Cloud Cryptography Powerpoint Presentation Slides
This Cloud Cryptography IT PPT includes a cloud computing overview, cryptography basics, and applications of cryptographic security. Our Symmetric encryption PowerPoint presentation demonstrates the key features, global market analysis, emerging trends, and benefits of cloud cryptography. Additionally, our hashing deck explored the various forms of cyber-attacks that can be thwarted through the implementation of cryptographic algorithms. This data security in cloud computing PPT also demonstrates the working steps and architecture of the cloud cryptography framework. Furthermore, the cloud encryption techniques module explains the implementation of the symmetric algorithm, asymmetric algorithm, and hashing in cloud computing. It also discusses the working of the Standard for Advanced Encryption AES, Common Data Encryption DES, Rivest Shamir Adleman RSA, and the Elliptic Curve Cryptography ECC algorithm. Moreover, this cloud data protection template contains sections about the services, tools, training, and budget for cloud cryptography. Lastly, this cloud privacy deck comprises a roadmap, a 30-60-90 days plan, a timeline, a checklist for implementing cryptography in the cloud, and a dashboard to monitor their performance. Download our 100 percent editable and customizable template, which is also compatible with Google Slides.
This Cloud Cryptography IT PPT includes a cloud computing overview, cryptography basics, and applications of cryptographic ..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of eighty five slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Cloud Cryptography. State Your Company Name and begin.
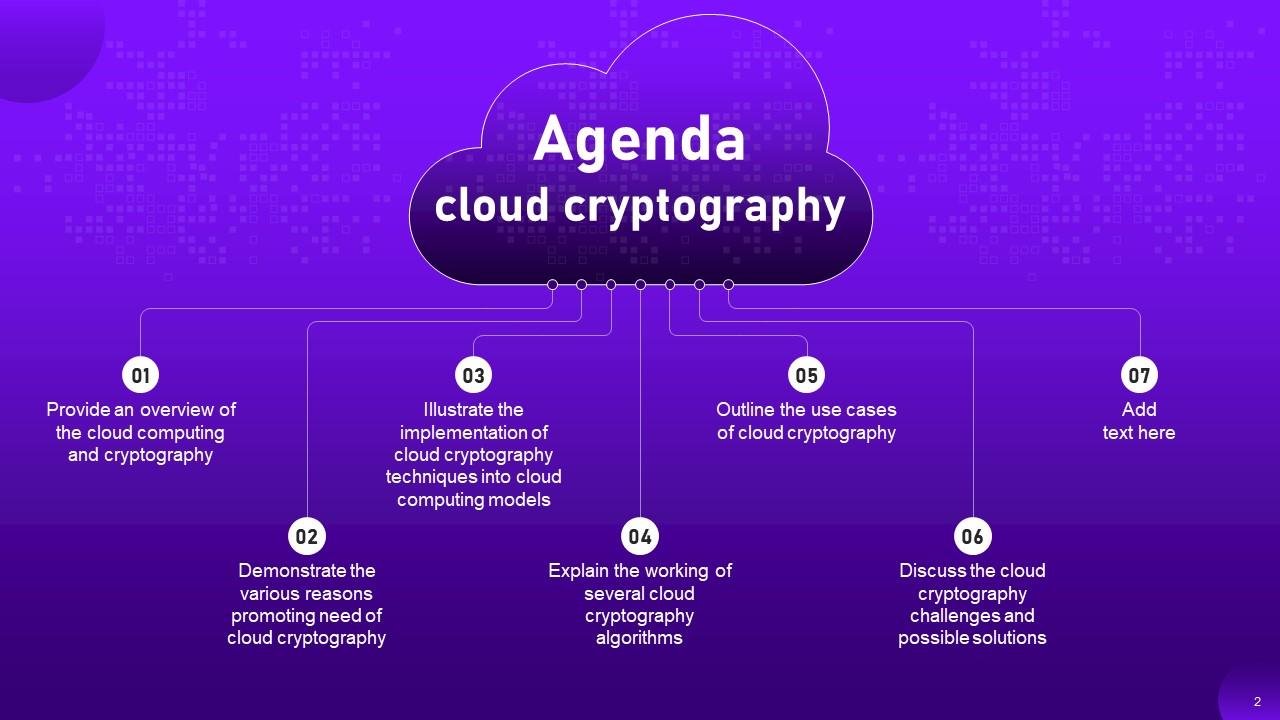
Slide 2: This slide is an Agenda slide. State your agendas here.
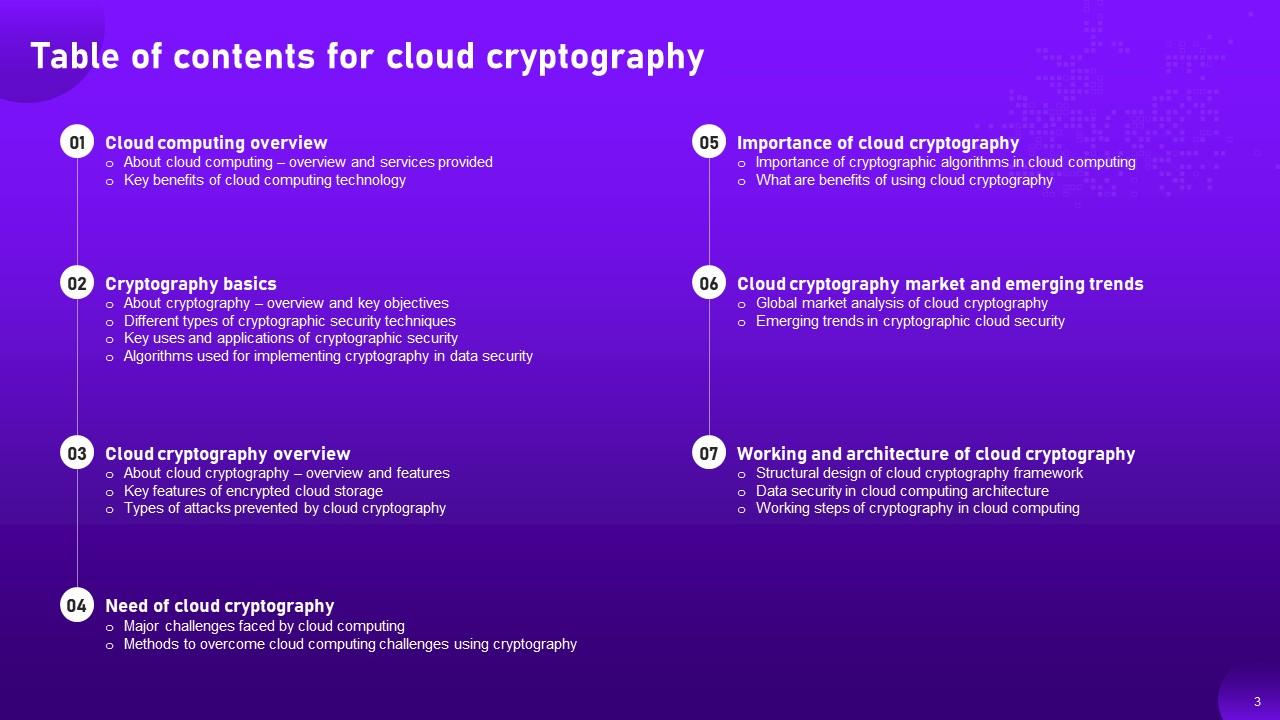
Slide 3: This slide shows a Table of Contents for the presentation.
Slide 4: It is in continuation with the previous slide.
Slide 5: This slide is an introductory slide.
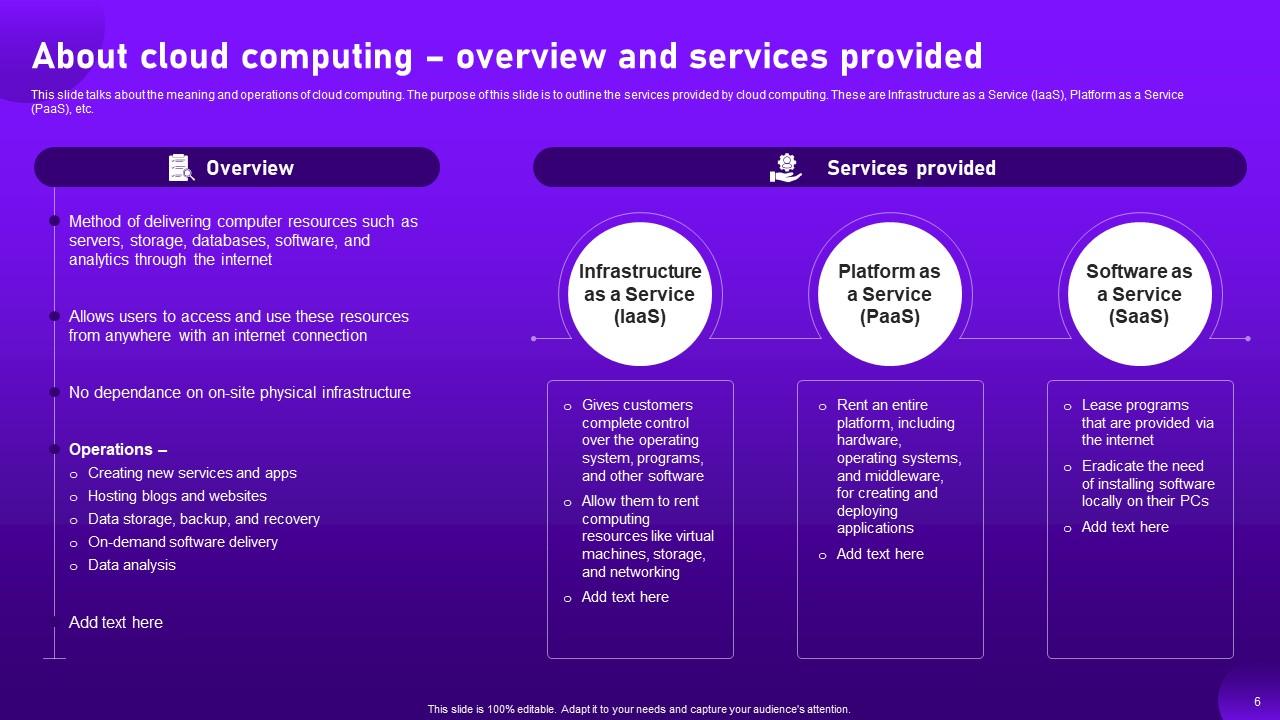
Slide 6: This slide talks about the meaning and operations of cloud computing.
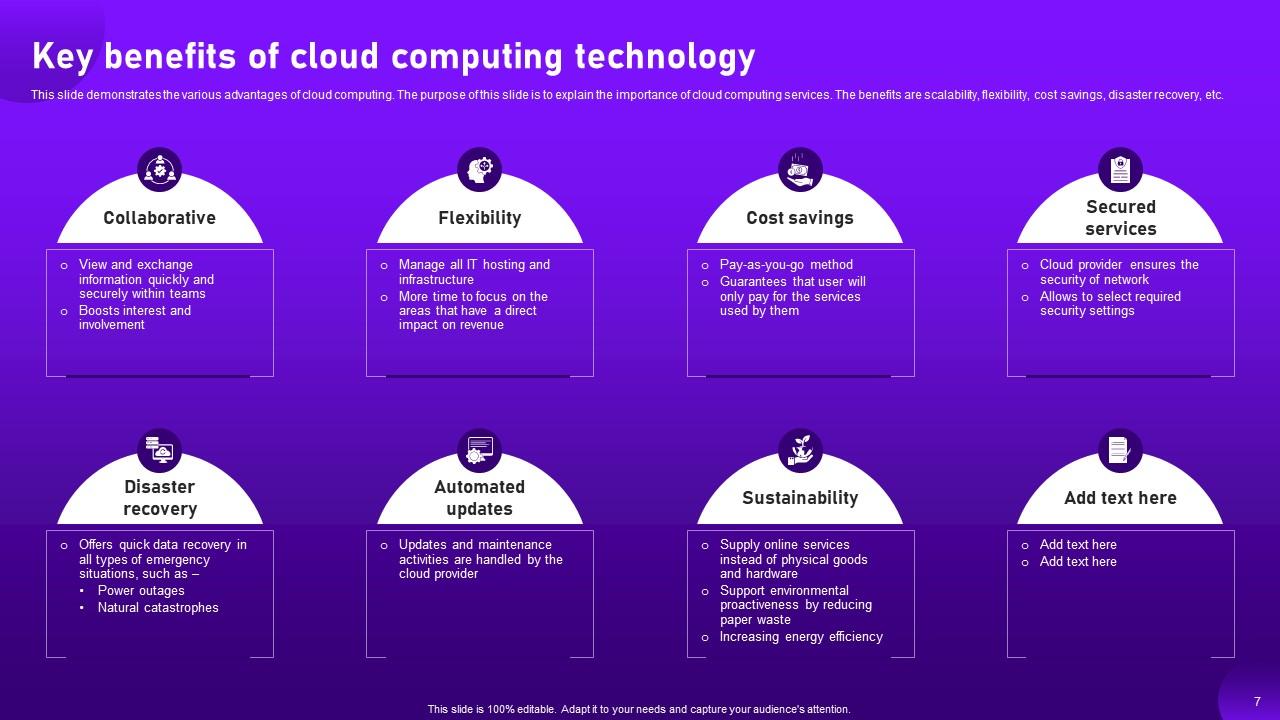
Slide 7: This slide demonstrates the various advantages of cloud computing.
Slide 8: This slide is an introductory slide.
Slide 9: This slide details about the concept of cryptography to secure the information sent to the recipient.
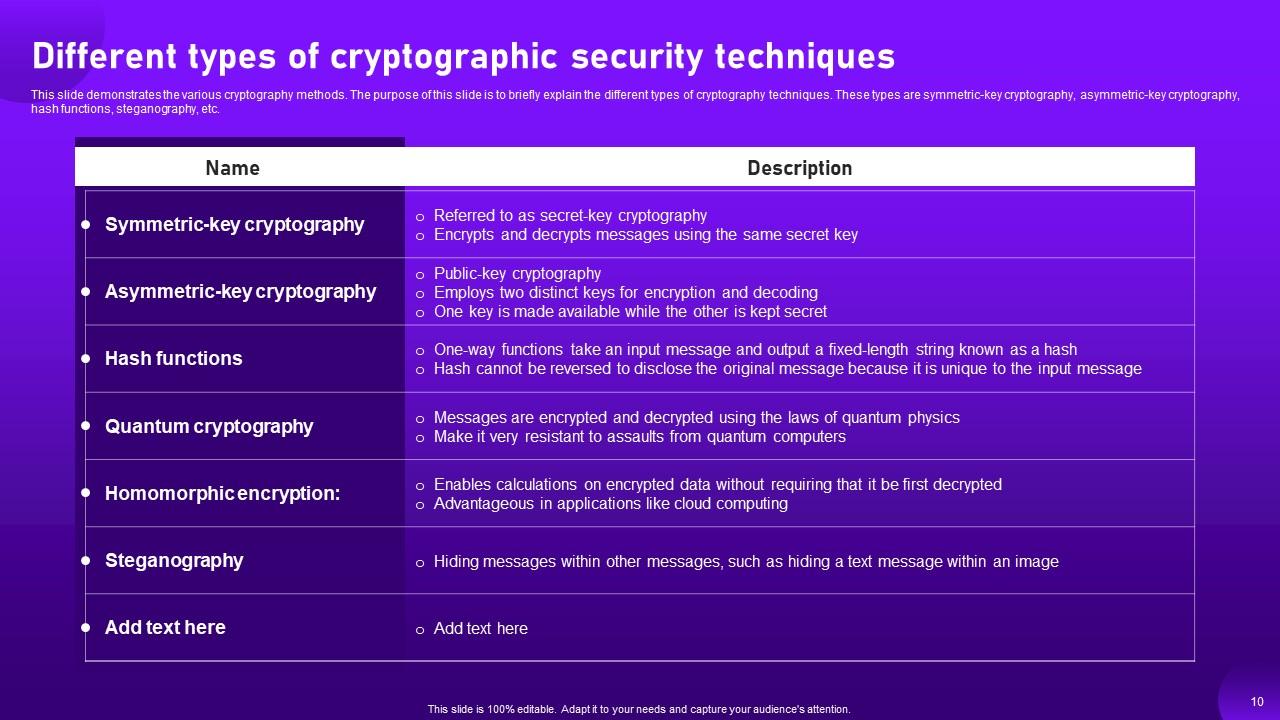
Slide 10: This slide demonstrates the various cryptography methods.
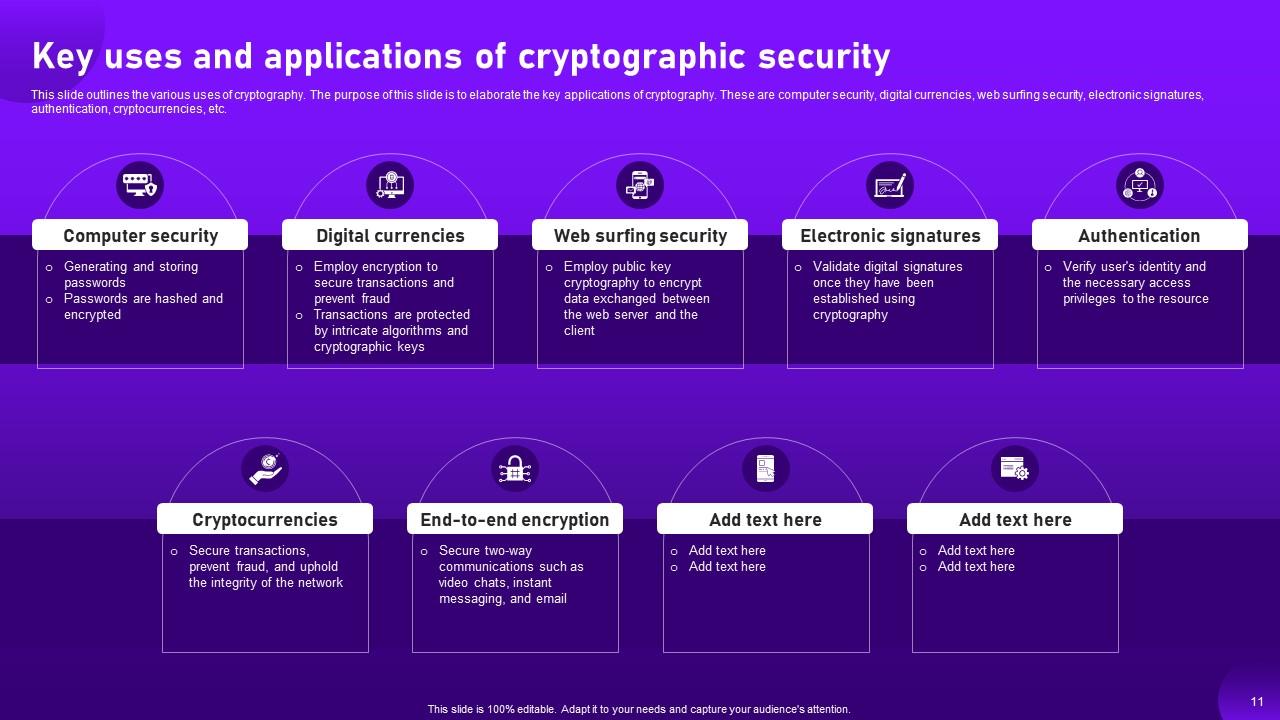
Slide 11: This slide outlines the various uses of cryptography.
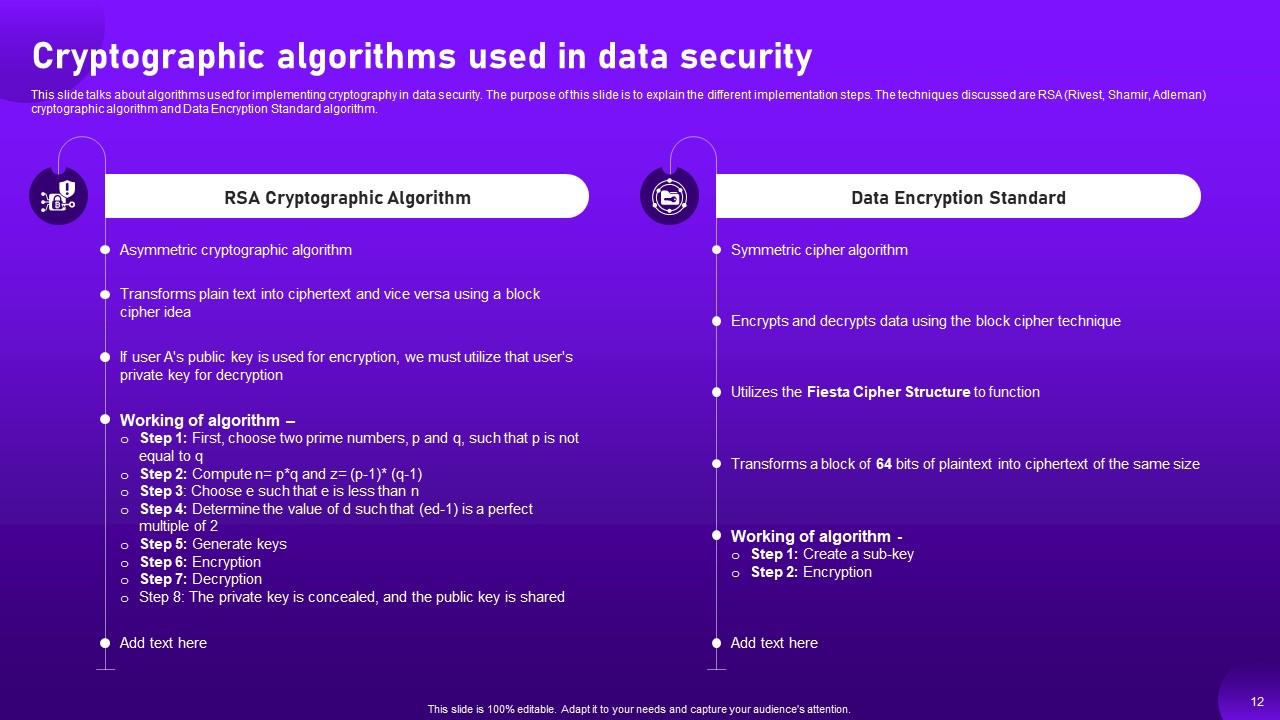
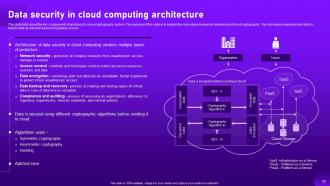
Slide 12: This slide shows about algorithms used for implementing cryptography in data security.
Slide 13: This slide is an introductory slide.
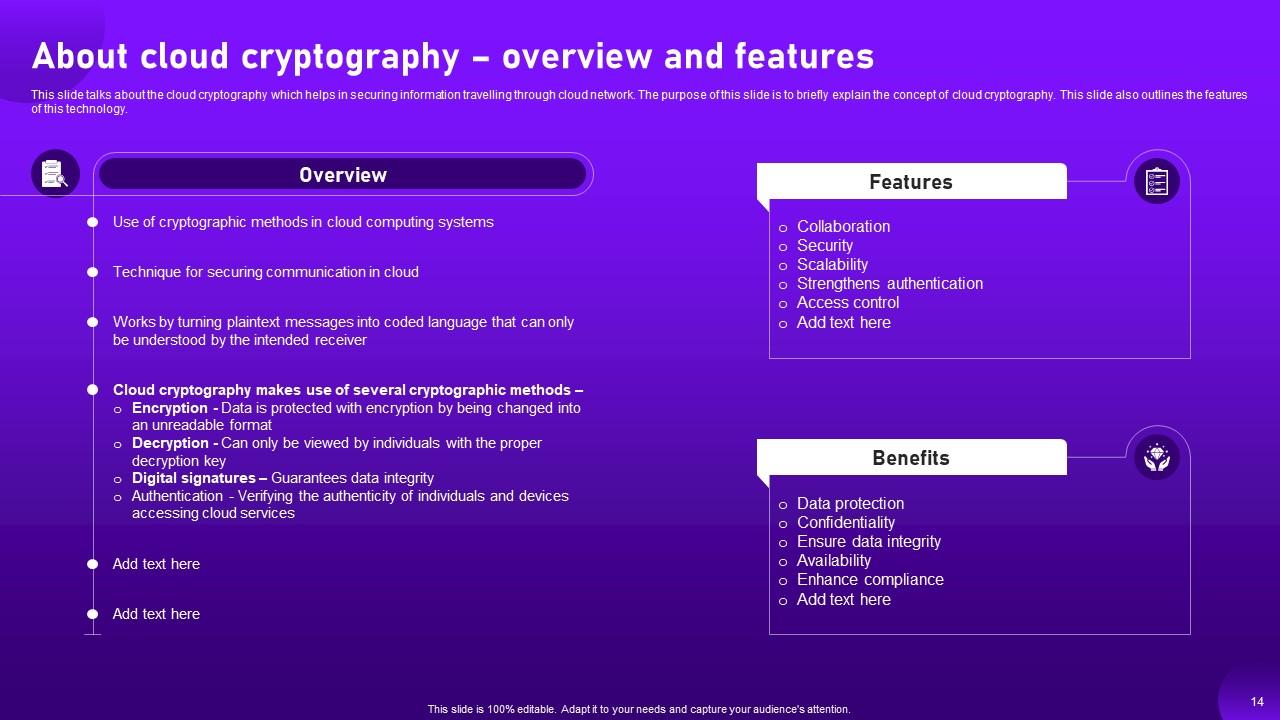
Slide 14: This slide showcases about the cloud cryptography which helps in securing information travelling through cloud network.
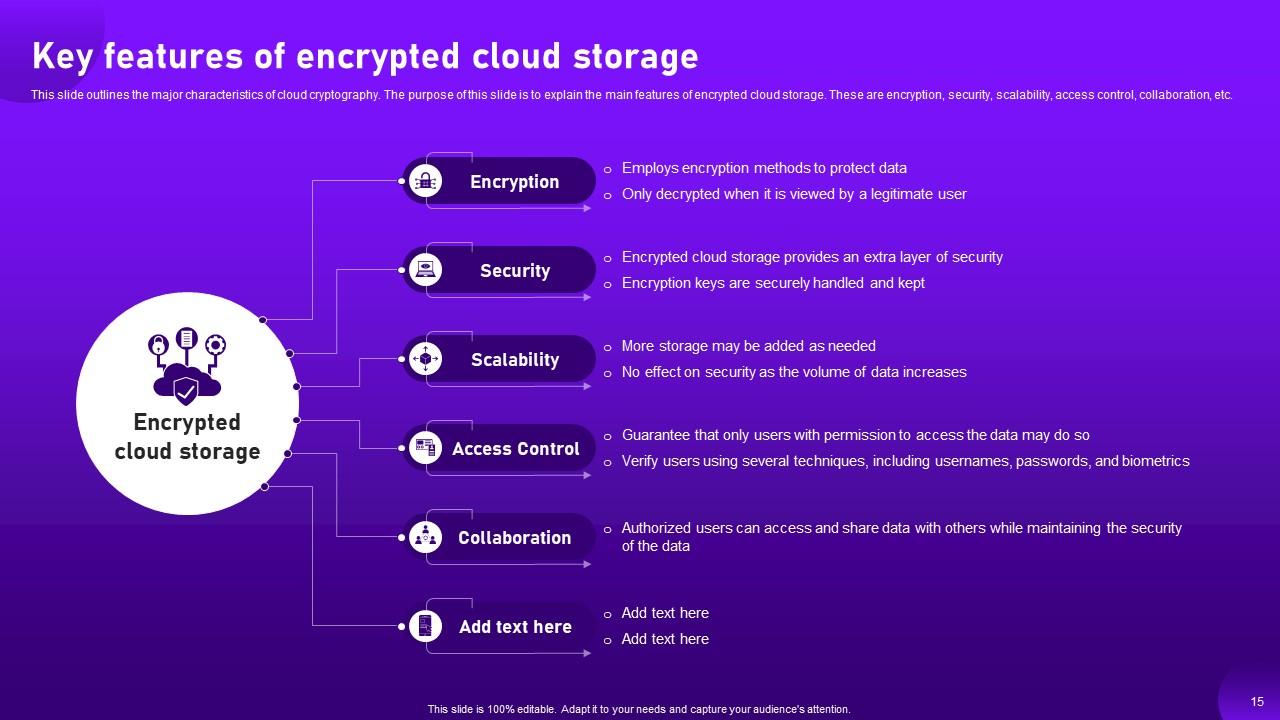
Slide 15: This slide outlines the major characteristics of cloud cryptography.
Slide 16: This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks.
Slide 17: This slide is an introductory slide.
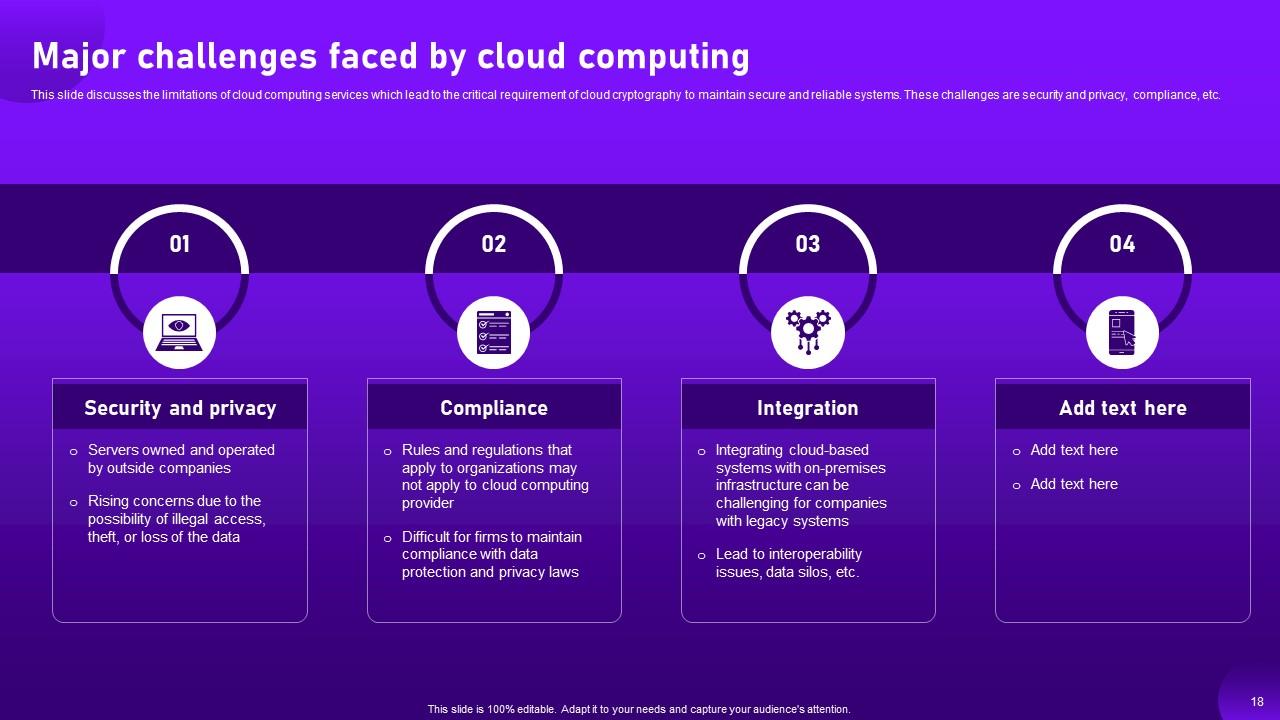
Slide 18: This slide discusses the limitations of cloud computing services.
Slide 19: The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges.
Slide 20: This slide is an introductory slide.
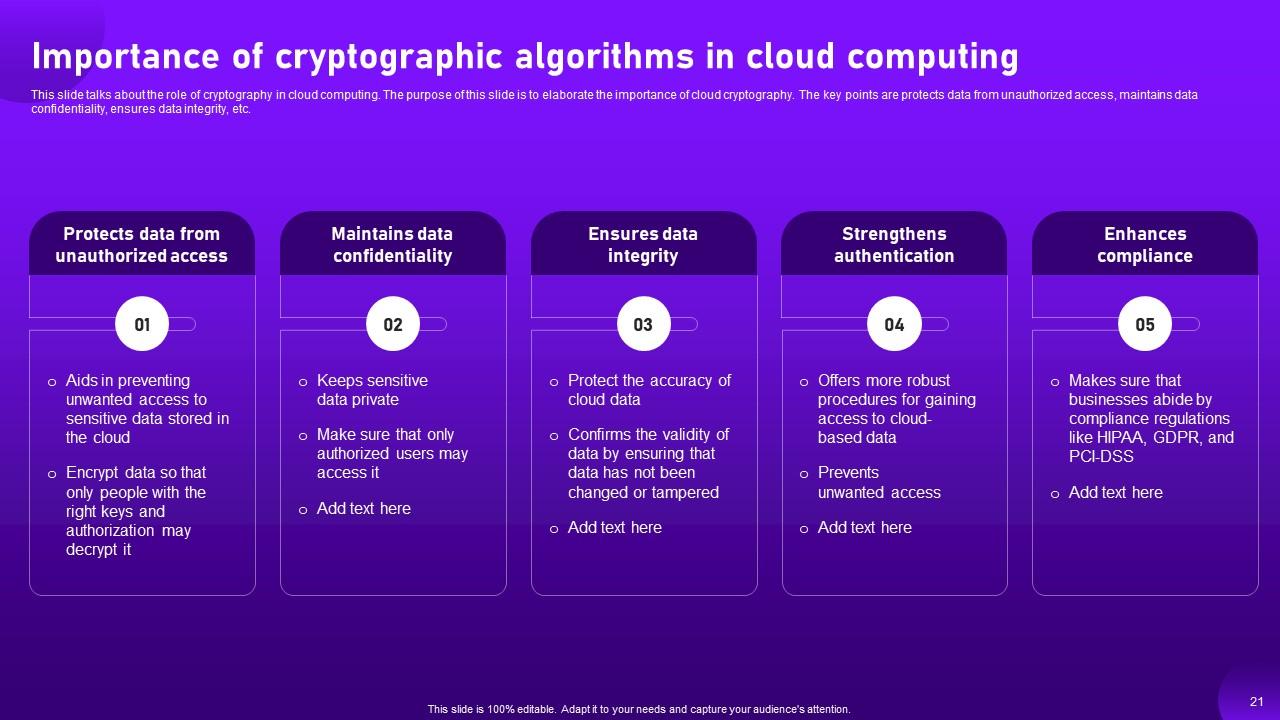
Slide 21: This slide entails about the role of cryptography in cloud computing.
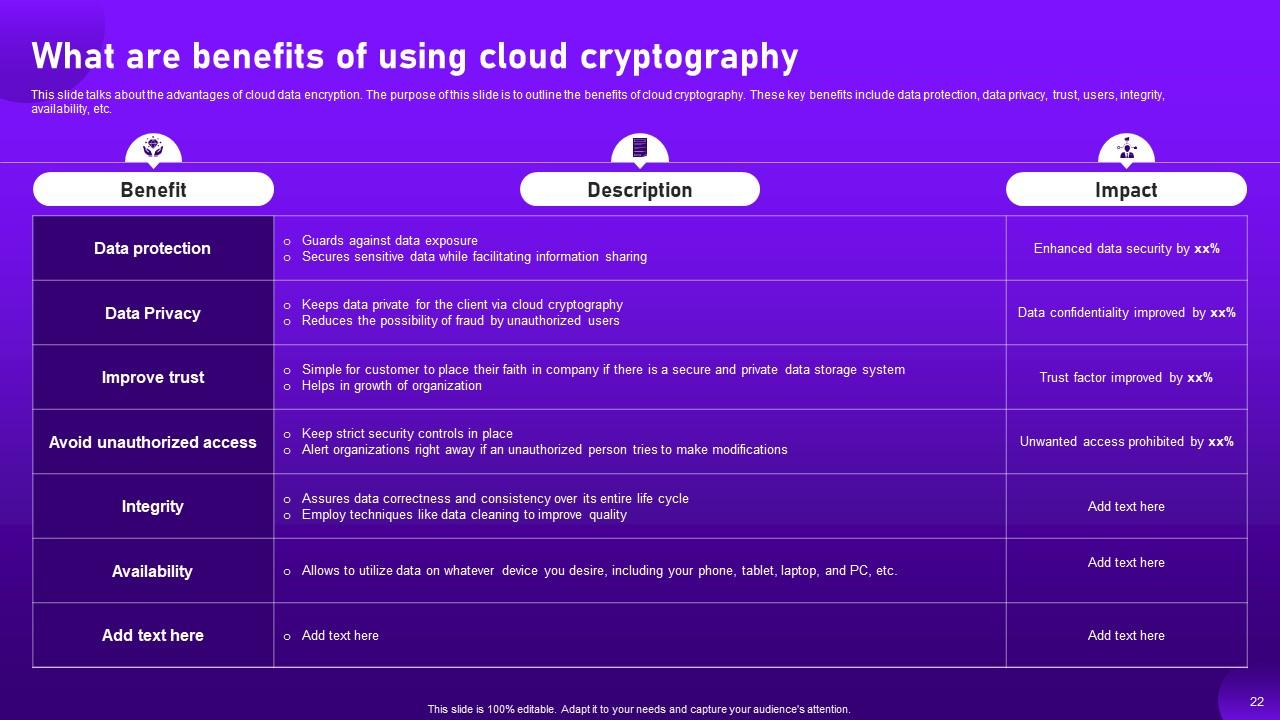
Slide 22: This slide illustrates about the advantages of cloud data encryption.
Slide 23: This slide is an introductory slide.
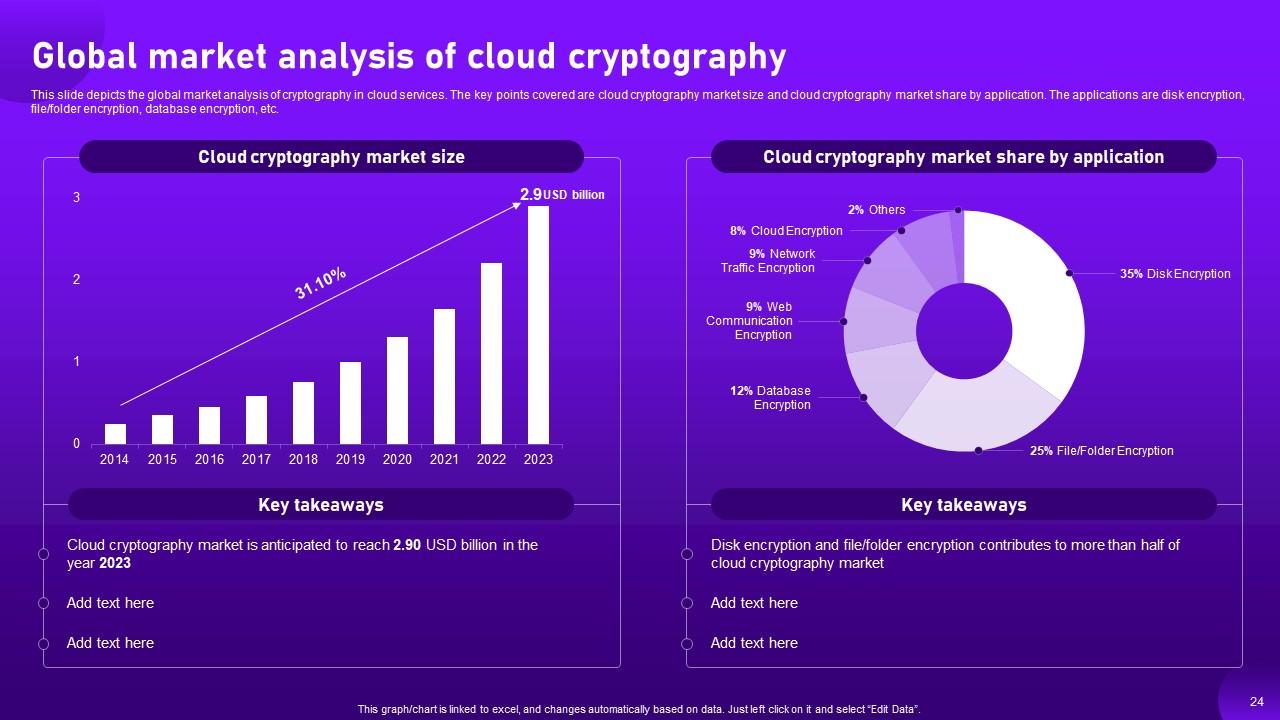
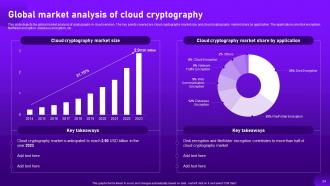
Slide 24: This slide depicts the global market analysis of cryptography in cloud services.
Slide 25: This slide describes the cloud cryptography trends.
Slide 26: This slide is an introductory slide.
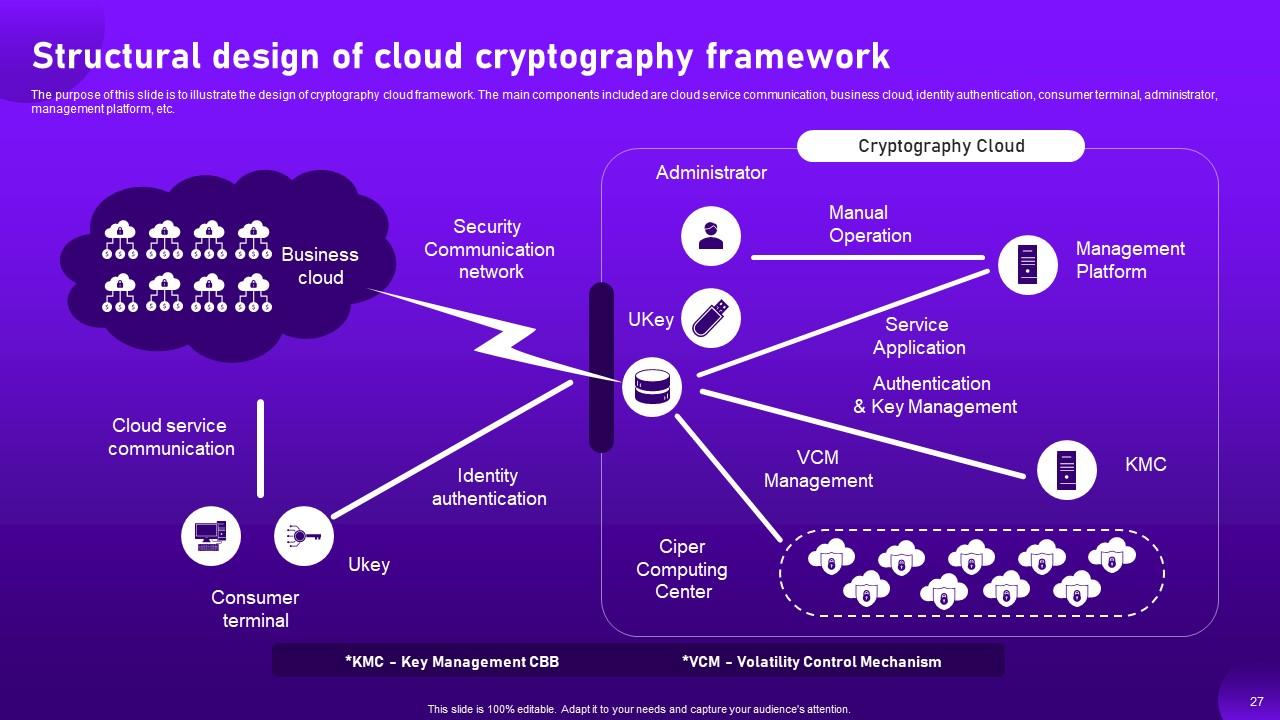
Slide 27: The purpose of this slide is to illustrate the design of cryptography cloud framework.
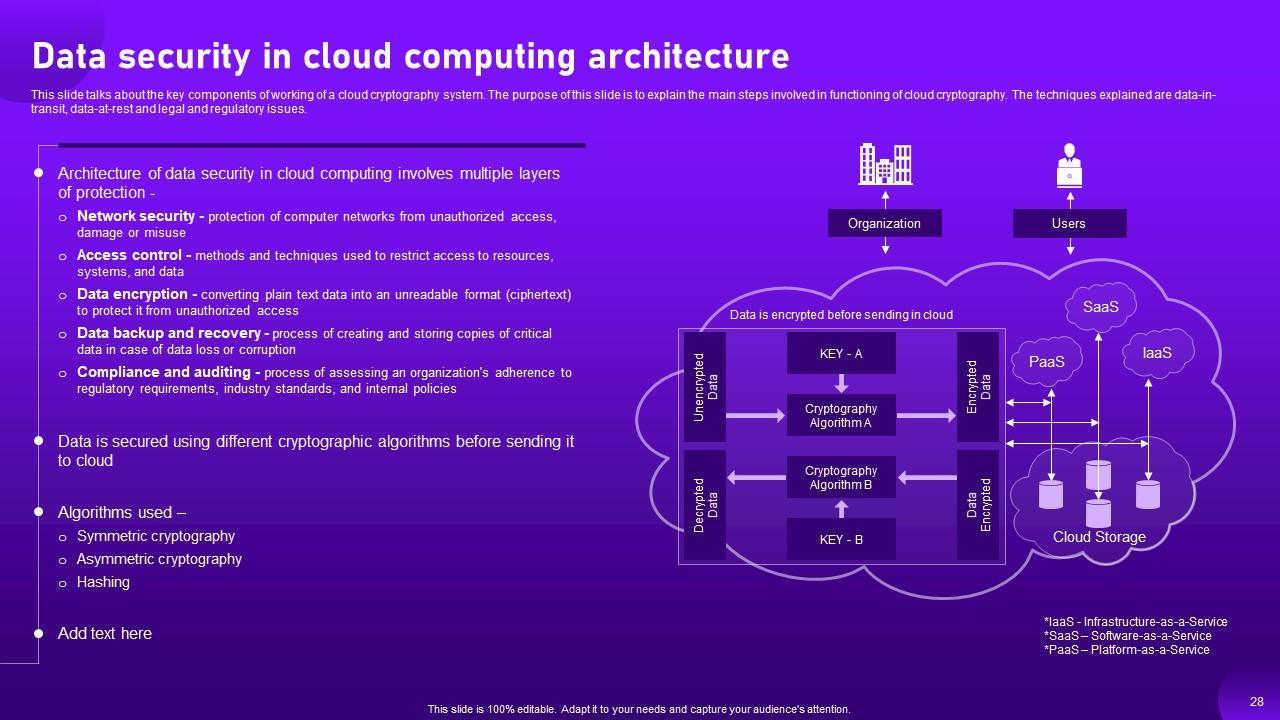
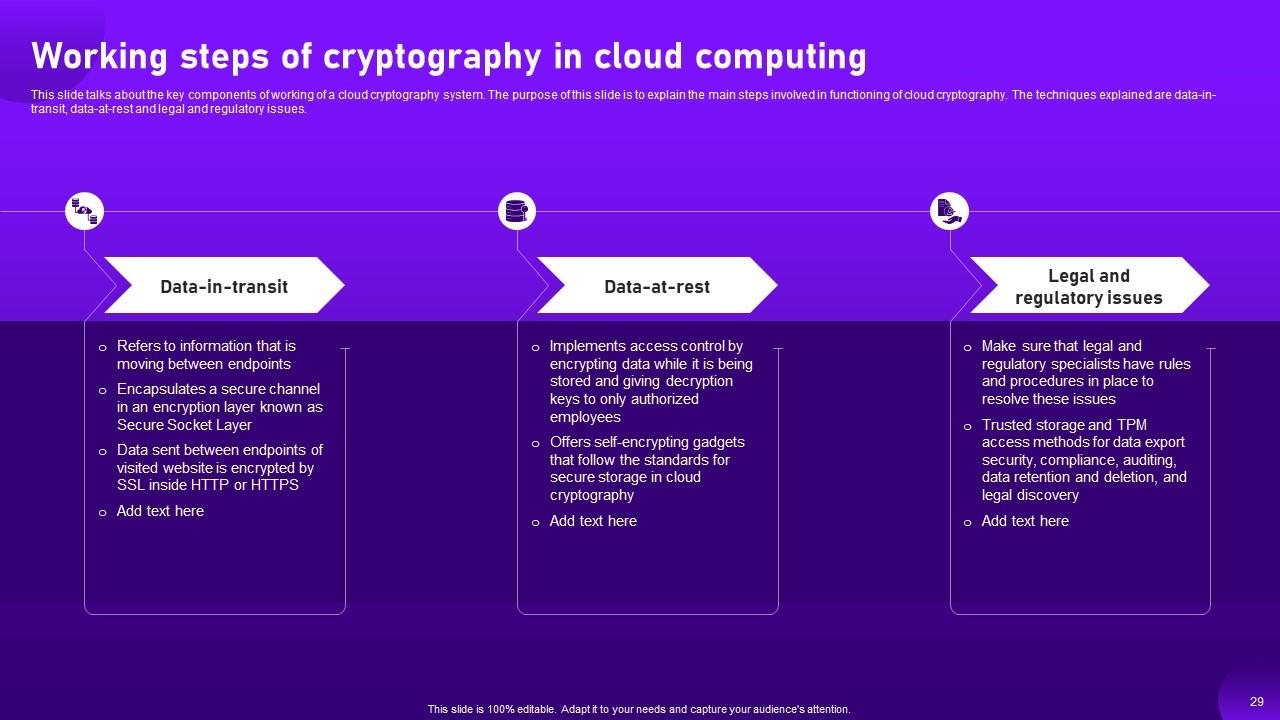
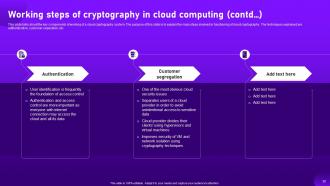
Slide 28: This slide highlights about the key components of working of a cloud cryptography system.
Slide 29: This slide showcases about the key components of working of a cloud cryptography system.
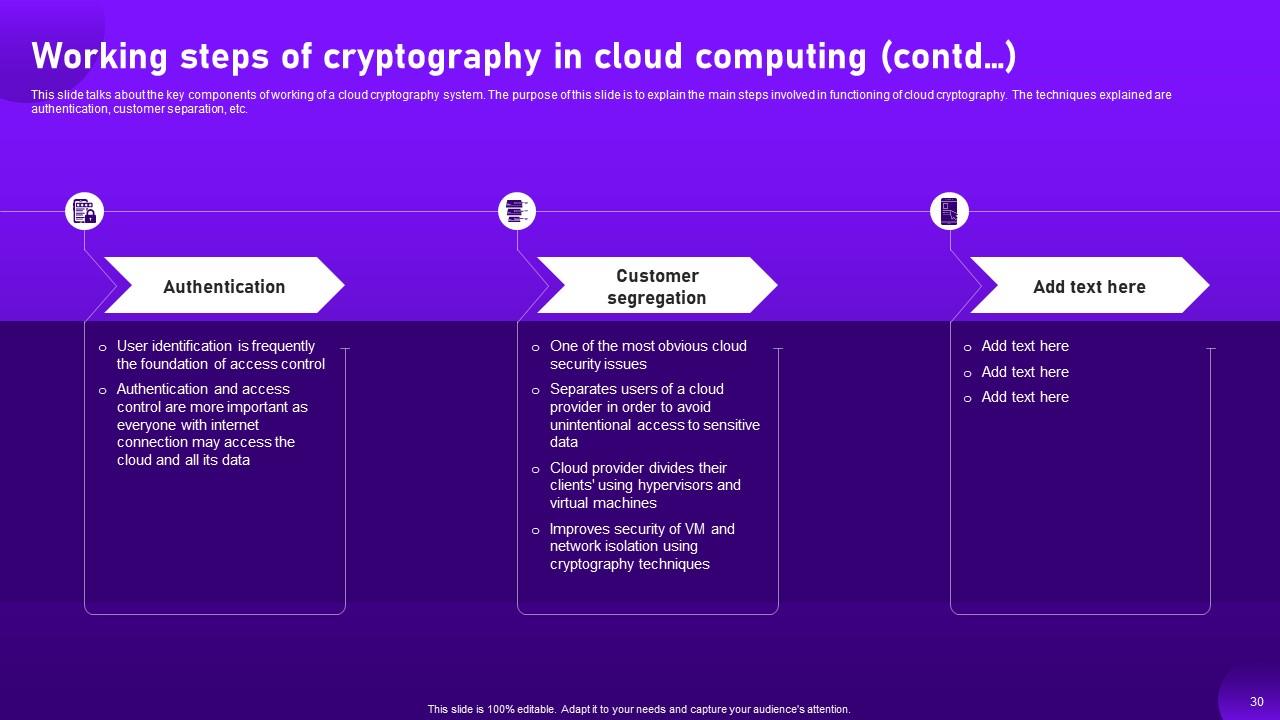
Slide 30: This slide talks about the key components of working of a cloud cryptography system.
Slide 31: This slide is an introductory slide.
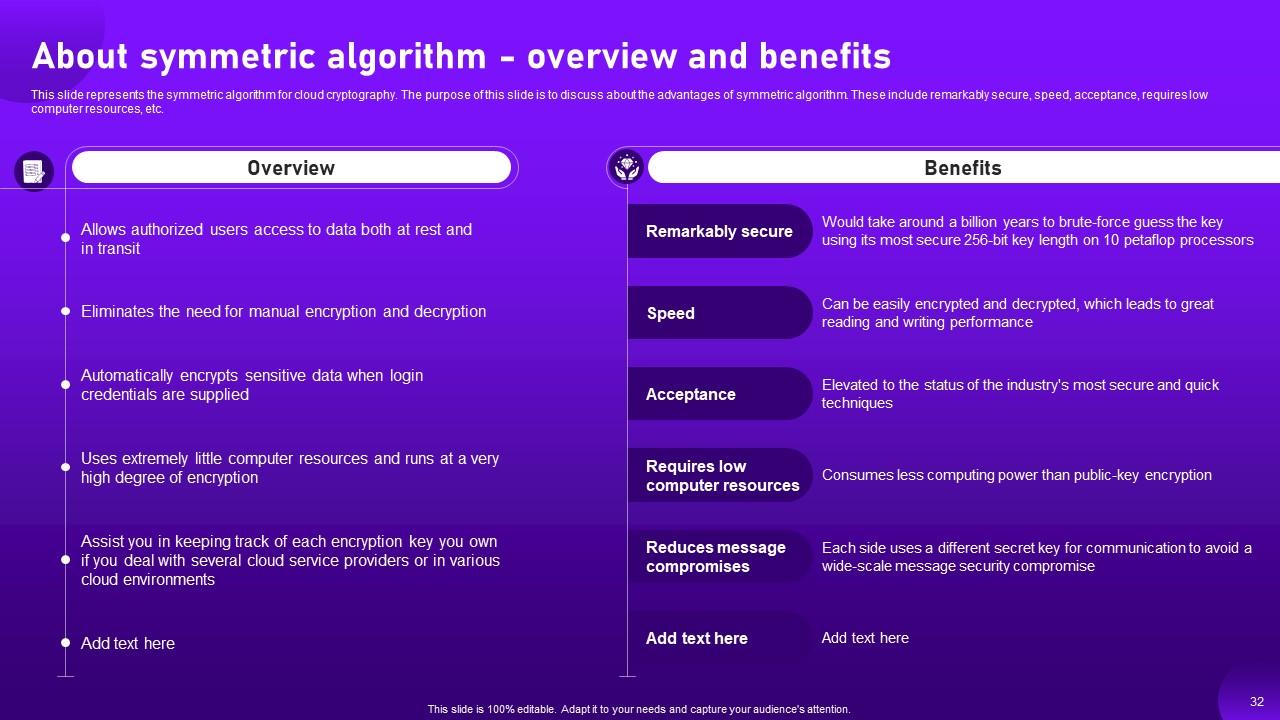
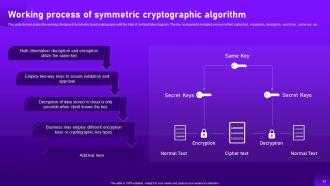
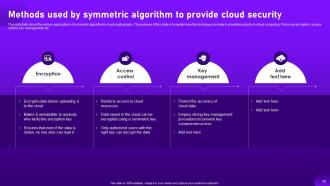
Slide 32: This slide caters to the symmetric algorithm for cloud cryptography.
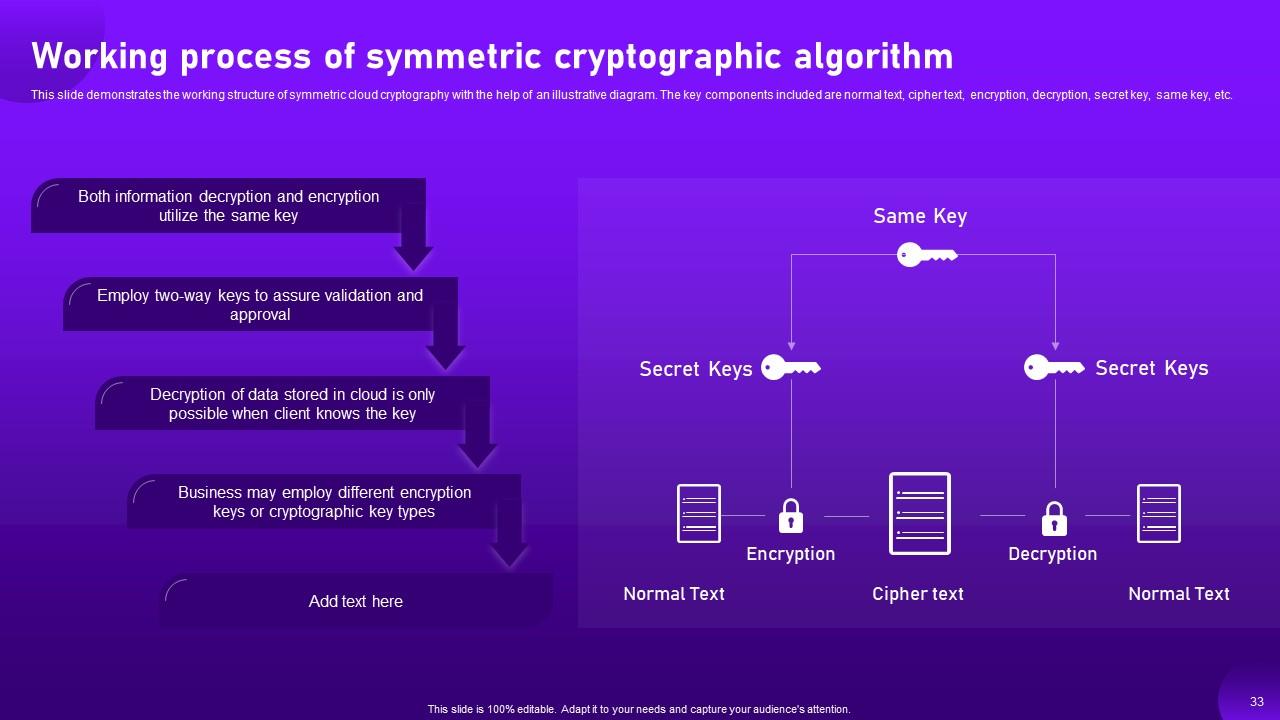
Slide 33: This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram.
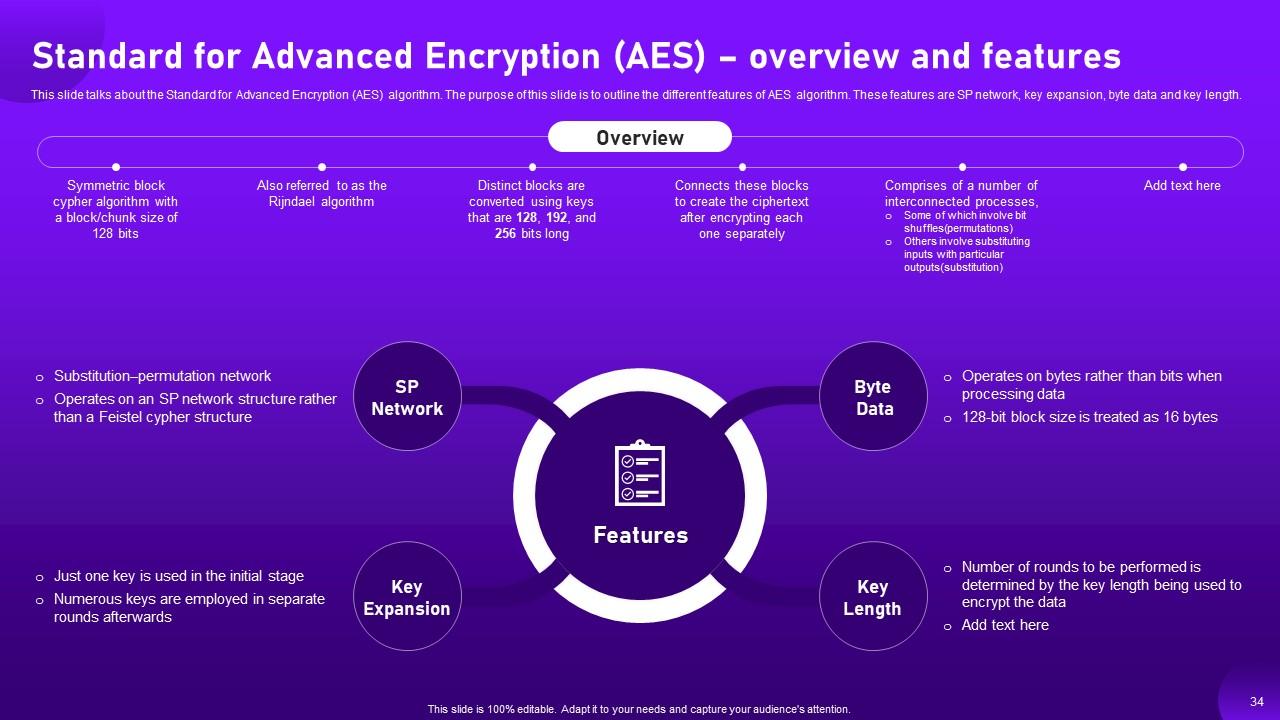
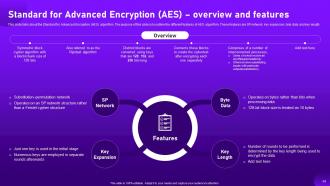
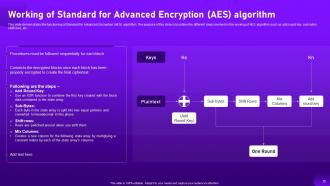
Slide 34: This slide talks about the Standard for Advanced Encryption (AES) algorithm.
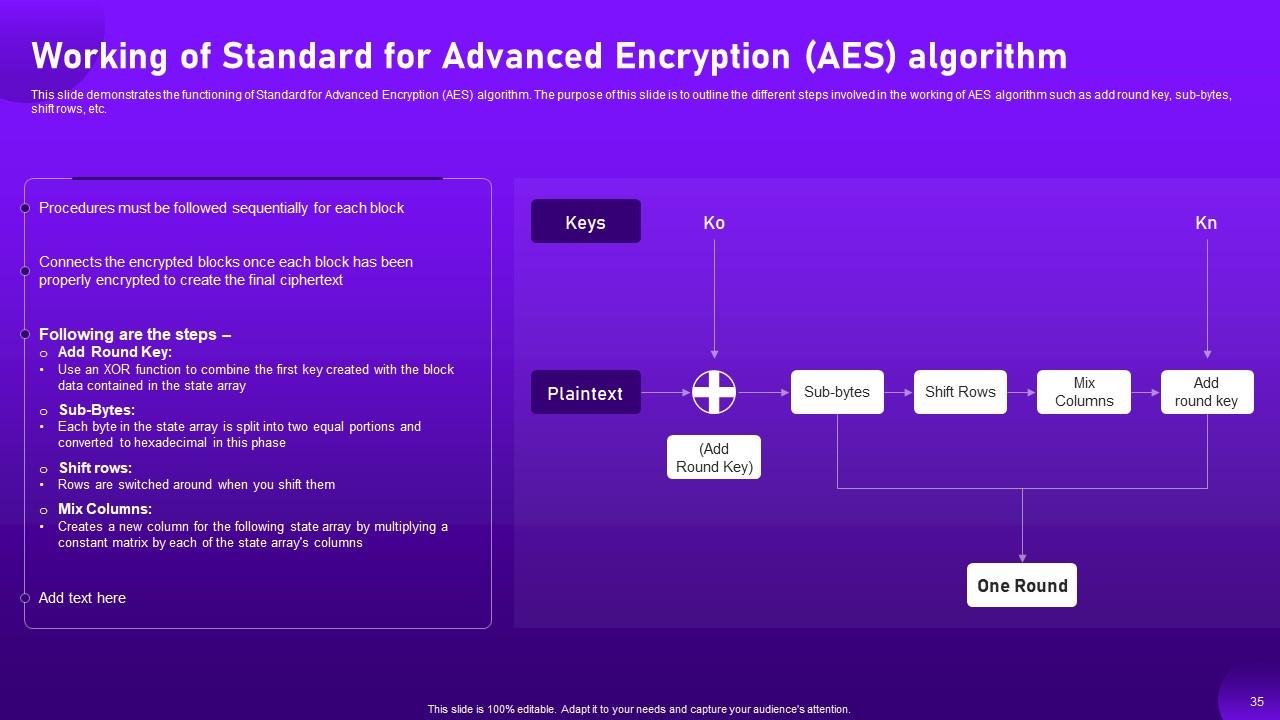
Slide 35: This slide describes the functioning of Standard for Advanced Encryption (AES) algorithm.
Slide 36: This slide represents the uses of Standard for Advanced Encryption (AES) algorithm.
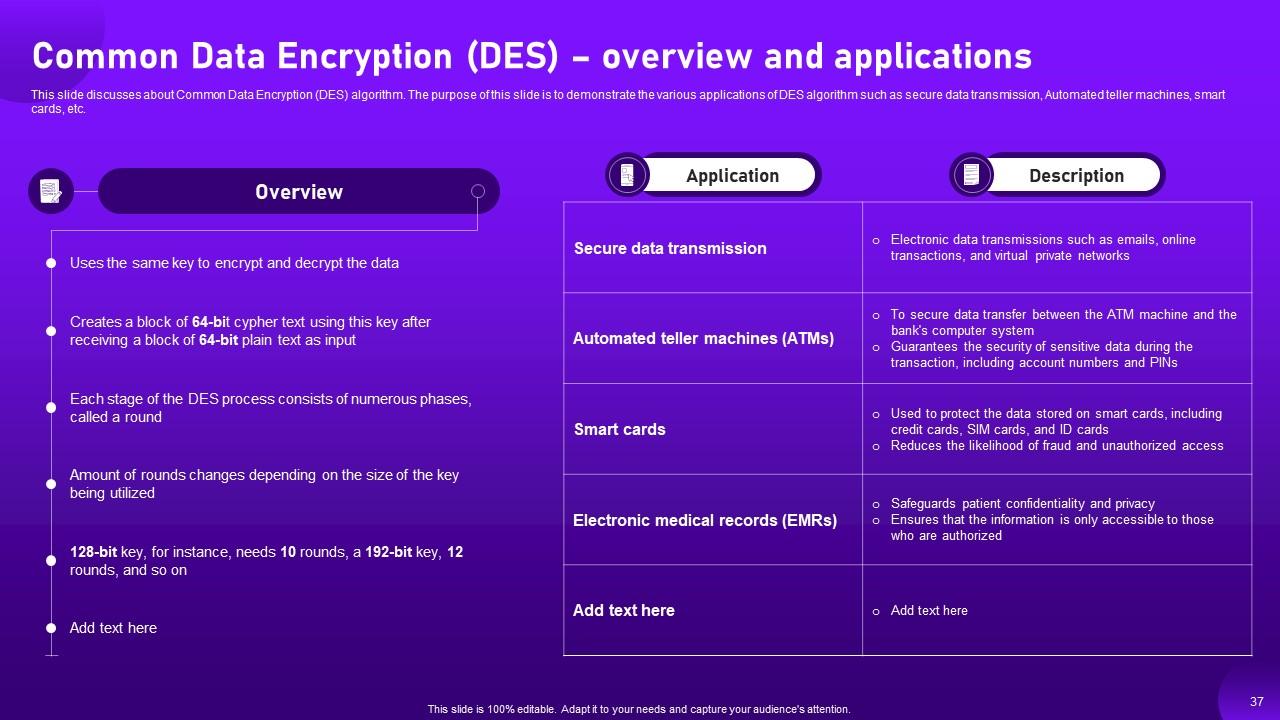
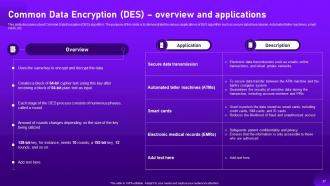
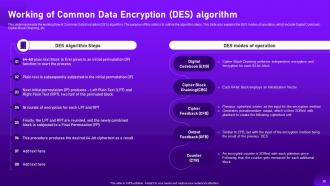
Slide 37: This slide discusses about Common Data Encryption (DES) algorithm.
Slide 38: This slide presents the working flow of Common Data Encryption (DES) algorithm.
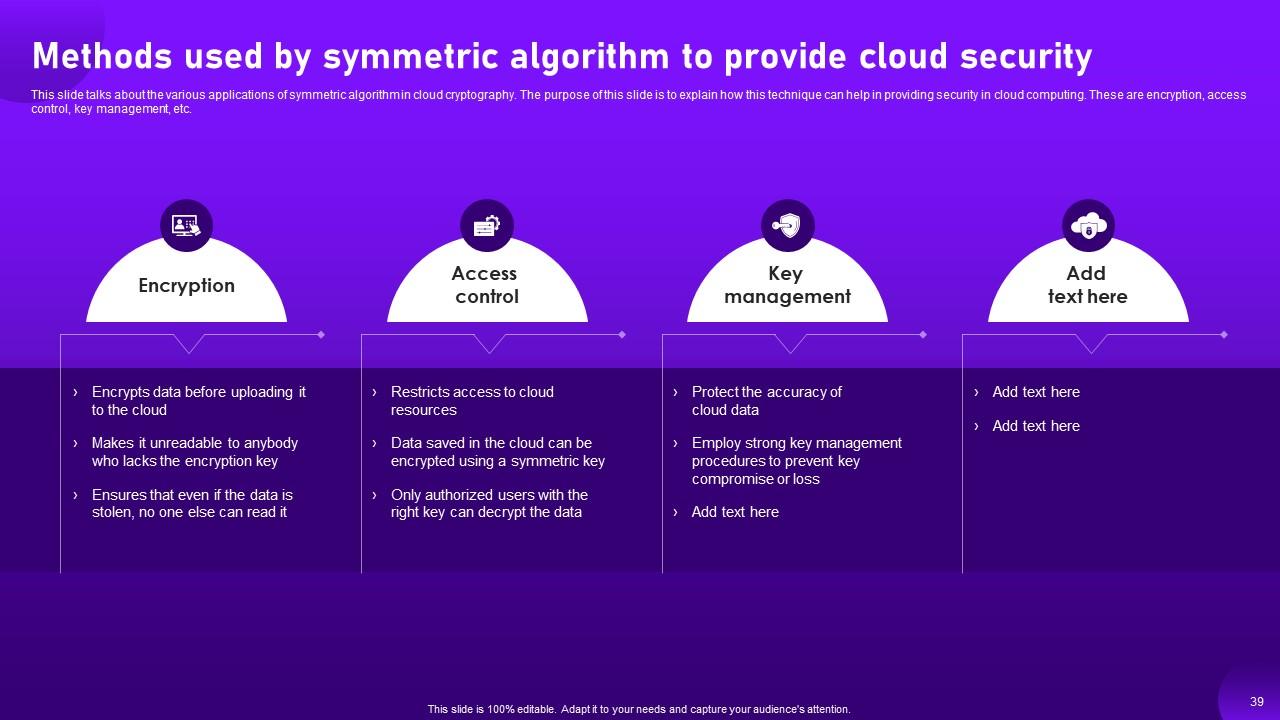
Slide 39: This slide contains about the various applications of symmetric algorithm in cloud cryptography.
Slide 40: This slide is an introductory slide.
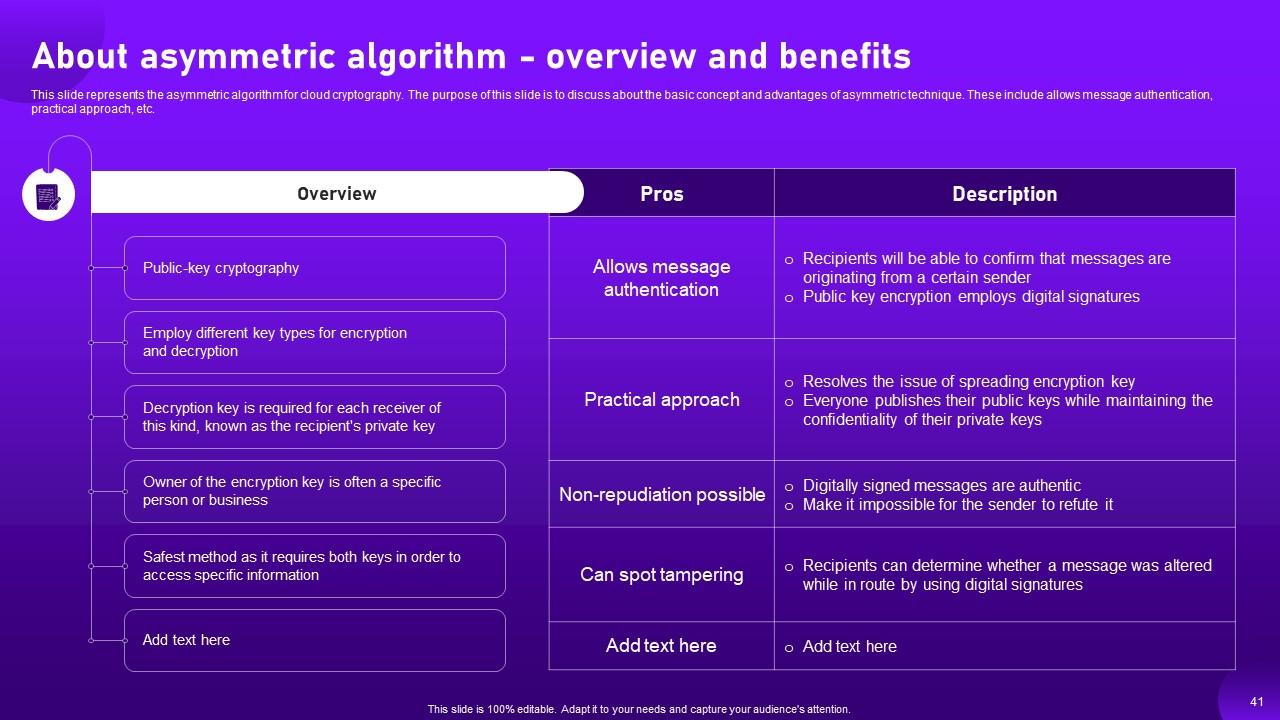
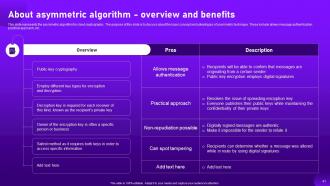
Slide 41: This slide represents the asymmetric algorithm for cloud cryptography.
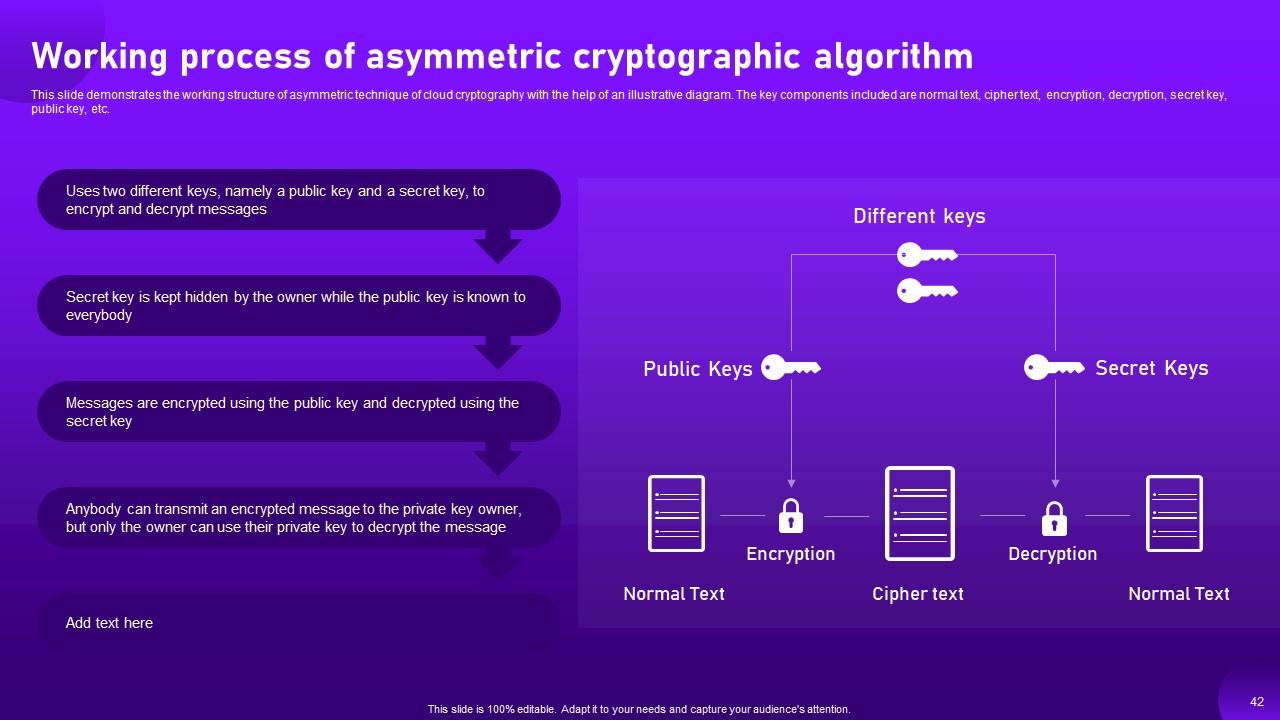
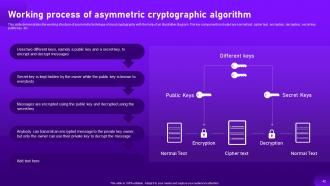
Slide 42: This slide processes the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram.
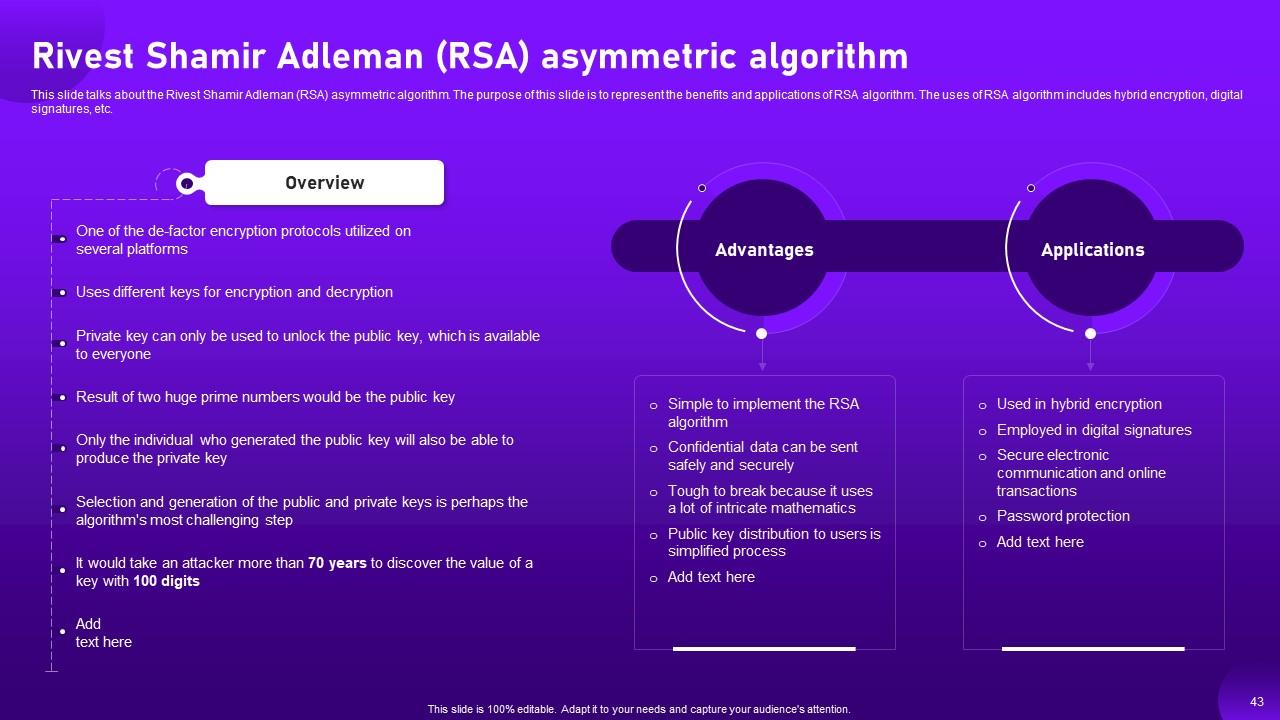
Slide 43: This slide talks about the Rivest Shamir Adleman (RSA) asymmetric algorithm.
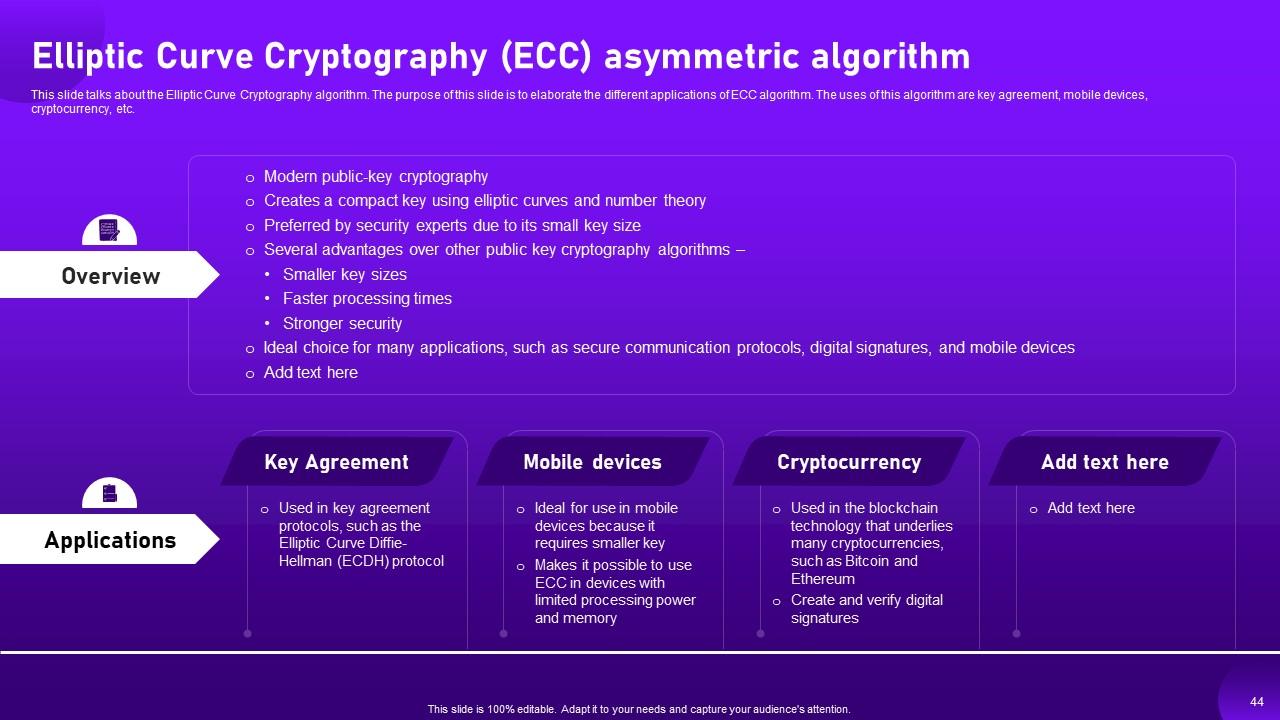
Slide 44: This slide talks about the Elliptic Curve Cryptography algorithm.
Slide 45: This slide portrays about the various applications of asymmetric algorithm in cloud cryptography.
Slide 46: This slide is an introductory slide.
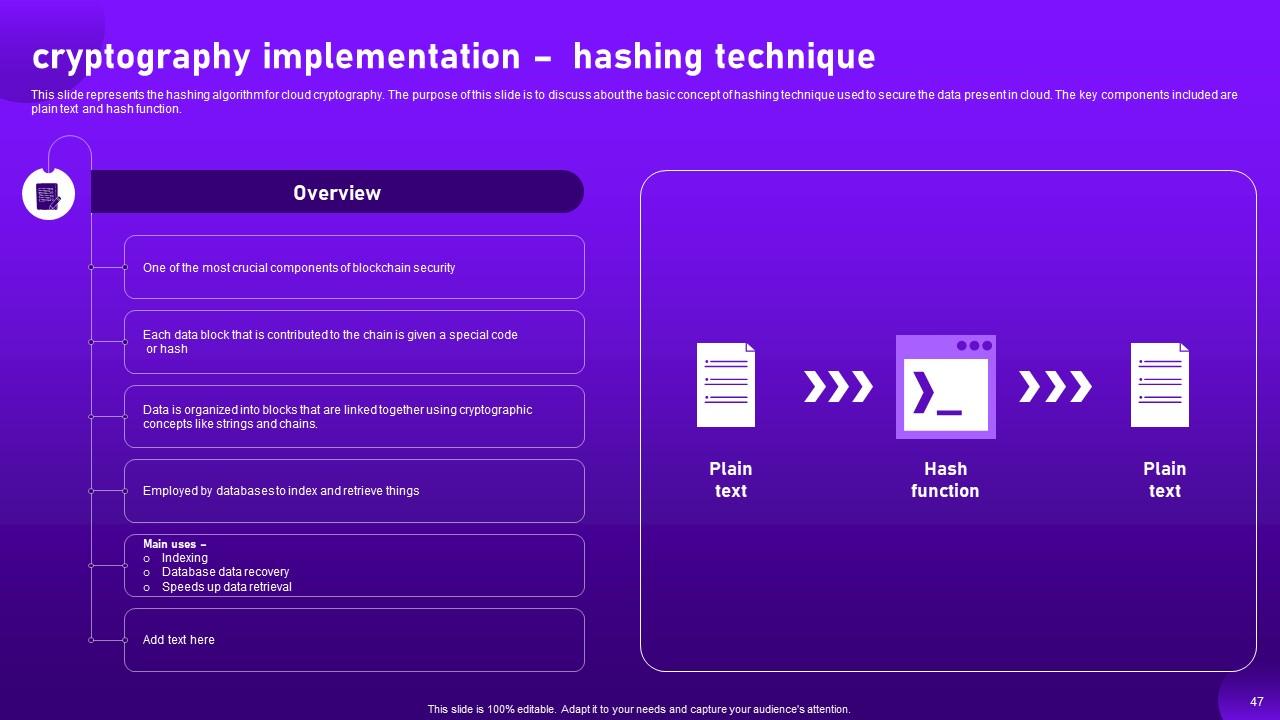
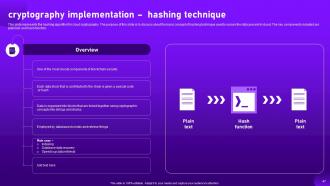
Slide 47: This slide represents the hashing algorithm for cloud cryptography.
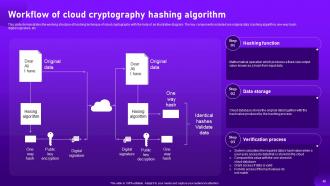
Slide 48: This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram.
Slide 49: This slide explains the working of hashing technique.
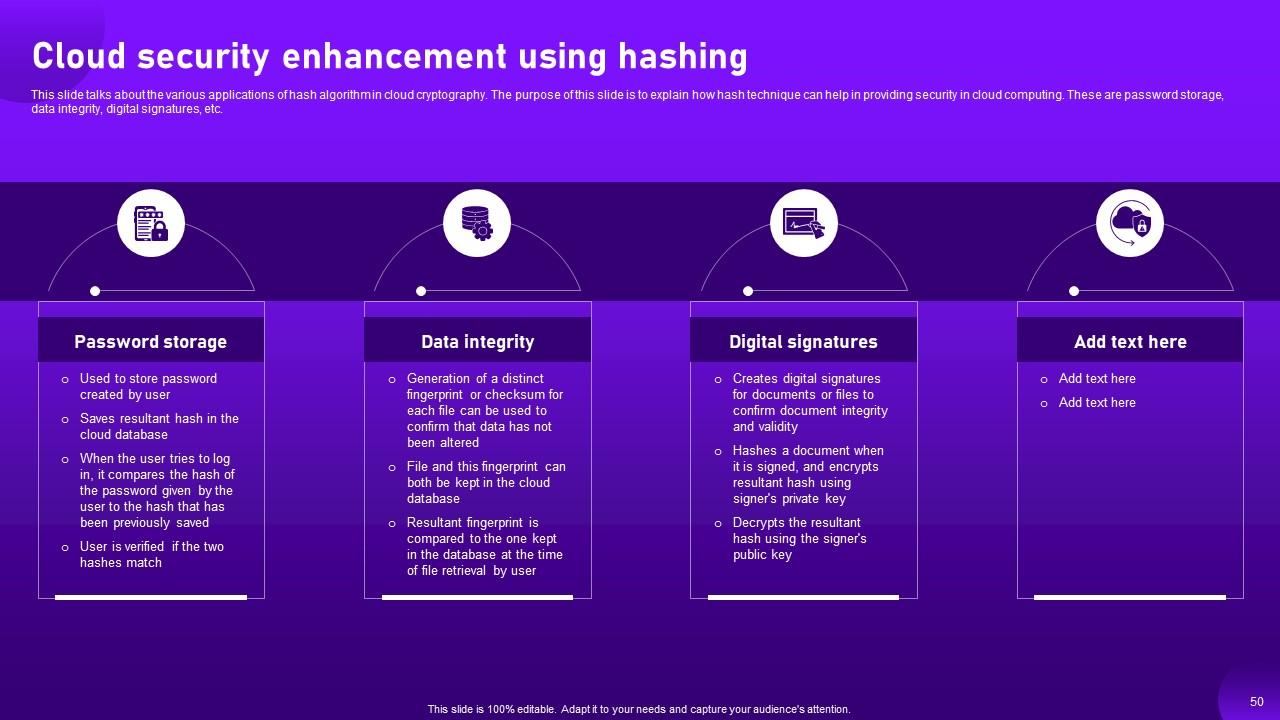
Slide 50: This slide entails about the various applications of hash algorithm in cloud cryptography.
Slide 51: This slide is an introductory slide.
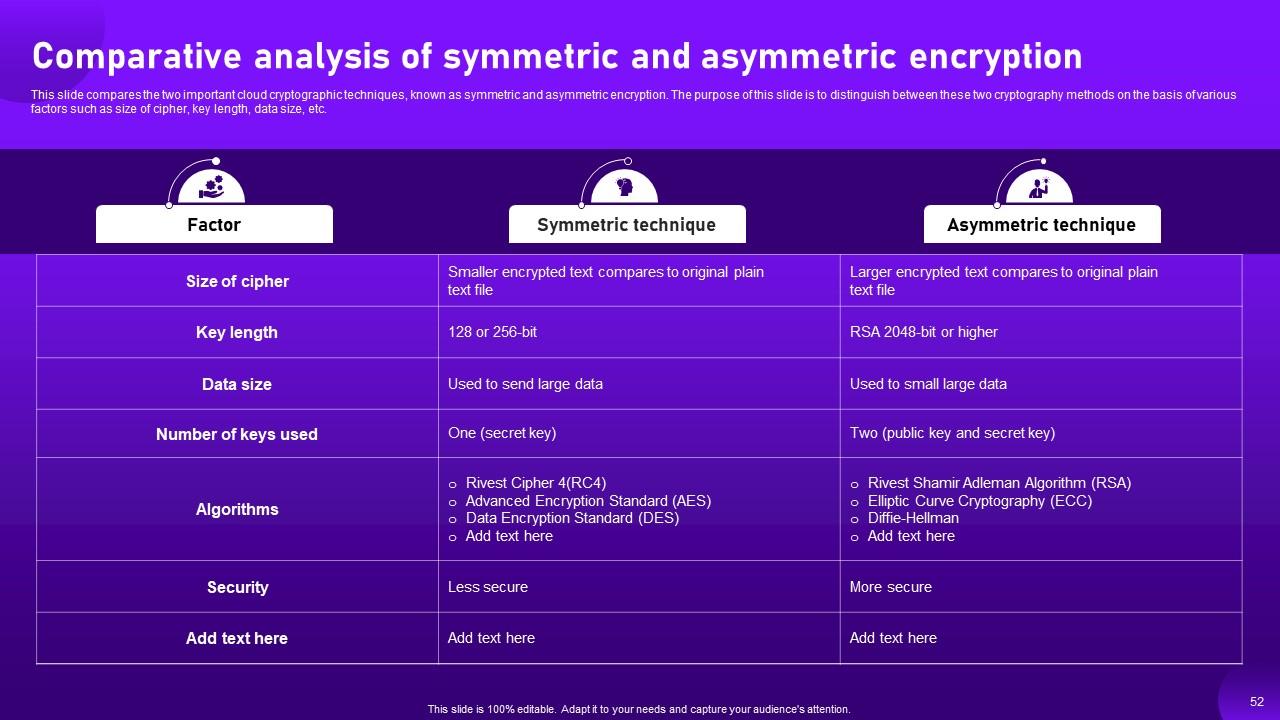
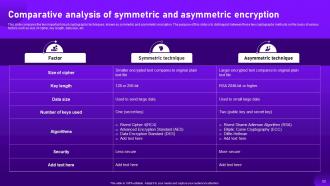
Slide 52: This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption.
Slide 53: This slide is an introductory slide.
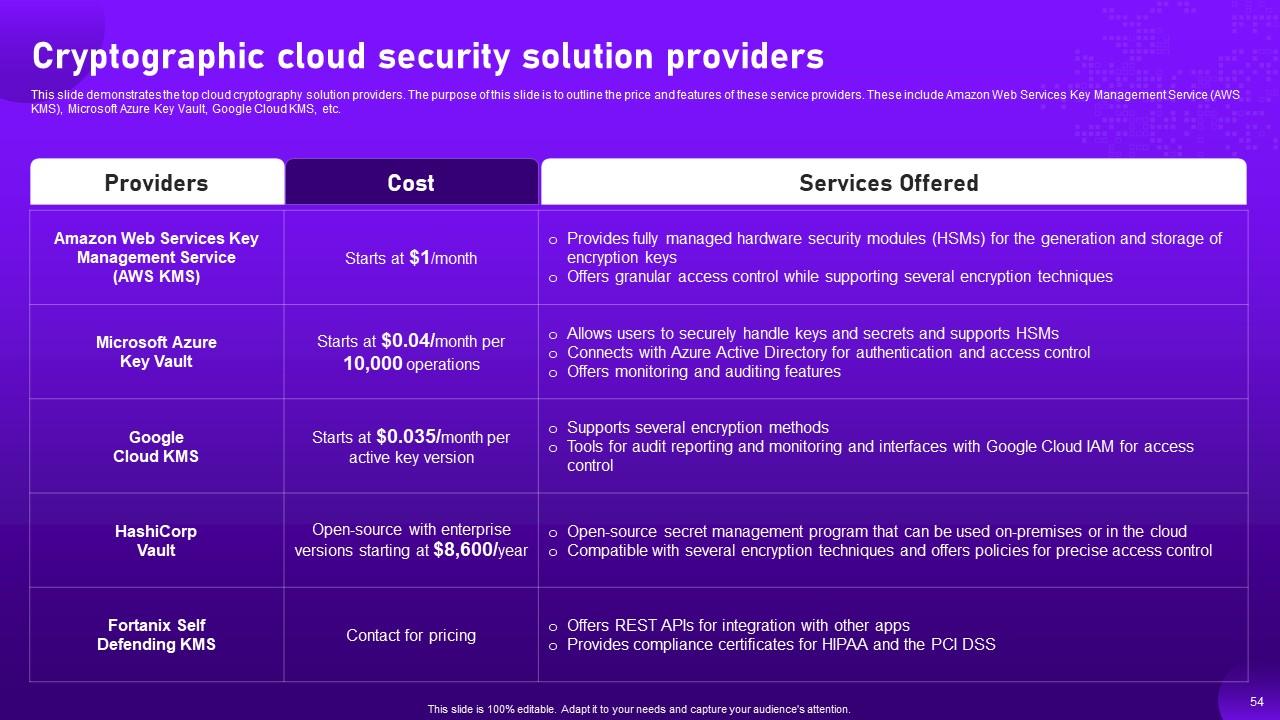
Slide 54: This slide demonstrates the top cloud cryptography solution providers.
Slide 55: This slide describes the top cloud cryptography solution providers.
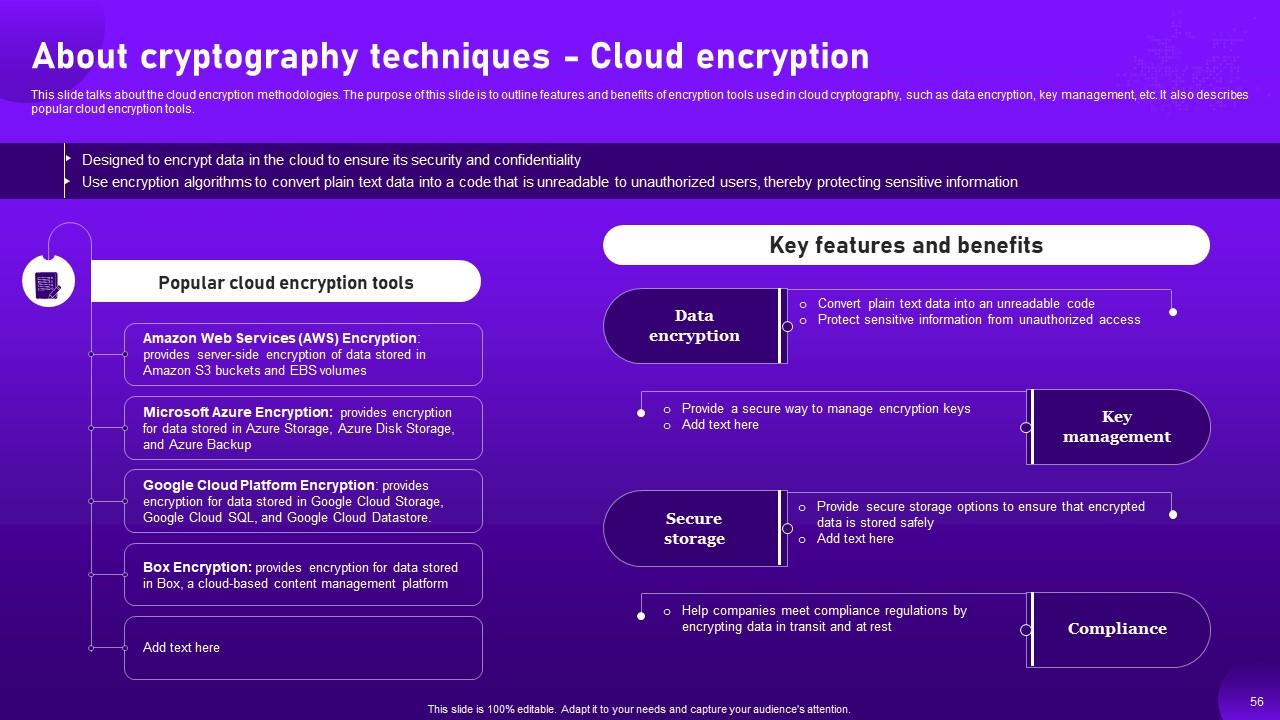
Slide 56: This slide talks about the cloud encryption methodologies.
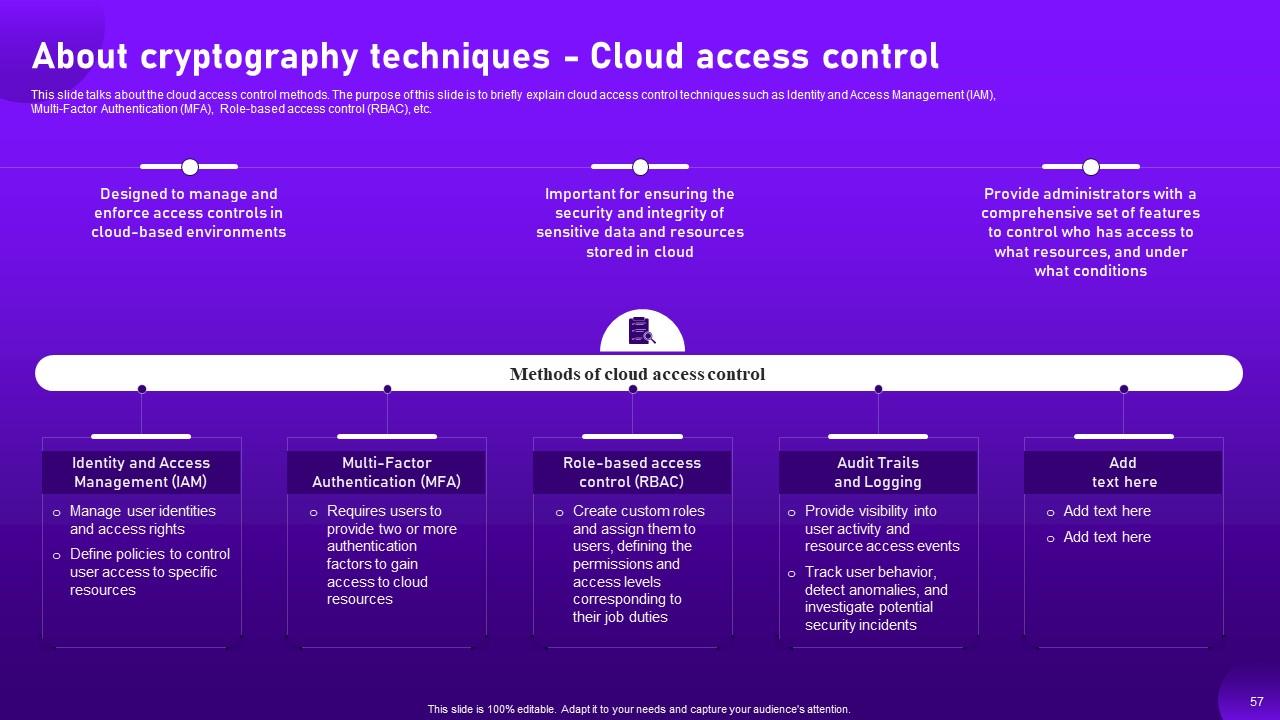
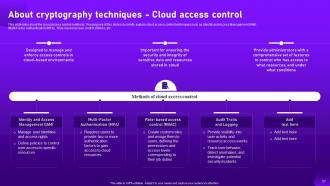
Slide 57: This slide showcases about the cloud access control methods.
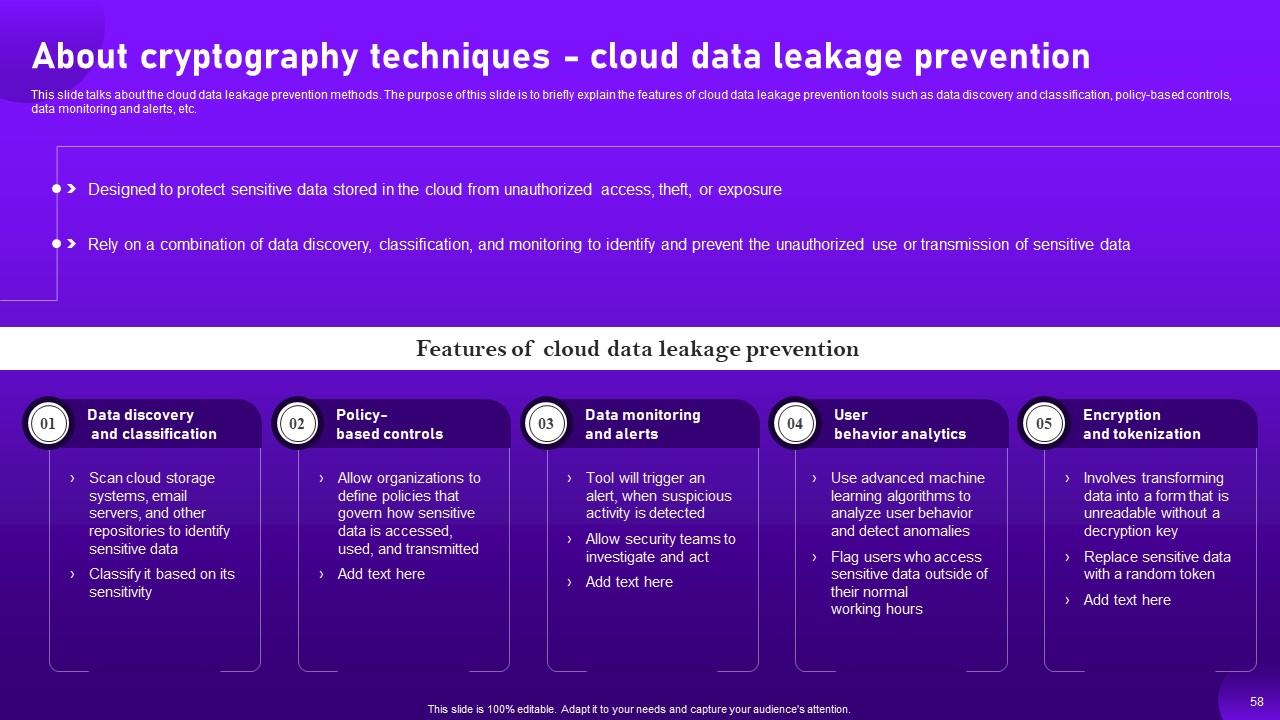
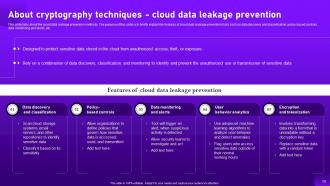
Slide 58: This slide shows about the cloud data leakage prevention methods.
Slide 59: This slide is an introductory slide.
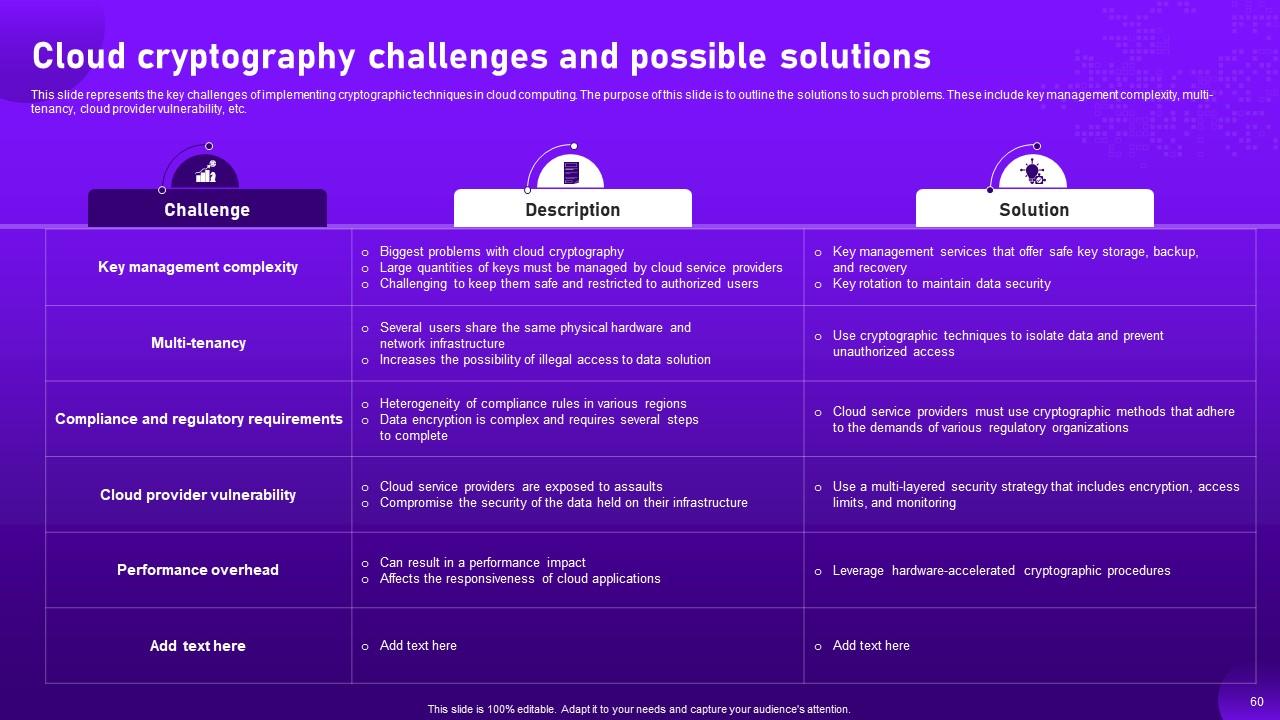
Slide 60: This slide represents the key challenges of implementing cryptographic techniques in cloud computing.
Slide 61: This slide is an introductory slide.
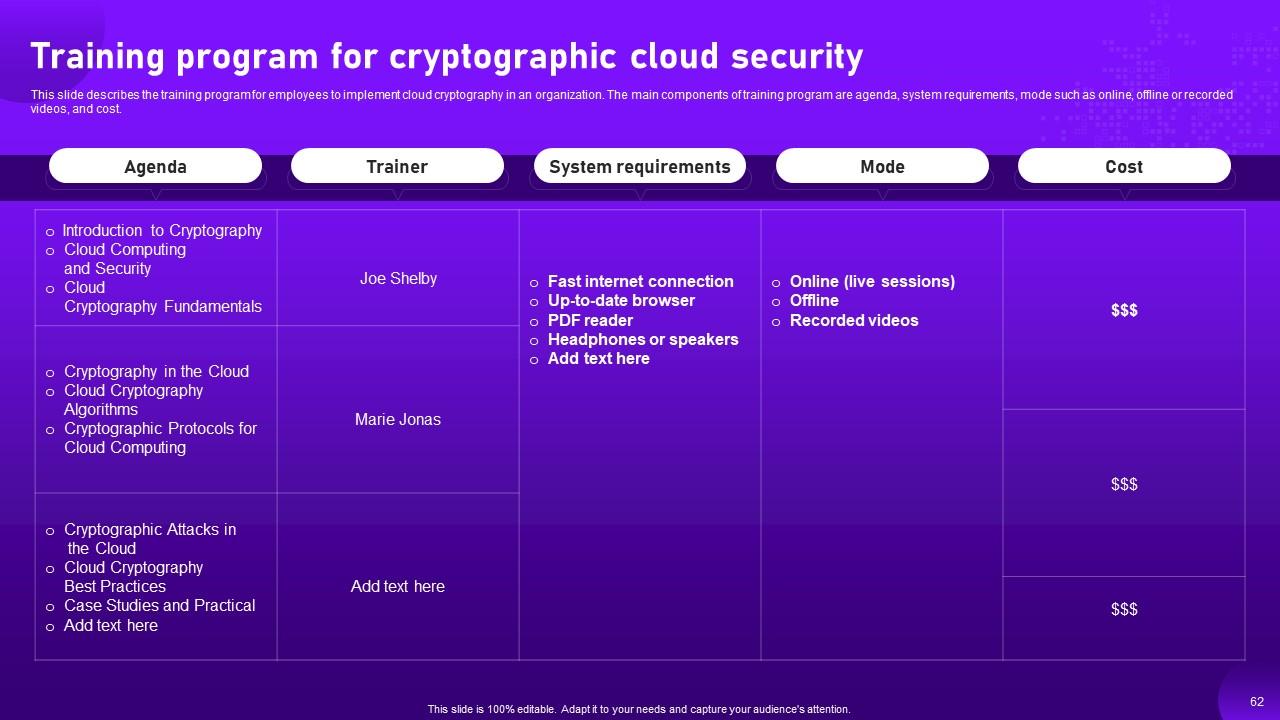
Slide 62: This slide describes the training program for employees to implement cloud cryptography in an organization.
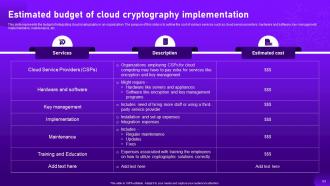
Slide 63: This slide represents the budget of integrating cloud cryptography in an organization.
Slide 64: This slide is an introductory slide.
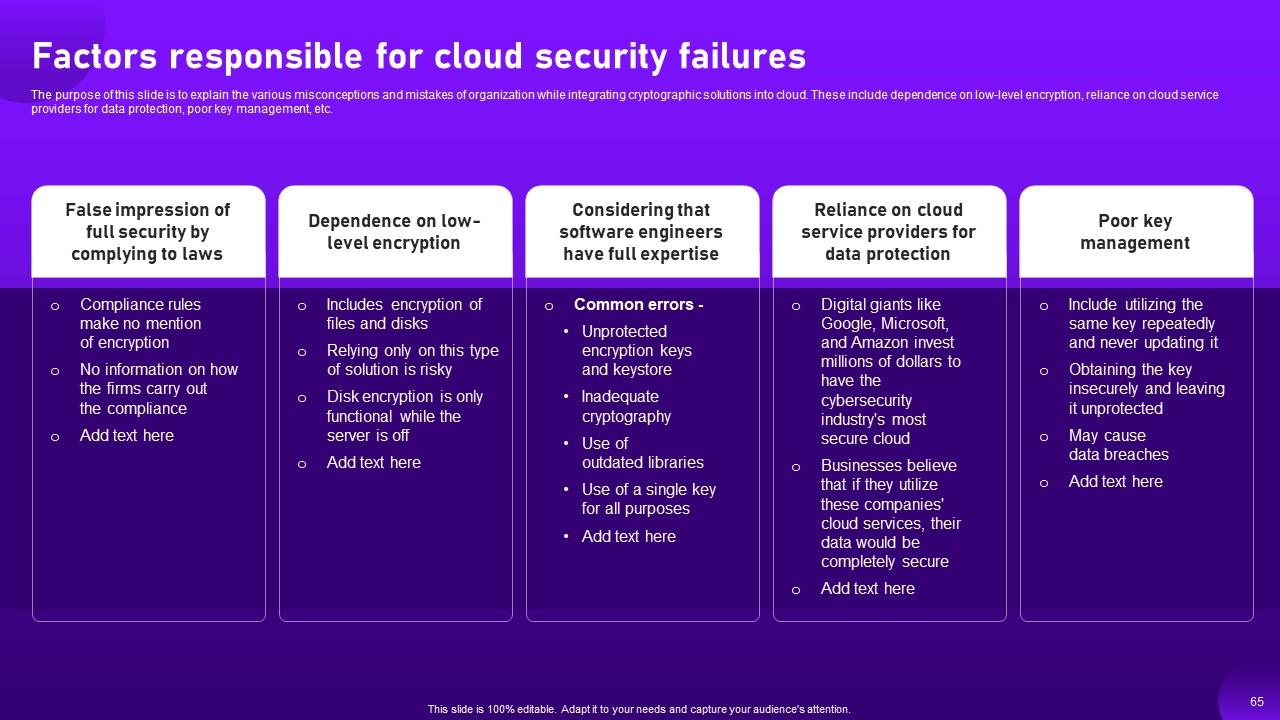
Slide 65: The purpose of this slide is to explain the various misconceptions and mistakes of organization.
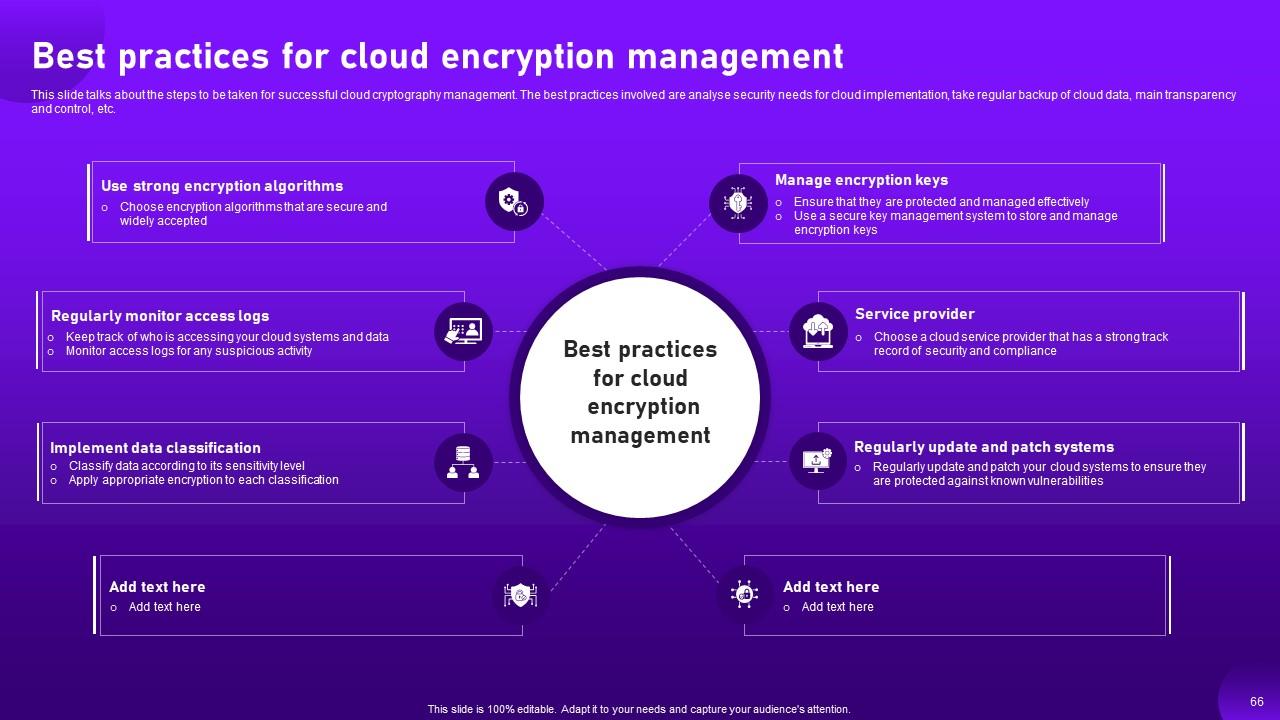
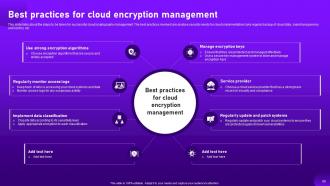
Slide 66: This slide showcases about the steps to be taken for successful cloud cryptography management.
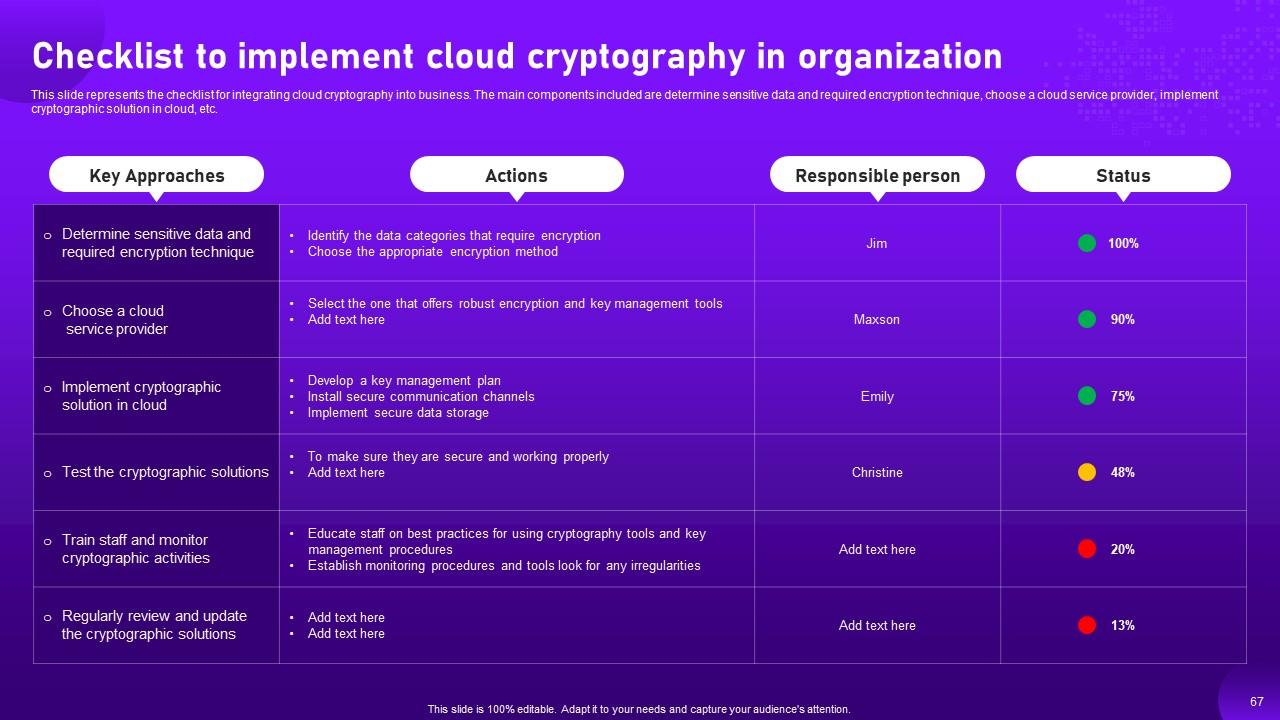
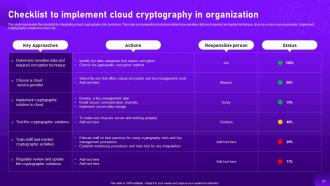
Slide 67: This slide illustrates the checklist for integrating cloud cryptography into business.
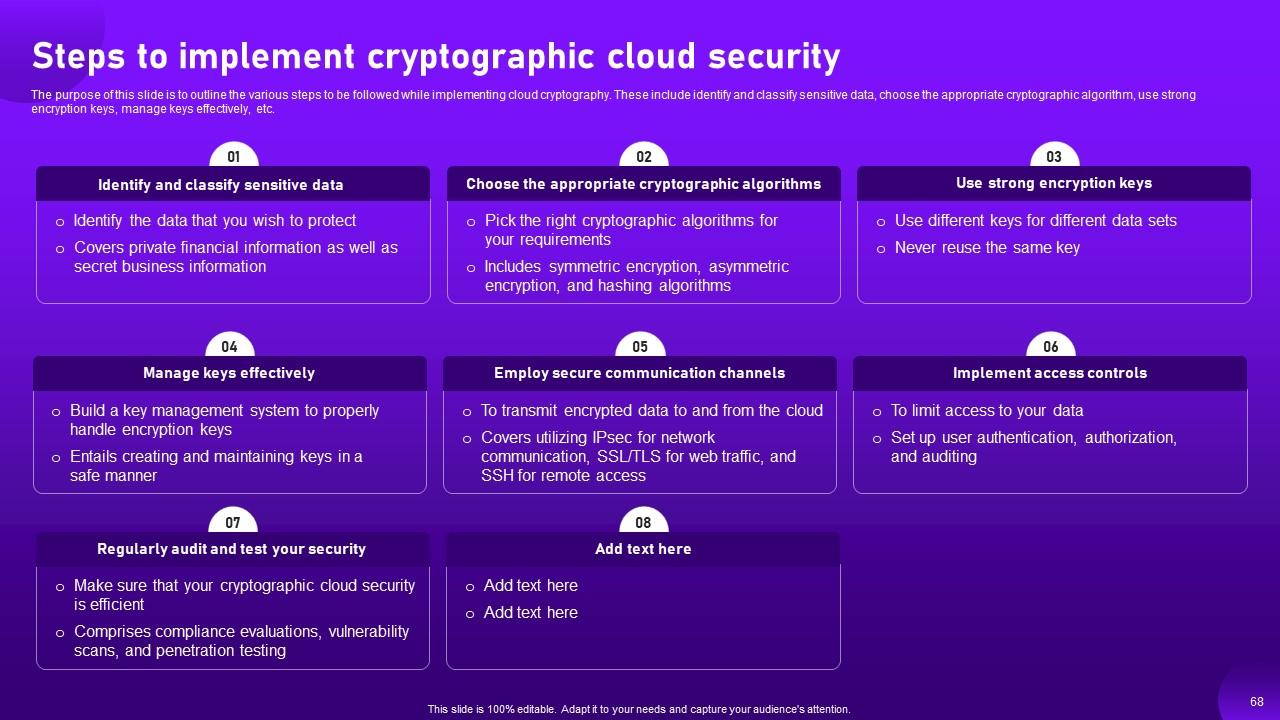
Slide 68: The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography.
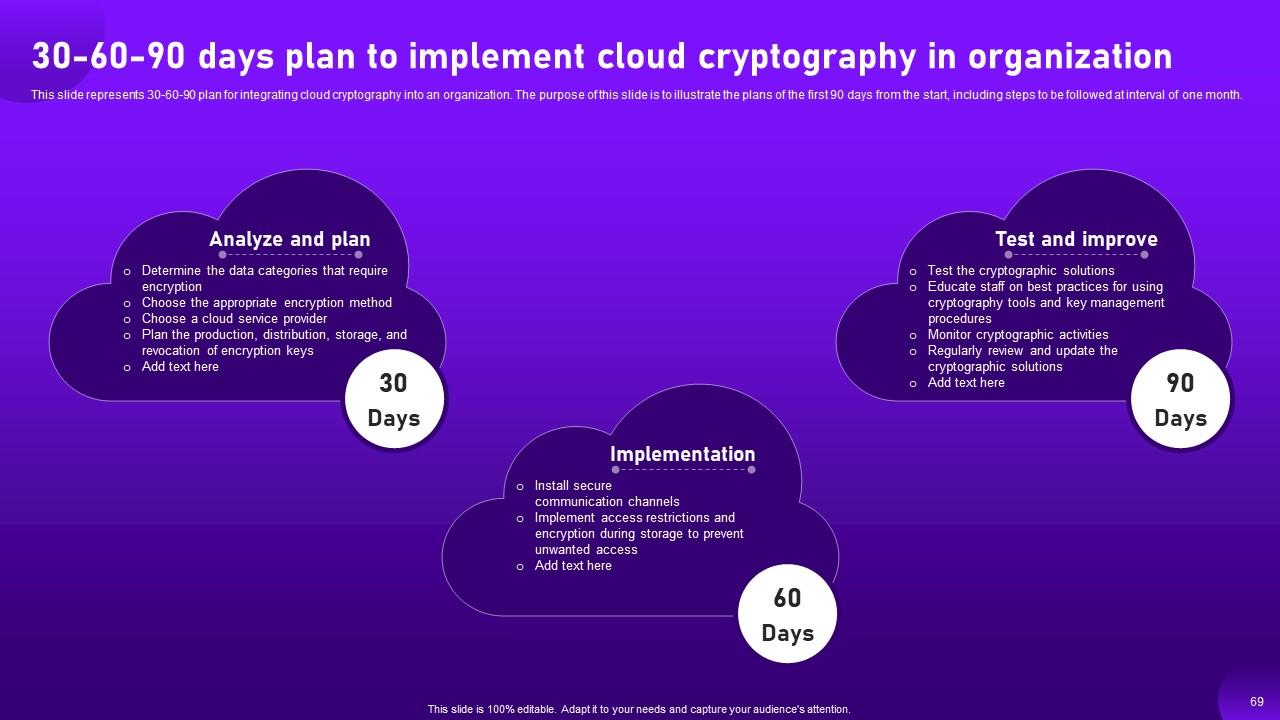
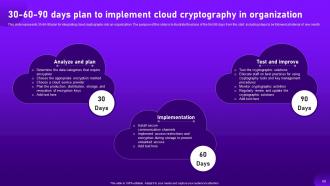
Slide 69: This slide highlights 30-60-90 plan for integrating cloud cryptography into an organization.
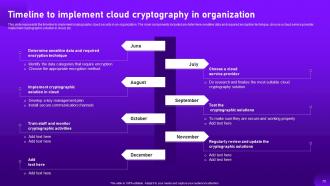
Slide 70: This slide represents the timeline to implement cryptographic cloud security in an organization.
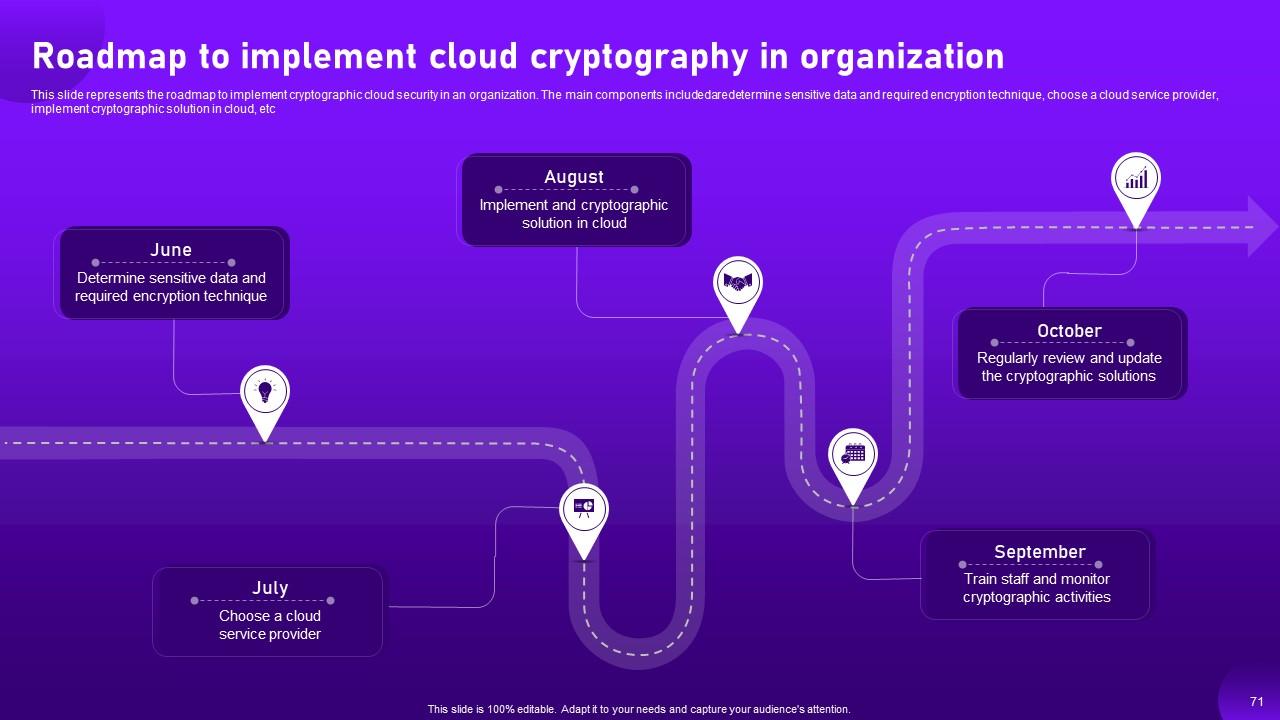
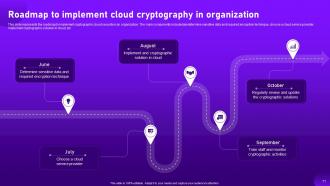
Slide 71: This slide highlights the roadmap to implement cryptographic cloud security in an organization.
Slide 72: This slide is an introductory slide.
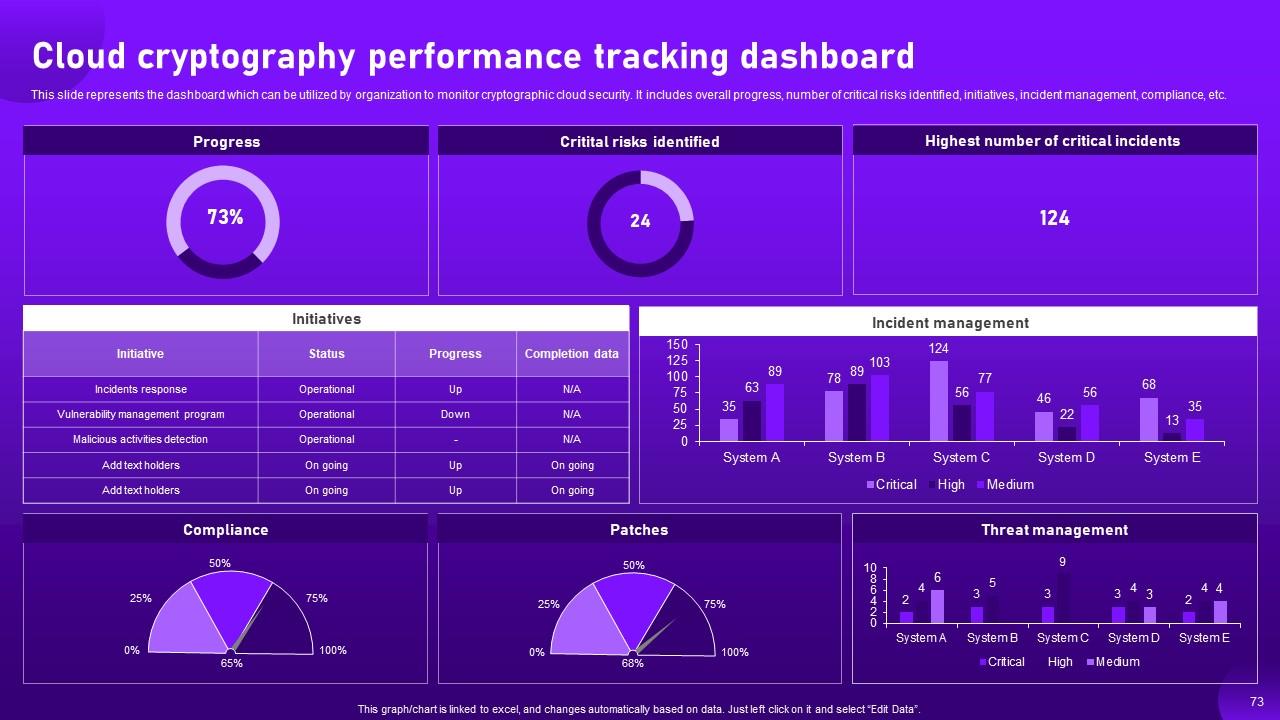
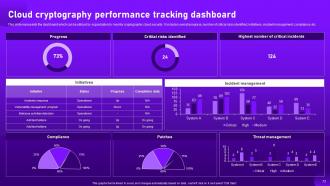
Slide 73: This slide entails the dashboard which can be utilized by organization to monitor cryptographic cloud security.
Slide 74: This slide is an introductory slide.
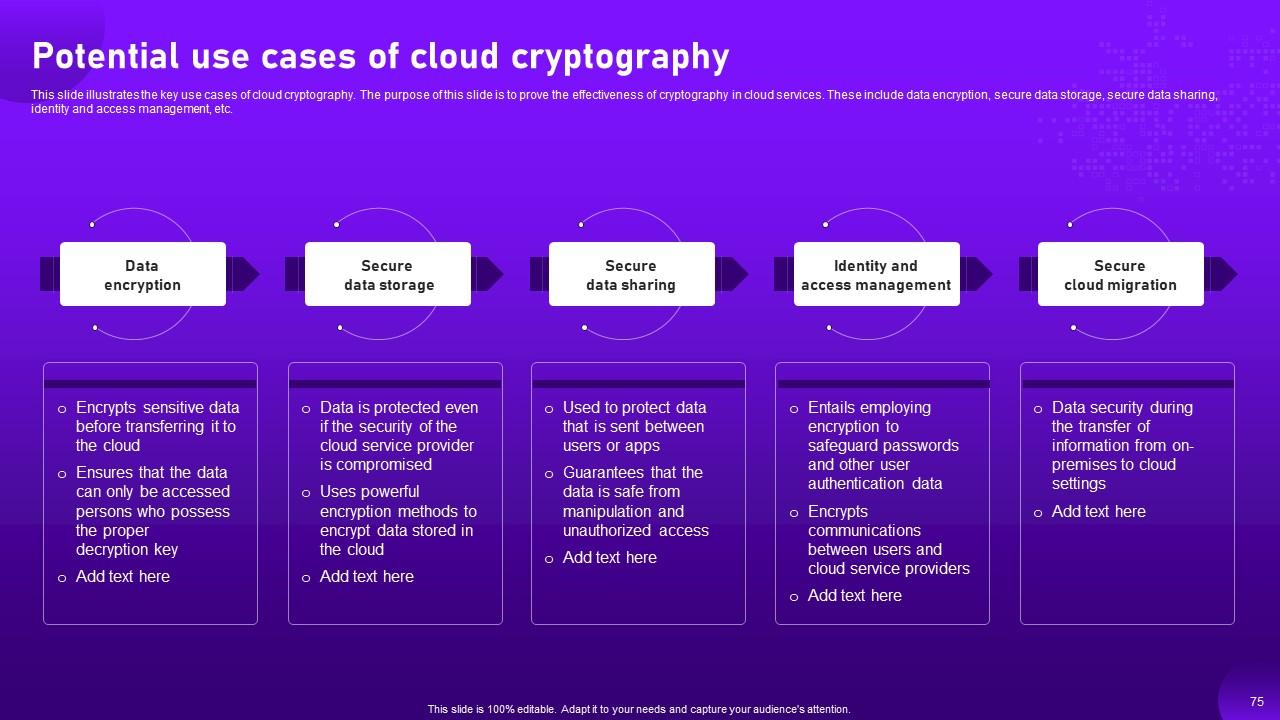
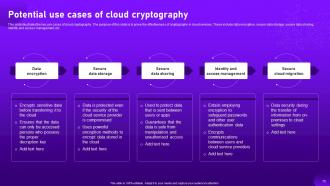
Slide 75: This slide illustrates the key use cases of cloud cryptography.
Slide 76: This slide shows all the icons included in the presentation.
Slide 77: This slide is titled Additional Slides for moving forward.
Slide 78: This slide is an About Us slide to show company specifications etc.
Slide 79: This slide is a Timeline slide. Show data related to time intervals here.
Slide 80: This slide contains a Puzzle with related icons and text.
Slide 81: This slide is an Idea Generation slide to state a new idea or highlight information, specifications, etc.
Slide 82: This slide shows SWOT describing- Strength, Weakness, Opportunity, and Threat.
Slide 83: This slide shows Post-It Notes. Post your important notes here.
Slide 84: This slide depicts a Venn diagram with text boxes.
Slide 85: This slide is a thank-you slide with address, contact numbers, and email address.
Cloud Cryptography Powerpoint Presentation Slides with all 94 slides:
Use our Cloud Cryptography Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Informative design.
-
The service is fast, and I could access any presentation after buying the subscription. I don’t think I’ll ever have to worry about a presentation in my life.