The incident response playbook is the detailed plan or methodology by which an organization handles a data breach or cyber-attack. Ultimately the goal is to minimize the damage occurring from incidents.
An organization should at minimum have a clear incident response plan in place. This plan should define what an incident for the company should comprise of and provide a clear, guided process to follow when an incident occurs.
Additionally, it’s advisable to specify the terms, to employees or leaders responsible for both managing the overall incident response initiative and taking actions specified in the incident response plan.
Six Steps for Effective Incident Response
# Preparation
The most important phase of incident response is preparing for the inevitable security breach. Preparation helps the organization determine how well they are able to respond to an incident and it should also involve policy, strategy, response, communication, and documentation determining the members of incident response to access control, tools, and training.
# Identification
Identification is the process through which incidents are detected. It enable rapid response and therefore aids in reducing cost and damages. For this step of incident response, IT staff gathers events from log files, monitoring tools, error messages, and detection system. The main aim is to detect and determine incident and their scope.
# Containment
Once an incident is detected or identified, containing it is a top priority. The main purpose of containment is to contain the damages and prevent them from further happening. The moment the incidents are detected they should be put into notice to minimize them from further happening.
# Eradication
Eradication is the phase of effective incident response, that demand removing the threats and restoring the affected system to its previous state while minimizing the data loss. At this stage, it is to ensure that proper steps have been taken, including measures that not only remove the rancorous content but also ensure that the affected system is completely clean.
# Recovery
Testing, monitoring, and validating system while putting them back into production. This is to be done in order to verify that they are not re-infected or compromised is the main task associated with this phase of incident response.
# Lessons Learned
The main essence of this phase is to help educate and improve further incident response efforts. This phase gives the opportunity to update their incident response plans with the information that was previously missed during the incident. Lesson learned reports give a clear review of the entire incident and further assistance can be taken from it.
Taking steps to create a comprehensive incident response plan can save your company substantial time and money by enabling you to get control over your system and data promptly.
So here we come with the readily-designed incident response playbook to reduce your hassle in preparing one. Here are some of the important slides that should be a part of an effective incident response playbook.
Slide 1: Addressing the Various Security Incidents and Attack
Address various security incidents and attacks to educate different team members that the organization has to face. It gives insight to members about all the security breaches and cyber-attacks that can be occurred.
This slide provides information related to traditional IT security incidents, cyber security attacks, and common techniques.
Slide2: Determining the Ransom Payment Paid by Organizations Over Time
This slide graphically represents the amount of ransom paid by the organization from time to time. You can show the quarterly data for the last two years to showcase the stabilization of ransom payments by adopting efficient incident response approaches.
You can add the stabilized ransom amount on the right side of the slide under the key takeaway to highlight the outcome of the incident response plan.
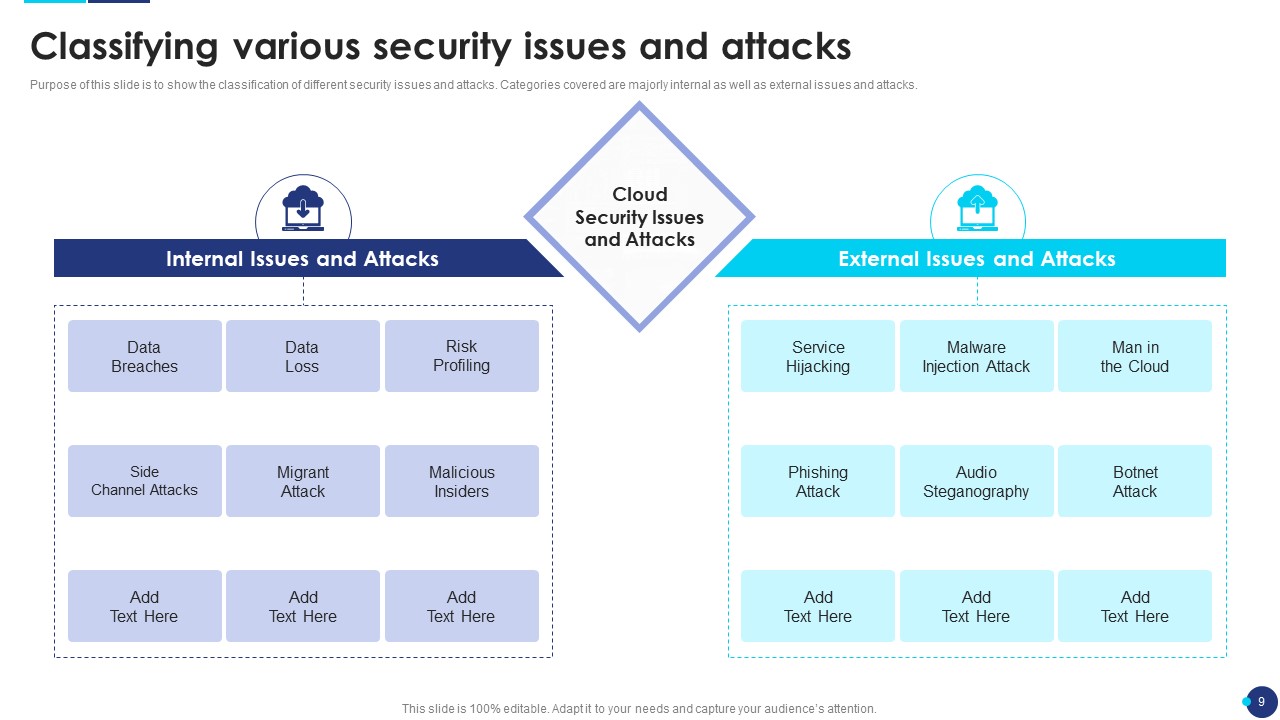
Slide3: Classifying Various Security Issues and Attack
Classify various sorts of security issues and attacks in this slide, to make a better understanding of the breaches faced by the company. In this slide, you can categorize the security issues on the basis of internal as well external issues and attacks.
Internal issues can be a data breach, data loss, or risk profiling.
External issues can be service hijacking, botnet attacks, and phishing attacks.
This slide presents the category in the form of a flow chart, you just need to edit the text.
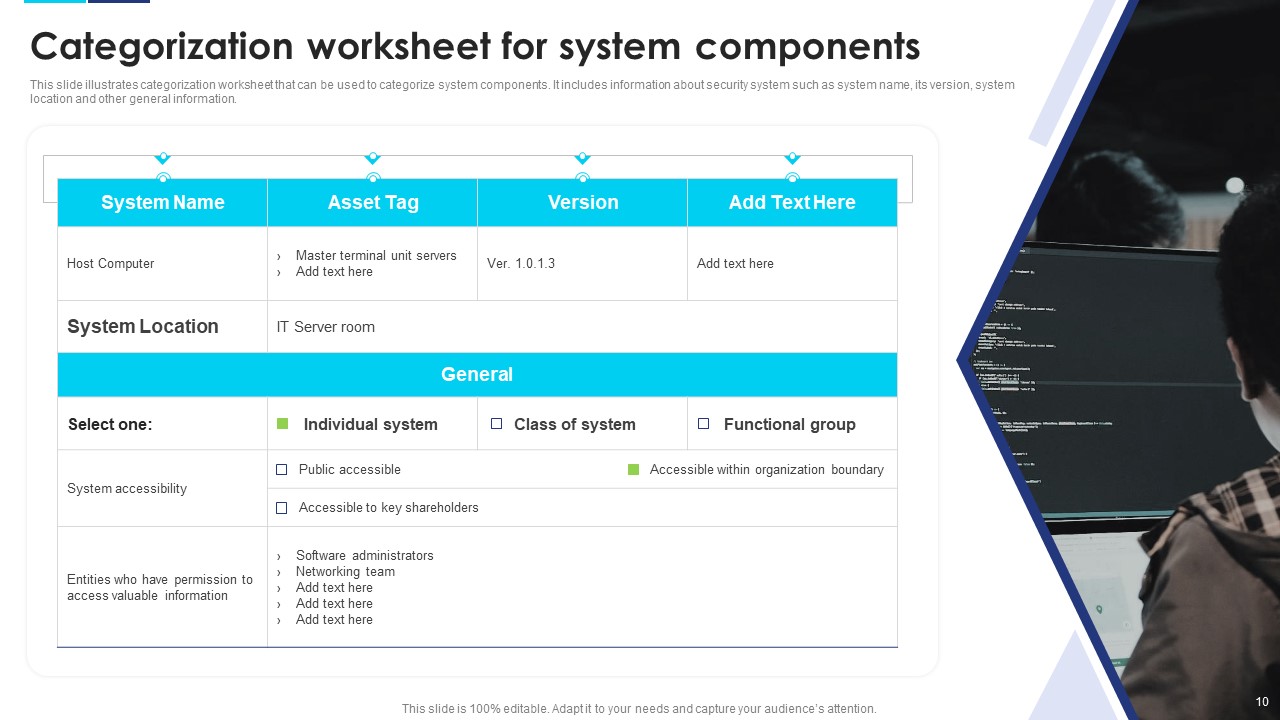
Slide4: Categorization Worksheet for System Components
Mention the slide in your incident response deck, that categorize system components. It includes information about the security system such as system name, its version, system location, and other general information.
You just need to edit the components in this readily-designed template to lessen the hassle of unnecessarily preparing from scratch.
Slide5: Addressing the Cyber Incident Logging Process
This slide displays the logging process for a cyber incident logging. It covers the key highlight of logging that includes process ID, procedure, description, and owner details. For instance, the procedure is:
- Create a new incident- A service desk analyst will create an incident summary which will be escalated to the service manager after interacting with a user.
- Complete incident details- Analyst will assess the incident categorization and will verify the incident accordingly.
Accordingly you can mention such steps in this slide for minimizing the incidents.
You can edit the text in the ready to use template as per the requirement of an organization.
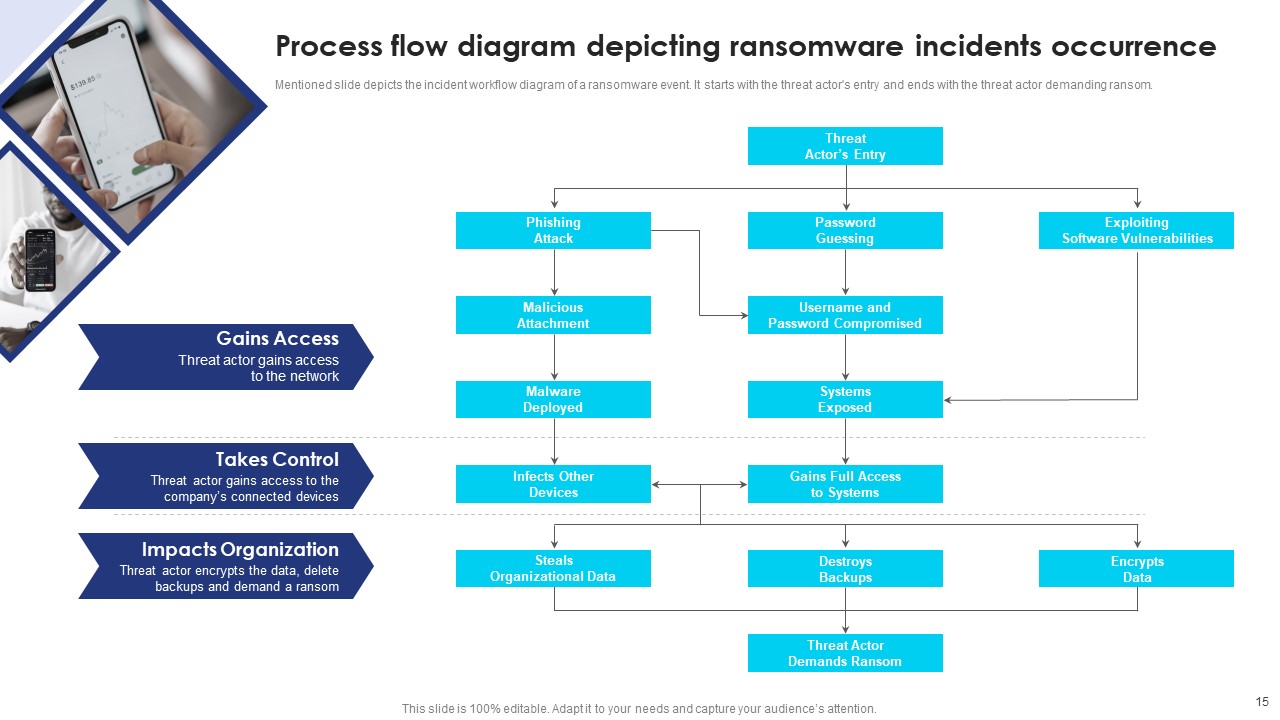
Slide6: Process Flow Diagram Depicting Ransomware Incident Occurrence
In this slide present the incident workflow diagram of a ransomware event. The flow starts with the threat actor’s entry and ends with threat actor asking for a ransom.
Three stages mentioned in the flow diagram:
Gain access- Here the threat actor gain the access to the network.
Takes control- Threat actor gets accessed to company’s connected device.
Impacts organization- Threat actor encrypts the data, delete the backups, and demands the ransom.
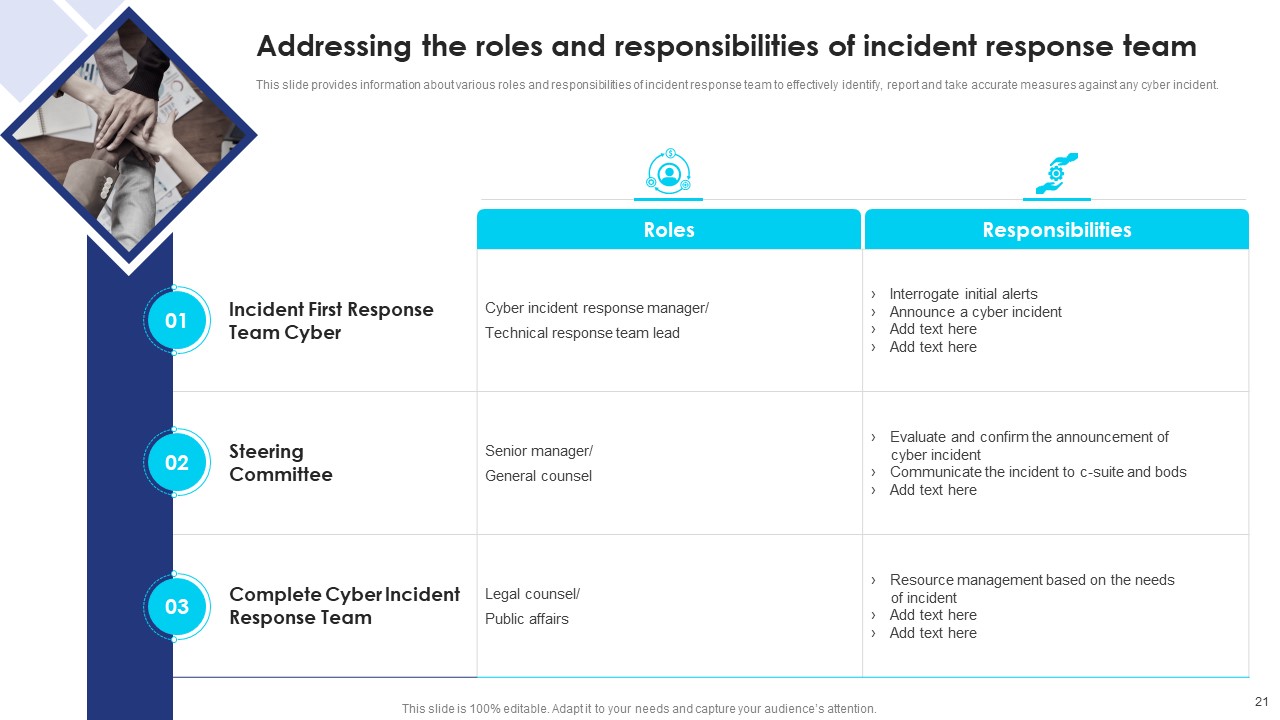
Slide7: Addressing the Roles and Responsibilities of an Incident Response Team
This slide provides information about various roles and responsibilities of the incident response team to effectively identify, report, and takes accurate measures against any cyber incident.
However, mention the duties to each staff and committee member so that there won't be any delay in taking necessary actions and incidents can be minimized.
Divide the authority among:
- Cyber incident first response team.
- Steering committee
- Complete cyber incident response team
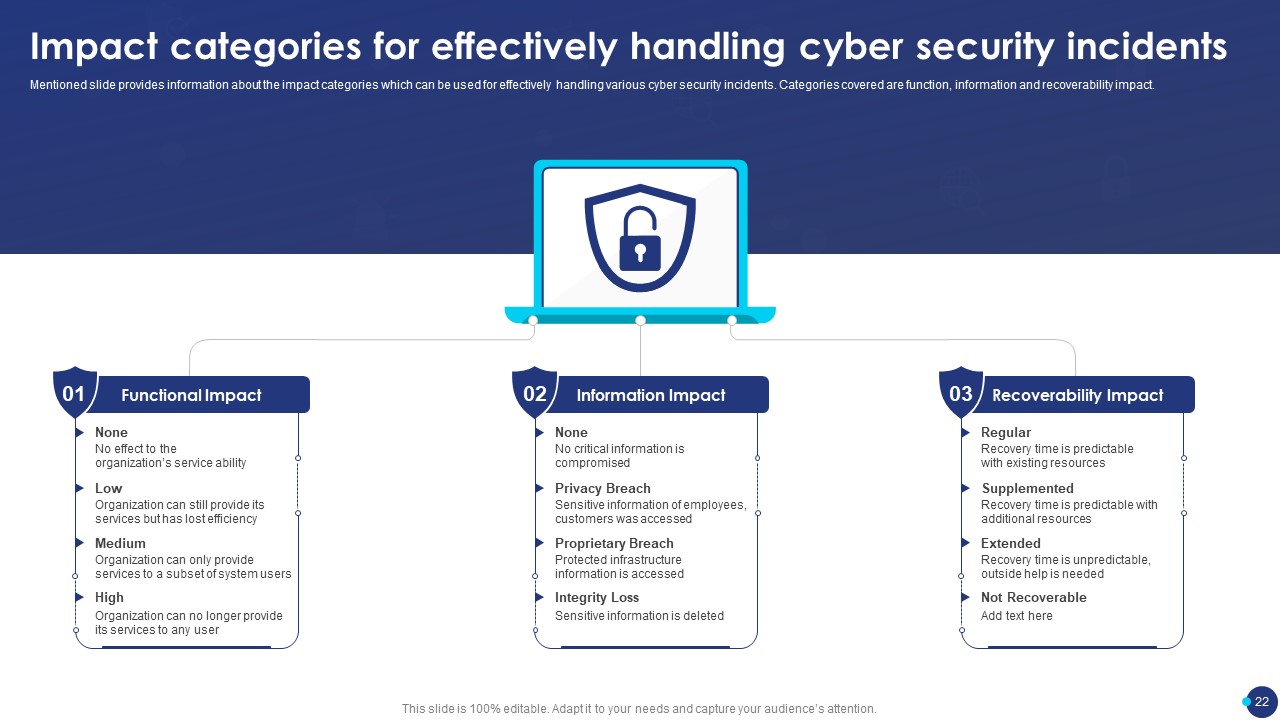
Slide8: Impact Categories for Effectively Handling Cyber Security Incidents
Present information about the impact categories so that it can be used for effectively handling various cyber security incidents in this slide.
Further, Categories covered are -
- Function Impact
- Information Impact
- Recoverability Impact
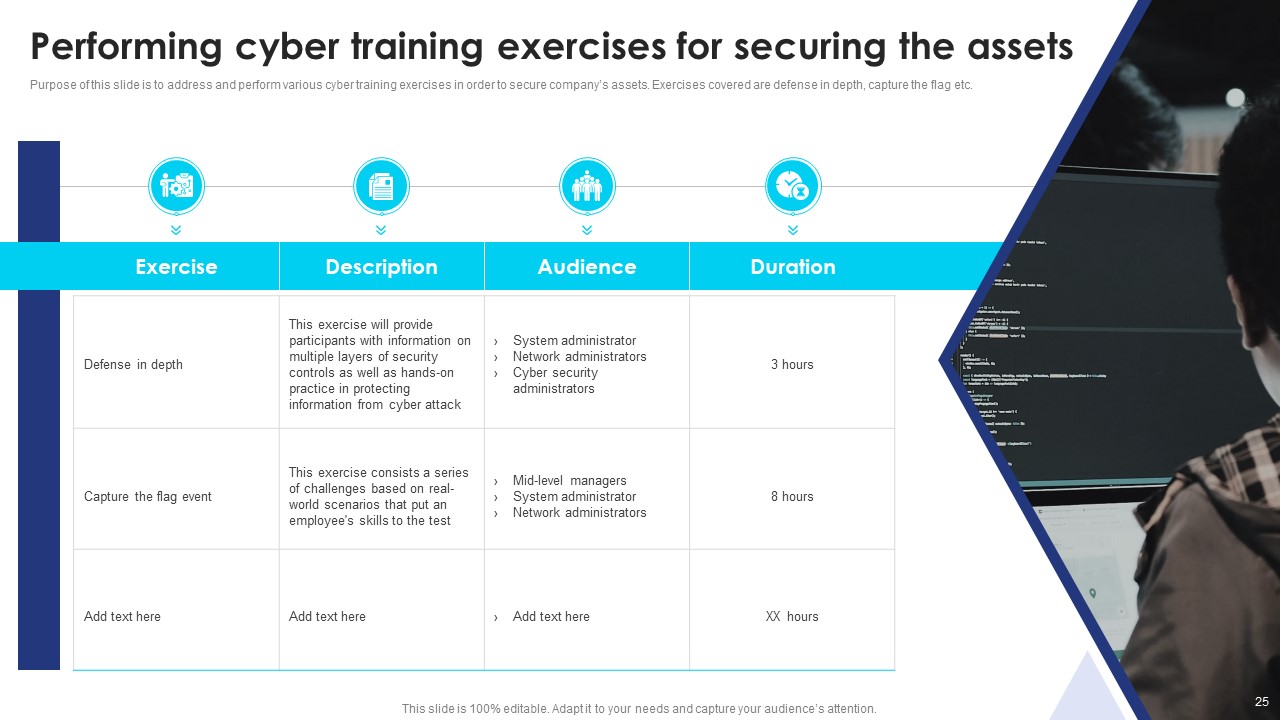
Slide9: Performing Cyber Training Exercises for Securing the Assets
The purpose of this slide is to address and perform various cyber training exercises in order to secure the company’s assets. Exercises covered are defense in depth, capture the flag, etc. And with each exercise mention the description, audience, and duration.
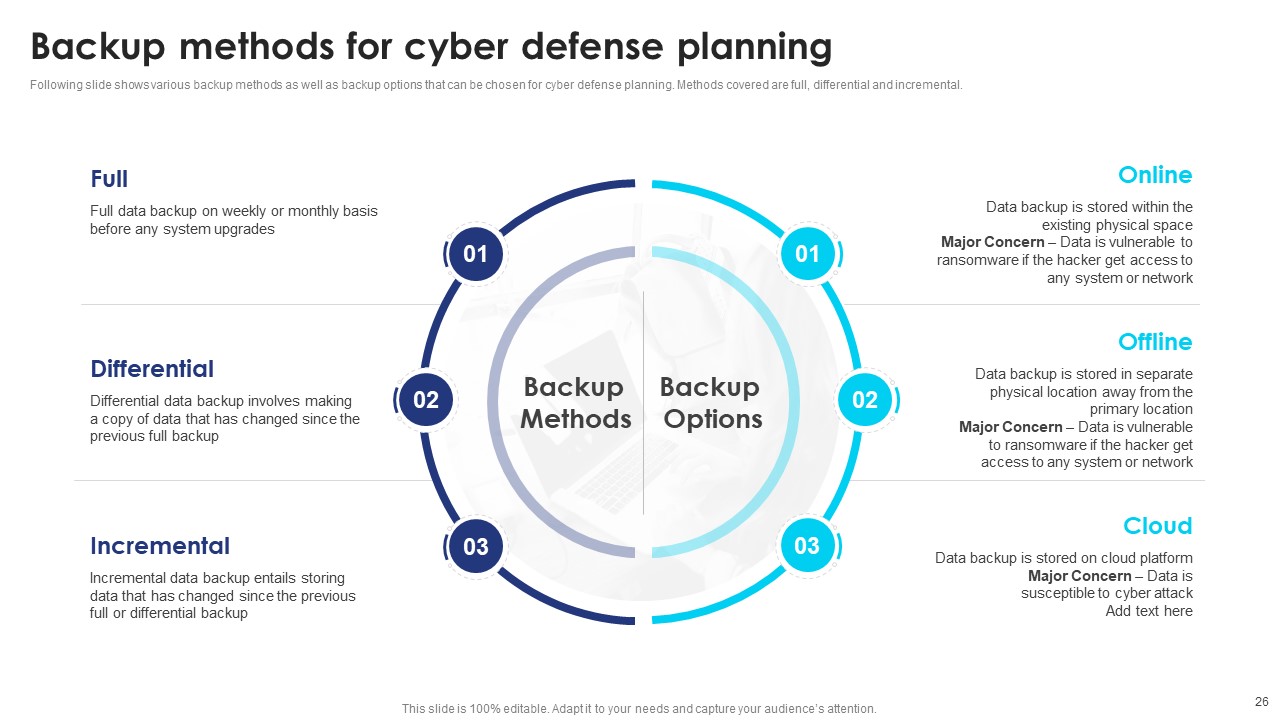
Slide10: Backup Methods for Cyber Defense Planning
Mention the slide to showcase various backup methods and backup options. This can aid in cyber defense planning.
Further methods covered are:
- Full- Full data backup on a weekly or monthly basis before any system upgrades
- Differential- Differential data backup involves making a copy of data that has changed since the previous full backup
- Incremental- Incremental data backup entails storing data that has changed since the previous full or differential backup
Moreover, Back options can be online, offline, and cloud. This is 100
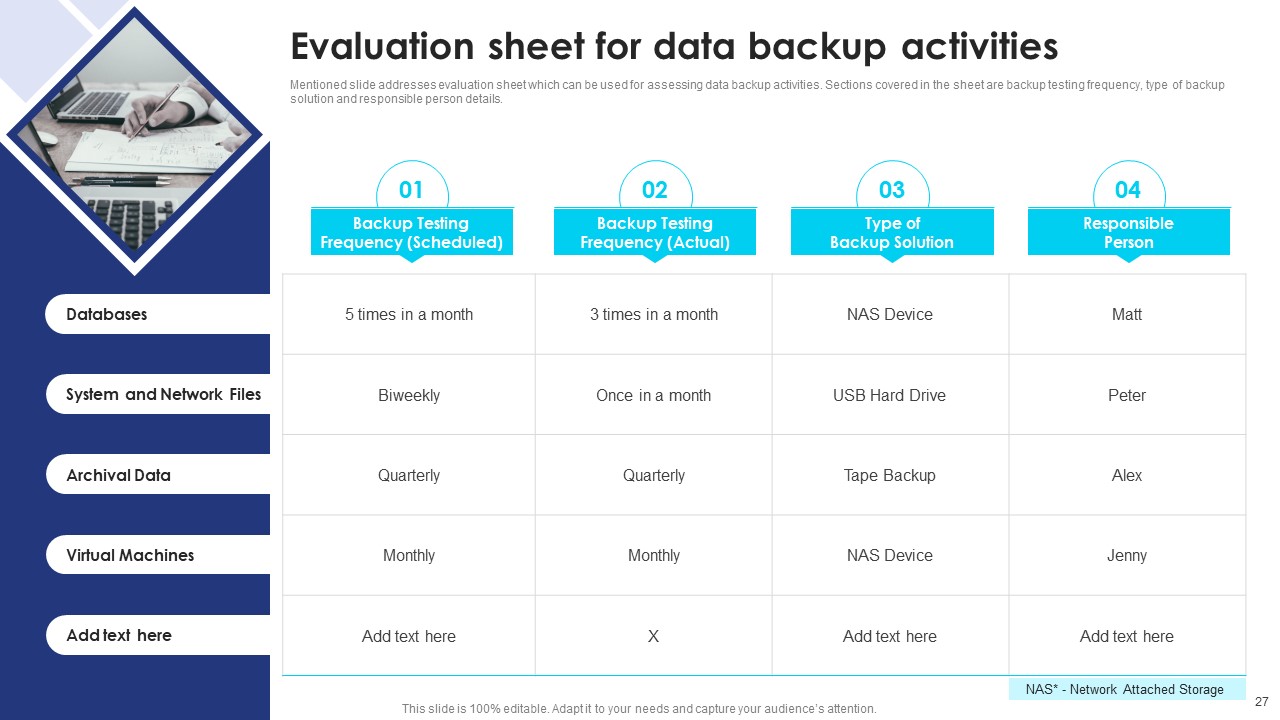
Slide11: Data Backup Evaluation Sheet
Mention this slide in your deck to showcase Data Backup Activities. Sections covered in the sheet are backup testing frequency, type of backup solution, and responsible person details.
You can make necessary changes as per the organization’s requirement in the template given below.
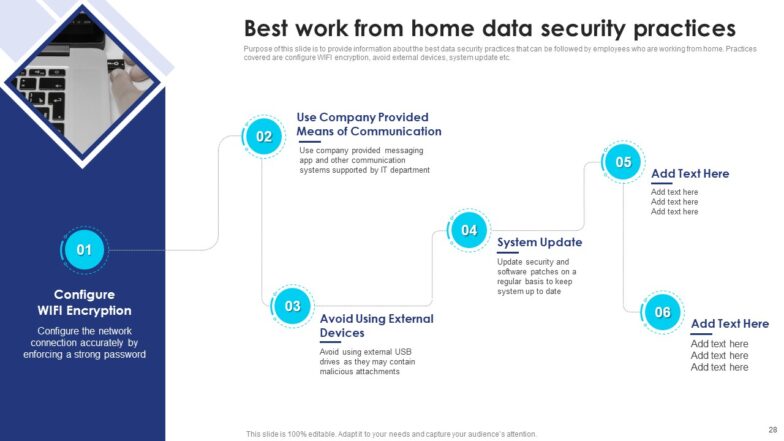
Slide12: Best Work from Home Data Security Practices
Mention a slide to provide information to employees who are working from home regarding the best data security practices. Practices covered are configuring WIFI encryption, avoiding external devices, system updates etc.
So, motive behind the slide is to define guidelines for the employees who are working from home to reduce security breaches and cyber-attacks.
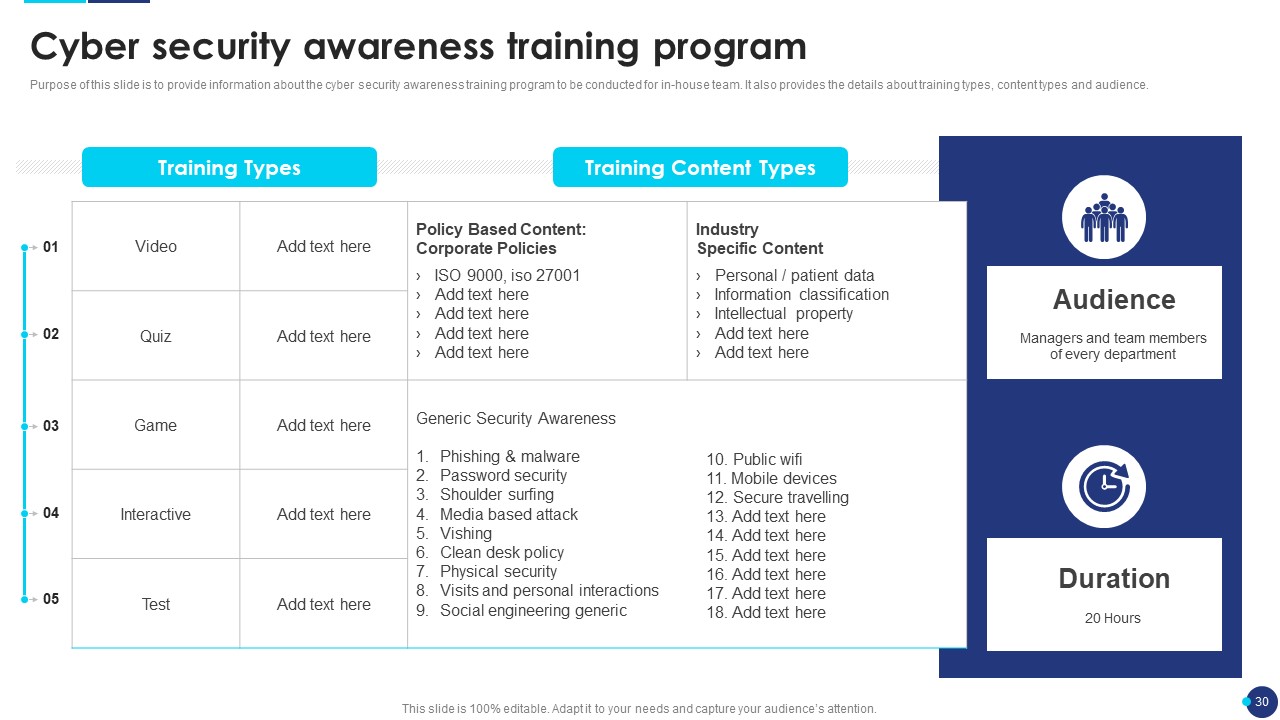
Slide13: Cyber Security Awareness Training Program
Mention the slide to showcase the awareness training program for an in-house team so to effectively implement the incident response plan. Moreover, it also provides details about training types, content types, and audience.
Further, this slide presents the initiative taken by the organization to aware the employees about cyber security by organizing a training program.
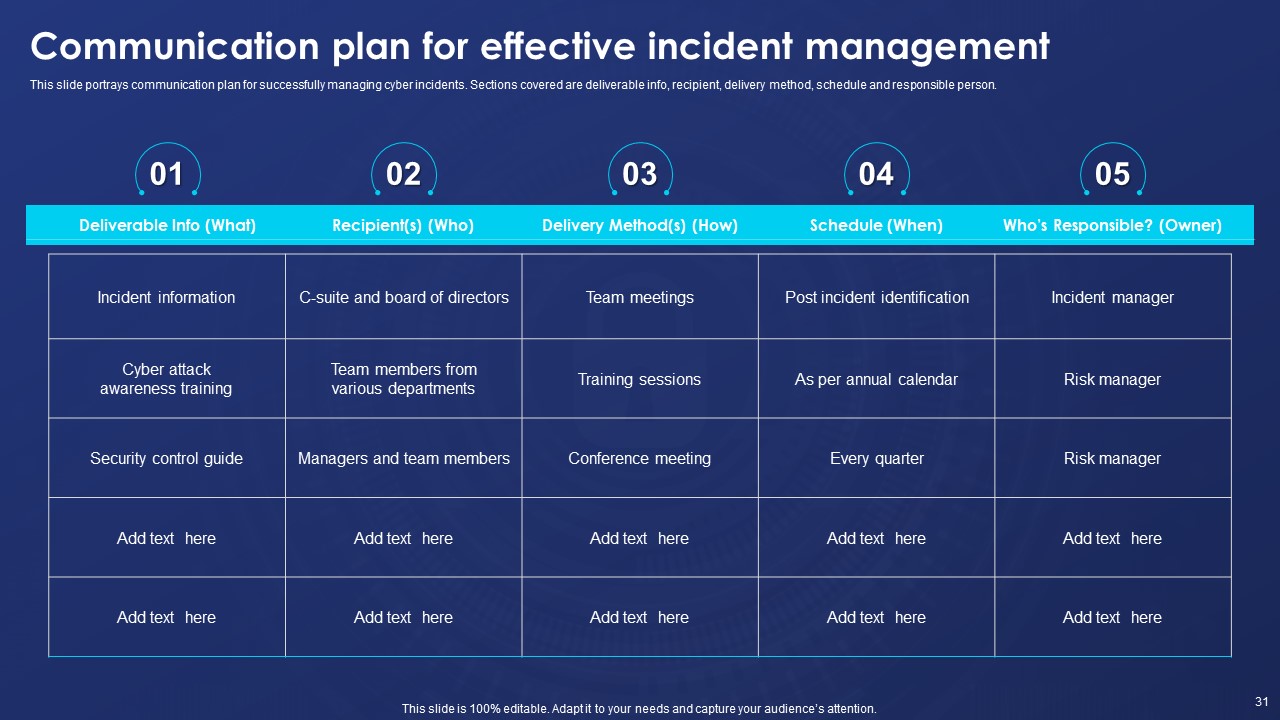
Slide14: Communication Plan for Effective Incident Management
Present the communication plan for successfully managing cyber incidents. Further, Sections covered are deliverable info(what), recipient(who), delivery method(how), schedule(when), and responsible person(owner).
So, edit the communication plan as per the requirement of the company.
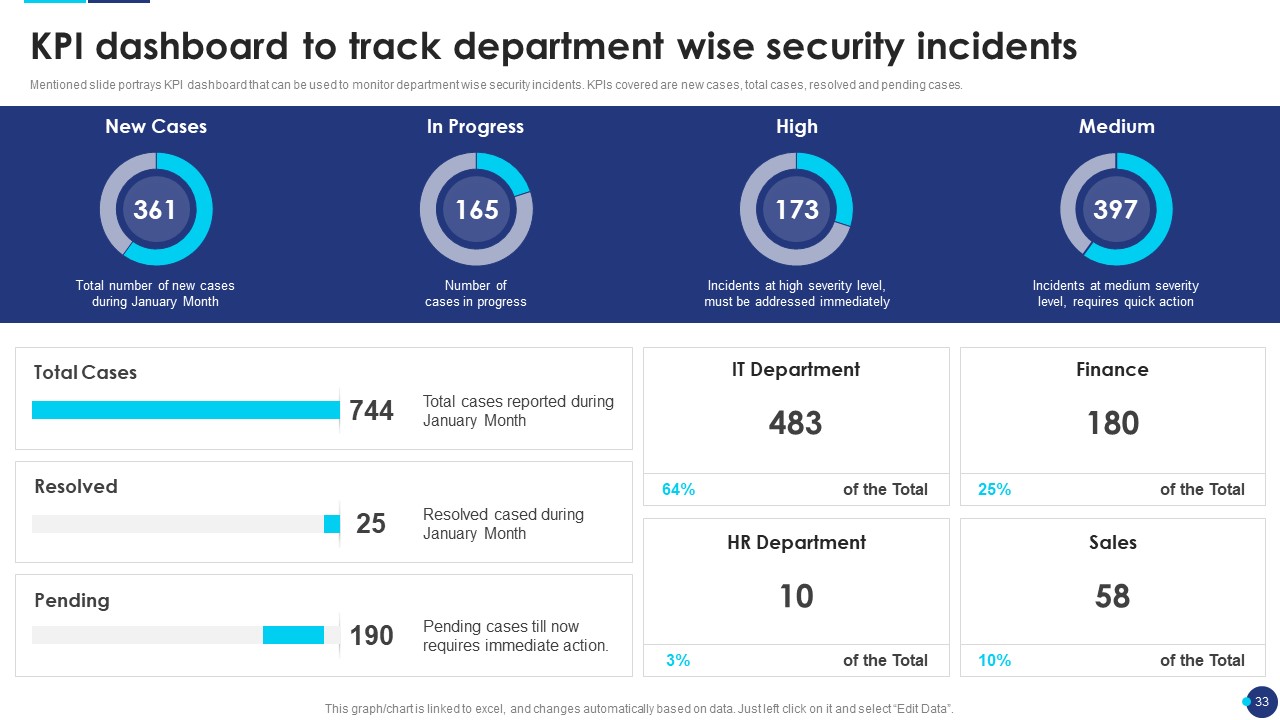
Slide15: KPI Dashboard to Track Department Wise Security Incidents
Add this slide to portray a KPI dashboard so that it can be used to monitor department-wise security incidents. Further, KPIs covered are new cases, total cases, resolved and pending cases.
Take into consideration different departments to track department-wise security incidents like:
- IT Department
- Finance Department
- HR Department
- Sales Department
Conclusion
So, basically incident response playbook helps the organization to properly plan out the ways to minimize the incident occurring in the company. The main aim to create a comprehensive incident response plan is to save your company substantial time and money. The incident response playbook enables you to get control over your system and data promptly.
Avoid the hassle by just downloading this 100% editable playbook template and can make changes as per the requirement of the company. Call directly at +1-408-659-4170 for further queries and our team will respond you in best possible way.





 Customer Reviews
Customer Reviews









![All You Need to Know About an Agile Playbook Template [Free PDF Attached]](https://www.slideteam.net/wp/wp-content/uploads/2022/06/Angile-Development-Banner_Size1013x441_I-150dpi66-1013x441.jpg)
![Powerful Digital Transformation Playbook for 2022 [Free PDF Attached]](https://www.slideteam.net/wp/wp-content/uploads/2022/07/47-1013x441.png)












