Feeling safe and having a sense of security is a basic human need. In an unsafe environment, our intuition senses it before we practically realize it.
It is essential for employees at workplace to feel secure to be productive and satisfied. Therefore, companies must put guidelines in place to safeguard the premises from physical and cyber threats.
It majorly includes personal data as well as organizational data. Organizations require to outline security reports on regular intervals to scrutinize unusual activities and create strategies to protect company data.
Security report captures the detailed description of the incidents occurring during the security lapse. It is critical to prevent incidents by preparing in advance and help track the violations.
A security report consists of the following elements:
- Factual aspects like the name and position of people involved
- Eye witness names, if any
- Location of the incident
- Detailed description with time and date of the incident
- Definition of any harm to people or property
Security reports are essential in keeping track of the risks that may occur. It is crucial to keep updated on the system for implementation and maintenance of security.
Security reports further help the insurance agency to maintain its liability and provide fair compensation.
Here we present to you our Top 5 security Report Templates to explain the need and importance of a security report.
Use these 100% customizable and ready-made Templates to curate elaborated and actionable reports to protect your business and its employees.
Template 1: Security Reports PPT Presentation
Below is the complete set of a PowerPoint Presentation comprising steps to write a crisp and professional security incident report. Maintain a monthly checklist and learn the business incident report for safety and security purposes using this Template. Deploy this slide to compare cyber security reporting tools with tips to create an evaluation report. Download this set of Templates to explain and evaluate various security reports with efficiency.
Template 2: Vulnerability Management and Lifecycle Risk Security Reporting Template
This PPT Template presents the global delivery infrastructure for the vulnerability management lifecycle. Identify, manage, and evaluate security reports to avoid online and offline attacks with this pre-planned monitoring plan. This Template explains the security, asset management, and compliance monitoring lifecycle.
Download this Template to explain and evaluate the security monitoring process in a 6-stage process.
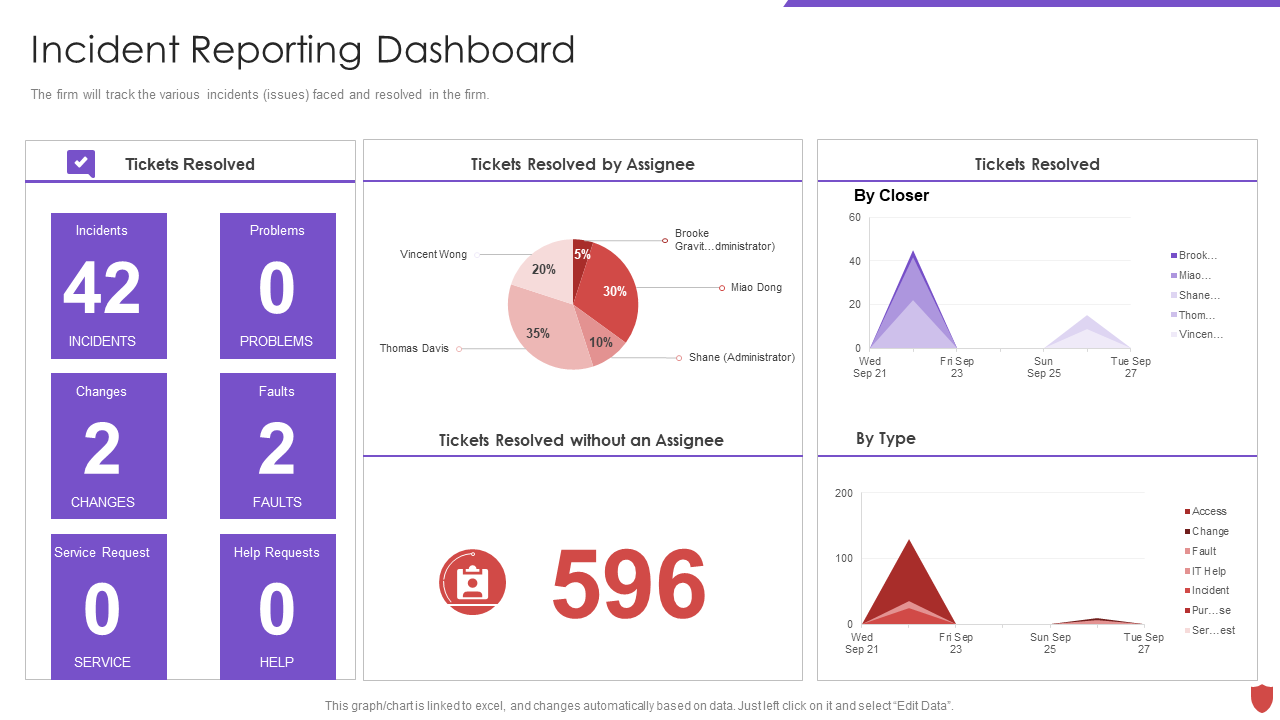
Template 3: Cyber Security Risk Management Incident Reporting Dashboard PPT
This PPT template displays a dashboard to track tickers raised and resolved in the firm in a given period. Use this actionable Template as a tool for navigation and discussion of tickets determined by an assignee and tickets fixed without an assignee. This PowerPoint Diagram consists of pie charts and graphs to help you identify the issues and gaps at a glance.
Template 4: One Pager Global Cyber Security Attacks Statistics Report PPT Presentation
This One-page PPT Document provides an overview of worldwide critical statistics on cyber security threats and risks within a digital ecosystem. Grab this one-pager PPT Template to highlight top malicious files, global and US cyber-attacks by category, major cyber security concerns, etc., This pre designed PowerPoint Diagram comprises graphs and charts to keep the data neat and crisp to understand. Download this ready to use PowerPoint Slide to create a comprehensive security report to educate your audience on cyber and other threats.
Template 5: Rent Sublease Agreement Security Report PPT Slide
Want to secure your property? SlideTeam brings you a content-ready rent sublease PPT Template containing guidelines in case of security mishap. Deploy this ready-made PowerPoint Slide and outline all the essential of the agreement to aware your tenant of the violations. It allows you to add yours and tenant name with location and date to keep the document professional. It also has the space to add your digital signature to make it an official agreement. Download now to craft a well-structured sublease agreement.
Security Reports to Protect Your Business
A security report maintains and records any accident or incident that threatens the safety of employees, organizations, and their critical data. It is crucial to enhance security for smooth functioning of the operations and processes. Security reports additional aid in case of any legal implications on the organization for security breaches.
FAQs on Security Report
What are Security Reports?
Security reports are the detailed information captured by prime security officers to report any incident or maintain track of events that occurred during their duty. Security reports help identify threats that may arise to critical information and ensure accountability of the security company.
How do you write an information security report?
An information security report keeps crucial data secure from cyber threats. It helps in risk management and reduces unauthorized access. While writing the information security reports, keep the following points in mind.
- Analyze data with relevant issues
- Document risk and observation
- Prioritize findings and recommendations
- Proofread and submitted the final report with data.
What are the two types of security reports?
Two types of security reports are SOC, which is the Service organization control report, and SOC1 and SOC2.
- SOC1: It focuses on transactional or financial measures essential for revenue management.
- SOC2: Its focus is on practical operation security controls, confidentiality and privacy maintenance, and processing integrity.





 Customer Reviews
Customer Reviews