Application Security Approaches In Cybersecurity Training Ppt
These slides in detail cover the application security approaches design review, automated tooling, code review, black-box security audit, and coordinated vulnerability platform.
These slides in detail cover the application security approaches design review, automated tooling, code review, black-box s..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Application Security Approaches in Cybersecurity. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content and present it with confidence.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 2
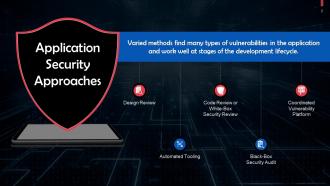
This slide highlights application security approaches. These are design review, automated tooling, code review, black-box security audit, and coordinated vulnerability platform.
Slide 3
This slide talks about design review as an application security approach. The application's architecture and design can be checked for security issues before writing the code.
Slide 4
This slide discusses Automated Tooling as an application security approach. Many security tools can be automated by incorporating them into the development or testing procedure.
Slide 5
This slide talks about Code Review or White-Box Security Review as an application security approach. A security engineer examines the application with a manual inspection of the source code and searching for security flaws.
Slide 6
This slide discusses the Black-Box Security Audit as an application security approach. This test seeks to replicate a situation in which external attackers target and try to compromise your systems in the real world.
Slide 7
This slide discusses talks about Coordinated Vulnerability Platform as an application security approach. Many websites and software providers offer hacker-powered application security solutions via which individuals can be recognized and compensated for reporting flaws or bugs.
Slide 8
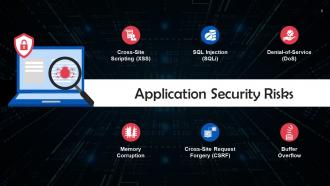
This slide lists application security risks. These are: Cross-Site Scripting (XSS), SQL injection, Denial-of-Service, memory corruption, cross-site request forgery, and buffer overflow.
Slide 9
This slide discusses cross-site scripting as a risk of application security. In Cross-Site Scripting attacks, malicious scripts are injected into benign and trustworthy websites. XSS attacks take place when an attacker sends malicious code, usually as a browser-side script, to a separate end-user using an online application.
Slide 10
This slide gives information about SQL Injection as a risk of application security. Hackers employ the SQL injection (SQLi) technique to exploit database vulnerabilities.
Slide 11
This slide talks about Denial-of-Service (DoS) as a risk of application security. Remote attackers may use DoS and Distributed Denial-of-Service (DDoS) attacks to bombard a targeted server or the infrastructure that supports it with false, non-genuine traffic.
Slide 12
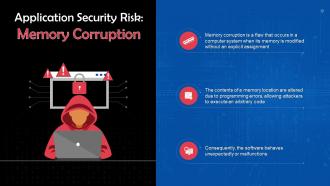
This slide discusses memory corruption as a risk of application security. Memory corruption is a flaw that occurs in a computer system when its memory is modified without an explicit assignment.
Slide 13
This slide talks about cross-site request forgery as a risk of application security. Hackers use Cross-Site Request Forgery (CSRF) to impersonate authorized users after tricking them into submitting an authorization request.
Slide 14
This slide talks about buffer overflow as a risk of application security. A buffer overflow takes place when malicious code is introduced into the system's allocated memory region.
Slide 15
This slide gives information about Application Performance Management (APM). The APM data can help enhance software security by giving a complete picture of an application's architecture and components, assessing optimal performance with dynamic baselining, and alerting when differences or abnormalities are detected.
Application Security Approaches In Cybersecurity Training Ppt with all 35 slides:
Use our Application Security Approaches In Cybersecurity Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Great experience, I would definitely use your services further.
-
“Slides are formally built and the color theme is also very exciting. This went perfectly with my needs and saved a good amount of time.”