"An ounce of prevention is better than a pound of cure" - Benjamin Franklin
Have you ever thought about how fragile a porcelain vase is? One small jolt and it will shatter into a million pieces, never to be put back together. Like a porcelain vase, a business can be equally delicate and vulnerable to threats if it doesn't have a solid security plan.
Did you know that 60% of small businesses that experience a cyber attack go out of business within six months? That's a staggering statistic, yet many businesses still operate without a comprehensive security plan in place.
To safeguard your business and protect it from potential threats, it's imperative to have a well-thought-out security plan. This is where our Security Plan PPT Templates come into play. The 100% customizable nature of the templates provides you with the desired flexibility to edit your presentations. The content-ready slides give you the much-needed structure.
Our templates are designed to help you develop a comprehensive and effective security plan that takes all the essential elements into account. Download our Security Plan PPT Templates today and protect your business from potential threats.
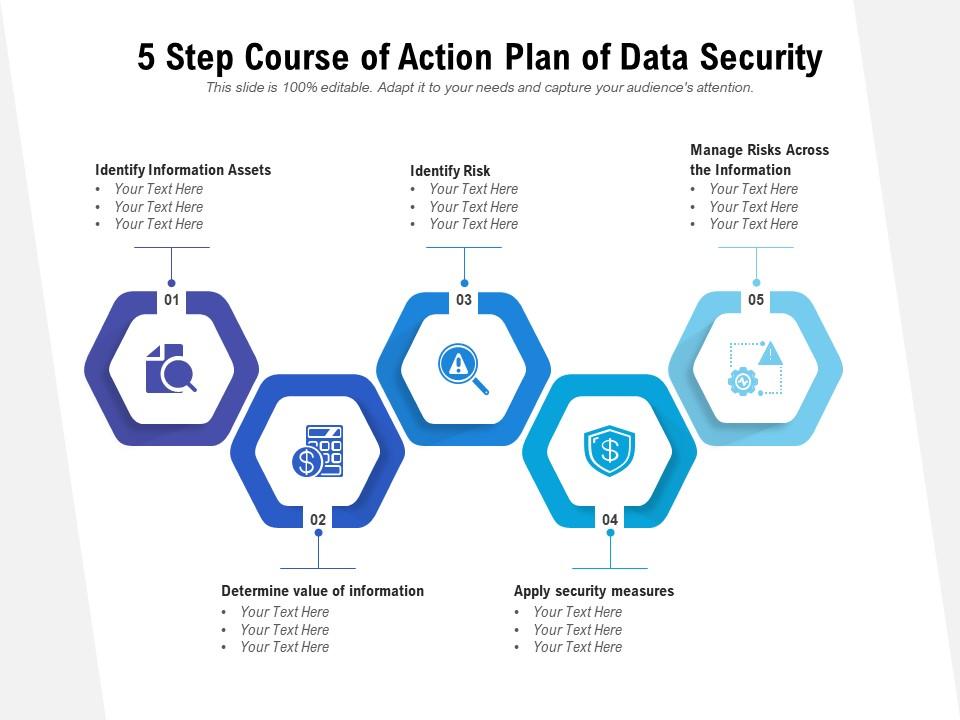
Template 1: 5-Step Course of Action Plan for Data Security PPT Template
Protect your valuable information assets with our PPT Template. In today's digital world, data security is more important than ever. This easy-to-use template breaks down the steps to secure your information into five simple, actionable steps: Identify Information Assets, Determine the Value of Information, Identify Risk, Apply Security Measures, and Manage Risks across the Information. Perfect for businesses and individuals who want to take their data security to the next level, download this slide now and safeguard your information assets!
Template 2: Effective Security Monitoring Plan to Eliminate Cyber Threats and Data Breaches Complete Deck
Shield your business from the perils of cyber threats with our comprehensive PPT Layout. Don't let your guard down against ever-evolving cyber threats with our easy-to-use template that outlines the essential components of a security monitoring plan, including key performance indicators (KPIs), elements, challenges, and best practices. Whether you're a small business owner, a government agency, or an individual, our template will help you stay one step ahead of cybercriminals. Say goodbye to worries of data breaches and hello to a secure future with our PPT Preset. Download now!
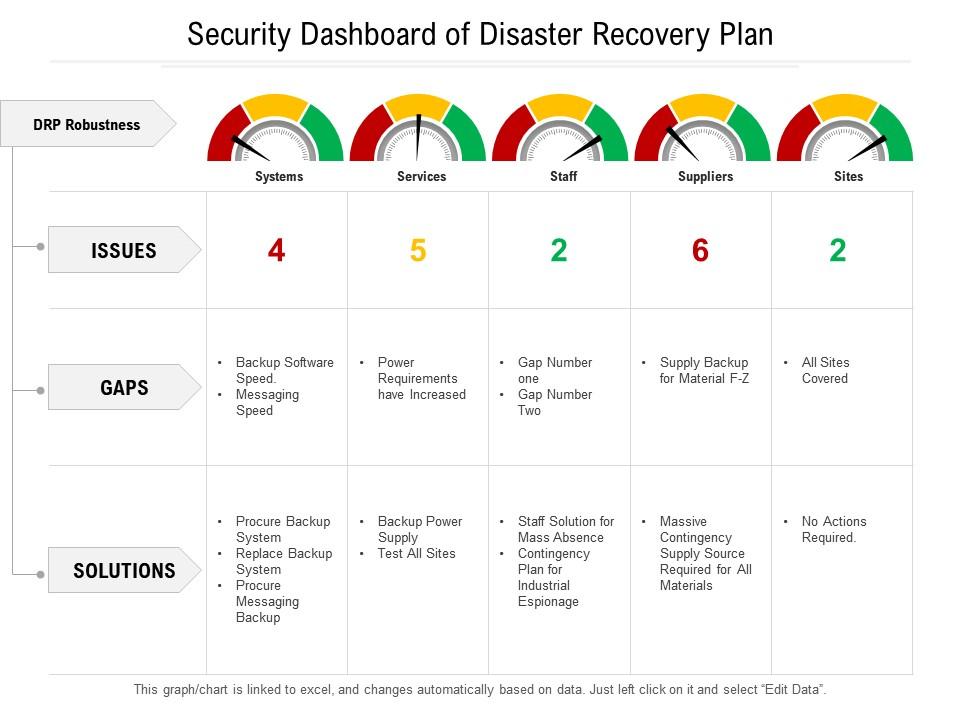
Template 3: Security Dashboard of Disaster Recovery Plan PPT Template
Be prepared for the unexpected with our Security Dashboard PPT Slide. Disasters can strike at any time, leaving behind chaos and destruction. But, with our template, you'll be ready for anything life throws your way. Our comprehensive dashboard highlights the key issues, gaps, and solutions surrounding systems, services, staff, suppliers, and sites to ensure your business stays up and running in the face of adversity. No matter how big your business, our template is the perfect tool to help you be ready for anything. Download now and take control of your disaster recovery plan!
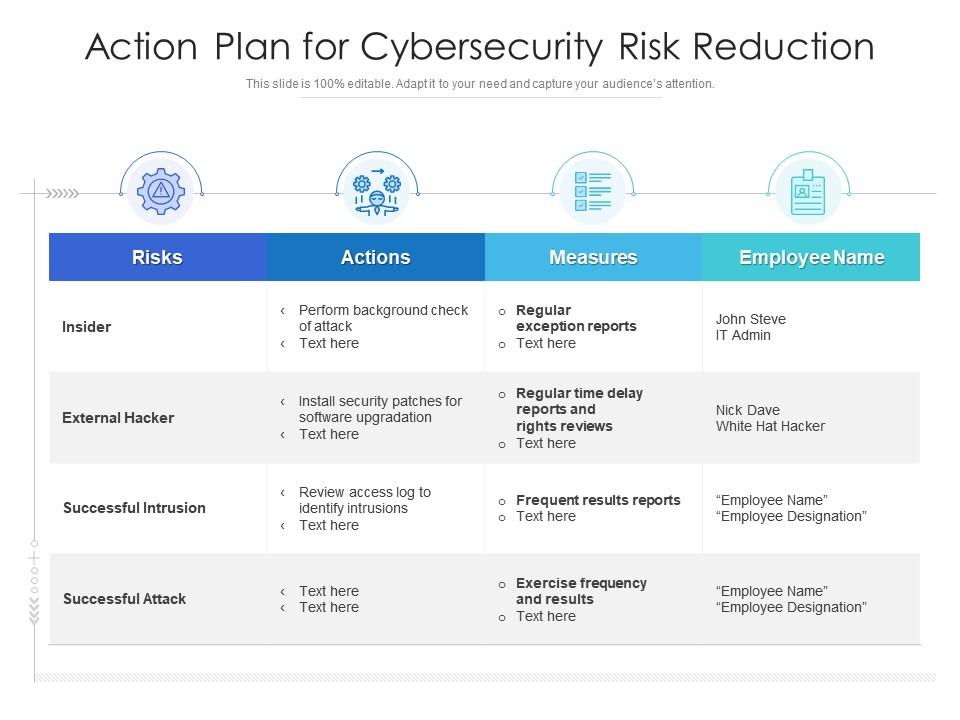
Template 4: Action Plan for Cybersecurity Risk Reduction
Stay protected in the ever-changing digital world with our Action Plan PPT Template. It outlines the major risks, the actions and measures that can be taken against them, and the person responsible for monitoring each risk. Our template is the perfect tool to help reduce your cybersecurity risks and stay protected. Don't wait until it's too late. Download our Risk Reduction PPT Theme now and secure your future!
Template 5: Implementing Security Management Plan to Reduce Threats and Protect Sensitive Company Data PPT Deck
Keep your company's sensitive information safe with our Security Management Plan PPT Template. Data breaches and cyber threats are a major concern for businesses of all sizes. Our comprehensive template outlines the critical success factors of security management, the elements of a successful security management plan, the challenges you may face and ways to overcome them, and a detailed security risk management process and checklist. Download now and take control of your security management plan!
Bonus Security Plan PPT Templates
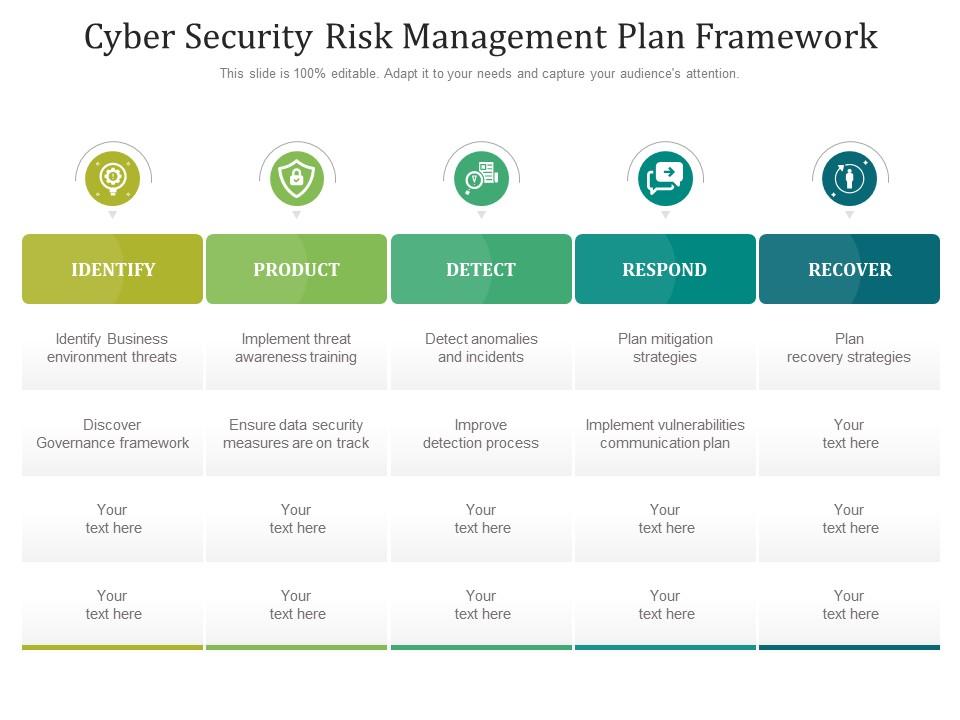
Template 6: Cyber Security Risk Management Plan PPT Framework
Unleash the power of unbeatable cyber protection with our Risk Management Plan PPT Template! Are you ready to take your security to the next level and keep your business protected from threats and data breaches? This comprehensive PPT template is your key to building a robust security framework that identifies business environment threats, implements threat awareness training, detects anomalies and incidents, and plans mitigation and recovery strategies. Whether you're a small business owner or a security professional, this template is the perfect tool to help you stay ahead of the game and protect what matters most. Download now and start securing your business today!
Template 7: Building Organizational Security Strategy Plan PPT Template
Unlock the power of digital protection with our Security Strategy Plan PPT Template! In today's rapidly evolving digital landscape, it's crucial to have a security strategy in place to safeguard your organization from potential threats. Our template provides a comprehensive framework to implement security management, incident management, and corporate governance, develop security centers, and reinforce brand protection, threat protection, and overall security. Don't wait, download now and take control of your organization's security with ease!
Protected and Prosperous: The Key to a Successful Security Plan
A robust security plan protects sensitive information, assets, and individuals. It is a comprehensive and multi-faceted approach that requires a combination of technology, process, and people to be effective. Organizations can significantly reduce the risk of a security breach and the resulting consequences by taking the time to assess the risks, implement the necessary controls, and regularly review and update the plan.
By prioritizing security and making it a core component of your operations, you can maintain the trust of your customers, employees, and stakeholders. Employing our security plan templates is an investment in the future success of your organization.
FAQs on Security Plan Templates
How do you write a security plan?
A security plan is a comprehensive document that outlines the measures an organization will take to protect its assets, information, and individuals. To write a security plan, follow these steps:
- Conduct a risk assessment: Evaluate the organization's vulnerabilities and assess the likelihood and impact of potential threats. It will help determine which areas of the business need the most protection.
- Define objectives and scope: Determine the specific goals of the security plan and the areas it will cover.
- Identify assets: List all the assets that need protection, including physical assets, information, and personnel.
- Develop security controls: Based on the risk assessment results, determine what security controls need to be implemented to protect the assets. These may include access controls, encryption, firewalls, and incident response procedures.
- Write the plan: Put the security plan in writing, including a description of the security controls, who is responsible for implementing them, and how they will be monitored and updated.
- Train personnel: Ensure that all employees are trained on the security plan and understand their role in maintaining the organization's security.
- Test and update: Regularly test and update the security plan to ensure it remains effective and relevant in light of changes to the business or the threat landscape.
What are the five pillars of security?
The five pillars of security refer to the key components that make up a comprehensive security program. These pillars are:
- Access control: This involves managing and controlling who has access to information and assets and how they access them. It includes both physical and logical access controls.
- Network security: This includes measures to protect a network and its components from unauthorized access, use, disclosure, disruption, modification, or destruction.
- Incident response: This involves having a plan to respond to security incidents, including identifying and containing threats and restoring normal operations.
- Data protection: This involves protecting sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. It includes data encryption, backups, and disaster recovery.
- Identity and access management: This involves managing user identities, granting access to systems and information, and controlling the actions the users can perform within those systems.
What are the five phases of the security life cycle?
The five phases of the security life cycle are a systematic approach to managing and improving an organization's security. The phases are:
- Planning: This involves defining the scope and objectives of the security program, conducting a risk assessment, and developing a security plan.
- Implementation: This involves implementing the security plan, including deploying security controls and training personnel.
- Operations: This involves maintaining and monitoring the security program on an ongoing basis, including reviewing and updating the security plan as needed.
- Assessment: This involves regularly evaluating the effectiveness of the security program and identifying areas for improvement. It may include internal audits, vulnerability assessments, and penetration testing.
- Continuous improvement: This involves making changes to the security program based on the results of the assessments and the evolving threat landscape. It includes updating security controls, processes, and personnel training.




 Customer Reviews
Customer Reviews