Information Security A Cybersecurity Component Training Ppt
This set of slides covers the information security as a part of cybersecurity. It also covers common information security threats such as unsecure systems, lack of encryption, security misconfiguration, and malware or endpoints.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Information Security a Cybersecurity Component. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content and present it with confidence.
Content of this Powerpoint Presentation
Slide 2
This slide talks about information security. Information security includes the protection of company data as well as the data you obtain from clients, consumers, or vendors.
Slide 3
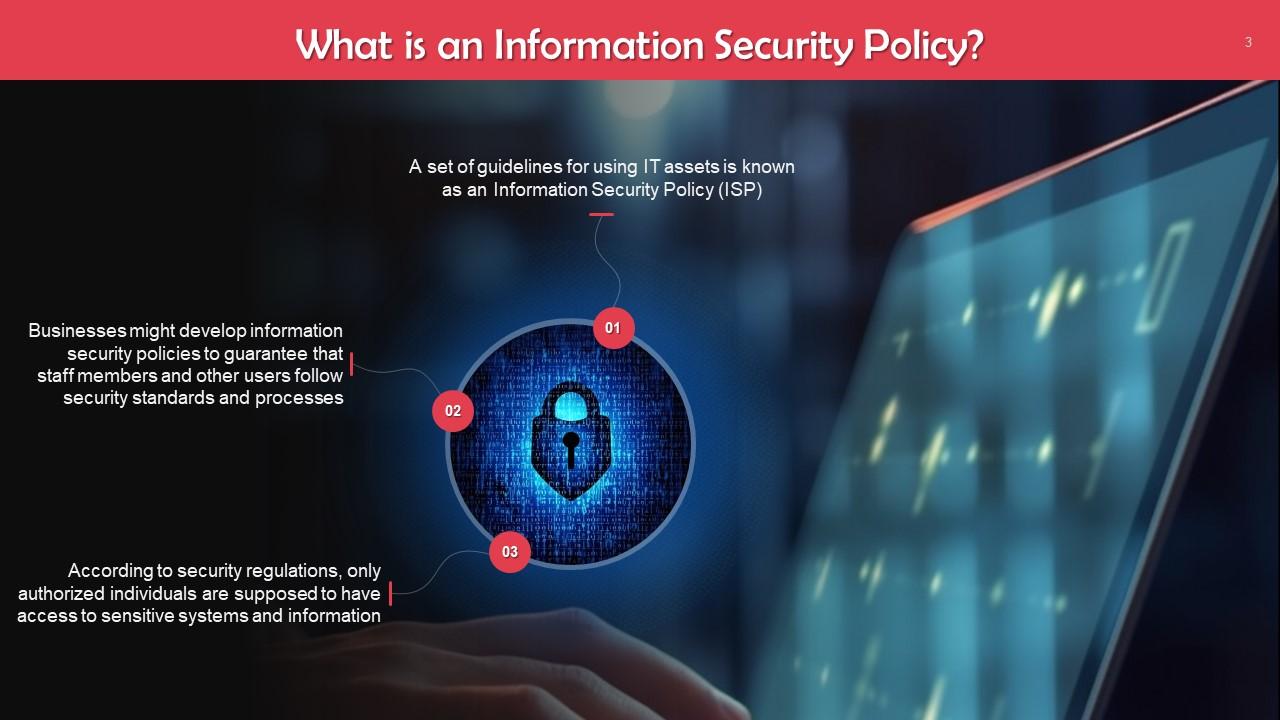
This slide gives an overview of Information Security Policy. A set of guidelines for using IT assets is known as an Information Security Policy (ISP).
Slide 4
This slide highlights common information security threats. These are: Unsecure systems, social engineering, social media attacks, lack of encryption, security misconfiguration, and malware or endpoints.
Slide 5
This slide discusses unsecure systems as an information security threat. The rapid advancement of technology frequently causes security precautions to be compromised. In many instances, systems are created without security considerations and continue to function as legacy systems within an enterprise.
Slide 6
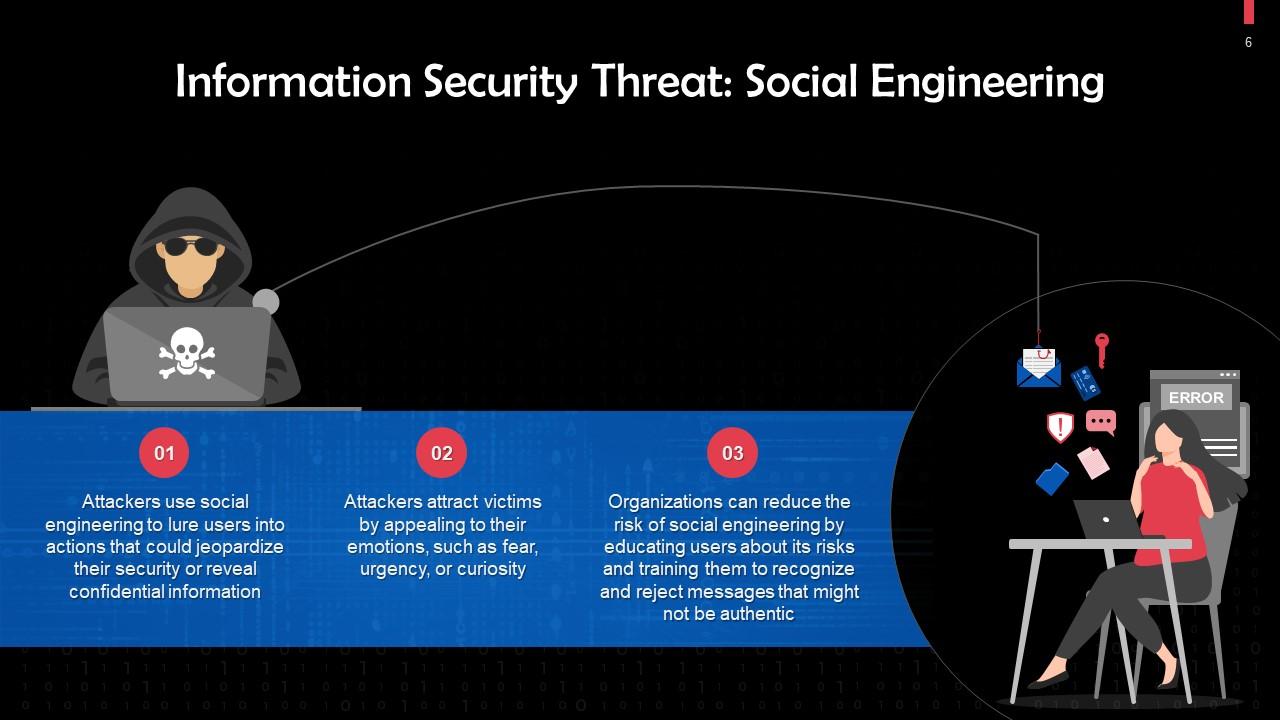
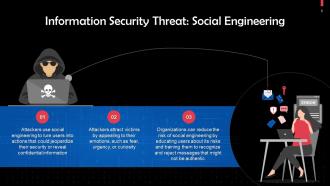
This slide discusses how social engineering poses a threat to information security. Attackers use social engineering to lure users into actions that could jeopardize their security or reveal confidential information.
Instructor’s Notes: Technology solutions can also be employed to stop social engineering at its source or to stop people from performing risky actions like clicking on suspicious sites or downloading unknown attachments.
Slide 7
This slide tells us about social media attacks. People who use social media frequently inadvertently disclose personal information about themselves. Attackers can carry out direct cyber attacks using social media, such as spreading malware through social media messaging.
Slide 8
This slide discusses lack of encryption as an information security threat. Data is encrypted through encryption operations, making it accessible only to users with secret keys. It is very effective and efficient in preventing data loss or corruption in case of loss of equipment or theft; it is extremely critical in case attackers compromise organizational systems.
Slide 9
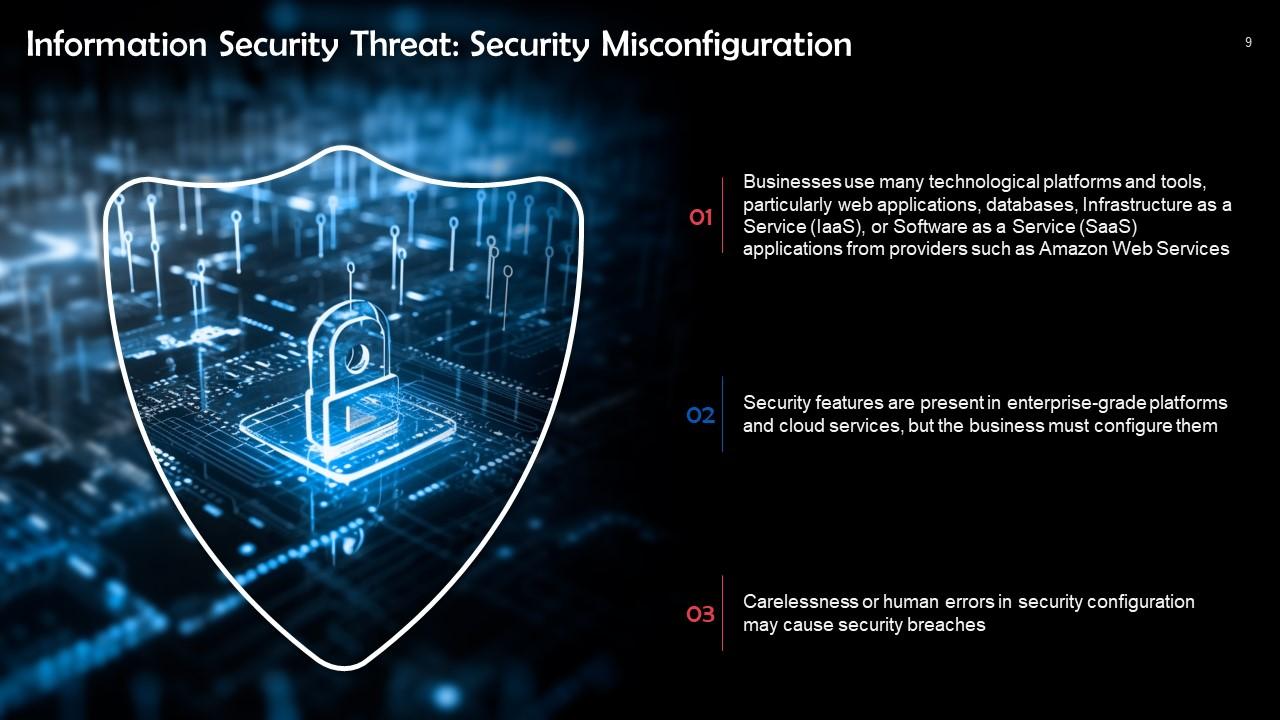
This slide talks about security misconfiguration as an information security threat. Businesses use many technological platforms and tools, particularly web applications, databases, Software as a Service (SaaS) applications, or Infrastructure as a Service (IaaS) from providers like Amazon Web Services.
Instructor’s Notes: Another issue is "configuration drift," in which, despite competent IT security employees with good IT knowledge, proper security configuration can quickly go out of date and make a system insecure.
Slide 10
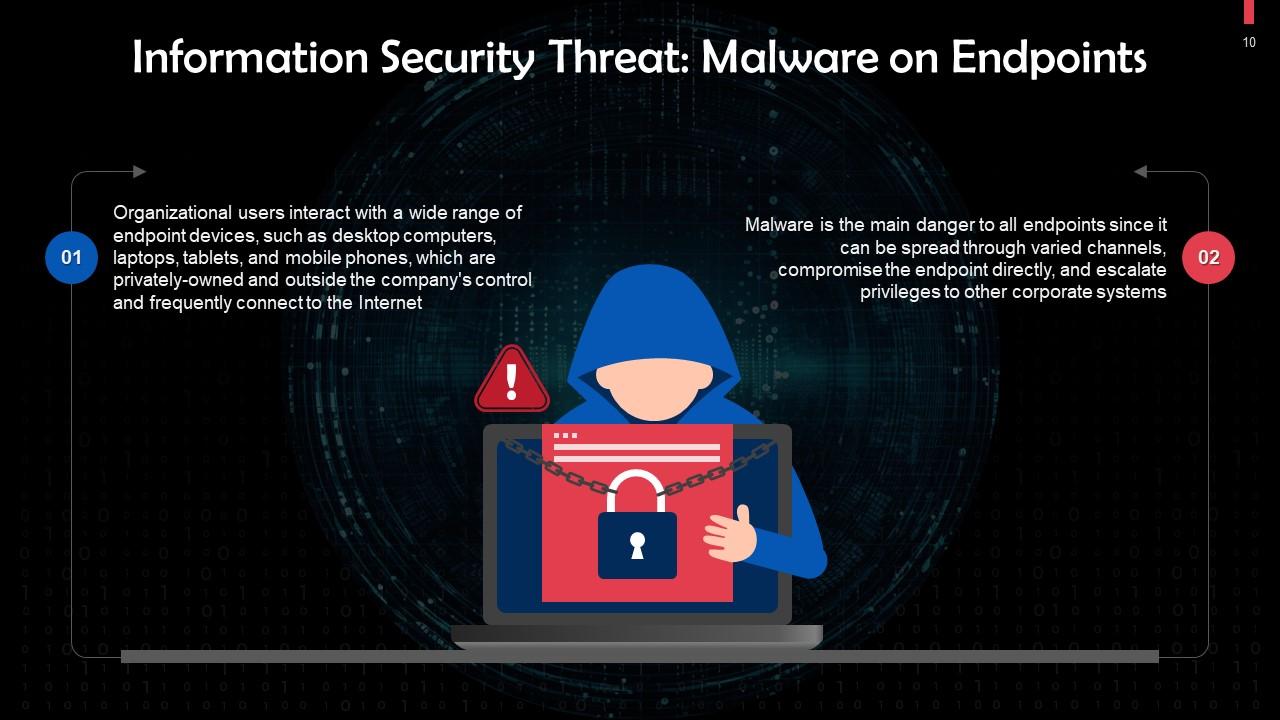
This slide discusses how malware on endpoints can pose a threat to information security. Malware is the main danger to all endpoints since it can be spread through varied channels, compromise the endpoint directly, and escalate privileges to other corporate systems.
Information Security A Cybersecurity Component Training Ppt with all 30 slides:
Use our Information Security A Cybersecurity Component Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
My search for complete decks ended with SlideTeam. Such a surplus collection of HD PowerPoints. Moreover, their standard and widescreen formats have helped me in delivering bullseye presentations.
-
I am a big fan of their newsletters because that is how I found my perfect requirement at the time of urgency. Thank God, I kept opening those.