Ethical hacking it powerpoint presentation slides
This PowerPoint presentation gives a brief idea about the ethical hacking training provider company, problems that ethical hackers can solve, and reasons to choose ethical hacking as a profession. Here is an efficiently designed Ethical Hacking IT template. We have covered skills required to become an ethical hacker, including roles, responsibilities, description, and an overview of hacking and ethical hacking by including the need, purpose, types, and legality of ethical hacking. Moreover, in this Ethical Hacking and Network Security slides, we have included fundamental concepts of ethical hacking, benefits, limitation of ethical hacking, different types of ethical hackers, and critical vulnerabilities found by them. In addition, this Ethical Hacking PPT contains other ethical hacking techniques, various phases of ethical hacking such as surveillance, scanning, gaining access, maintaining access, clearing tracks, and best ethical hacking tools and software. Furthermore, this Ethical Hacking and Network Security template compares white and black hat hackers and ethical hacking and penetration testing. Lastly, this deck comprises a timeline, a roadmap, and a dashboard for ethical hacking. Download our 100 percent editable and customizable Hacking it ppt now.
This PowerPoint presentation gives a brief idea about the ethical hacking training provider company, problems that ethical ..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver an informational PPT on various topics by using this Ethical Hacking IT Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with eighty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Ethical Hacking (IT). State Your Company Name and begin.
Slide 2: This slide presents Agenda for Ethical Hacking.
Slide 3: This slide displays Table of Contents for Ethical Hacking.
Slide 4: This is another slide continuing Table of Contents for Ethical Hacking.
Slide 5: This slide highlights title for topics that are to be covered next in the template.
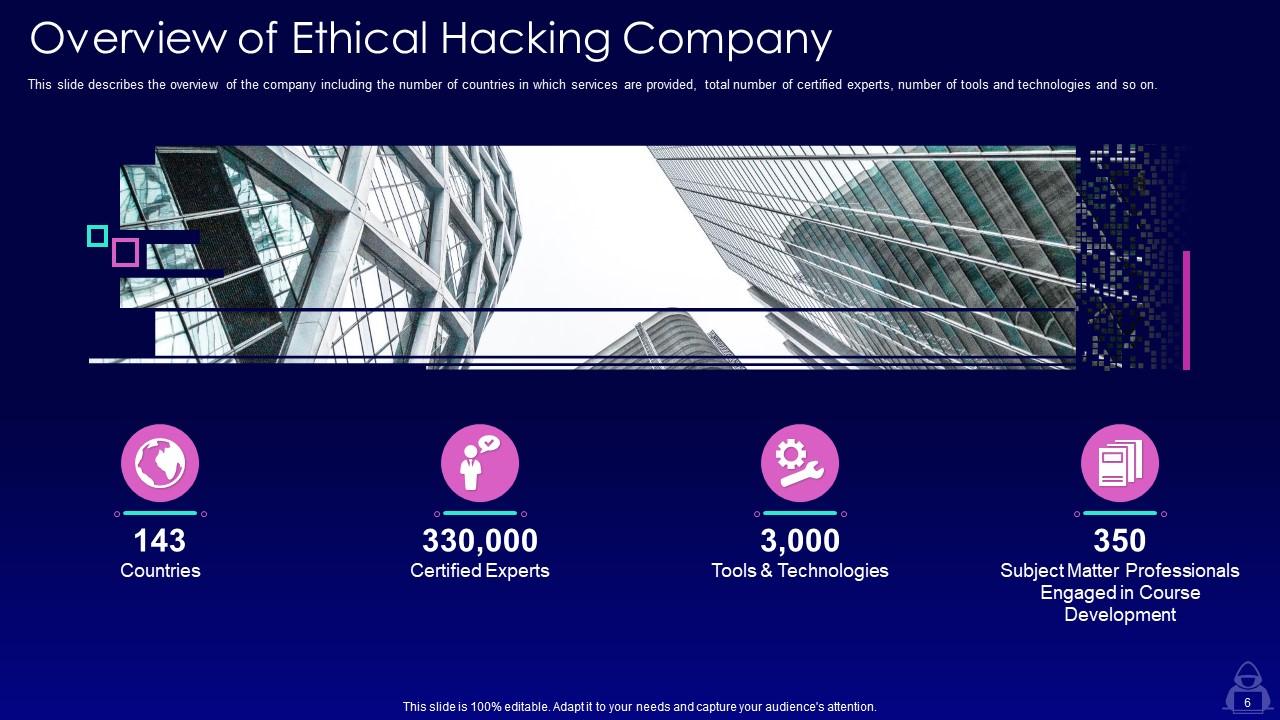
Slide 6: This slide describes the overview of the company including the number of countries in which services are provided.
Slide 7: This slide highlights title for topics that are to be covered next in the template.
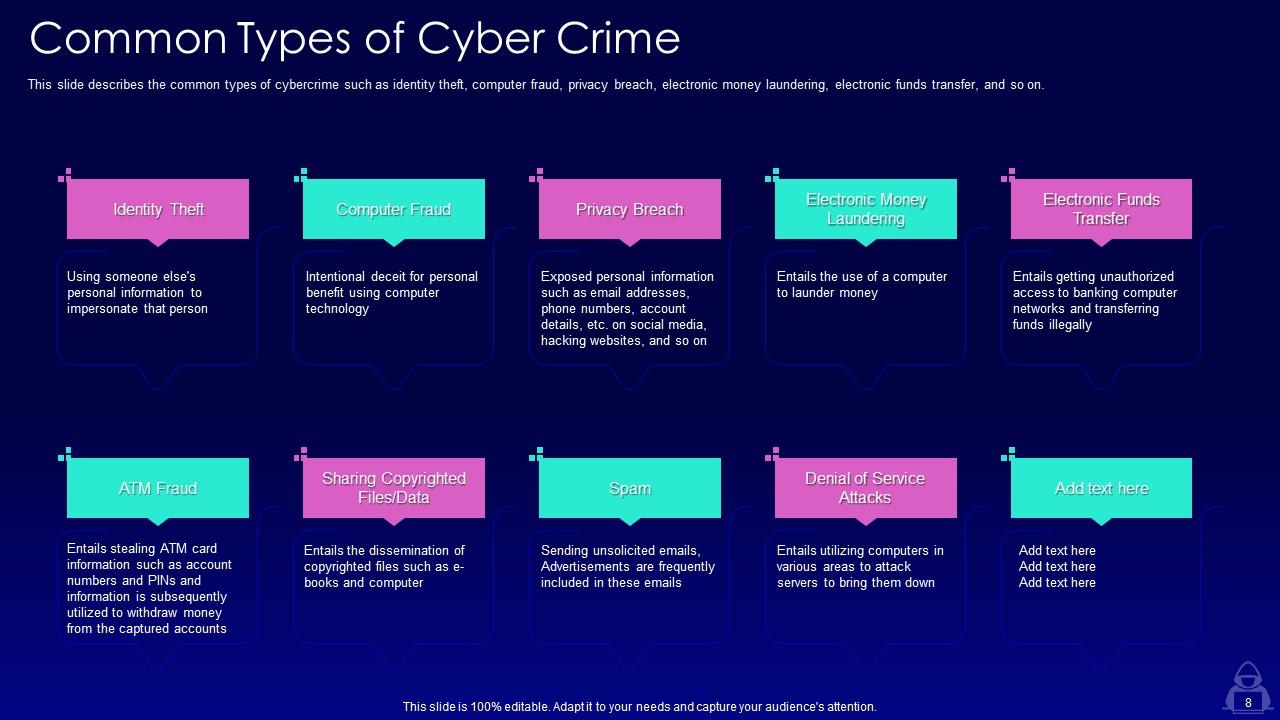
Slide 8: This slide presents common types of cybercrime such as identity theft, computer fraud, privacy breach, etc.
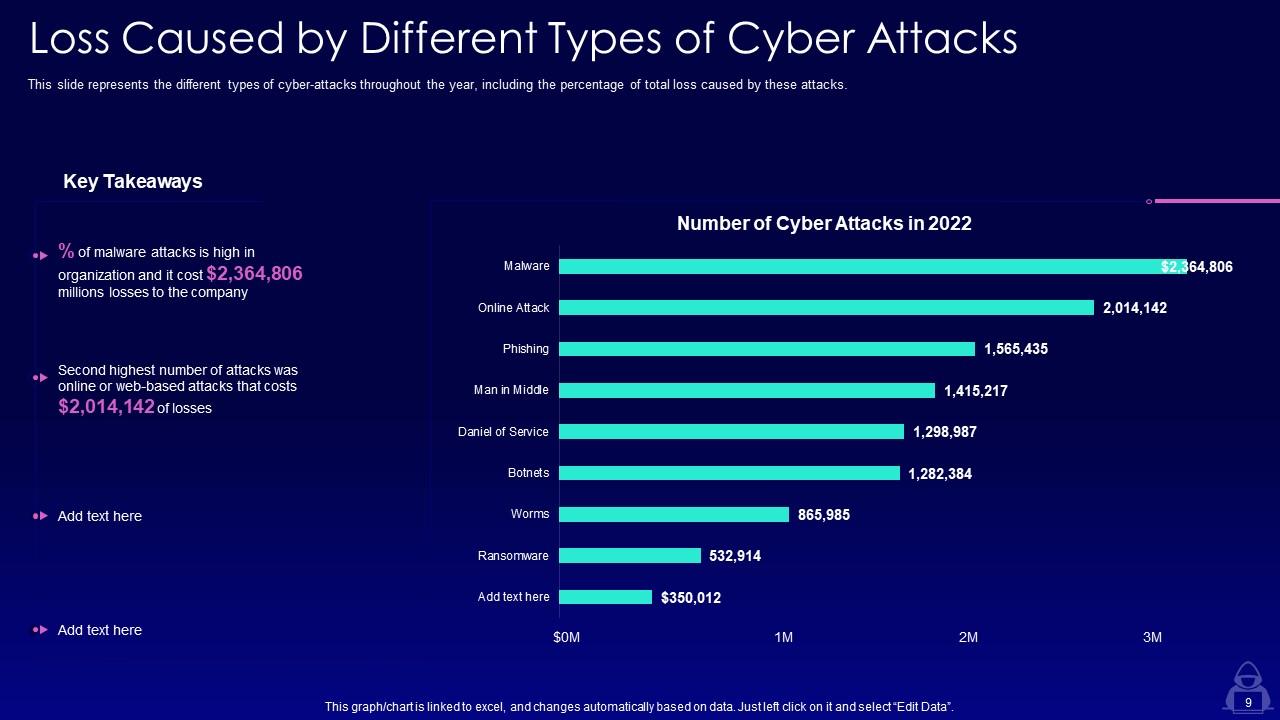
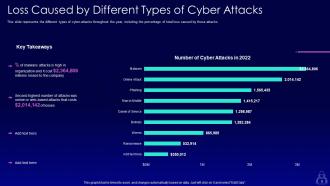
Slide 9: This slide displays Loss Caused by Different Types of Cyber Attacks.
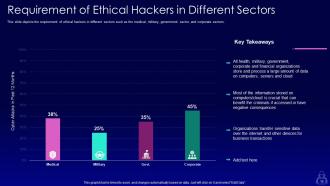
Slide 10: This slide represents Requirement of Ethical Hackers in Different Sectors.
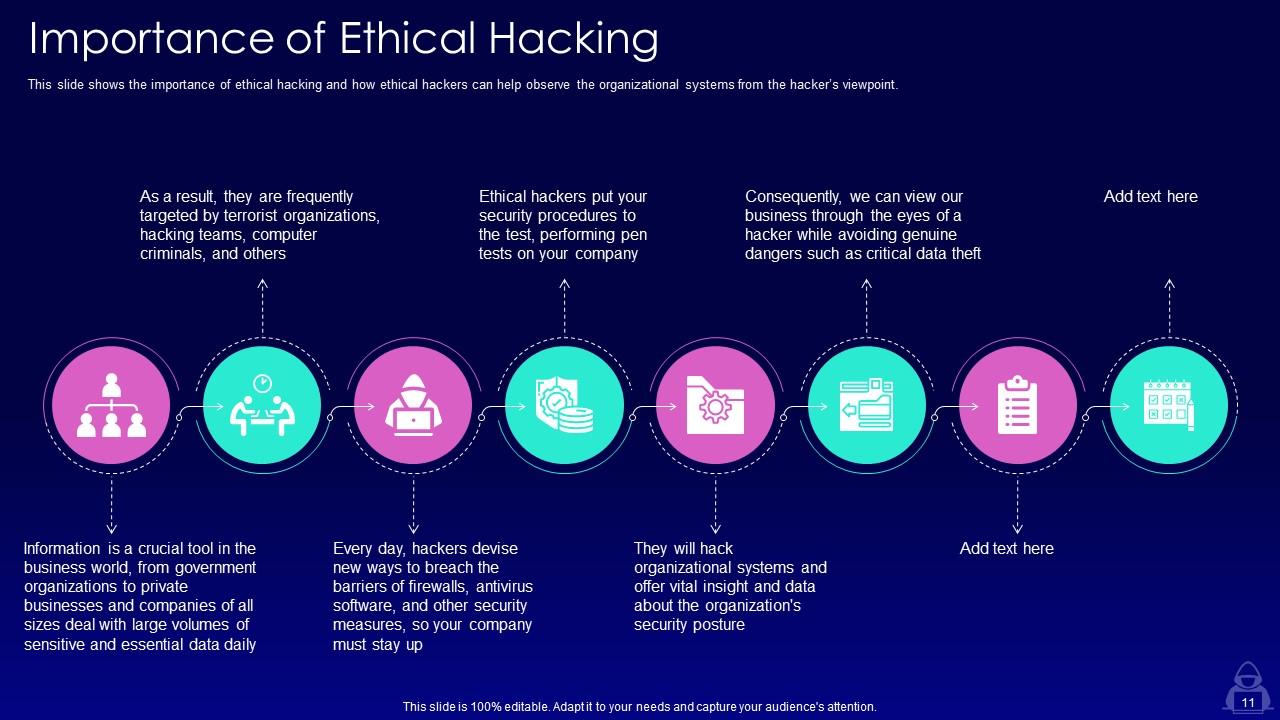
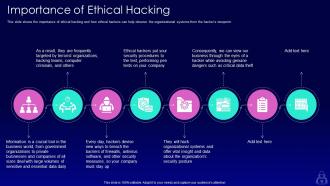
Slide 11: This slide shows the importance of ethical hacking and how ethical hackers can help observe the organizational systems from the hacker’s viewpoint.
Slide 12: This slide highlights title for topics that are to be covered next in the template.
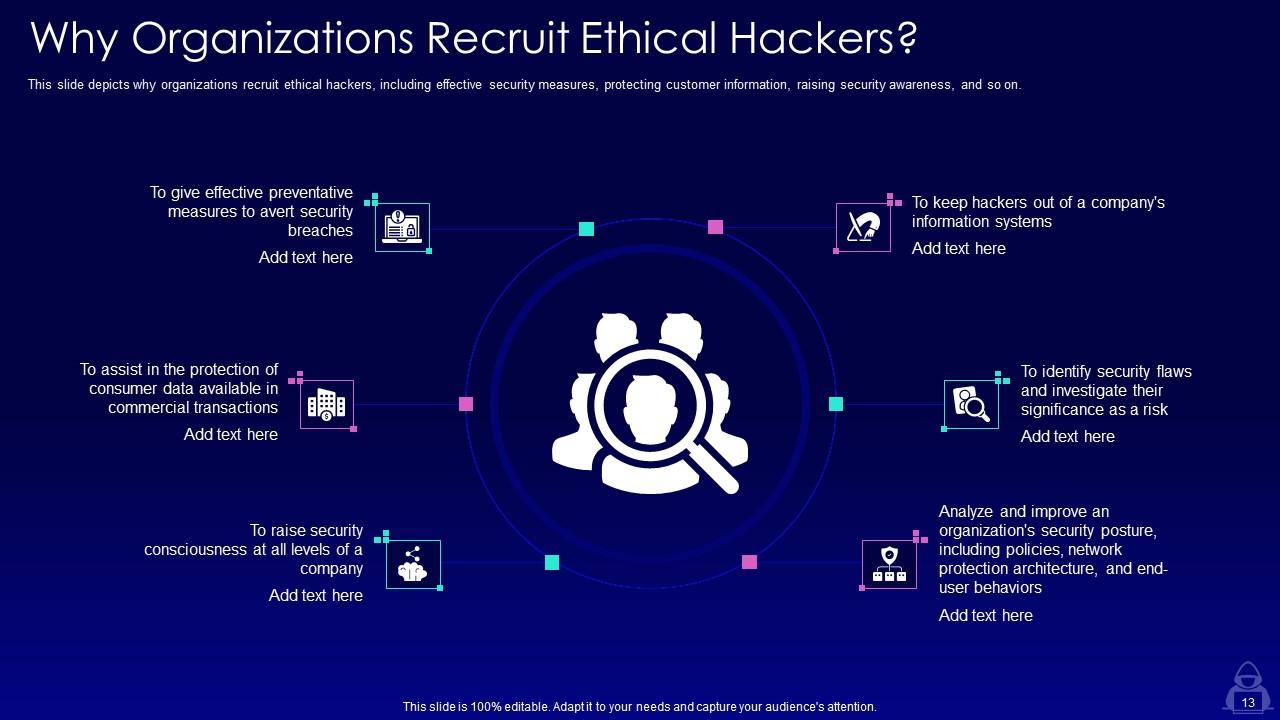
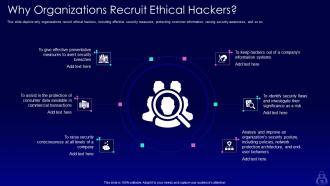
Slide 13: This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, etc.
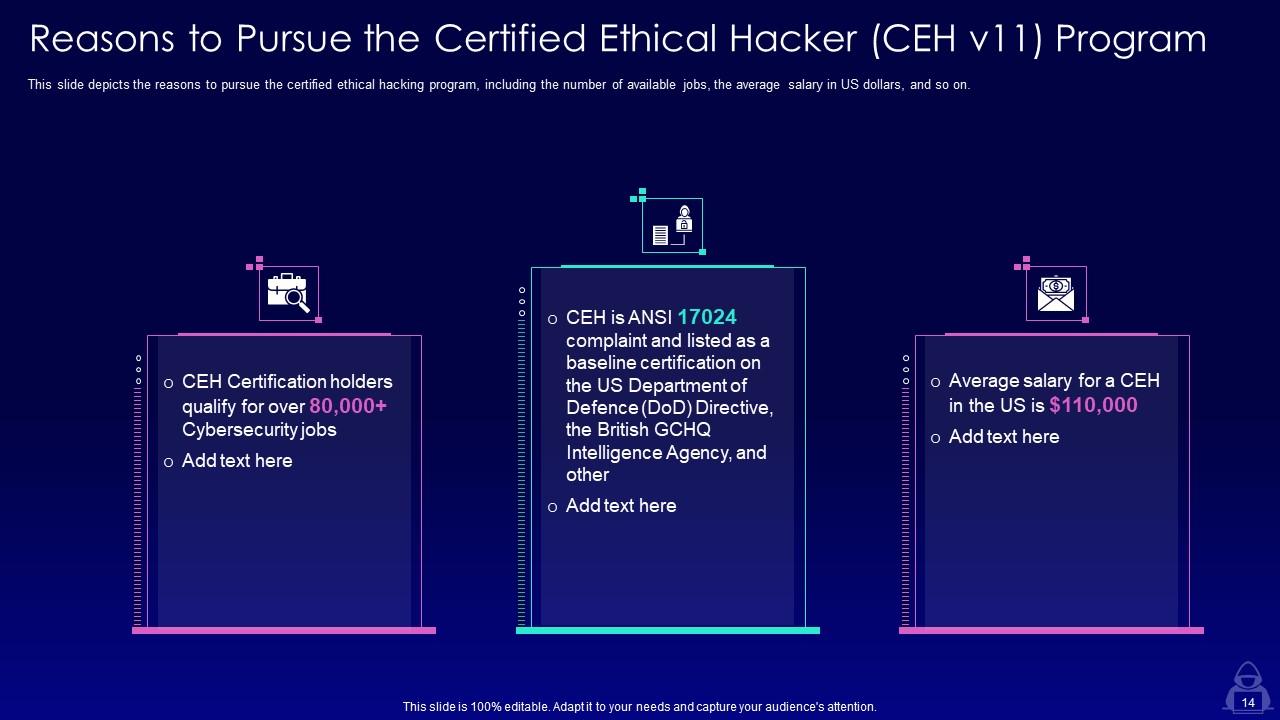
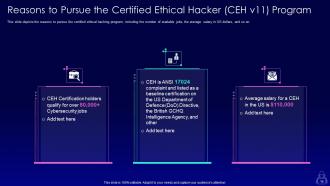
Slide 14: This slide showcases Reasons to Pursue the Certified Ethical Hacker (CEH v11) Program.
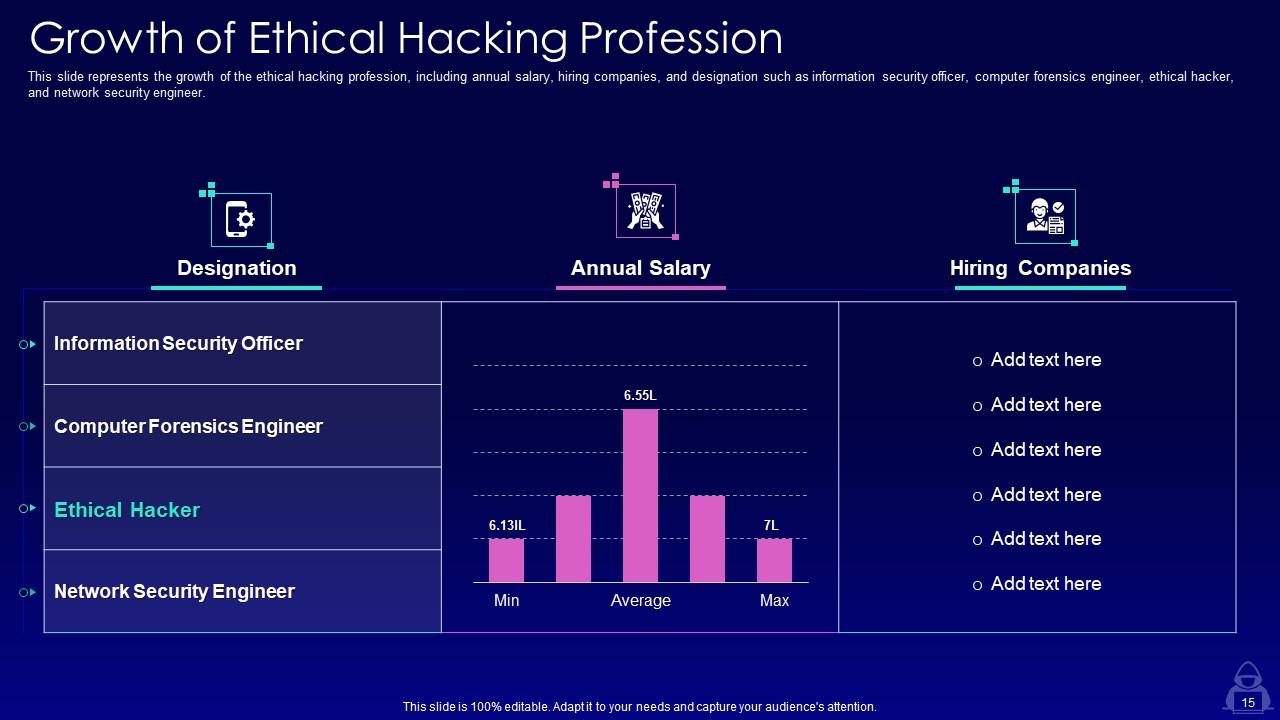
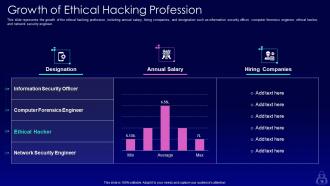
Slide 15: This slide represents the growth of the ethical hacking profession, including annual salary, hiring companies, and designation.
Slide 16: This slide highlights title for topics that are to be covered next in the template.
Slide 17: This slide presents Skills and Certifications Required for Ethical Hacker.
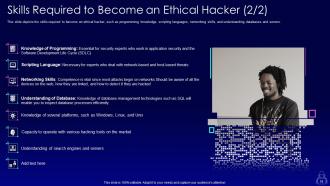
Slide 18: This is another slide continuing Skills Required to Become an Ethical Hacker.
Slide 19: This slide depicts the roles and responsibilities of ethical hackers, including preventing future attacks by recognizing open ports.
Slide 20: This slide highlights title for topics that are to be covered next in the template.
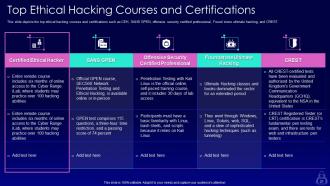
Slide 21: This slide presents top ethical hacking courses and certifications such as CEH, SANS GPEN, offensive security certified professional, etc.
Slide 22: This slide represents the overview of the ethical hacking course, including the significant benefits, skills covered and the key features.
Slide 23: This slide showcases ethical hacking training options including online bootcamp and corporate training.
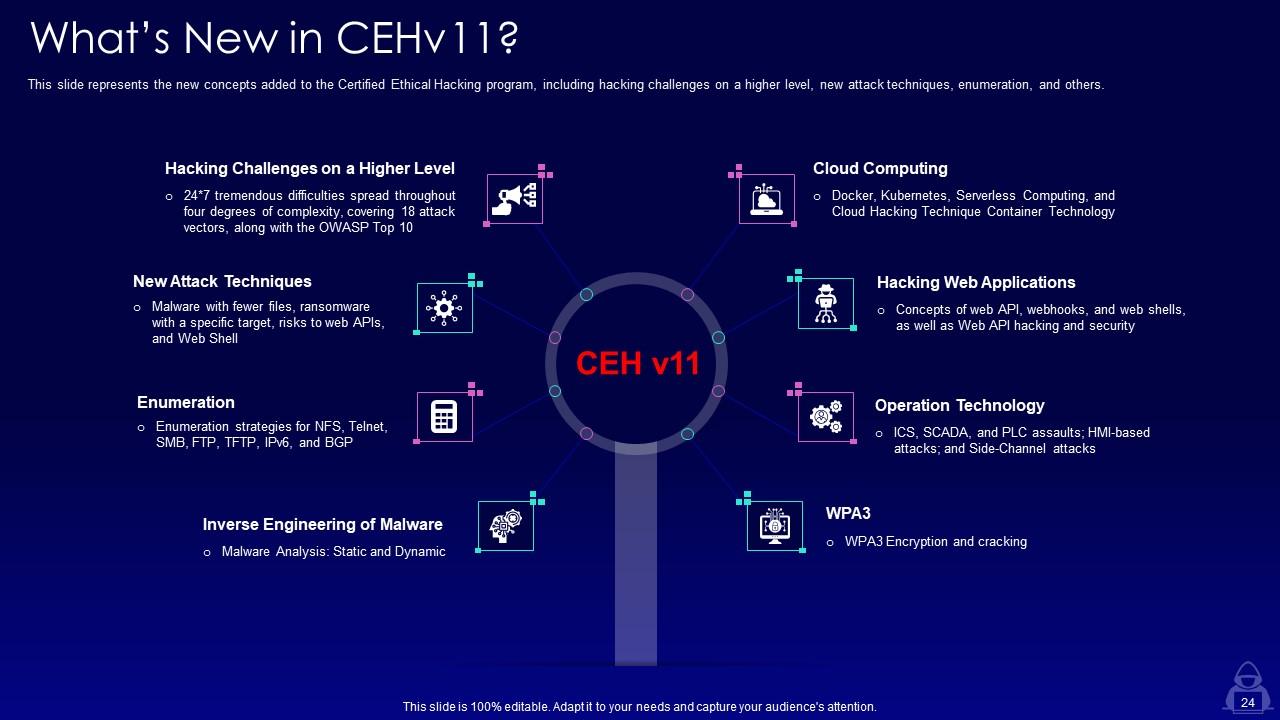
Slide 24: This slide represents the new concepts added to the Certified Ethical Hacking program.
Slide 25: This slide highlights title for topics that are to be covered next in the template.
Slide 26: This slide illustrates what hacking is and how businesses are getting affected by it every year.
Slide 27: This slide depicts ethical hacking and how ethical hackers could be an asset to a company.
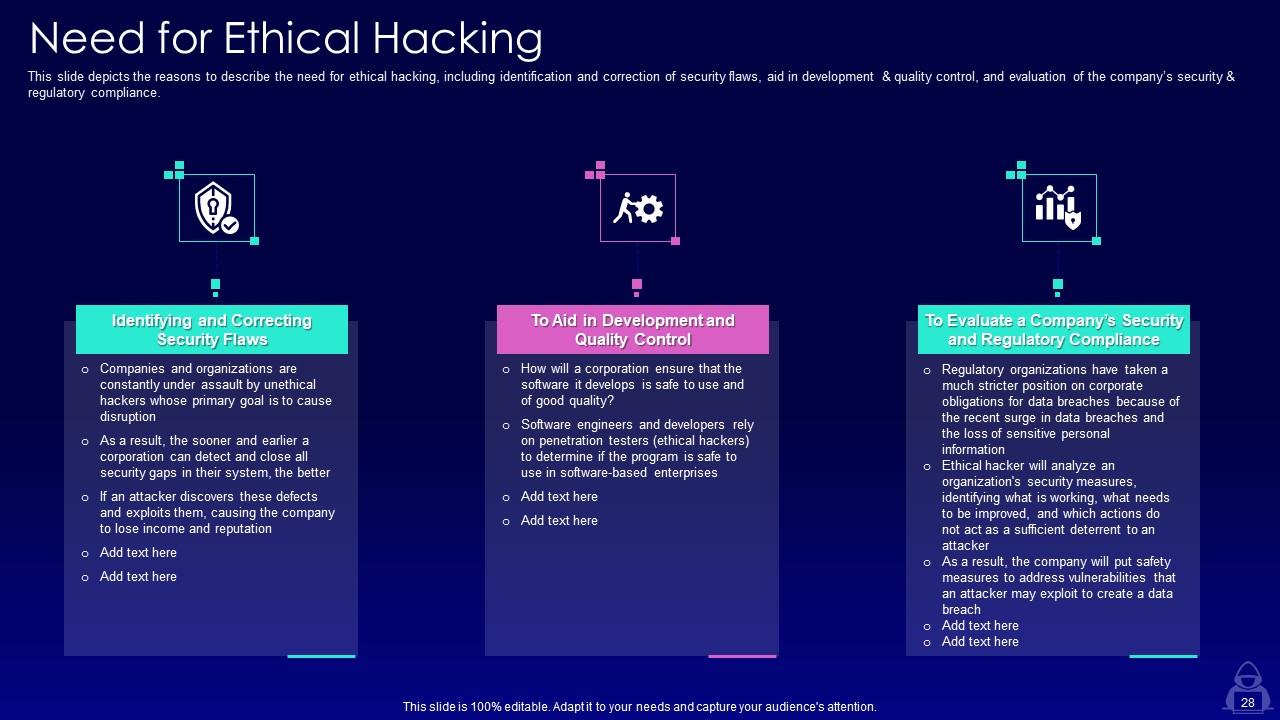
Slide 28: This slide represents reasons to describe the need for ethical hacking, including identification and correction of security flaws.
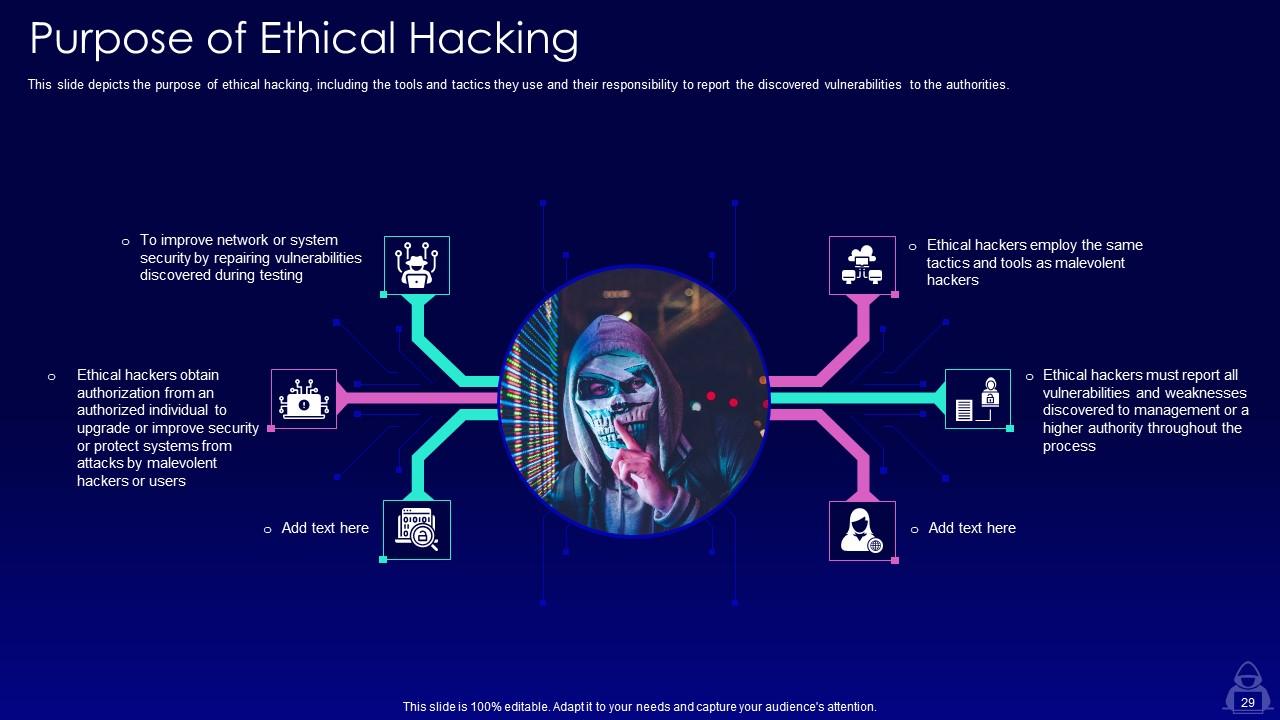
Slide 29: This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report.
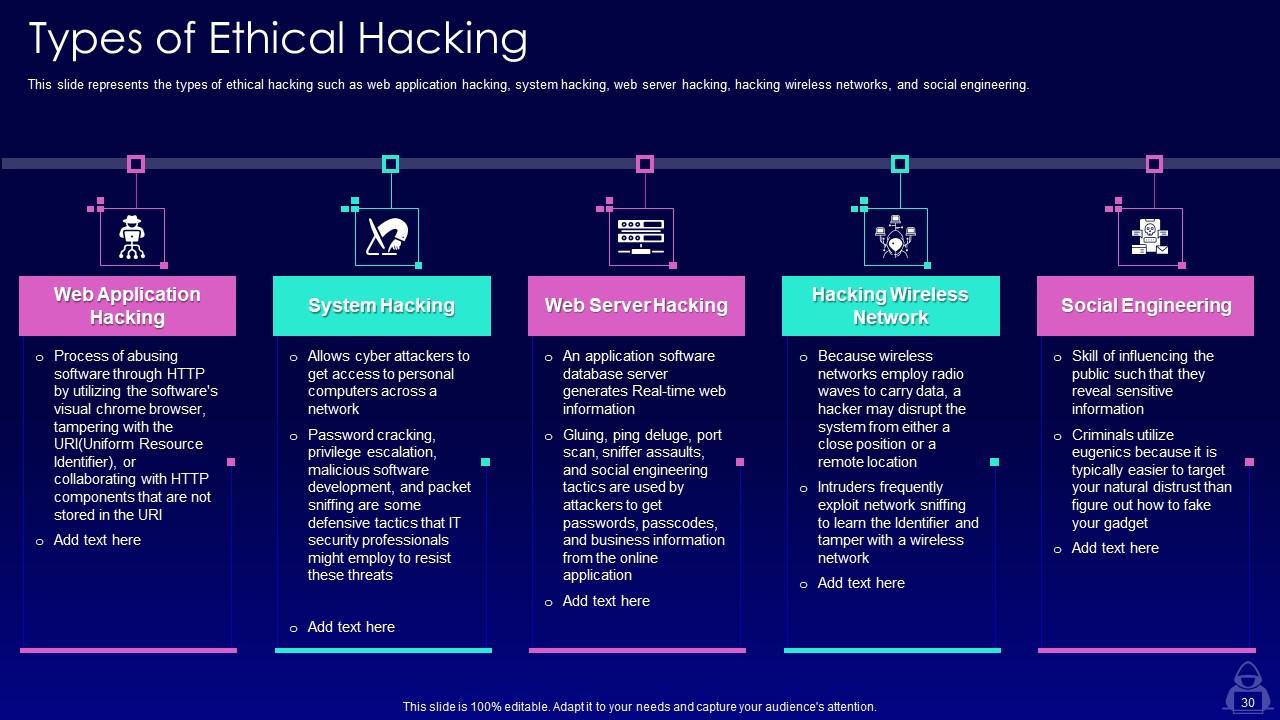
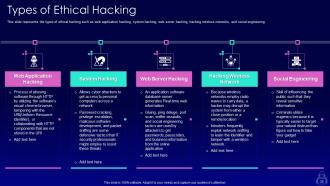
Slide 30: This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, etc.
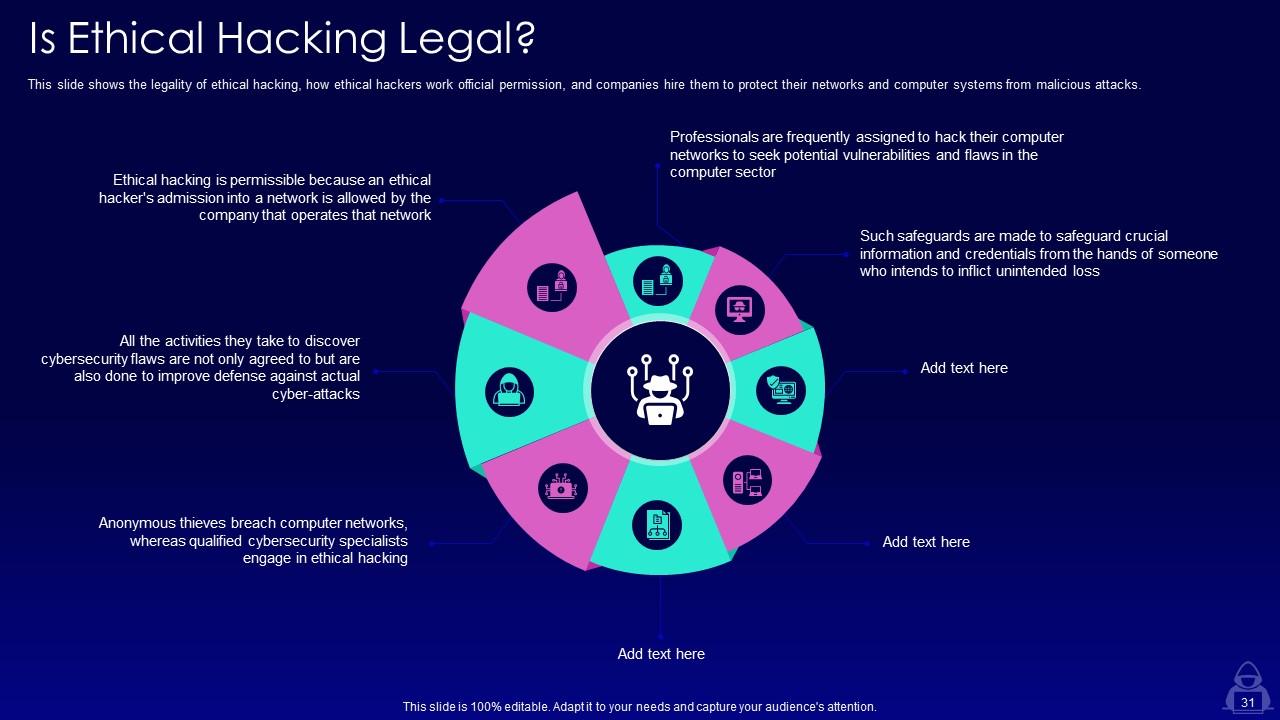
Slide 31: This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks.
Slide 32: This slide highlights title for topics that are to be covered next in the template.
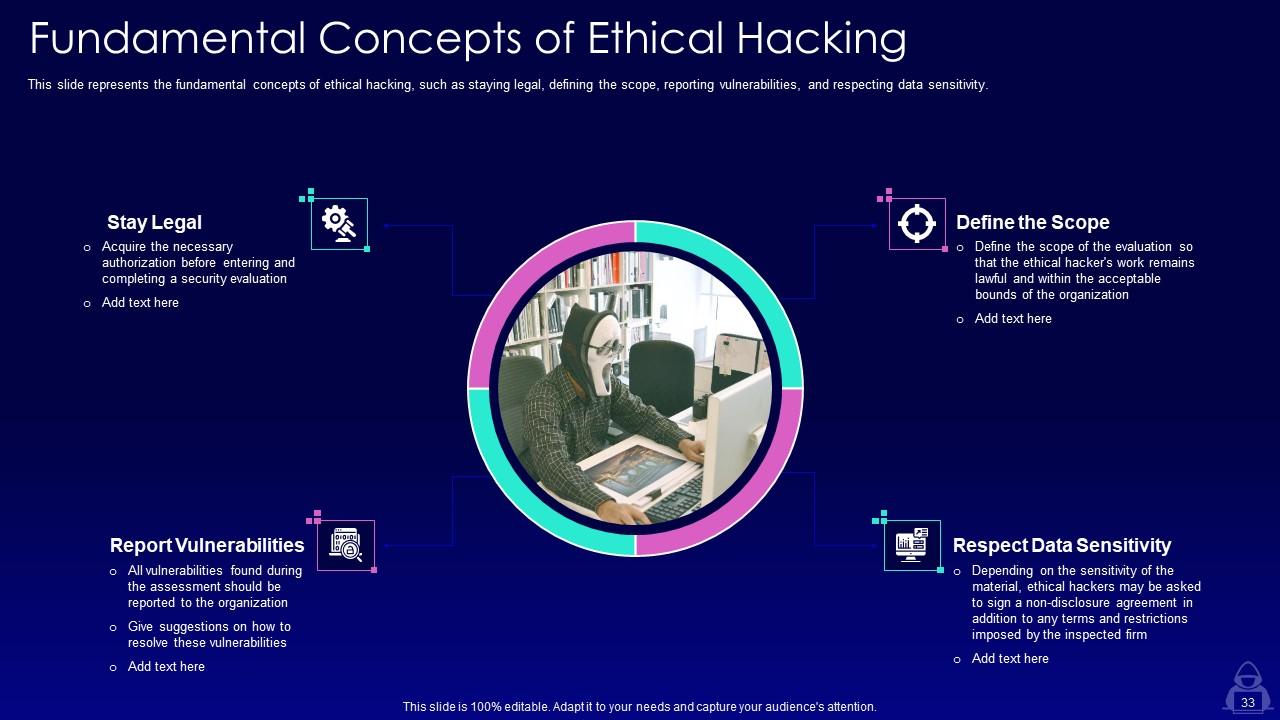
Slide 33: This slide represents the fundamental concepts of ethical hacking, such as staying legal, defining the scope, reporting vulnerabilities, etc.
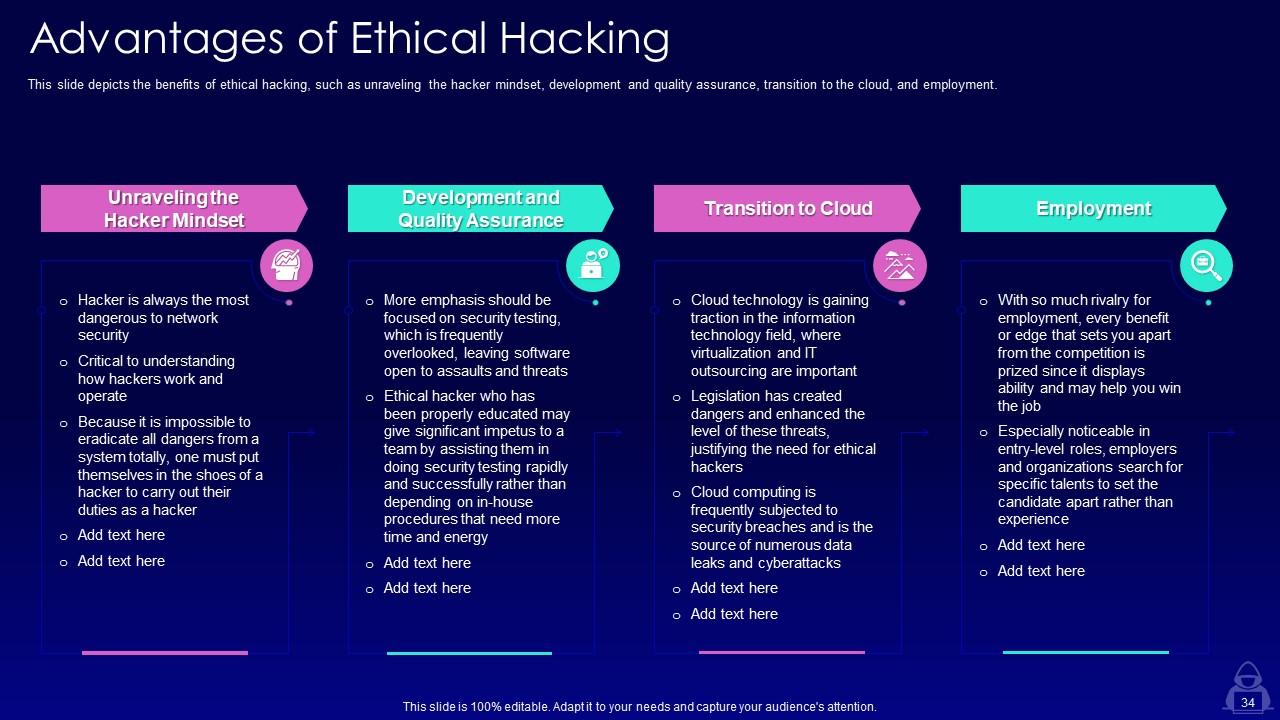
Slide 34: This slide depicts the benefits of ethical hacking, such as unraveling the hacker mindset, development and quality assurance.
Slide 35: This slide showcases benefits of ethical hacking to the companies, including testing security, identifying weaknesses, understanding hacker methods, etc.
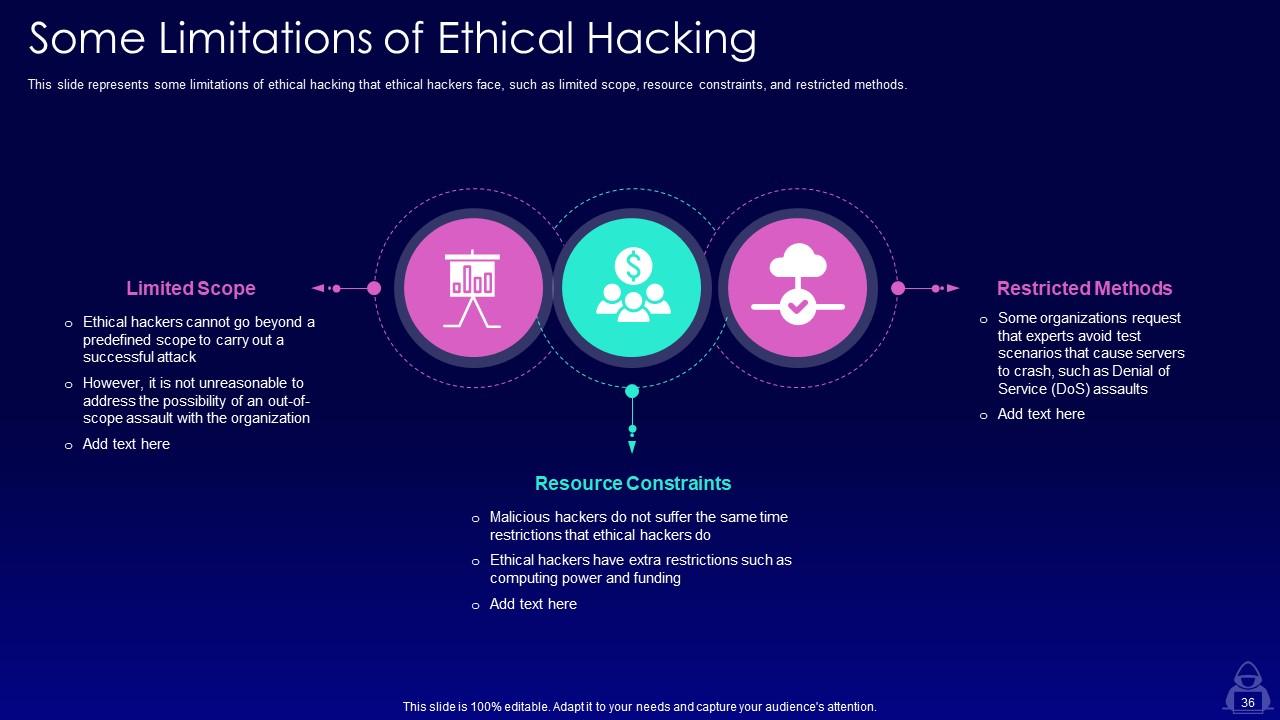
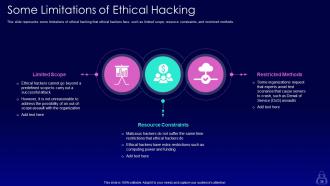
Slide 36: This slide represents some limitations of ethical hacking that ethical hackers face, such as limited scope, resource constraints, and restricted methods.
Slide 37: This slide highlights title for topics that are to be covered next in the template.
Slide 38: This slide describes the black hat hackers and how they can take advantage of a vulnerability in a software, network, and computer system.
Slide 39: This slide represents the white hat or ethical hackers and how they test the information systems of the organizations.
Slide 40: This slide depicts the grey hat hackers and how they first hack any system, computer, software, or network and then ask for permission.
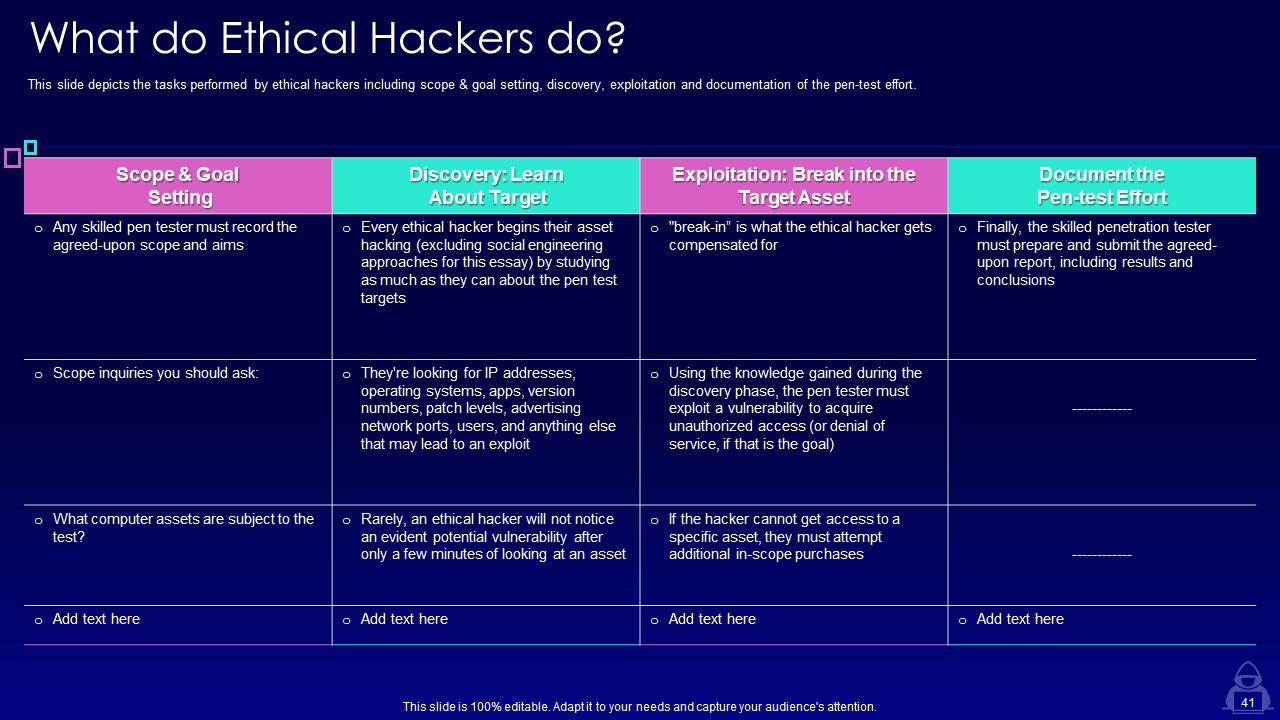
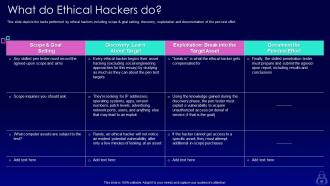
Slide 41: This slide presents tasks performed by ethical hackers including scope & goal setting, discovery, exploitation, etc.
Slide 42: This slide represents Key Vulnerabilities that Ethical Hackers Check.
Slide 43: This slide highlights title for topics that are to be covered next in the template.
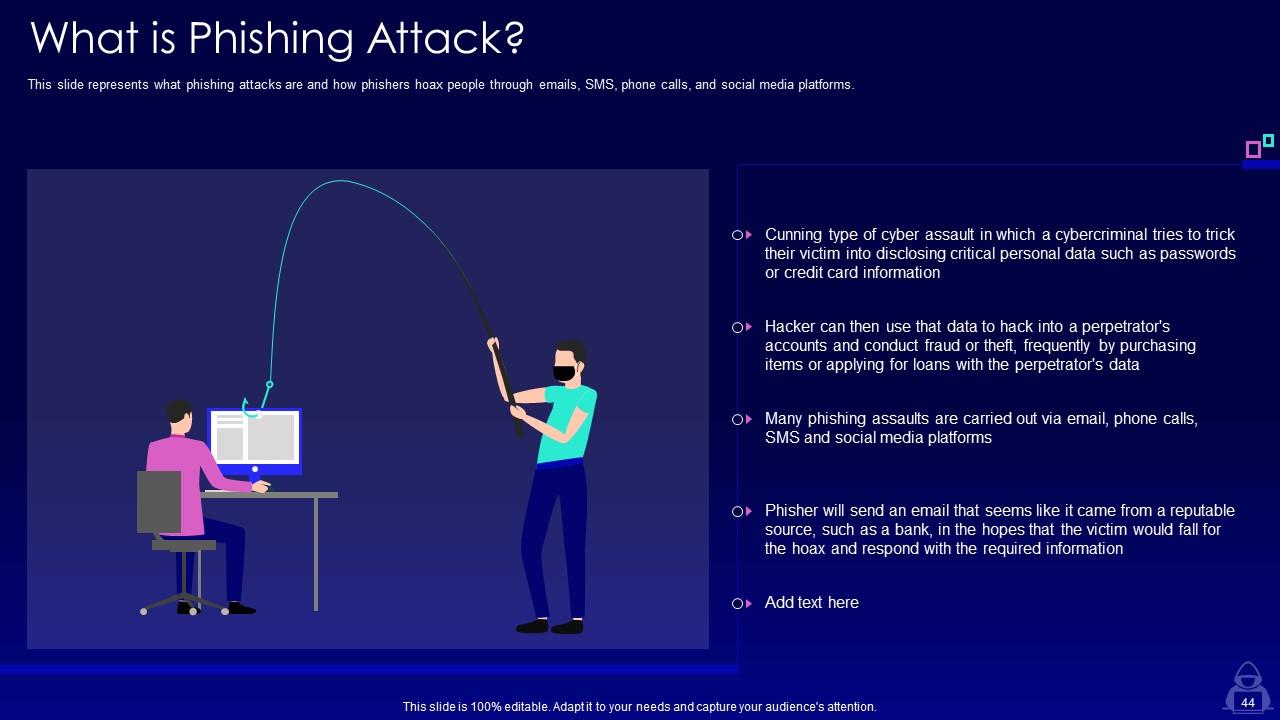
Slide 44: This slide represents what phishing attacks are and how phishers hoax people through emails, SMS, phone calls, and social media platforms.
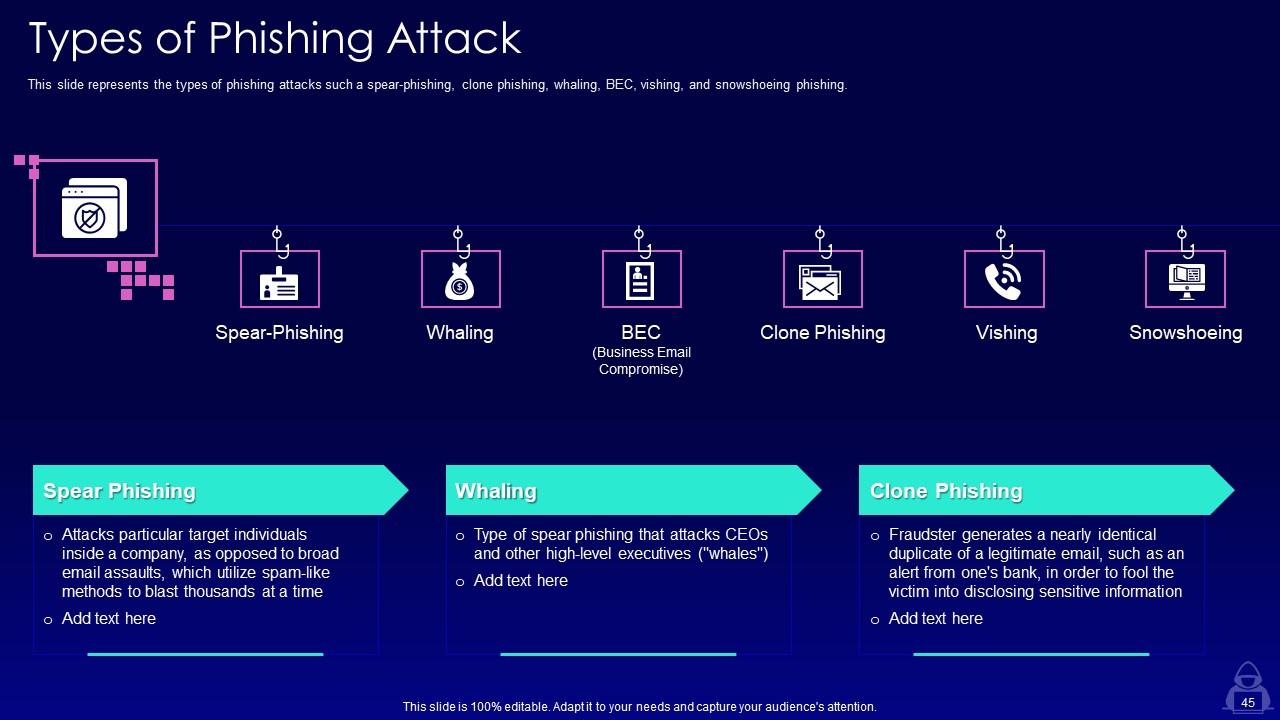
Slide 45: This slide showcases types of phishing attacks such a spear-phishing, clone phishing, whaling, BEC, vishing, and snowshoeing phishing.
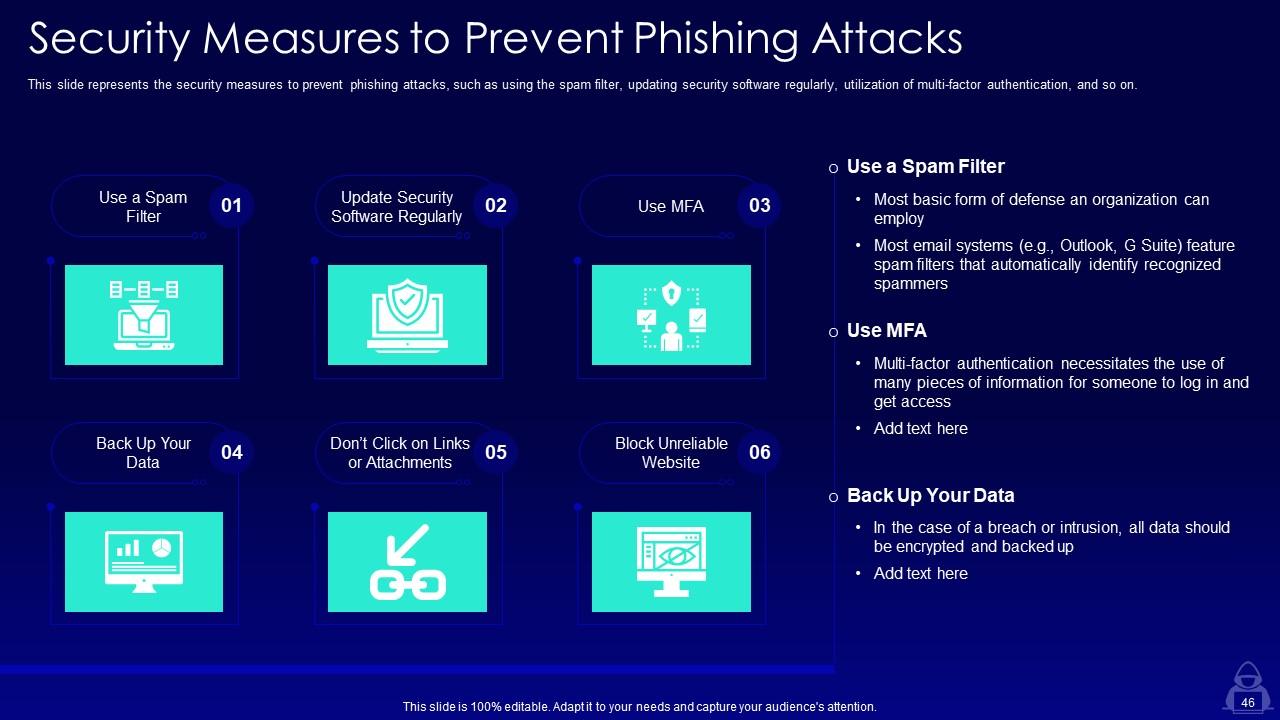
Slide 46: This slide shows Security Measures to Prevent Phishing Attacks.
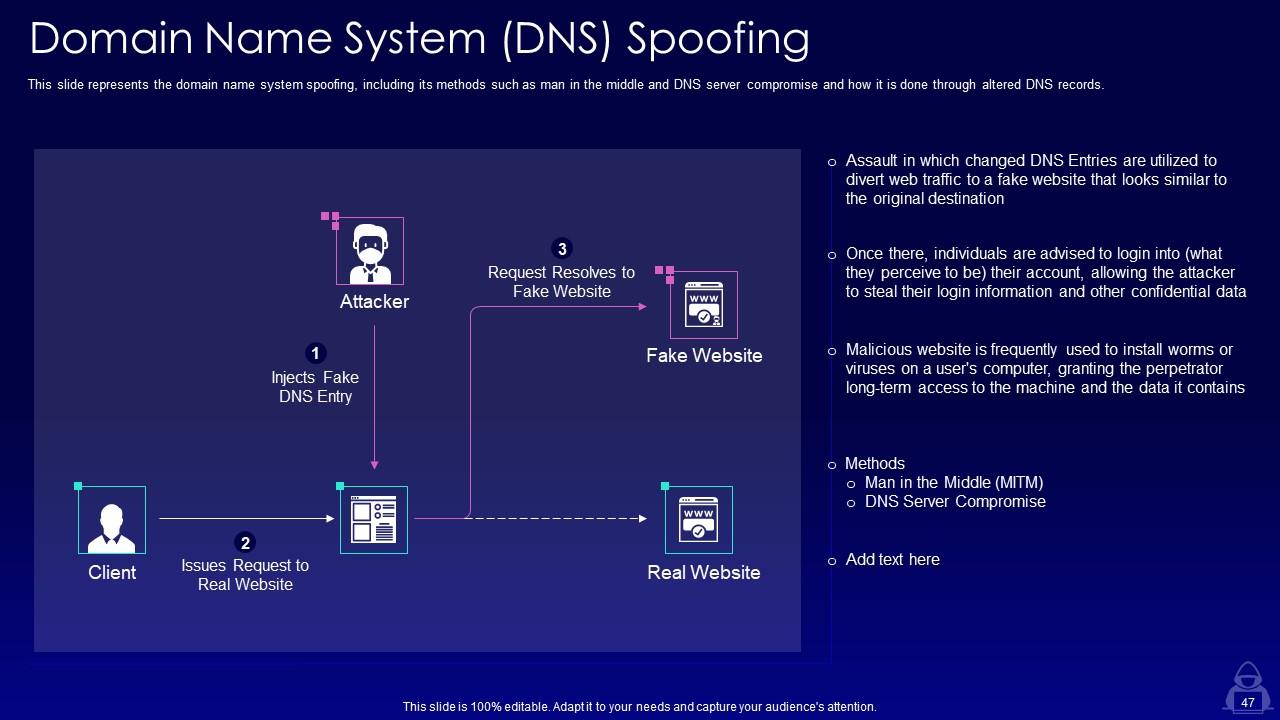
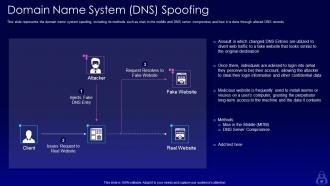
Slide 47: This slide displays domain name system spoofing, including its methods such as man in the middle and DNS server compromise.
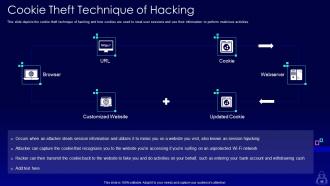
Slide 48: This slide depicts the cookie theft technique of hacking and how cookies are used to steal user sessions.
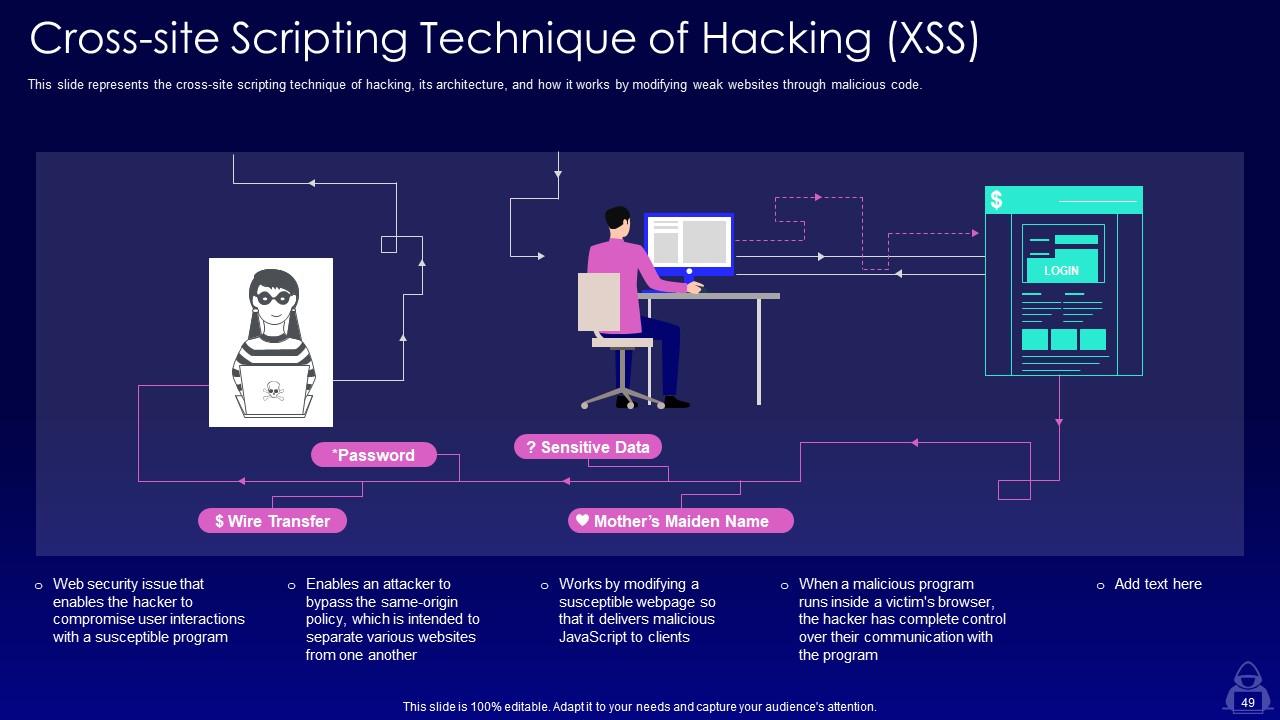
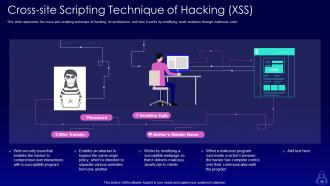
Slide 49: This slide represents the cross-site scripting technique of hacking, its architecture, and how it works by modifying weak websites through malicious code.
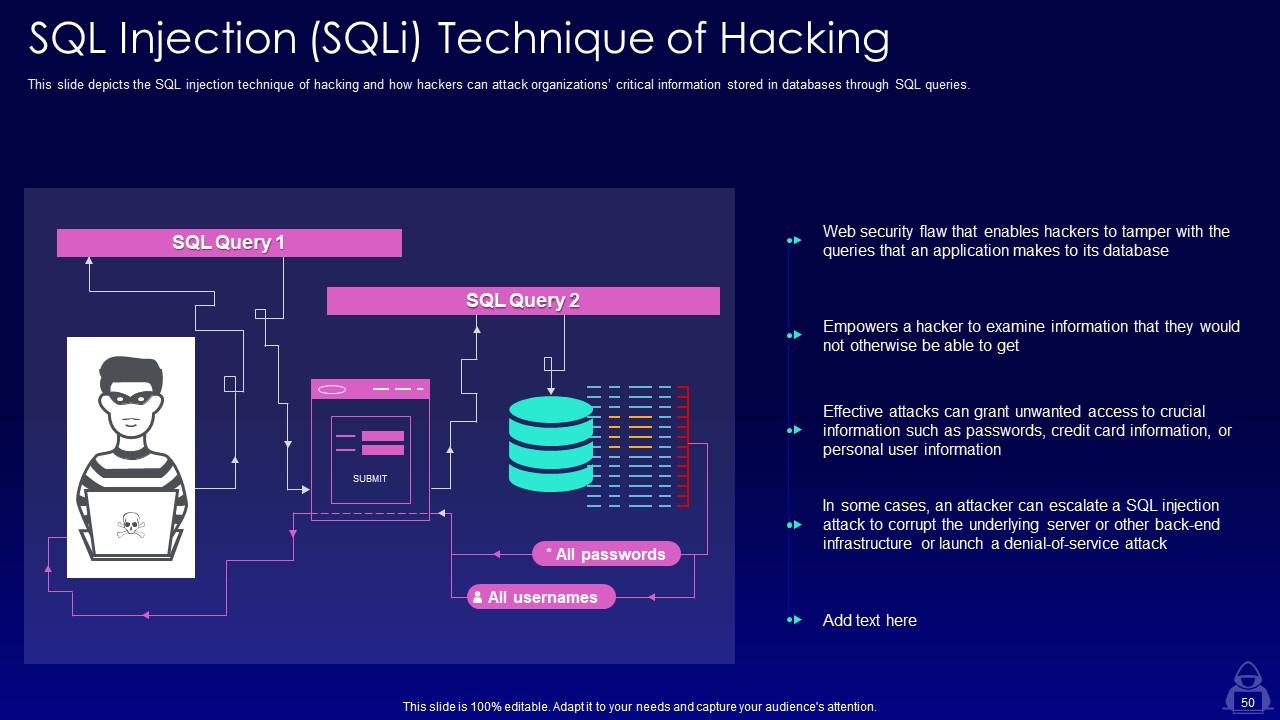
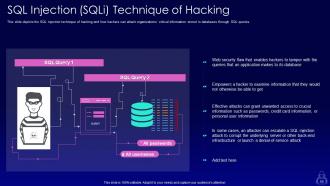
Slide 50: This slide depicts the SQL injection technique of hacking and how hackers can attack organizations’ critical information.
Slide 51: This slide represents techniques of ethical hacking such as port scanning, analyzing and sniffing network traffic.
Slide 52: This slide highlights title for topics that are to be covered next in the template.
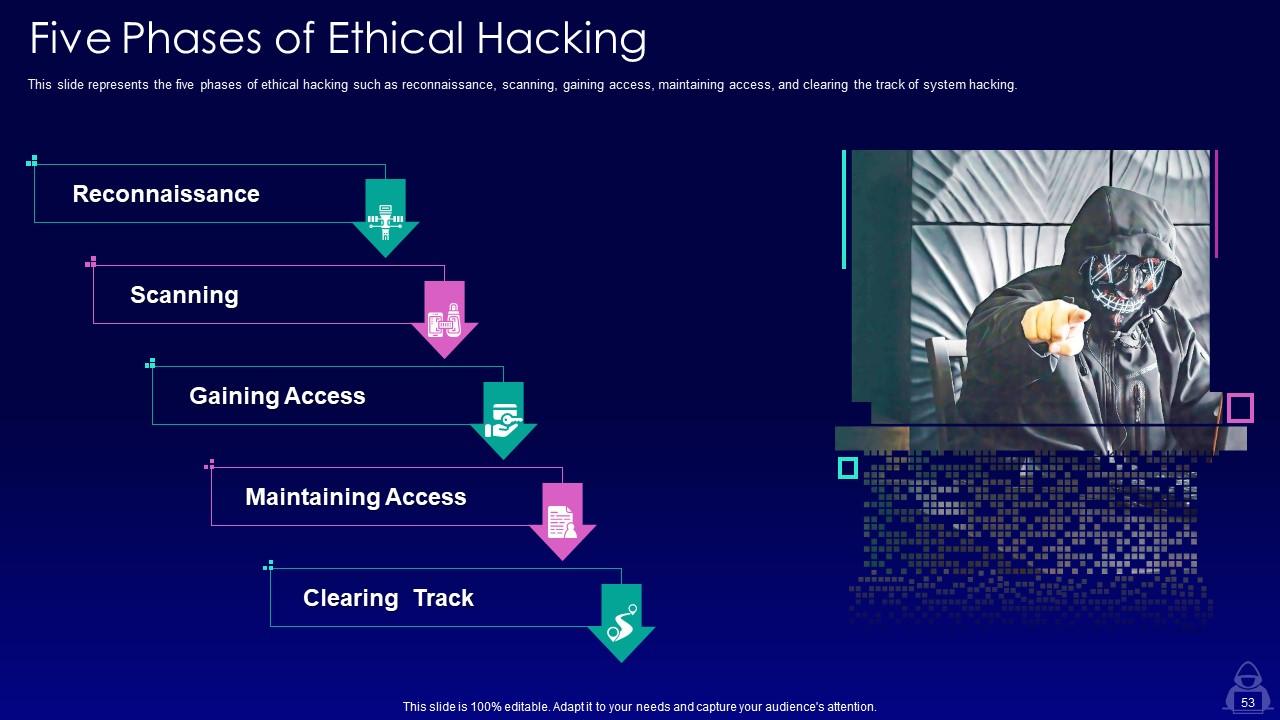
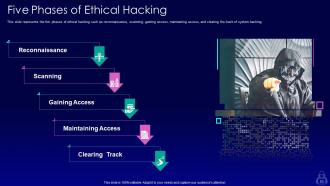
Slide 53: This slide showcases five phases of ethical hacking such as reconnaissance, scanning, gaining access, etc.
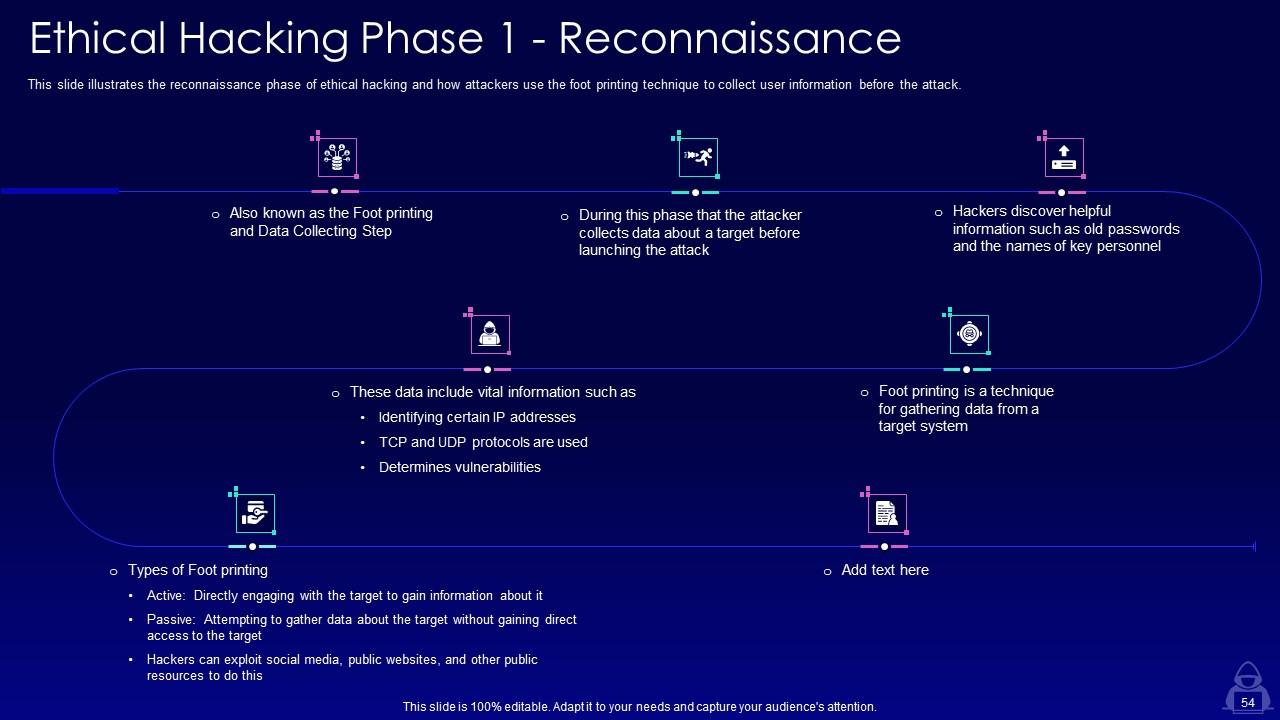
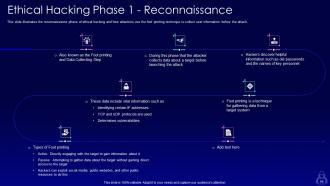
Slide 54: This slide illustrates the reconnaissance phase of ethical hacking and how attackers use the foot printing technique.
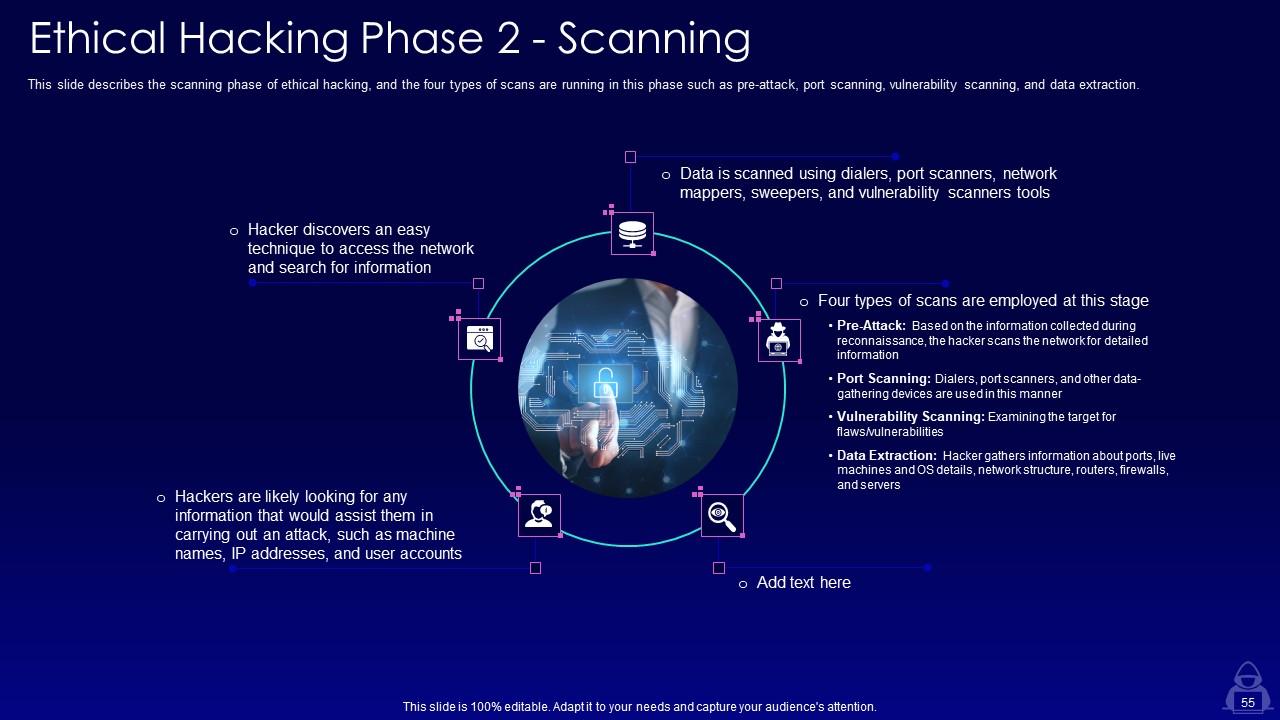
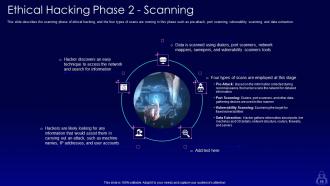
Slide 55: This slide describes the scanning phase of ethical hacking, and the four types of scans are running in this phase.
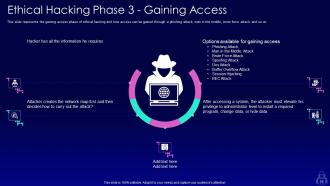
Slide 56: This slide represents the gaining access phase of ethical hacking and how access can be gained through a phishing attack.
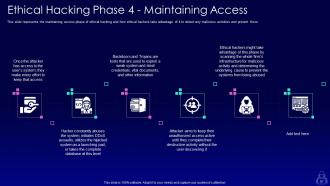
Slide 57: This slide showcases maintaining access phase of ethical hacking and how ethical hackers take advantage of it.
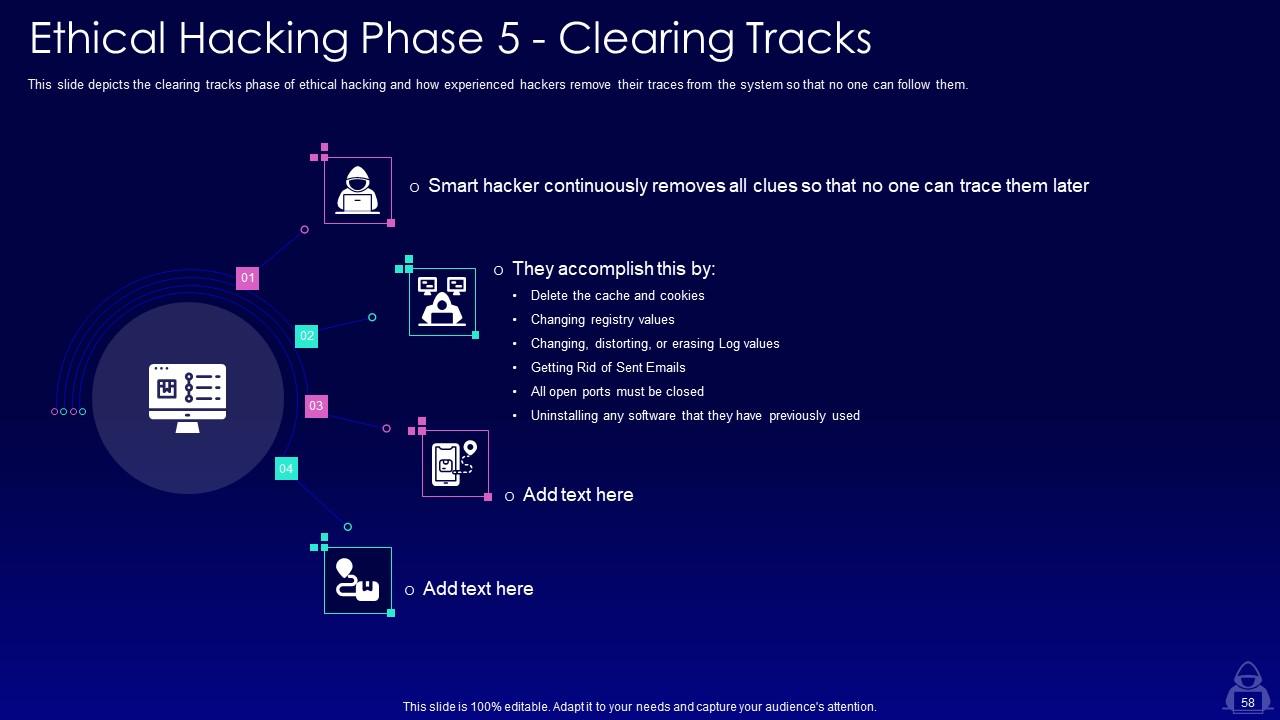
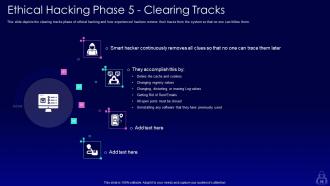
Slide 58: This slide depicts the clearing tracks phase of ethical hacking and how experienced hackers remove their traces.
Slide 59: This slide highlights title for topics that are to be covered next in the template.
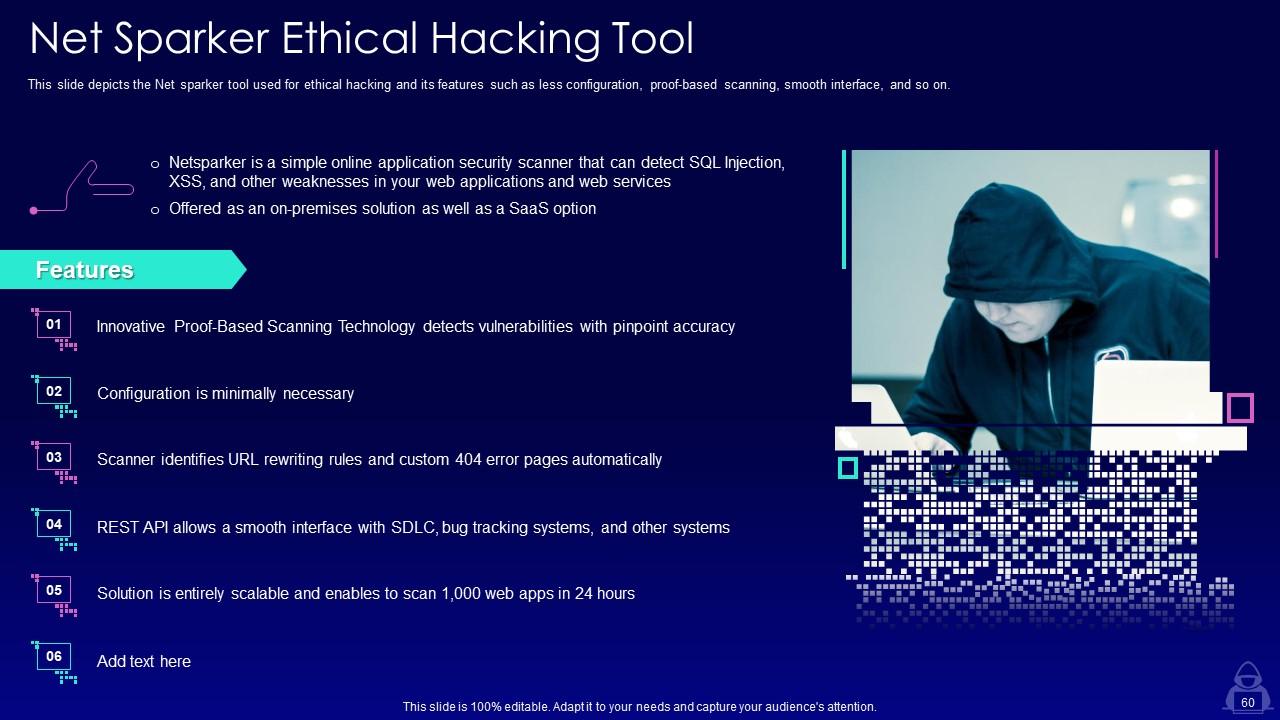
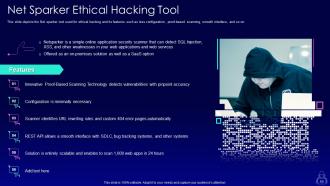
Slide 60: This slide depicts the Net sparker tool used for ethical hacking and its features such as less configuration, proof-based scanning, smooth interface, and so on.
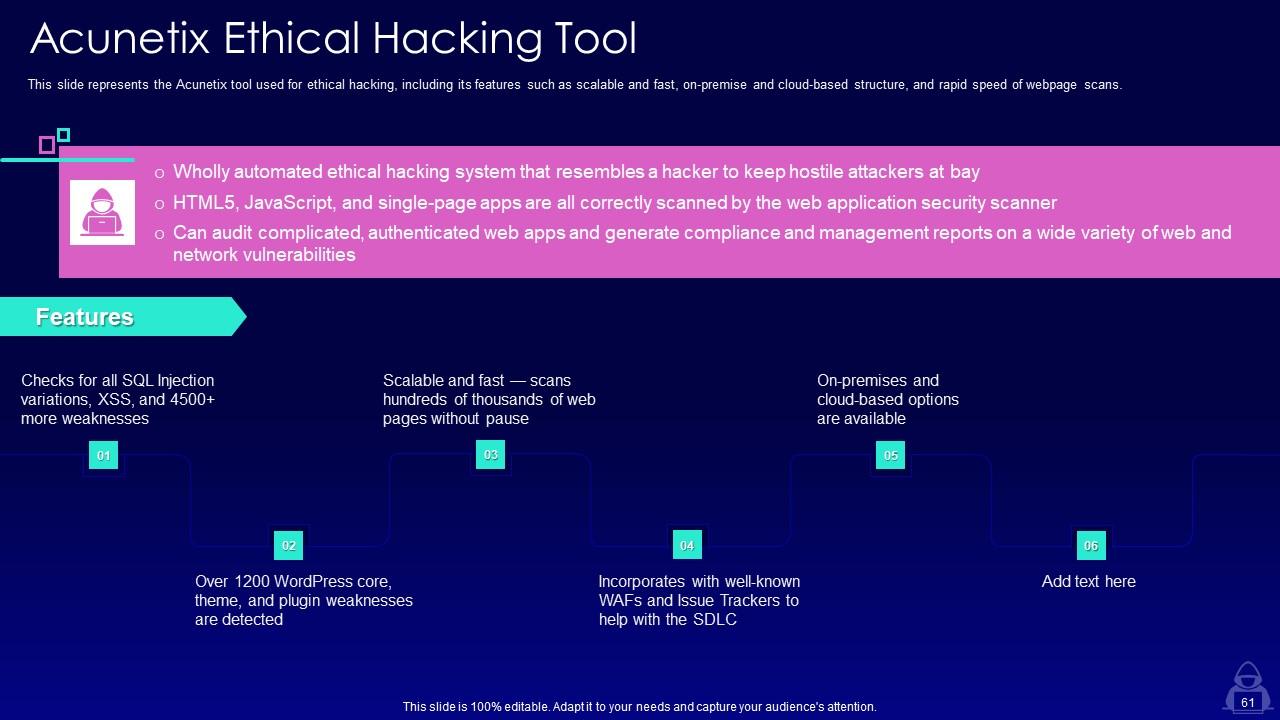
Slide 61: This slide represents the Acunetix tool used for ethical hacking, including its features such as scalable and fast, on-premise and cloud-based structure.
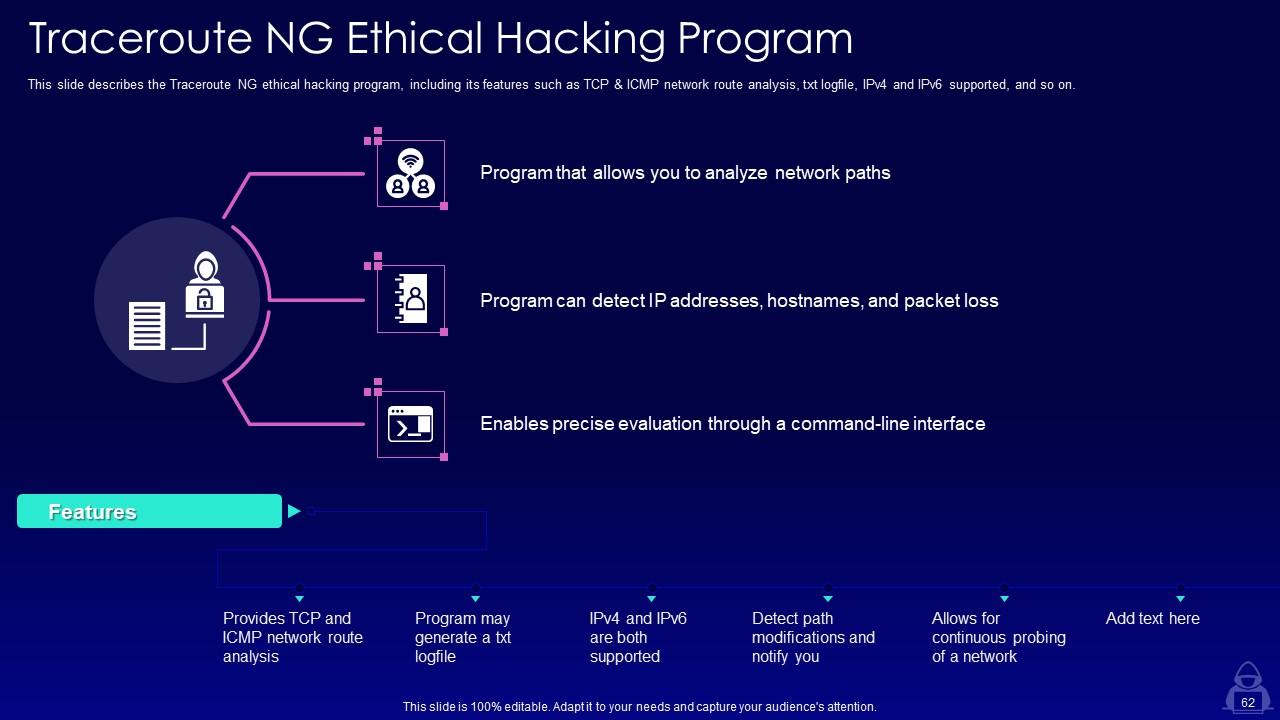
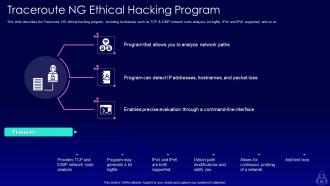
Slide 62: This slide describes the Traceroute NG ethical hacking program, including its features such as TCP & ICMP network route analysis.
Slide 63: This slide represents SolarWinds Security Event Manager Ethical Hacking Tool.
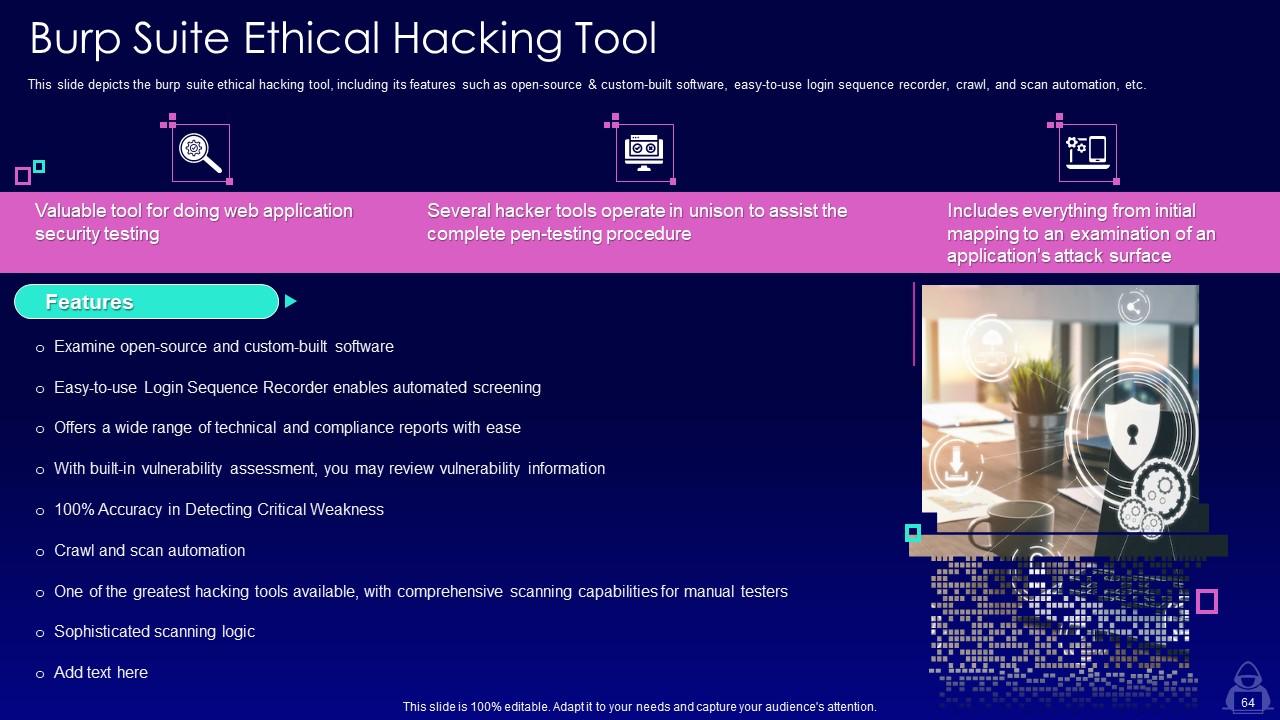
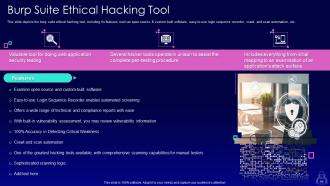
Slide 64: This slide depicts the burp suite ethical hacking tool, including its features such as open-source & custom-built software.
Slide 65: This slide highlights title for topics that are to be covered next in the template.
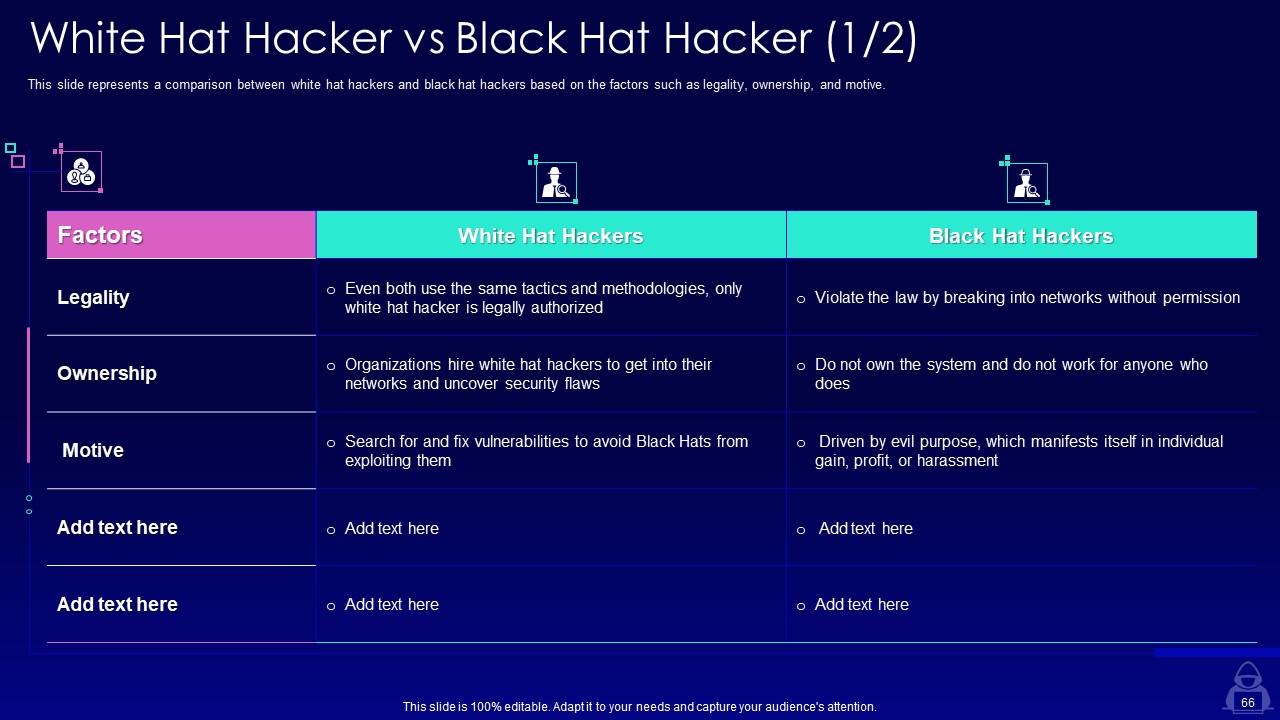
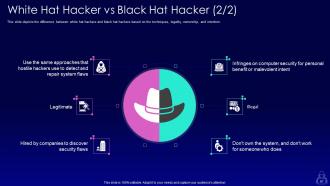
Slide 66: This slide represents a comparison between white hat hackers and black hat hackers based on the factors such as legality, ownership, and motive.
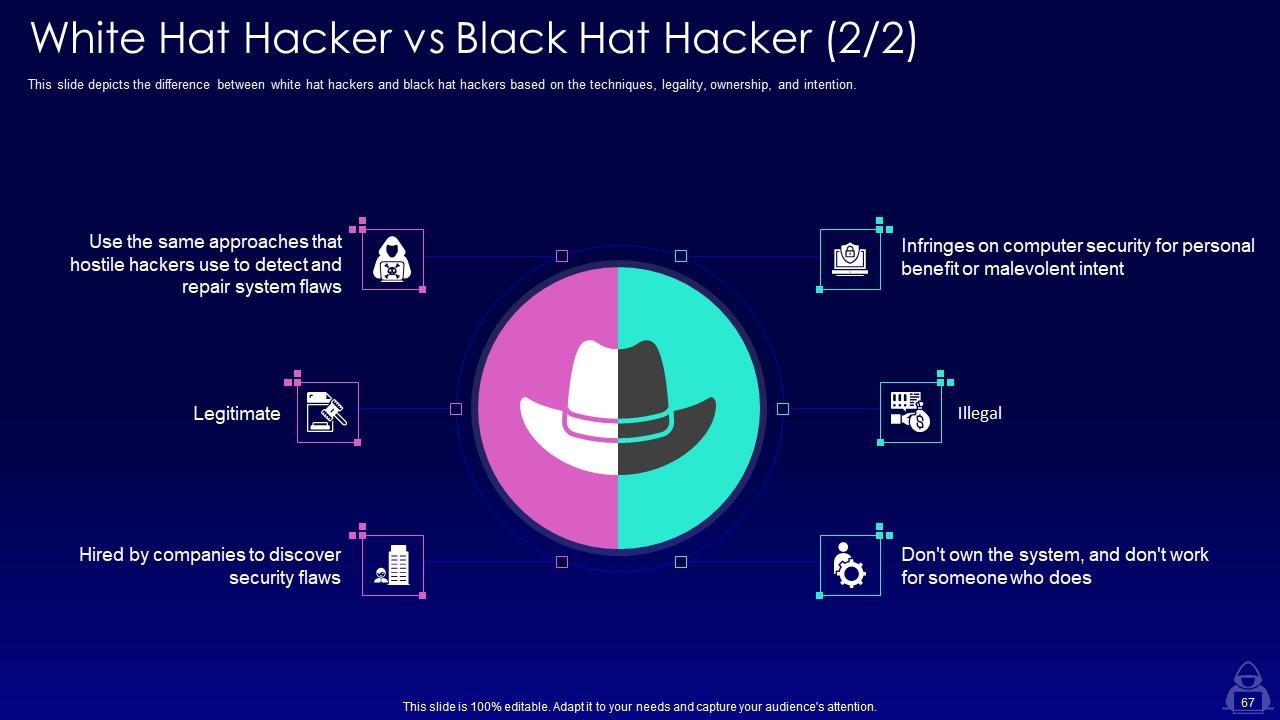
Slide 67: This slide depicts the difference between white hat hackers and black hat hackers based on the techniques, legality, ownership, and intention.
Slide 68: This slide showcases how ethical hackers are different from malicious hackers based on their purpose of hacking.
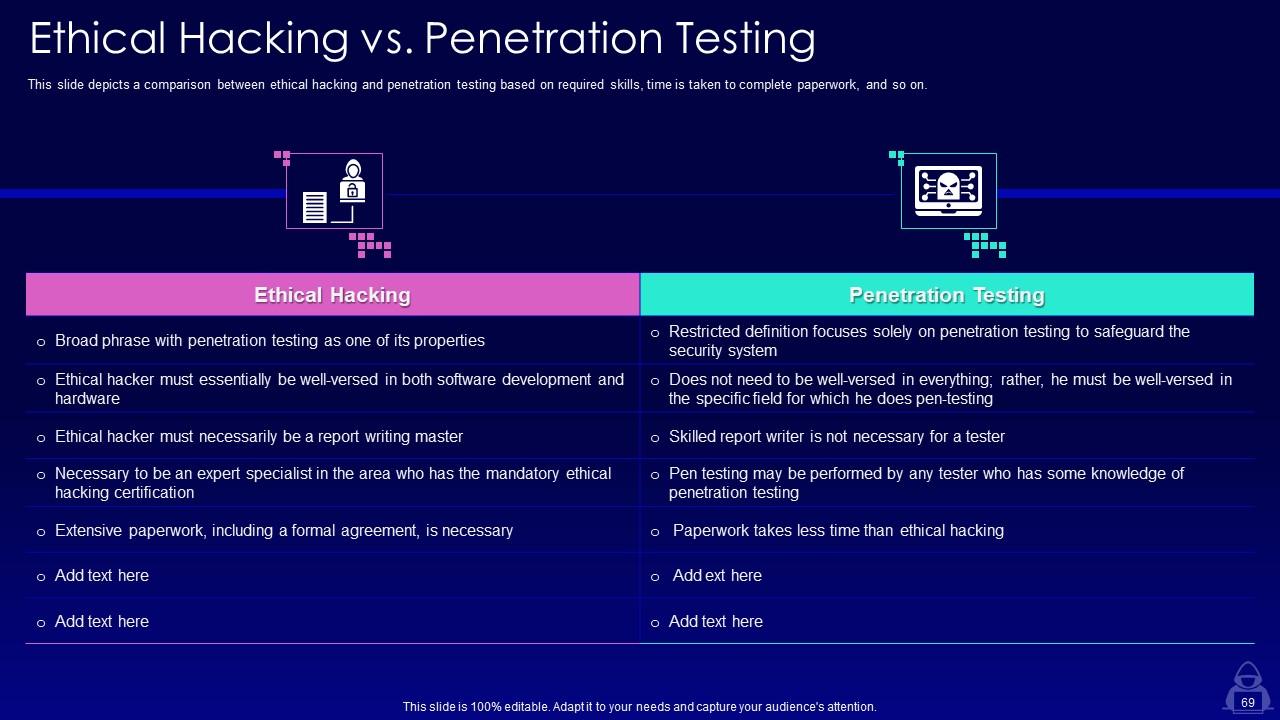
Slide 69: This slide depicts a comparison between ethical hacking and penetration testing based on required skills.
Slide 70: This slide highlights title for topics that are to be covered next in the template.
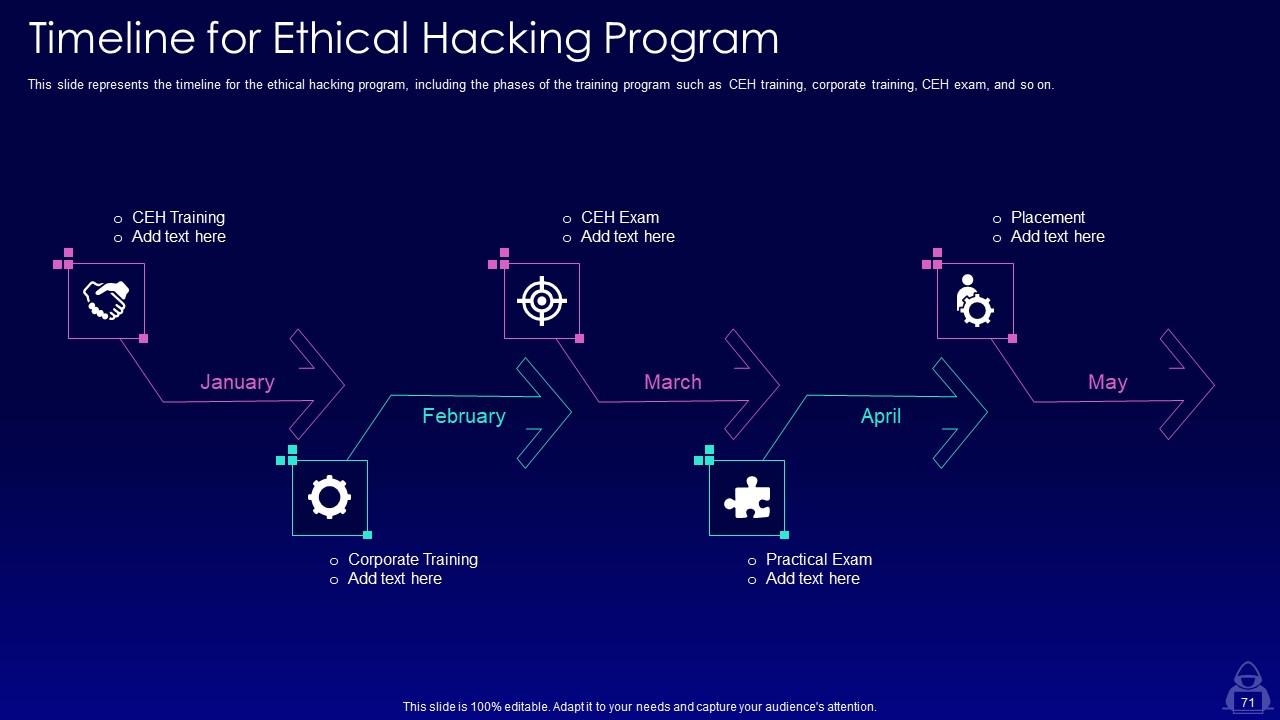
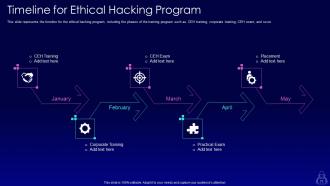
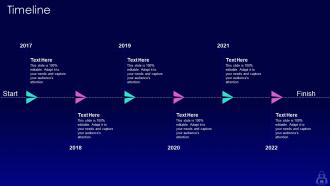
Slide 71: This slide represents the timeline for the ethical hacking program, including the phases of the training program.
Slide 72: This slide highlights title for topics that are to be covered next in the template.
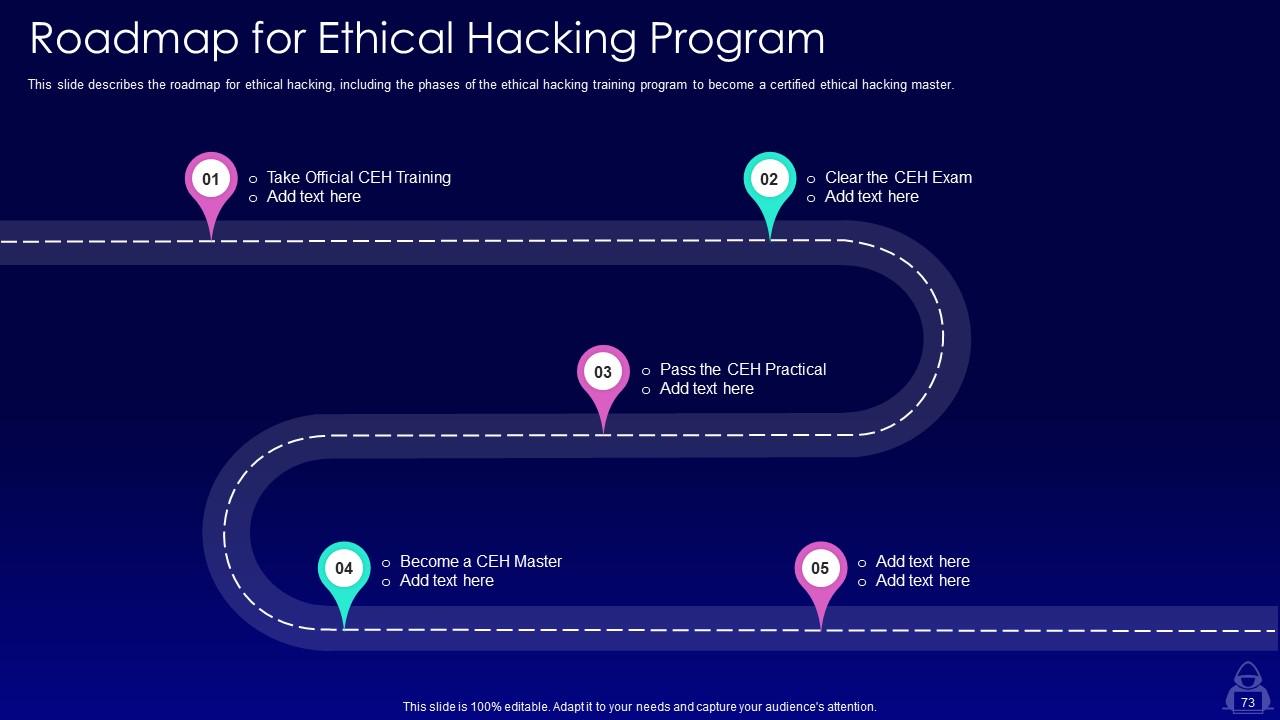
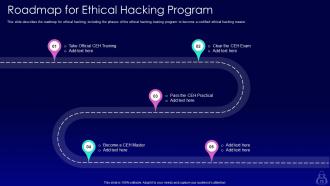
Slide 73: This slide showcases Roadmap for Ethical Hacking Program.
Slide 74: This slide highlights title for topics that are to be covered next in the template.
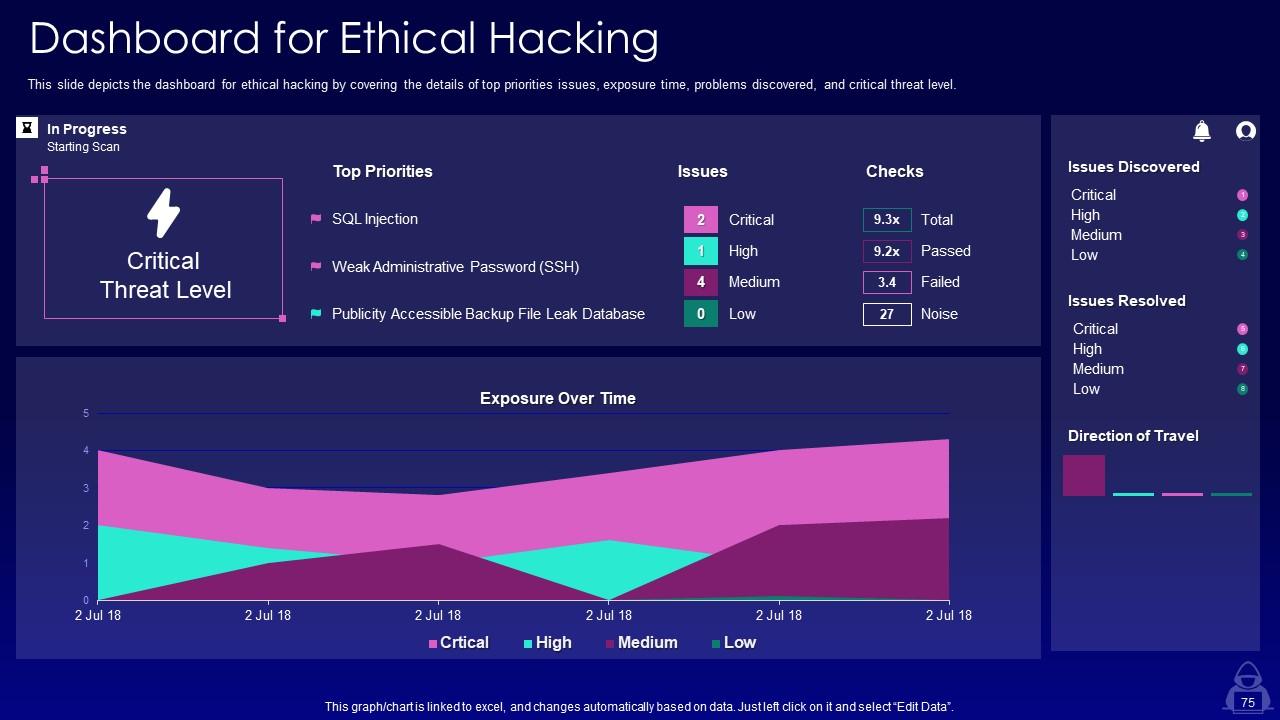
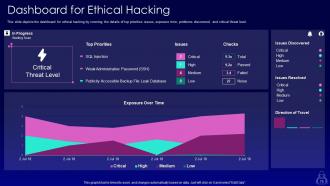
Slide 75: This slide depicts the dashboard for ethical hacking by covering the details of top priorities issues.
Slide 76: This slide displays Icons for Ethical Hacking (IT).
Slide 77: This slide is titled as Additional Slides for moving forward.
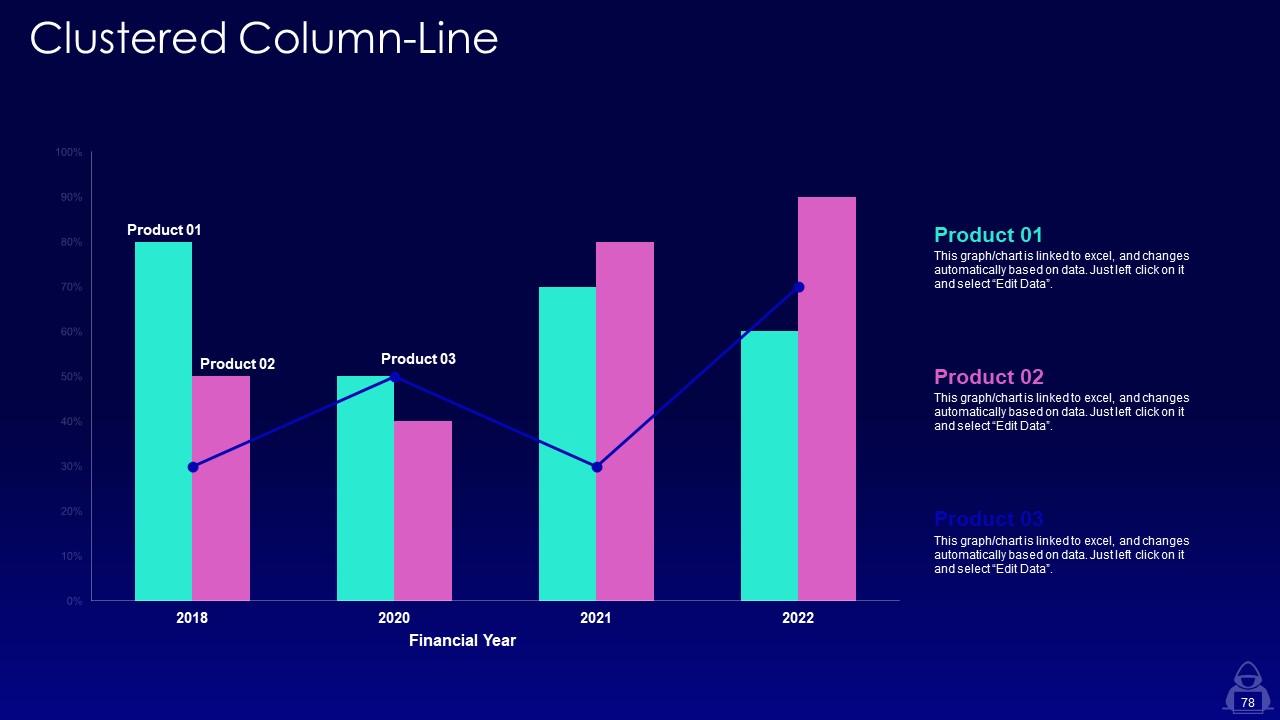
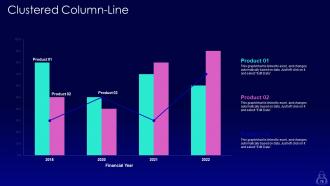
Slide 78: This slide provides Clustered Column chart with two products comparison.
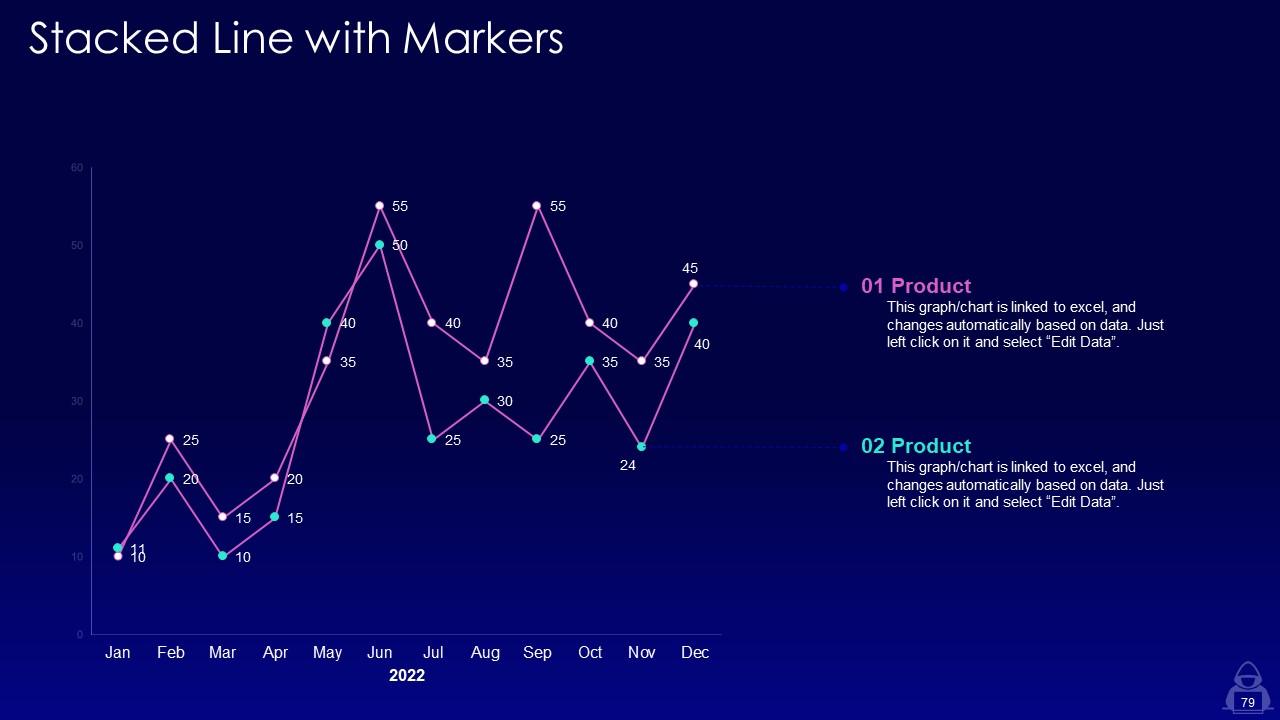
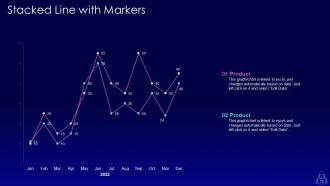
Slide 79: This slide displays Stacked Line with Markers.
Slide 80: This is an Idea Generation slide to state a new idea or highlight information, specifications etc.
Slide 81: This is a Comparison slide to state comparison between commodities, entities etc.
Slide 82: This is a Financial slide. Show your finance related stuff here.
Slide 83: This slide contains Puzzle with related icons and text.
Slide 84: This is Our Target slide. State your targets here.
Slide 85: This slide shows Post It Notes. Post your important notes here.
Slide 86: This is a Timeline slide. Show data related to time intervals here.
Slide 87: This is a Thank You slide with address, contact numbers and email address.
Ethical hacking it powerpoint presentation slides with all 92 slides:
Use our Ethical Hacking IT Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
FAQs
Common types of cybercrime include identity theft, computer fraud, privacy breach, and more. These can cause financial losses, reputational damage, and compromised customer data, among other consequences.
Organizations recruit ethical hackers to improve their security measures, protect customer information, raise security awareness, and more. Ethical hackers can help observe organizational systems from a hacker’s viewpoint and identify vulnerabilities that need to be fixed.
Ethical hackers need to have skills such as knowledge of programming languages, operating systems, and networking protocols, as well as the ability to use various ethical hacking tools. Certifications such as Certified Ethical Hacker (CEH v11) can also be helpful in demonstrating expertise
Ethical hacking can provide benefits such as unraveling the hacker mindset, improving development and quality assurance processes, and identifying weaknesses in security measures. For organizations, it can also help test security, understand hacker methods, and prevent future attacks.
Some techniques of ethical hacking include port scanning, analyzing and sniffing network traffic, and SQL(Sequel Query Language) injection. These techniques work by identifying vulnerabilities in networks and systems that can be exploited by malicious actors, and then testing them to see if they can be fixed.
-
Very unique and reliable designs.
-
Great experience, I would definitely use your services further.