In a recent cybercrime case, a ransomware attack targeted Toyota, a major automaker. The hackers demanded a ransom of $30 million in Bitcoin. Toyota refused to pay the ransom, but the attack caused widespread disruption to Toyota's production lines. This devastating cyber-attack compromised sensitive customer data and cost them millions in damages.
That's right, folks. Cybersecurity risks are very real, and they can happen to anyone, no matter how big. But don't get panicky yet because today, we've got something that will make you a digital pro!
Is your business equipped enough to thrive in the age of Artificial Intelligence and rapid technological advancement? Find out and conquer the competition using our Must-Have Technology Plan Templates!
Feeling vulnerable? Here are our Cybersecurity Plan Templates– The ultimate weapon to safeguard your digital kingdom!
Cybersecurity Plan Templates are the pre-designed documents or frameworks from SlideTeam that provide an organized approach to creating and implementing a cybersecurity strategy for an organization. These templates include step-by-step guides, procedures, checklists, expert tips, and best practices to help businesses or individuals establish, maintain, and enhance robust cybersecurity measures.
These valuable tools provide a structured foundation for safeguarding digital assets, mitigating risks, and staying ahead of evolving cyber threats.
Our templates are for everyone– Whether you're a business owner, an IT professional, or someone who wants to protect their online presence – they've got you covered. These let you craft a battle-ready cybersecurity strategy and keep those cyber villains at bay.
Cybersecurity isn't just a choice; it's a responsibility. Gear up with our Must-Have Cybersecurity Policy Templates and protect what matters most!
And the best part? These are pre-designed, fully customizable, well-researched, and packed with the necessary cybersecurity information to give you a strong head start on Information Security Awareness. It's like having a cybersecurity SWAT team at your fingertips!
So, let's dive into these game-changing Templates!
Template 1: Formulating Cybersecurity Plan To Safeguard Information Assets PowerPoint Presentation Slides
A risk assessment and management plan can help organizations identify cybersecurity threats and implement measures to mitigate them. This one-stop-shop provides an efficient way to formulate a cybersecurity plan to safeguard information assets. It also discusses types of cybersecurity threats, the process of managing information security risks, and an information security risk management plan. Furthermore, the template covers vulnerability rating, risk assessment matrix, mitigation plans, training, roles and responsibilities of the risk management team, budget allocation, and the impact of a risk management plan on the information security capabilities of the organization.
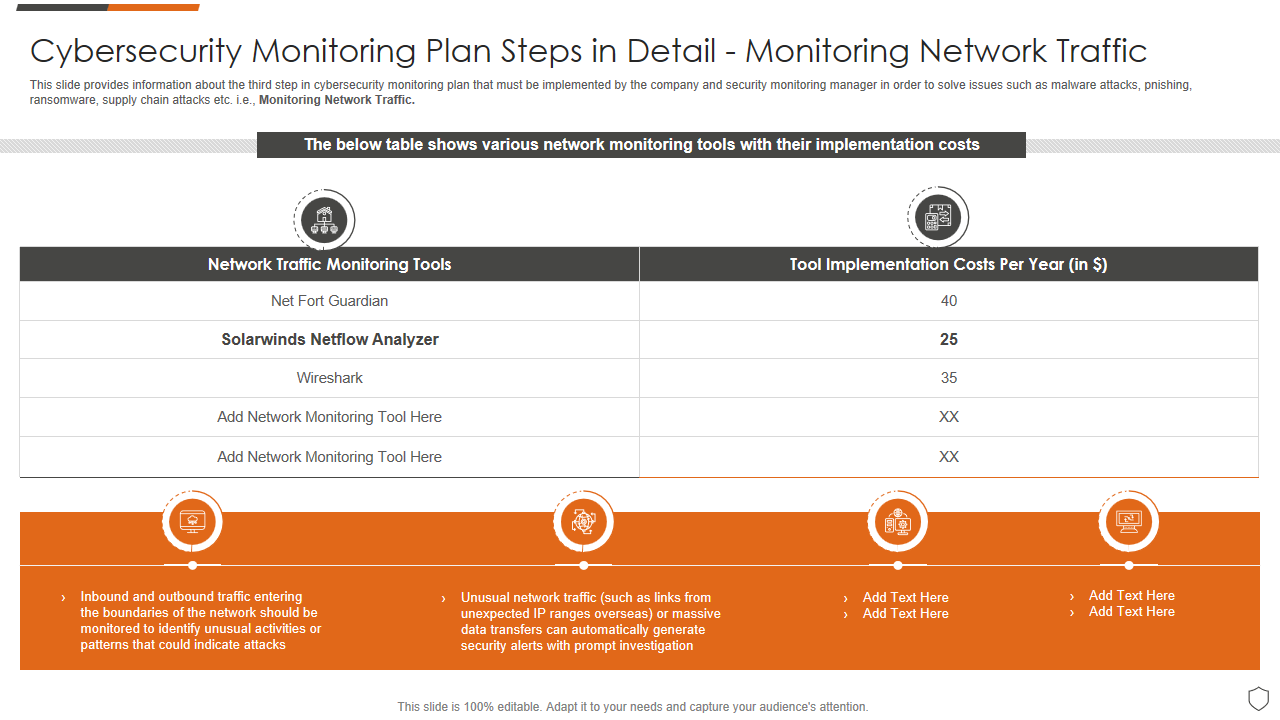
Template 2: Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic
See who is sneaking on you using this super-helpful PPT Template. See who is accessing your network, what they are doing, and where they are coming from. This slide holds information on the third step (Monitoring Network Traffic) in the cybersecurity monitoring plan, helping you to identify and block threats, ransomware, supply chain attacks, or malware attacks. Encompassed with four stages, the template allows you to define your network traffic monitoring goals, choose the right traffic monitoring tools, Implement the tools, and analyze the network traffic data.
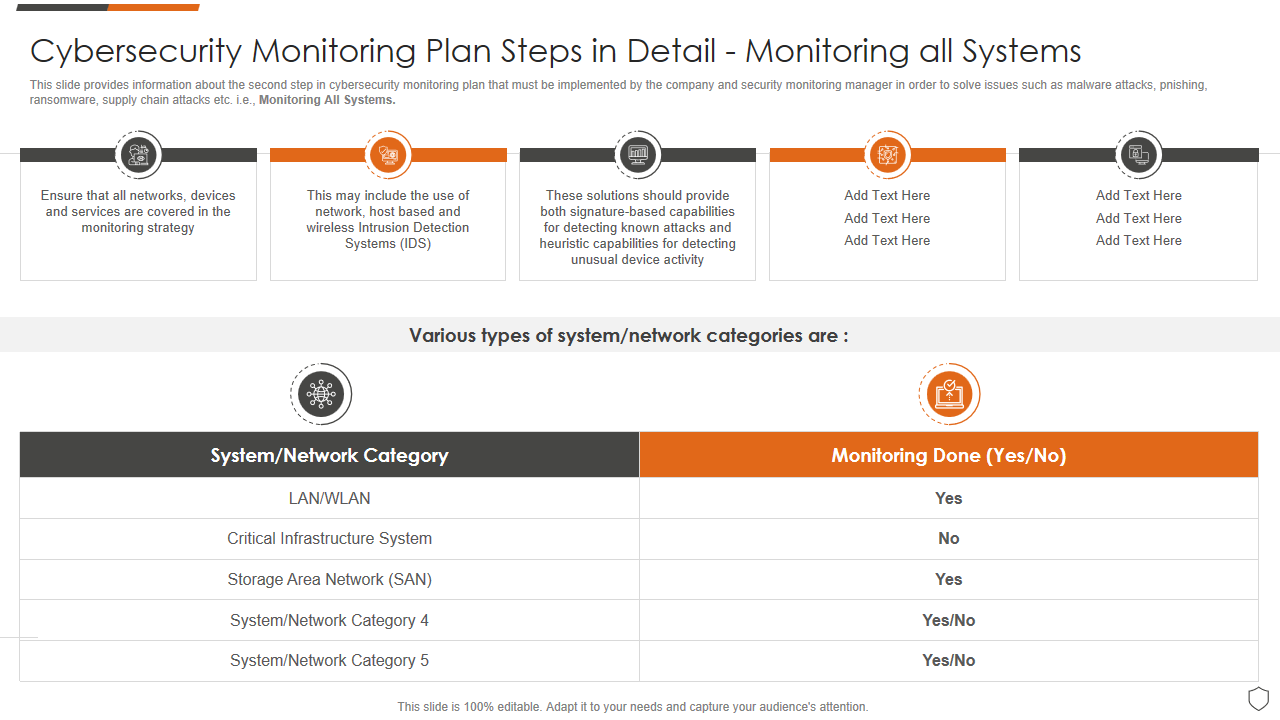
Template 3: Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems
This PPT Preset holds the keys to your cyber security doors! It highlights the crucial second step within the cybersecurity monitoring plan (Monitoring All Systems) that the company and the security monitoring manager must implement to address various cybersecurity threats and attacks. This versatile template facilitates the presentation of information across five distinct stages. Additionally, it allows for exploring critical aspects such as critical infrastructure systems, storage area networks, and system network categories.
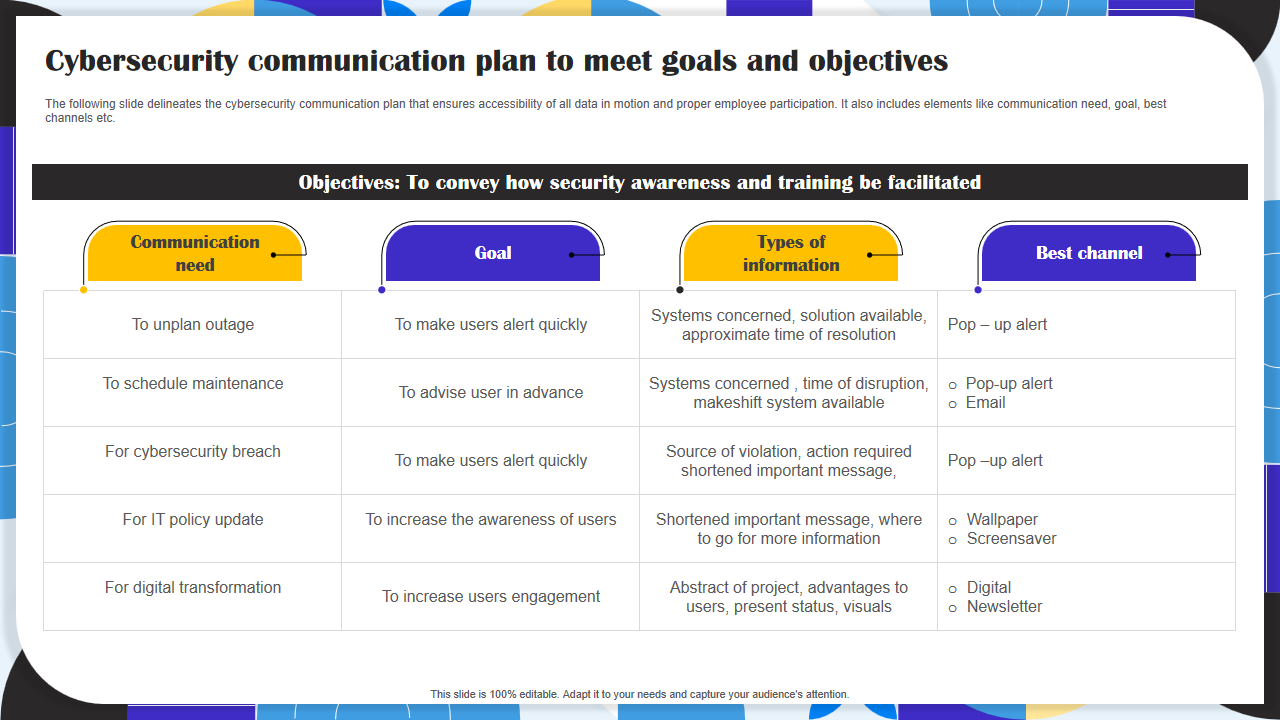
Template 4: Cybersecurity Communication Plan To Meet Goals And Objectives
Have you ever wondered how to make cybersecurity as fun as cracking a secret code? Then, this template holds all your answers! It provides a structured framework for clear and concise messaging. The template delineates the cybersecurity communication plan that ensures accessibility of all data in motion and proper employee participation. It also includes elements like communication needs, goals, best channels, etc. Additionally, it outlines the key strategies and tactics, ensuring everyone in your organization stays on the same page when it comes to cybersecurity.
These are not just templates but the hacks to hack a hacker!
In a world where cyber threats loom large and even giants like Toyota can fall victim, the importance of cybersecurity has never been clearer. But fret not, we’ve provided you with our best tools to gain knowledge and awareness and turn the tables on those cyber threats, maintaining your peace of mind! Remember, in the digital world, it's not about luck – it's about having the right plan. Stay safe out there, cyber warriors!
Don't just manage risks; master them with flair! Our Top 5 IT Security Risk Management Plan Templates are like the James Bond of IT security. Try these out now!
FAQs on Cybersecurity Plan Templates
How do you create a cybersecurity plan?
Creating a cybersecurity plan involves several crucial steps:
- Objectives and Goals: Define the plan's objectives and what you aim to protect.
- Asset and Risk Assessment: Identify your digital assets and potential risks.
- Assess Current Security: Evaluate existing security measures, including firewalls, antivirus software, intrusion detection systems, and employee training.
- Risk Assessment: Analyze potential threats and prioritize them based on the risk level.
- Policies and Procedures: Establish clear cybersecurity policies and procedures. These include data encryption, password management, access control, incident response, and employee training.
- Implement Security Measures: Put in place security tools and configurations.
- Employee Training: Educate employees about cybersecurity best practices. Stay updated on the cybersecurity regulations and compliance requirements.
- Incident Response: Develop a strategy for responding to security incidents.
- Monitoring and Updates: Continuously monitor systems and update security measures. Ensure your plan aligns with these measures.
- Data Backup and Recovery: Create a robust data backup and recovery plan.
- Vendor and Supply Chain Security: Assess and ensure the security of vendors and suppliers.
- Compliance: Stay compliant with relevant cybersecurity regulations.
- Testing and Simulation: Test the plan through cybersecurity drills.
- Communication Plan: Develop a communication strategy for breaches.
- Documentation: Maintain records of security incidents and improvements.
- Regular Reviews: Continuously review and update the plan.
- Board Involvement: Ensure senior management and the board are engaged.
- Security Culture: Promotes a culture of cybersecurity awareness.
What is a cybersecurity implementation plan?
A cybersecurity implementation plan is a detailed strategy that outlines how an organization intends to execute and implement its cybersecurity policies, procedures, and measures. It provides a roadmap for implementing cybersecurity policies and enhancing the organization's security posture. Here are some of the critical components of a cybersecurity implementation plan:
- Objectives: Covers the scope of the implementation plan
- Roles: Defines roles and responsibilities of individuals and teams involved in implementing cybersecurity measures
- Risk Assessment: It is important to identify vulnerabilities, threats, and potential risks to your organization's digital assets
- Security Measures
- Asset Inventory: Includes digital assets such as hardware, software, data, and network resources
- Incident Response: Outlines the steps to take in the event of a security breach, including incident detection, containment, eradication, and recovery
- Access Control: Explain the procedures for controlling and managing user access to systems and data
- Data Protection: This component addresses how sensitive data will be encrypted, backed up, and securely stored to prevent data breaches
- Compliance: Discusses how the organization will maintain compliance with relevant cybersecurity regulations and standards
- Testing and assessment: Involves the regular testing and vulnerability assessments of the security measures
- Budget and Timeline: Involves creating a timeline with specific milestones for the implementation of various cybersecurity measures
- Documentation: This component establishes processes for documenting security incidents, improvements, compliance efforts, and retaining records for future reference and auditing
- Budget and Resource Allocation: This defines resource allocation and budget for implementing and maintaining cybersecurity measures
- Communication: Outlines the organization's communication structure to share security updates, incidents, and policy changes with employees and stakeholders
- Continuous Improvement: This element emphasizes the importance of continuous improvement and adaptation to evolving cybersecurity threats and technologies
What is the importance of a cybersecurity plan?
A cybersecurity plan is crucial because it:
- Protects Against Threats: A cybersecurity plan shields serves as a defense mechanism against cyberattacks and data breaches.
- Preserves Reputation: A data breach can severely damage an organization's reputation and erode trust among customers and partners. A well-executed plan helps maintain trust and reputation.
- Legal and Regulatory Compliance: Many industries have specific cybersecurity regulations and compliance requirements. A cybersecurity plan ensures adherence to these standards and eliminates the risk of penalties and legal consequences.
- Prevents Disruption: Minimizes downtime and financial losses without interruptions.
- Secures Data: Safeguards sensitive information, such as customer data, financial documentation, and intellectual assets, from unauthorized access, theft, or manipulation.
- Builds Trust: A well-executed cybersecurity plan fosters customer and stakeholder trust, encouraging long-term relationships.
- Adapts to Threats: A well-structured plan helps evolve an organization according to the changing cyber threats.
What are the five types of cyber security?
Cybersecurity encompasses various layers and approaches to protect digital systems and data. Here are five essential types of cybersecurity:
- Network Security: This type focuses on securing an organization's network infrastructure, including routers, firewalls, and intrusion detection systems. It aims to safeguard data in transit, prevent unauthorized access, and detect and respond to network threats.
- Endpoint Security: Endpoint security safeguards individual devices (endpoints), such as computers, smartphones, and tablets, from malware, unauthorized access, and other threats. This involves the implementation of antivirus software, encryption, and access controls.
- Cloud Security: Cloud security protects data and applications hosted in cloud environments. It involves securing cloud infrastructure, monitoring user access, and ensuring data encryption and compliance with cloud service providers' security policies.
- Application Security: Application security focuses on the security of software and applications. It involves identifying and addressing application vulnerabilities through secure coding practices, penetration testing, and code analysis tools.
- Information Security: This is a broader category encompassing all aspects of protecting sensitive data, including data classification, access control, encryption, and data loss prevention. It ensures confidentiality, integrity, and availability of data.





 Customer Reviews
Customer Reviews