Data Breach Prevention And Mitigation Strategies For Businesses Powerpoint Presentation Slides
Did you know how important it is for organizations to ensure data security and other essential security tools. Well, it is super important. Considering how essential this is, we have curated a full-fledged Data Breach Prevention and Mitigation Strategies PPT for Businesses. It includes data breach impacts and attack modes, data exploitation techniques, analysis of attack cycles, and target vulnerabilities. This PowerPoint presentation demonstrates the working process of the data breach attack cycle. In addition, Data Breach Prevention Detection and Management Guide PPT demonstrates the different types of data breach attack techniques used by the attackers. These types are phishing, brute force attacks, social engineering, malware, etc. Furthermore, the Data Security Attacks Prevention and Recovery module explains identity theft and its techniques. It also discusses the far-reaching consequences of data breach attacks on organizations and individuals. Moreover, this Data Fortification Strengthening Defenses Against Breaches deck contains sections about developing and implementing a data breach response plan. It illustrates a complete program to implement data breach awareness training for organizations and the training budget. Lastly, this Data Breach Prevention and Mitigation Strategies for Businesses deck comprise a roadmap, a 30-60-90 day plan, a timeline, a checklist to secure organizations from data breach attacks, and a dashboard to track data breaches. Download our 100 percent editable and customizable template, also compatible with Google Slides.
Did you know how important it is for organizations to ensure data security and other essential security tools. Well, it is ..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Data Breach Prevention And Mitigation Strategies For Businesses Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of seventy five slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Data Breach Prevention and Mitigation Strategies for Businesses. State your company name and begin.
Slide 2: This slide states Agenda of the presentation.
Slide 3: This slide shows Table of Content for the presentation.
Slide 4: This slide highlights title for topics that are to be covered next in the template.
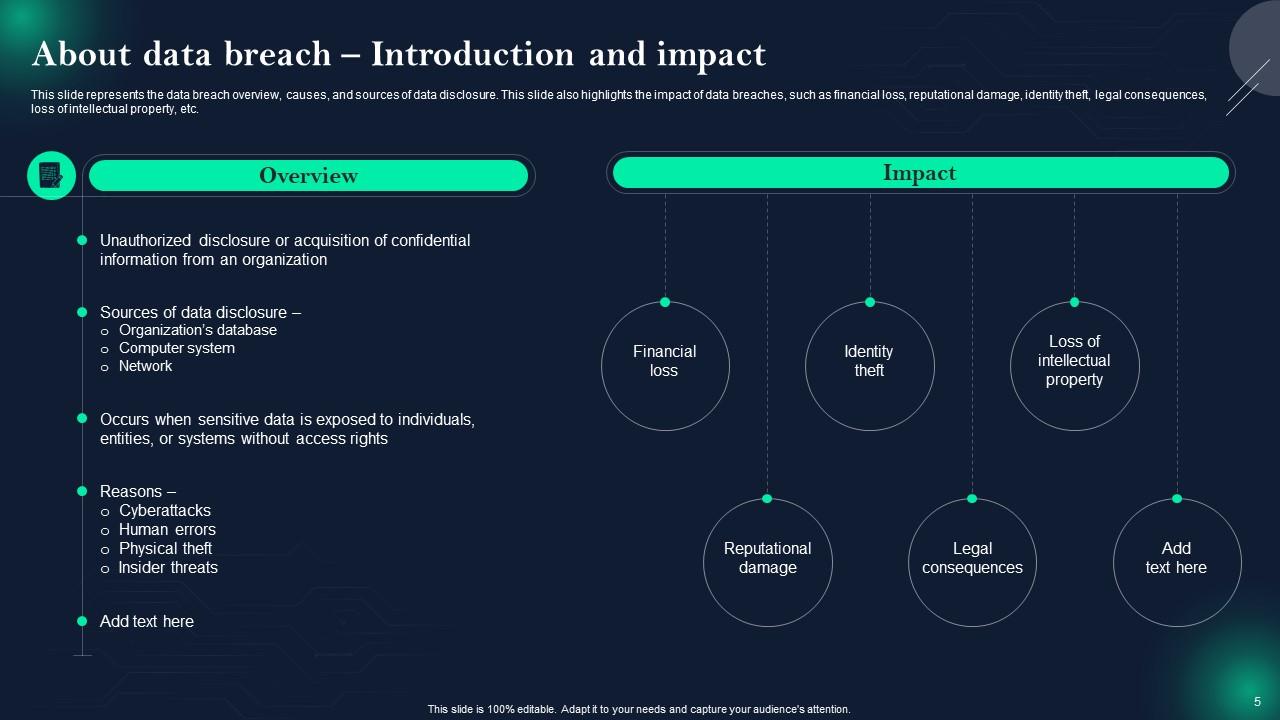
Slide 5: This slide represents the data breach overview, causes, and sources of data disclosure.
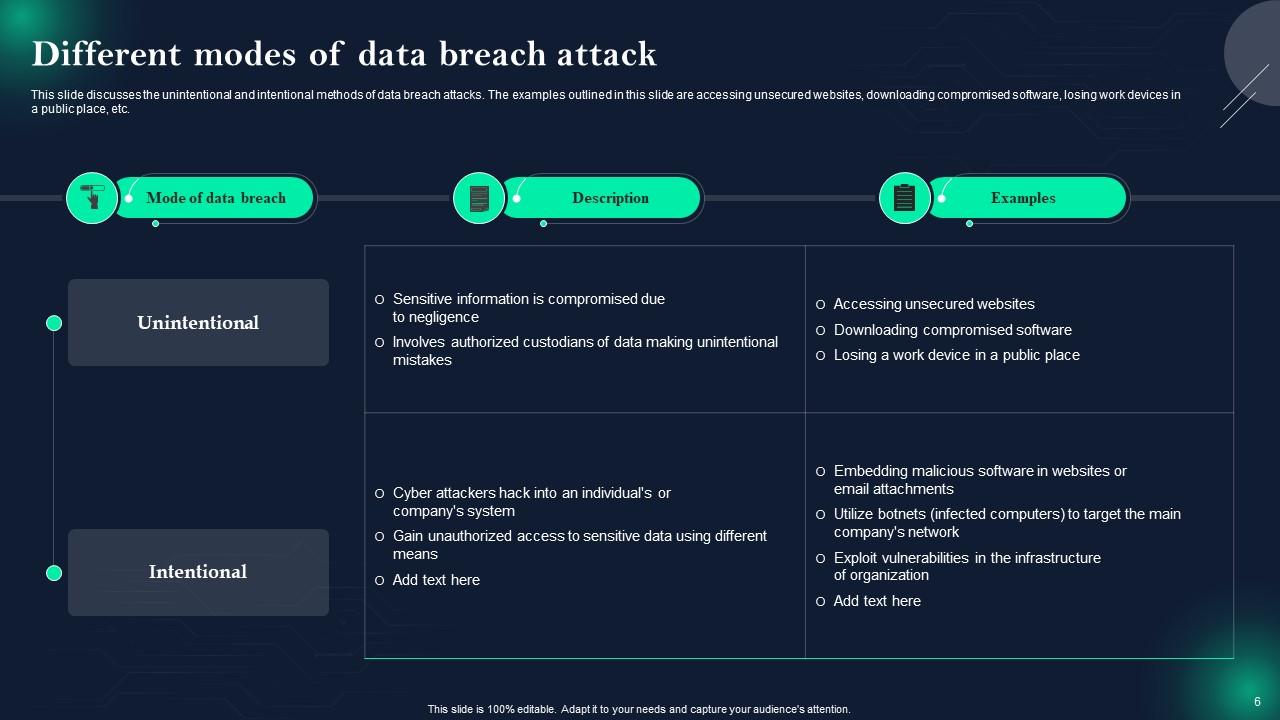
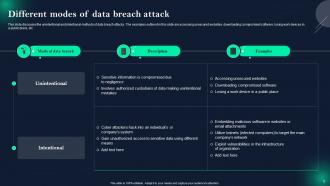
Slide 6: This slide showcases Different modes of data breach attack.
Slide 7: This slide shows Major types of data security breaches.
Slide 8: This slide highlights title for topics that are to be covered next in the template.
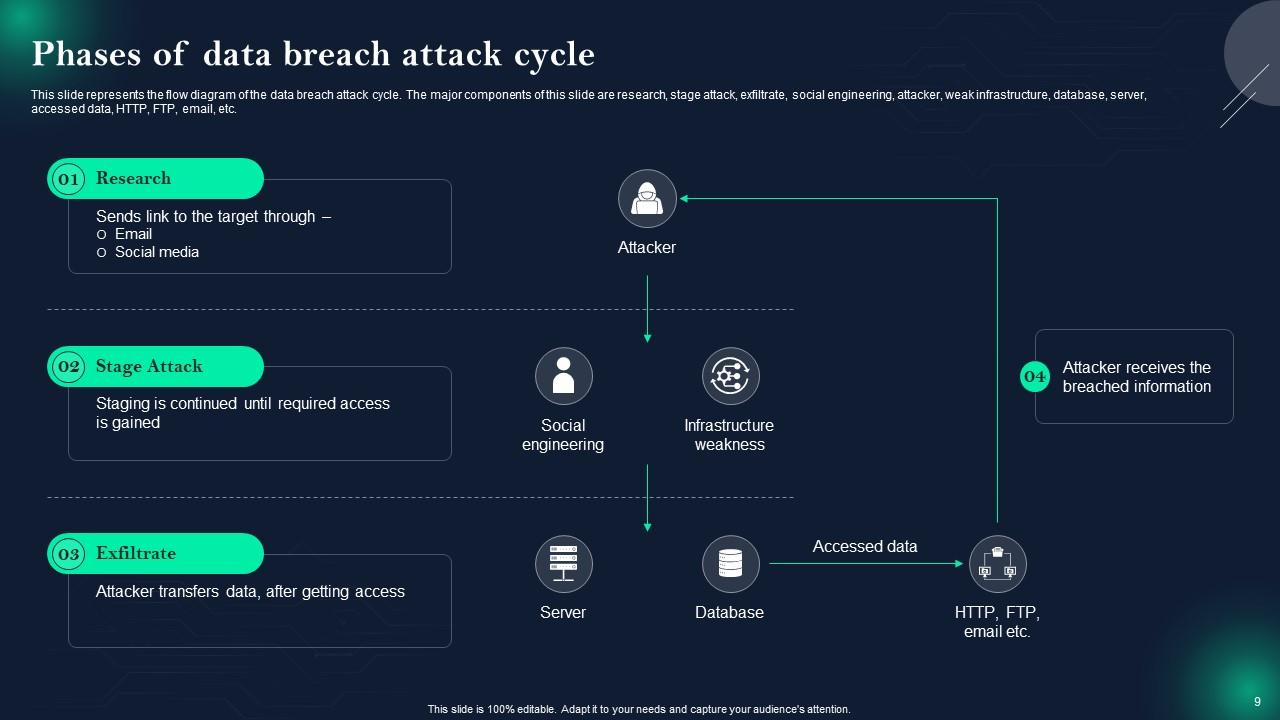
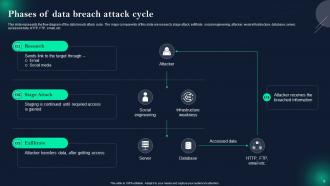
Slide 9: This slide presents Phases of data breach attack cycle.
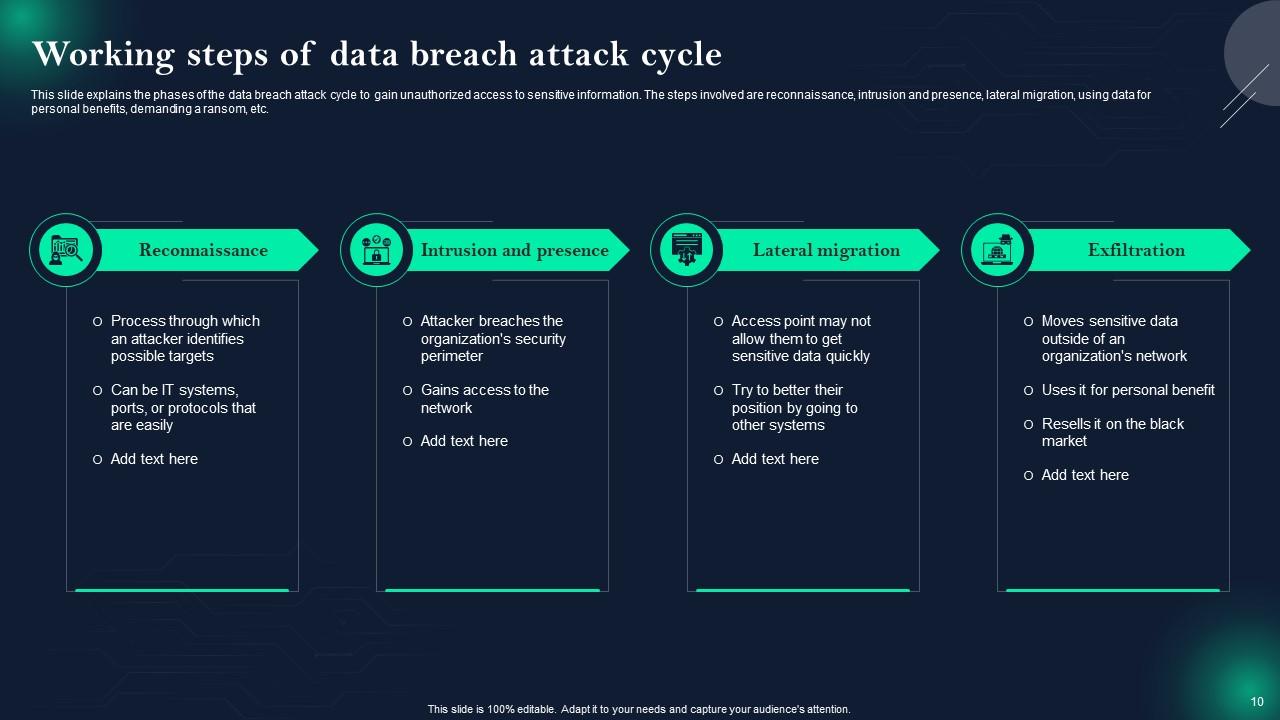
Slide 10: This slide displays Working steps of data breach attack cycle.
Slide 11: This slide highlights title for topics that are to be covered next in the template.
Slide 12: This slide represents Overview of various targets of data breach.
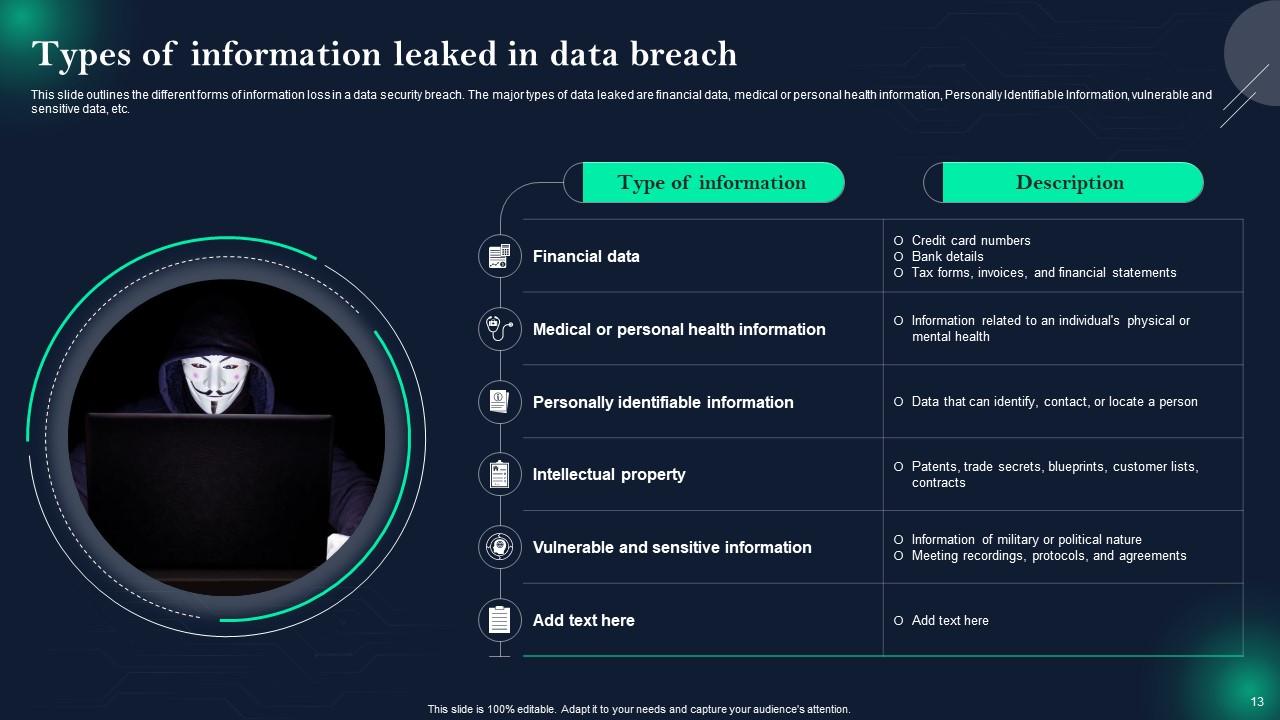
Slide 13: This slide showcases Types of information leaked in data breach.
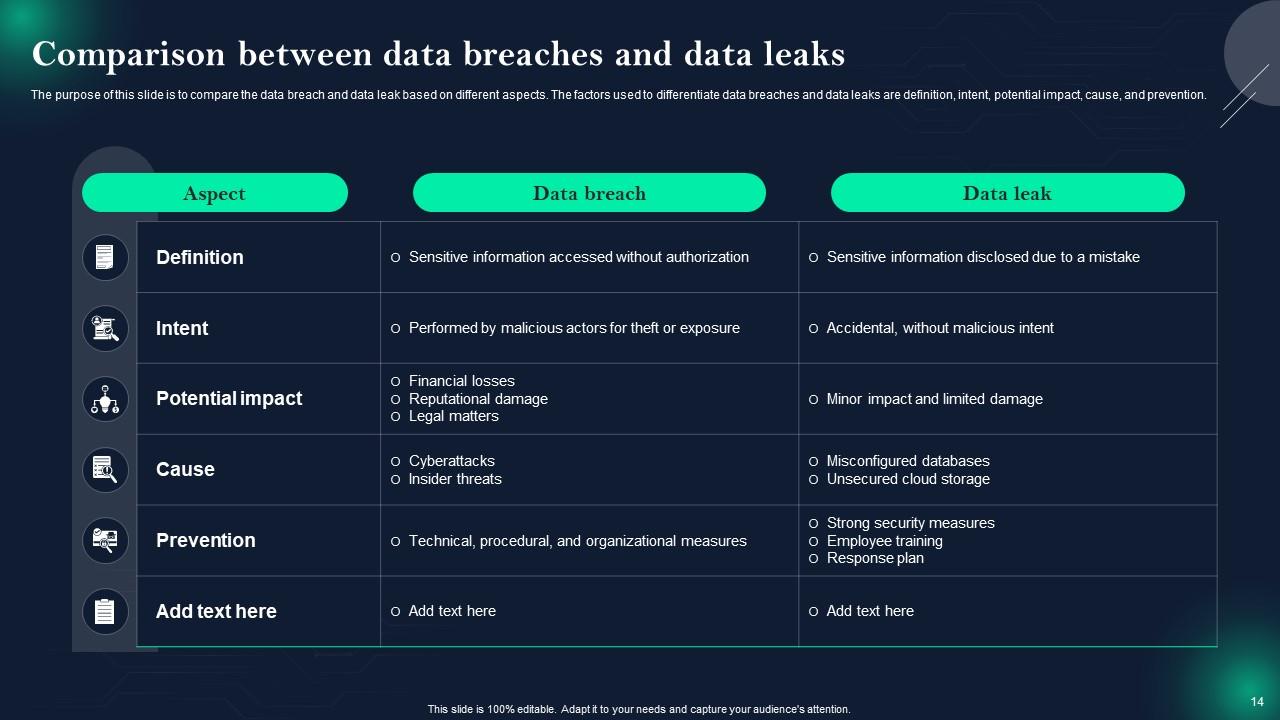
Slide 14: This slide shows Comparison between data breaches and data leaks.
Slide 15: This slide highlights title for topics that are to be covered next in the template.
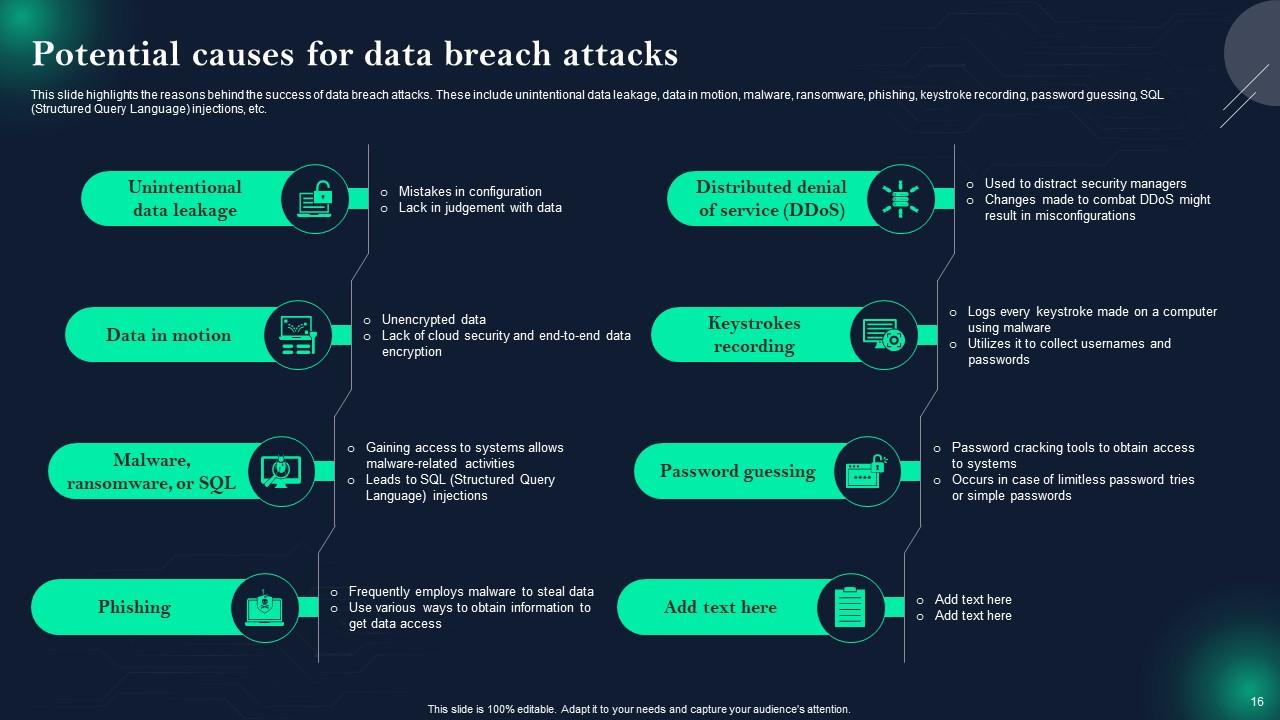
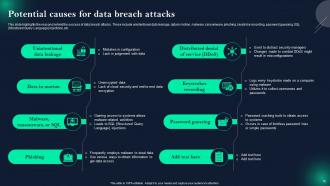
Slide 16: This slide presents Potential causes for data breach attacks.
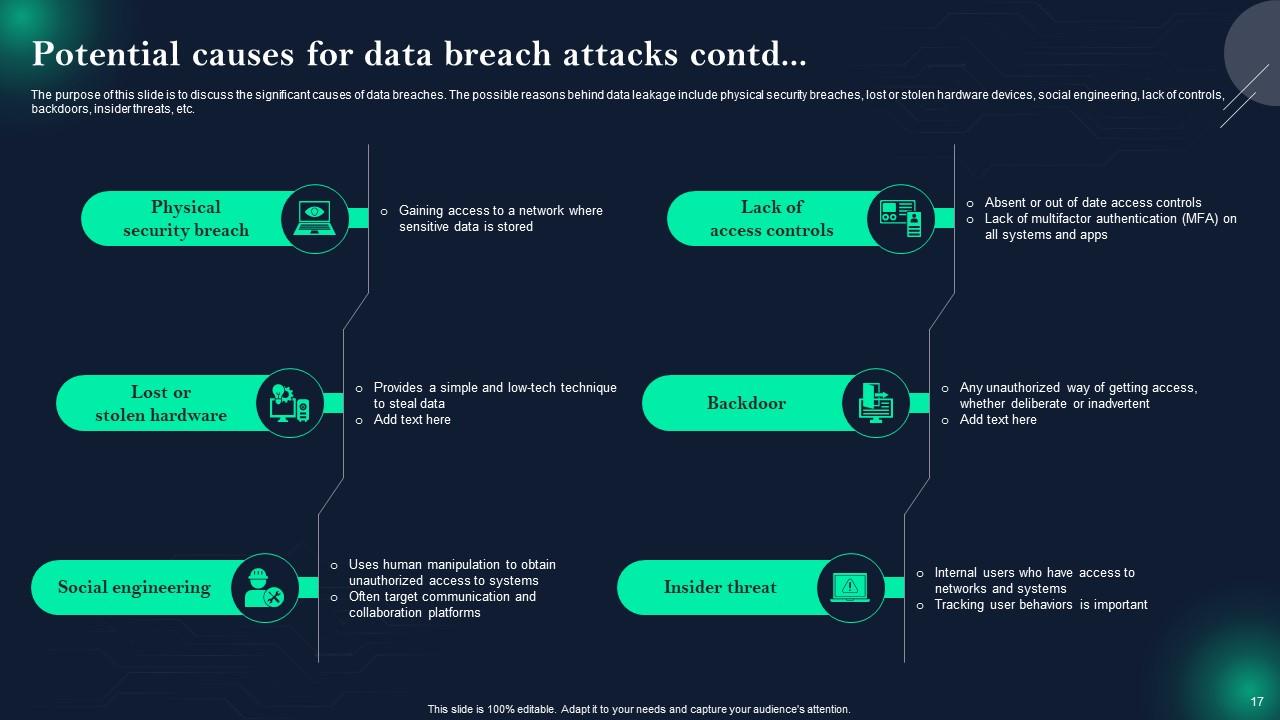
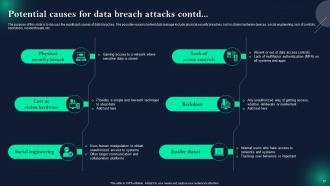
Slide 17: This is another slide continuing Potential causes for data breach attacks.
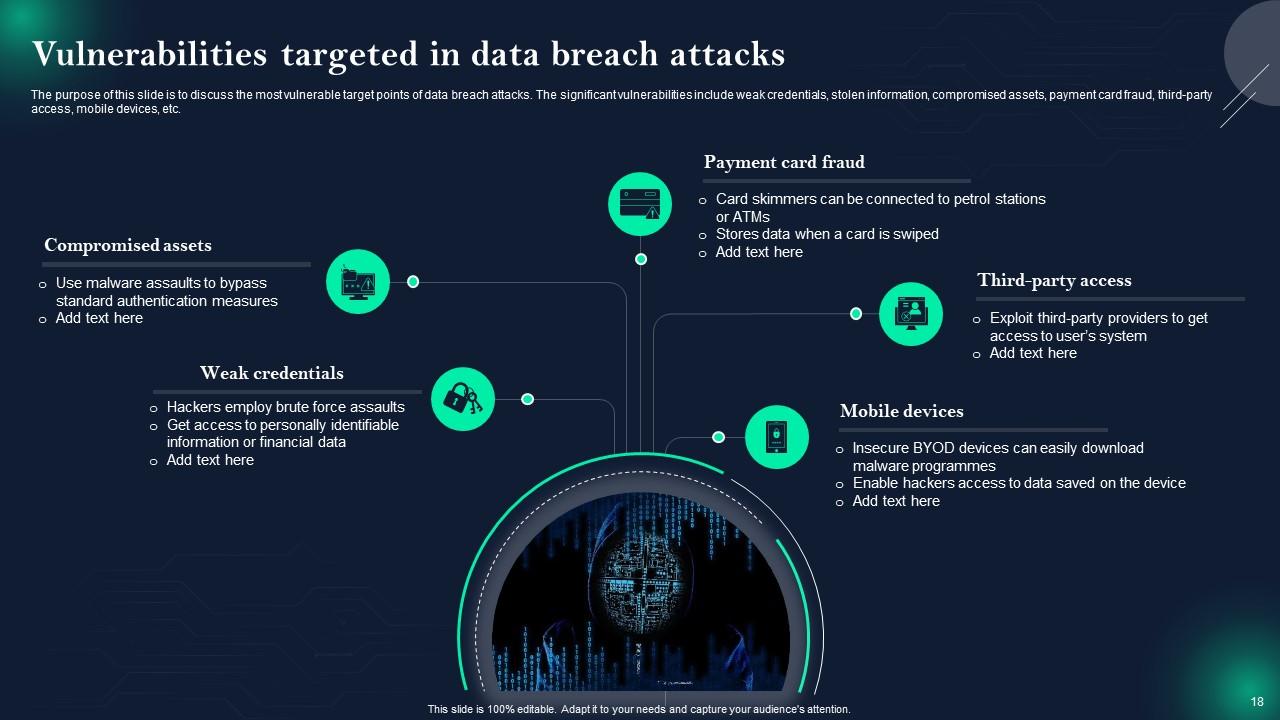
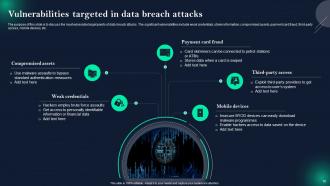
Slide 18: This slide displays Vulnerabilities targeted in data breach attacks.
Slide 19: This slide highlights title for topics that are to be covered next in the template.
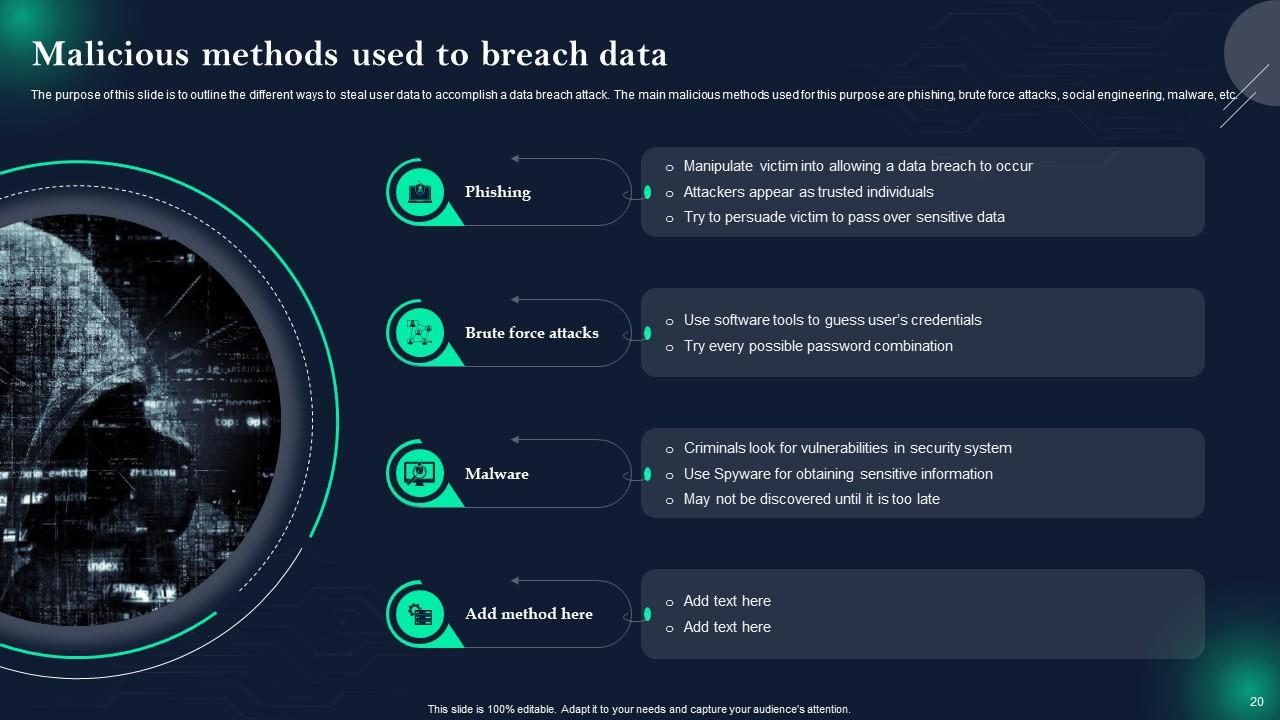
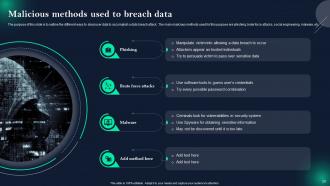
Slide 20: This slide represents Malicious methods used to breach data.
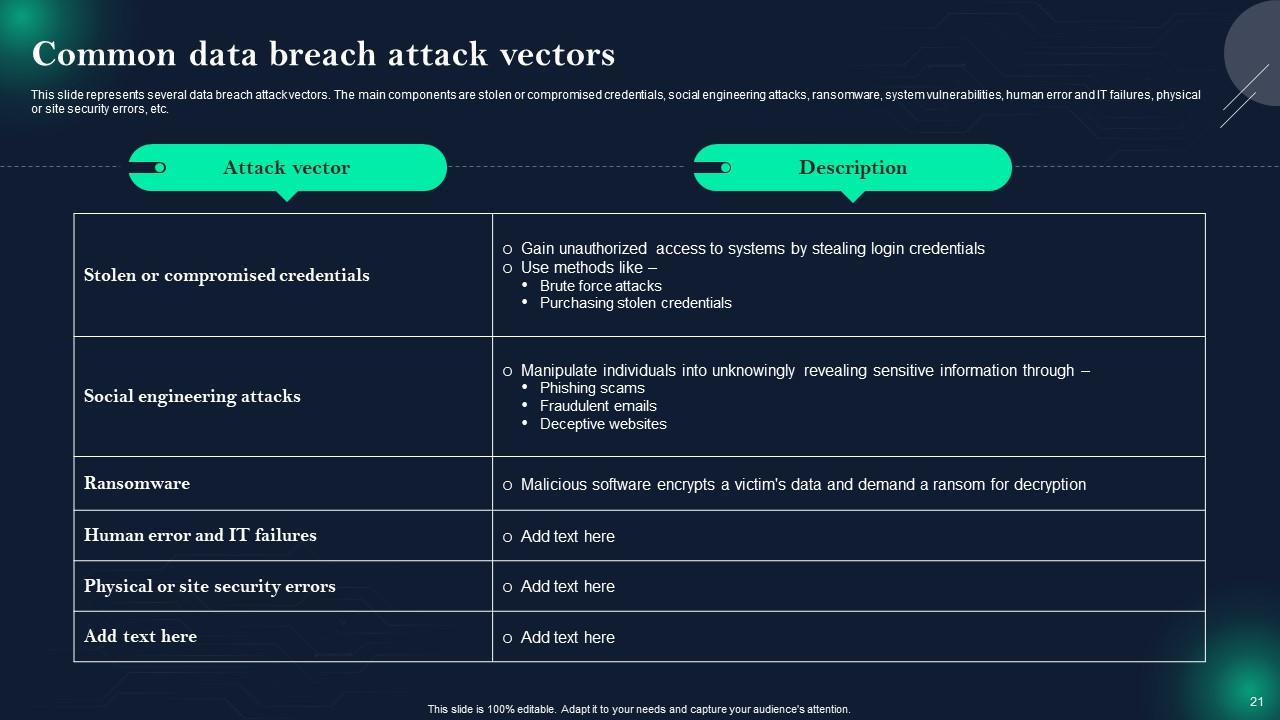
Slide 21: This slide showcases Common data breach attack vectors.
Slide 22: This slide shows Data exploitation methods used by criminals.
Slide 23: This slide highlights title for topics that are to be covered next in the template.
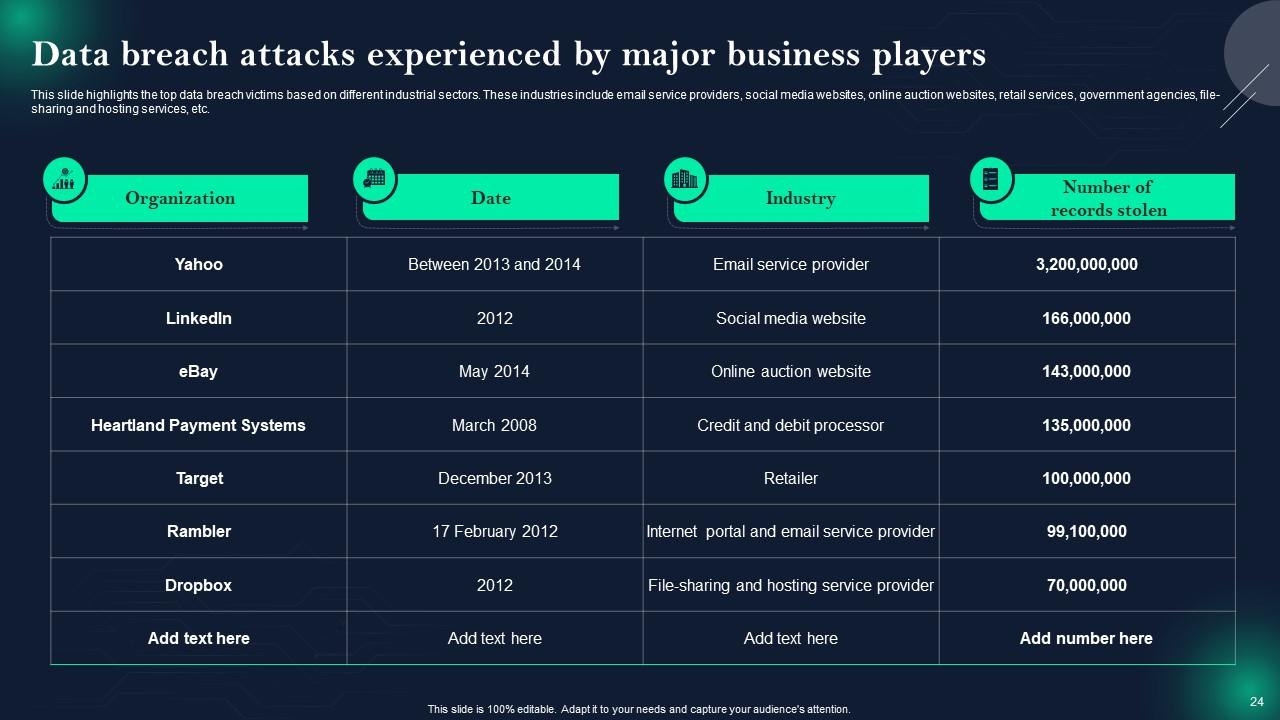
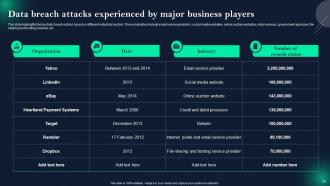
Slide 24: This slide presents Data breach attacks experienced by major business players.
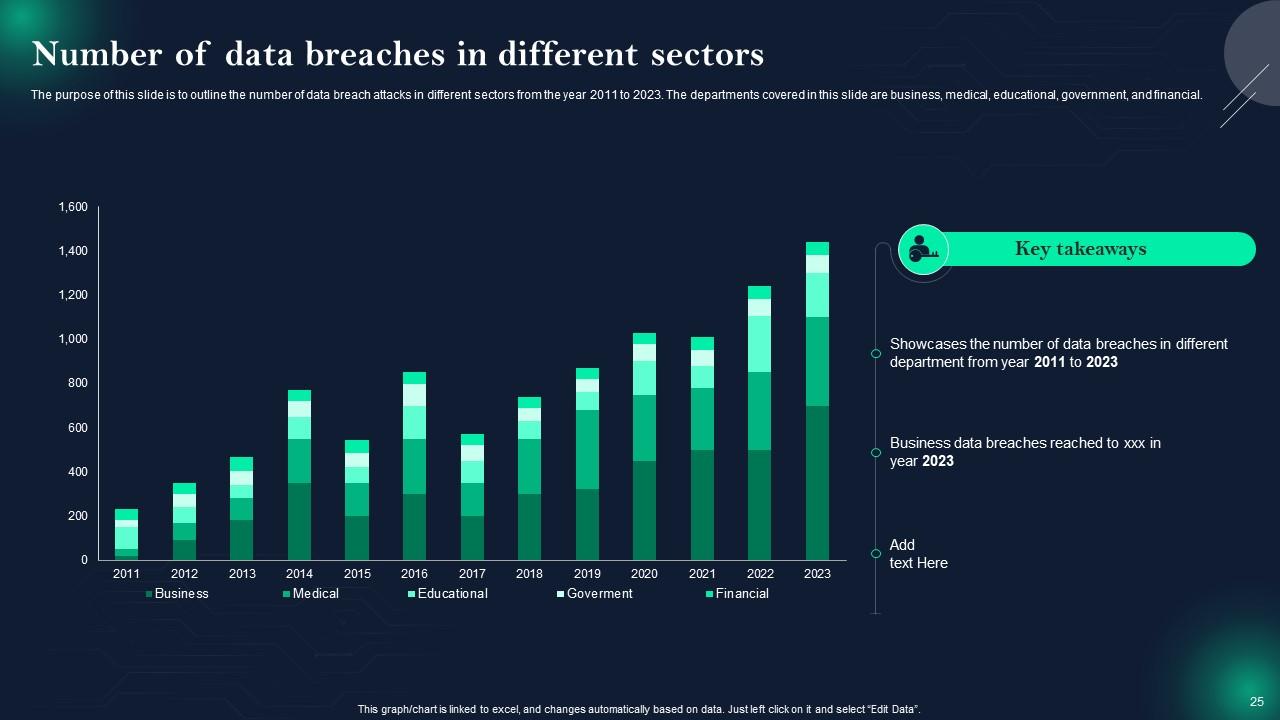
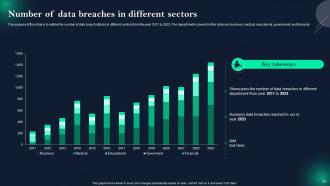
Slide 25: This slide displays Number of data breaches in different sectors.
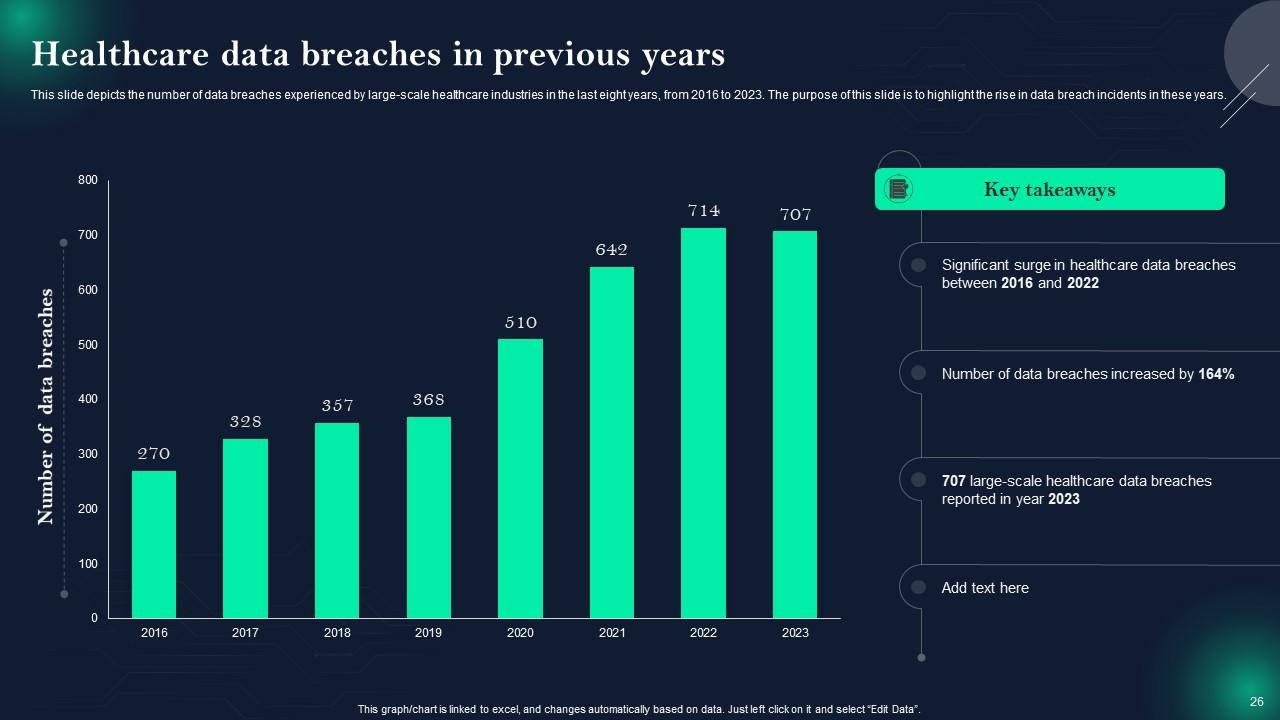
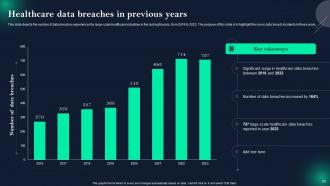
Slide 26: This slide represents Healthcare data breaches in previous years.
Slide 27: This slide highlights title for topics that are to be covered next in the template.
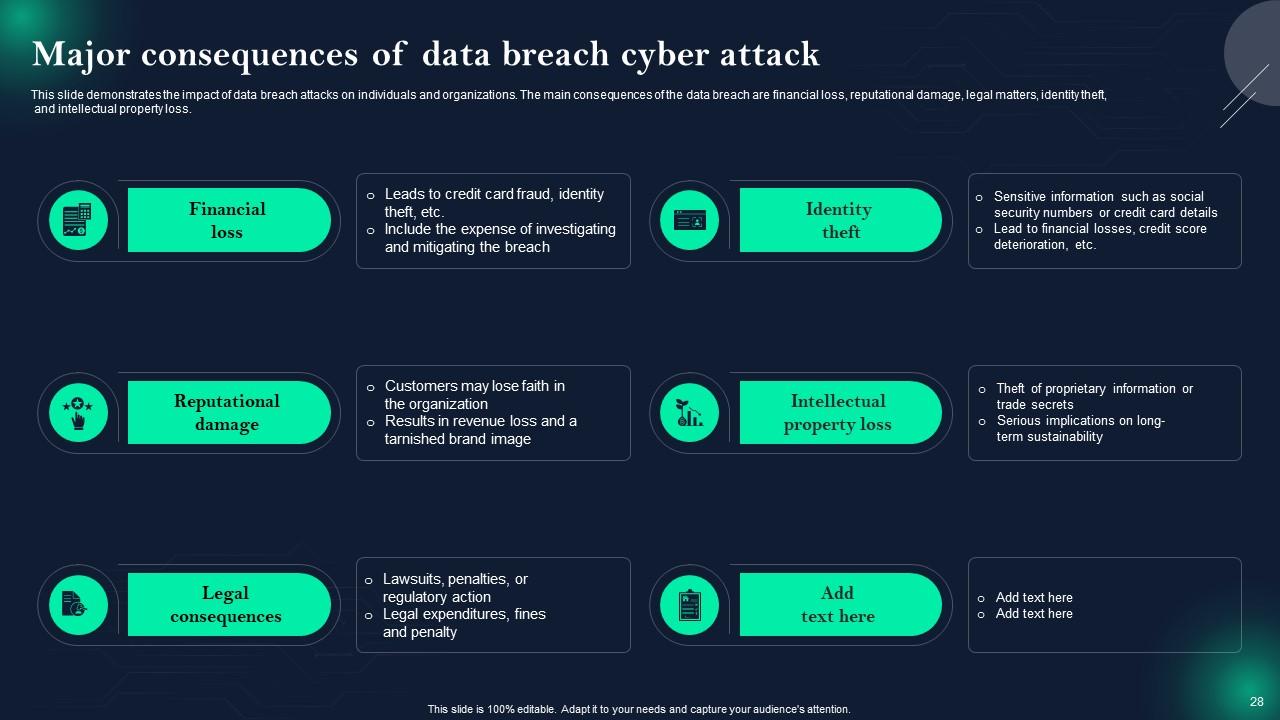
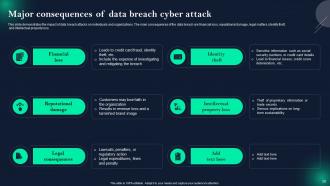
Slide 28: This slide showcases Major consequences of data breach cyber attack.
Slide 29: This slide talks about the major crime committed by phishers, named as identity theft.
Slide 30: This slide highlights title for topics that are to be covered next in the template.
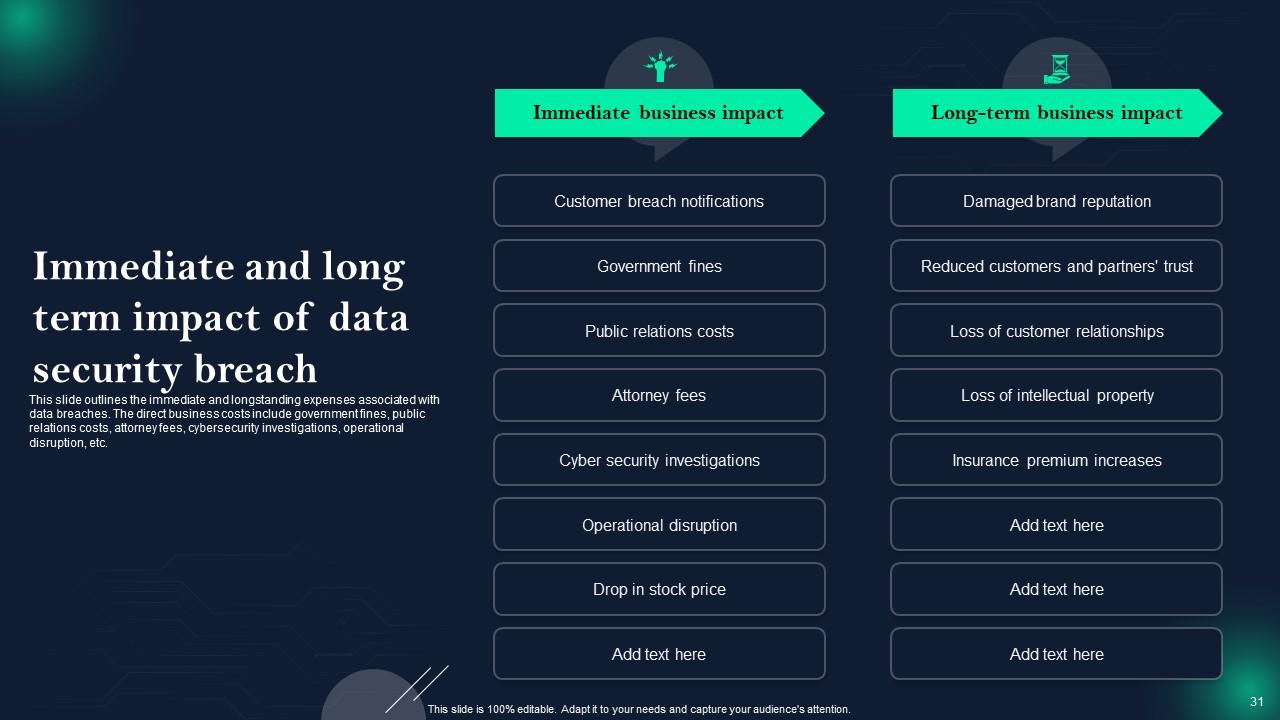
Slide 31: This slide shows Immediate and long term impact of data security breach.
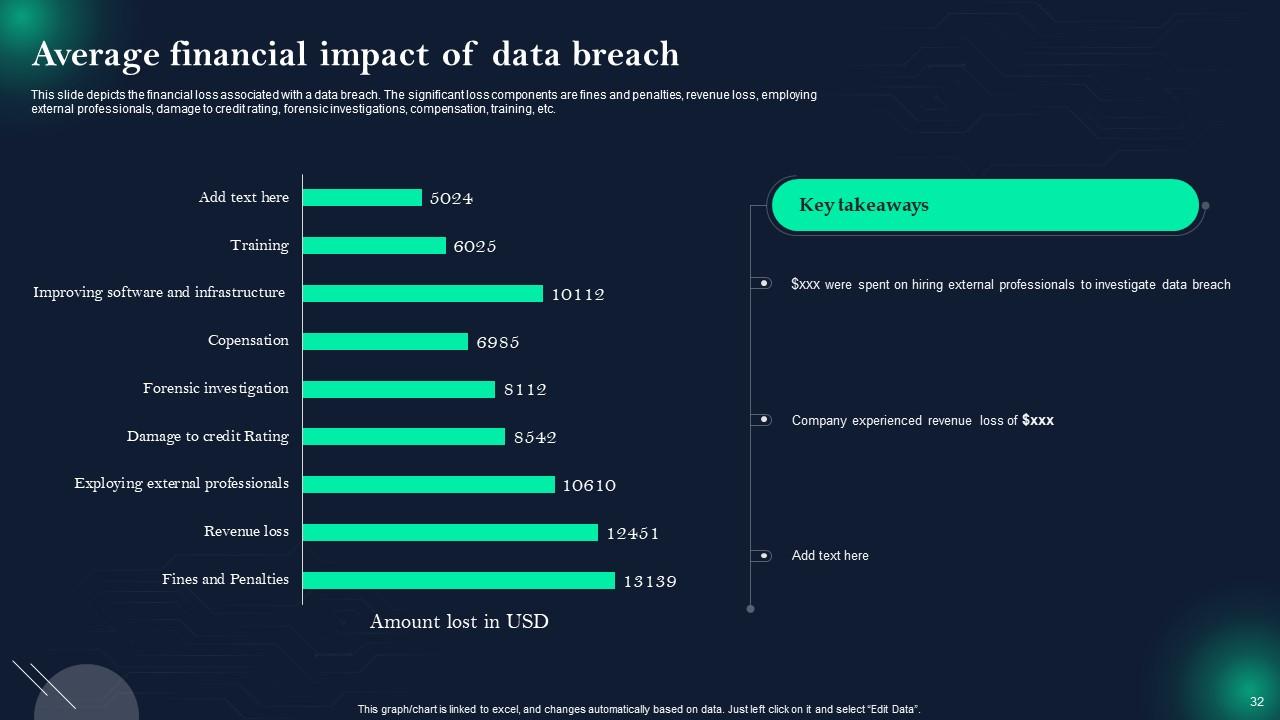
Slide 32: This slide presents Average financial impact of data breach.
Slide 33: This slide highlights title for topics that are to be covered next in the template.
Slide 34: This slide displays Data breach prevention strategies for enterprises.
Slide 35: This slide represents Data breach prevention strategies for users.
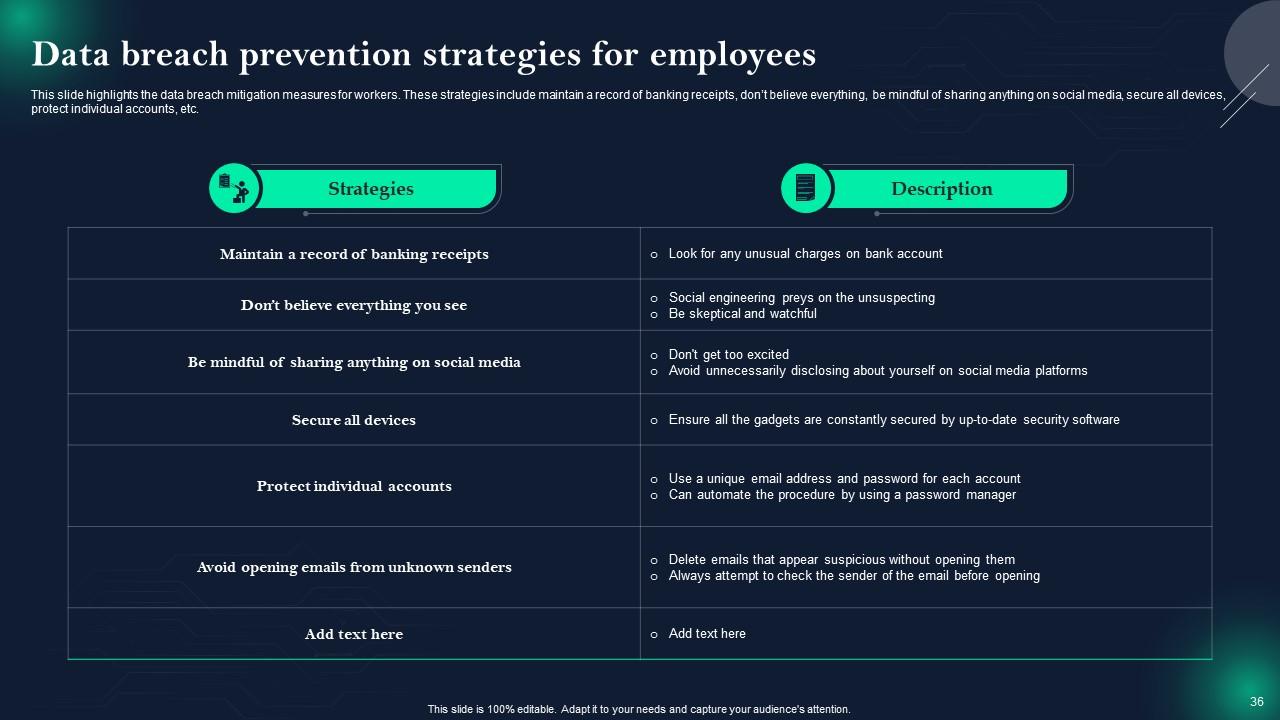
Slide 36: This slide showcases Data breach prevention strategies for employees.
Slide 37: This slide highlights title for topics that are to be covered next in the template.
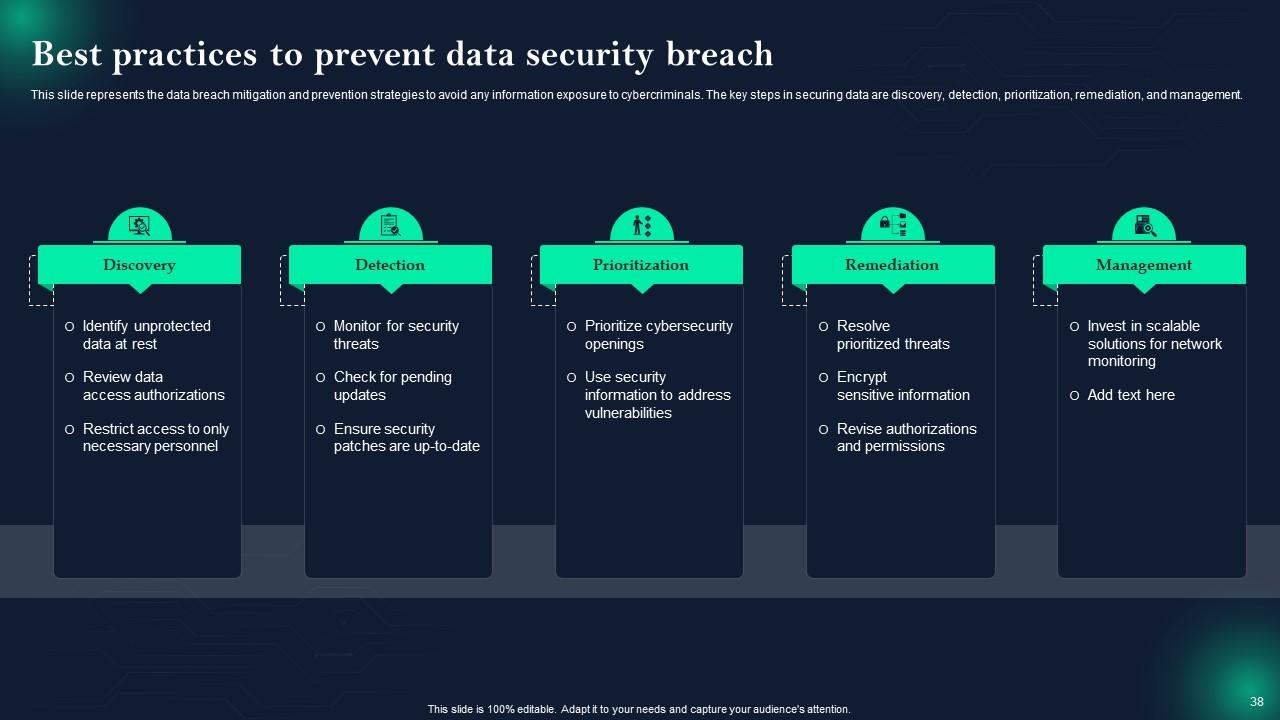
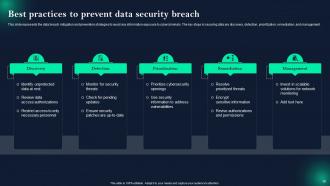
Slide 38: This slide shows Best practices to prevent data security breach.
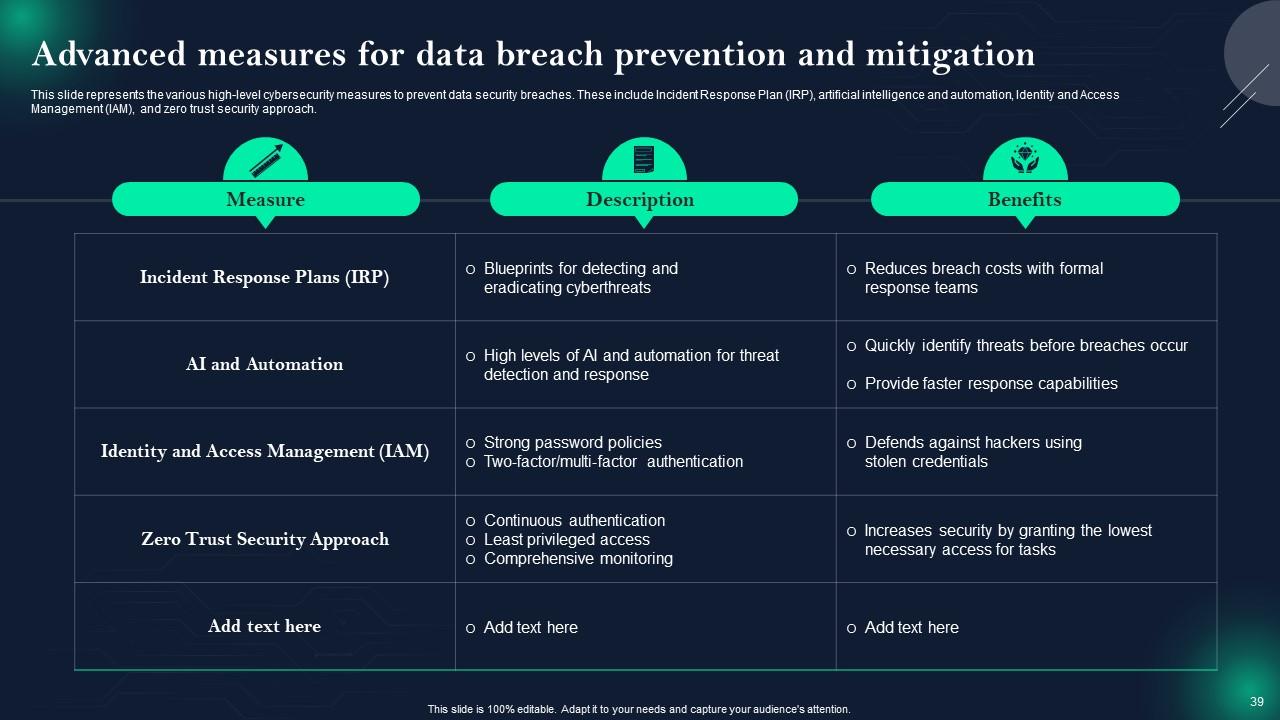
Slide 39: This slide presents Advanced measures for data breach prevention and mitigation.
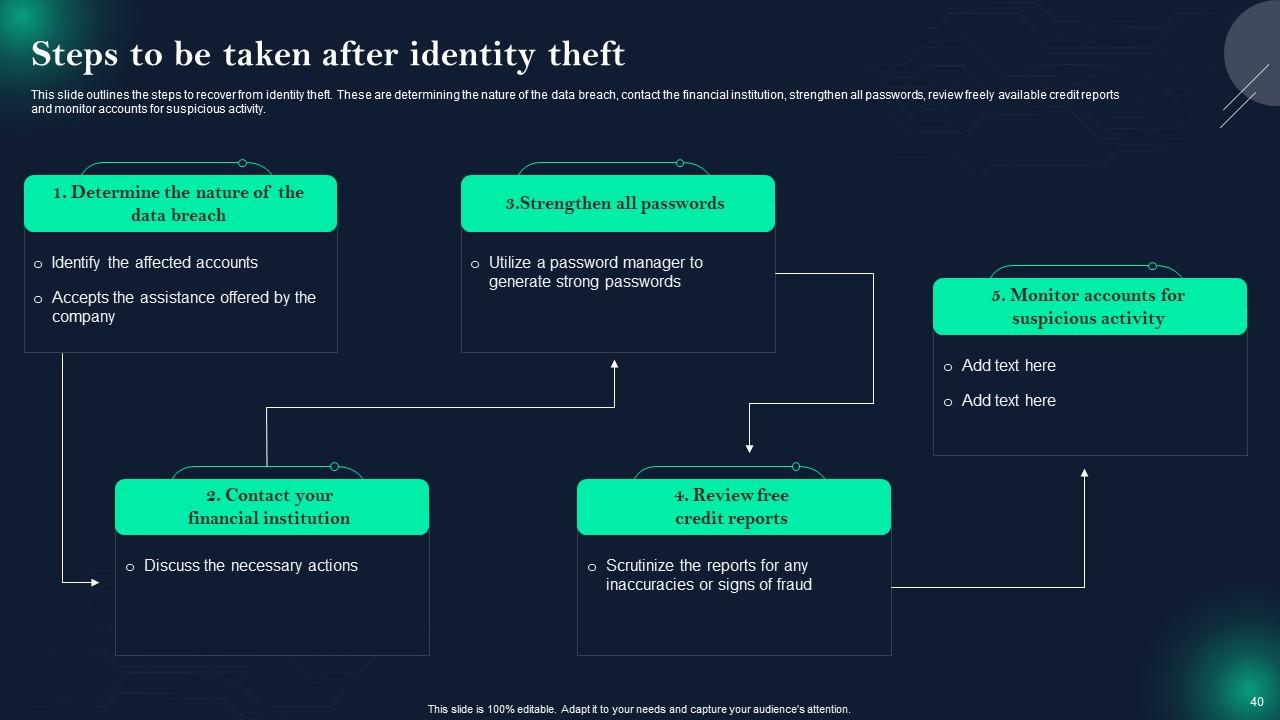
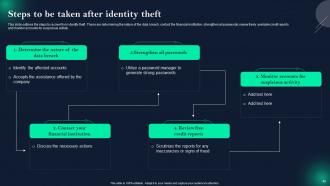
Slide 40: This slide displays Steps to be taken after identity theft.
Slide 41: This slide highlights title for topics that are to be covered next in the template.
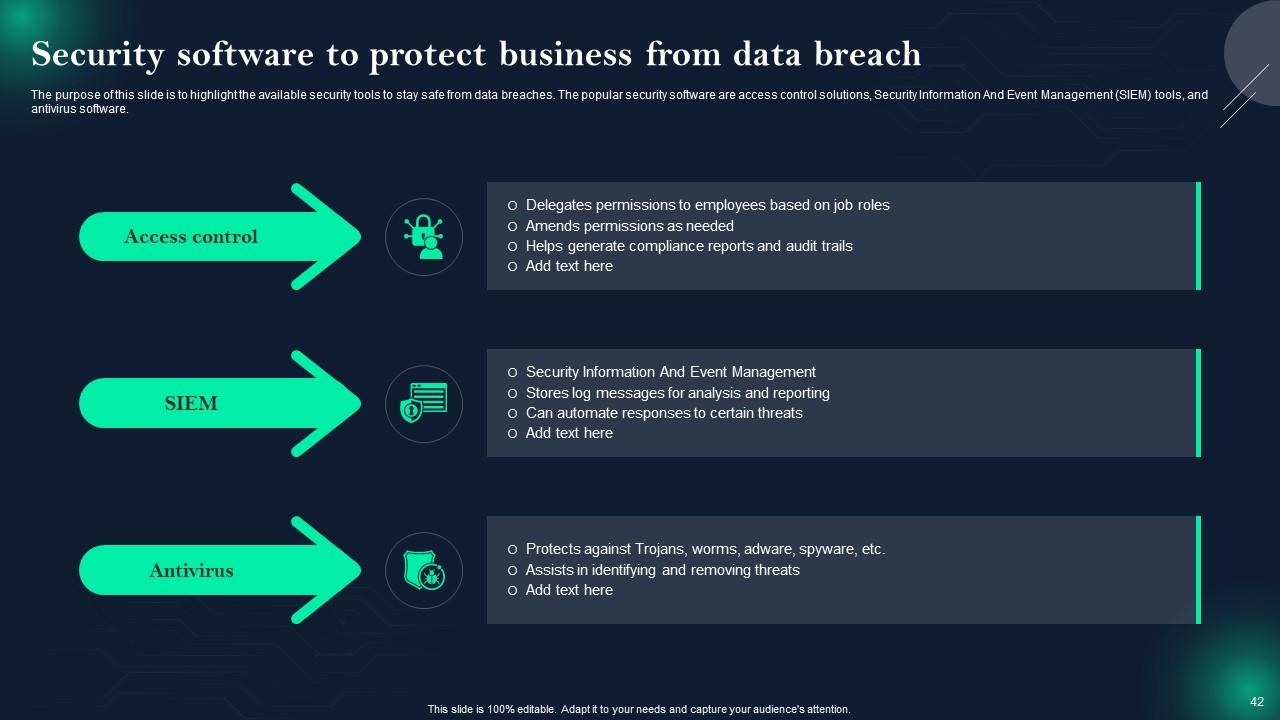
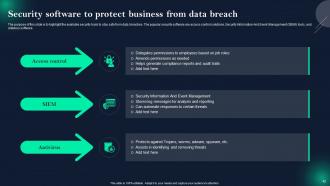
Slide 42: This slide represents Security software to protect business from data breach.
Slide 43: This slide showcases Data breach prevention services provided by security tools.
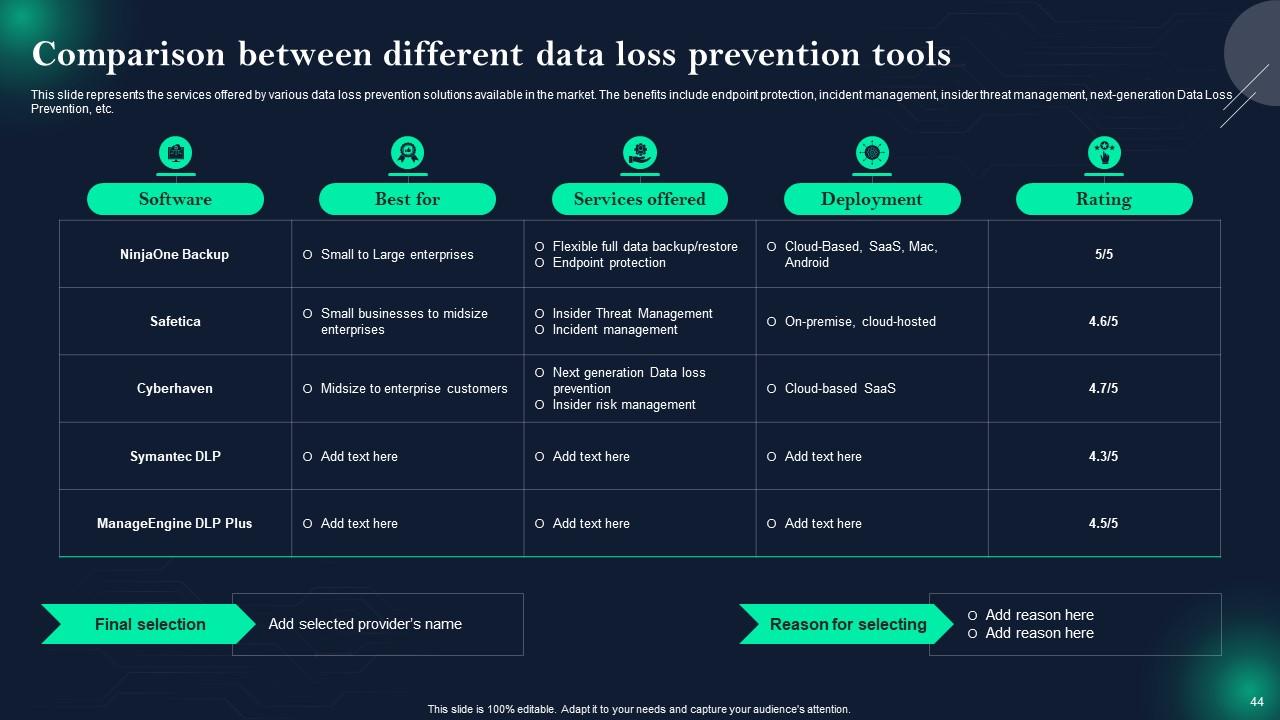
Slide 44: This slide shows Comparison between different data loss prevention tools.
Slide 45: This slide highlights title for topics that are to be covered next in the template.
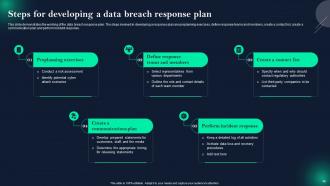
Slide 46: This slide presents Steps for developing a data breach response plan.
Slide 47: This slide highlights title for topics that are to be covered next in the template.
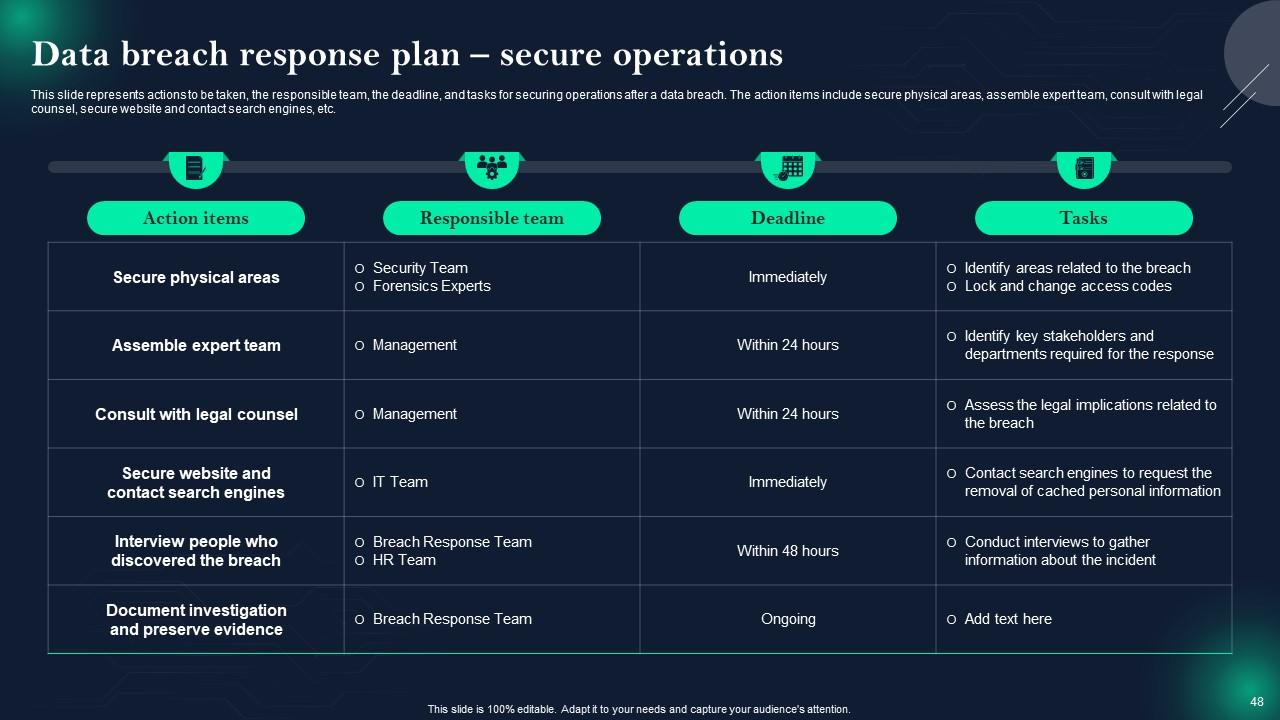
Slide 48: This slide displays Data breach response plan – secure operations.
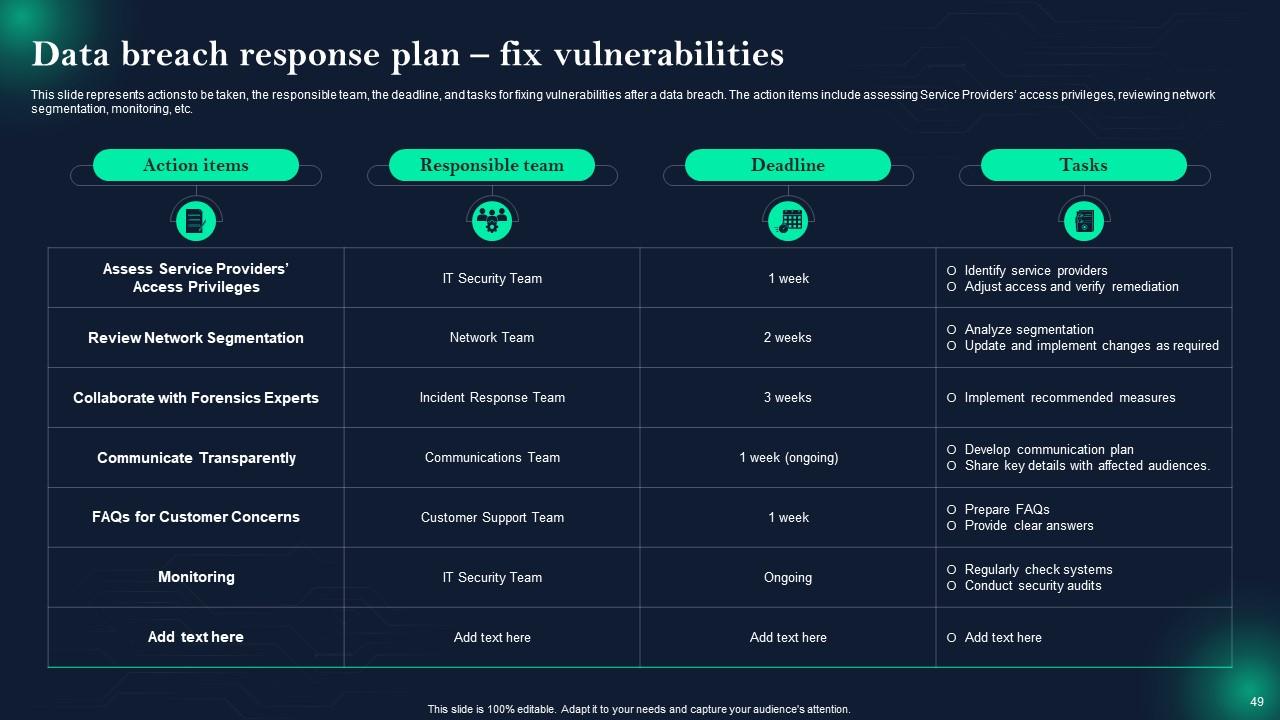
Slide 49: This slide represents Data breach response plan – fix vulnerabilities.
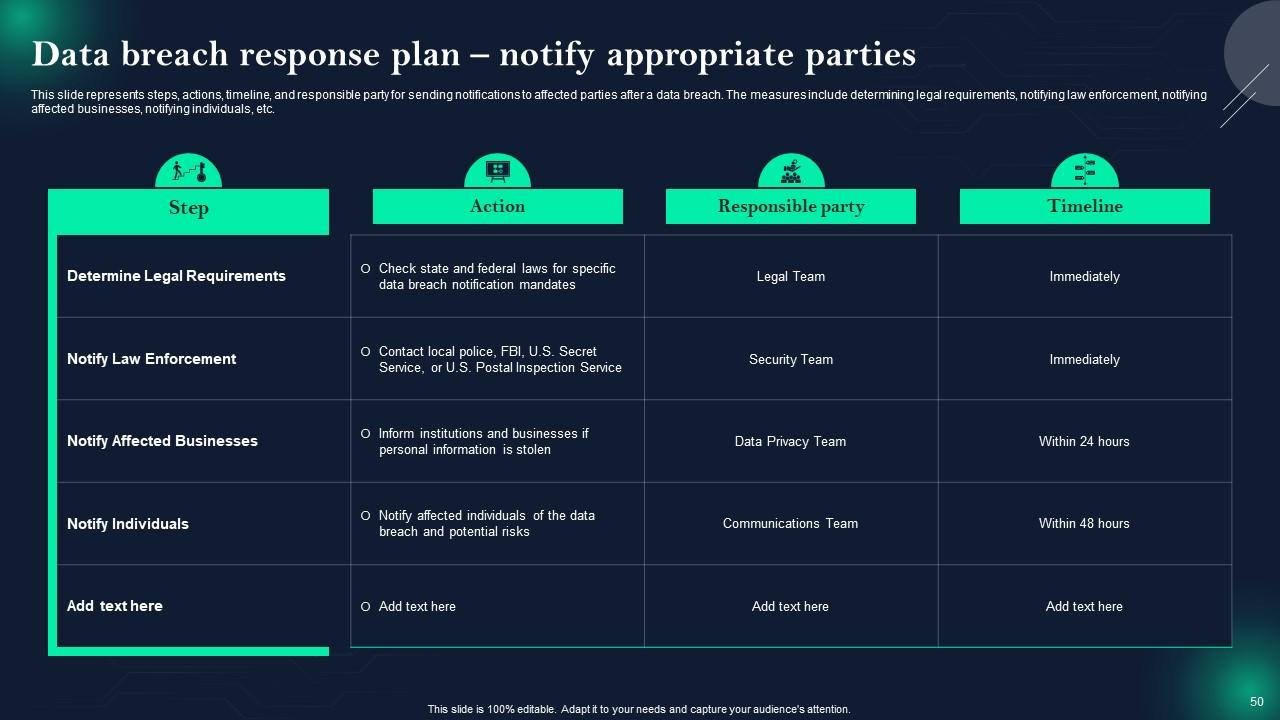
Slide 50: This slide showcases Data breach response plan – notify appropriate parties.
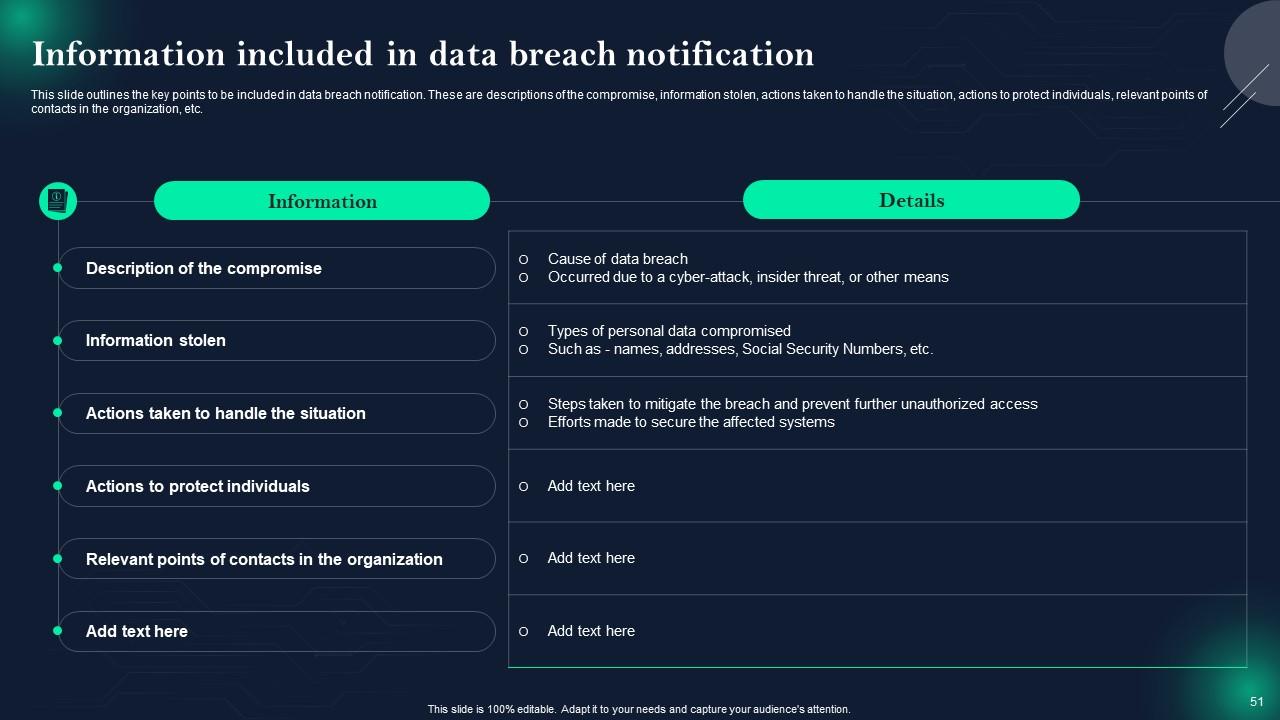
Slide 51: This slide shows Information included in data breach notification.
Slide 52: This slide highlights title for topics that are to be covered next in the template.
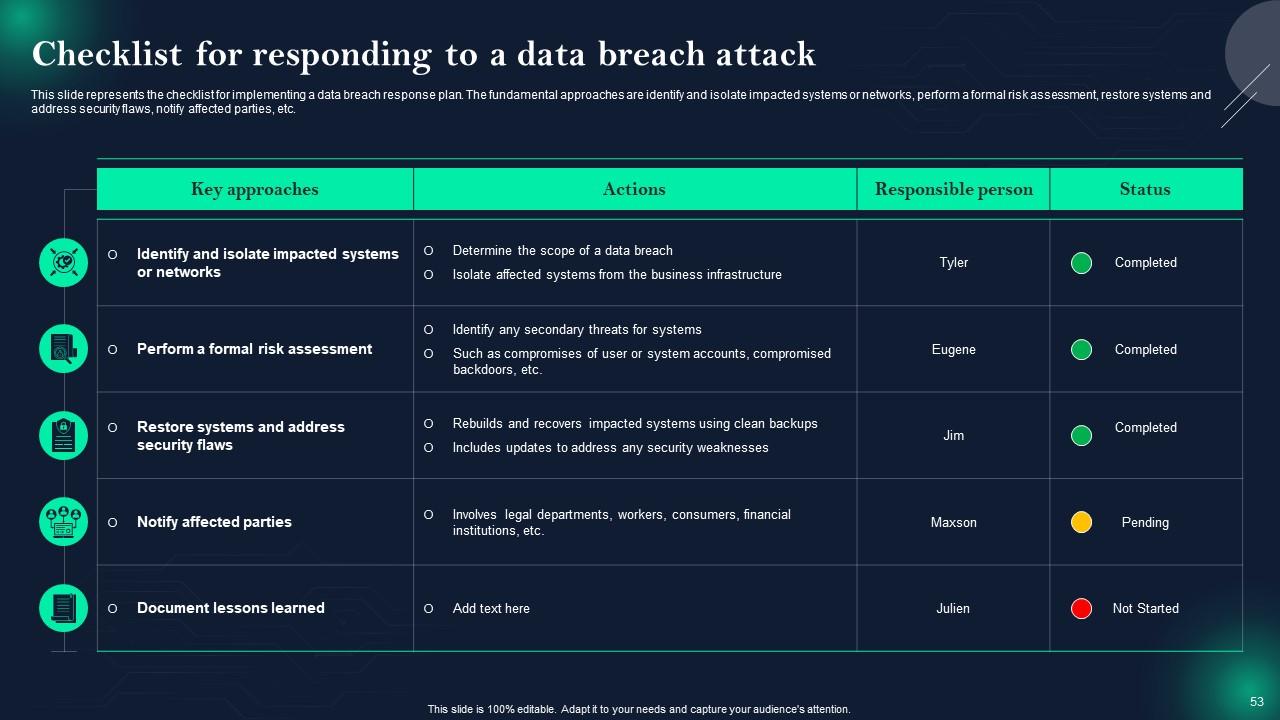
Slide 53: This slide presents Checklist for responding to a data breach attack.
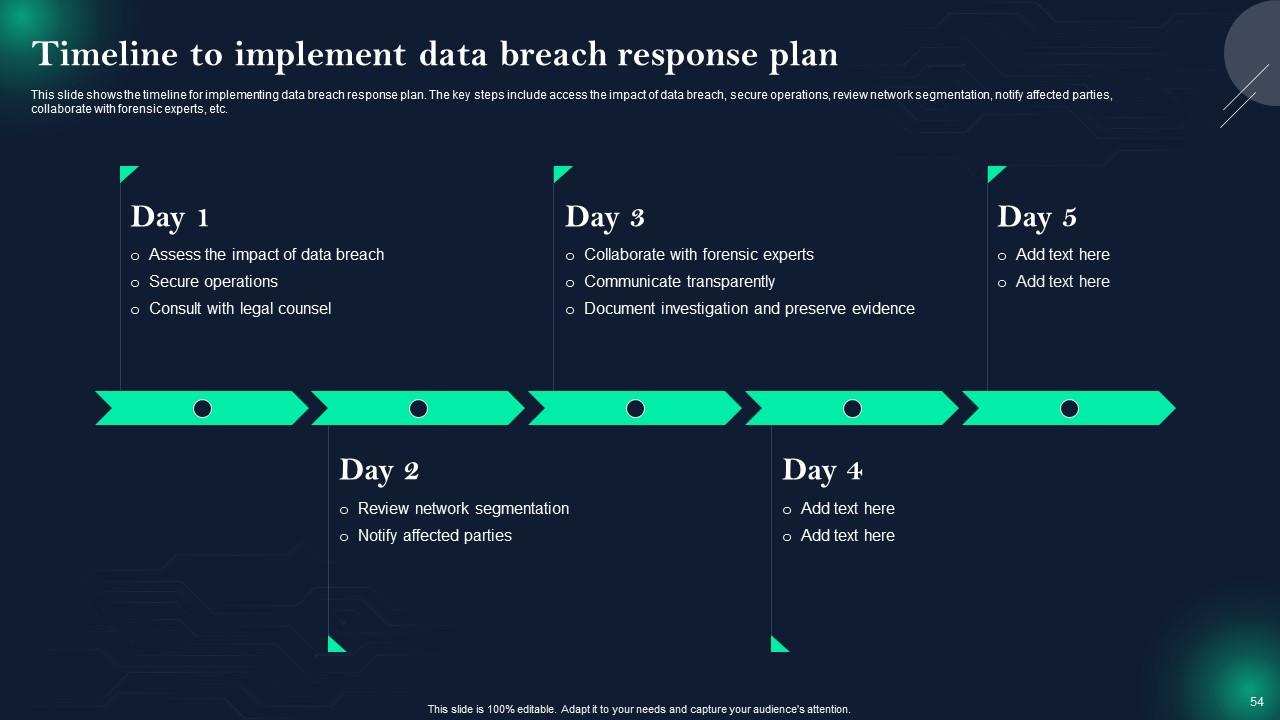
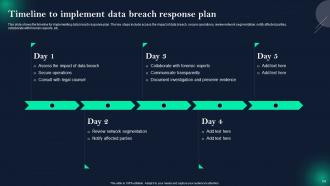
Slide 54: This slide displays Timeline to implement data breach response plan.
Slide 55: This slide highlights title for topics that are to be covered next in the template.
Slide 56: This slide represents Data breach awareness training program.
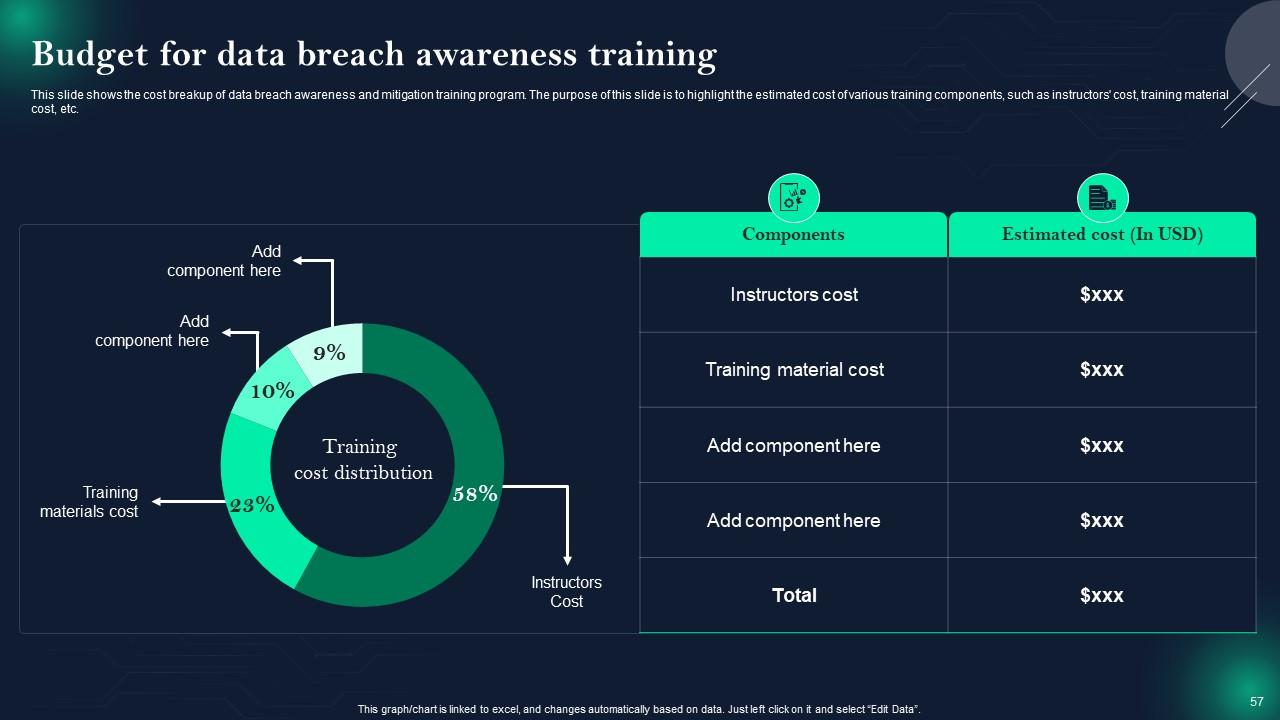
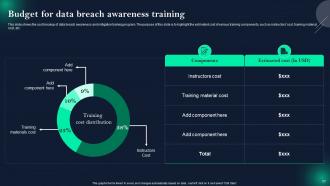
Slide 57: This slide showcases Budget for data breach awareness training.
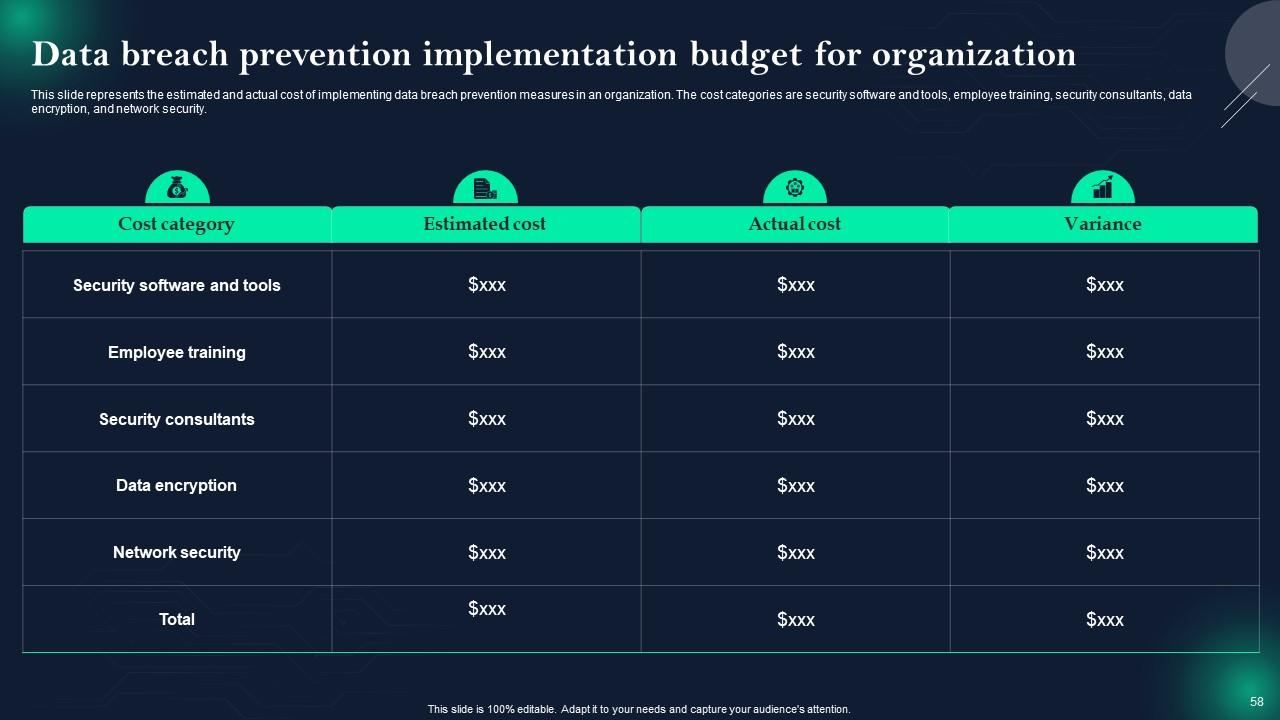
Slide 58: This slide shows Data breach prevention implementation budget for organization.
Slide 59: This slide highlights title for topics that are to be covered next in the template.
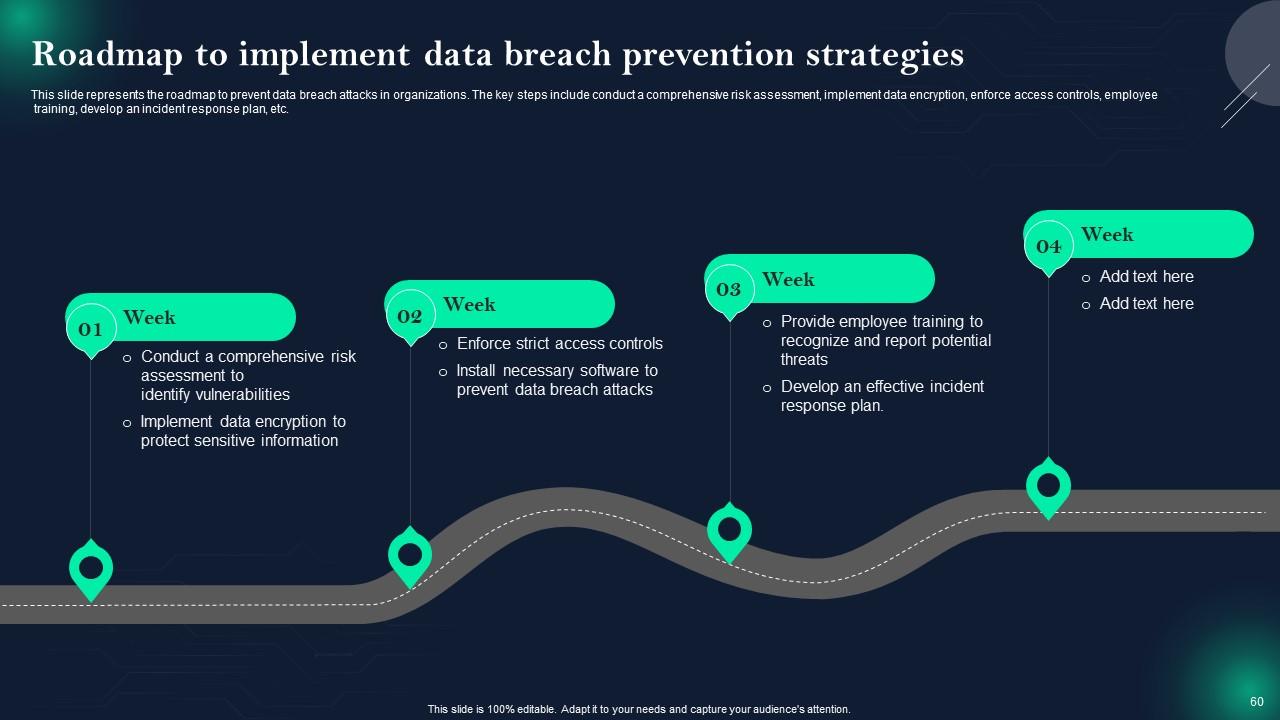
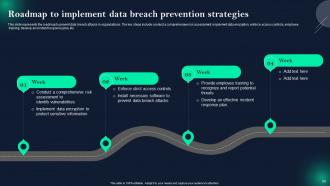
Slide 60: This slide presents Roadmap to implement data breach prevention strategies.
Slide 61: This slide highlights title for topics that are to be covered next in the template.
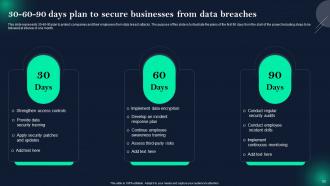
Slide 62: This slide displays 30-60-90 days plan to secure businesses from data breaches.
Slide 63: This slide highlights title for topics that are to be covered next in the template.
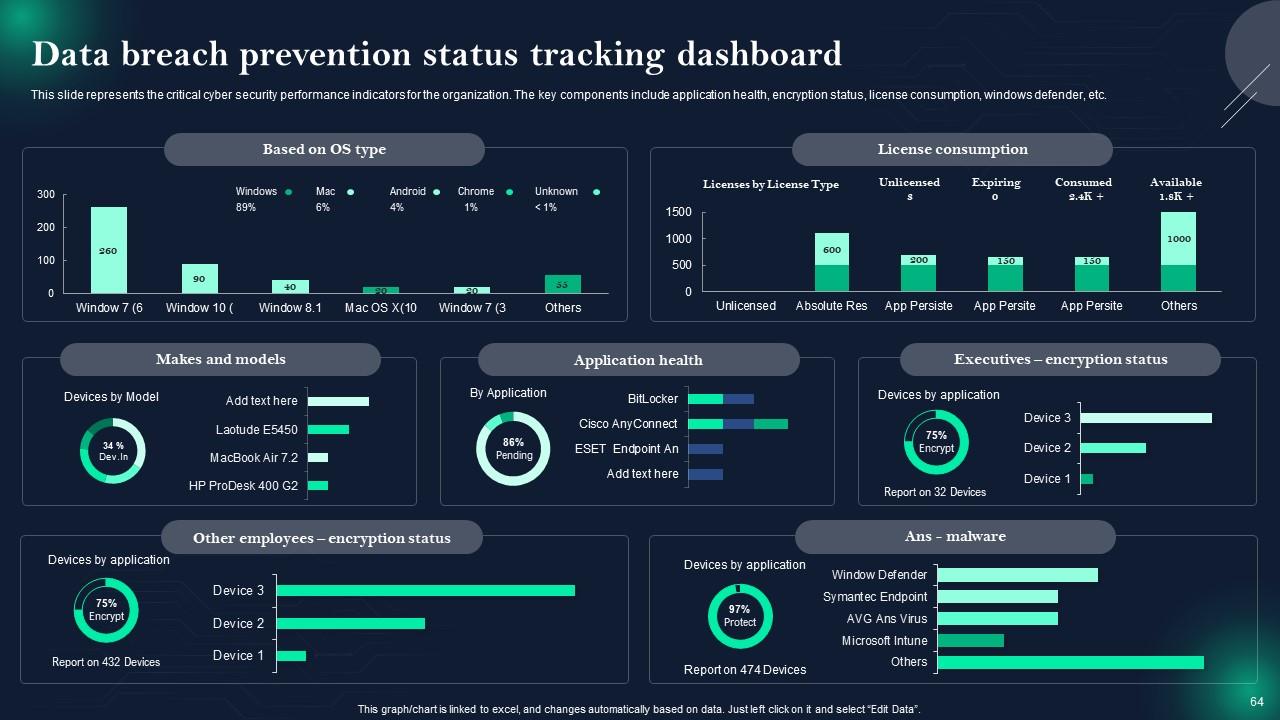
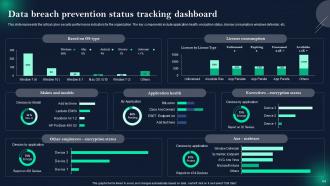
Slide 64: This slide represents Data breach prevention status tracking dashboard.
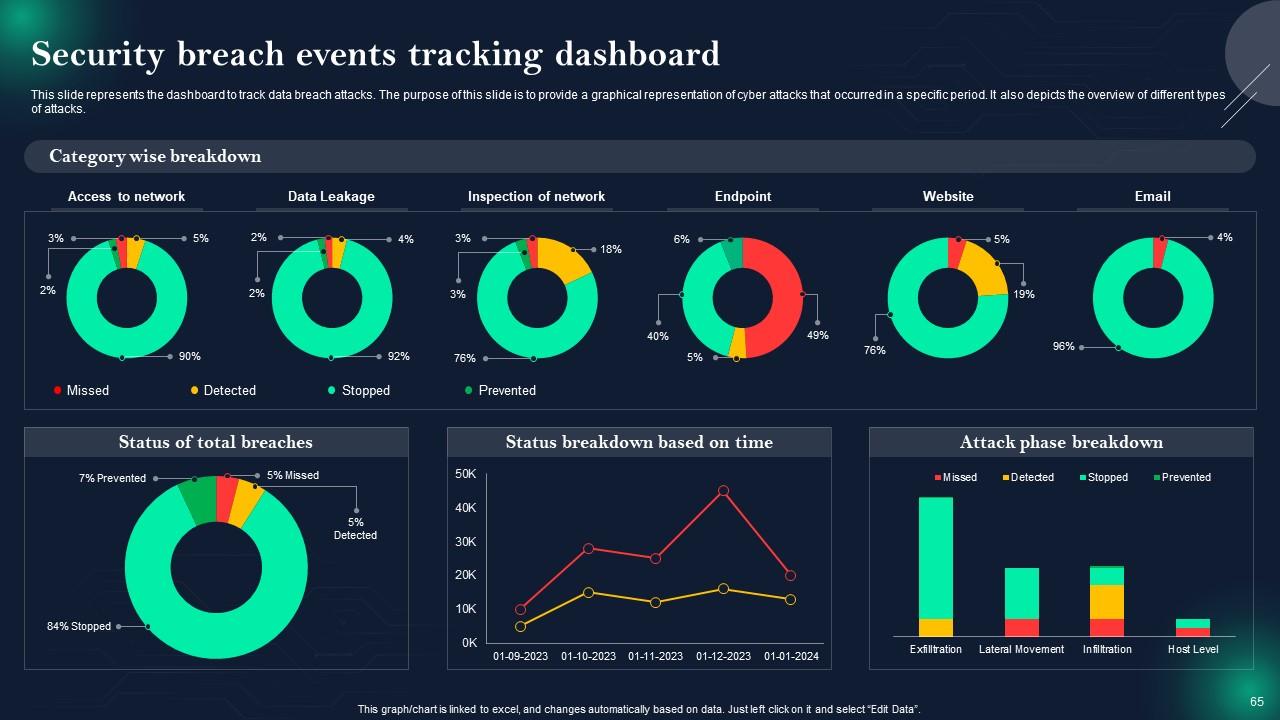
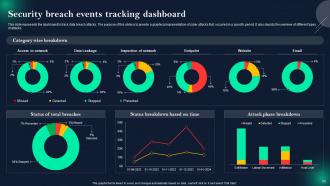
Slide 65: This slide showcases Security breach events tracking dashboard.
Slide 66: This slide contains all the icons used in this presentation.
Slide 67: This slide is titled as Additional Slides for moving forward.
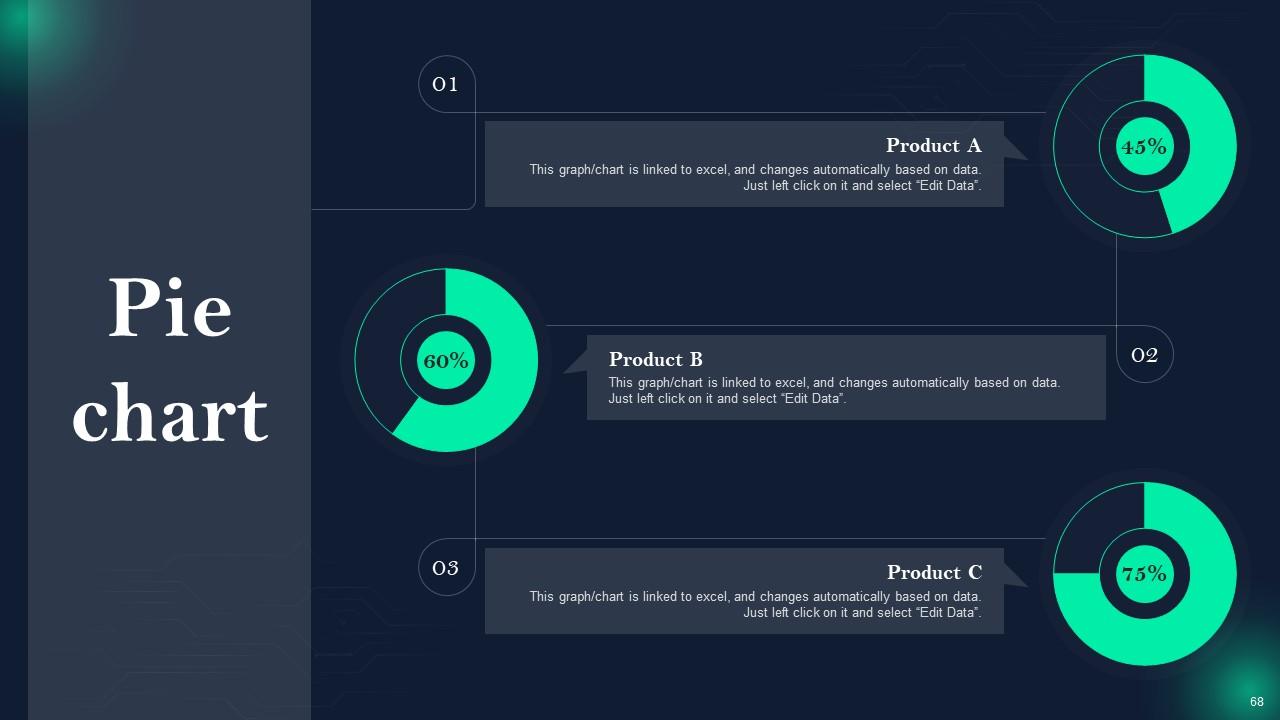
Slide 68: This slide shows Pie Chart with data in percentage.
Slide 69: This slide contains Puzzle with related icons and text.
Slide 70: This slide shows SWOT describing- Strength, Weakness, Opportunity, and Threat.
Slide 71: This is an Idea Generation slide to state a new idea or highlight information, specifications etc.
Slide 72: This is a Financial slide. Show your finance related stuff here.
Slide 73: This slide shows Post It Notes. Post your important notes here.
Slide 74: This slide depicts Venn diagram with text boxes.
Slide 75: This is a Thank You slide with address, contact numbers and email address.
Data Breach Prevention And Mitigation Strategies For Businesses Powerpoint Presentation Slides with all 80 slides:
Use our Data Breach Prevention And Mitigation Strategies For Businesses Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
FAQs
Data security breaches can take various forms, including unauthorized access, data leaks, phishing attacks, malware infections, and insider threats. Each type poses unique risks and challenges to organizations.
Data breach attacks can occur due to a range of factors, including weak passwords, software vulnerabilities, human errors, and social engineering tactics like phishing. Addressing these causes is essential for prevention.
Attack vectors for data breaches include email phishing, malware, SQL injection, and credential theft. Understanding these vectors helps organizations better defend against potential attacks.
The immediate impact includes data exposure and potential legal consequences. Long-term effects may include damage to an organization's reputation, loss of customer trust, and financial repercussions due to legal fees and regulatory fines.
Best practices for data breach prevention include regular employee training, strong password policies, software patch management, multi-factor authentication, and encryption. These measures help safeguard data and reduce the risk of breaches.
-
Professional and unique presentations.
-
The quality of PowerPoint templates I found here is unique and unbeatable. Keep up the good work and continue providing us with the best slides!