Blockchain Technology Vulnerabilities User Wallet Attack Training Ppt
These slides cover the types of user wallet attacks in blockchain technology which are phishing attack and dictionary attack. It also includes recent user wallet attacks and preventative strategies to avoid them.
These slides cover the types of user wallet attacks in blockchain technology which are phishing attack and dictionary attac..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Blockchain Technology Vulnerabilities User Wallet Attack. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. You can add or delete the content as per your need.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1
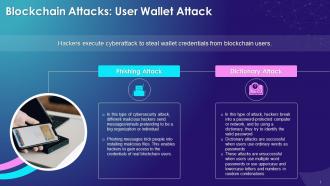
This slide illustrates the concept of user wallet attack in the blockchain. It also explains that the hacker executes cyberattack to steal credentials from the blockchain users. It also explains the different user wallet attack types such as phishing attack and dictionary attack. In phishing attack, malicious hackers send messages/emails pretending to be big organizations. Phishing messages make people do activities like installing malicious files from which the hackers can access their credentials. In dictionary attack, hackers use every possible word in the dictionary to crack the password. These attacks are successful when the hackers use ordinary words as passwords.
Instructor’s Notes:
The different types of user wallet attacks are as follows:
Types of phishing attacks are as follows:
Email Phishing:
- It is the most common type of phishing attack that hackers use to send emails to different users, informing them about security issues in their accounts
- Users sometimes panic and respond to these emails by clicking on the links provided and ends up losing money
Spear Phishing:
- A spear-phishing attack is used to attain sensitive information from a computer system by sending counterfeit messages that appear to be legitimate
Whaling:
- It is also known as CEO fraud. It is an attack used to steal money from high-stake players in the organization by sending messages, emails and website spoofing to trick targets into performing some actions that could lead to loss of money or essential information from an organization or an individual
Smishing:
- In smishing attack, individual gets false text messages; users may reply directly or visit phishing sites
Vishing:
- This attack is accomplished by using voice calls. The purpose remains the same, but in this case, instead of SMS, attackers use voice calls to trick the users into getting data or money
Search Engine Phishing:
- In this type of attack, hackers use SEO engines to trick organizations
- Hacking the SEO search list and getting on the top of the list when an organization or individual clicks on their link displayed within the search engine, the link gets the individual directly to the hacker’s website
- The hackers then hack the important information from different organizations such as banks, money transfers, social media, and shopping sites
Types of Dictionary attacks are as follows:
- Brute Force Attack: This attack uses a trial-and-error method to guess login passwords, encryption keys, or find a hidden web page. The hackers work on all possible combinations to find the correct combination
- Hybrid Attack: This type of attack is the same as a dictionary attack, but in such an attack, hackers add some numbers and symbols to words from the dictionary and try to crack the password
- Syllable Attack: This type of attack is a combination of both brute force attacks and hybrid attacks. This attack is done when cracking any password with no word but rather based on characters and syllables
- Rule-Based Attack: This type of attack is a programming language coded to generate candidates' passwords
Slide 2
This slide showcases the different user wallet attacks in the blockchain such as vulnerable signatures and flawed key generation. The vulnerable signatures attack explains that the digital signature cryptographically links a user to a particular message/agreement in the blockchain. The signature is referred to as private key. The private key is essential in the blockchain during the process of transaction. In flawed key generation, the public key can be generated by using RSA algorithm to encrypt sensitive data and transactions in the blockchain.
Slide 3
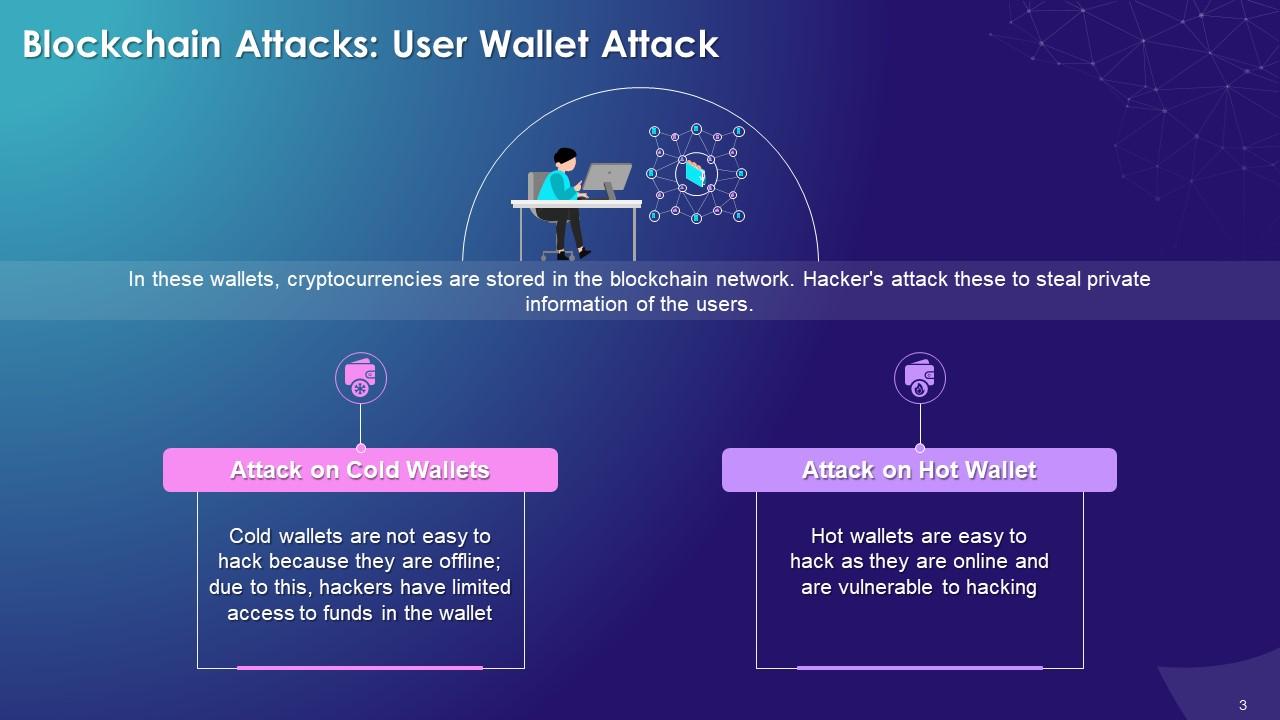
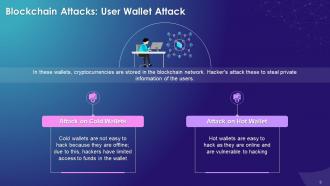
This slide showcases the hot and cold user wallet attacks on the blockchain network. It explains that the cold wallet is not connected to the internet. It is not easy to hack as it is offline, and hackers have limited access to the funds in the wallet. The hot wallet is connected to the internet. The hot wallets are comparatively easier to hack as they are online and are vulnerable to hackers.
Slide 4
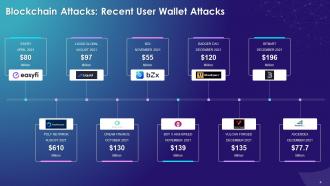
This slide showcases multiple recent attacks on blockchains such as Easyfi, Ascend EX, Polynetwork, Bitmart, Badger, Bzx, Vulcan Forged, Cream, Boy x highspeed, and Liquid.
Slide 5
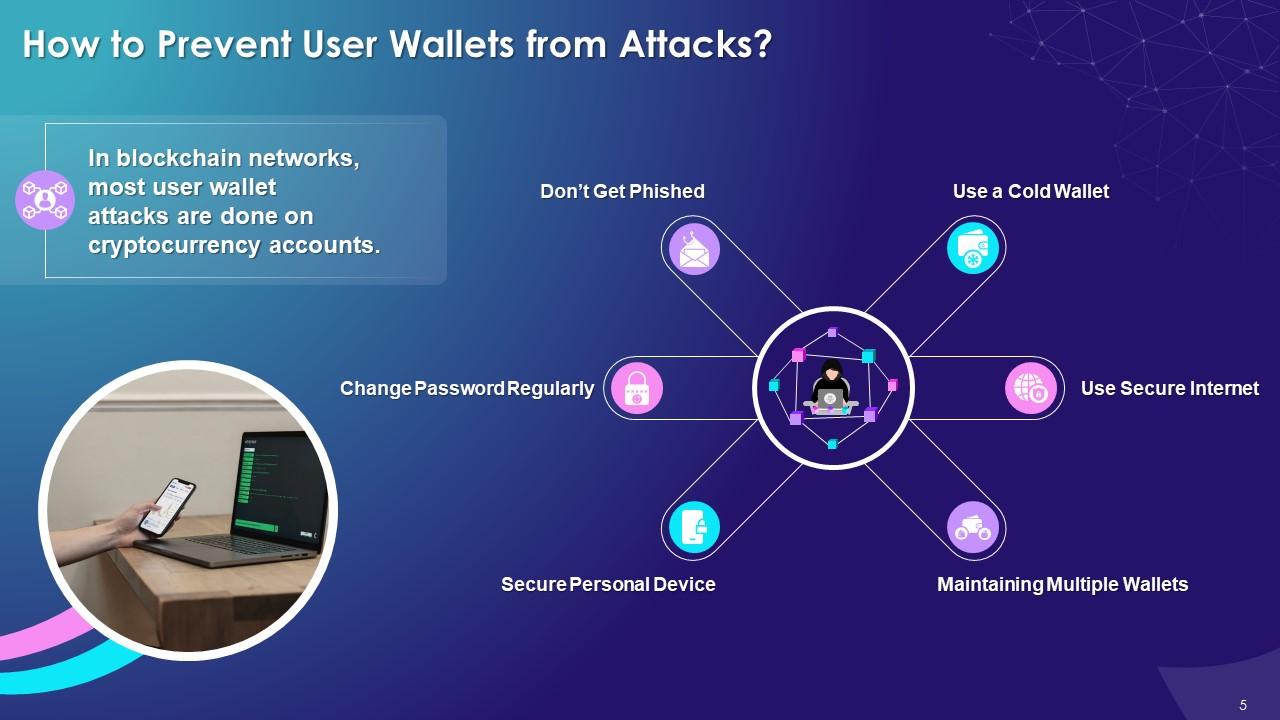
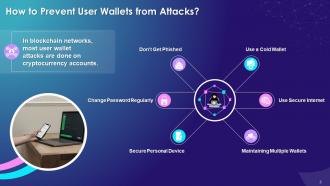
This slide showcases multiple ways in which blockchain users can prevent a user wallet from multiple attacks. This slide also discusses ways such as: using a cold wallet or using a secure internet wallet, maintaining multiple wallets, securing personal devices, changing password regularly and not being phished.
Instructor’s Notes:
Different measures taken to protect user wallet attacks are as follows:
Use a Cold Wallet:
- Cold wallets work offline, so they are not prone to cyberattacks as hackers have limited access to funds
Use Secure Internet:
- It is important to use a private, secure internet connection while trading or making crypto transactions in blockchain network
- Moreover, while using a home network connection, use a VPN for additional security to avoid any hacking activity
- VPN helps keep the internet network secure by changing the IP address and location and keeping your blockchain network activity safe and private from hackers
Maintaining Multiple Wallets:
- In blockchain network, participants should use only one wallet as the main wallet to do daily transactions and keep the remaining wallets separate
- This will keep the data secure and away from any security breach or attack
Secure Personal Device:
- Keeping all personal devices secure with the latest antivirus software is essential to defend the system against new vulnerabilities
- Use a strong antivirus software to improve the security of devices to prevent hackers from hacking the devices
Change Password Regularly:
- It is important to put a strong password in the blockchain network to keep it secure from attackers
- Keep the password strong and complex, and change it regularly, then it is difficult to guess
- In the case of multiple wallets, use separate passwords to keep the data secure
Don’t Get Phished:
- Phishing scams via malicious ads and emails are common in the blockchain network
- Warn all nodes in the system against clicking any unidentified link while making crypto transactions in the blockchain network
Blockchain Technology Vulnerabilities User Wallet Attack Training Ppt with all 21 slides:
Use our Blockchain Technology Vulnerabilities User Wallet Attack Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
The best and engaging collection of PPTs I’ve seen so far. Great work!
-
I want to thank SlideTeam for the work that they do, especially their customer service.