Five year cyber information security career growth roadmap
Our Five Year Cyber Information Security Career Growth Roadmap are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
Presenting Five Year Cyber Information Security Career Growth Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
Content of this Powerpoint Presentation
Description:
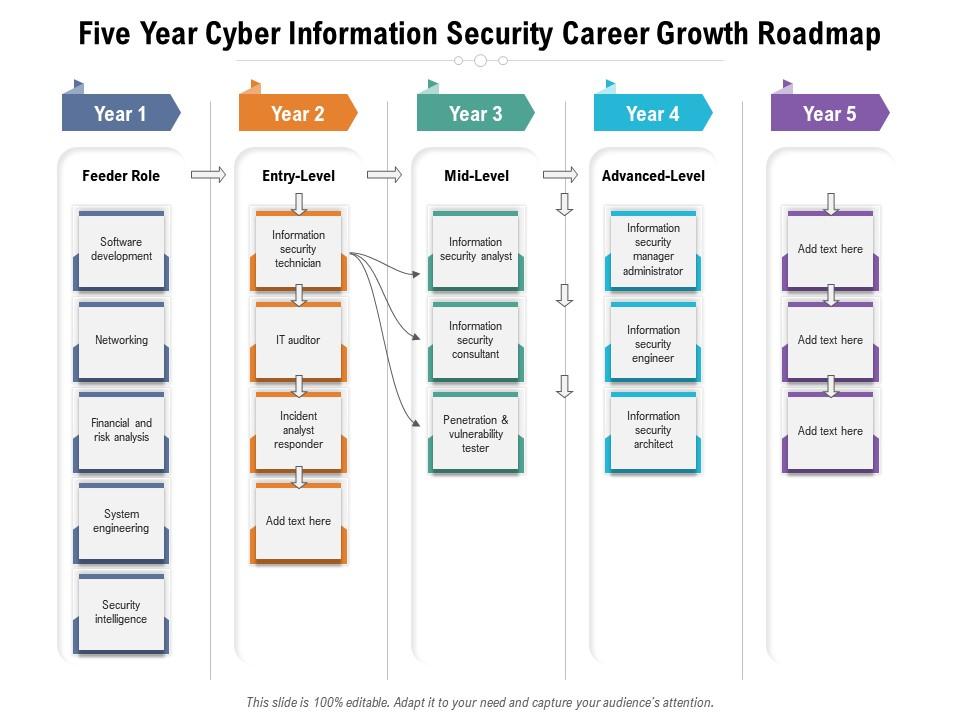
The image is a PowerPoint slide titled "Five Year Cyber Information Security Career Growth Roadmap." It outlines a progression plan for a career in information security, segmented into five years. Each year highlights key roles within the field:
Year 1:
Feeder Role – Includes foundational roles like software development, networking, financial and risk analysis, system engineering, and security intelligence.
Year 2:
Entry-Level – Positions such as information security technician, IT auditor, and incident analyst responder are typical starting points for security professionals.
Year 3:
Mid-Level – Progression to roles like information security analyst, information security consultant, and penetration & vulnerability tester.
Year 4:
Advanced-Level – These are more senior roles, including information security manager/administrator, information security engineer, and information security architect.
Year 5:
Further Development – This column has placeholders to add additional advanced roles or specializations.
Use Cases:
This career roadmap can be used across various industries, particularly those where cybersecurity is crucial:
1. Technology:
Use: Planning career paths for IT security teams.
Presenter: Chief Information Security Officer (CISO).
Audience: IT professionals, HR managers.
2. Finance:
Use: Developing cybersecurity expertise in banking and finance.
Presenter: Security Compliance Manager.
Audience: Financial analysts, cybersecurity staff.
3. Healthcare:
Use: Ensuring patient data protection through advanced security roles.
Presenter: Health Information Manager.
Audience: IT staff, healthcare administrators.
4. Government:
Use: Structuring the growth of personnel in charge of protecting sensitive government data.
Presenter: Government IT Security Head.
Audience: Public sector IT workers, policy makers.
5. Education:
Use: Creating academic programs for cybersecurity careers.
Presenter: Academic Dean of Computer Science.
Audience: Students, academic advisors.
6. Retail:
Use: Safeguarding customer data and financial transactions.
Presenter: Retail Data Protection Officer.
Audience: Retail management, security teams.
7. Telecommunications:
Use: Protecting infrastructure and customer data from cyber threats.
Presenter: Telecom Network Security Manager.
Audience: Network engineers, cybersecurity specialists.
Five year cyber information security career growth roadmap with all 2 slides:
Use our Five Year Cyber Information Security Career Growth Roadmap to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
No Reviews