Upgrading cybersecurity is a race between the good and the bad guys; a never-ending race. But we can quantify this race with the right tools to stay ahead. In today's interconnected world, organizations face a constant barrage of cyber threats and Cybersecurity incidents that can disrupt operations, compromise sensitive data, and tarnish reputations. The global cyber security market size was valued at USD 153.65 billion in 2022.
In the world of Cyber awareness and upgrading cybersecurity, being prepared is the key to getting one step ahead of cyber threats and Cybersecurity incidents. Incident Response, a proactive and strategic approach to cybersecurity, is critical in safeguarding organizations from these malicious attacks.
Incident Response Playbooks provide organizations with a structured approach to effectively detecting, responding and recovering from Cybersecurity incidents. Today, SlideTeam brings you a collection of the top-notch Incident Response Playbook Templates designed to empower you and your team in the face of cyber-attacks. By utilizing an Incident Response playbook, professionals can efficiently orchestrate their response efforts, minimize the impact of an incident, and ensure a swift recovery.
Unleash the power of our meticulously crafted PowerPoint slides, designed to equip you with an ironclad defense against cyber threats. These pre-designed templates are your secret weapon for effortlessly implementing a comprehensive playbook. With the flexibility to customize every aspect, you'll have an arsenal of professionally structured slides that will empower you to tackle Cybersecurity incidents with precision and move toward Cyber awareness. Take the proactive step today and download one of these game-changing templates to elevate your incident management like never before. Your organization's security is worth it.
Let's explore how these templates can help you quickly identify and mitigate security incidents while reducing the risk of future breaches.
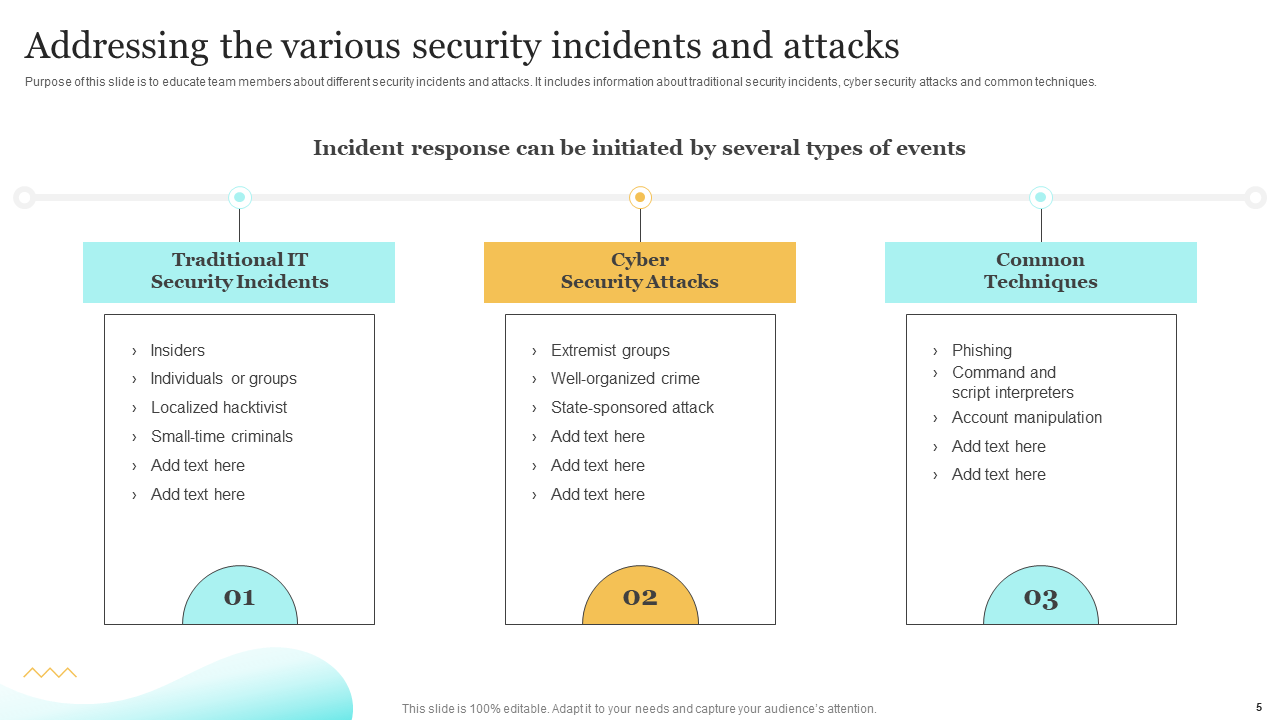
Template 1: Addressing the Various Security Incidents and Attacks
This slide provides comprehensive tables to address diverse security incidents and attacks, including traditional IT Cybersecurity incidents, cyber security attacks, and other standard techniques. It offers a systematic approach to handling different threats, allowing organizations to respond swiftly and effectively and move toward Cyber awareness.
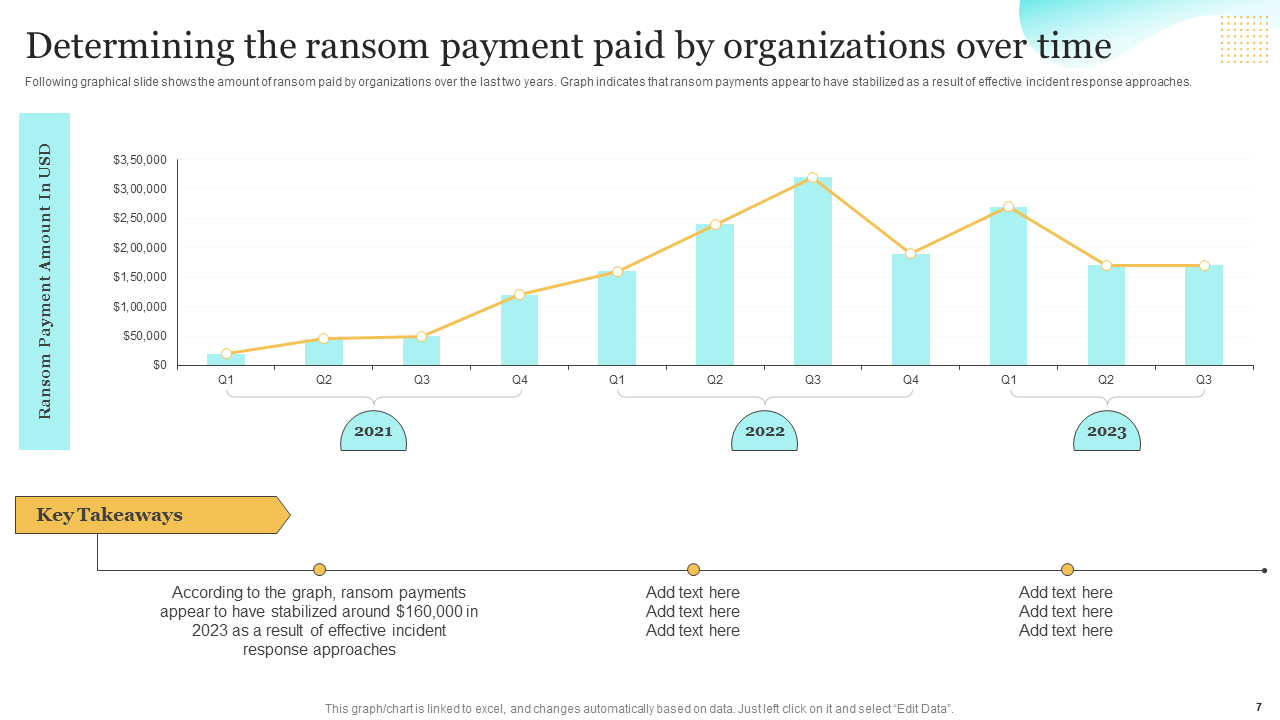
Template 2: Determining the Ransom Payment Paid by Organizations Over Time
Understanding the ransom payment trends is crucial for incident response teams. This slide enables organizations to track and analyze ransom payments made over time, providing Cyber awareness, valuable insights and takeaways to shape incident response strategies. Get it now!
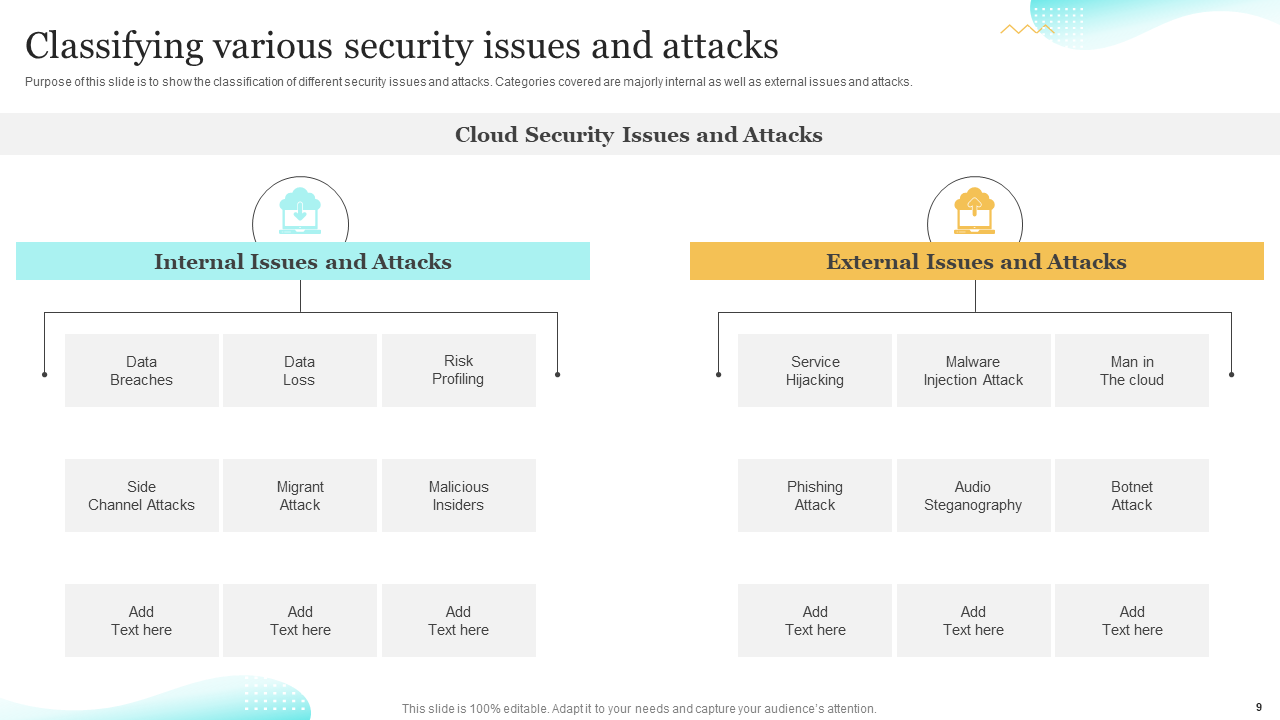
Template 3: Classifying Various Security Issues and Attacks
Classification is vital in incident response. This slide offers a classification model to categorize different security issues and attacks based on severity and impact, aiding in prioritization and response planning. It enhances incident response coordination and enables better communication among team members. Enhance your Cybersecurity incident classification process with our robust security issues and attacks template. Download today!
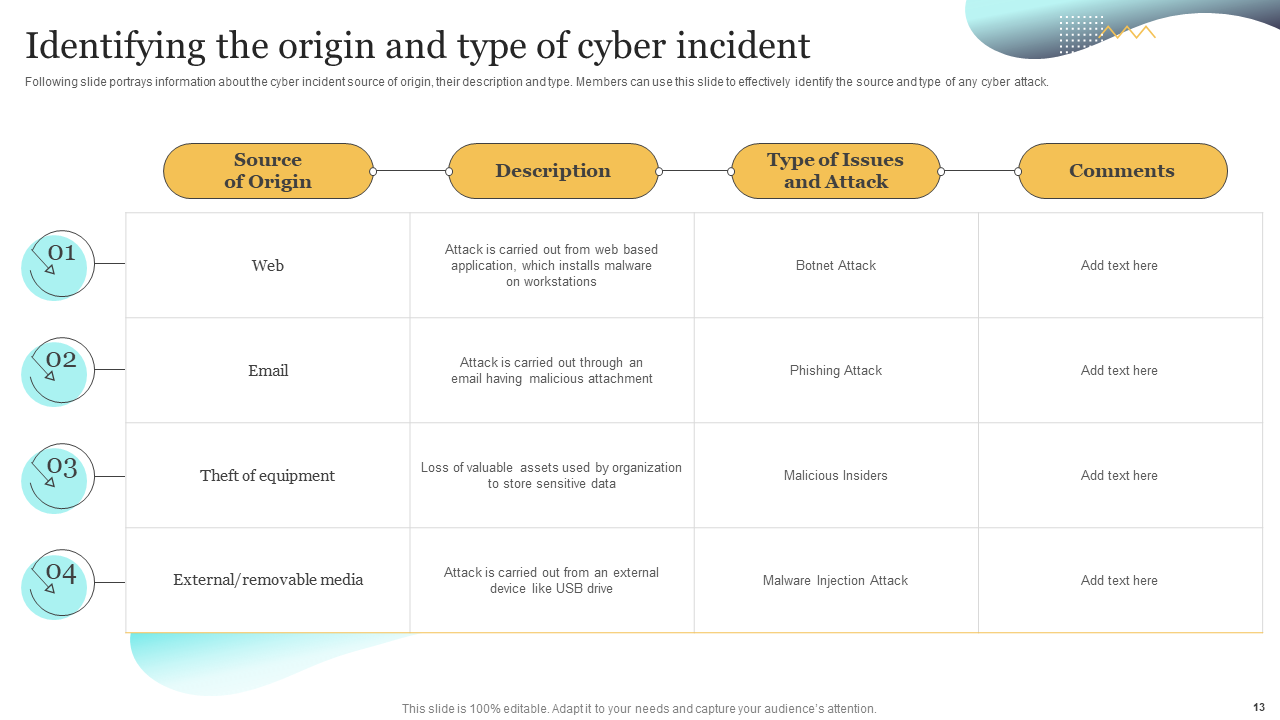
Template 4: Identifying the Origin and Type of Cyber Incident
This slide empowers incident responders to promptly identify the origin and type of cybersecurity incidents. This specialized slide aids in the accurate categorization and subsequent response to incidents. Don't miss out; download now!
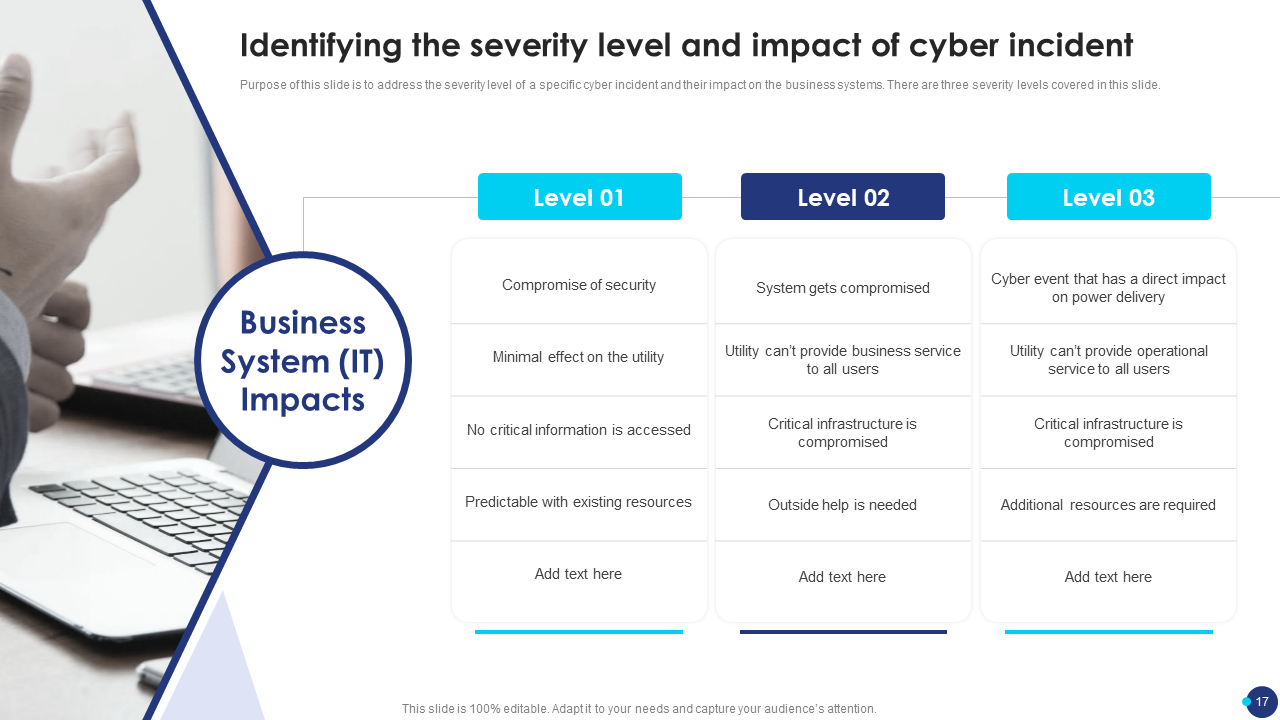
Template 5: Identifying the Severity Level and Impact of a Cyber Incident
This valuable slide helps assess cybersecurity incidents' severity level and impact. It broadly segregates the effects into three levels providing a systematic approach to prioritize response actions and allocate resources effectively. Get your hands on it now!
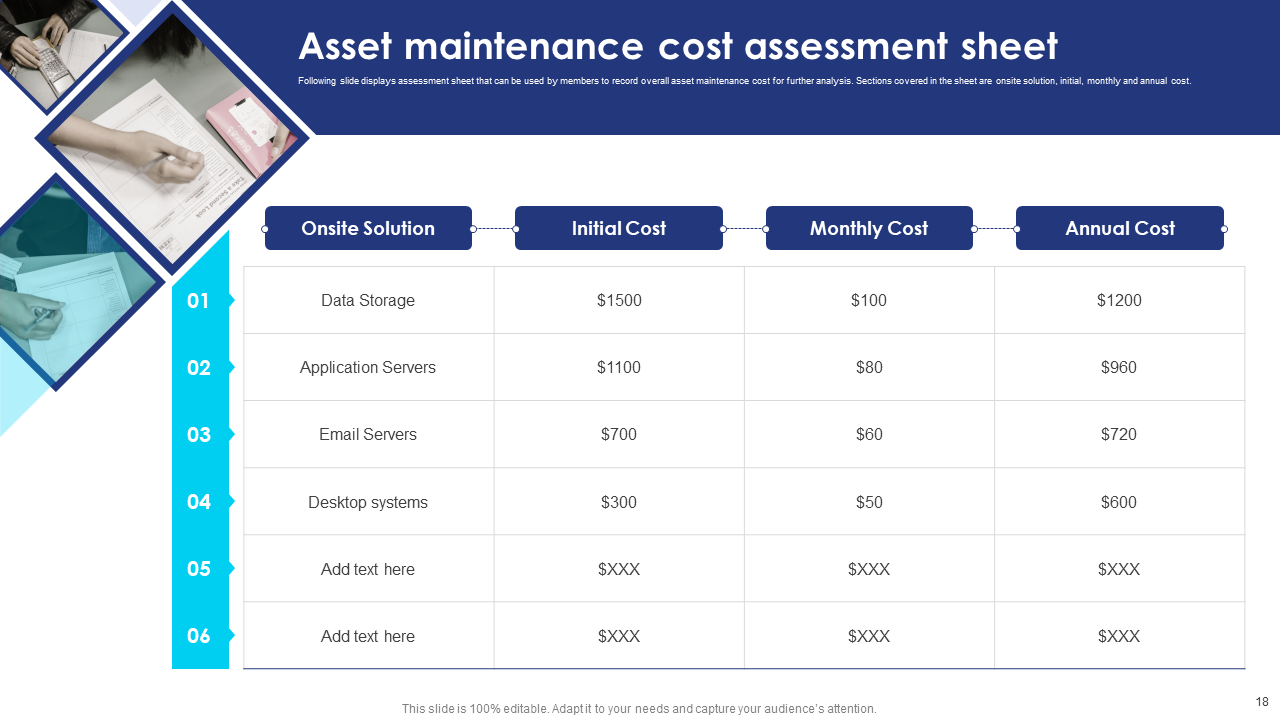
Template 6: Asset Maintenance Cost Assessment Sheet
Evaluate the costs associated with maintaining assets in the event of an incident using this slide. It aids in understanding the financial implications and optimizing asset protection measures. It provides the cost detailing across the onsite solution and the initial, monthly, and annual expenses. Download and streamline your incident response and Cyber awareness!
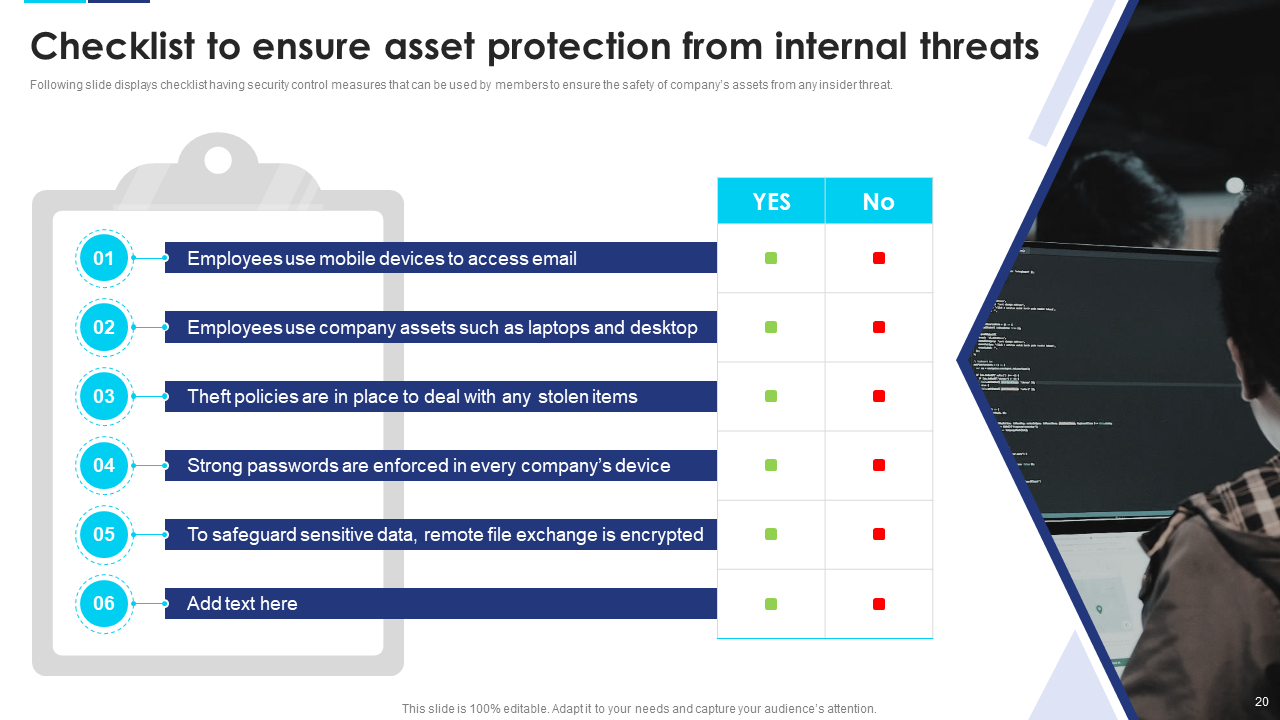
Template 7: Checklist to Ensure Asset Protection from Internal Threats
Prevent internal threats from compromising critical assets with this checklist slide. It serves as a reminder of essential security measures and helps organizations establish a robust defense against insider risks. Don't wait; download now!
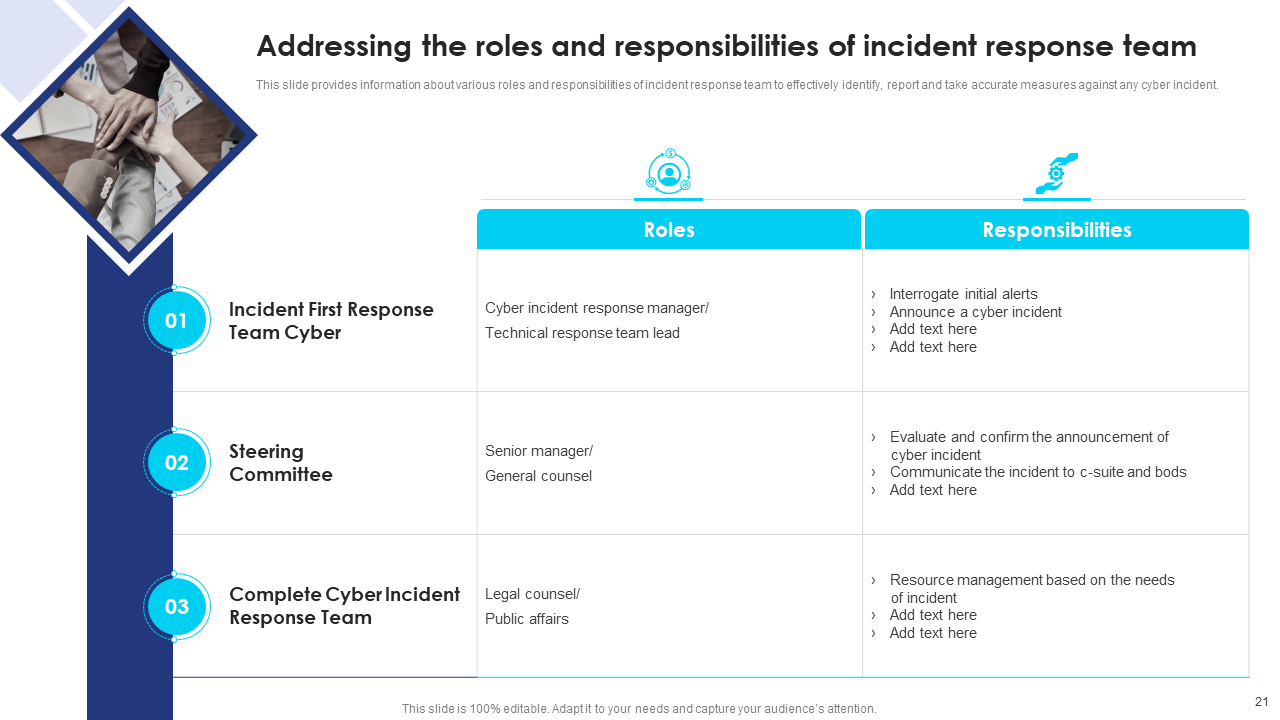
Template 8: Addressing the Roles and Responsibilities of the Incident Response Team
Define the roles and responsibilities of the incident response team with this slide. It promotes clarity and coordination within the team, ensuring an efficient and effective incident response. Streamline your incident response team's roles and responsibilities with our insightful slide. Get it today!
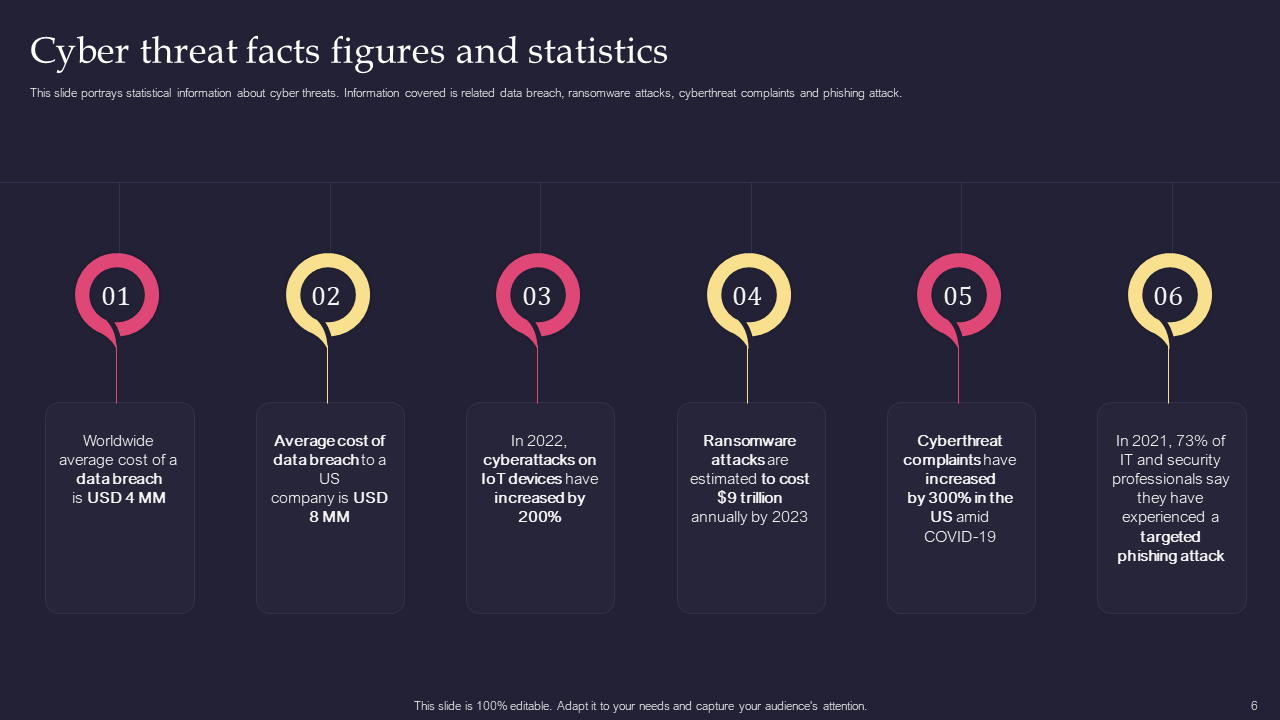
Template 9: Cyber Threat Facts Figures and Statistics
Stay informed about the latest cyber threat landscape with this slide. It presents relevant facts, figures, and statistics, enhancing situational awareness and guiding incident response strategies. Get it now
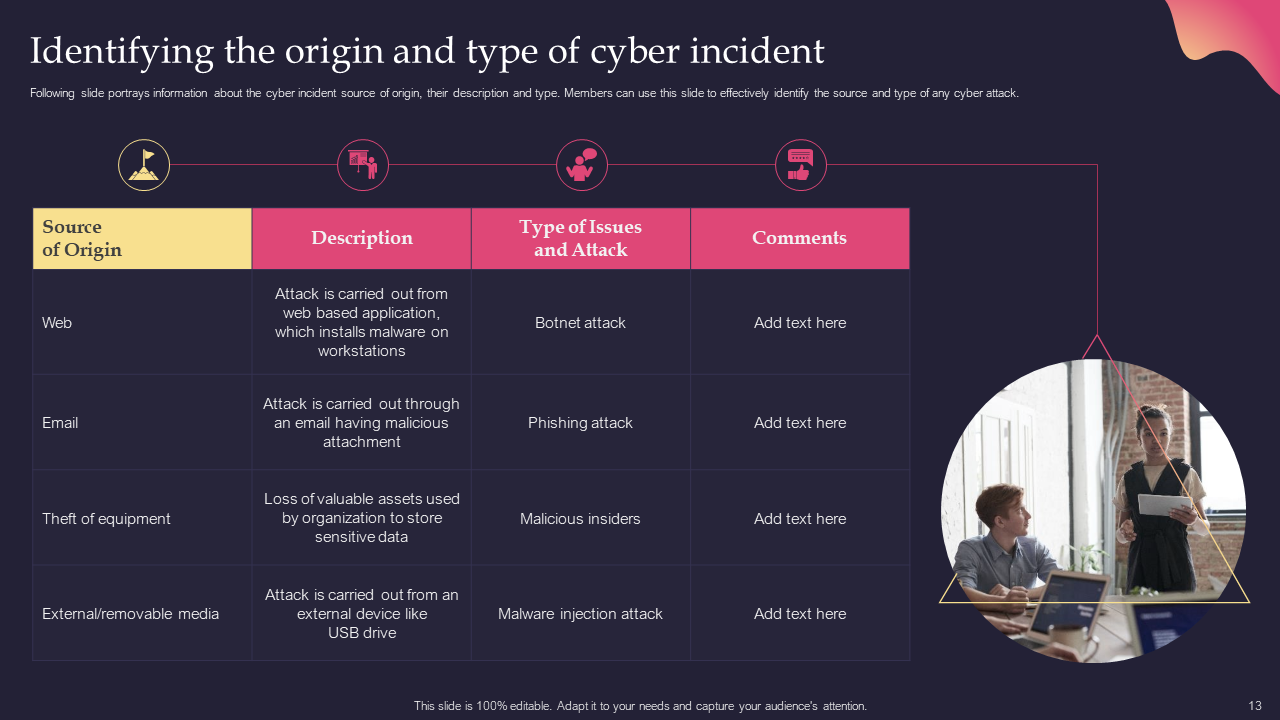
Template 10: Identifying the Origin and Type of Cyber Incident
Recognizing the cyber incident's origin and type is vital to defend against the threats. This clever slide offers the source of the basis of cybersecurity incidents, like web, email, or removable media, its description, and attack types. Elevate your incident response capabilities with this comprehensive preset. Download now!
Template 11: Performing Cyber Training Exercises for Securing the Assets
This slide facilitates the execution of cyber training exercises aimed at strengthening asset security. It enables organizations to prepare their workforce to handle potential threats proactively. Get it and boost your security!
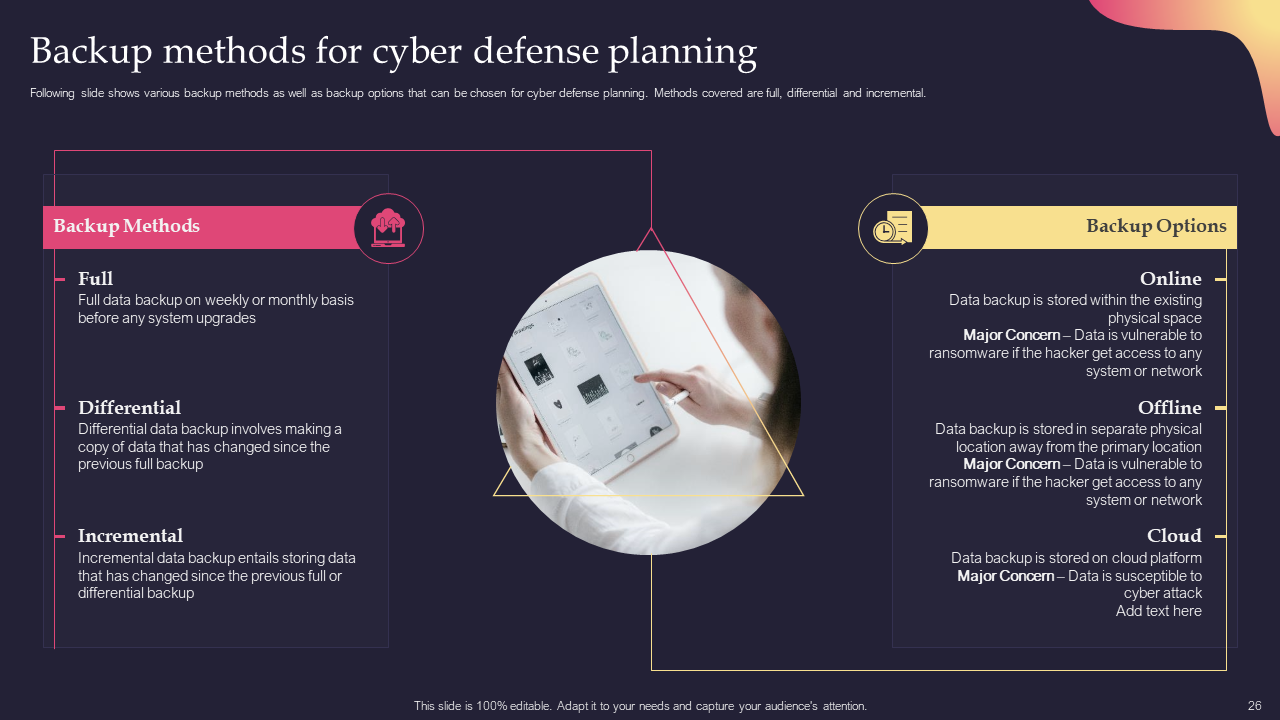
Template 12: Backup Methods for Cyber Defense Planning
Develop a robust backup strategy for cyber defense planning using this theme. It guides organizations in implementing effective data backup measures to minimize the impact of incidents. Develop a breakthrough backup strategy with our backup methods set. Download and safeguard your data effectively!
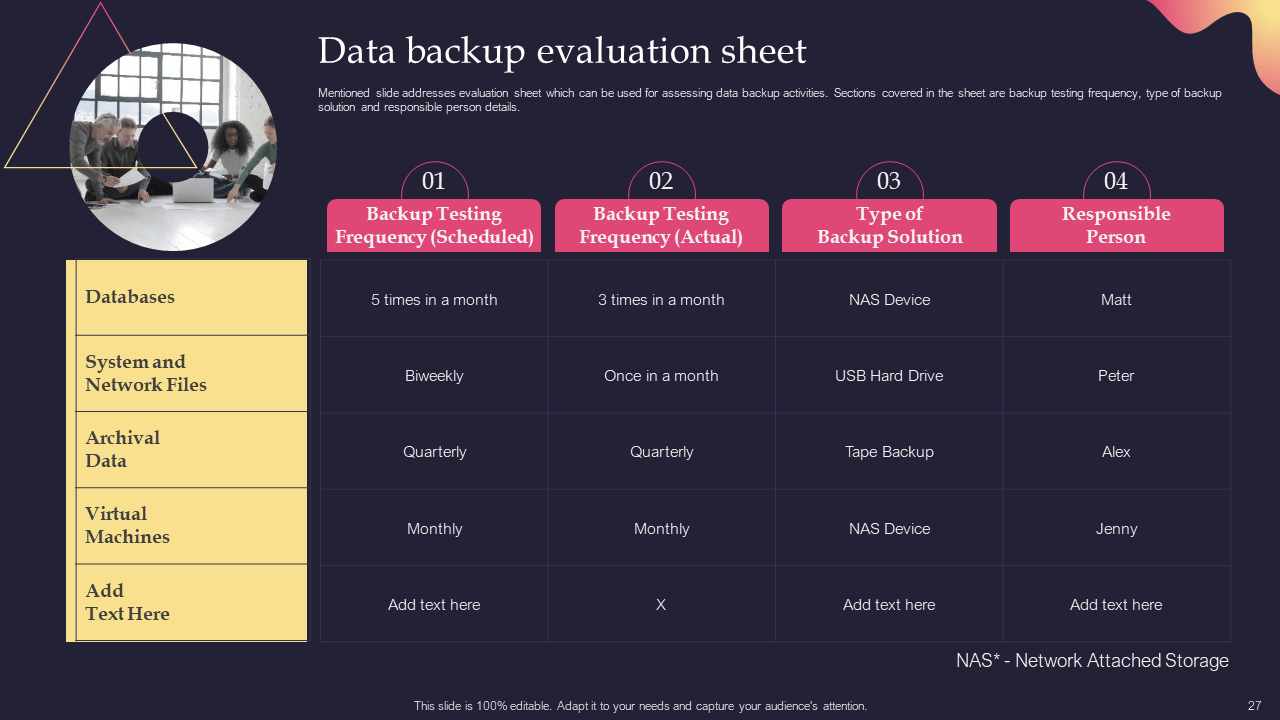
Template 13: Data Backup Evaluation Sheet
Evaluate the effectiveness of data backups with this slide. It helps organizations assess the integrity and availability of backup systems, ensuring reliable restoration during incident response. It includes scheduled and actual backup testing frequency, types of backup solutions, and the personnel responsible for the backup. Don't miss out; download now and ensure data resilience!
The Way Forward:
In the face of increasing cyber threats, having a solid Incident Response playbook is paramount for organizations to protect their valuable assets and minimize the impact of incidents. Our collection of Incident Response playbook templates equips you with the necessary tools to fortify your cybersecurity defenses. Whether addressing cybersecurity incidents, identifying cyber threats, or defining incident response team roles, these templates empower you to respond swiftly and effectively. Download these templates now and take a proactive stance in safeguarding your organization against the evolving cyber landscape.
Furthermore, step towards strengthening your cybersecurity by accessing the Ultimate Guide to Incident Response Playbook Template. Download these templates and empower your organization to navigate the complex landscape of cyber threats with confidence and resilience.
Remember, it's not a matter of "if" but "when" a cyber incident will occur. Be prepared.
FAQs on Incident Response Playbook
What is an example of an incident playbook?
An example of an incident playbook is a set of predefined and documented procedures that guide organizations in responding to specific cybersecurity incidents. It outlines the necessary steps, roles, and responsibilities to handle and mitigate an incident's impact effectively.
What is the difference between a playbook and an incident response?
A playbook is a documented set of procedures and guidelines that provide step-by-step instructions for responding to specific types of incidents. On the other hand, incident response is the overall process of detecting, analyzing, and responding to security incidents or breaches in an organization's network or systems. The playbook is a part of the broader incident response strategy.
What are the 5 phases in the incident response process?
The incident response process typically involves the following five phases:
- Preparation: Establishing an incident response plan, defining roles and responsibilities, and implementing necessary security measures.
- Detection and analysis: Identifying signs of an incident, investigating its cause and impact, and assessing the severity.
- Containment: Taking immediate actions to prevent further damage or spread of the incident, isolating affected systems or networks.
- Eradication: Removing the root cause of the incident, eliminating the presence of threats, and restoring affected systems.
- Recovery: Bringing systems and operations back to normal, restoring data and services, and implementing measures to prevent future incidents.
What are the seven stages of an incident response plan?
An incident response plan typically includes the following seven stages:
- Preparation: Developing an incident response strategy, establishing communication channels, and defining incident response roles and responsibilities.
- Identification: Detecting and recognizing signs of potential security incidents or breaches.
- Containment: Taking immediate actions to isolate and contain the incident, minimizing its impact.
- Eradication: Removing the incident's root cause, eliminating threats, and restoring affected systems.
- Recovery: Restoring operations, services, and data to normalcy and verifying the effectiveness of recovery measures.
- Lessons learned: Evaluating the incident response process, identifying areas for improvement, and updating the incident response plan accordingly.
- Post-incident activities: Conduct post-incident analysis, reporting, documentation, and implementing measures to prevent future incidents.


![[Updated 2023] Top 13 Templates to Build an Incident Response Playbook](https://www.slideteam.net/wp/wp-content/uploads/2021/08/Top-13-Templates-to-Build-an-Incident-Response-Playbook-1-1013x441.png)


 Customer Reviews
Customer Reviews






![[Updated 2023] Top 15 PowerPoint Templates to Improve Work Safety](https://www.slideteam.net/wp/wp-content/uploads/2021/03/06_1013x441-493x215.png)













Could you please inform me about the cost of the 13 application