Data breaches causing significant business losses are on the rise, with cyberattacks becoming more sophisticated and damaging. According to a recent IBM Security report, in 2022, the average cost of a single incident of data breach was $4.35 million. The report also found that it took an average of 290 days to detect and contain a data breach. This disturbing set of figures points to the need for proactive incident response measures against data breach of any kind, howsoever minor it may appear at the time.
Having a data breach incident response plan in place is crucial for businesses to manage and mitigate the impact of such security catastrophes. Data breach incident response plan Templates provide a structured approach to handling cyber threats, with predefined steps and procedures that can be tailored to the specific needs of a business. Furthermore, data breach incident response plan PPT Templates also assist businesses in meeting regulatory compliance requirements. The end-result of this effort is greater, fool-proof security of sensitive data of businesses that also protects operations and reputation in today’s challenging cybersecurity landscape.
Therefore, SlideTeam brings you a collection of ready-made PPT Templates to detect an attack and put an action plan in place to minimize or contain the damage should you be the victim of a data breach incident. These PowerPoint Slides are content-ready and custom-made, offering you both structure and flexibility. Outline a simplified procedure to respond to the threat as quickly as possible using our actionable templates. Each of the templates is 100% customizable and editable.
Browse the collection below and choose a presentation template that meets your requirements.
Let’s begin!
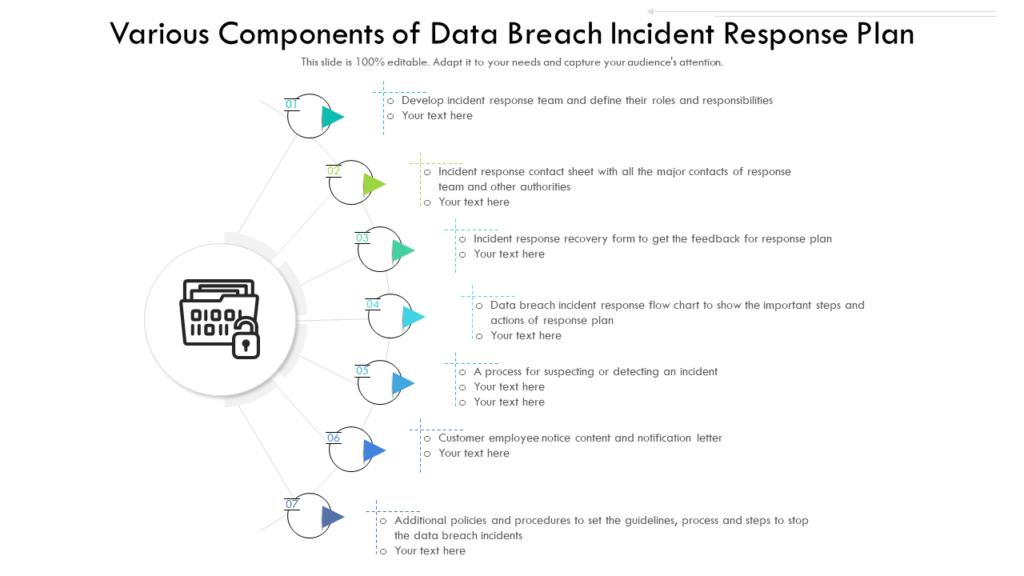
Template 1: Data Breach Incident Response Plan PPT Template
Are you prepared for the worst? Don’t wait until it’s too late to ramp up your defences! Our data breach incident response plan PPT Template is the key to protecting your business against cyber threats. With comprehensive and actionable components, this layout provides you with a step-by-step guide on how to respond to data breaches, minimizing damage, and downtime. From proactive measures to breach notification procedures, this ready to use PPT Template ensures you’re equipped to handle any security breach. Don’t risk your business reputation and financial well-being to chance and luck. Invest in our data breach incident response plan template today and be prepared for the unexpected, but breathe easy! Download now!
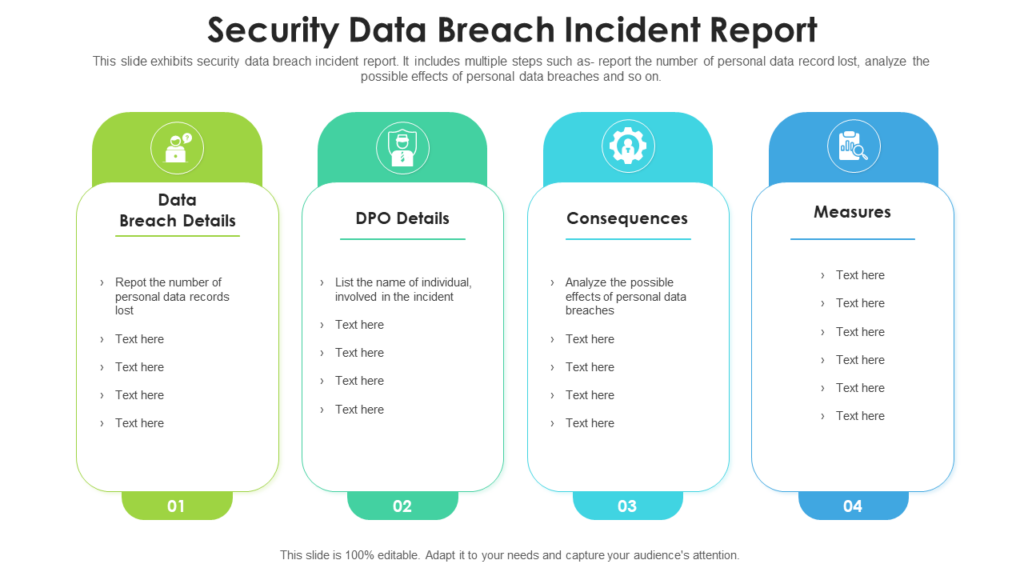
Template 2: Security Data Breach Incident Report PPT Slide
Data breaches can strike anytime, anywhere. Be prepared and take necessary action with this pre-designed data breach incident report PPT Template. This template simplifies and organizes your approach to documenting and reporting data breaches, helping you comply with legal requirements and industry regulations. This presentation template decodes the process of documenting breach details, impact assessment, and remedial steps. Don't fumble through the chaos of a data breach. Trust our data breach incident report Template to help you respond swiftly and effectively, safeguarding your business and maintaining trust with your customers. In fact, your capability encourages others to also shore up their defenses. Download now!
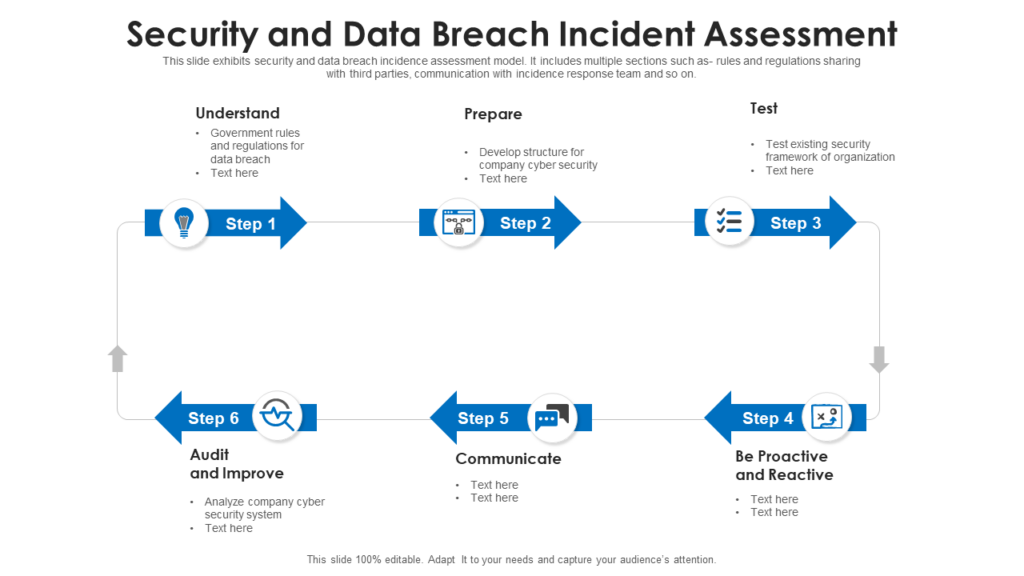
Template 3: Security and Data Breach Incident Assessment Template
Don’t leave your business vulnerable to the aftermath of a security or data breach! Our content-ready security and data breach incident assessment Template is your comprehensive tool for monitoring and managing the impact of security incidents. With a clear and structured format, this PPT Template guides you through the critical steps of incident assessment, including identification of affected systems, data, and potential risks. Ensure timely and effective response to security breaches with our user-friendly Template. Invest in proactive incident assessment and mitigation today to protect your business reputation and valuable assets. Download now!
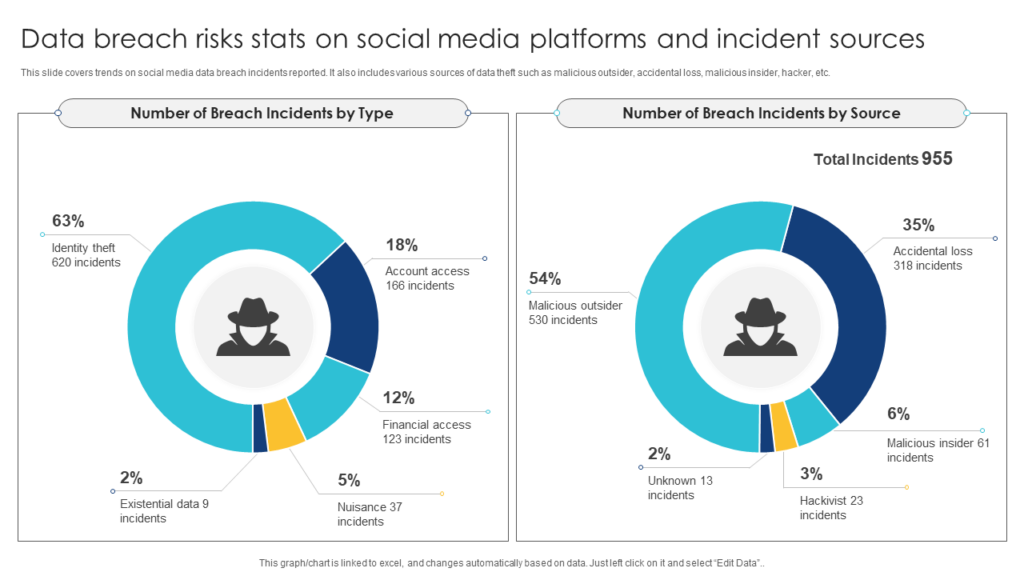
Template 4: Data Breach Risk Stats PowerPoint Template
Stay ahead of the curve with the help of this actionable data breach risk stats PPT Template. It is a ready to use presentation template that highlights a systematic approach to assess and quantify the risks associated with data breaches, helping you make informed decisions to protect your organization’s sensitive and classified information. This content-ready PPT Template empowers you to track and analyze breach risks, identify vulnerabilities, and prioritize mitigation efforts. Stay strategic in your data breach risk management using this flexible PPT Slide. Invest in our data breach risk stats template now and safeguard your business against potential threats. Download now!
INVEST IN PREPAREDNESS TODAY!
Data breaches are a constant threat in a business environment that prioritizes innovation, and openness to making the customer experience increasingly more engaging. Yet, it does not mean that businesses have to be caught off guard and suffer damage to critical assets! Use our data breach incident response plan PPT Templates to get a comprehensive and customizable solution to respond to security breaches. Be prepared, stay organized, and protect the reputation of your business with our reliable PPT templates. Download now!
FAQs on Data Breach Incident Response Plan
What are the five steps in a data breach response plan?
A data breach response plan typically includes several steps to effectively address and mitigate its impact. Here are five common steps in a data breach response plan:
Detection and Assessment: The first step is to detect and assess the data breach. This may involve monitoring systems for signs of unauthorized access, conducting audits, and analyzing logs and other data to identify any unusual or suspicious activity. Once a breach is detected, the severity and scope of the breach are assessed to determine the appropriate response.
Notification and Communication: Once a data breach is confirmed, stakeholders such as the internal incident response team, legal counsel, senior management, and relevant regulatory authorities, must be notified promptly. External communication with affected individuals, customers, partners, and other stakeholders may also be necessary, depending on applicable laws and regulations.
Containment and Remediation: The next step is to contain the breach and prevent more damage. This may involve isolating affected systems, disabling compromised accounts, changing passwords, and patching vulnerabilities. It may also include deploying additional security measures, such as firewalls, intrusion detection systems, and other security controls to prevent more such breaches.
Investigation and Forensics: A thorough investigation of the data breach is crucial to determine the root cause, extent of the breach, and potential impacts. This may involve conducting forensics analysis, reviewing logs and other relevant data, and working with law enforcement, external experts, and forensic teams to gather evidence and identify perpetrators.
Evaluation and Improvement: After the breach has been contained and resolved, it’s important to evaluate the effectiveness of the response plan and identify areas for improvement. This may involve conducting a post-incident review, updating policies and procedures, enhancing security measures, and providing additional training and awareness programs for employees.
Note that specific steps in a data breach response plan may vary depending on the nature and severity of the breach, the organization's size and industry, and applicable laws and regulations. It’s crucial for organizations to have a well-defined and regularly reviewed data breach response plan in place to respond to and mitigate the impact of a data breach.
How do you respond to a data breach incident?
Responding to a data breach incident requires a prompt and coordinated approach to mitigate the impact and minimize damage. Here are some general steps that organizations can take in responding to a data breach incident:
Activate Incident Response Plan: If your organization has an incident response plan in place, activate it immediately. This plan should outline the roles and responsibilities of the incident response team, communication protocols, and steps to take in containing and resolving the breach.
Contain the Breach: Take immediate action to contain the breach and prevent further unauthorized access or data exposure. This may involve isolating affected systems or accounts, changing passwords, disabling compromised accounts, and implementing additional security measures.
Assess the Scope and Severity: Conduct a thorough assessment of the breach to determine the extent of the data exposure, potential impact, and the root cause of the breach. This may involve forensics analysis, reviewing logs and other relevant data, and working with external experts or law enforcement, if necessary.
Notify Appropriate Stakeholders: Notify relevant stakeholders, including senior management, legal counsel, internal incident response team, and regulatory authorities, as required. External communication with affected individuals, customers, partners, and other stakeholders may also be necessary.
Investigate and Remediate: Conduct a comprehensive investigation into the breach to identify the root cause and take necessary remedial action. This may include patching vulnerabilities, updating security measures, and implementing additional controls.
Evaluate and Improve: After the breach has been contained and resolved, conduct a post-incident review to evaluate the effectiveness of the response. Update policies, procedures, and security measures, and provide additional training and awareness programs for employees.
Monitor and Manage the Aftermath: Keep a close eye on the situation even after the breach has been resolved. Monitor for any potential ongoing threats, assess the impact on individuals or customers, and take appropriate actions to manage the aftermath. This might involve providing credit monitoring services or addressing potential legal and financial ramifications.
What is a data breach response plan?
A data breach response plan is a documented set of procedures and protocols that an organization follows in the event of a data breach or security incident. It outlines the steps that the incident response team must take to respond to and mitigate the impacts of a data breach, with the goal of minimizing potential damage and restoring normal operations.
A typical data breach response plan includes the following key elements:
Incident Detection and Reporting: Procedures for detecting and reporting potential security incidents or data breaches, including monitoring systems, identifying suspicious activities, and reporting incidents.
Incident Response Team Roles and Responsibilities: Clearly defined roles and responsibilities for members of the incident response team, including the chain of command, communication protocols, and decision-making authority during a breach response.
Incident Containment and Mitigation: Steps to isolate and contain the breach, prevent unauthorized access or data exposure, and implement initial measures to mitigate the impacts of the breach.
Forensics Investigation: Procedures for conducting forensics investigation to determine the root cause of the breach, identify the extent of the data exposure, and gather evidence for potential legal or regulatory purposes.
Notification and Communication: Protocols for notifying relevant stakeholders, including senior management, legal counsel, regulatory authorities, affected individuals, customers, partners, and media, in compliance with applicable laws and regulations.
Remediation and Recovery: Procedures for taking necessary actions to remediate vulnerabilities, restore normal operations, and implement additional preventive security measures.
Post-Incident Review and Lessons Learned: Evaluation of the incident response process, identification of areas for improvement, and updates to policies, procedures, and security measures based on lessons learned from the incident.





 Customer Reviews
Customer Reviews




![Top 10 Confidentiality Agreement Templates to Protect Your Ideas, Invention, and More [Free PDF Attached]](https://www.slideteam.net/wp/wp-content/uploads/2022/06/Confidentiality-Agreement-Template-1013x441.jpg)












