Understanding Types of Cyber Attacks Training Ppt
The PowerPoint Training Module on Understanding Types of Cyber Attacks thoroughly examines various cyber attack methodologies. It begins with an exploration of Phishing Attacks and Spam, discussing how these deceptive techniques are used to steal sensitive information. The Malware section delves into various malicious software types, including viruses, worms, and trojans, and their impact on systems. Password Attack focuses on methods attackers use to compromise or steal passwords. The PPT Deck addresses SQL Injection Attack, a critical vulnerability that affects database-driven websites. DoS and DDoS Attack sections elucidate how these attacks disrupt services by overwhelming systems. Man-in-the-Middle Attack and Man-in-the-Browser Attack segments explore how attackers intercept and manipulate communications or transactions. It also has Key Takeaways and Discussion Questions related to the topic to make the training session more interactive.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Training Deck on Understanding Types of Cyber Attacks. This deck comprises of 116 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
Content of this Powerpoint Presentation
Slide 3
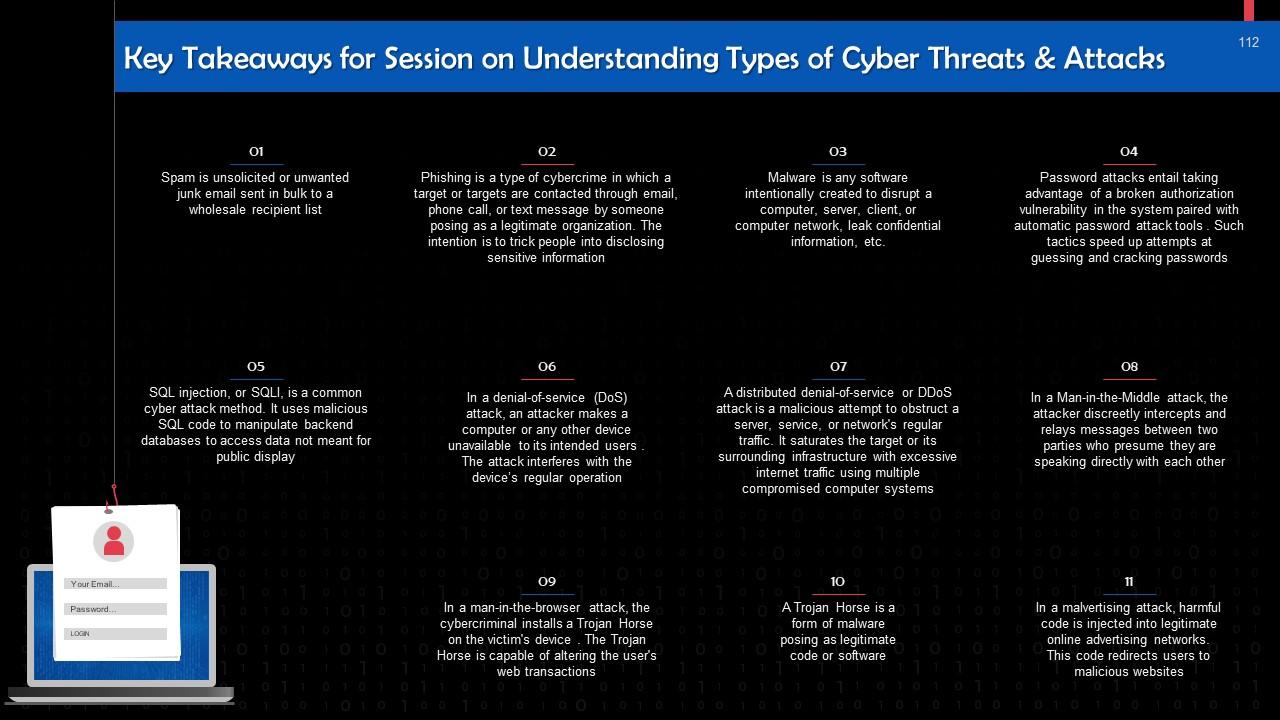
This slide gives information about spam as a cyber threat. Spam is unsolicited or unwanted junk email sent in bulk to a wholesale recipient list. Typically, it is sent for commercial purposes.
Slide 4
This slide gives an overview of phishing attacks. Phishing is a type of cybercrime where a target or targets are contacted through email, phone call, or text message. The fraudster poses as representative of a legitimate organization to trick people into disclosing sensitive information like OTPs, passwords, banking, credit card, and personally identifiable information.
Slide 5
This slide tells us about the working of spam and phishing attacks. Although sending spam emails is considered unethical, many companies still send these as it is a low cost method of sending a large number of mails, regularly. Botnets can also be used to send spam in large quantities.
Slide 6
This slide highlights the difference between spam and phishing attacks.
Slide 7
This slide lists types of phishing attacks. These are spear phishing, whaling, vishing, smishing, email phishing, and search engine phishing.
Slide 8
This slide talks about spear phishing. Spear phishing seeks to gain illegal access to confidential data by targeting specific organizations or individuals.
Slide 9
This slide gives information about whaling. A whaling phishing attack targets CEOs or CFOs to steal sensitive information from a company. Many whaling phishing attempts aim to trick the victim into approving high-value wire transfers to the attacker.
Slide 10
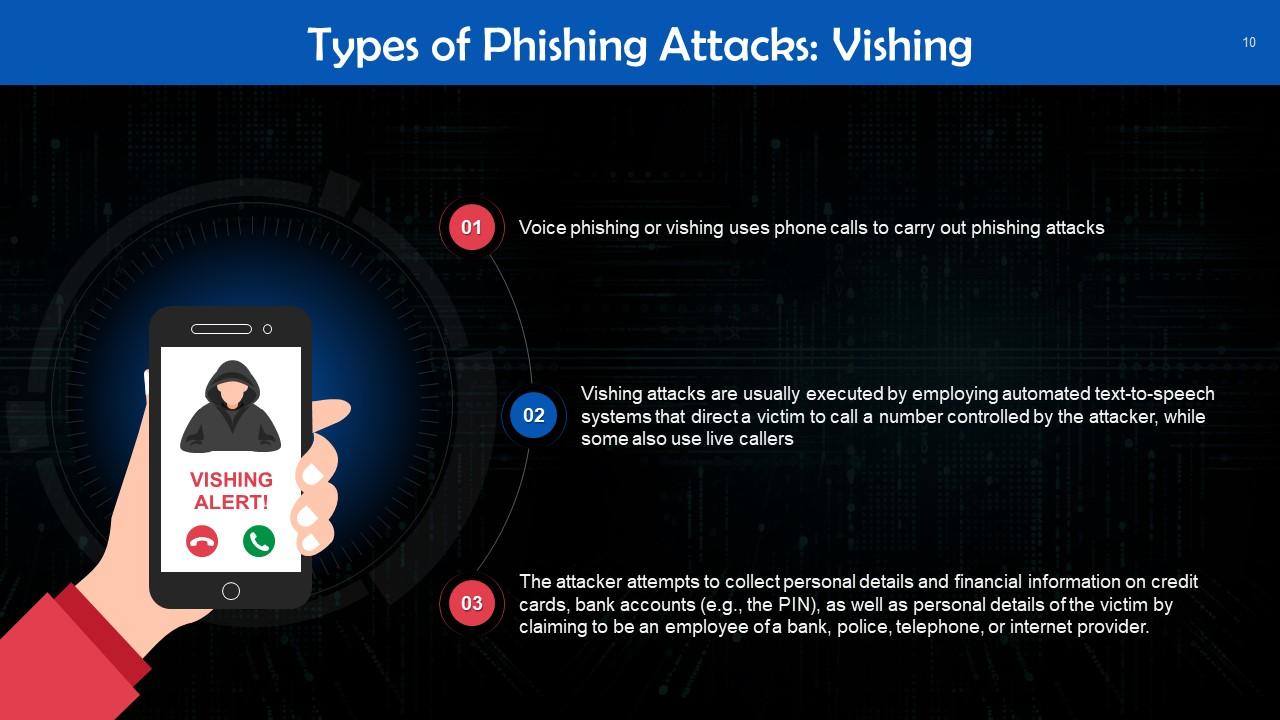
This slide talks about vishing. Voice phishing or vishing uses phone calls to carry out phishing attacks. Vishing attacks are usually conducted using automated text-to-speech systems that direct a victim to call a number that the attacker controls, while some also use live callers.
Slide 11
This slide talks about smishing. Smishing uses text messaging or short message service (SMS) to carry out the attack. These messages usually contain clickable links or a return phone number.
Slide 12
This slide cautions against email phishing. Email phishing is the most prevalent form of phishing, where hackers send emails to any email address they can obtain.
Slide 13
This slide talks about search engine phishing. In search engine phishing or SEO poisoning, hackers work to become the top hit on a search engine using Search Engine Optimization.
Slide 14
This slide gives us information about employee actions that lead to phishing attacks in organizations. Over 20% of employees tend to click on fake attachments.
Slide 15
This slide gives some tips on how to prevent phishing attacks. Some of these include: Conducting regular training for employees, deploying multi-factor authentication.
Slide 16
This slide introduces malware. Malware is any software intentionally created to disrupt a computer, server, client, or computer network.
Slide 17
This slide tells us how malware is harmful to your devices. Malware can infect devices and networks and is designed with the intention of harming these networks, devices, and/or their users.
Slide 18
This slide gives information on how malwares are spread. Threat actors use physical and virtual means to spread malware that infects networks and devices.
Slide 19
This slide depicts leading malware carriers. Emails account for the majority (about 92%) of the spread of malwares.
Slide 20
This slide highlights types of malware. These are viruses, adware, rootkit, spyware, ransomware.
Instructor’s Notes:
- Virus: A virus is the most prevalent form of malware that executes itself and spreads by infecting other files or programs
- Adware: Adware keeps track of a user's download history and browsing habits, intending to display pop-up or banner ads that tempt the users to make a purchase. For instance, an advertiser may use cookies to track the web pages a user visits to target advertising
- Rootkit: A rootkit gains system administrator privileges for the victim's system. After it is installed, the program provides threat actors the root or privileged access to the user's system
- Spyware: Spyware gathers information and data about the device and user and observes the user's activity without their knowledge
- Ransomware: When ransomware infects a user's system, it encrypts its data. The victim is then told to pay a ransom to the cybercriminals to have the data on the system decrypted
- Trojan Horse: A Trojan Horse is made to seem like a legitimate software program so as to gain access to a system. Trojans can execute malicious functions once activated following installation
- Remote Access: Remote Access Trojan (RAT), or a backdoor virus, discreetly creates a backdoor into an infected computer system that allows threat actors to access it remotely without warning the user or the system's security programs
- Worm: A worm is able to self-replicate without a host program and spreads without interacting with the malware authors
- Keylogger: Keyloggers, or system monitors, track almost everything a user does on their computer, including emails, opened web pages, programs, and keystrokes
Slide 21
This slide depicts leading types of malware infecting android. The most common type are trojans that account for about 92% of the attacks or infections.
Slide 22
This slide gives information about how to detect a malware. Users can detect malware if they observe unusual activity, such as prolonged delays, sudden loss of disk space, repeated crashes, frequent hanging of the system, increased unwanted internet activity, and pop-up advertisements
Slide 23
This slide highlights a six-step response plan for malwares. These steps are: Identify, communicate, block, restore, recover, and re-examine.
Slide 24
This slide tells us ways to remove a malware. Many security software products are designed to detect, prevent and remove malware from infected systems.
Slide 25
This slide talks about the ways to prevent a malware infection. Companies should implement dual approval for business-to-business (B2B) transactions and second-channel verification for business-to-consumer (B2C) transactions.
Slide 26
This slide discusses malware infections on mobile devices. Malware can infect mobile phones and provide access to a device's components, such as the microphone, camera, GPS.
Slide 27
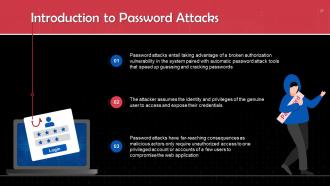
This slide introduces password attacks. These attacks entail taking advantage of a broken authorization vulnerability in the system paired with automatic password attack tools that speed up guessing and cracking passwords.
Instructor’s Notes: Additionally, apps that rely solely on passwords for authentication are more vulnerable to password attacks.
Slide 28
This slide lists types of password attacks. These are phishing, brute-force attacks, dictionary attacks, password spraying, and keylogging.
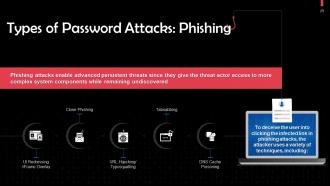
Slide 29
This slide discusses types of phishing password attacks. To deceive the user into clicking the infected link in phishing attacks, the attacker employs many techniques, including: DNS Cache Poisoning, Tabnabbing, URL Hijacking/Typosquatting, Clone Phishing, and UI Redressing/iFrame Overlay.
Slide 30
This slide talks about how phishing attacks can be executed by DNS Cache Poisoning. Attackers use weaknesses in the DNS server of the application to redirect user requests to a malicious website.
Slide 31
This slide discusses how phishing attacks can be executed by Tabnabbing. Tabnabbing is a type of password phishing attack that tricks users into submitting their login details and passwords on well-known websites, which were actually duplicate copies of these websites. The ruse that works here is that the website is genuine.
Slide 32
This slide talks about how phishing attacks can be executed by URL Hijacking or Typosquatting. Typosquatting targets internet users who incorrectly type a URL into their web browser instead of using a search engine.
Slide 33
This slide discusses clone phishing as a type of password attack. Clone phishing attacks work by cloning an email from a trusted or reputable source.
Slide 34
This slide talks about how phishing attacks can be executed by UI Redressing and iFrame Overlay. In this type of cyber attack, the user is tricked into clicking something on the User Interface (UI) on a genuine-looking web page. However, a specially created page is loaded behind the website that is malicious but appears to be legitimate.
Slide 35
This slide discusses brute-force password attacks. This attack uses trial-and-error methods to guess a user’s login information. The threat actor tries to guess the user’s password correctly with the use of automated scripts to work through permutations.
Slide 36
This slide talks about simple brute-force password attacks. In this attack, a threat actor tries many passwords until a match is found
Slide 37
This slide discusses credential stuffing as a type of brute-force password attack. This attack involves using previously exposed login combinations that have been maliciously acquired across vulnerable websites.
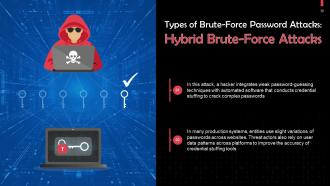
Slide 38
This slide discusses hybrid brute-force password attacks. In this attack, a hacker integrates weak password-guessing techniques with automated software that conducts credential stuffing to crack complex passwords.
Slide 39
This slide tells us about reverse brute-force password attacks. In this type of brute-force attack, an attacker begins with a known password and then searches for usernames that match it.
Slide 40
This slide gives an overview of dictionary password attacks. This method uses a predetermined list of words that a specific target network is likely to use as passwords
Slide 41
This slide talks about password spraying attacks. In this attack, the threat actor attempts to log in using the same password across multiple accounts before switching to another password.
Slide 42
This slide tells us about keylogging. In a Keylogging attack, a threat actor installs monitoring tools in the user’s computer to secretly record the keystrokes of a user.
Slide 43
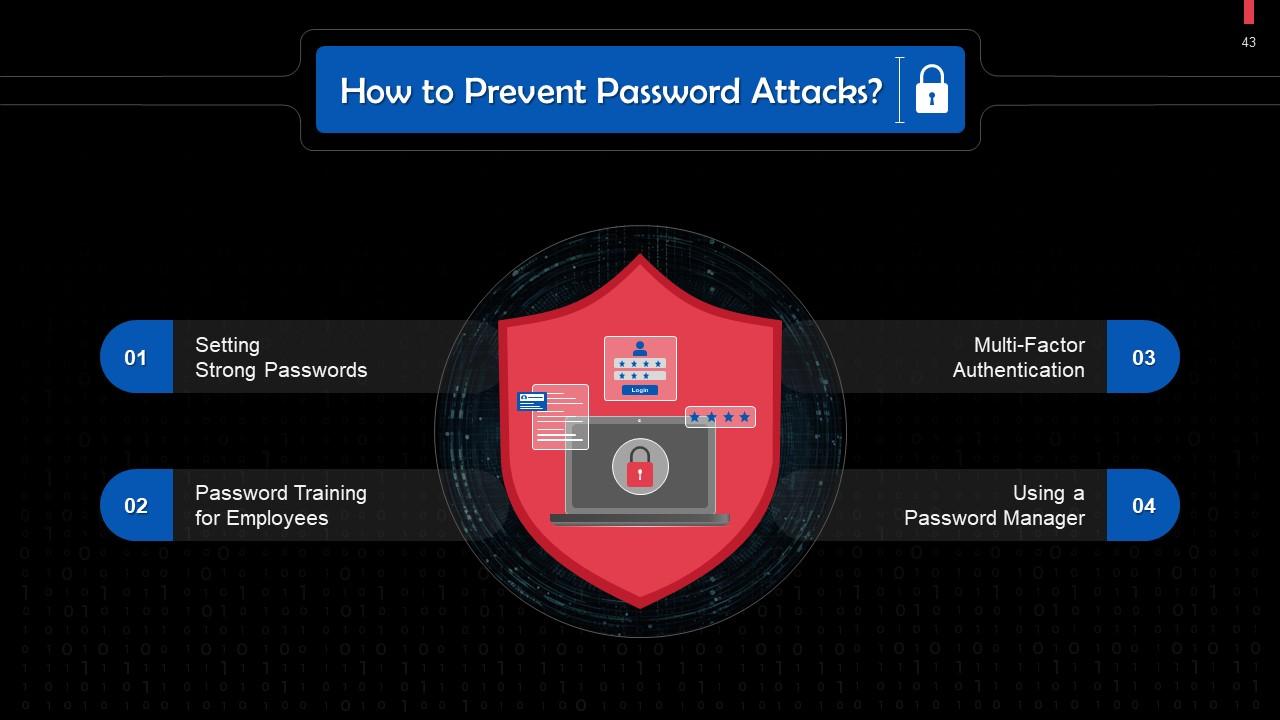
This slide highlights the ways to prevent password attacks. These include: setting strong passwords, conduct regular password training for employees, employing multi-factor authentication, and using a password manager.
Slide 44
This slide discusses how setting strong passwords can help in preventing password attacks. Organizations must enforce policies to prevent malicious actors from cracking their employees' passwords.
Slide 45
This slide discusses how organization-wide password training can help in preventing password attacks. It is crucial to ensure every user knows the importance of a solid password policy.
Slide 46
This slide explains how multi-factor authentication can help in preventing password attacks. Mult-ifactor authentication entails the use of passwords in conjunction with additional security measures.
Slide 47
This slide tells how using a password manager can help in preventing password attacks. A password manager assists web administrators in storing and managing user credentials. Password management solutions also generate user passwords following strict guidelines and best practices.
Slide 48
This slide talks about SQL Injection. SQL injection, or SQLI, is a common cyber attack method that uses malicious SQL code to manipulate backend databases to access data that is private and not meant to be shown in public.
Slide 49
This slide lists types of SQL Injections. These include: In-Band SQLi, Inferential or Blind SQLi, and Out-of-Band SQLi.
Slide 50
This slide discusses In-Band SQLi. The threat actor uses the same communication channel to launch attacks and gather results.
Slide 51
This slide highlights types of In-Band SQL injections. These are: Error-Based SQLi and Union-Based SQLi.
Slide 52
This slide talks about Inferential or Blind SQLi. To better understand the server's architecture, the threat actor sends data payloads to the server and monitors how it responds and behaves.
Slide 53
This slide highlights types of Inferential or Blind SQL injections. Blind SQL injections are either boolean or time-based.
Slide 54
This slide discusses Out-of-Band SQLi. Out-of-band SQLi is executed when the attacker cannot use the same transmission channel to launch the attack and collect data or when a server is unstable or too slow for these actions to be conducted.
Slide 55
This slide highlights ways of mitigating SQL Injection attacks. These are: Object relational mappers, web application firewalls, escaping, parameterized statements, database permissions, and pattern check.
Slide 56
This slide discusses how Object Relational Mappers (ORM) can be used to mitigate the risk of SQL injection attacks. Developers can use ORM frameworks to create database queries in a secure and user-friendly way.
Slide 57
This slide talks about how Web Application Firewalls (WAFs) are used to mitigate the risk of SQL injection attacks. WAF technologies can make discovery and exploitation significantly more challenging for an attacker.
Slide 58
This slide discusses how Escaping mitigates the risk of SQL injection attacks. A way to prevent SQL injections is to attempt to escape all characters with special significance in SQL.
Slide 59
This slide discusses how Parameterized Statements mitigate the risk of SQL injection attacks. Instead of integrating user input into the statement, most development platforms allow the usage of parameterized statements that operate with restrictions.
Slide 60
This slide discusses how Database Permissions can be used to mitigate the risk of SQL injection attacks. Limiting the permissions or rights on the database login may help reduce the effectiveness of any SQL injection attack.
Slide 61
This slide discusses how Pattern Check can be used to mitigate the risk of SQL injection attacks. String parameters, integers, float, or boolean, can be checked if their value is a valid representation for the specified type.
Slide 62
This slide talks about DoS attacks. In a Denial-of-Service (DoS) attack, an attacker makes a computer or any other device unavailable to its intended users by interfering with its regular operation.
Slide 63
This slide explains the working of DoS attacks. A DoS attack aims to overload the capacity of a target system to deny service to additional requests.
Slide 64
This slide discusses buffer overflow attacks. In this type of DoS attack, a memory buffer overflow can lead a device to consume all its hard disk space, memory, or CPU time.
Slide 65
This slide talks about flood attacks. A malicious actor can oversaturate a server's capacity and cause denial-of-service by flooding a targeted server with an excessive number of packets.
Slide 66
This slide lists popular types of denial-of-service attacks. These are smurf attacks, ping flood attacks, and ping of death attacks.
Slide 67
This slide gives information about smurf attack. In this, a threat actor floods the targeted IP address by sending spoof packets.
Slide 68
This slide discusses Ping Flood Attack. Ping Flood is a simple denial-of-service attack based on flooding a target with ICMP or ping packets.
Slide 69
This slide gives information about ping of death attack. In this, the attacker sends a malformed packet to a targeted device.
Slide 70
This slide highlights warning signs of a DoS attack. These include: Unusually slow network performance, such as slow file or website loading times.
Slide 71
This slide talks about DDoS attacks. A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to obstruct a server, service, or network's regular traffic by saturating the target or its surrounding infrastructure with excessive internet traffic by using multiple compromised computer systems.
Slide 72
This slide explains the working of DDoS attacks. DDoS attacks are executed on networks comprising computers and other devices (IoT devices) known as bots that are infected with malware. An attacker can then remotely control such bots.
Slide 73
This slide highlights differences between DoS and DDoS attacks based on the manner of execution, traffic volume, ease of detection, origin source, and attack speed.
Slide 74
This slide tells us how to identify DDoS attacks using traffic analysis tools.
Slide 75
This slide highlights components of a network that can be affected by a DDoS attack. DDoS attack types target components of the network connection. The OSI model is a framework that explains network connectivity in seven distinct layers.
Slide 76
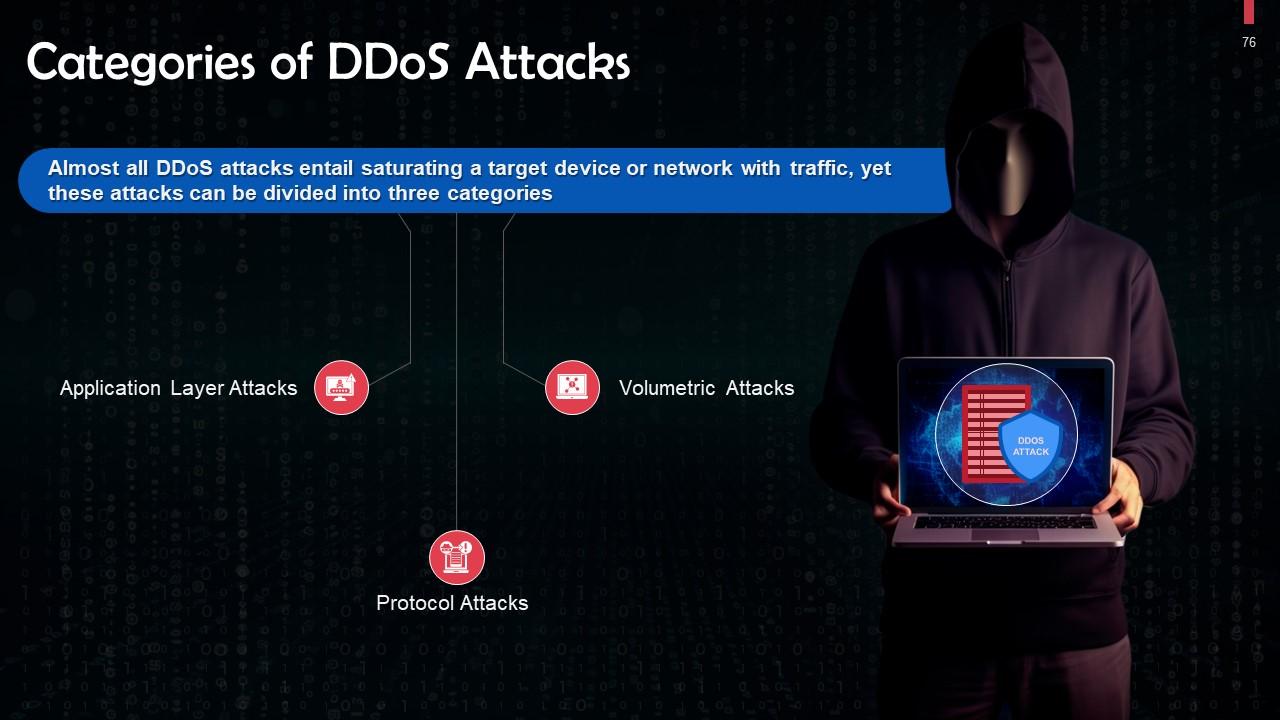
This slide lists the categories of DDoS Attacks. These are: Application layer, protocol, and volumetric attacks.
Slide 77
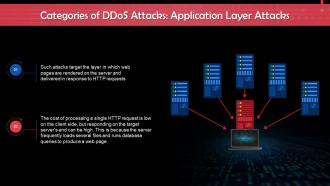
This slide gives us an overview of application layer attacks. These attacks target the layer where web pages are generated on the server and delivered in response to HTTP requests.
Slide 78
This slide discusses HTTP flood attack. This attack causes denial-of-service by flooding the server with numerous HTTP requests. This is comparable to repeatedly hitting the refresh button on multiple PCs.
Slide 79
This slide tells us gives an overview of protocol attacks. Protocol assaults, also known as state-exhaustion attacks, result in denial-of-service by over-consuming server resources and network resources used by firewalls and load balancers.
Slide 80
This slide discusses SYN Flood Attack. This attack manipulates the TCP handshake by sending the target a large number of TCP “Initial Connection Request” SYN packets with false-source IP addresses.
Slide 81
This slide tells us gives an overview of volumetric attacks. These attacks aim to create congestion by using all available bandwidth between the target and the Internet.
Slide 82
This slide discusses DNS Amplification attack. This attack uses open DNS resolvers' functionality to flood a target server or network with increased traffic.
Slide 83
This slide lists ways to mitigate a DDoS attack. These are: Blackhole routing, rate limiting, anycast network diffusion, and web application firewalls.
Slide 84
This slide discusses how blackhole routing can help mitigate the risk of a DDoS attack. Blackhole filtering refers to dropping packets at the routing level.
Slide 85
This slide talks about rate limiting to prevent DDoS attacks. APIs that use rate limiting can slow down or temporarily block any client that attempts to make too many API calls.
Slide 86
This slide discusses how Anycast Network Diffusion mitigates the risk of DDoS attack. In this mitigation strategy, an Anycast Network disperses the attack traffic across a network of remote servers until the network entirely absorbs it.
Slide 87
This slide shows how WAFs mitigate the risk of a DDoS attack. A Web Application Firewall can function as a reverse proxy and shield the targeted server from malicious traffic.
Slide 88
This slide talks about man-in-the-middle attacks. In a Man-in-the-Middle attack, the attacker discreetly intercepts and relays messages between two parties, who assume they are speaking directly with each other.
Slide 89
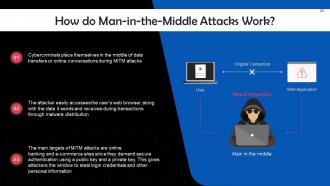
This slide depicts the working of Man-in-the-Middle (MiTM). Cybercriminals place themselves in the middle of data transfers or online conversations during MiTM attacks.
Slide 90
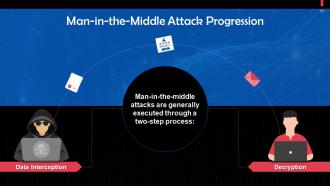
This slide highlights a two-step process of executing a MiTM attack. The steps are data interception and decryption.
Slide 91
This slide discusses the first step, i.e. Interception, for executing MiTM attacks. Data interception involves a threat actor intercepting data transfers between a server and a client. The threat actor misleads the client and the server into believing they are exchanging information with each other.
Slide 92
This slide discusses the second step, i.e. decryption, for executing MITM attacks. In the decryption phase, the intercepted data is unencrypted.
Slide 93
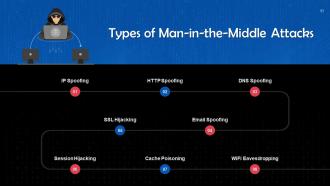
This slide depicts the working of man-in-the-middle attacks. These are: IP Spoofing, HTTP spoofing, DNS spoofing, email spoofing, SSL hijacking, session hijacking, cache poisoning, and WiFi eavesdropping.
Slide 94
This slide talks about IP Spoofing. IP spoofing is similar to identity theft; it occurs when hackers modify the source IP address of a website, email address, or device to disguise it.
Slide 95
This slide discusses HTTP Spoofing. It involves redirecting a browser session to an unsecured or HTTP-based web page without the user's knowledge or consent. This also easy stealing of sensitive information to cybercriminals.
Slide 96
This slide talks about DNS Spoofing. Cybercriminals change domain names in this man-in-the-middle attack to divert traffic to fake websites.
Slide 97
This slide discusses Email Spoofing. This type of MiTM attack allows cybercriminals to take over the email accounts of banks and other financial organizations and track all user transactions.
Slide 98
This slide talks about SSL (Secure Sockets Layer) Hijacking. SSL is a protocol that helps establish an encrypted and secure connection between a browser and the web server.
Slide 99
This slide discusses Session Hijacking. Session hijacking, or stealing browser cookies, is a malicious practice that takes place when hackers steal personal information and passwords stored in the cookies of a user's browsing session.
Slide 100
This slide talks about Cache Poisoning. It enables threat actors on the same subnet as the victims’ to eavesdrop on traffic being routed between them.
Slide 101
This slide discusses WiFi Eavesdropping. During this attack, public Wi-Fi users are tricked into connecting to malicious Wi-Fi networks and hotspots.
Slide 102
This slide depicts an example of a man-in-the-middle attack. One of the biggest credit reporting companies, Equifax, suffered a major data breach in 2017 that revealed the financial data of around 150 million Americans.
Slide 103
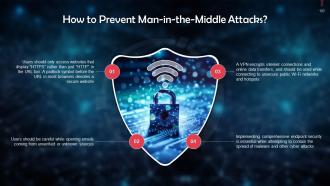
This slide gives information about the prevention of man-in-the-attacks. Users should visit secure websites that display “HTTPS” in the URL bar or a padlock symbol before the URL. A VPN should be used while connecting to public WiFi networks and hotspots.
Slide 104
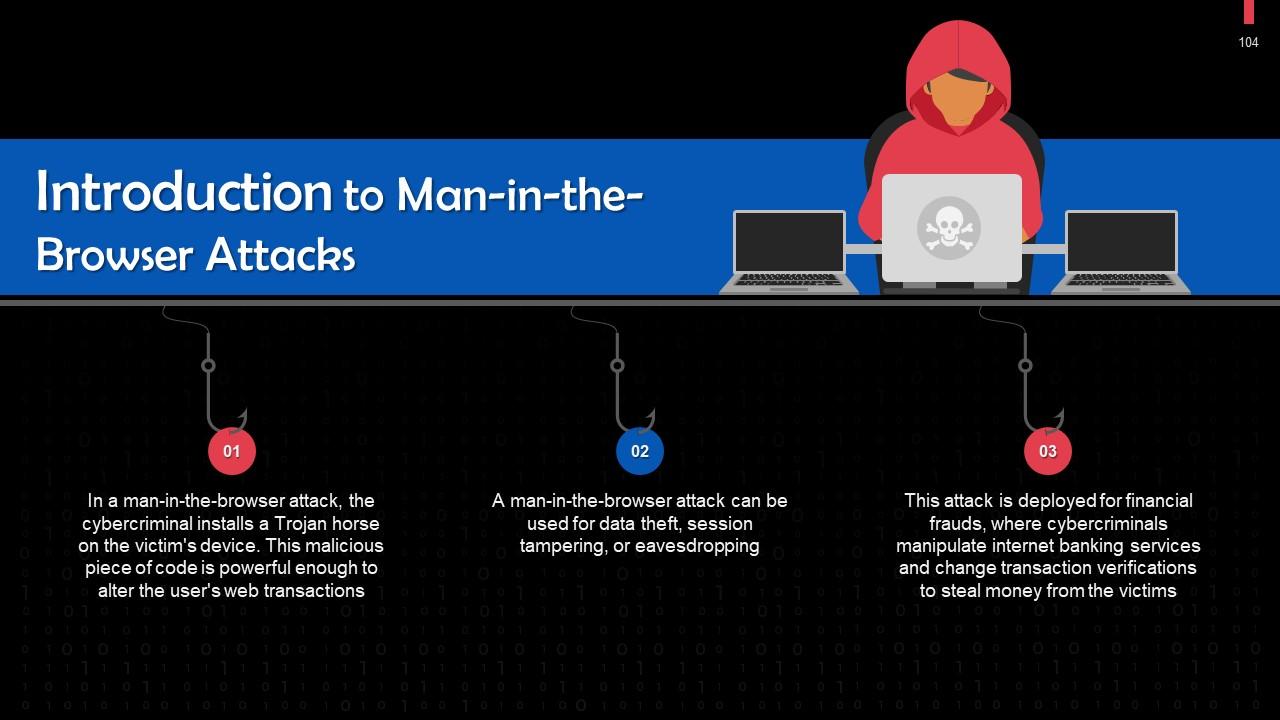
This slide gives an overview of man-in-the-browser attacks. In a man-in-the-browser attack, the cybercriminal installs a Trojan horse on the victim's device capable of altering the user's web transactions.
Slide 105
This slide shows the working of man-in-the-browser attacks.
Slide 106
This slide highlights some examples of man-in-the-browser attacks. These are Zeus, SpyEye, and OddJob.
Slide 107
This slide discusses zeus, which is a type of man-in-the-browser attack. This attack that gathers online banking credentials and conducts illicit fund transfers.
Slide 108
This slide gives information about SpyEye, which is a type of man-in-the-browser attack. The SpyEye Trojan prompts users for details such as bank account login credentials, passwords, usernames, or credit card information.
Slide 109
This slide discusses OddJob, which is a type of man-in-the-browser attack. This attack is initiated through Firefox or the Internet Explorer and activates when the victim opens a banking website.
Slide 110
This slide showcases warning signs of a man-in-the browser attack. These may include: Malware detection by antivirus software, abrupt logging out of accounts.
Slide 111
This slide gives information about how to prevent man-in-the-middle attacks. You can prevent these by installing antivirus softwares, using multi-factor authentication.
Understanding Types of Cyber Attacks Training Ppt with all 126 slides:
Use our Understanding Types of Cyber Attacks Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
I am extremely pleased with these PPT slides that we used for our event. They were easy to modify and came out great in all aspects!
-
SlideTeam never fails to surprise me with its amazing PPT designs. Thanks team for providing me with your constant support!