum Encryption Technology Encryption For Data Privacy In Digital Age ItThis slide demonstrates the steps involved in encrypting and decrypting the keys using quantum cryptography. The steps involved are passing the photon to receiver, receive the photon, set the kay by analysing correct streams and verify the authenticity of data. Increase audience engagement and knowledge by dispensing information using Understanding Working Of Quantum Encryption Technology Encryption For Data Privacy In Digital Age It. This template helps you present information on four stages. You can also present information on Passing The Photon To Receiver, Receive The Photon, Verify Authenticity Of Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
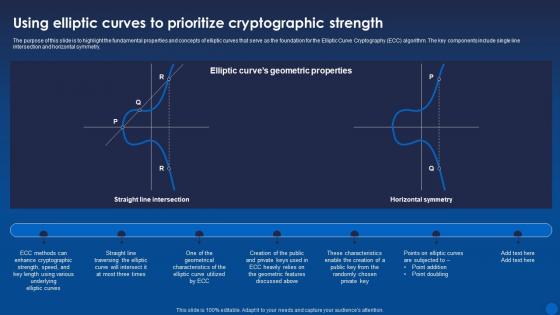 Using Elliptic Curves To Prioritize Cryptographic Strength Encryption For Data Privacy In Digital Age It
Using Elliptic Curves To Prioritize Cryptographic Strength Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to highlight the fundamental properties and concepts of elliptic curves that serve as the foundation for the Elliptic Curve Cryptography ECC algorithm. The key components include single line intersection and horizontal symmetry. Present the topic in a bit more detail with this Using Elliptic Curves To Prioritize Cryptographic Strength Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Prioritize, Cryptographic, Strength. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
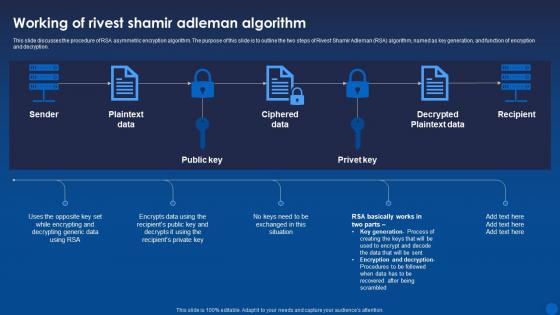 Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age It
Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age ItThis slide discusses the procedure of RSA asymmetric encryption algorithm. The purpose of this slide is to outline the two steps of Rivest Shamir Adleman RSA algorithm, named as key generation, and function of encryption and decryption. Deliver an outstanding presentation on the topic using this Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Algorithm, Ciphered Data, Decrypted Plaintext Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Techniques Icon For Securing Big Data Analytics
Encryption Techniques Icon For Securing Big Data AnalyticsIntroducing our Encryption Techniques Icon For Securing Big Data Analytics set of slides. The topics discussed in these slides are Encryption Techniques, Securing Big Data Analytics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
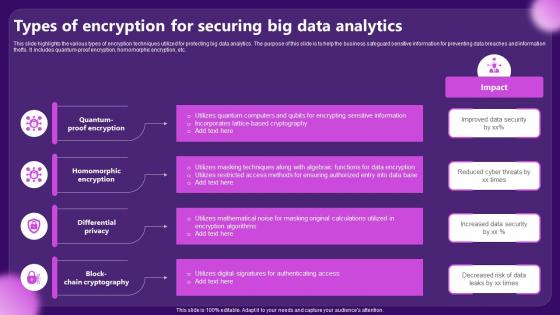 Types Of Encryption For Securing Big Data Analytics
Types Of Encryption For Securing Big Data AnalyticsThis slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum proof encryption, homomorphic encryption, etc. Introducing our premium set of slides with Types Of Encryption For Securing Big Data Analytics. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Homomorphic Encryption, Differential Privacy. So download instantly and tailor it with your information.
-
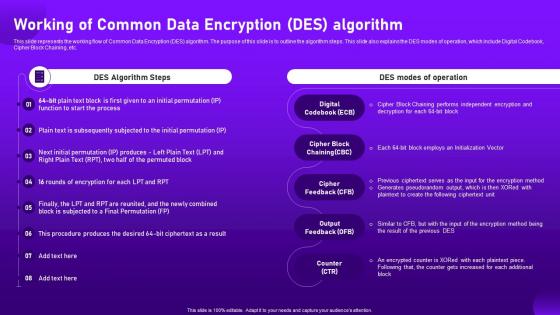 Working Of Common Data Encryption Des Algorithm Cloud Cryptography
Working Of Common Data Encryption Des Algorithm Cloud CryptographyThis slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Deliver an outstanding presentation on the topic using this Working Of Common Data Encryption Des Algorithm Cloud Cryptography. Dispense information and present a thorough explanation of Pseudorandom, Initialization, Independent using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
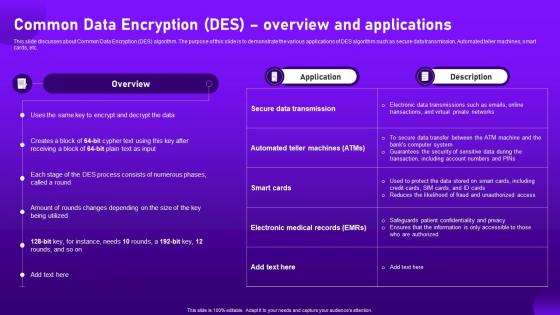 Common Data Encryption Des Overview And Applications Cloud Cryptography
Common Data Encryption Des Overview And Applications Cloud CryptographyThis slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Deliver an outstanding presentation on the topic using this Common Data Encryption Des Overview And Applications Cloud Cryptography. Dispense information and present a thorough explanation of Overview, Applications, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
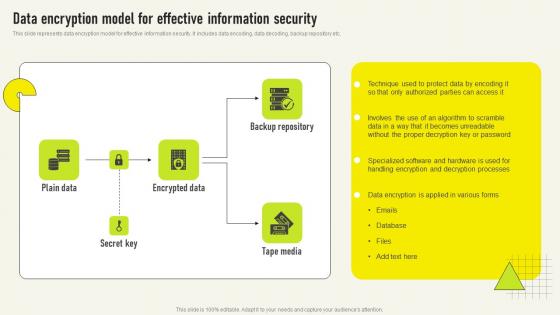 Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS V
Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS VThis slide represents data encryption model for effective information security It includes data encoding, data decoding, backup repository etc Introducing our Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS V set of slides The topics discussed in these slides are Specialized Software, Handling Encryption, Authorized Parties This is an immediately available PowerPoint presentation that can be conveniently customized Download it and convince your audience
-
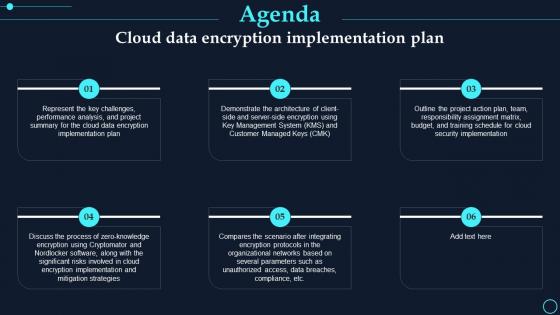 Agenda Cloud Data Encryption Implementation Plan
Agenda Cloud Data Encryption Implementation PlanIntroducing Agenda Cloud Data Encryption Implementation Plan to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Represent Challenges, Performance Analysis, using this template. Grab it now to reap its full benefits.
-
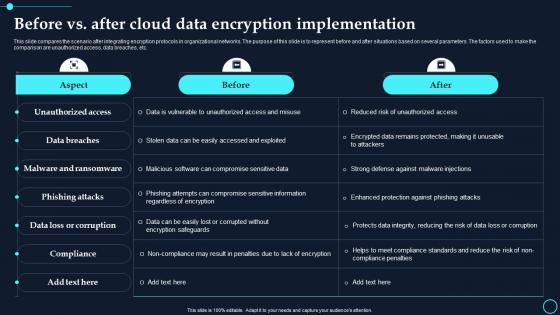 Before Vs After Cloud Data Encryption Implementation Cloud Data Encryption
Before Vs After Cloud Data Encryption Implementation Cloud Data EncryptionThis slide compares the scenario after integrating encryption protocols in organizational networks. The purpose of this slide is to represent before and after situations based on several parameters. The factors used to make the comparison are unauthorized access, data breaches, etc. Present the topic in a bit more detail with this Before Vs After Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Unauthorized Access, Data Breaches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
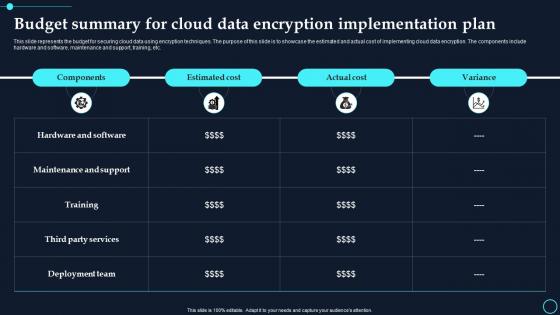 Budget Summary For Cloud Data Encryption Implementation Plan Cloud Data Encryption
Budget Summary For Cloud Data Encryption Implementation Plan Cloud Data EncryptionThis slide represents the budget for securing cloud data using encryption techniques. The purpose of this slide is to showcase the estimated and actual cost of implementing cloud data encryption. The components include hardware and software, maintenance and support, training, etc. Present the topic in a bit more detail with this Budget Summary For Cloud Data Encryption Implementation Plan Cloud Data Encryption. Use it as a tool for discussion and navigation on Maintenance And Support, Hardware And Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
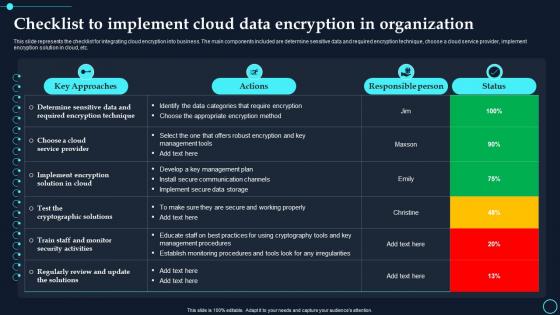 Checklist To Implement Cloud Data Encryption In Organization Cloud Data Encryption
Checklist To Implement Cloud Data Encryption In Organization Cloud Data EncryptionThis slide represents the checklist for integrating cloud encryption into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Deliver an outstanding presentation on the topic using this Checklist To Implement Cloud Data Encryption In Organization Cloud Data Encryption. Dispense information and present a thorough explanation of Key Approaches, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
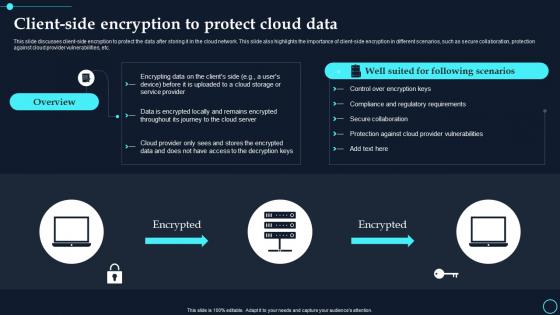 Client Side Encryption To Protect Cloud Data Cloud Data Encryption
Client Side Encryption To Protect Cloud Data Cloud Data EncryptionThis slide discusses client side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc. Introducing Client Side Encryption To Protect Cloud Data Cloud Data Encryption to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Following Scenarios, Encrypted, using this template. Grab it now to reap its full benefits.
-
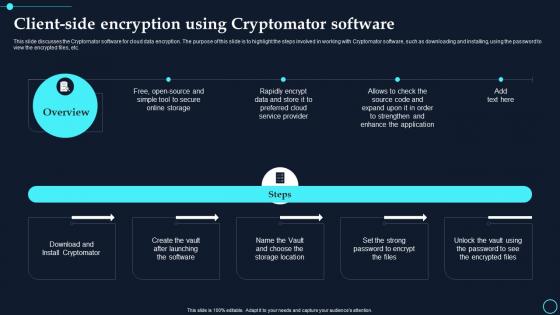 Client Side Encryption Using Cryptomator Software Cloud Data Encryption
Client Side Encryption Using Cryptomator Software Cloud Data EncryptionThis slide discusses the Cryptomator software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with Cryptomator software, such as downloading and installing, using the password to view the encrypted files, etc. Increase audience engagement and knowledge by dispensing information using Client Side Encryption Using Cryptomator Software Cloud Data Encryption. This template helps you present information on one stages. You can also present information on Rapidly Encrypt, Online Storage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
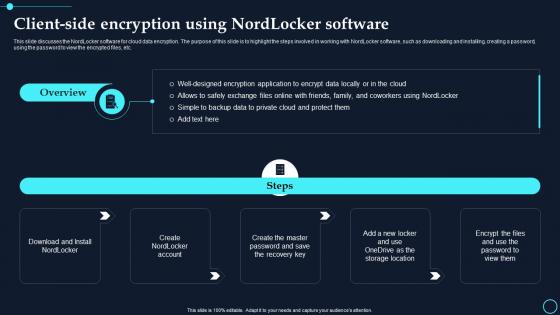 Client Side Encryption Using Nordlocker Software Cloud Data Encryption
Client Side Encryption Using Nordlocker Software Cloud Data EncryptionThis slide discusses the NordLocker software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with NordLocker software, such as downloading and installing, creating a password, using the password to view the encrypted files, etc. Introducing Client Side Encryption Using Nordlocker Software Cloud Data Encryption to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Download And Install, Create The Master, using this template. Grab it now to reap its full benefits.
-
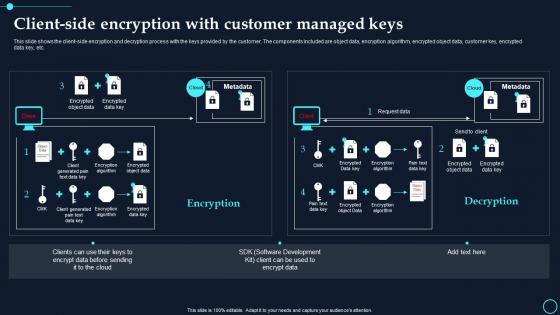 Client Side Encryption With Customer Managed Keys Cloud Data Encryption
Client Side Encryption With Customer Managed Keys Cloud Data EncryptionThis slide shows the client side encryption and decryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encrypted data key, etc. Present the topic in a bit more detail with this Client Side Encryption With Customer Managed Keys Cloud Data Encryption. Use it as a tool for discussion and navigation on Encrypted Object Data, Encryption Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Data Encryption Implementation Plan Table Of Contents
Cloud Data Encryption Implementation Plan Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Cloud Data Encryption Implementation Plan Table Of Contents. This template helps you present information on one stages. You can also present information on Key Challenges, Cloud Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Data Encryption Service Providers Cloud Data Encryption
Cloud Data Encryption Service Providers Cloud Data EncryptionThis slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Present the topic in a bit more detail with this Cloud Data Encryption Service Providers Cloud Data Encryption. Use it as a tool for discussion and navigation on Providers, Reason For Selecting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
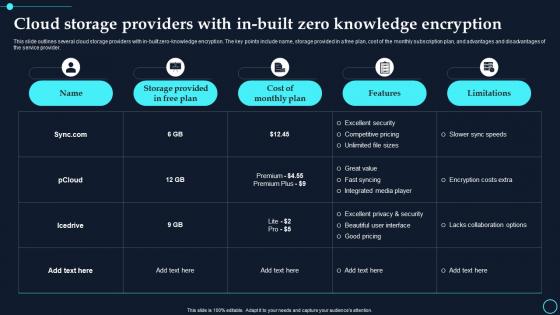 Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data Encryption
Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data EncryptionThis slide outlines several cloud storage providers with in built zero knowledge encryption. The key points include name, storage provided in a free plan, cost of the monthly subscription plan, and advantages and disadvantages of the service provider. Deliver an outstanding presentation on the topic using this Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data Encryption. Dispense information and present a thorough explanation of Storage Provided Free Plan, Cost Of Monthly Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparison Between Cryptomator And Nordlocker Software Cloud Data Encryption
Comparison Between Cryptomator And Nordlocker Software Cloud Data EncryptionThis slide compares the two popular encryption software, named Cryptomator and NordLocker. The comparison is carried out based on several factors, such as encryption method, client side encryption, platforms supported, user interface, pricing, etc. Present the topic in a bit more detail with this Comparison Between Cryptomator And Nordlocker Software Cloud Data Encryption. Use it as a tool for discussion and navigation on Cryptomator, Nordlocker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
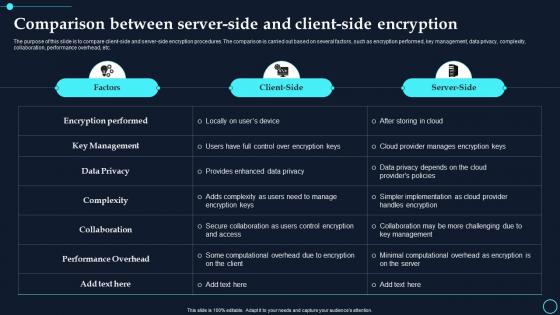 Comparison Between Server-Side And Client Side Encryption Cloud Data Encryption
Comparison Between Server-Side And Client Side Encryption Cloud Data EncryptionThe purpose of this slide is to compare client side and server side encryption procedures. The comparison is carried out based on several factors, such as encryption performed, key management, data privacy, complexity, collaboration, performance overhead, etc. Deliver an outstanding presentation on the topic using this Comparison Between Server Side And Client Side Encryption Cloud Data Encryption. Dispense information and present a thorough explanation of Encryption Performed, Key Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Considerations For Zero Knowledge Encryption Service Selection Cloud Data Encryption
Considerations For Zero Knowledge Encryption Service Selection Cloud Data EncryptionThe purpose of this slide is to highlight the several factors to be considered while selecting zero knowledge encryption service providers. The main discussed factors are storage space, privacy and security, price, and other perks. Present the topic in a bit more detail with this Considerations For Zero Knowledge Encryption Service Selection Cloud Data Encryption. Use it as a tool for discussion and navigation on Storage Space, Privacy And Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
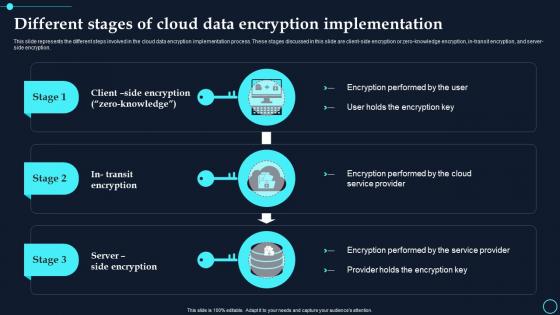 Different Stages Of Cloud Data Encryption Implementation Cloud Data Encryption
Different Stages Of Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the different steps involved in the cloud data encryption implementation process. These stages discussed in this slide are client side encryption or zero knowledge encryption, in transit encryption, and server side encryption. Increase audience engagement and knowledge by dispensing information using Different Stages Of Cloud Data Encryption Implementation Cloud Data Encryption. This template helps you present information on three stages. You can also present information on Encryption Performed, Service Provider using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
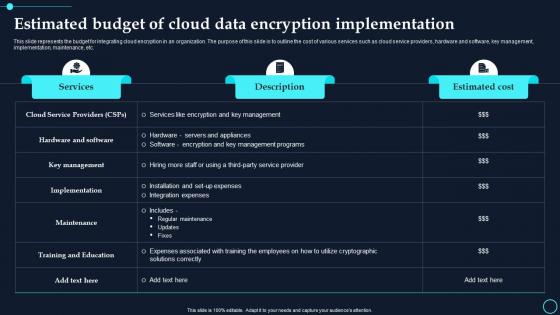 Estimated Budget Of Cloud Data Encryption Implementation Cloud Data Encryption
Estimated Budget Of Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the budget for integrating cloud encryption in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. Present the topic in a bit more detail with this Estimated Budget Of Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Services, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
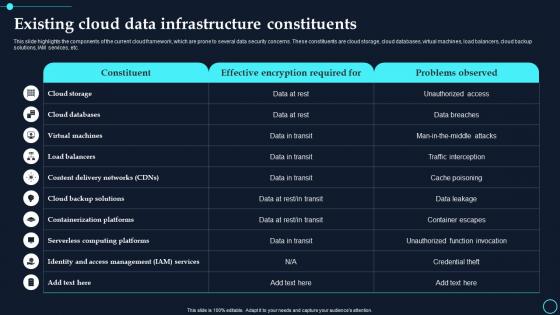 Existing Cloud Data Infrastructure Constituents Cloud Data Encryption
Existing Cloud Data Infrastructure Constituents Cloud Data EncryptionThis slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc. Deliver an outstanding presentation on the topic using this Existing Cloud Data Infrastructure Constituents Cloud Data Encryption. Dispense information and present a thorough explanation of Cloud Storage, Cloud Databases using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide Cloud Data Encryption Implementation Plan
Icons Slide Cloud Data Encryption Implementation PlanIntroducing our well researched set of slides titled Icons Slide Cloud Data Encryption Implementation Plan. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption
Impact Of Encryption Implementation On Cloud Security Cloud Data EncryptionThis slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
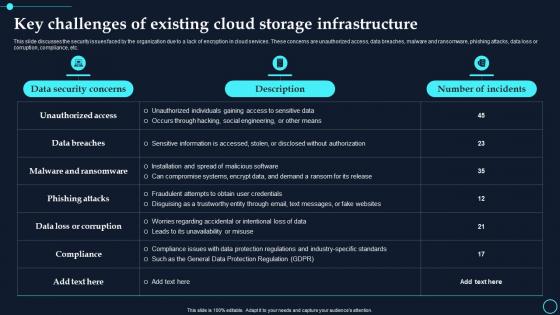 Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data Encryption
Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data EncryptionThis slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc. Present the topic in a bit more detail with this Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data Encryption. Use it as a tool for discussion and navigation on Data Security Concerns, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data Encryption
Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data EncryptionThe purpose of this slide is to discuss the challenges faced while encrypting cloud data. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies. Deliver an outstanding presentation on the topic using this Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data Encryption. Dispense information and present a thorough explanation of Probability, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
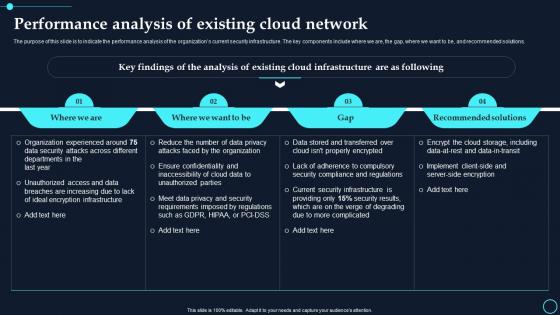 Performance Analysis Of Existing Cloud Network Cloud Data Encryption
Performance Analysis Of Existing Cloud Network Cloud Data EncryptionThe purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Present the topic in a bit more detail with this Performance Analysis Of Existing Cloud Network Cloud Data Encryption. Use it as a tool for discussion and navigation on Where We Are, Where We Want To Be. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
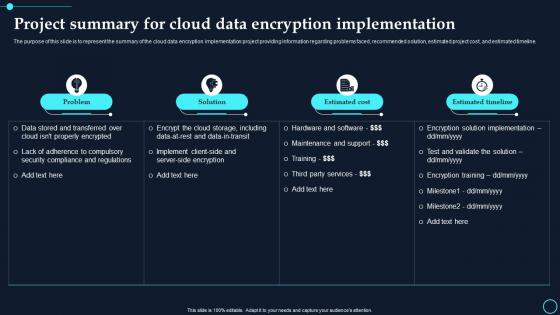 Project Summary For Cloud Data Encryption Implementation Cloud Data Encryption
Project Summary For Cloud Data Encryption Implementation Cloud Data EncryptionThe purpose of this slide is to represent the summary of the cloud data encryption implementation project providing information regarding problems faced, recommended solution, estimated project cost, and estimated timeline. Deliver an outstanding presentation on the topic using this Project Summary For Cloud Data Encryption Implementation Cloud Data Encryption. Dispense information and present a thorough explanation of Problem, Solution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data Encryption
Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data EncryptionThis slide shows the matrix to assign multiple responsibilities to the different team members for the cloud data encryption implementation project. The responsibilities include problem assessment, solution selection, encryption implementation, etc. Present the topic in a bit more detail with this Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data Encryption. Use it as a tool for discussion and navigation on Problem Assessment, Solution Selection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
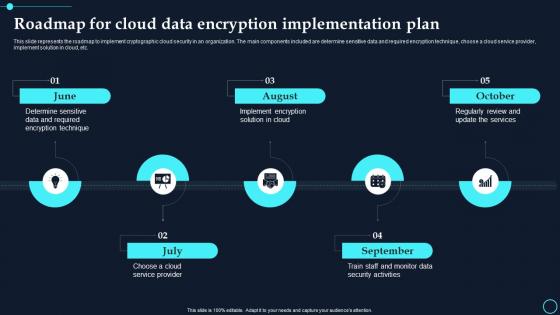 Roadmap For Cloud Data Encryption Implementation Plan Cloud Data Encryption
Roadmap For Cloud Data Encryption Implementation Plan Cloud Data EncryptionThis slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc.Increase audience engagement and knowledge by dispensing information using Roadmap For Cloud Data Encryption Implementation Plan Cloud Data Encryption. This template helps you present information on five stages. You can also present information on August, October using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
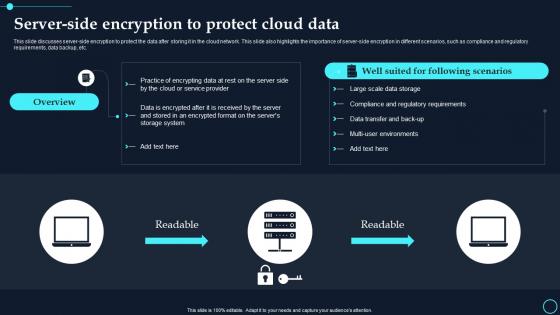 Server Side Encryption To Protect Cloud Data Cloud Data Encryption
Server Side Encryption To Protect Cloud Data Cloud Data EncryptionThis slide discusses server side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of server side encryption in different scenarios, such as compliance and regulatory requirements, data backup, etc. Present the topic in a bit more detail with this Server Side Encryption To Protect Cloud Data Cloud Data Encryption. Use it as a tool for discussion and navigation on Readable, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Server Side Encryption With Customer Managed Keys Cloud Data Encryption
Server Side Encryption With Customer Managed Keys Cloud Data EncryptionThis slide demonstrates the server side encryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encryption, decryption, etc. Deliver an outstanding presentation on the topic using this Server Side Encryption With Customer Managed Keys Cloud Data Encryption. Dispense information and present a thorough explanation of Customer Key, Encryption Algorithm using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
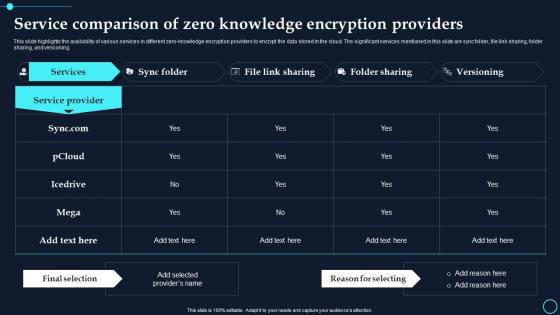 Service Comparison Of Zero Knowledge Encryption Providers Cloud Data Encryption
Service Comparison Of Zero Knowledge Encryption Providers Cloud Data EncryptionThis slide highlights the availability of various services in different zero knowledge encryption providers to encrypt the data stored in the cloud. The significant services mentioned in this slide are sync folder, file link sharing, folder sharing, and versioning. Deliver an outstanding presentation on the topic using this Service Comparison Of Zero Knowledge Encryption Providers Cloud Data Encryption. Dispense information and present a thorough explanation of Service Provider, Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
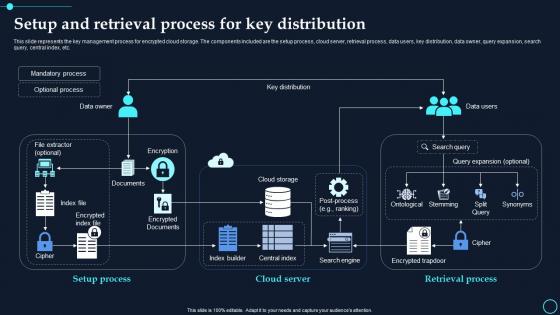 Setup And Retrieval Process For Key Distribution Cloud Data Encryption
Setup And Retrieval Process For Key Distribution Cloud Data EncryptionThis slide represents the key management process for encrypted cloud storage. The components included are the setup process, cloud server, retrieval process, data users, key distribution, data owner, query expansion, search query, central index, etc. Present the topic in a bit more detail with this Setup And Retrieval Process For Key Distribution Cloud Data Encryption. Use it as a tool for discussion and navigation on Mandatory Process, Optional Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Cloud Data Encryption Implementation Plan
Table Of Contents Cloud Data Encryption Implementation PlanIncrease audience engagement and knowledge by dispensing information using Table Of Contents Cloud Data Encryption Implementation Plan. This template helps you present information on one stages. You can also present information on Existing Cloud Data, Infrastructure Constituents using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.


