Ack Tee Introduction And Version 1 0 Confidential Computing It Ppt Slides Diagrams
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Deliver an outstanding presentation on the topic using this Ack Tee Introduction And Version 1 0 Confidential Computing It Ppt Slides Diagrams. Dispense information and present a thorough explanation of Goal, Confidential Computing, Cloud Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Description:
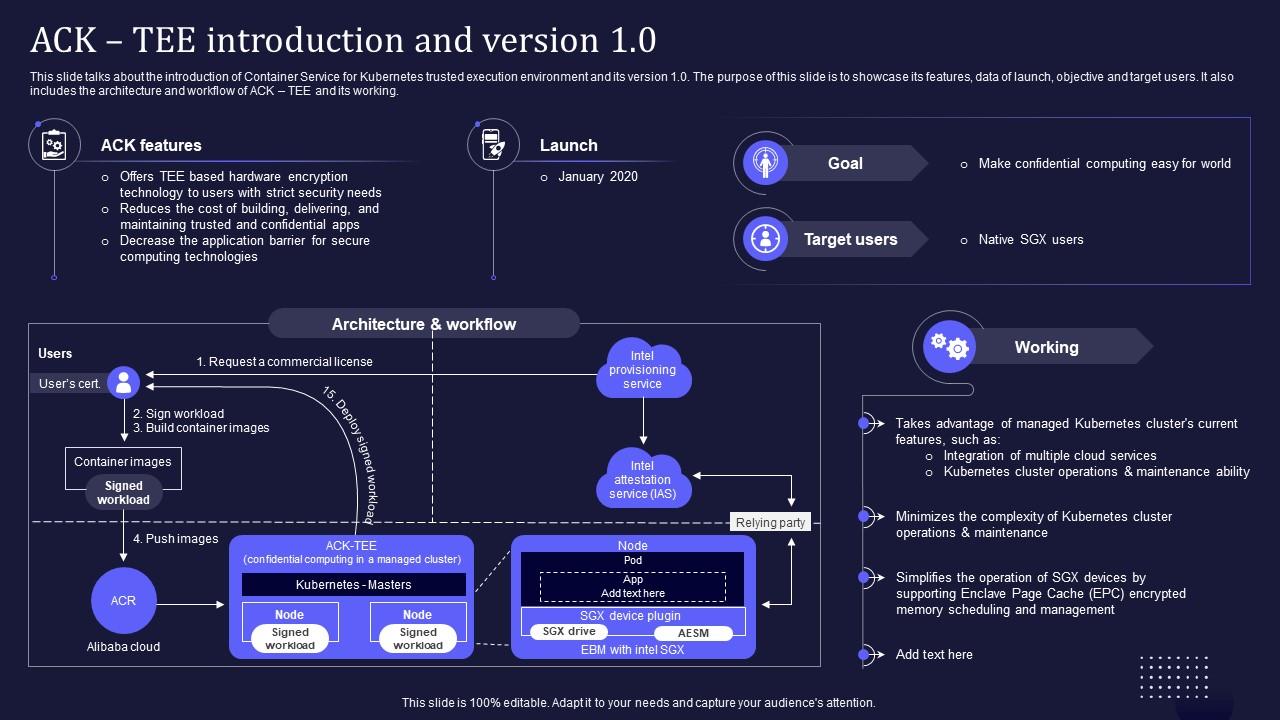
The image is a PowerPoint slide titled "ACK - TEE introduction and version 1.0," which introduces the Container Service for Kubernetes (ACK) trusted execution environment (TEE) and its first major version. The slide is designed to highlight the features, launch date, objectives, and target users of the service, as well as to explain its architecture and workflow.
Key points presented in the slide include:
1. ACK features:
Offers TEE based hardware encryption technology for users with strict security needs.
Reduces the cost of building, delivering, and maintaining trusted and confidential apps.
Decreases the application barrier for secure computing technologies.
2. Launch:
The service was launched in January 2020.
3. Goal:
The goal is to make confidential computing easy for the world.
4. Target users:
The primary users are native SGX users.
The slide also outlines the architecture and workflow of ACK - TEE:
1. Users must request a commercial license and have a user's certificate.
2. Users sign their workload and build container images.
3. The images are pushed to the Alibaba cloud ACR (Alibaba Cloud Container Registry).
The Kubernetes Masters node features signed workloads, which are part of the confidential computing in a managed cluster.
The working mechanism of ACK - TEE is detailed, highlighting:
1. It takes advantage of managed Kubernetes cluster's current features like cloud services integration and maintenance abilities.
2. It minimizes the complexity of Kubernetes cluster operations and maintenance.
3. It simplifies the operation of SGX devices by supporting Enclave Page Cache (EPC) encrypted memory scheduling and management.
The slide includes diagrams that represent the process flow and components, such as the Intel Provisioning Service and Intel Attestation Service (IAS), which are part of the TEE ecosystem.
The SGX device plugin, EBM with Intel SGX, and AESM are also mentioned, indicating the involvement of Intel's Software Guard Extensions (SGX) technology in creating a secure computing environment.
Use Cases:
This slide is ideal for industries that require stringent data security measures and utilize containerization for their applications and services.
1. Cloud Computing:
Use: Secure cloud service deployments.
Presenter: Cloud Solutions Architect.
Audience: IT Security Teams and Cloud Service Customers.
2. Financial Services:
Use: Protection of financial data in Kubernetes environments.
Presenter: FinTech Security Specialist.
Audience: Compliance Officers and IT Professionals.
3. Healthcare:
Use: Ensuring patient data confidentiality in applications.
Presenter: Health Informatics Manager.
Audience: Healthcare IT Staff and Data Protection Officers.
4. E-commerce:
Use: Safeguarding customer transactions and data.
Presenter: E-commerce Platform Developer.
Audience: Site Reliability Engineers and Data Security Analysts.
5. Government:
Use: Securing sensitive government digital services.
Presenter: Cybersecurity Policy Advisor.
Audience: Government IT Departments and Contractors.
6. Telecommunications:
Use: Protecting infrastructure for customer data privacy.
Presenter: Network Security Engineer.
Audience: Network Operations and Compliance Teams.
7. Automotive:
Use: Securing connected vehicle data systems.
Presenter: Automotive Systems Engineer.
Audience: Vehicle Telematics Designers and Privacy Officers.
Ack Tee Introduction And Version 1 0 Confidential Computing It Ppt Slides Diagrams with all 6 slides:
Use our Ack Tee Introduction And Version 1 0 Confidential Computing It Ppt Slides Diagrams to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
It saves your time and decrease your efforts in half.
-
Crisp and neat slides. Makes it fun and easier to curate presentations.