Cloud Computing Security Powerpoint Presentation Slides
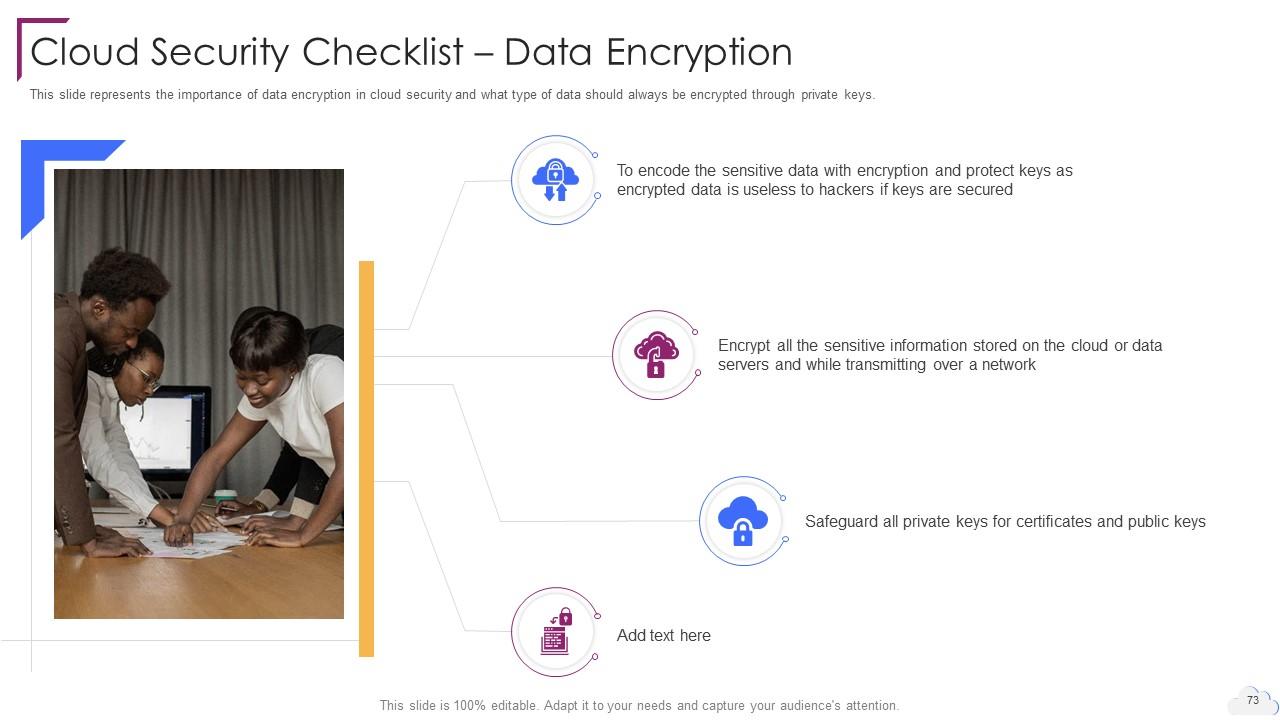
Cloud Security, also known as cloud computing security, comprises various approaches, controls, strategies, and technologies that work together to safeguard cloud based frameworks, information, and infrastructure. These security measures are designed to protect cloud information, support administrative consistency, secure clients privacy, and set validation rules for individual clients and devices. Also, it highlights the security measures taken in cloud security and details on risks or threats that can impact the security of a cloud. Furthermore, this PPT covers the segmentation of cloud security responsibilities and topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. Moreover, the cloud data protection PPT covers the list of the industries that can benefit from cloud security. It also provides information on the zero trust policy along with its benefit. At last, this cloud computing security presentation captures the 30 60 90 days plan to implement cloud security in the organization, a roadmap to measure the implementation process, and a dashboard to observe the performance after implementing cloud security in the business. Get access to our powerful cloud computing ppt templates now.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of eighty eight slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Cloud Computing Security. State Your Company Name and begin.
Slide 2: This slide states Agenda of the presentation.
Slide 3: This slide presents Table of Content for the presentation.
Slide 4: This is another slide continuing Table of Content for the presentation.
Slide 5: This slide highlights title for topics that are to be covered next in the template.
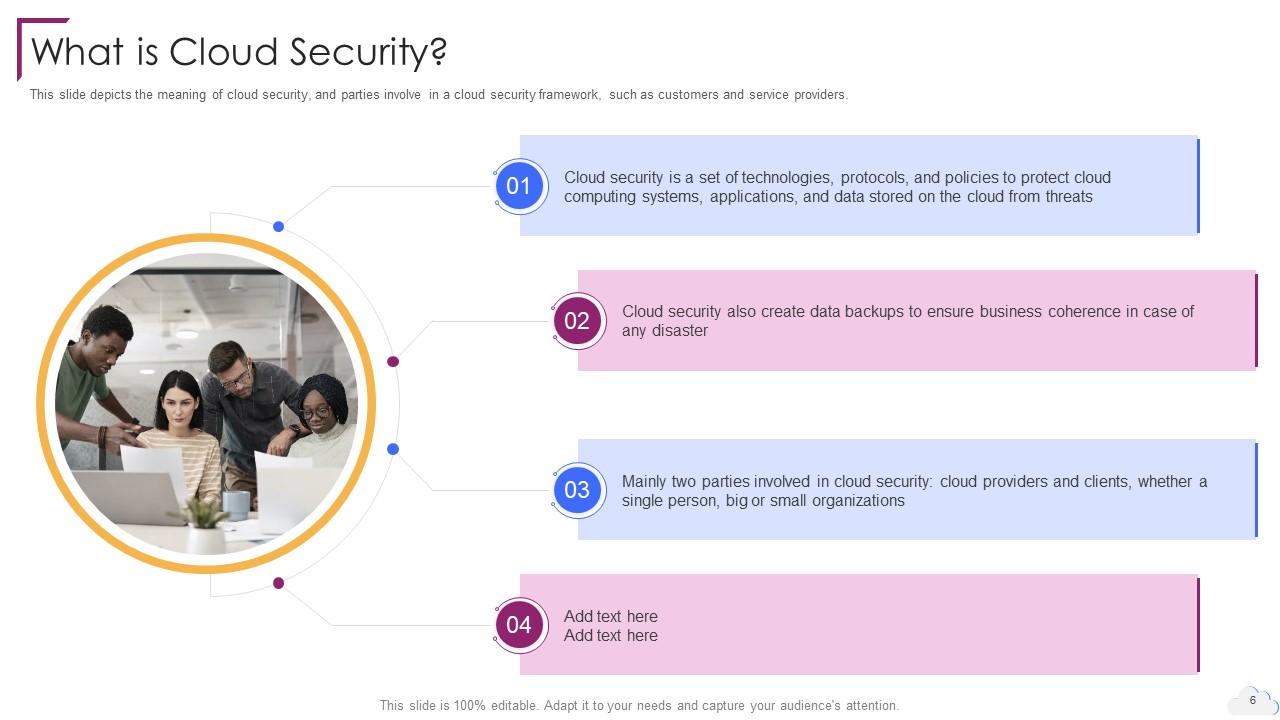
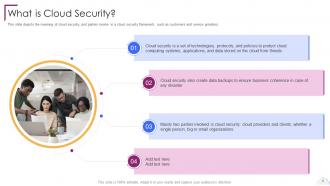
Slide 6: This slide depicts the meaning of cloud security, and parties involve in a cloud security framework.
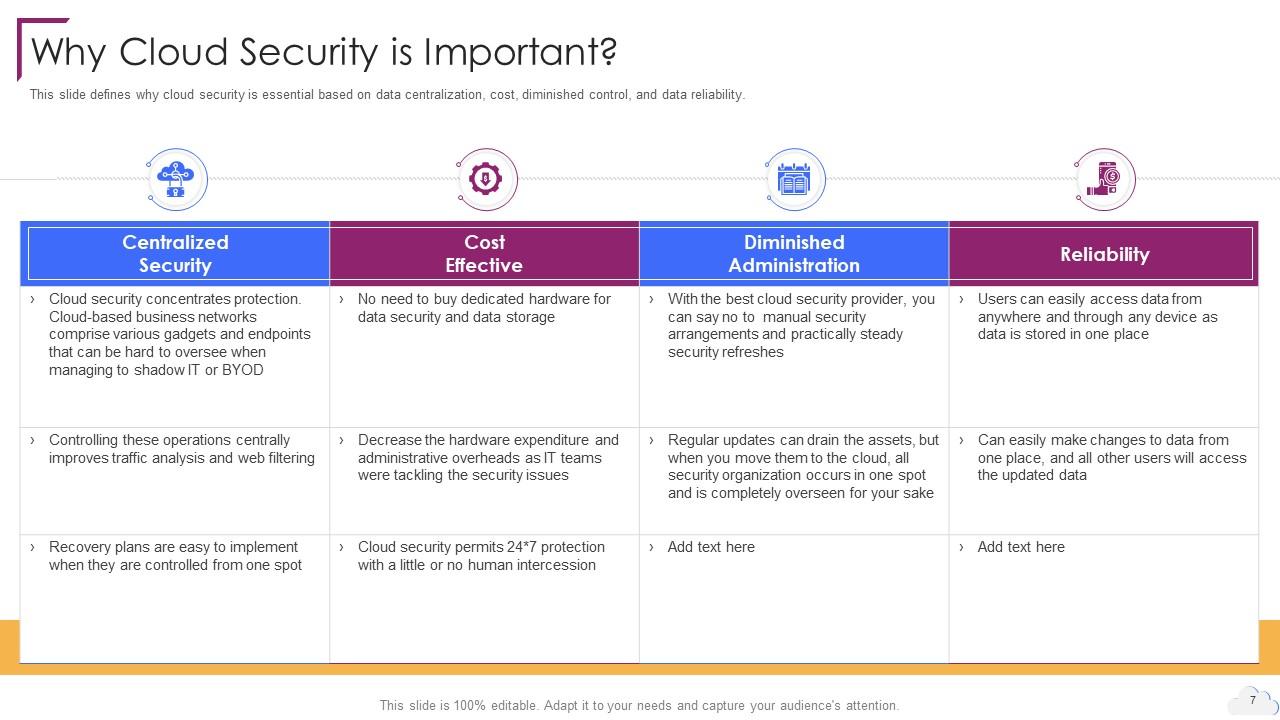
Slide 7: This slide defines why cloud security is essential based on data centralization, cost, diminished control, etc.
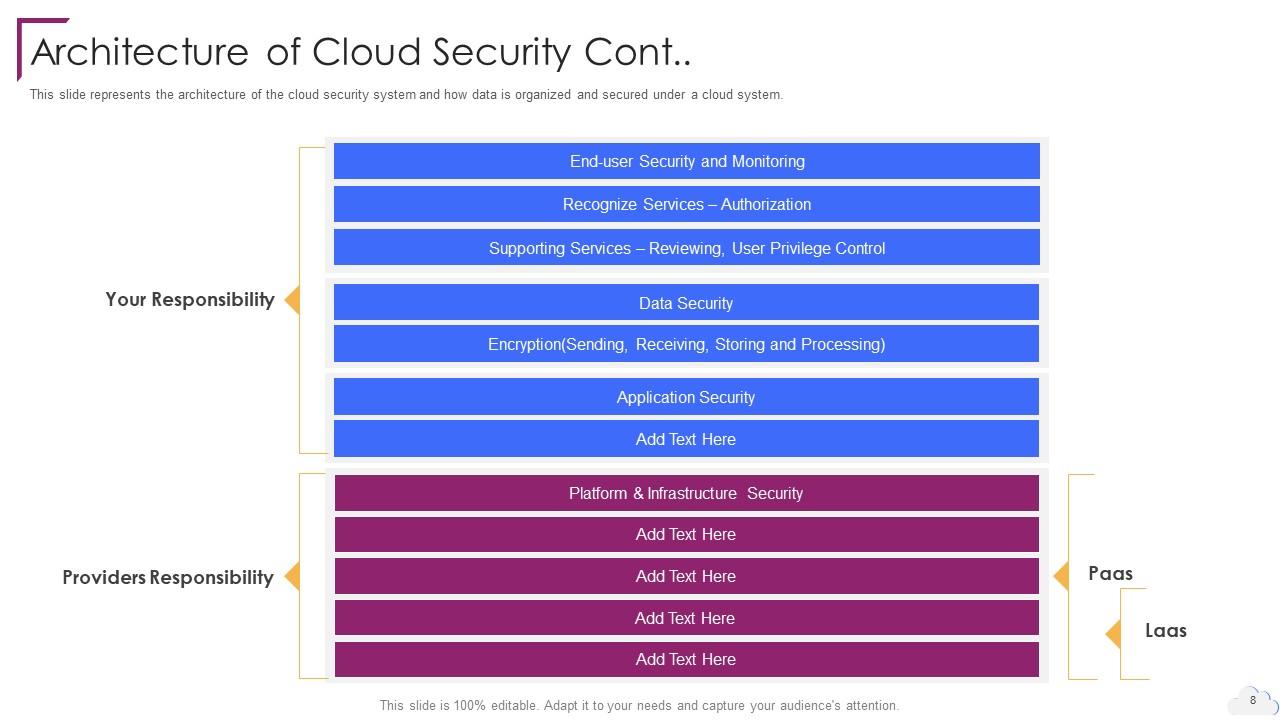
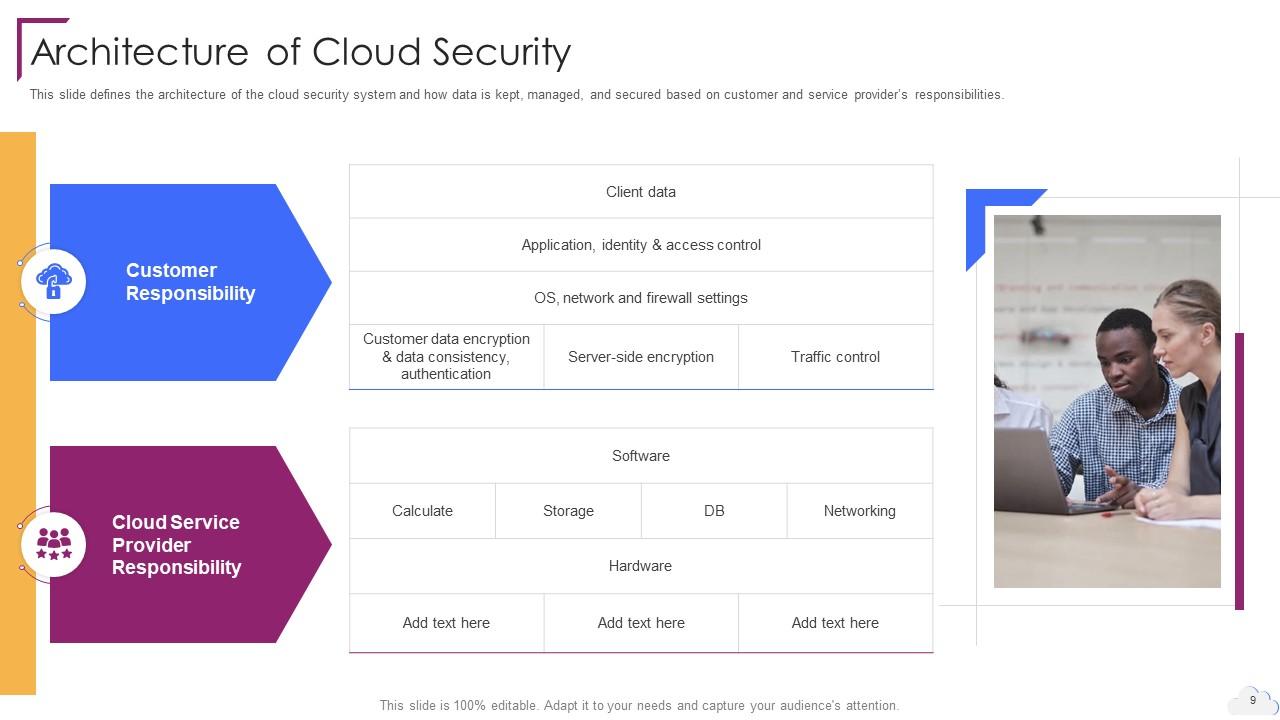
Slide 8: This slide represents the architecture of the cloud security system.
Slide 9: This is another slide continuing architecture of the cloud security system.
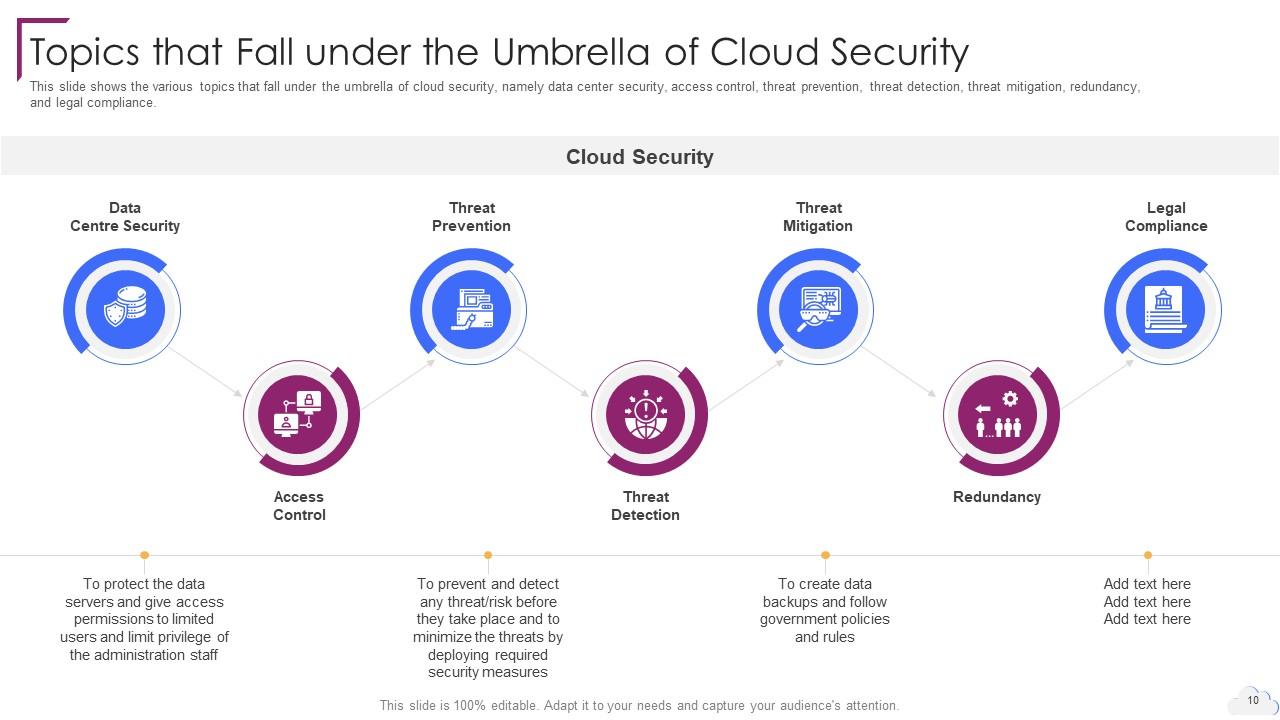
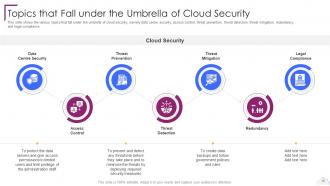
Slide 10: This slide shows Topics that Fall under the Umbrella of Cloud Security.
Slide 11: This slide shows factors that make cloud security different.
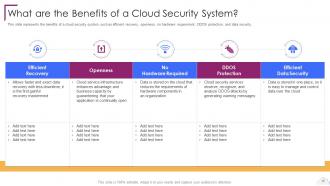
Slide 12: This slide represents the benefits of a cloud security system.
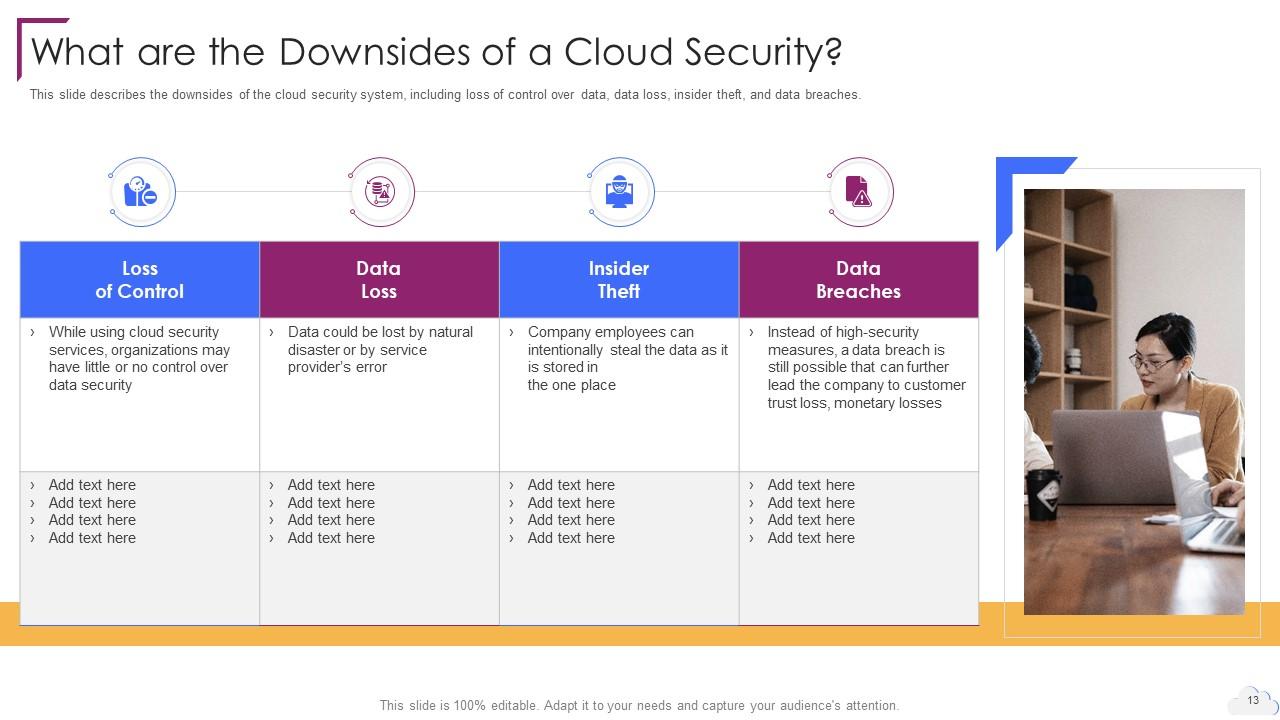
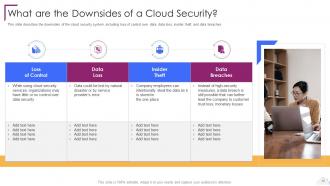
Slide 13: This slide describes the downsides of the cloud security system.
Slide 14: This slide highlights title for topics that are to be covered next in the template.
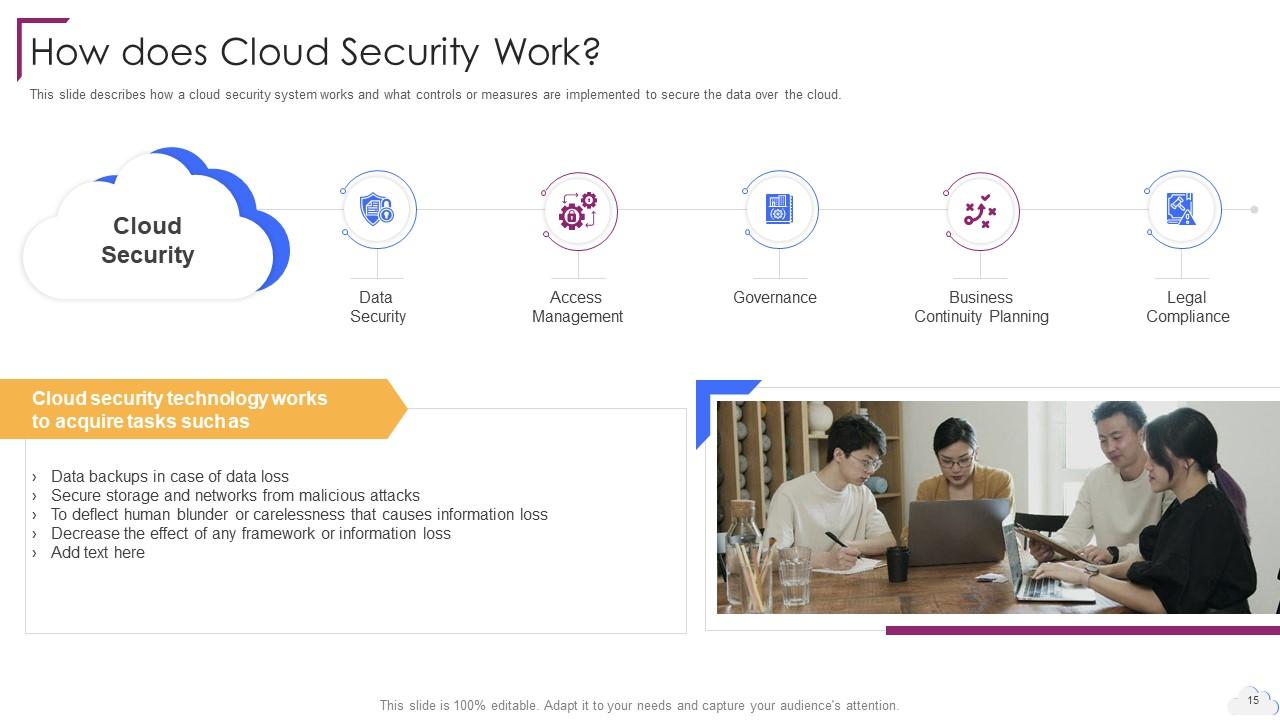
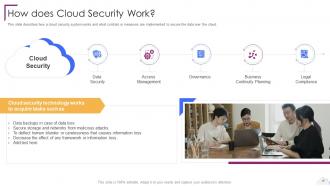
Slide 15: This slide describes how a cloud security system works.
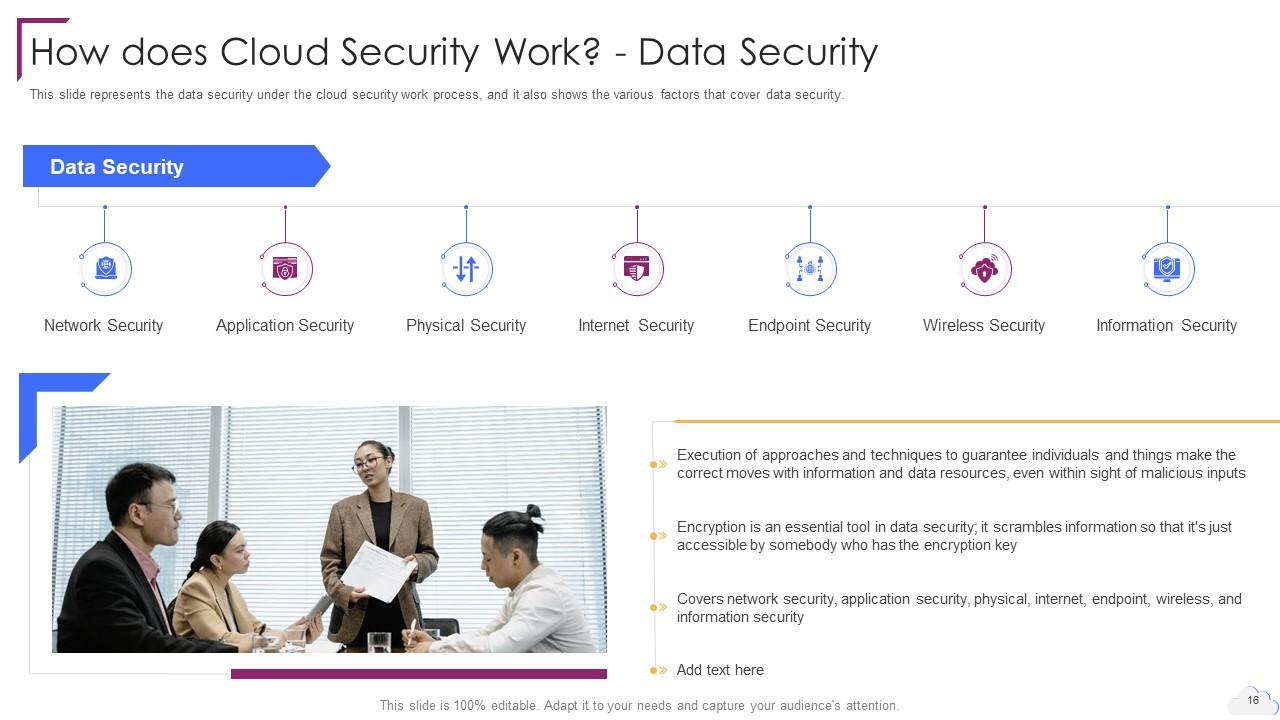
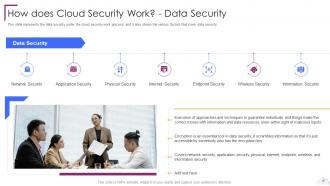
Slide 16: This slide represents the data security under the cloud security work process.
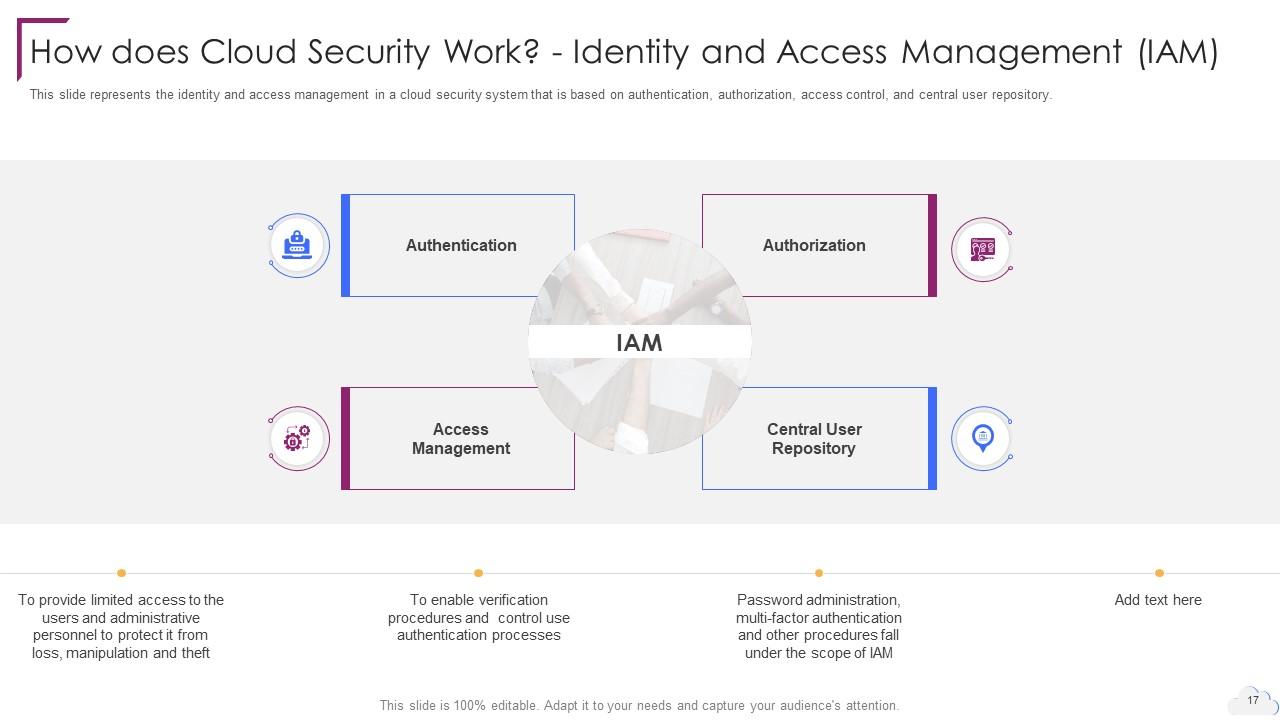
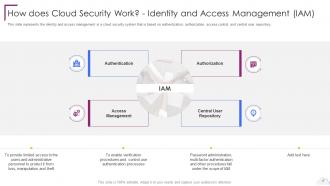
Slide 17: This slide represents the identity and access management in a cloud security system.
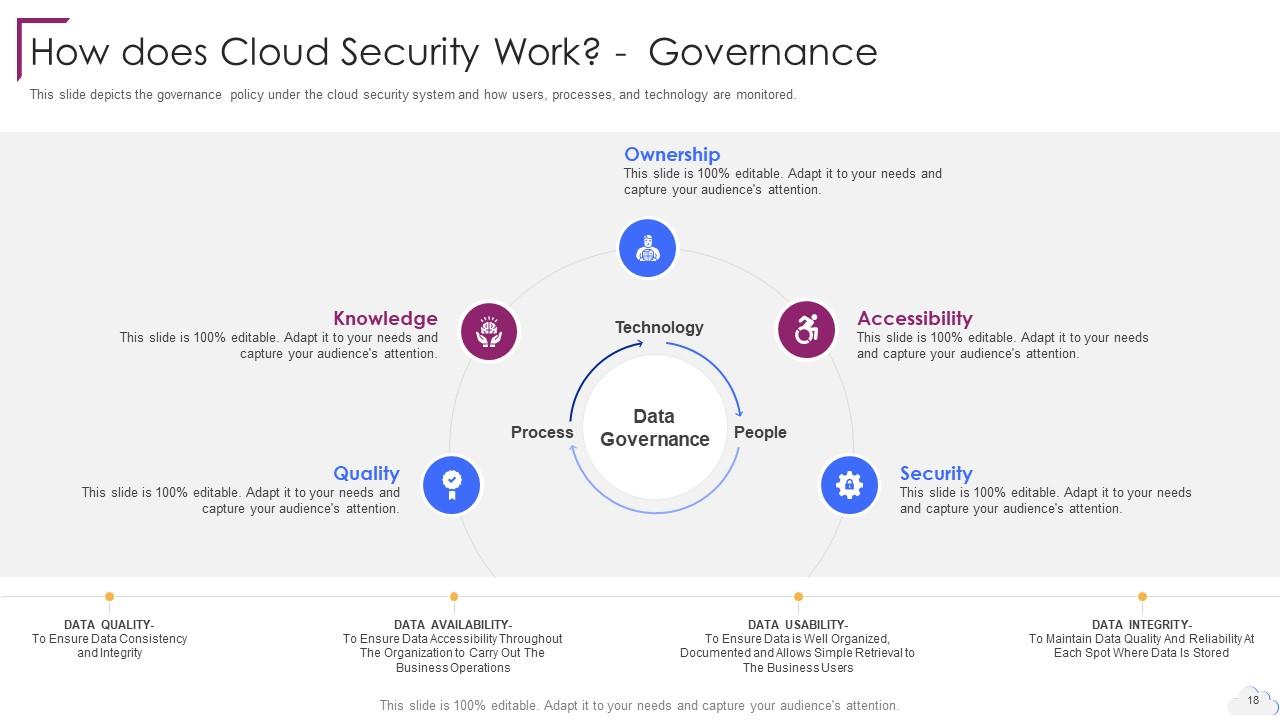
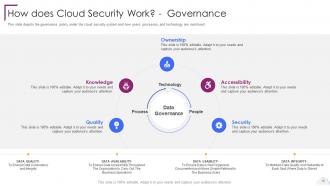
Slide 18: This slide depicts the governance policy under the cloud security system.
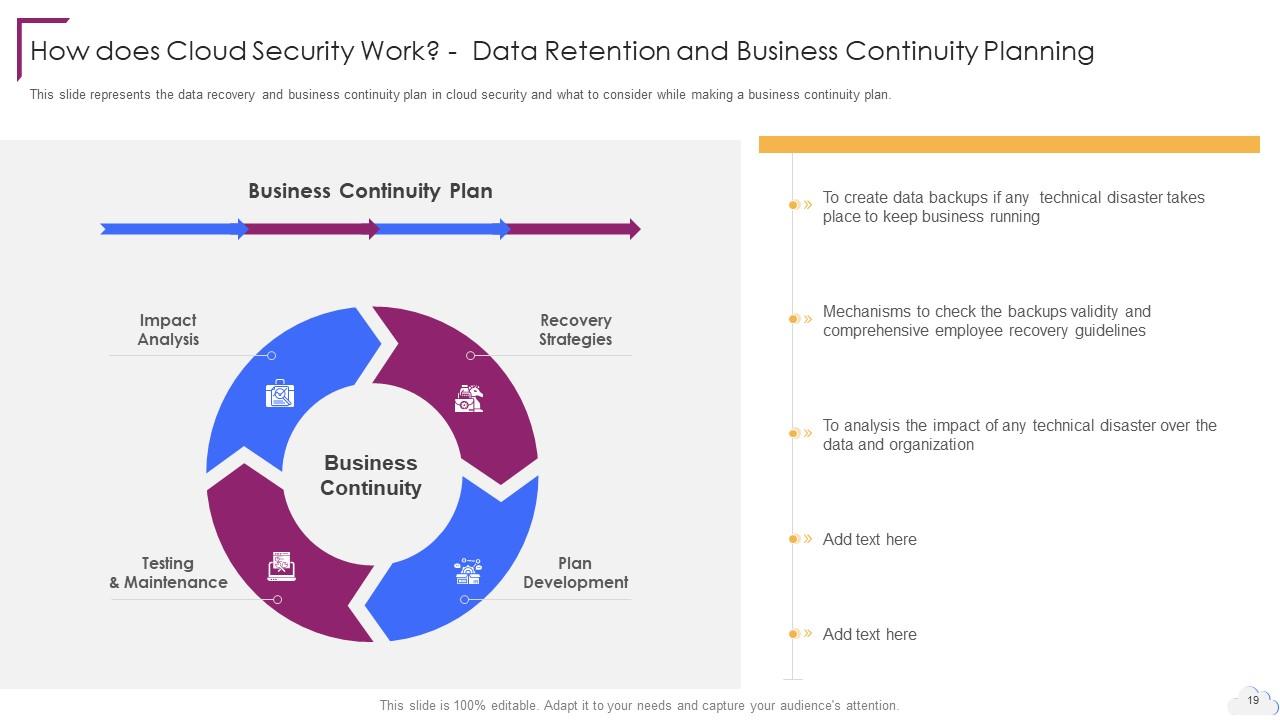
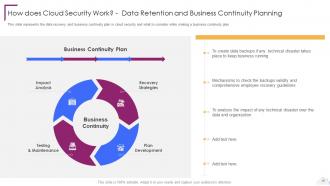
Slide 19: This slide represents the data recovery and business continuity plan in cloud security.
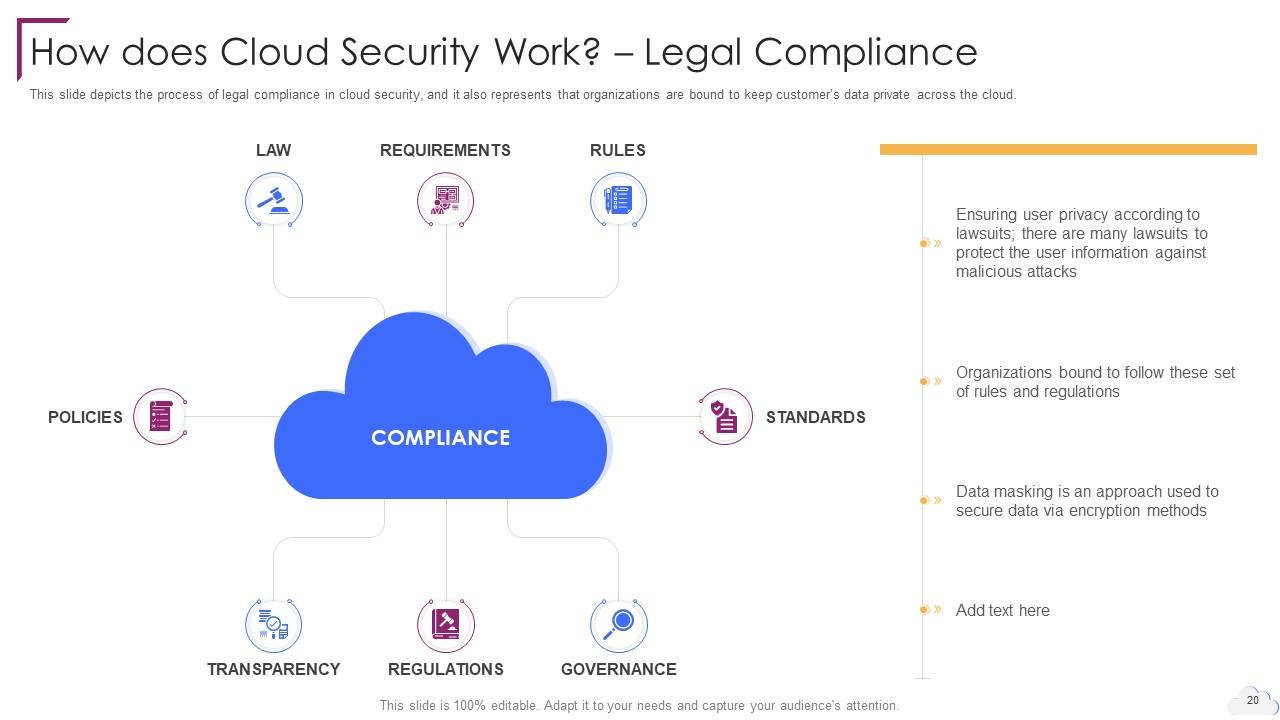
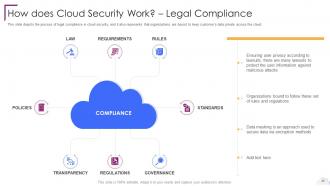
Slide 20: This slide depicts the process of legal compliance in cloud security.
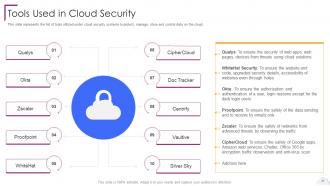
Slide 21: This slide represents the list of tools utilized under cloud security systems.
Slide 22: This slide highlights title for topics that are to be covered next in the template.
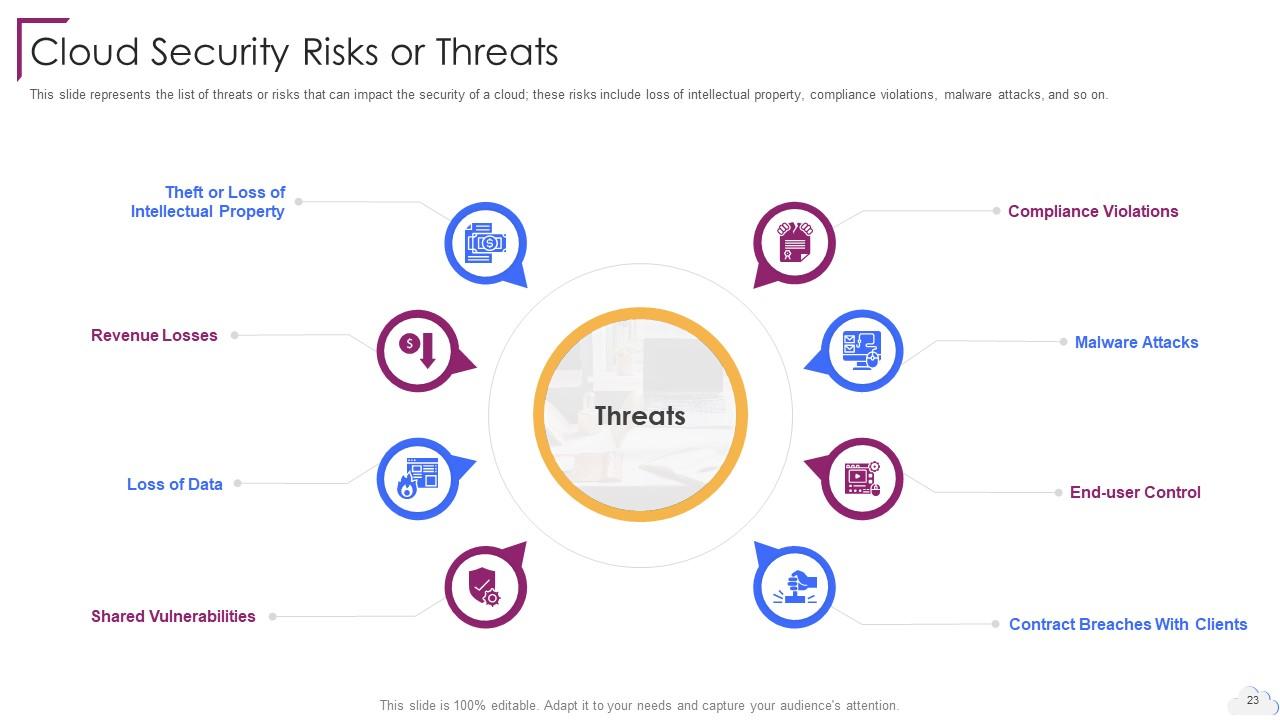
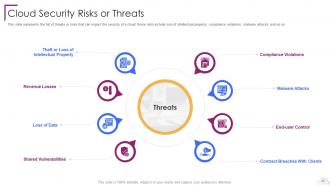
Slide 23: This slide represents the list of threats or risks that can impact the security of a cloud.
Slide 24: This slide showcases Theft or Loss of Intellectual Property.
Slide 25: This slide depicts the value of compliance violations threat of cloud security.
Slide 26: This slide represents the malware threat of cloud security and how it can affect data stored on the cloud.
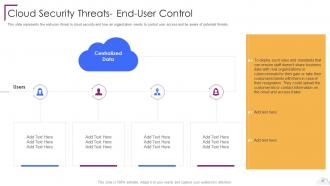
Slide 27: This slide presents the end-user threat in cloud security.
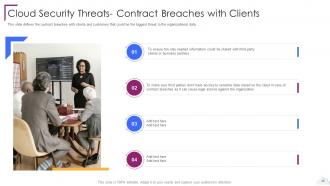
Slide 28: This slide defines the contract breaches with clients and customers.
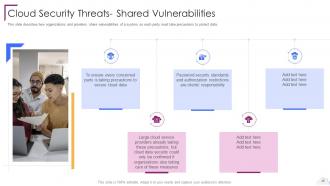
Slide 29: This slide describes how organizations and providers share vulnerabilities of a system.
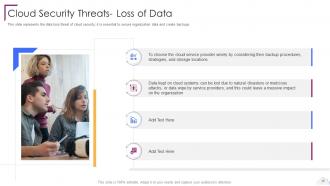
Slide 30: This slide represents the data loss threat of cloud security.
Slide 31: This slide represents the revenue loss threat of cloud security.
Slide 32: This slide highlights title for topics that are to be covered next in the template.
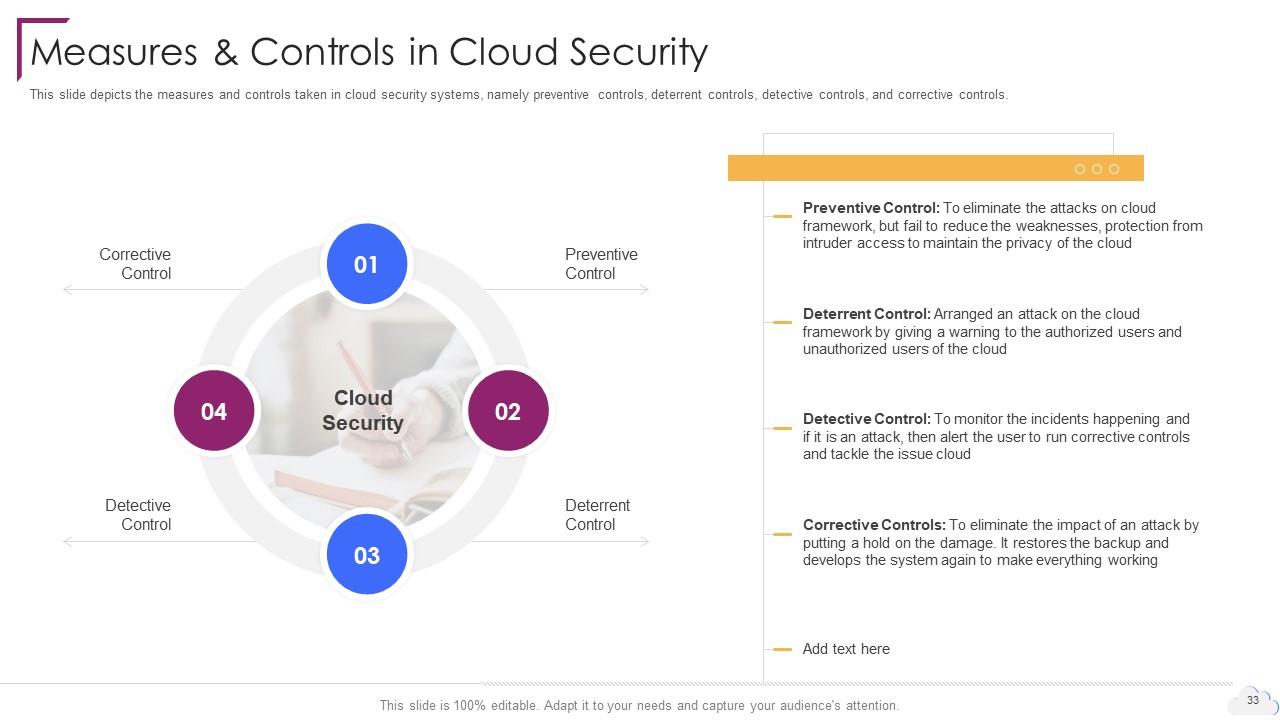
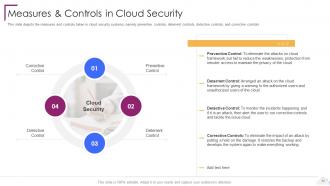
Slide 33: This slide depicts the measures and controls taken in cloud security systems.
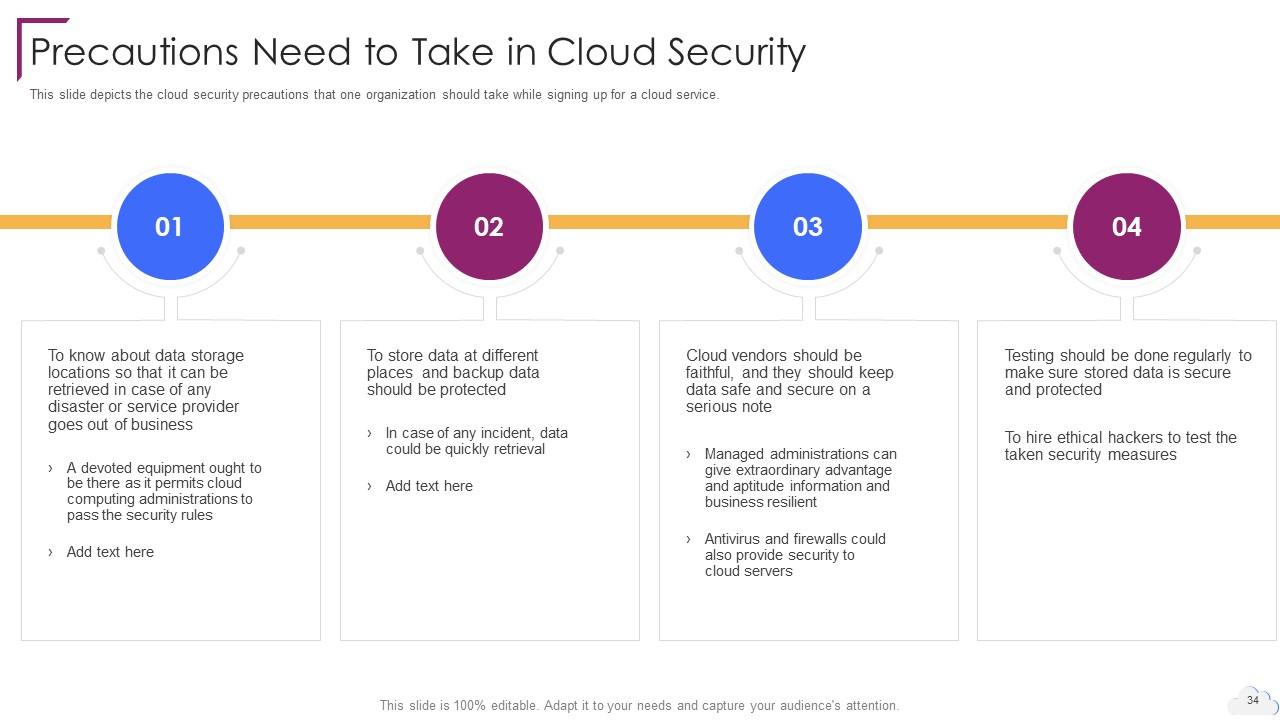
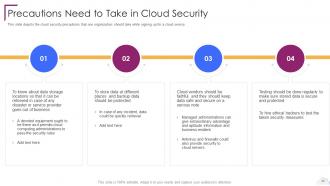
Slide 34: This slide shows Precautions Need to Take in Cloud Security.
Slide 35: This slide highlights title for topics that are to be covered next in the template.
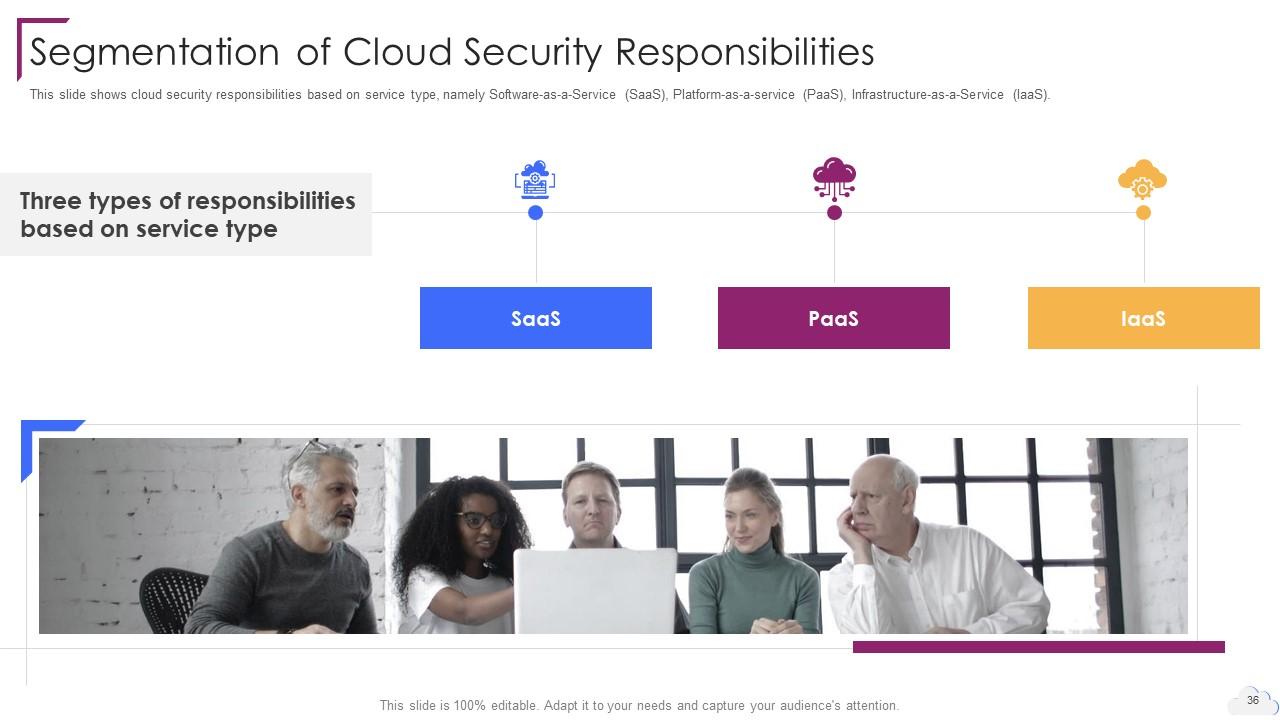
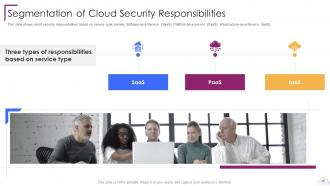
Slide 36: This slide presents Segmentation of Cloud Security Responsibilities.
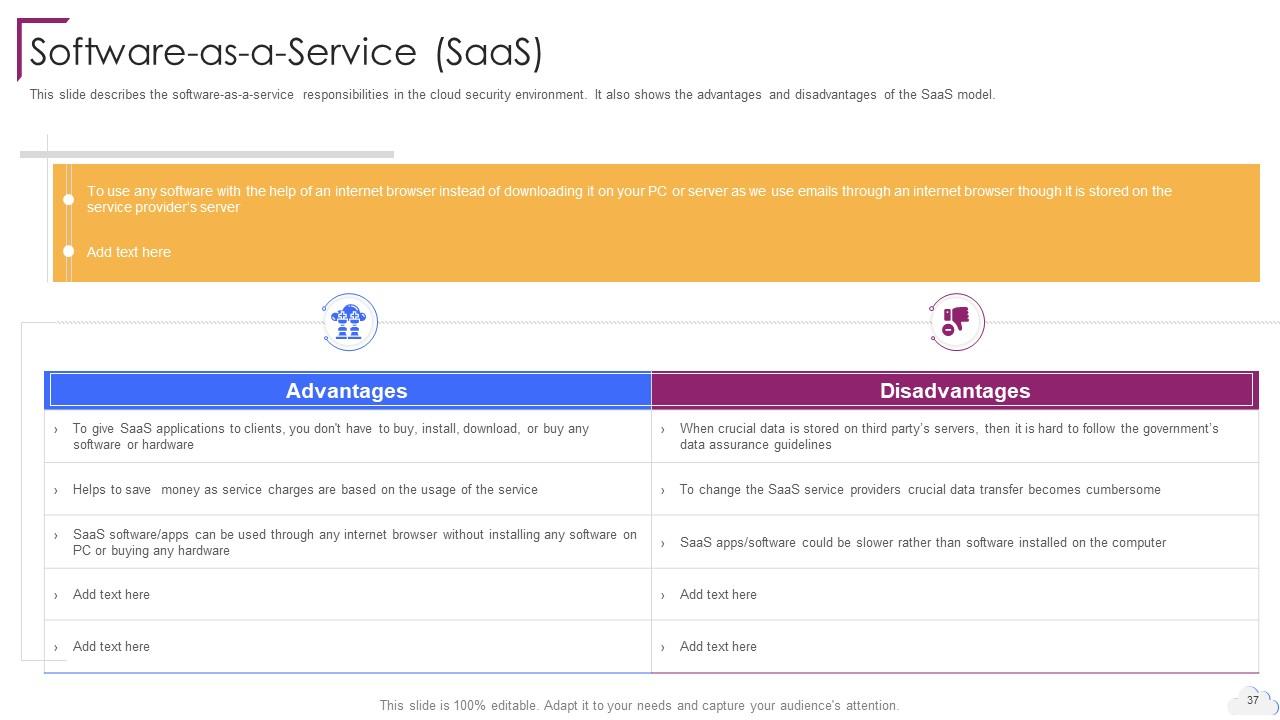
Slide 37: This slide describes the software-as-a-service responsibilities in the cloud security environment.
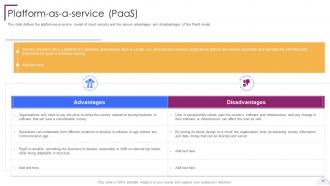
Slide 38: This slide defines the platform-as-a-service model of cloud security.
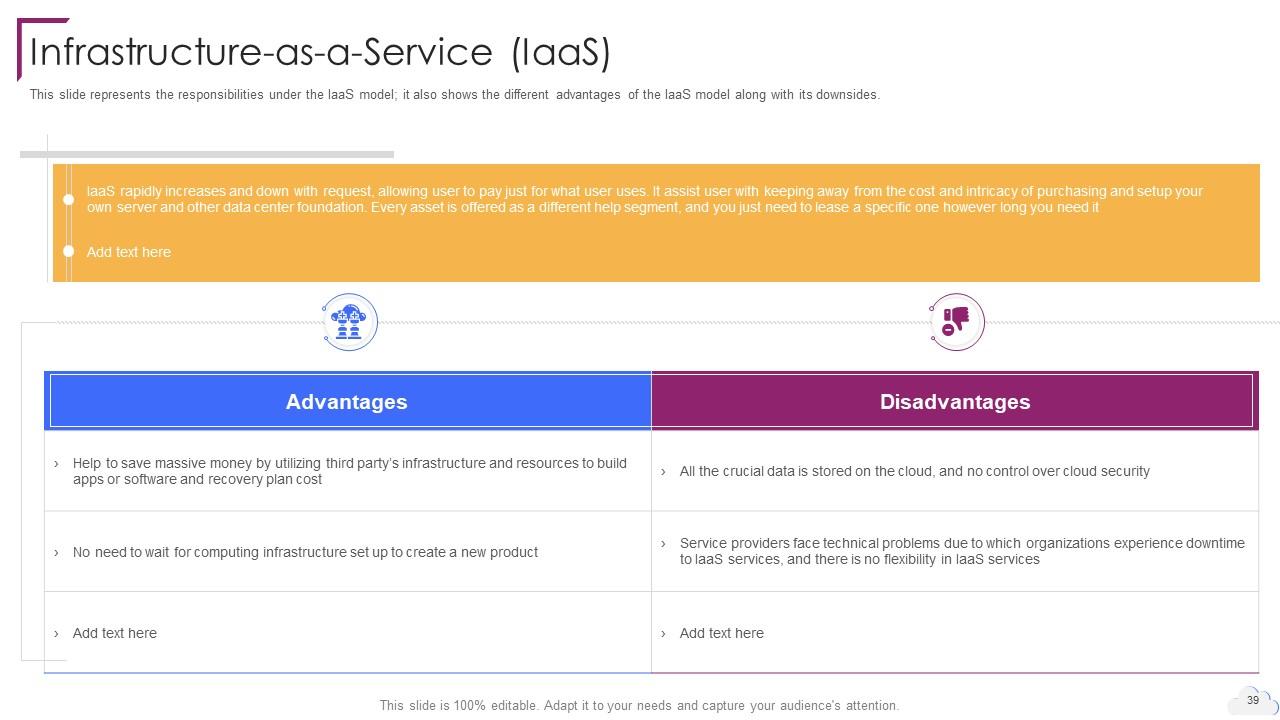
Slide 39: This slide represents the responsibilities under the IaaS model.
Slide 40: This slide highlights title for topics that are to be covered next in the template.
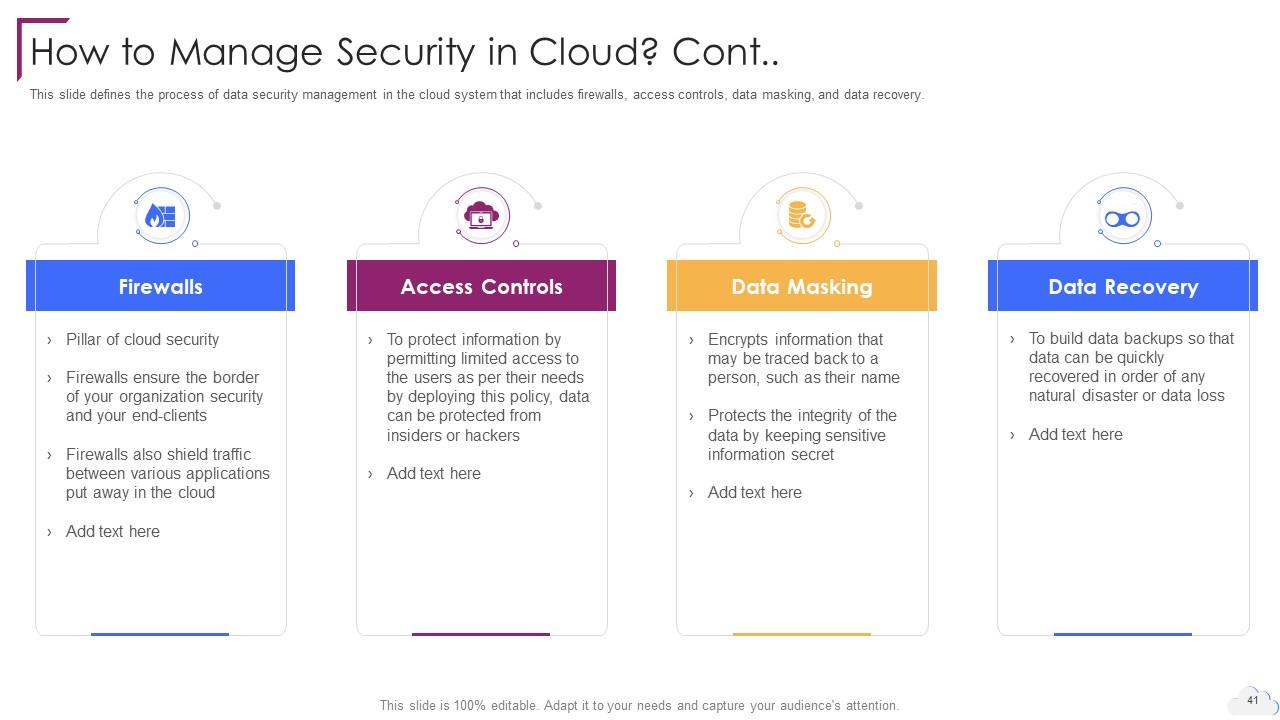
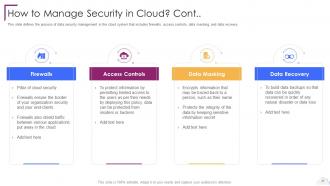
Slide 41: This slide defines the process of data security management in the cloud system.
Slide 42: This slide represents how data is managed in a cloud security system.
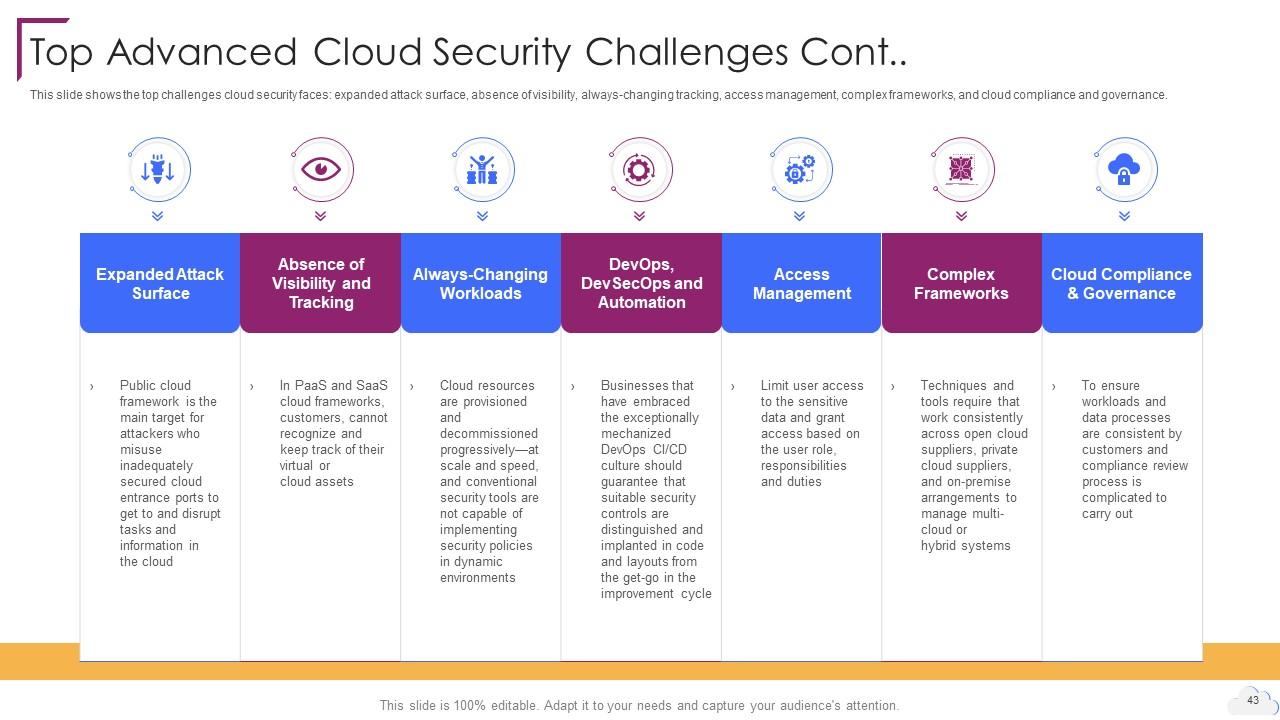
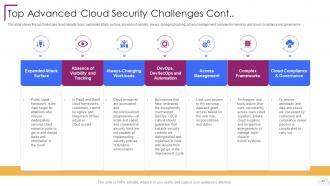
Slide 43: This slide shows the top challenges cloud security faces.
Slide 44: This slide describes the critical challenges in the cloud security system.
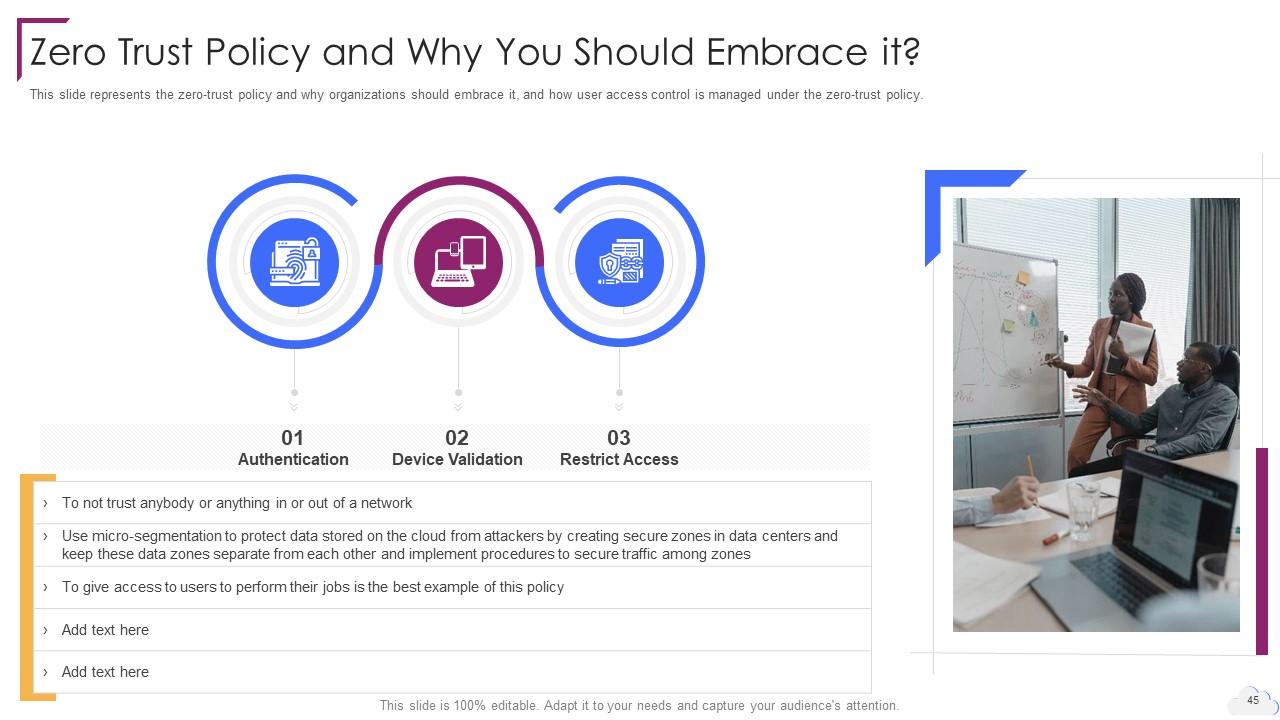
Slide 45: This slide represents the zero-trust policy and why organizations should embrace it.
Slide 46: This slide highlights title for topics that are to be covered next in the template.
Slide 47: This slide represents the cloud security solutions.
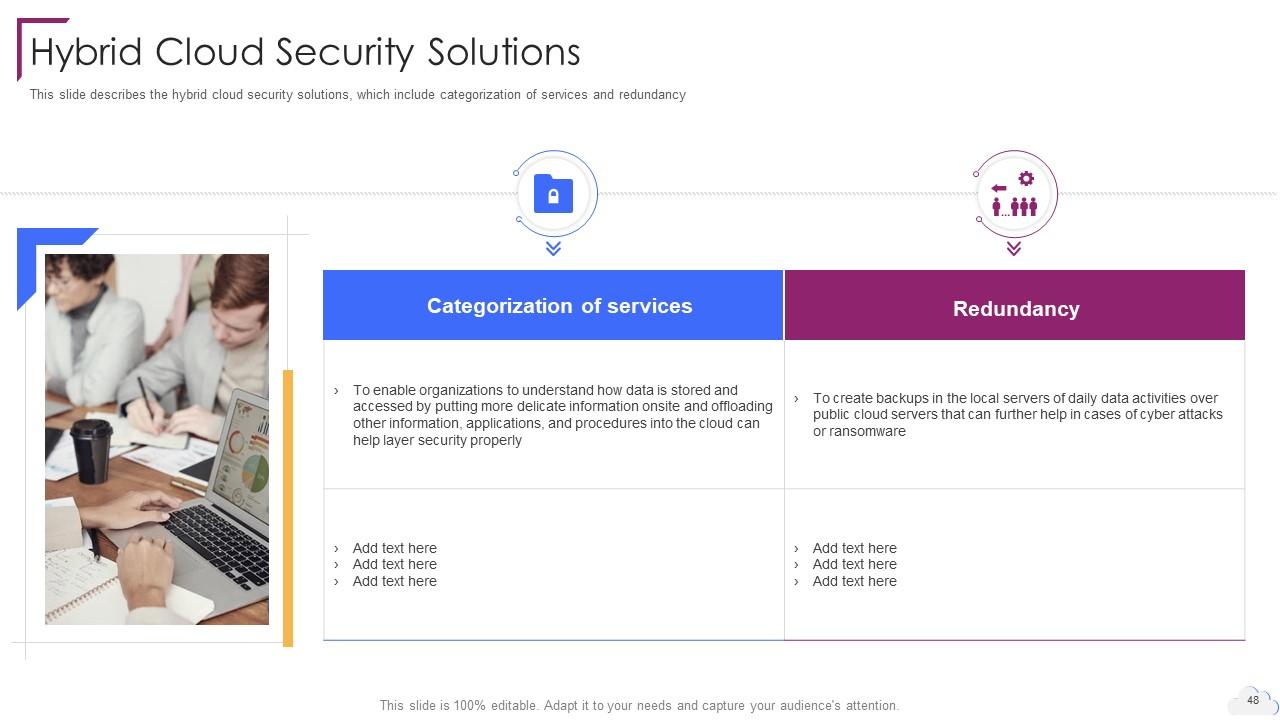
Slide 48: This slide describes the hybrid cloud security solutions.
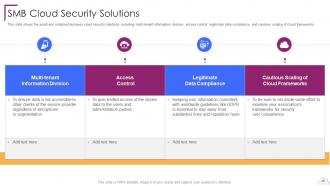
Slide 49: This slide shows the small and midsized business cloud security solutions.
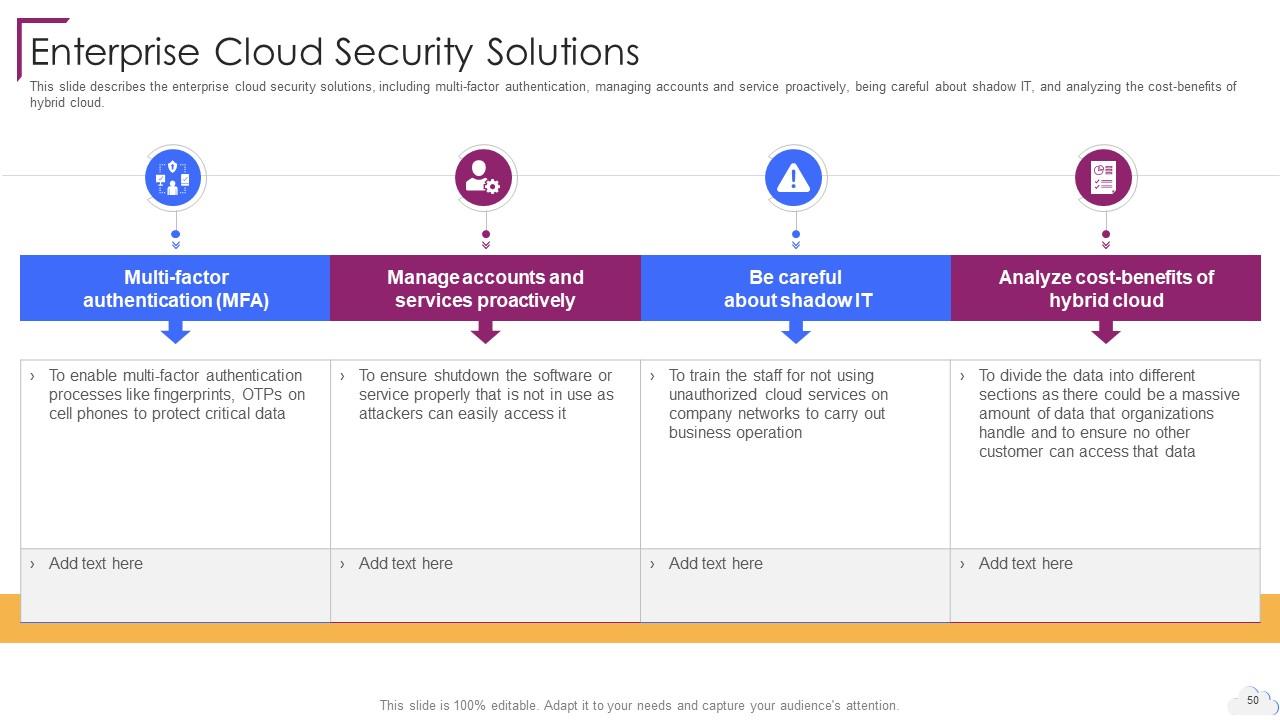
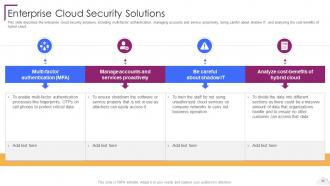
Slide 50: This slide describes the enterprise cloud security solutions.
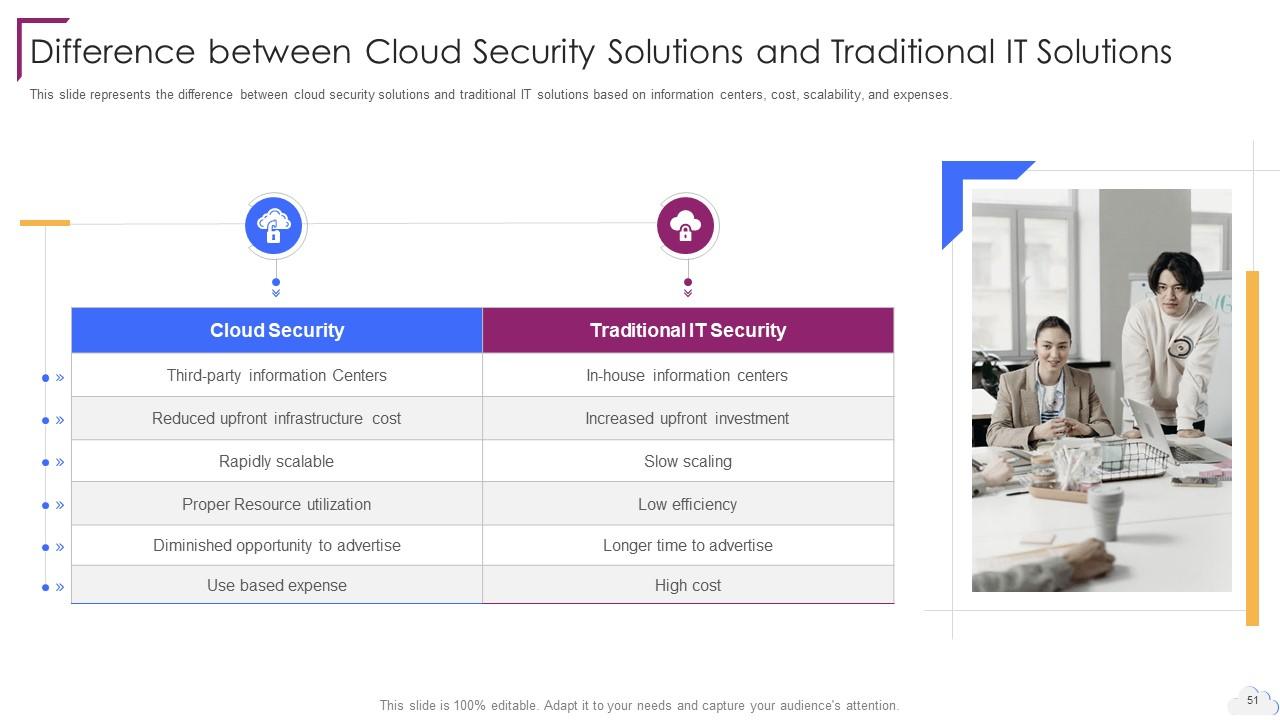
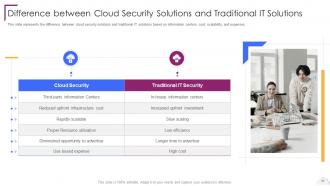
Slide 51: This slide presents Difference between Cloud Security Solutions and Traditional IT Solutions.
Slide 52: This slide highlights title for topics that are to be covered next in the template.
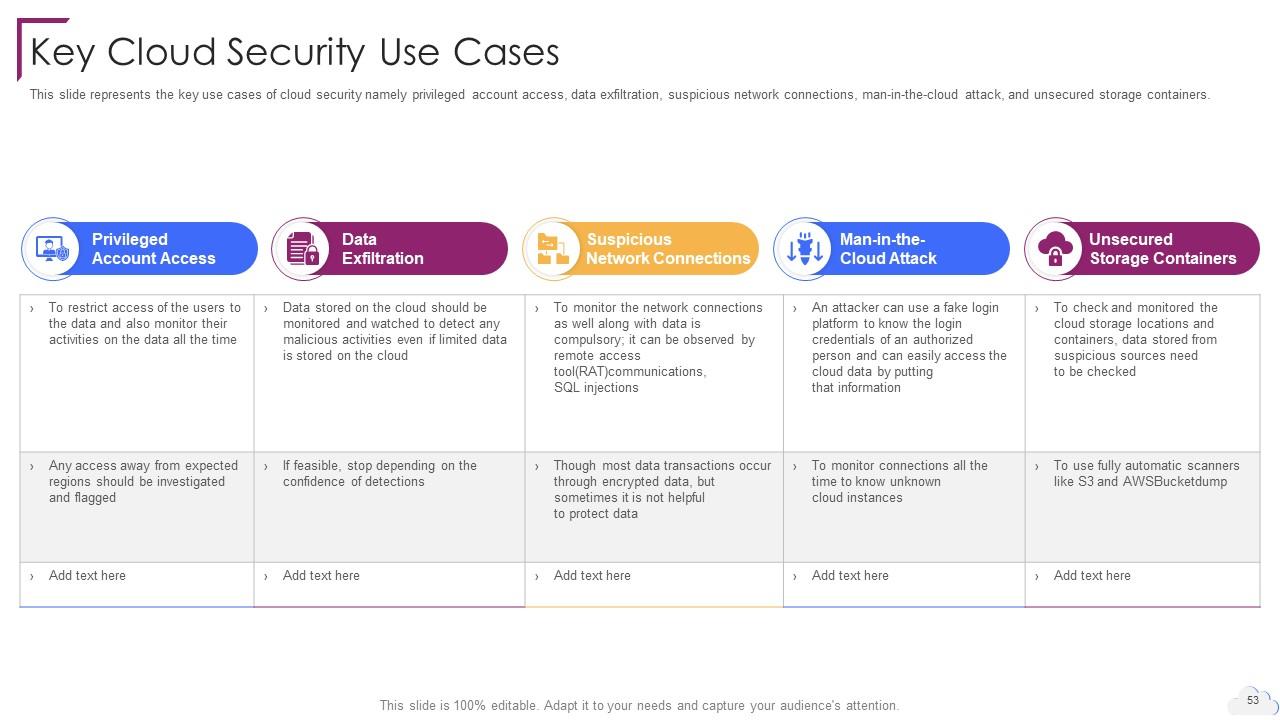
Slide 53: This slide represents the key use cases of cloud security.
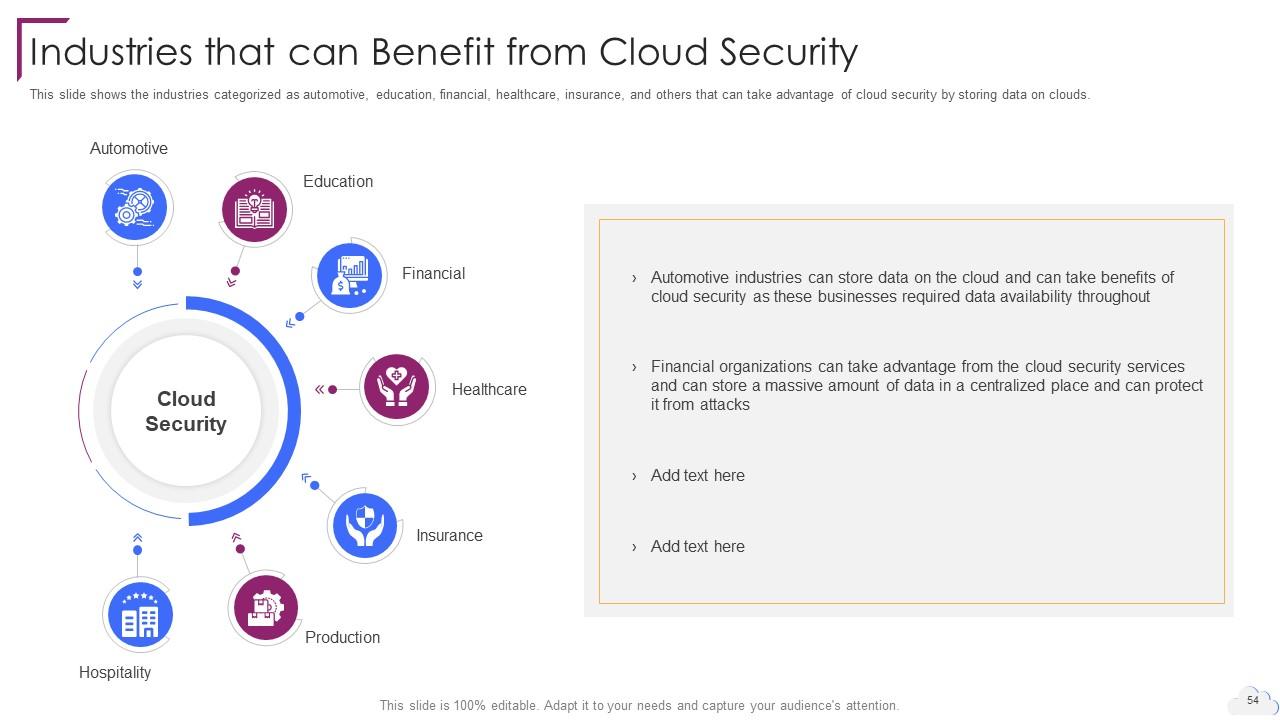
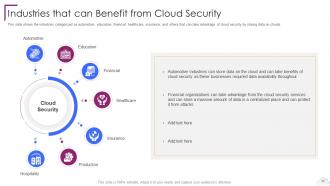
Slide 54: This slide showcases Industries that can Benefit from Cloud Security.
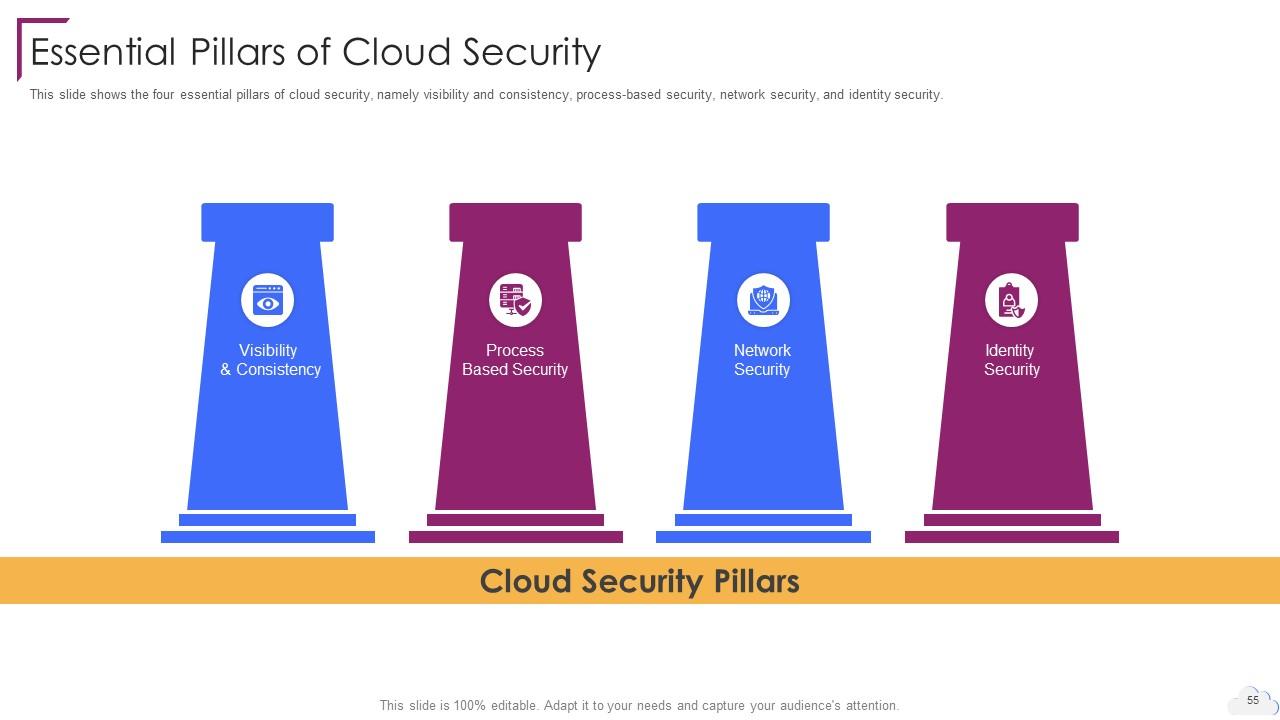
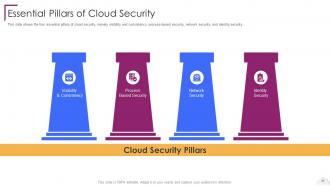
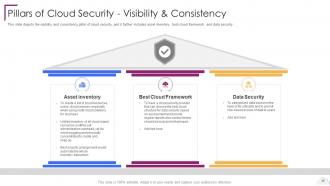
Slide 55: This slide shows the four essential pillars of cloud security, namely visibility and consistency.
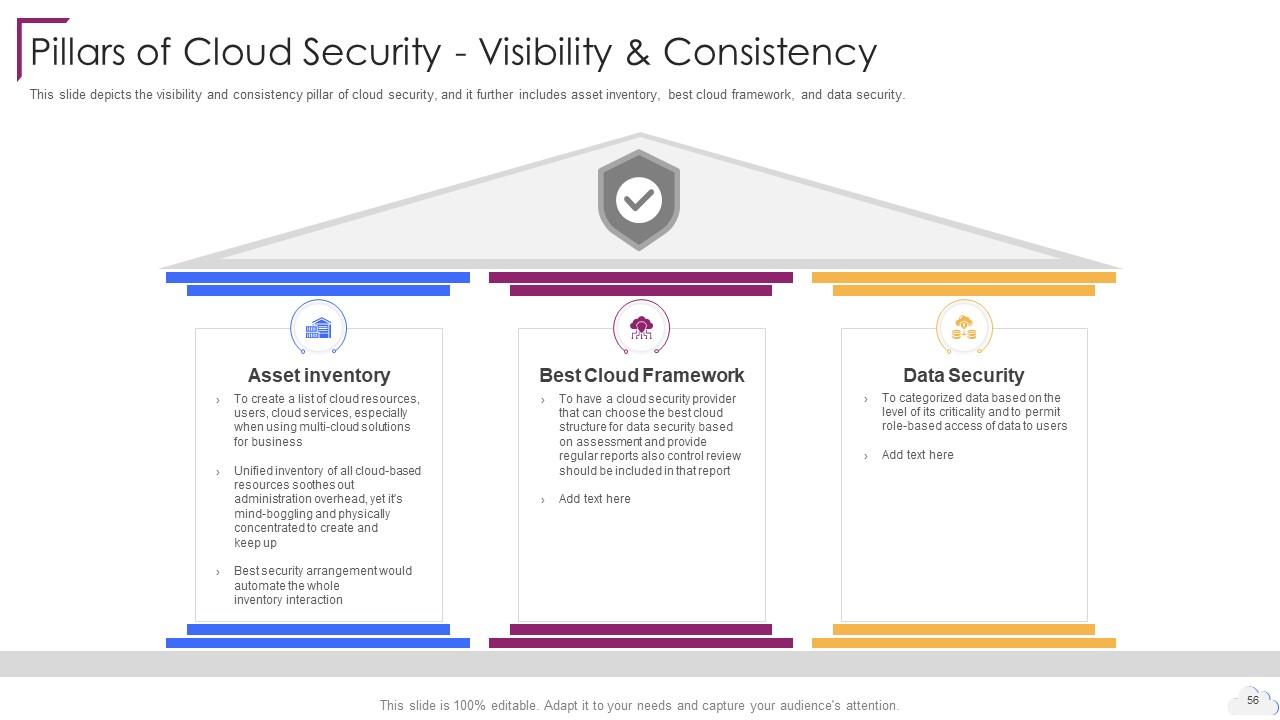
Slide 56: This slide depicts the visibility and consistency pillar of cloud security.
Slide 57: This slide represents the process-based security pillar of cloud security.
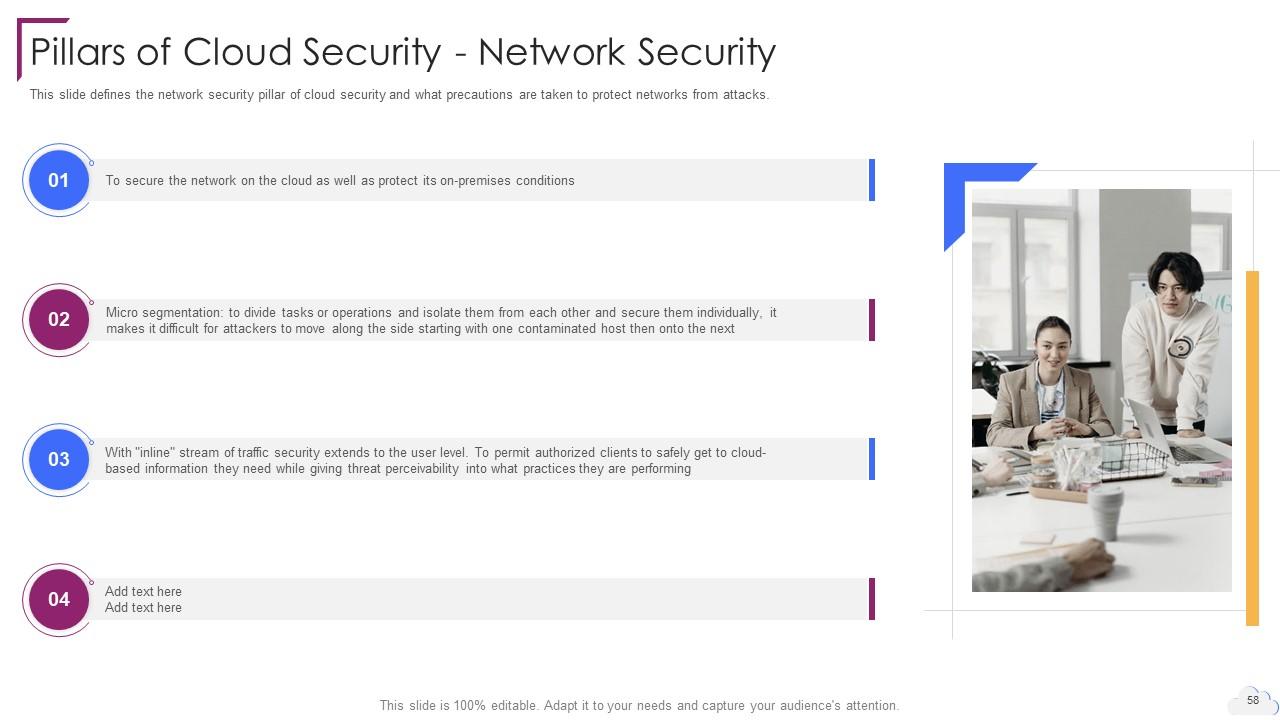
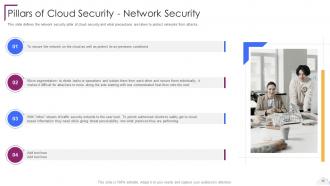
Slide 58: This slide defines the network security pillar of cloud security.
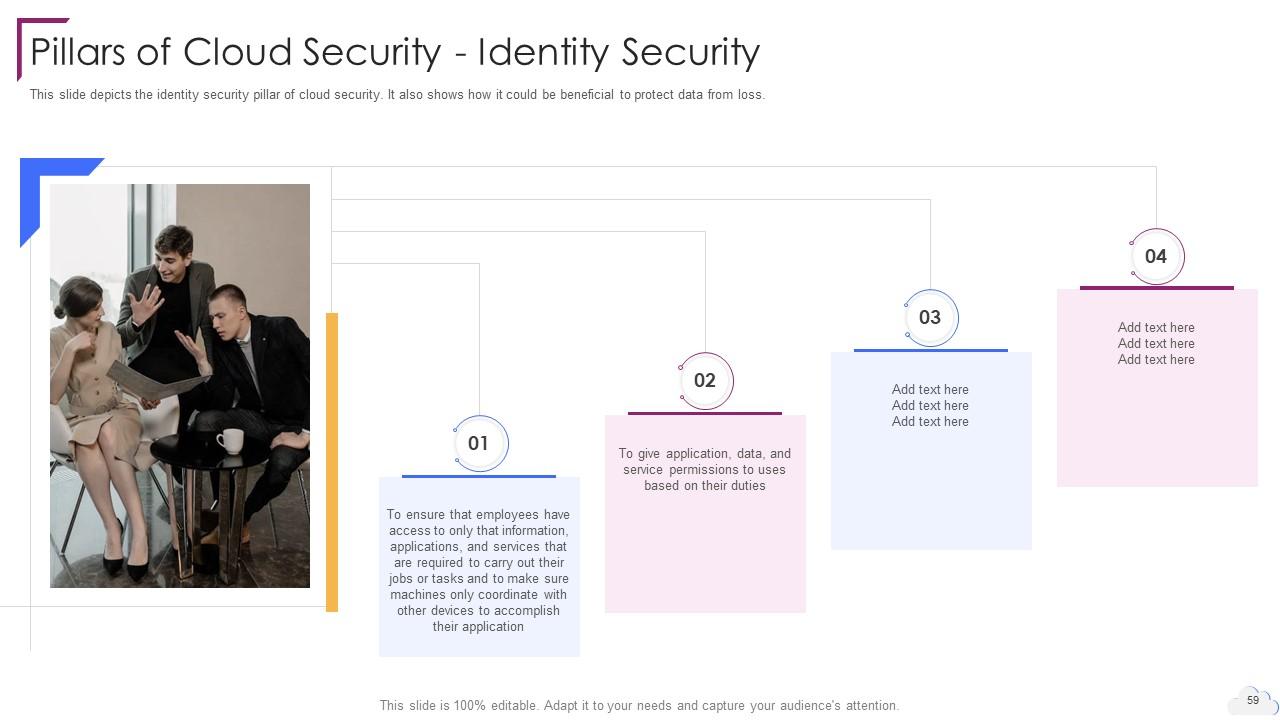
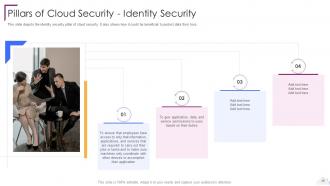
Slide 59: This slide depicts the identity security pillar of cloud security.
Slide 60: This slide highlights title for topics that are to be covered next in the template.
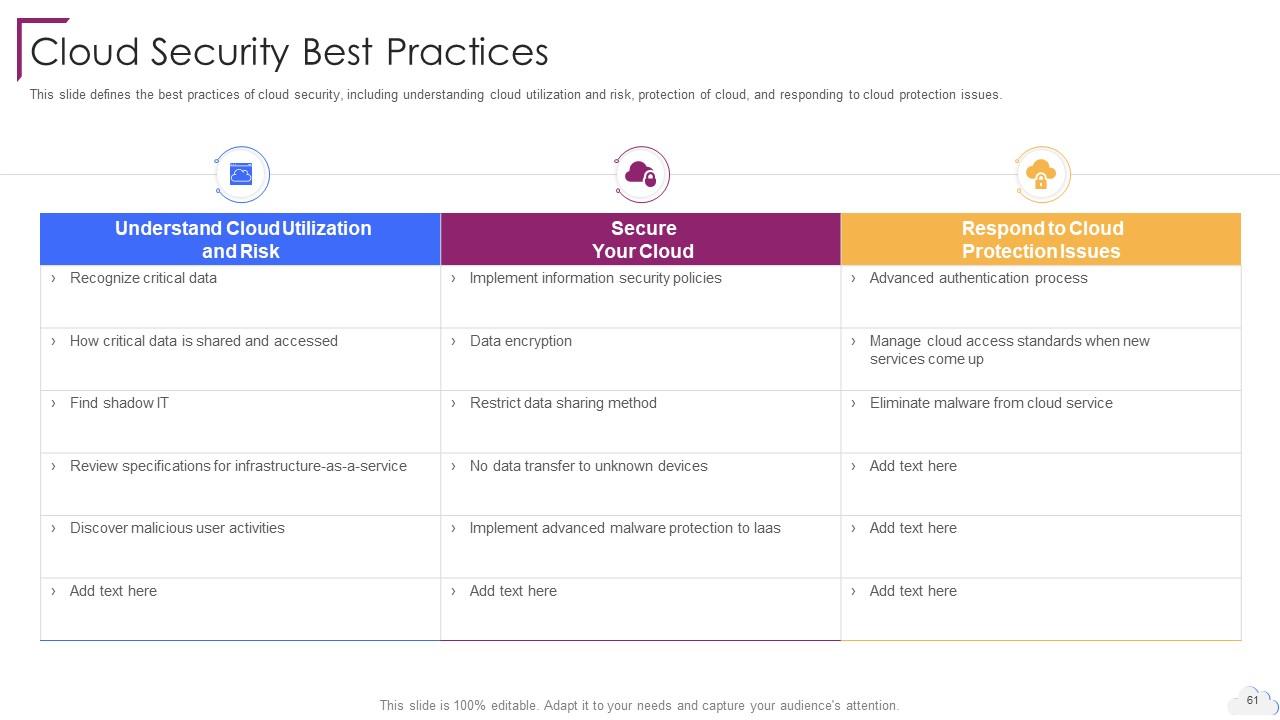
Slide 61: This slide defines the best practices of cloud security.
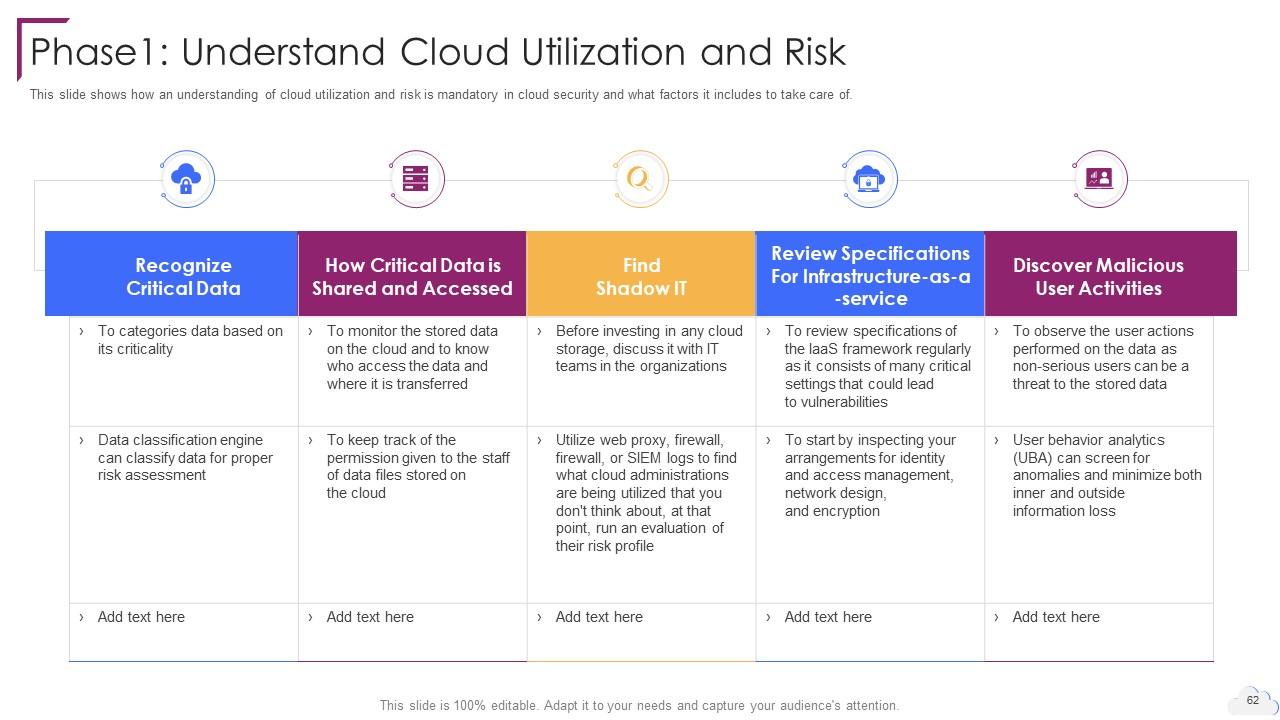
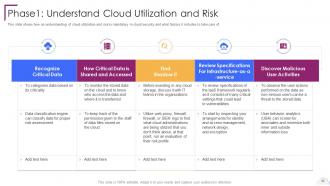
Slide 62: This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security.
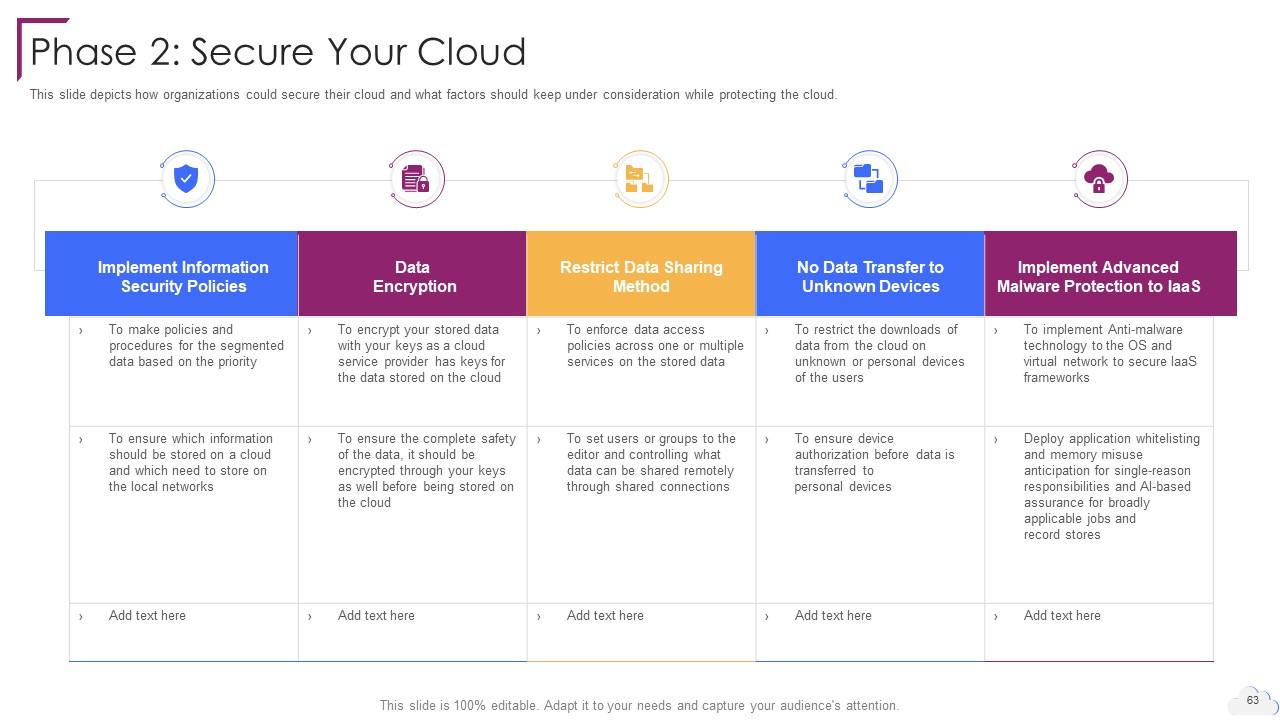
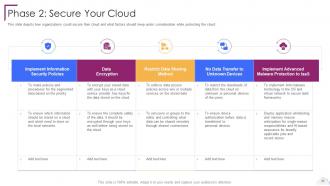
Slide 63: This slide depicts how organizations could secure their cloud.
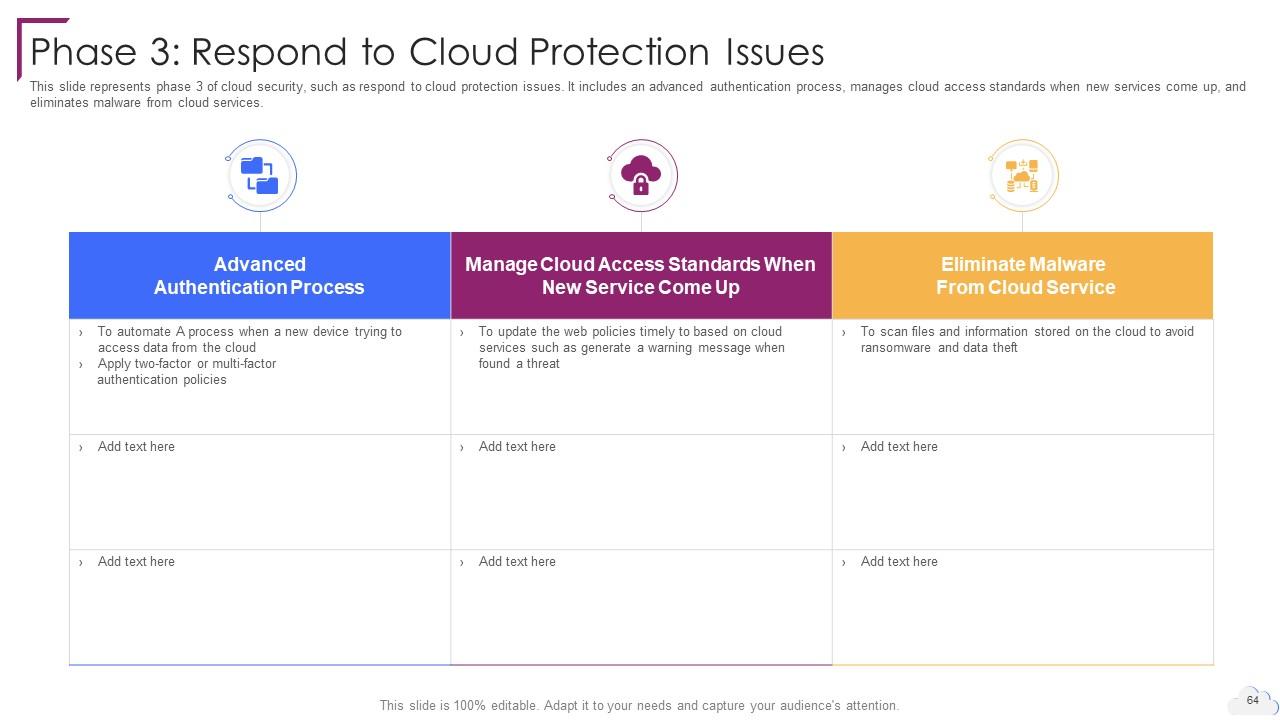
Slide 64: This slide represents phase 3 of cloud security, such as respond to cloud protection issues.
Slide 65: This slide highlights title for topics that are to be covered next in the template.
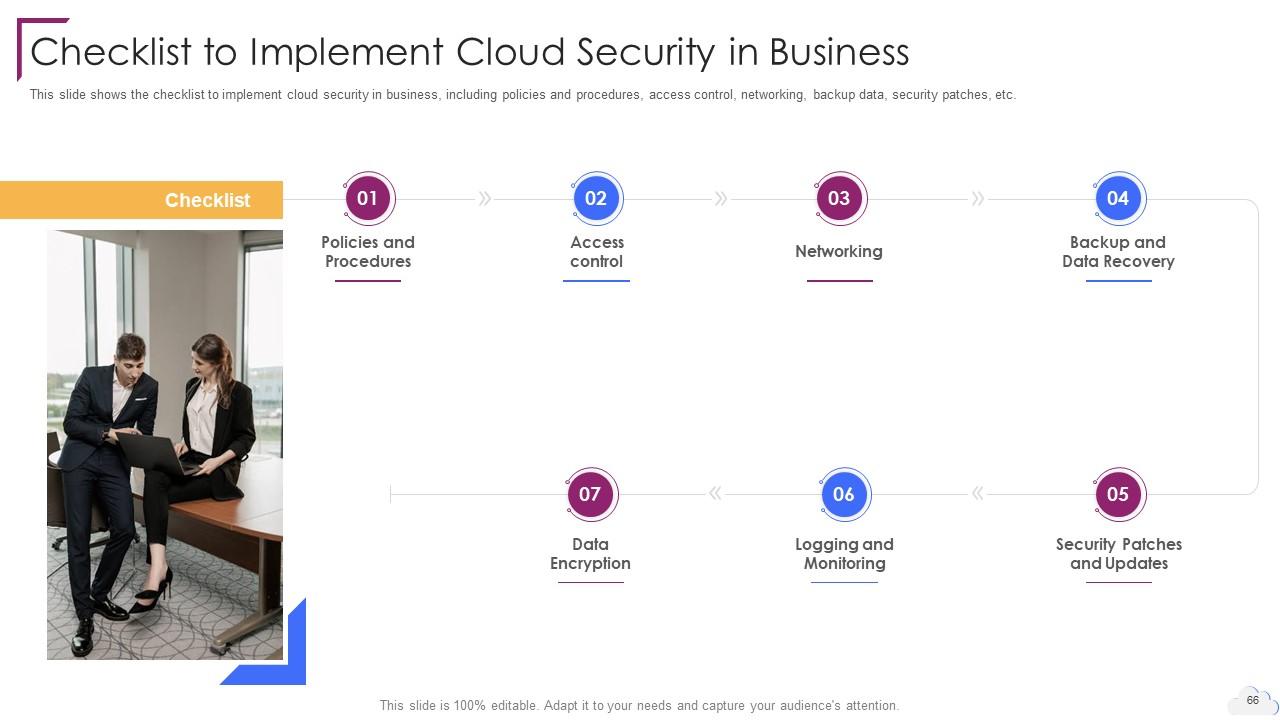
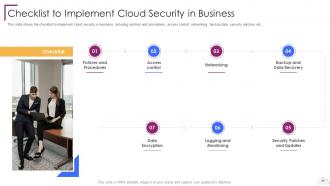
Slide 66: This slide shows Checklist to Implement Cloud Security in Business.
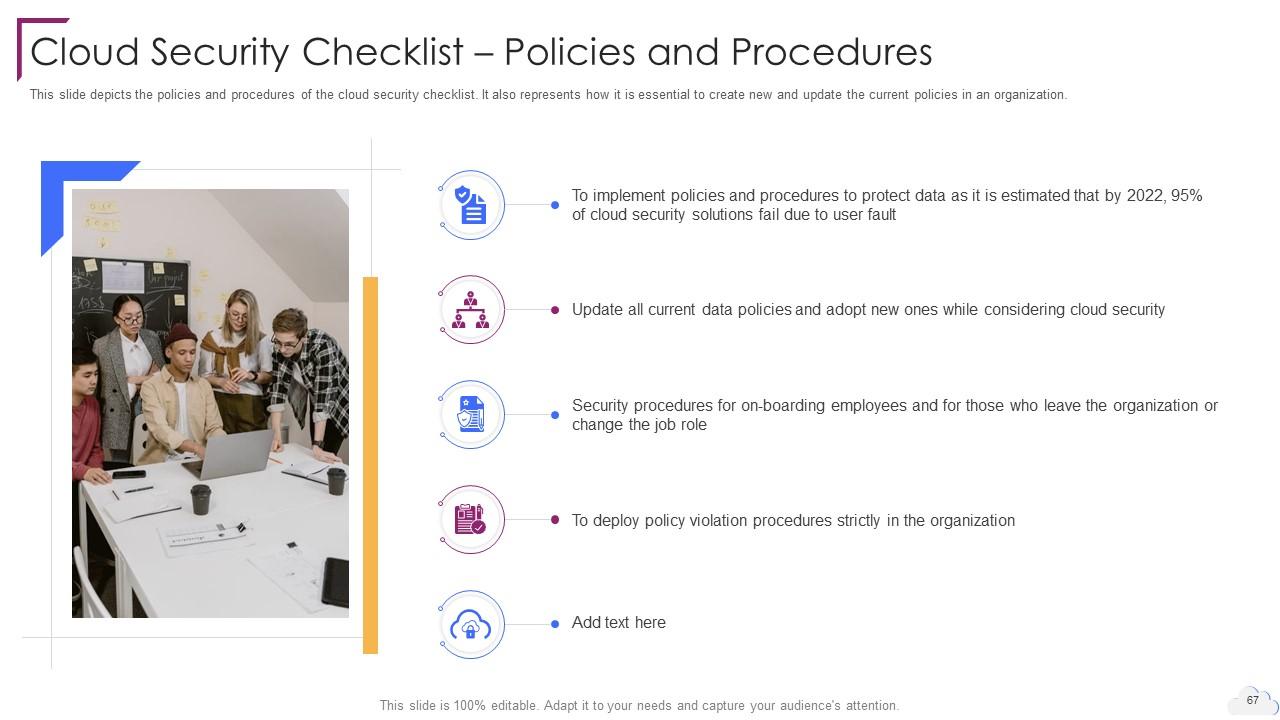
Slide 67: This slide depicts the policies and procedures of the cloud security checklist.
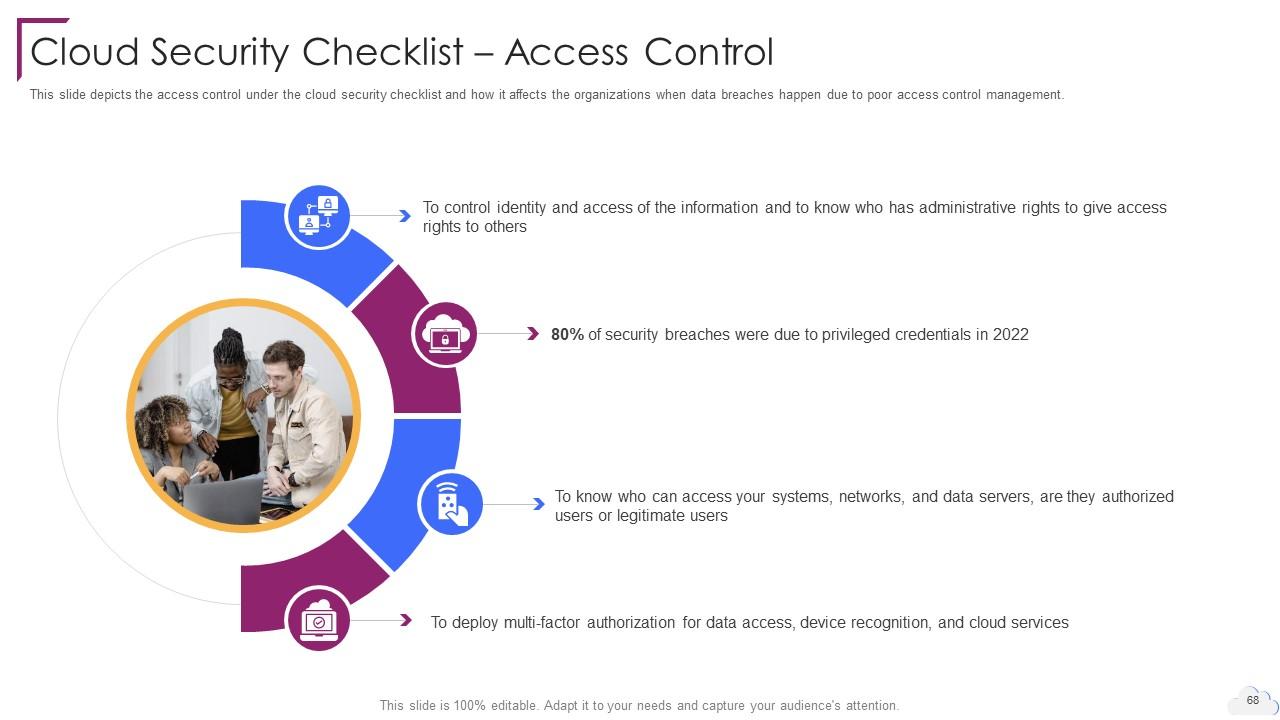
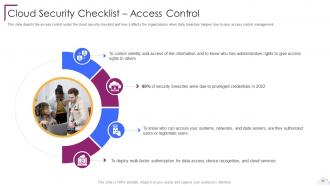
Slide 68: This slide depicts the access control under the cloud security checklist.
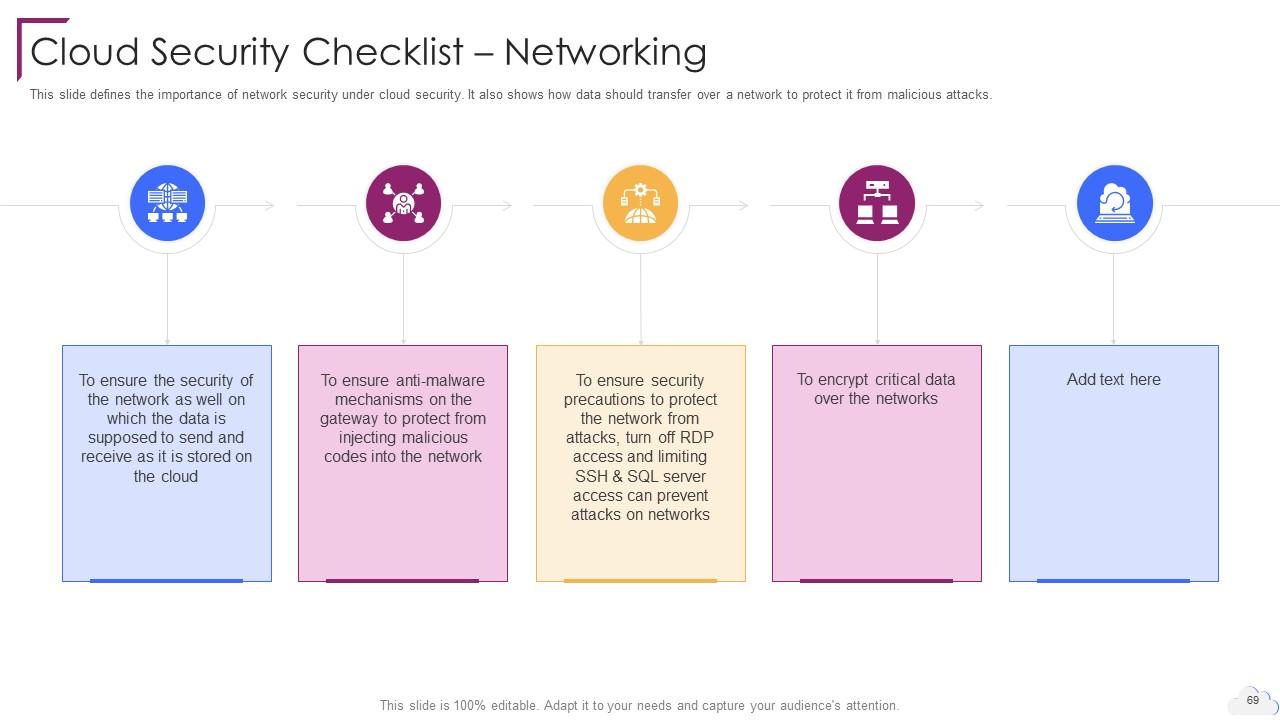
Slide 69: This slide defines the importance of network security under cloud security.
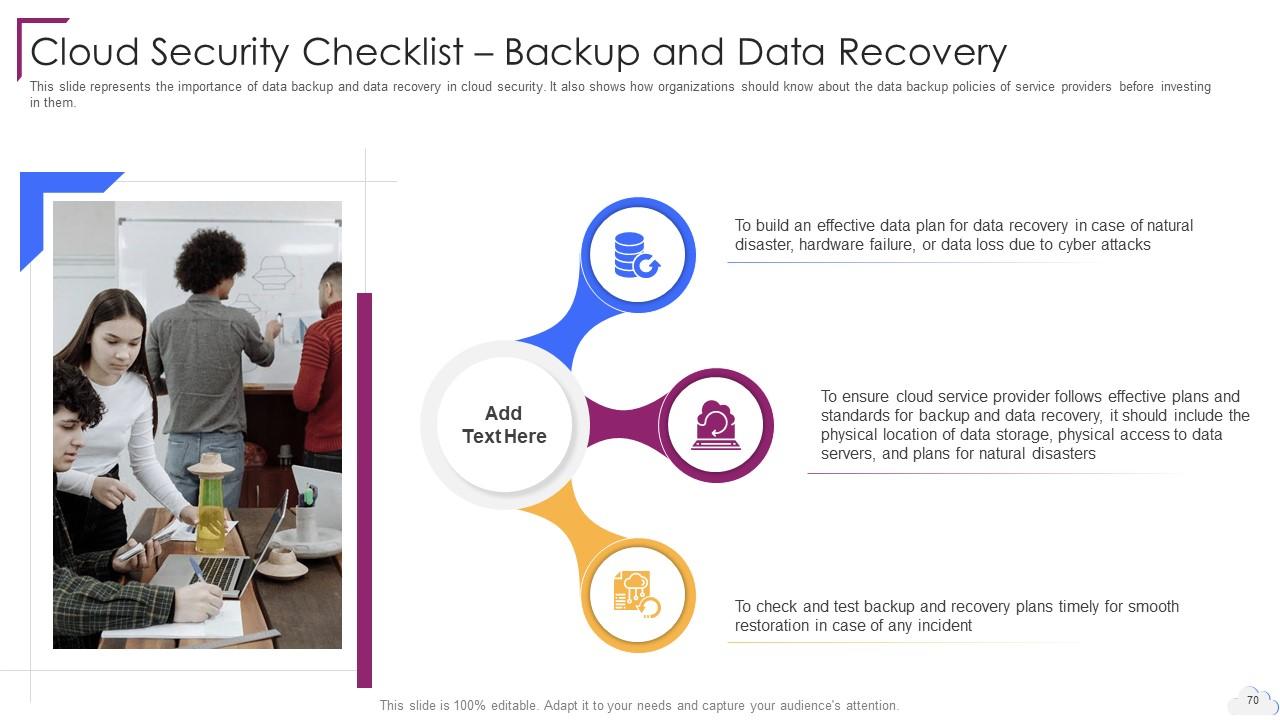
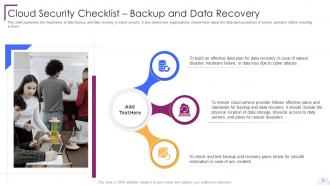
Slide 70: This slide represents the importance of data backup and data recovery in cloud security.
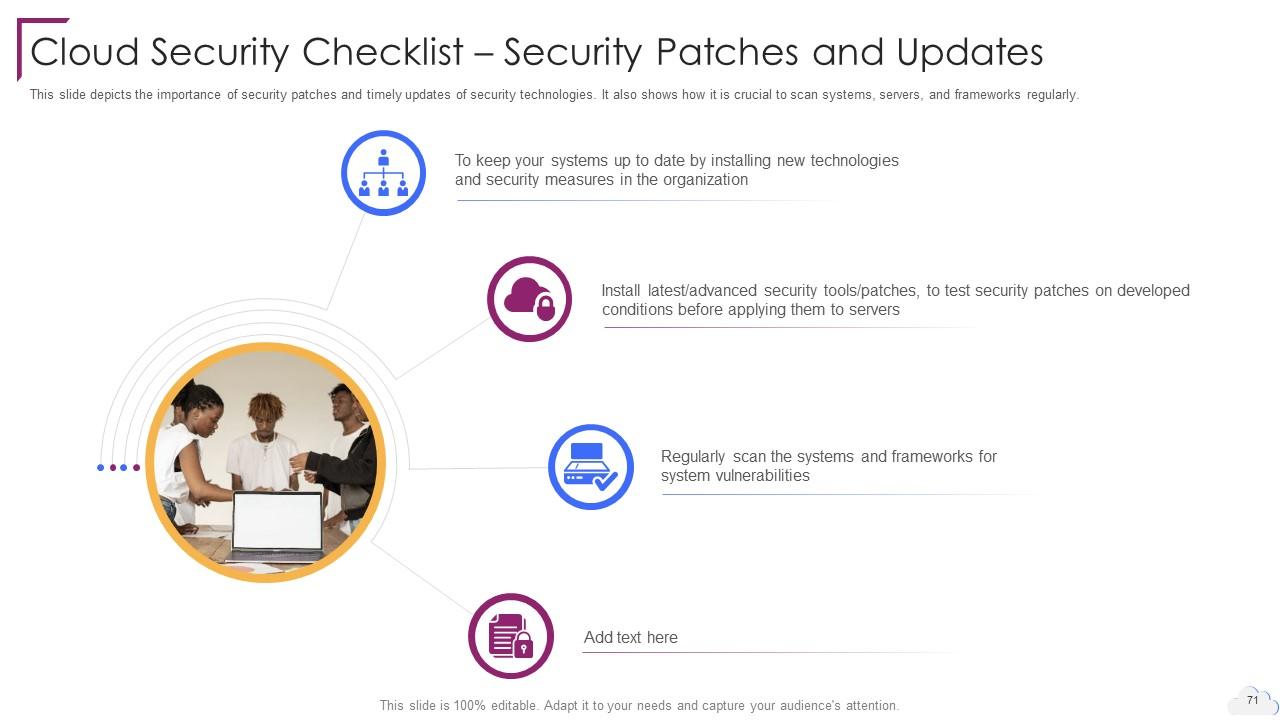
Slide 71: This slide depicts the importance of security patches and timely updates of security technologies.
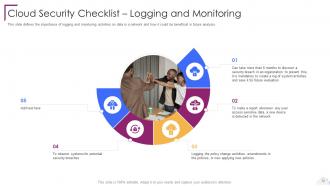
Slide 72: This slide defines the importance of logging and monitoring activities on data in a network.
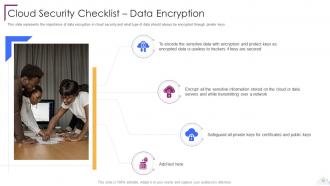
Slide 73: This slide represents the importance of data encryption in cloud security.
Slide 74: This slide highlights title for topics that are to be covered next in the template.
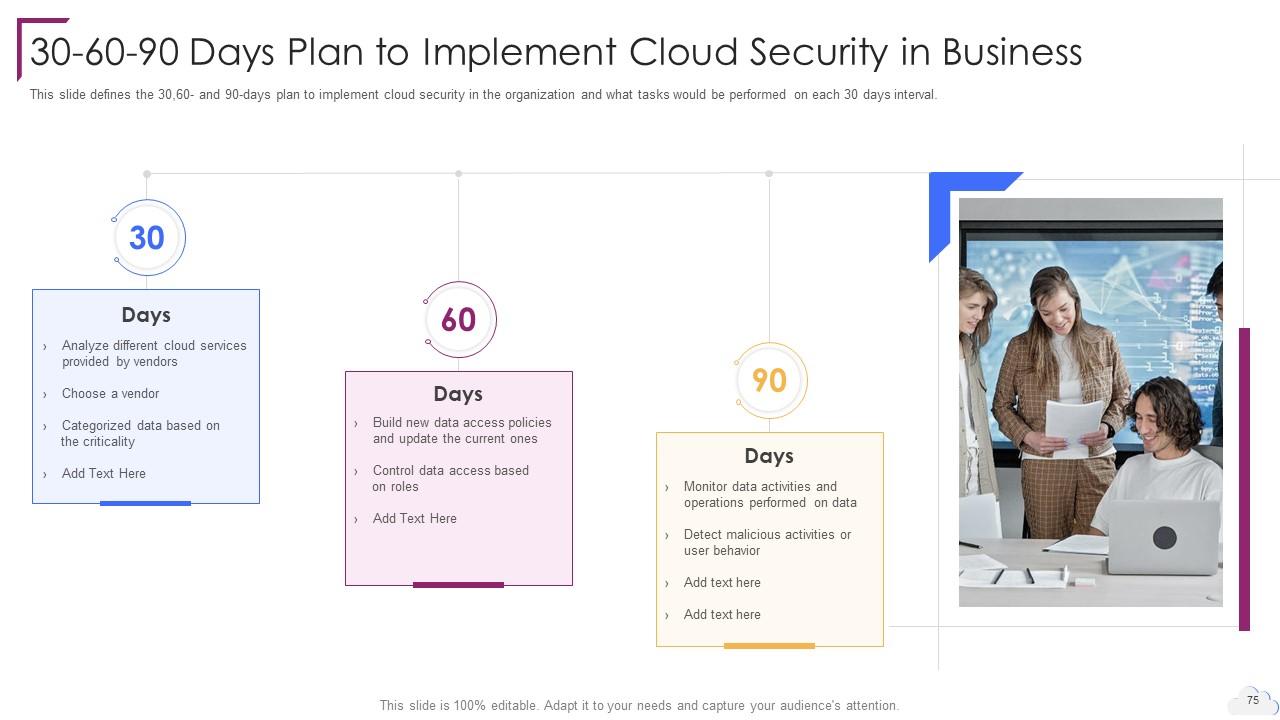
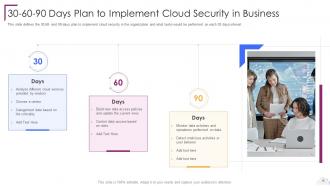
Slide 75: This slide showcases 30-60-90 Days Plan to Implement Cloud Security in Business.
Slide 76: This slide highlights title for topics that are to be covered next in the template.
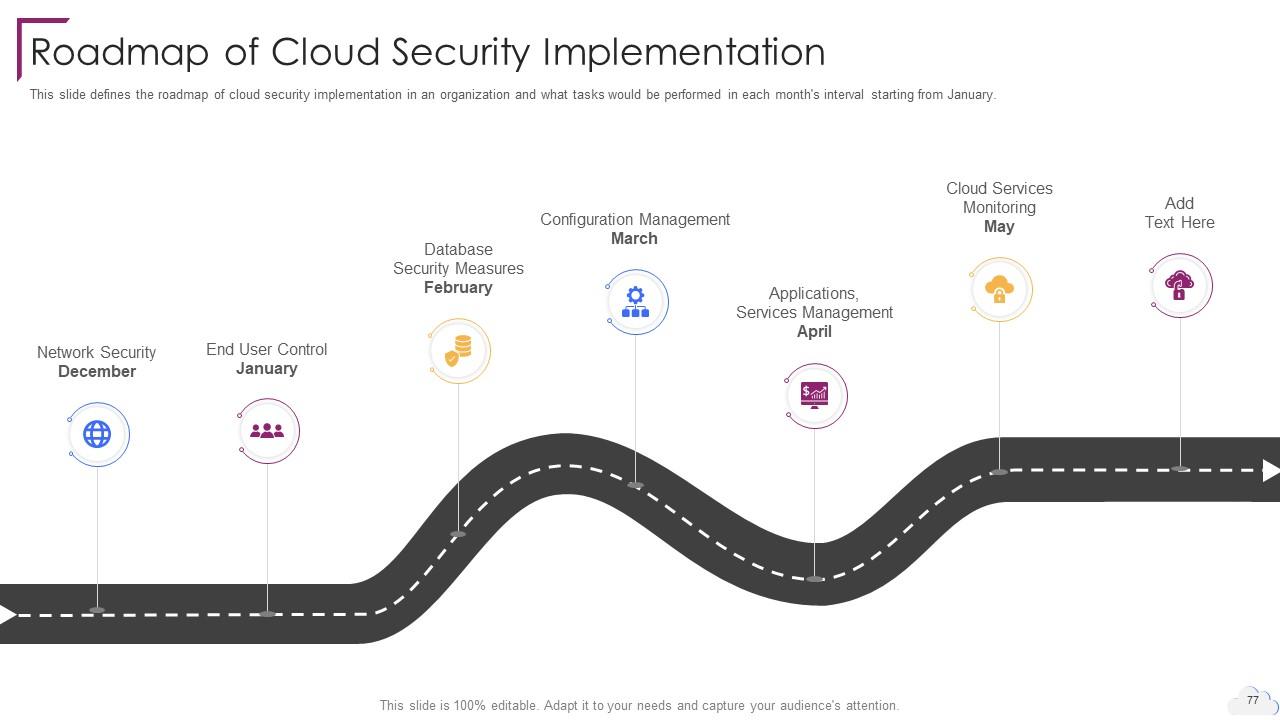
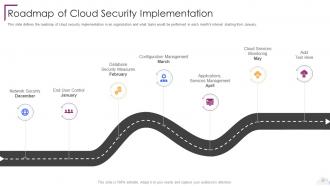
Slide 77: This slide shows Roadmap of Cloud Security Implementation.
Slide 78: This slide displays Icons for Cloud Computing Security.
Slide 79: This slide is titled as Additional Slides for moving forward.
Slide 80: This is Our Mission slide with related imagery and text.
Slide 81: This is About Us slide to show company specifications etc.
Slide 82: This is Our Team slide with names and designation.
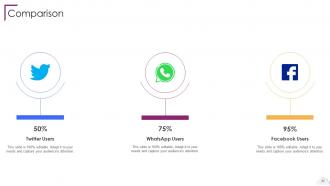
Slide 83: This is a Comparison slide to state comparison between commodities, entities etc.
Slide 84: This is a Timeline slide. Show data related to time intervals here.
Slide 85: This slide depicts Venn diagram with text boxes.
Slide 86: This slide provides 30 60 90 Days Plan with text boxes.
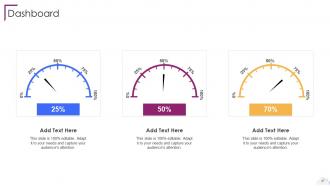
Slide 87: This slide represents Dashboard with additional text boxes to show information.
Slide 88: This is a Thank You slide with address, contact numbers and email address.
Cloud Computing Security Powerpoint Presentation Slides with all 93 slides:
Use our Cloud Computing Security Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
FAQs
Cloud security is essential due to data centralization, cost-effectiveness, and reduced control. By protecting cloud-based data and systems, organizations can maintain confidentiality, integrity, and availability of their information, which is vital to their operations and reputation.
The benefits of a cloud security system include increased data protection, improved compliance with regulatory requirements, better risk management, and reduced costs associated with traditional IT security solutions.
Some of the main threats to cloud security include data loss, malware attacks, contract breaches, compliance violations, and end-user threats. Organizations need to implement measures and controls to mitigate these risks and protect their cloud-based systems and data.
There are several types of cloud security solutions, including hybrid cloud security solutions, small and mid-sized business cloud security solutions, and enterprise cloud security solutions. Each of these solutions is tailored to the specific needs and requirements of the organization.
Best practices for cloud security include understanding cloud utilization and risk, securing the cloud with appropriate controls and measures, and responding to cloud protection issues. Organizations should also have policies and procedures, access controls, network security measures, data backup and recovery plans, and logging and monitoring activities in place to ensure effective cloud security.
-
I can say with full confidence that all your business, academic, or professional work requirements will be sufficed with SlideTeam. Their gallery is as rich as 2Million+!!
-
Graphics are very appealing to eyes.