A security checklist and assessment are essential tools for fortifying an organization’s digital assets and operations. A security checklist comprises a compendium of measures and best practices to ensure the effective implementation of critical controls. A security assessment also appraises an organization’s security stance, pinpointing vulnerabilities, and potential risks.
These processes enable organizations to rectify security weaknesses and diminish the chances of data breaches, financial setbacks, and damage to their reputation. The end-result is fostering trust with customers and stakeholders.
Explore the top five security PowerPoint templates featuring samples and examples for creating security reports. Download these here to safeguard your valuable resources.
With security apprehensions addressed, busineses can concentrate on actualizing their mission and vision.
Each of the security templates is 100% editable and customizable. You get a starting point, the much-needed structure and flexibility to tailor the presentation to unique audience profiles. Let’s explore.
Access the network security presentation templates here and secure the network against unauthorized access.
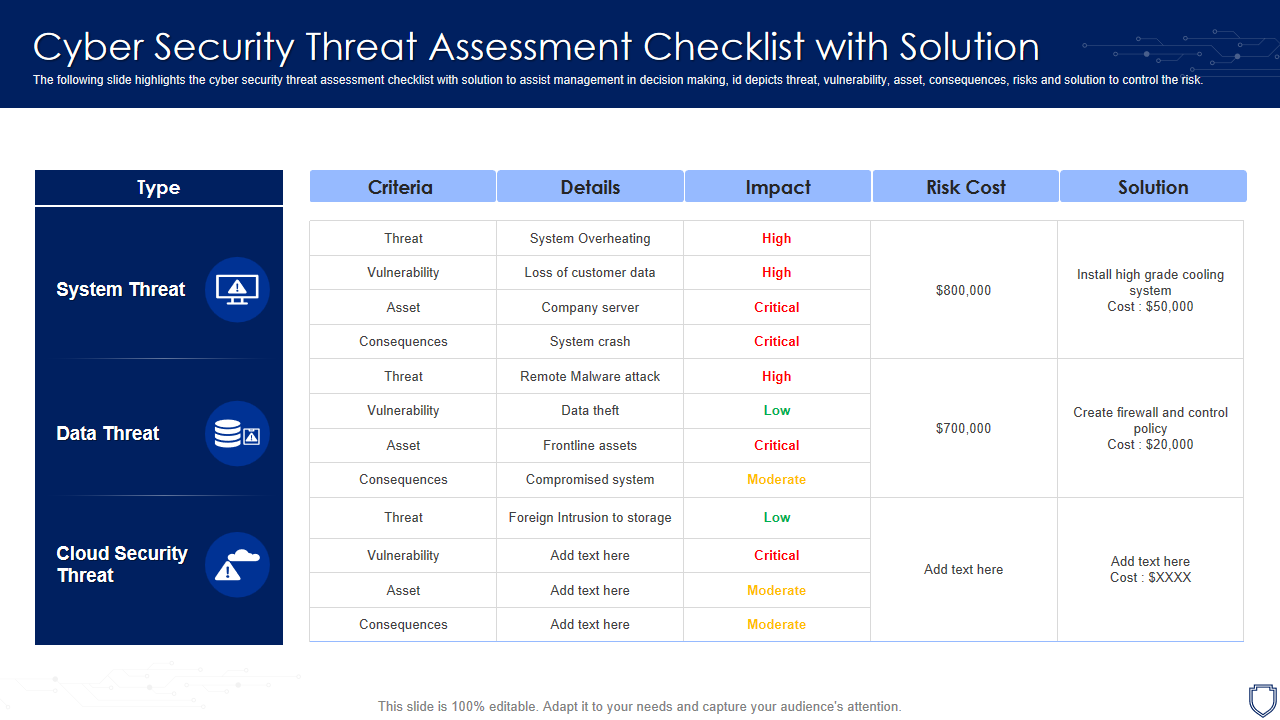
Template 1: Cyber Security Threat Assessment Checklist with Solution
This PPT Presentation offers a structured format detailing potential cyber threat, their likelihood impact, and recommended solutions and preventive measures. It contains a complete checklist with the three major threats of system, data, and cloud security covered. Each of the three threats is mapped to its individual criteria, details, impact, risk cost, and the perfect solution.
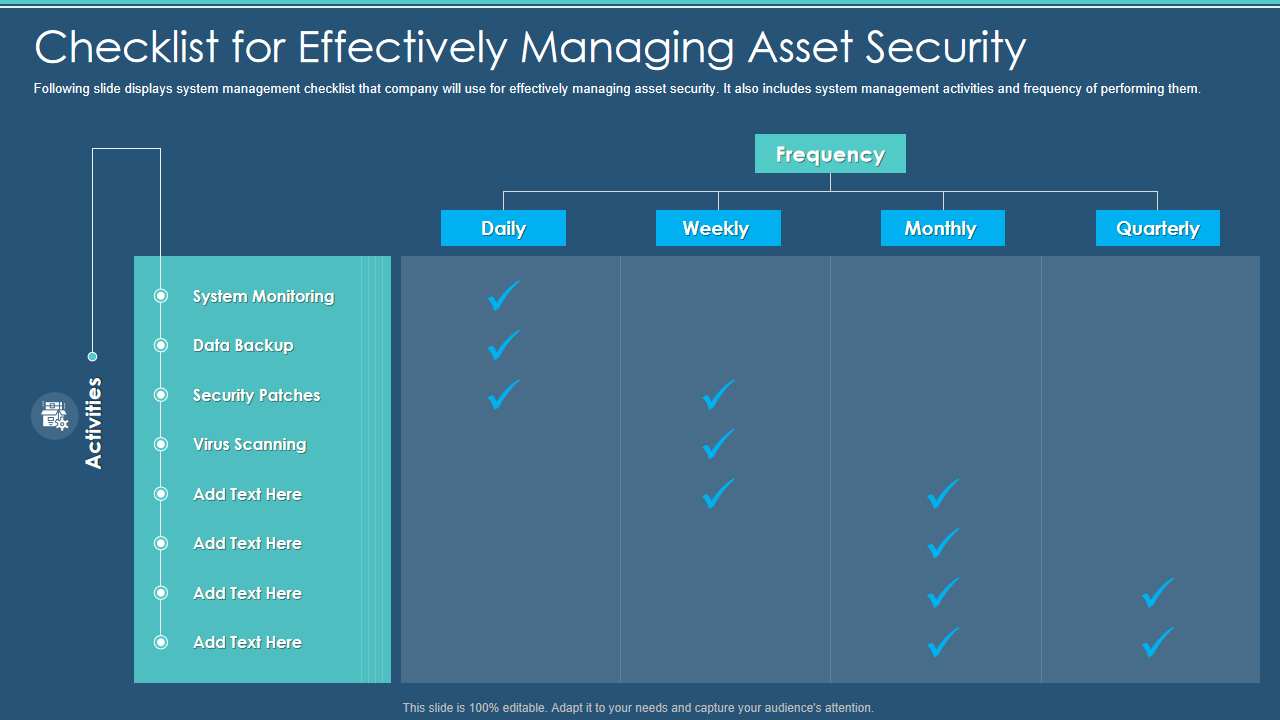
Template 2: Information Security Program Cybersecurity Checklist Managing Asset Security
This PPT checklist showcases the process for managing asset security presentation graphics. This visual PPT design helps share information about activities and frequency. Use this template to highlight other vital features, such as system monitoring, data backup, security patches, virus scanning, etc as well. Professionals engaged in network security services can make the most of it.
Template 3: Information Security Complete Information Security Implementation Checklist
This PowerPoint Template outlines a systematic approach that organizations use in employing security measures. Use this slide to ingrain the habit of frequent staff training, hardware and software updates, antivirus software, strong passwords, minimized administrative privileges, data backup, etc. This template also shares details about recovery planning, strong IT policies, secure communications, disposal of data and equipment, device security, and access control measures
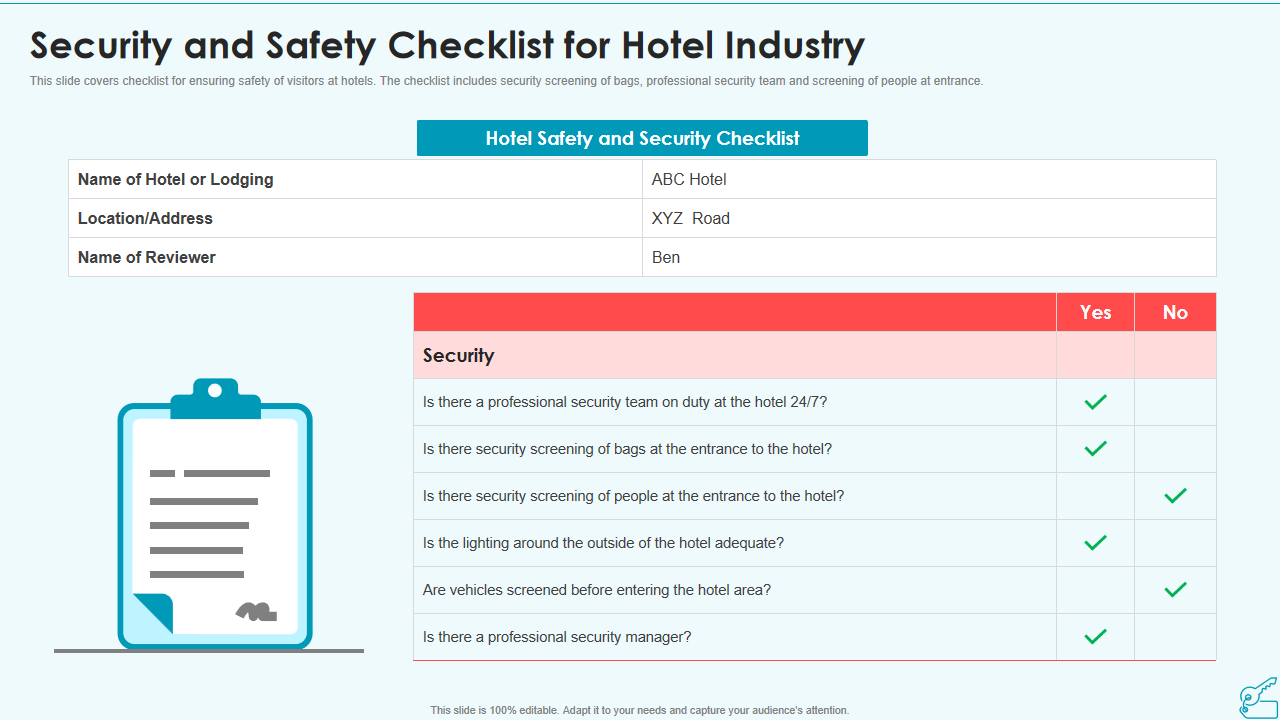
Template 4: Security and Safety Checklist for Hotel Industry
Are you looking for a quality resource to highlight security and safety measures in the hotel industry? If yes, your search ends here. Our presentation template provides an opportunity to make effective communication about risk and threats involved. The PowerPoint layout displays hotel safety and security checklist, such as the name of the hotel or lodging, location or address, name of the reviewer, etc. Along with this, it also contains some critical security questions that can be answered with a YES or NO. Hotel security is one aspect that can excel with this PPT visual.
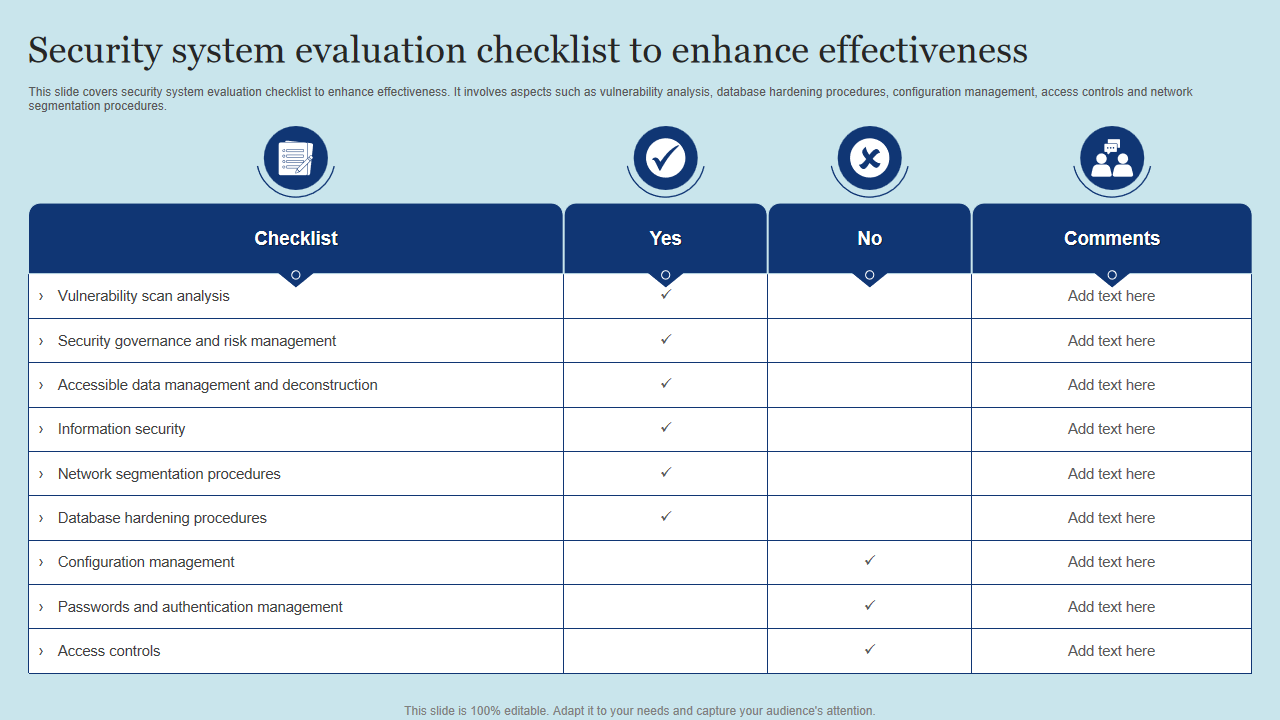
Template 5: Security System Evaluation Checklist to Enhance Effectiveness
This one-page PPT Template shares details about network security checklists such as vulnerability scan analysis, security governance and risk management, accessible data management and deconstruction, information security, etc. Use it to also gather comprehensive processes on network segmentation, database hardening, configuration management, passwords and authentication management, and access controls. Download now and make a part of hour safety and security presentation.
Template 6: Checklist to Ensure Asset Protection from Internal Threats Cybersecurity Incident and Vulnerability
Data protection is vital for business success. This six-point checklist PPT Presentation guides your colleagues to ensure asset protection from internal threats. This PPT Design makes creating a checklist and asking your people to share their responses accessible. Some questions that the slide makes businesses answer are whether employees use mobile devices to access email, use company assets such as laptops and desktops, use solid passwords, whether remote file exchange is encrypted, etc.
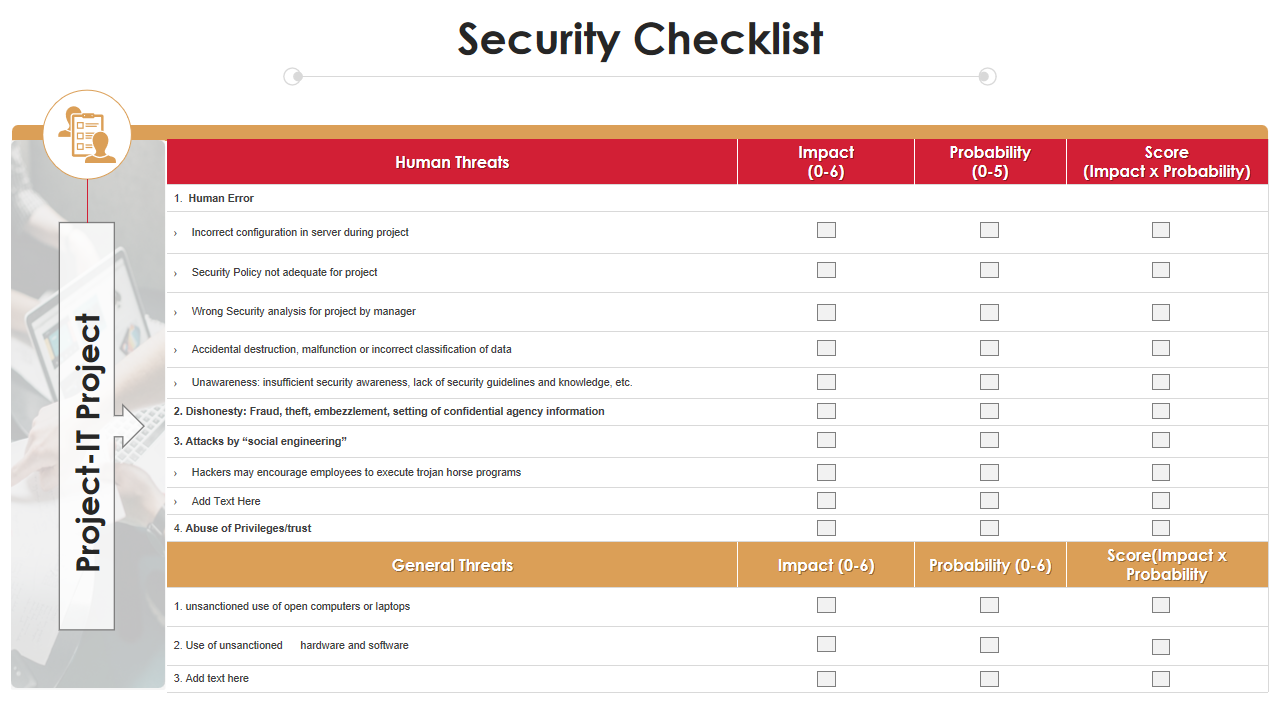
Template 7: Security Checklist Project Analysis Templates Bundle PPT Slides
Use this PowerPoint Template to prepare a list of threats involved in business functioning. This slide shows both human and general threats. Besides this, it also showcases the level of impact, probability, and overall score. The presentation layout helps share detailed information with your team about threats such as human error, dishonesty, fraud, theft, attacks by social engineering, abuse of privileges and trust, etc.
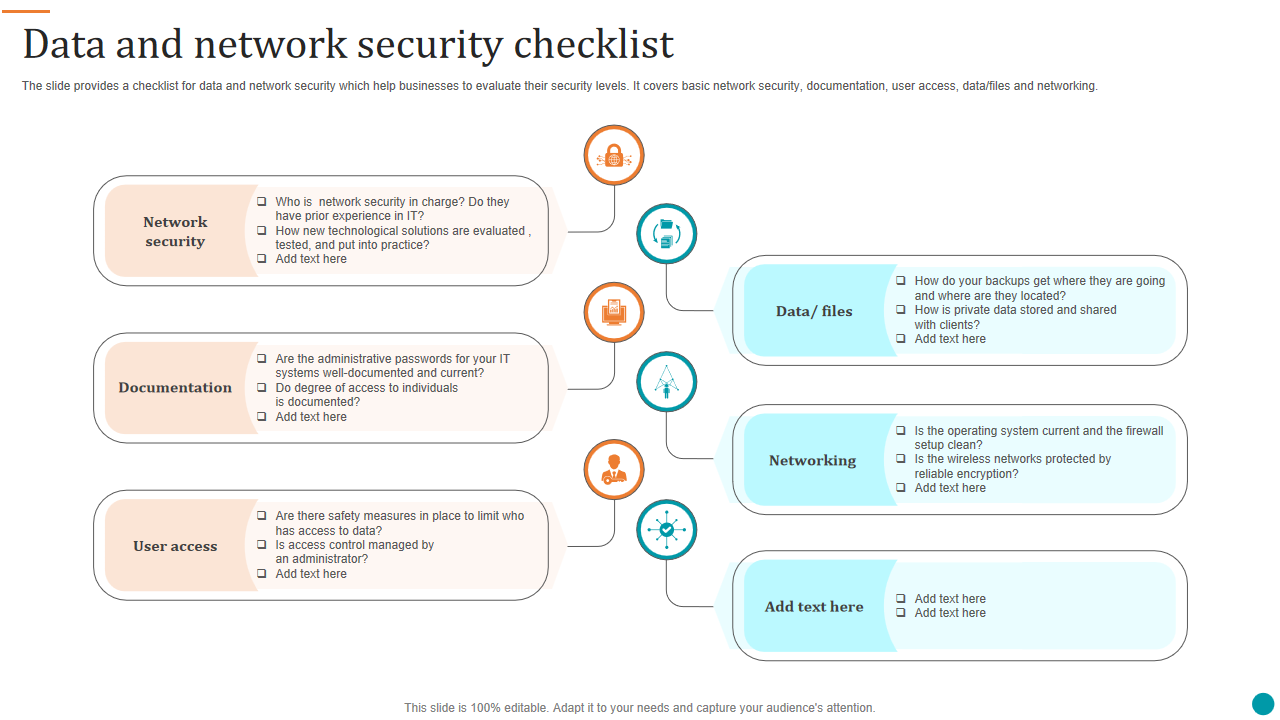
Template 8: Data and Network Security Checklist
This PPT template is ideal for project managers, IT leaders, and other networking professionals for sharing critical concepts related to data security. It showcases network security, documentation, user access, data or files, networking, etc. The presentation slide comes with relevant icons, making it easier to understand the information. It also highlights some vital questions from the security perspective.
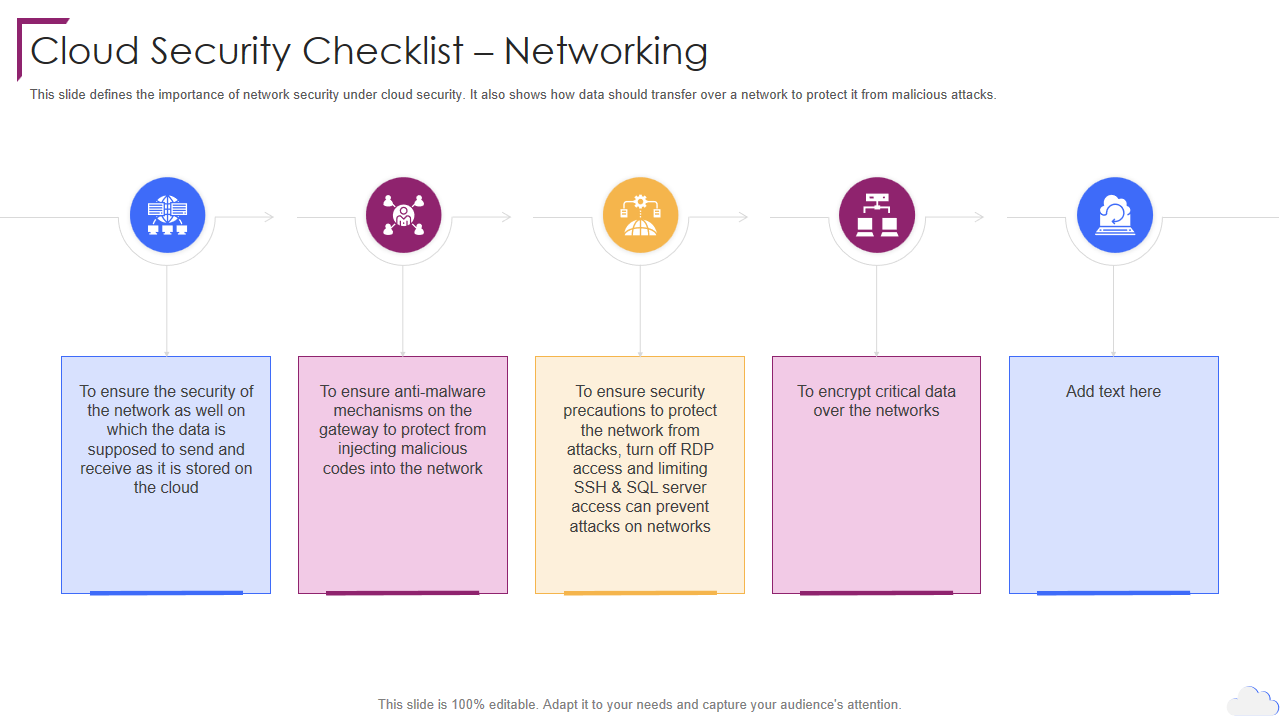
Template 9: Cloud Security Checklist Networking Cloud Computing Security
This Cloud Computing PPT framework guides you through a cloud security checklist for networking. The slide enlists five vital steps, including ensuring the network’s security on which the data is shared, received, and stored in the cloud. Additionally, the slide documents the importance of ensuring that anti-malware mechanisms are present on the gateway to protect against malicious codes. Critical data should also be encrypted when transmitted over the networks. This presentation design includes relevant icons and easy-to-edit options, making it the first choice for giving presentations on cloud security.
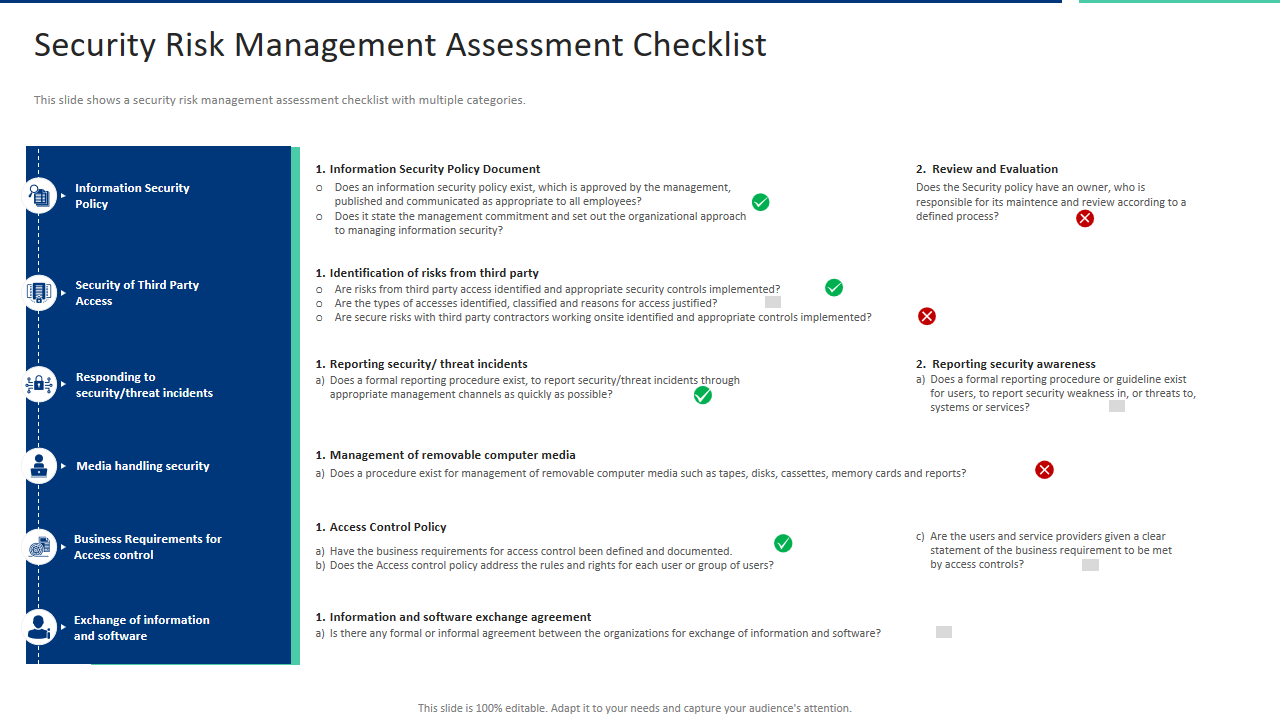
Template 10: Security Risk Management Assessment Checklist PPT Ideas Graphics Tutorials
This resourceful PPT Template lets you keep your team members informed about information security policy, security of third-party access and responding to security threat incidents. Other topic covered are media handling security, business requirements for access control, and exchange of information and software. Moreover, it allows for highlighting details about information security policy documents, identifying risks from third parties, reporting security or threat incidents, managing removable computer media, access control policy, information, and software exchange agreements. Use this template to showcase details on review, evaluation and reporting security awareness.
HOLISTI SECURITY APPROACH WORKS BEST
Security checklists and assessments are vital for businesses in the contemporary digital realm. These proactive strategies are pivotal in detecting and mitigating potential risks to essential systems and sensitive data. Through meticulous scrutiny of security controls and vulnerabilities, businesses can fortify their defenses, bolster their resilience against cyber threats, and, safeguard their reputation and prosperity. Embracing a holistic security approach shields the organization and fosters trust among customers, partners, and stakeholders, positioning the business for enduring success and growth.
Download the top 5 security plan templates with samples and examples here.
FAQs on Security Checklists
How do I make a security checklist?
Ensuring computer security at the individual level contributes to the collective safeguarding against data and identity theft, viruses, hackers, and cyber threats. Some key measures to make a security checklist are creating robust passwords, avoiding risky downloads, installing antivirus, securing the internet, backing up data, examining attachments, employing firewalls, ignoring unsolicited emails, etc.
What is an application security checklist?
An application security checklist is a detailed compendium of security measures and recommended practices to evaluate and bolster software applications' security. It encompasses guidelines and tasks for developers, security experts, and organizations to identify and address potential application vulnerabilities and threats. This checklist encompasses facets of application security, including authentication, authorization, encryption, input validation, error handling, and more. Such a checklist helps individuals and organizations minimize the likelihood of security breaches, safeguarding valuable data and digital assets.
What is a security risk assessment?
A security risk assessment entails identifying, evaluating, and implementing critical security measures within applications. Its primary objective is to address and mitigate potential security flaws and vulnerabilities, emphasizing the prevention of application security issues. The three phases in successful data security risk assessment are recognizing risks, categorizing data by risk, and mitigating risks.





 Customer Reviews
Customer Reviews