Confidential Computing V2 Powerpoint Presentation Slides
Our insightfully developed PowerPoint presentation titled, Confidential Computing briefly explains confidential computing technology, covering its importance, various technologies, consortiums, and architecture. In this Confidential Computing PowerPoint Presentation, we have covered the overview of the confidential computing environment, including an introduction, key features, functions, benefits, and business scenarios. It also comprises the importance of confidential computing for users, its technical stack, and how it provides complete data security. Additionally, this Confidential Computing Consortium PPT contains an overview of the confidential computing consortium, covering its structure and different membership levels. Furthermore, this Confidential Computing Market template caters to a section of the confidential computing market that covers market segments, executive summary, growth drivers, the adoption rate of confidential computing in North America and APAC, and the total addressable market overview. Moreover, this Confidential Computing Hardware deck comprises applications of confidential computing technology in different sectors such as healthcare and research, finance, engineering and manufacturing, and automobiles. Lastly, this Confidential Computing Technology module contains a budget, the future of the technology, an implementation roadmap and timeline, and a case study. Download our 100 percent editable and customizable template, which is also compatible with Google Slides.
Our insightfully developed PowerPoint presentation titled, Confidential Computing briefly explains confidential computing t..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of eighty nine slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Confidential Computing (IT). State Your Company Name and begin.
Slide 2: This slide is an Agenda slide. State your agendas here.
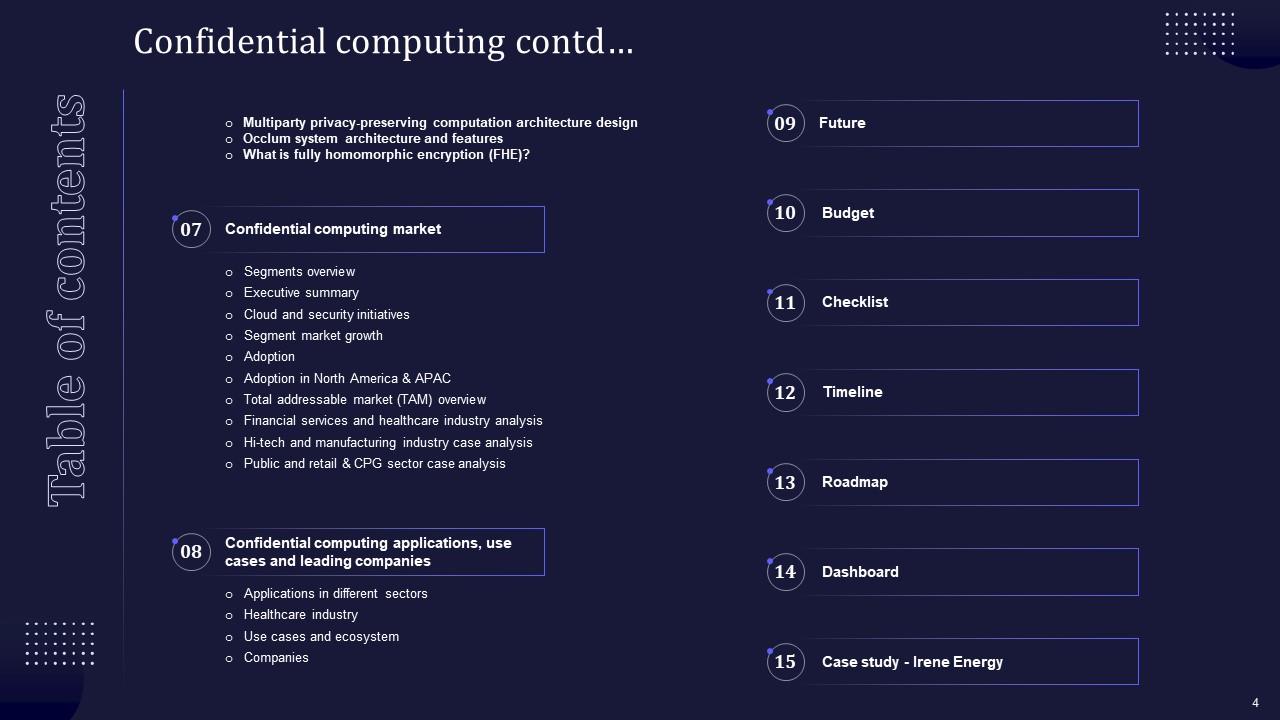
Slide 3: This slide shows a Table of Contents for the presentation.
Slide 4: This slide is in continuation with the previous slide.
Slide 5: This slide is an introductory slide.
Slide 6: This slide represents the introduction to confidential computing, including its overview and objectives.
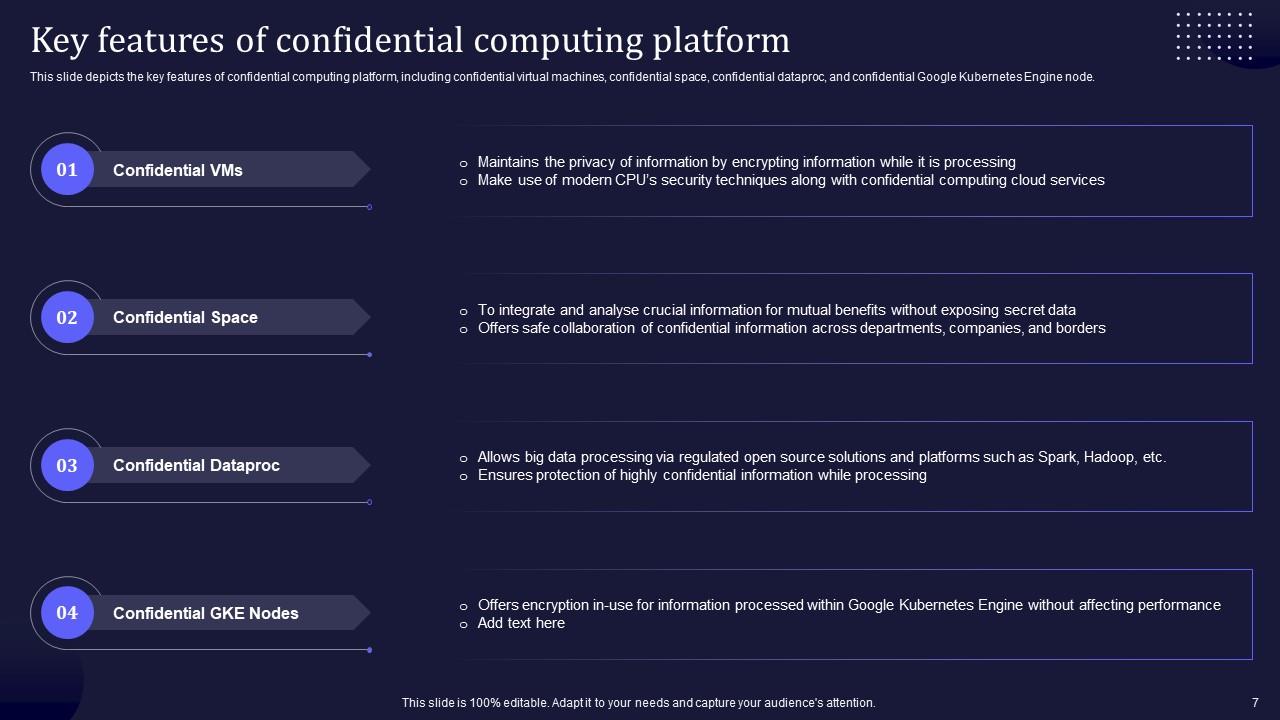
Slide 7: This slide depicts the key features of confidential computing platform.
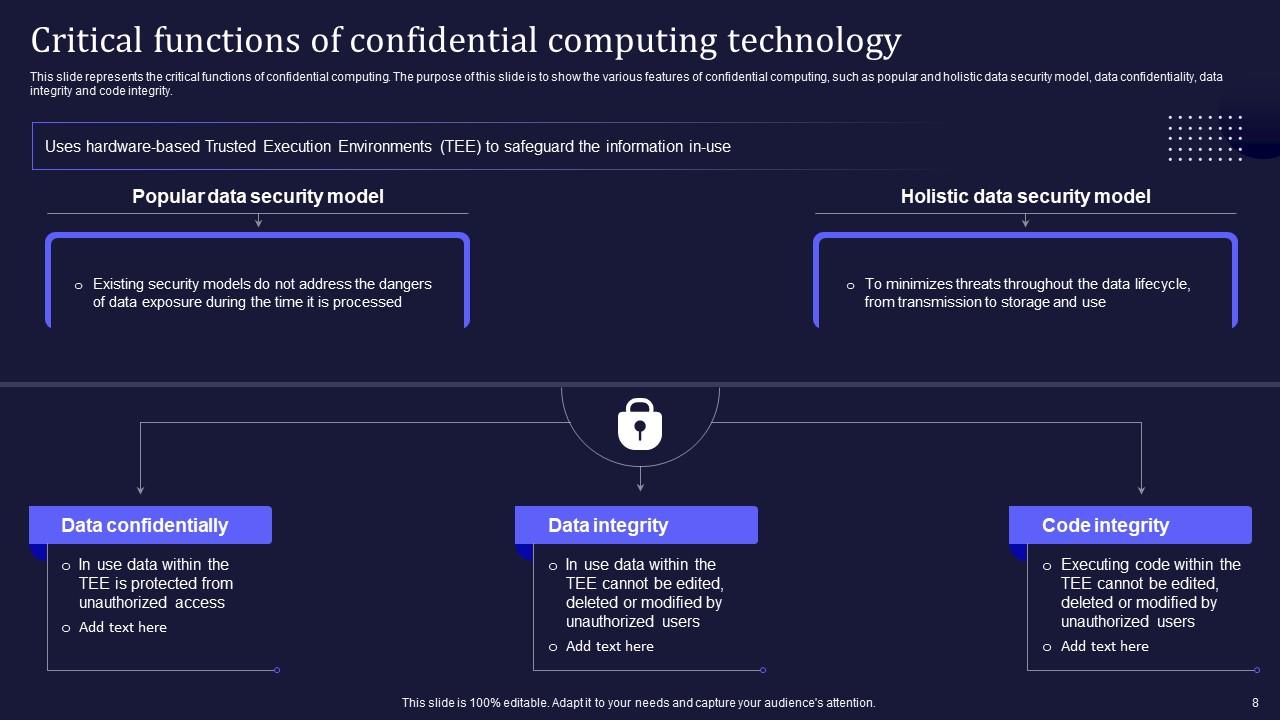
Slide 8: This slide presents the critical functions of confidential computing.
Slide 9: This slide describes the benefits of confidential computing for organizations.
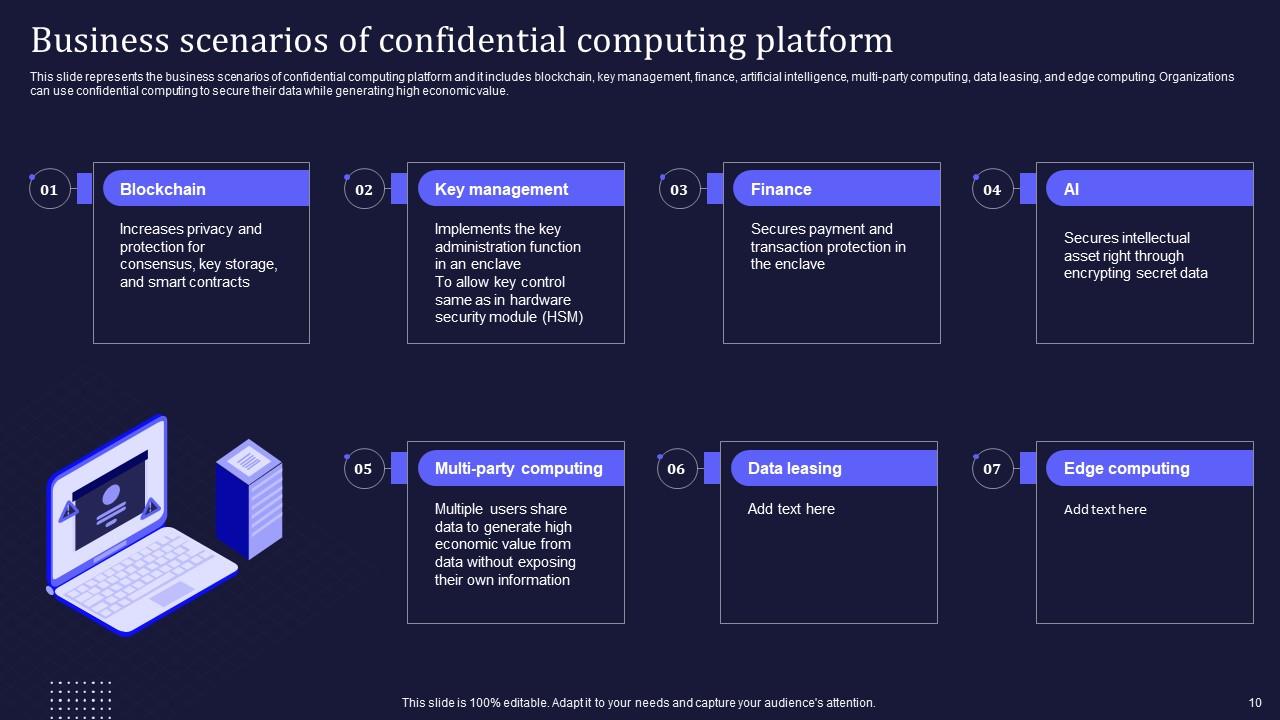
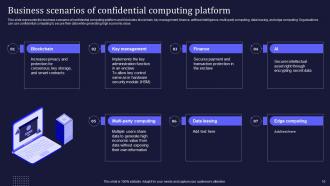
Slide 10: This slide entails the business scenarios of confidential computing platform.
Slide 11: This slide is an introductory slide.
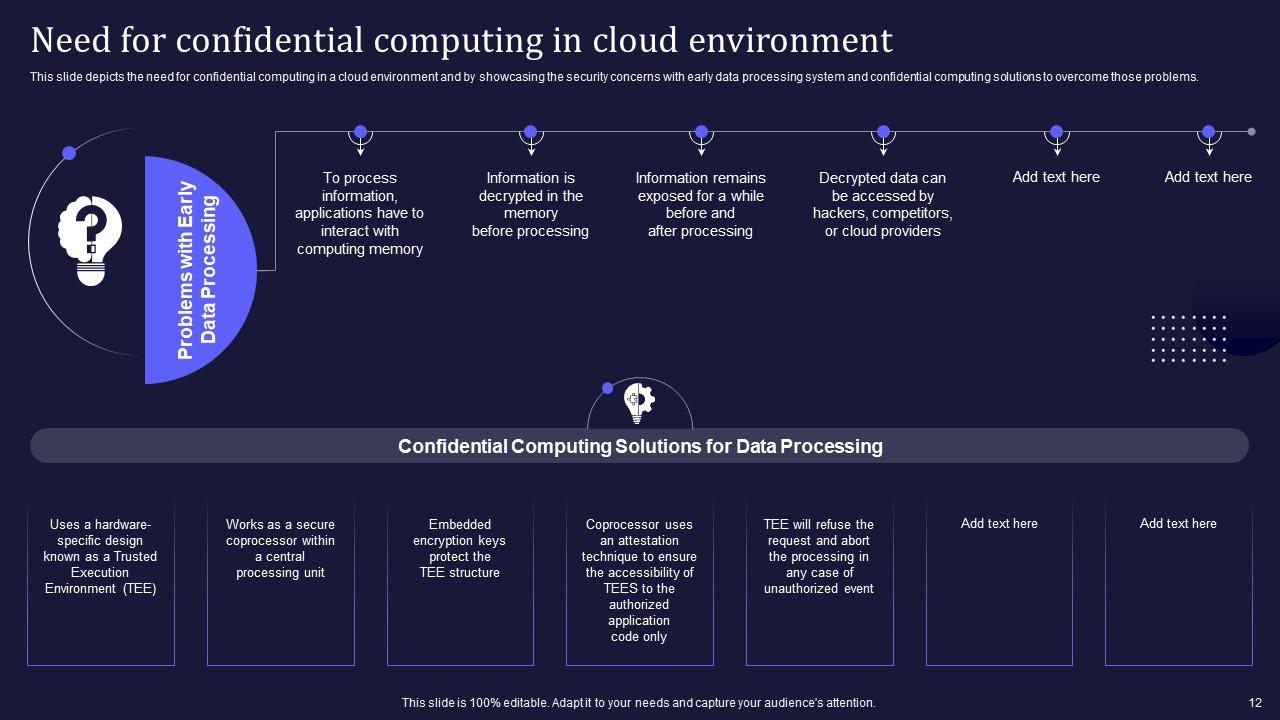
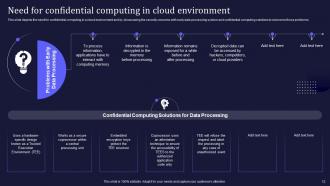
Slide 12: This slide consists the need for confidential computing in a cloud environment.
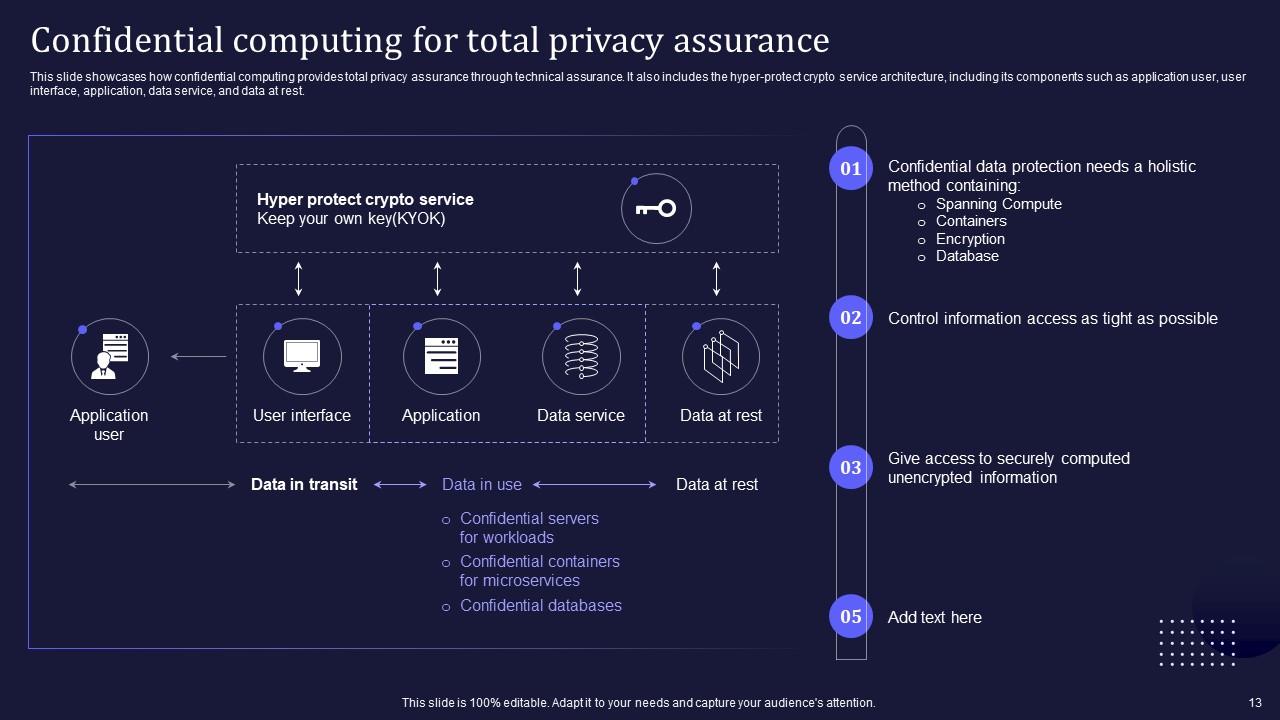
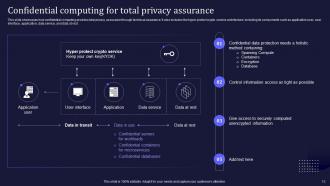
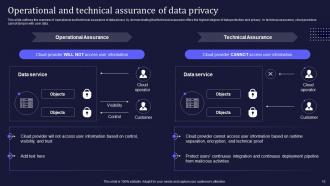
Slide 13: This slide elaborates on how confidential computing provides total privacy assurance through technical assurance.
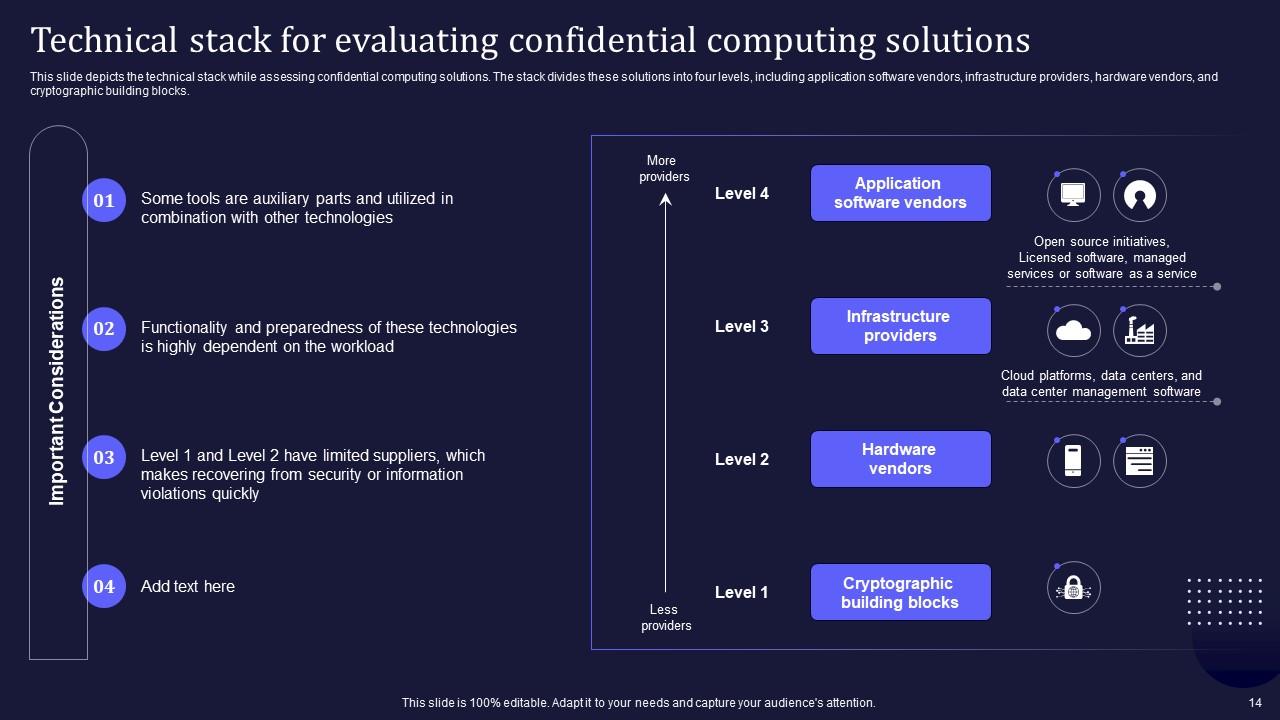
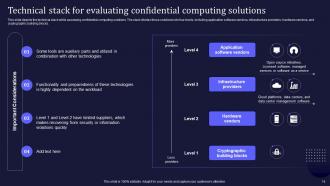
Slide 14: This slide portrays the technical stack while assessing confidential computing solutions.
Slide 15: This slide outlines the overview of operational and technical assurance of data privacy.
Slide 16: This slide is an introductory slide.
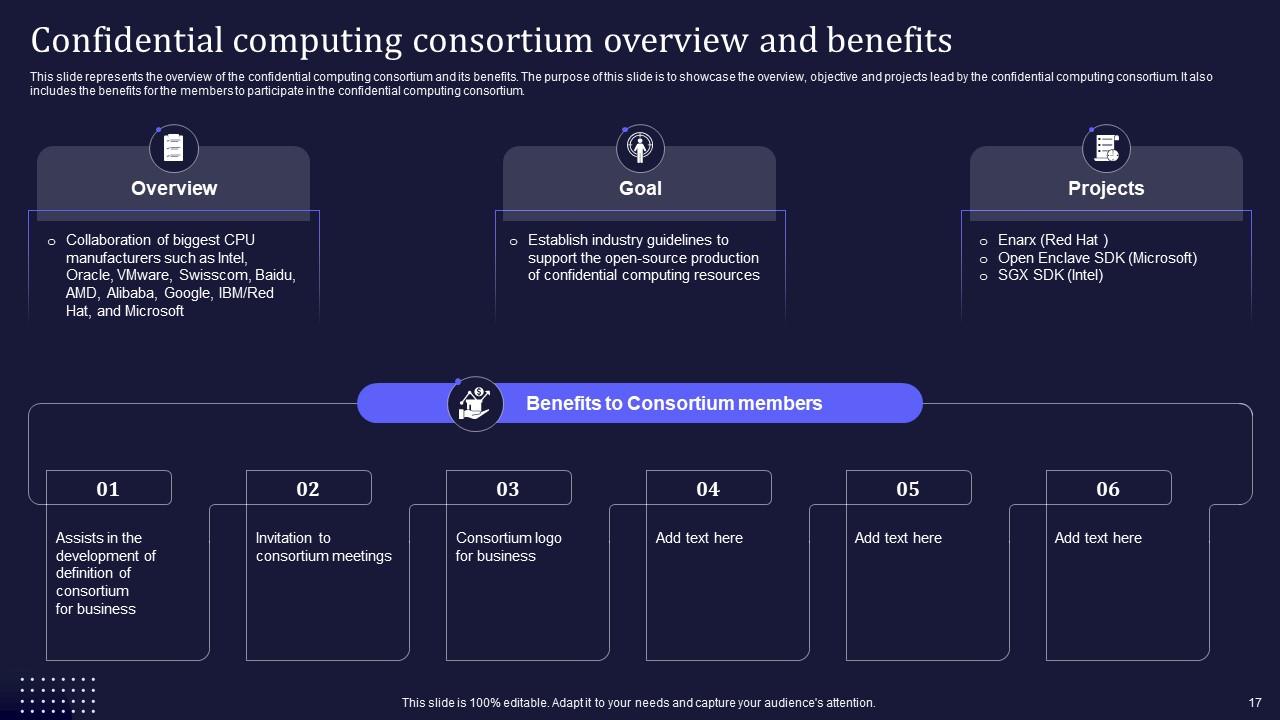
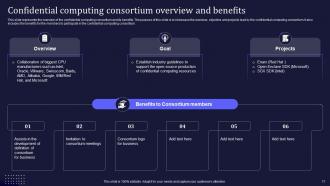
Slide 17: This slide demonstrates the overview of the confidential computing consortium and its benefits.
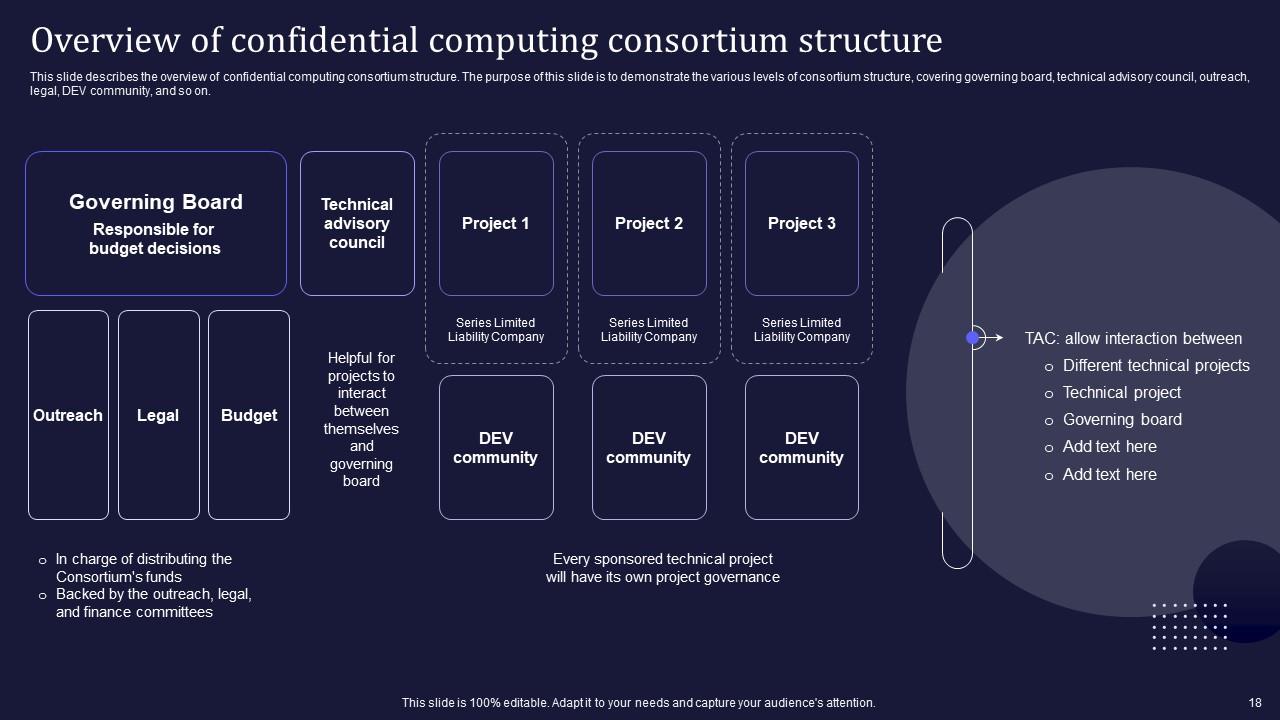
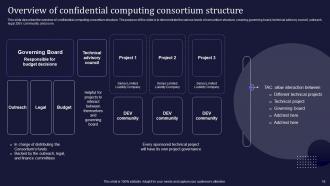
Slide 18: This slide caters to the overview of confidential computing consortium structure.
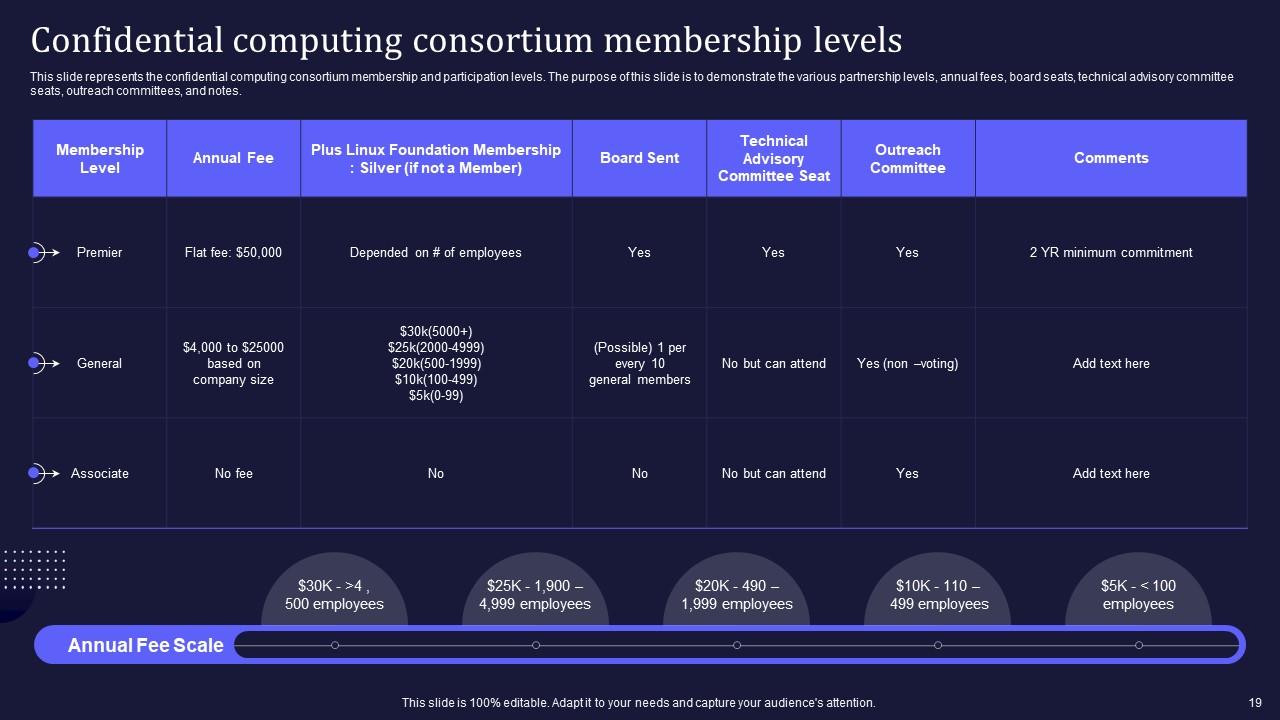
Slide 19: This slide consists the confidential computing consortium membership and participation levels.
Slide 20: This slide is an introductory slide.
Slide 21: This slide represents the in-scope and out-of-scope threat for confidential computing.
Slide 22: This slide is an introductory slide.
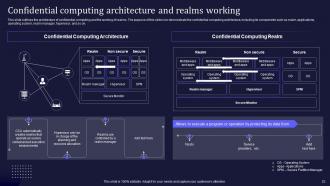
Slide 23: This slide presents the architecture of confidential computing and the working of realms.
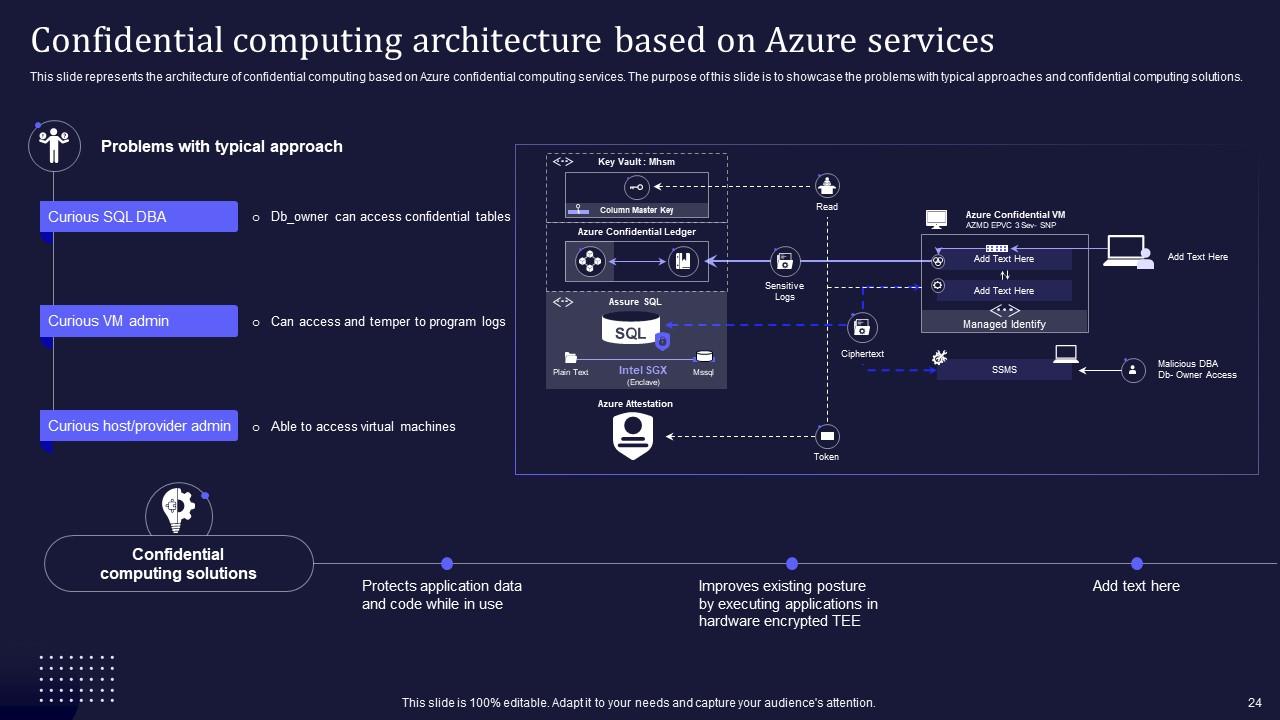
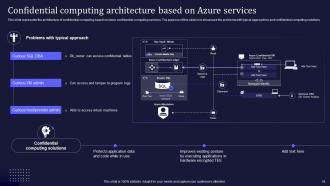
Slide 24: This slide entails the architecture of confidential computing based on Azure confidential computing services.
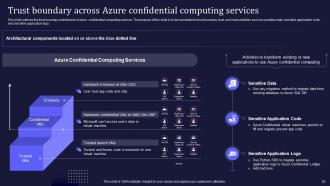
Slide 25: This slide outlines the trust boundary architecture of Azure confidential computing services.
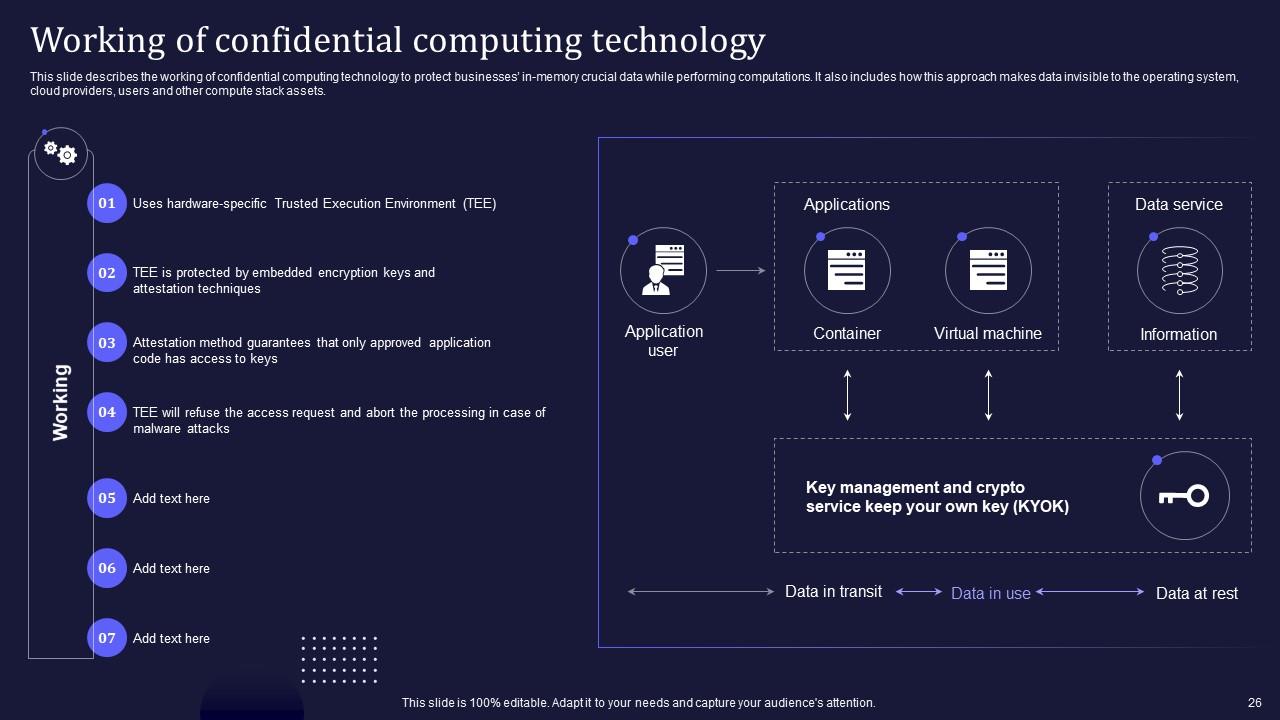
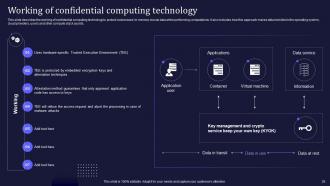
Slide 26: This slide describes the working of confidential computing technology to protect businesses’ in-memory crucial data while performing computations.
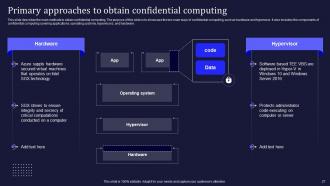
Slide 27: This slide focuses on the main methods to obtain confidential computing.
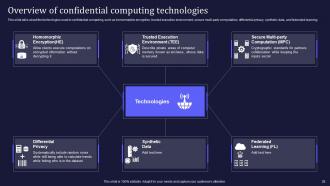
Slide 28: This slide talks about the technologies.
Slide 29: This slide mentions the related technologies used to protect the information in processing.
Slide 30: This slide is an introductory slide.
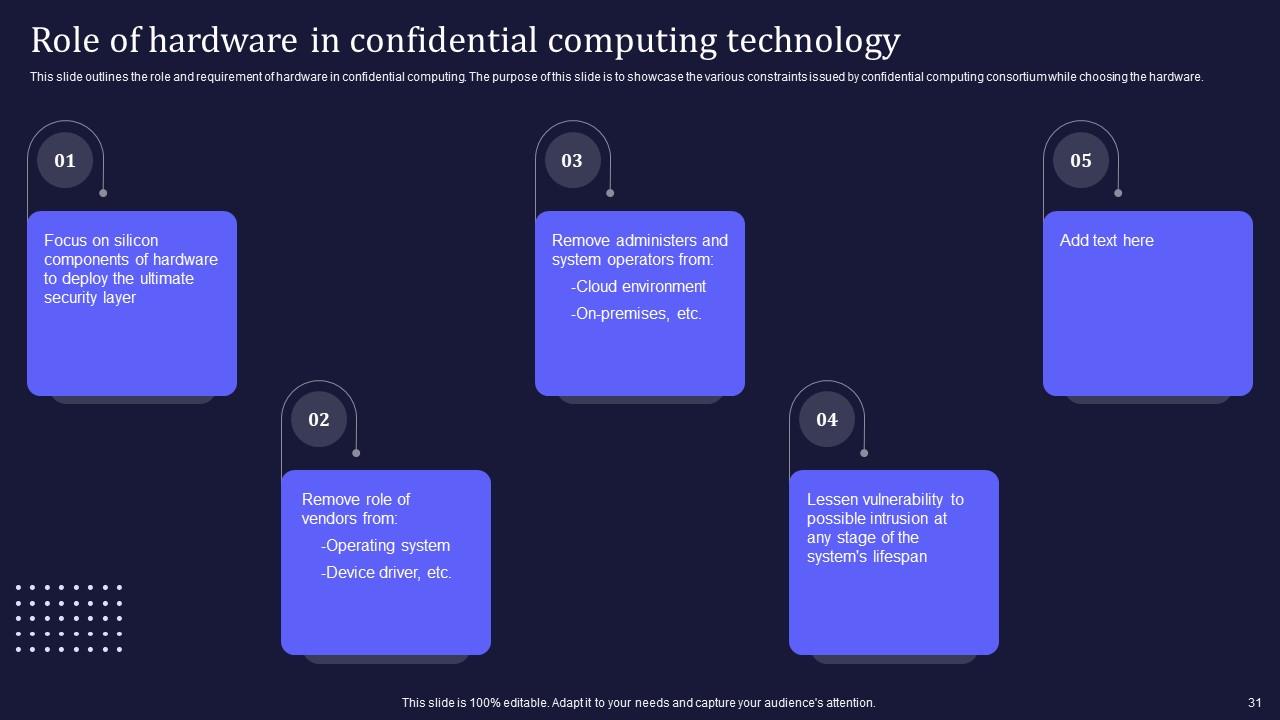
Slide 31: This slide outlines the role and requirement of hardware in confidential computing.
Slide 32: This slide is an introductory slide.
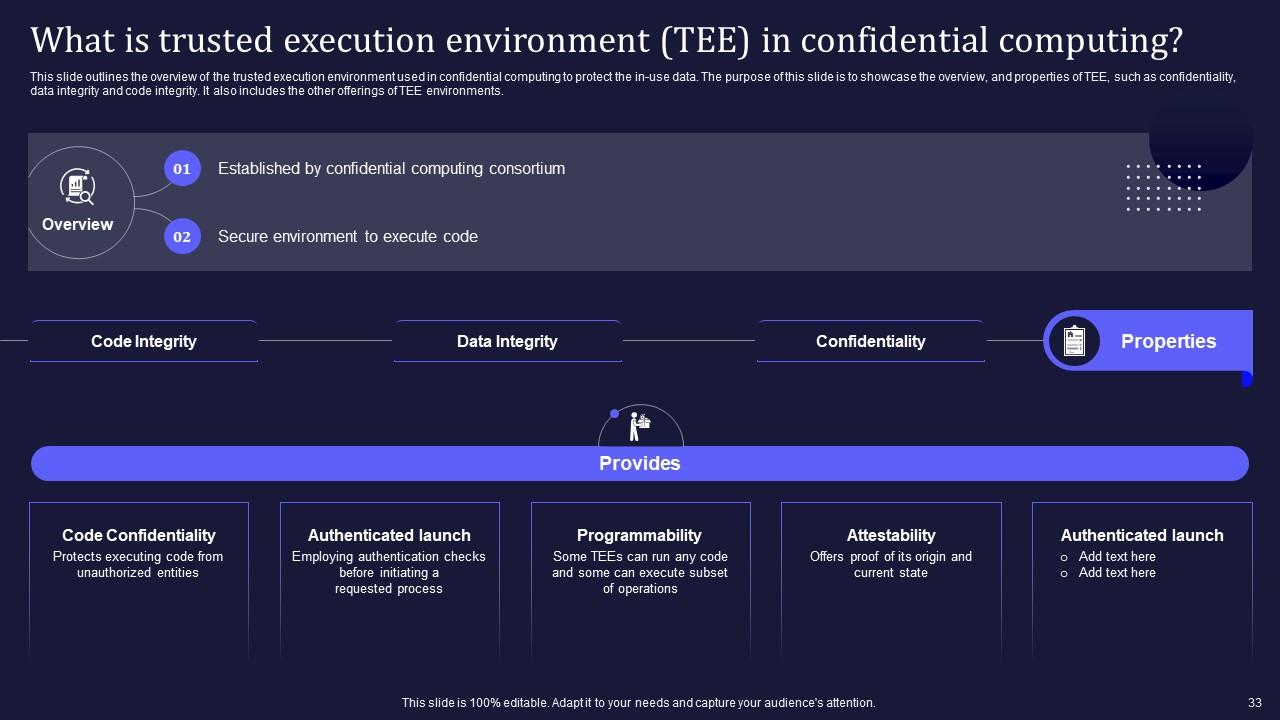
Slide 33: This slide shows the overview of the trusted execution environment used in confidential computing to protect the in-use data.
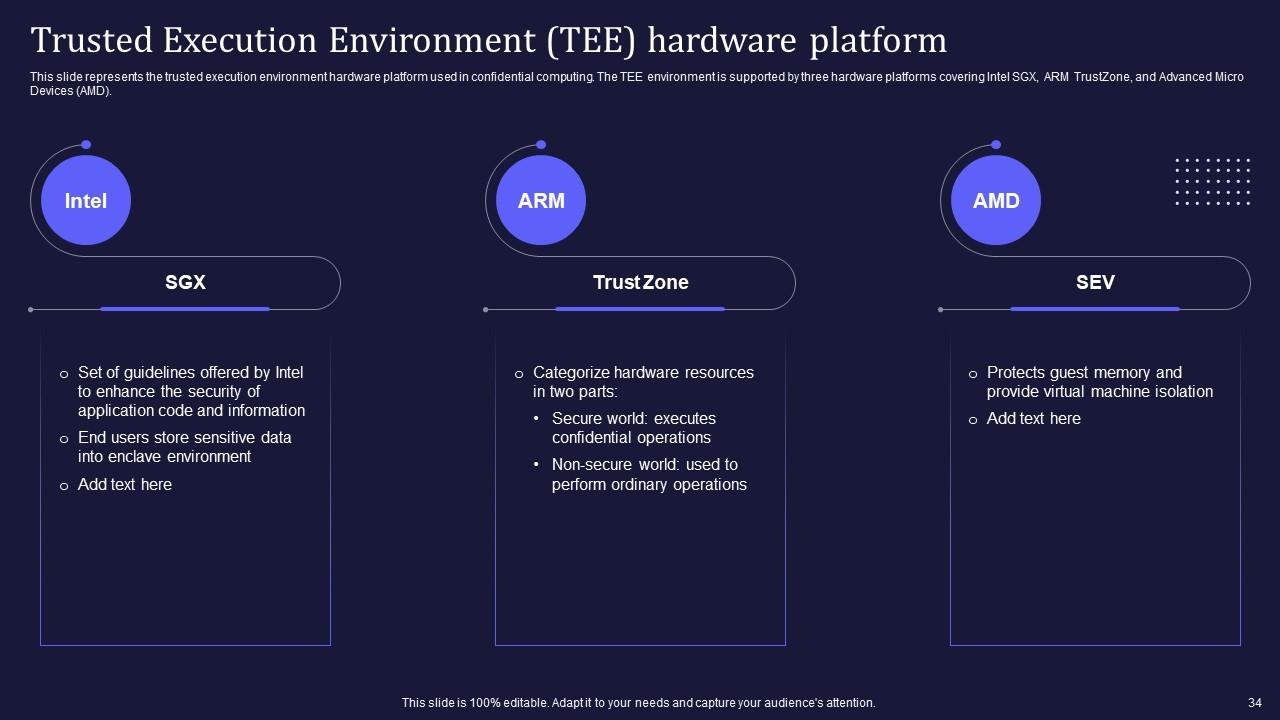
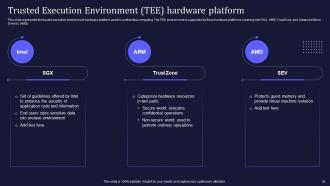
Slide 34: This slide represents the trusted execution environment hardware platform used in confidential computing.
Slide 35: This slide showcases about the functional comparison between different TEE environments available in the market.
Slide 36: This slide is an introductory slide.
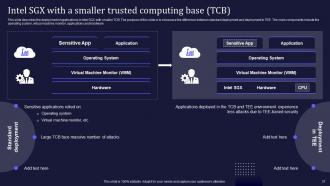
Slide 37: This slide describes the deployment of applications in Intel SGX with smaller TCB.
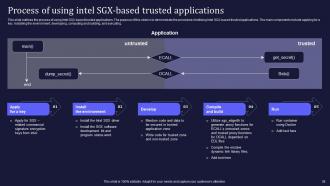
Slide 38: This slide depicts the process of using Intel SGX-based trusted applications.
Slide 39: This slide is an introductory slide.
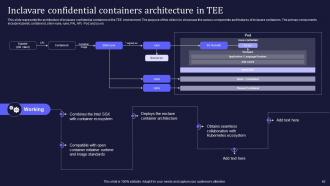
Slide 40: This slide elucidates the architecture of inclavare confidential containers in the TEE environment.
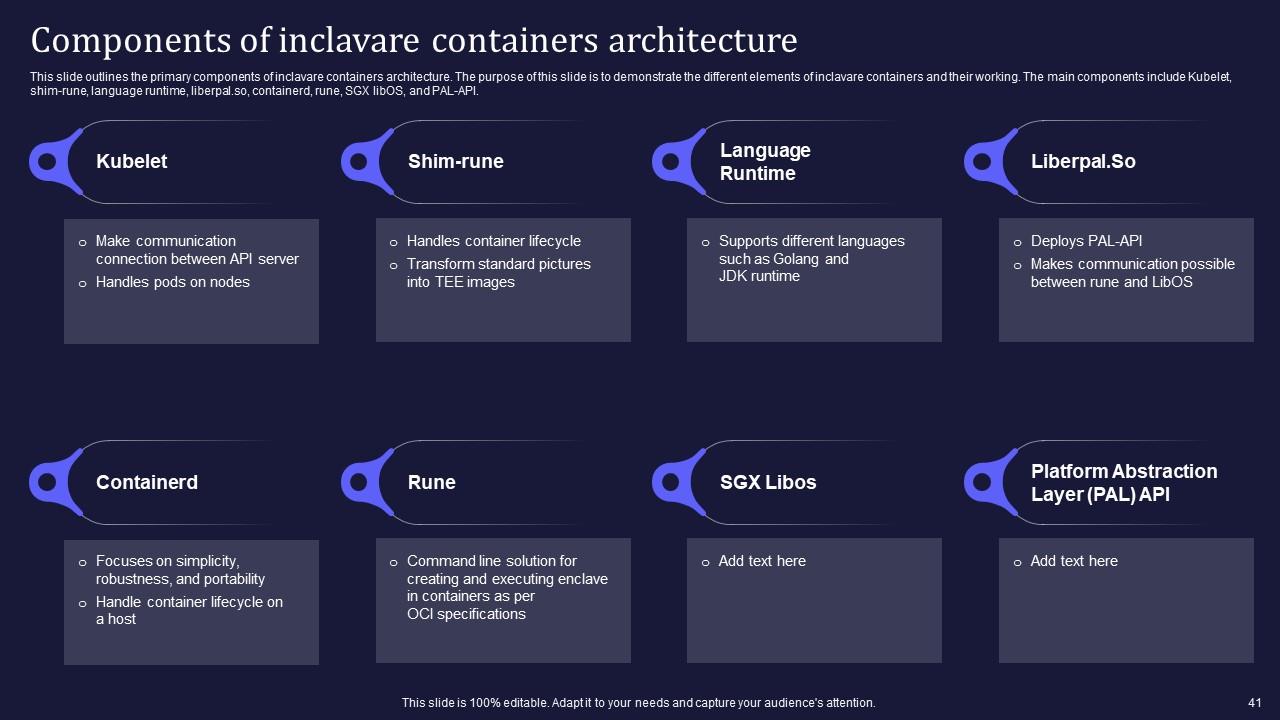
Slide 41: This slide outlines the primary components of inclavare containers architecture.
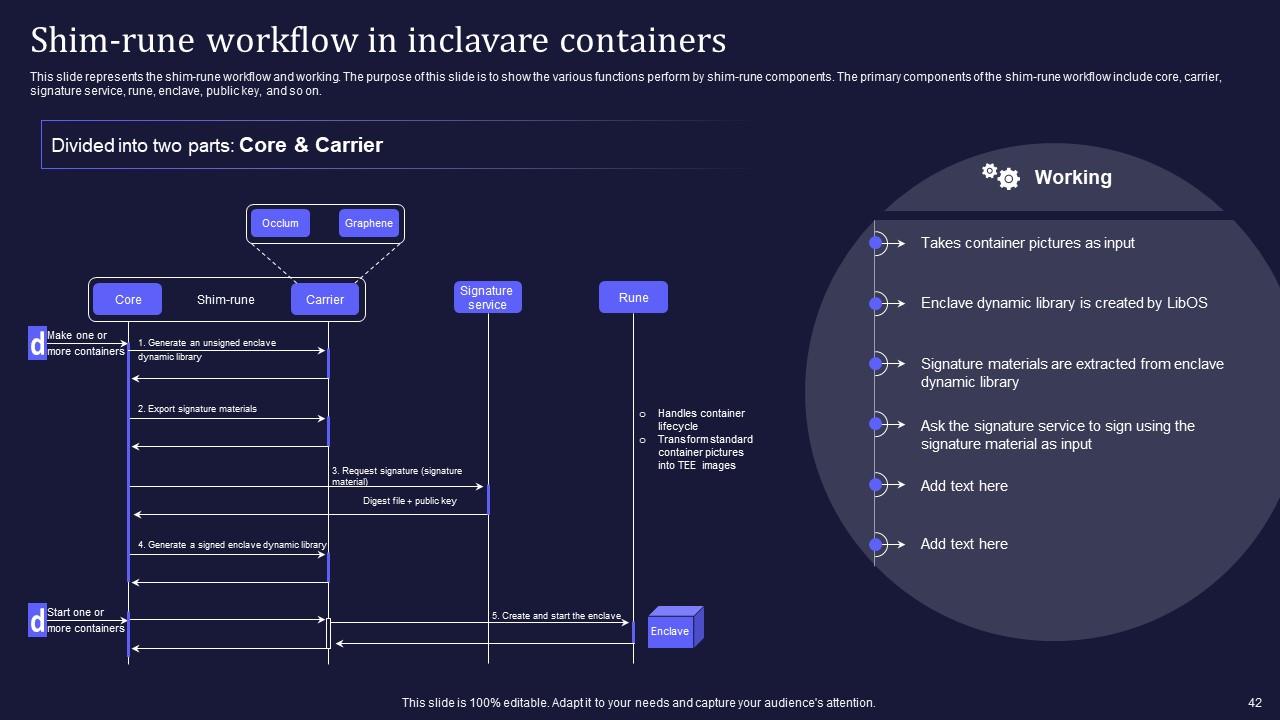
Slide 42: This slide represents the shim-rune workflow and working.
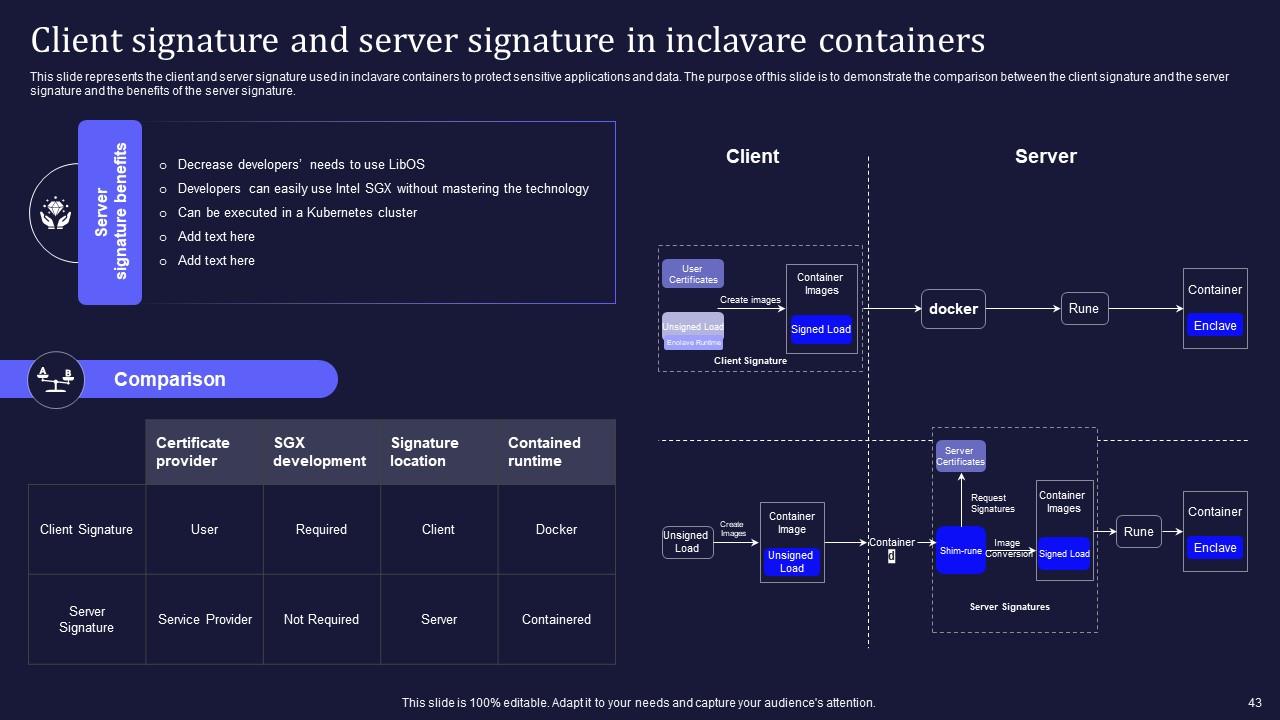
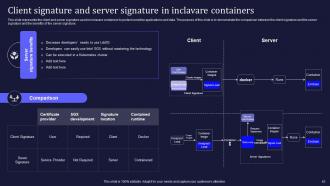
Slide 43: This slide highlights the client and server signature used in inclavare containers to protect sensitive applications and data.
Slide 44: This slide outlines the architecture of multi-team construction and cooperation.
Slide 45: This slide is an introductory slide.
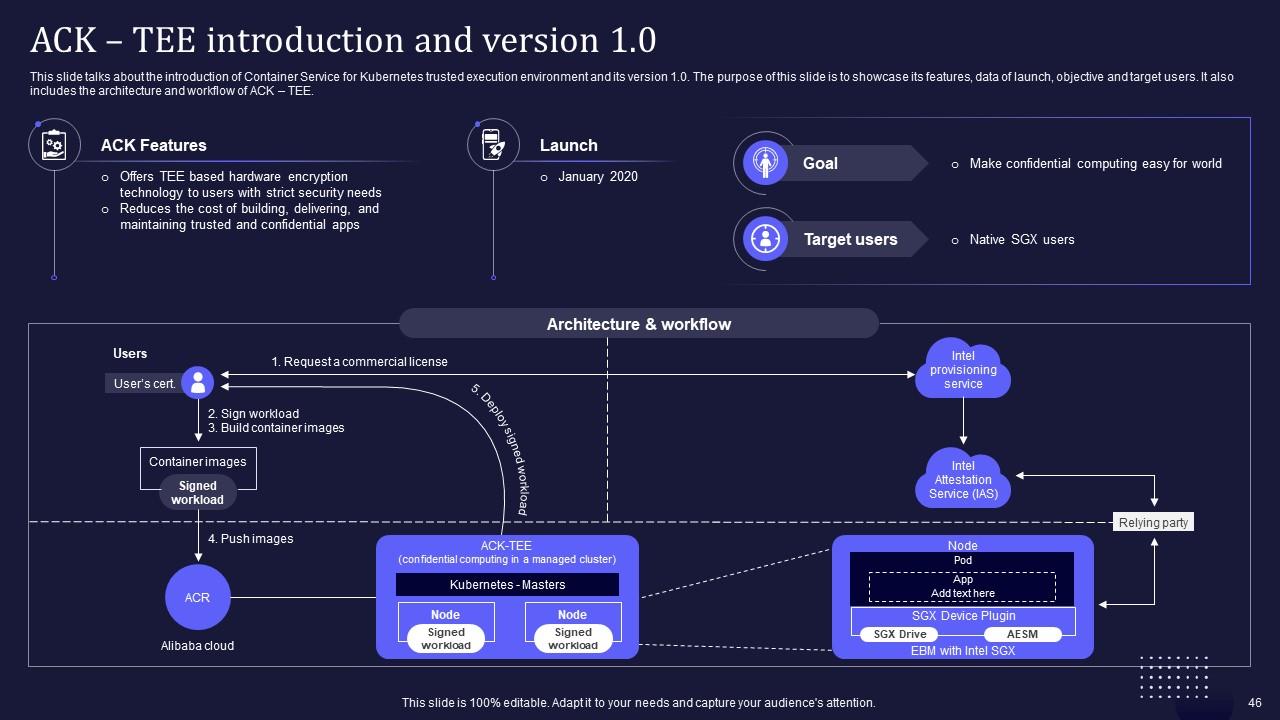
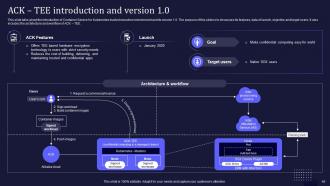
Slide 46: This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0.
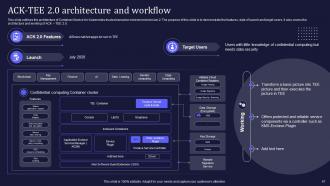
Slide 47: This slide mentions the architecture of Container Service for Kubernetes trusted execution environment version 2.
Slide 48: This slide is an introductory slide.
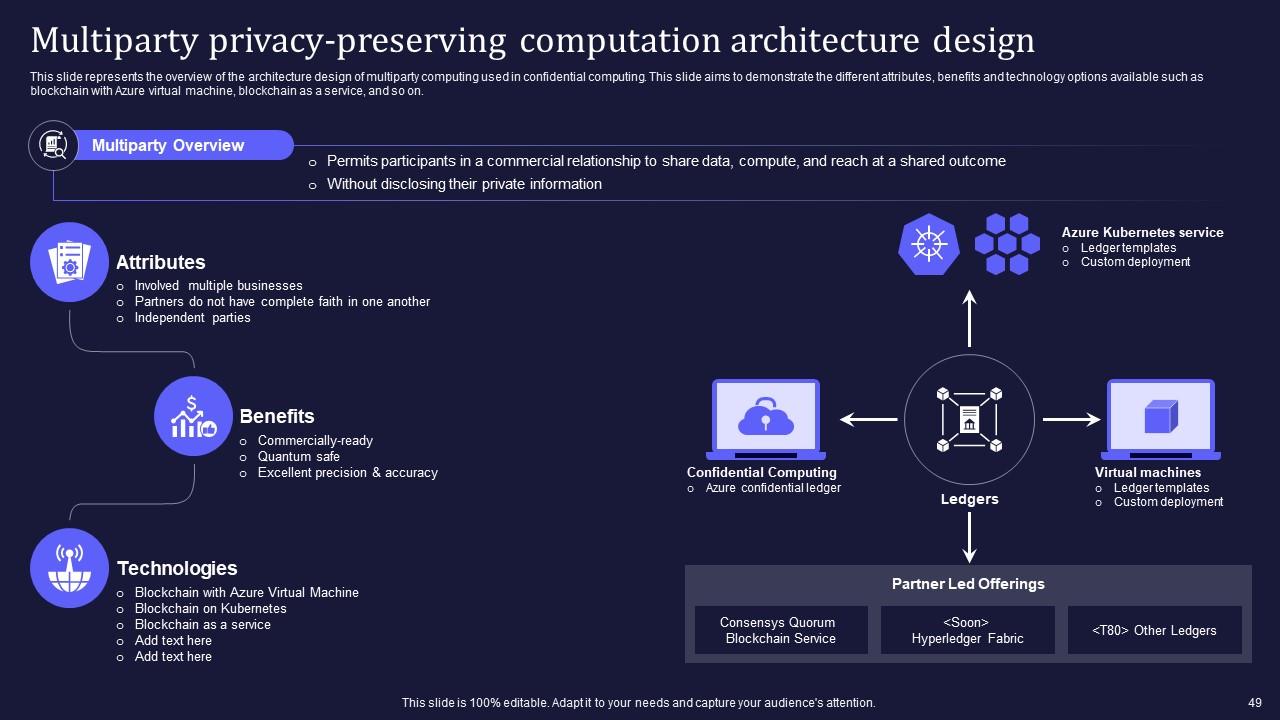
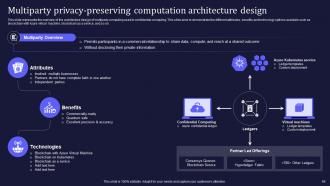
Slide 49: This slide encompasses the overview of the architecture design of multiparty computing used in confidential computing.
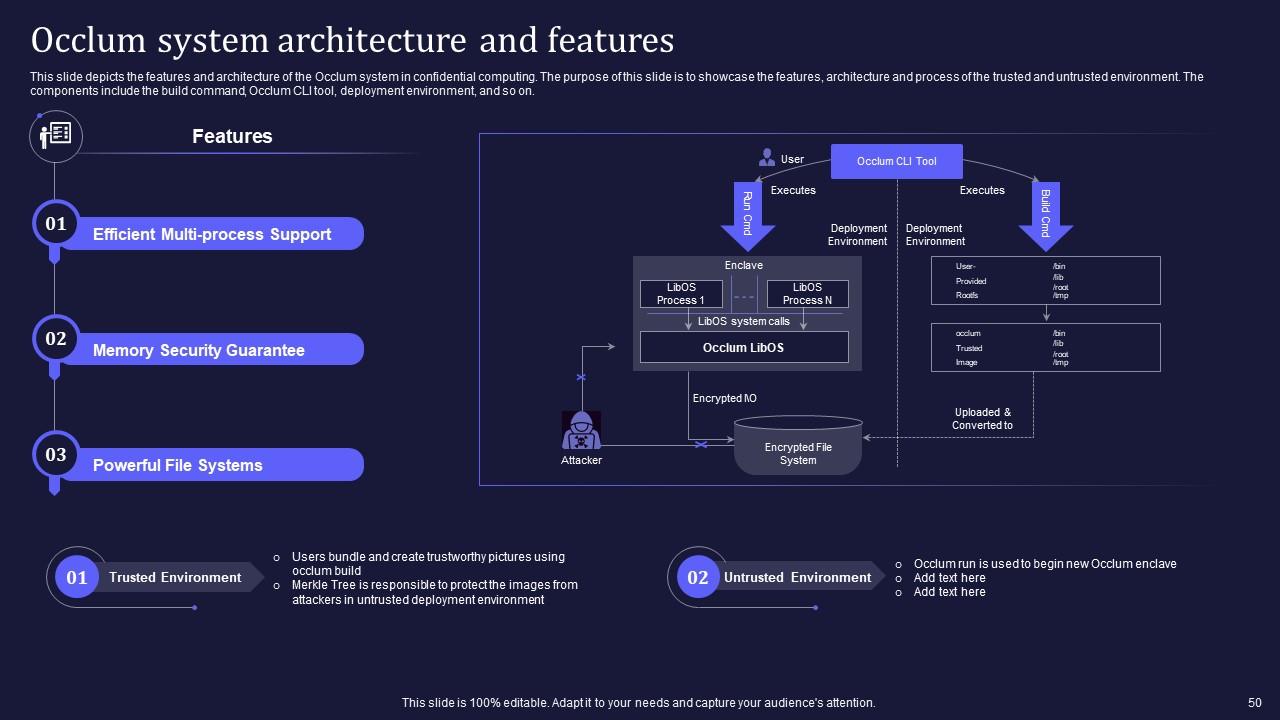
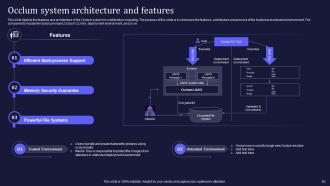
Slide 50: This slide depicts the features and architecture of the Occlum system in confidential computing.
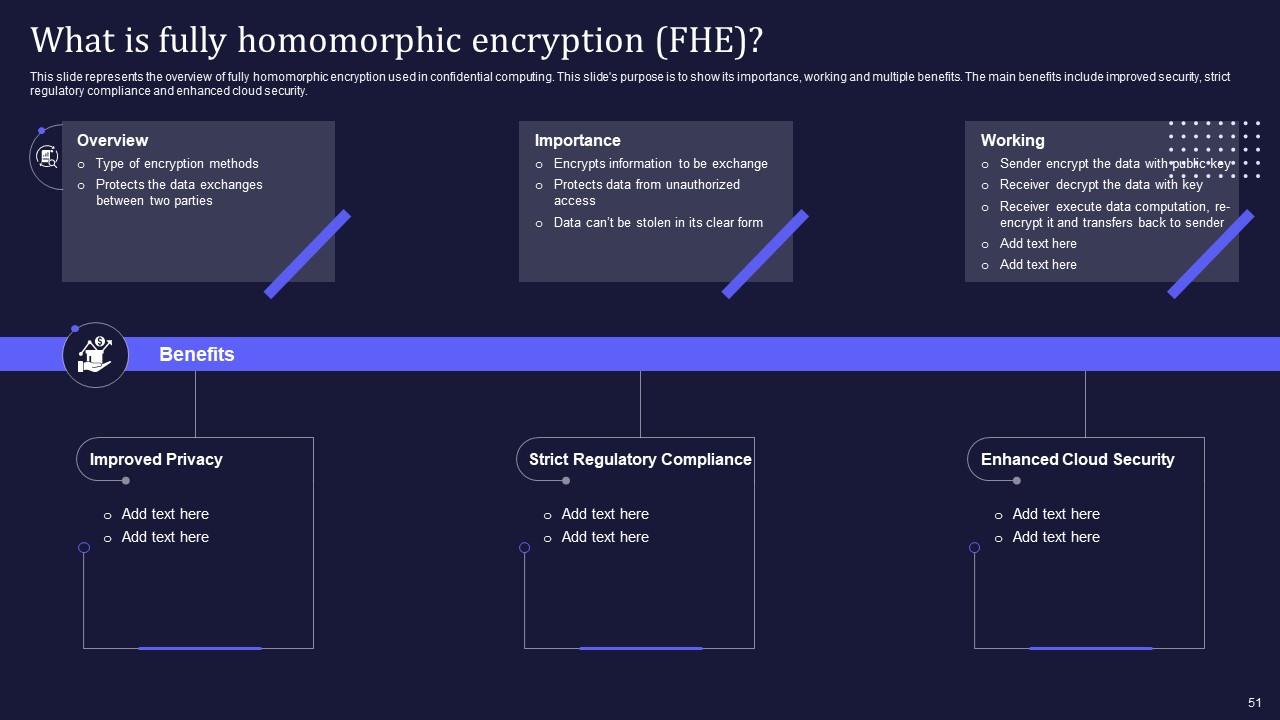
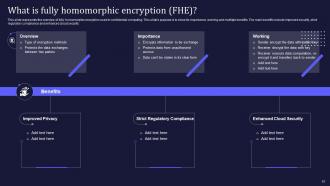
Slide 51: This slide describes the overview of fully homomorphic encryption used in confidential computing.
Slide 52: This slide is an introductory slide.
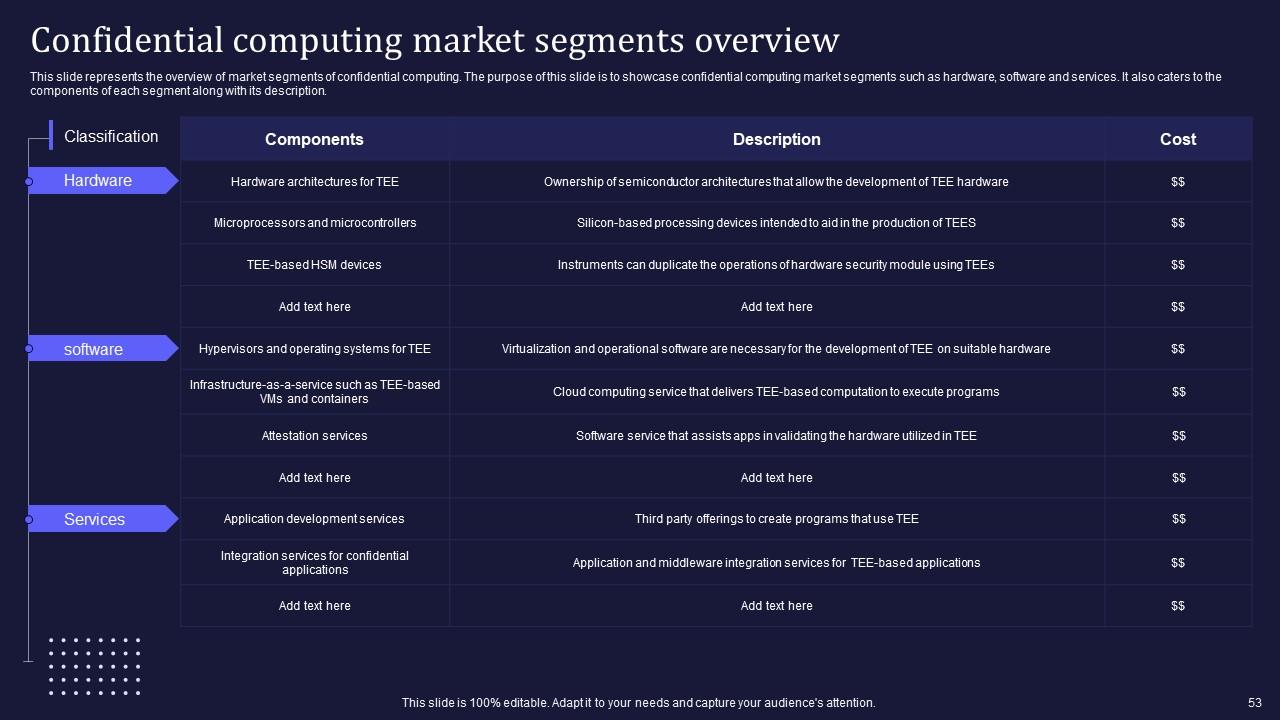
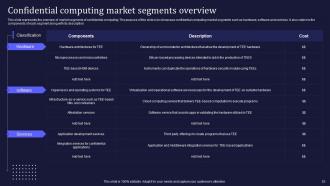
Slide 53: This slide demarcates the overview of market segments of confidential computing.
Slide 54: This slide pertains to the executive summary of key findings of confidential computing.
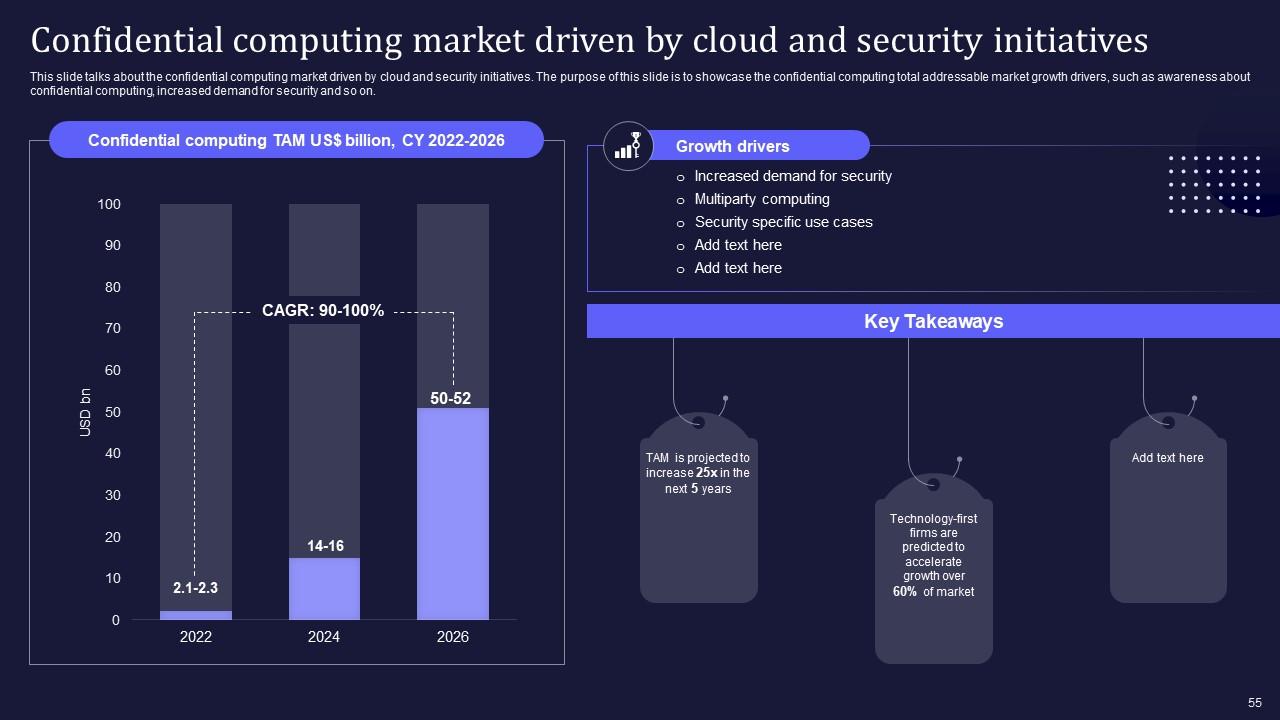
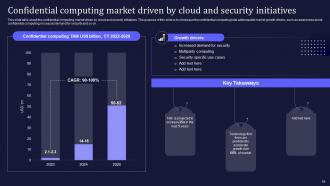
Slide 55: This slide entails about the confidential computing market driven by cloud and security initiatives.
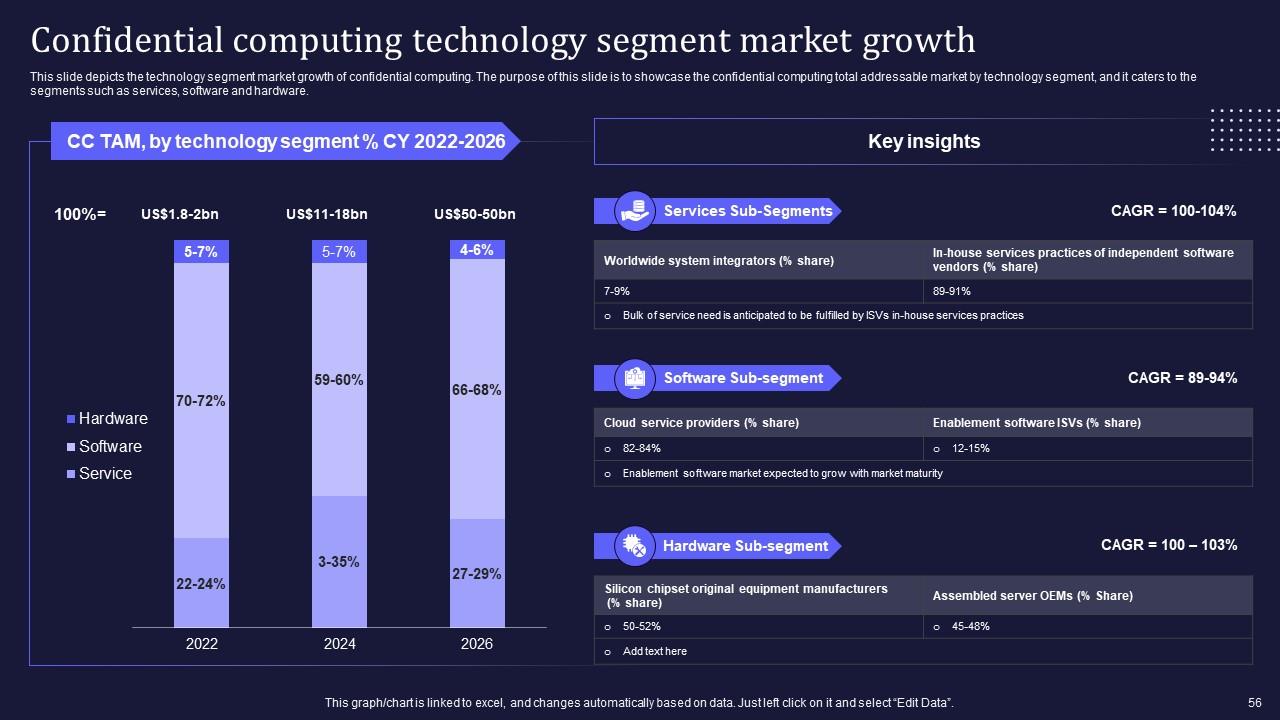
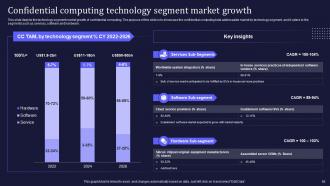
Slide 56: This slide consists the technology segment market growth of confidential computing.
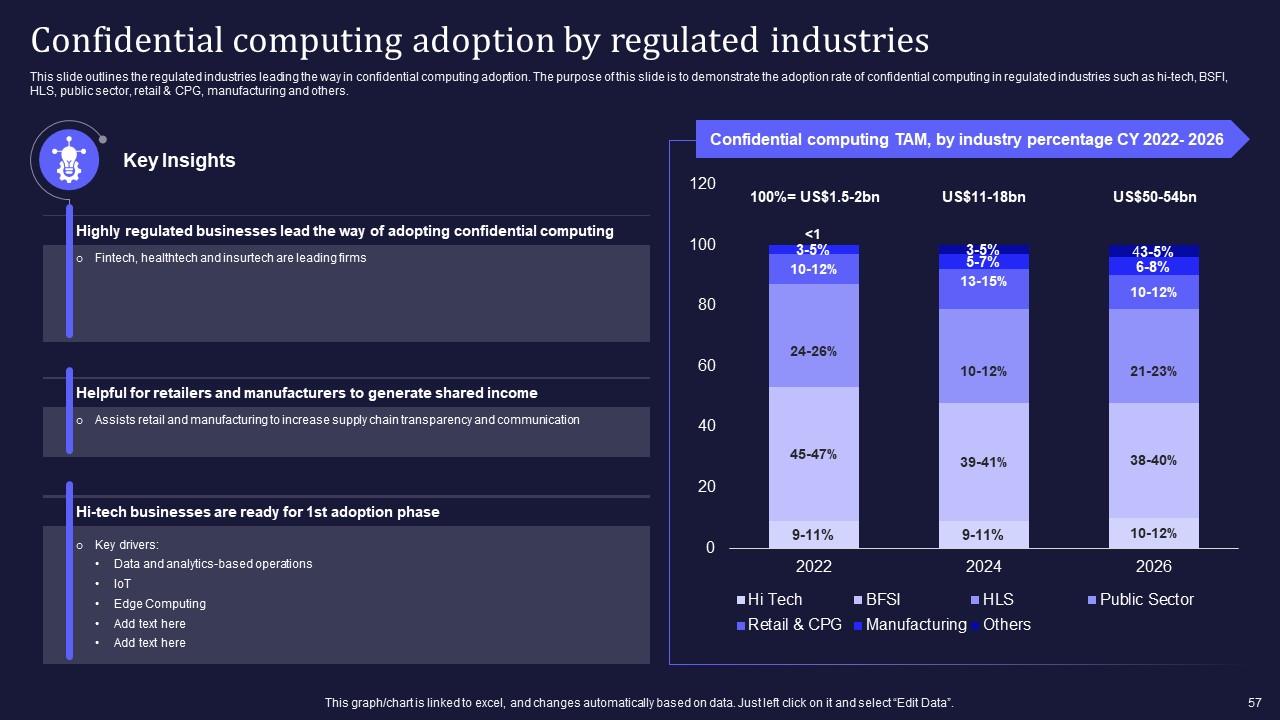
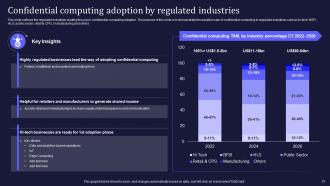
Slide 57: This slide caters to the regulated industries leading the way in confidential computing adoption.
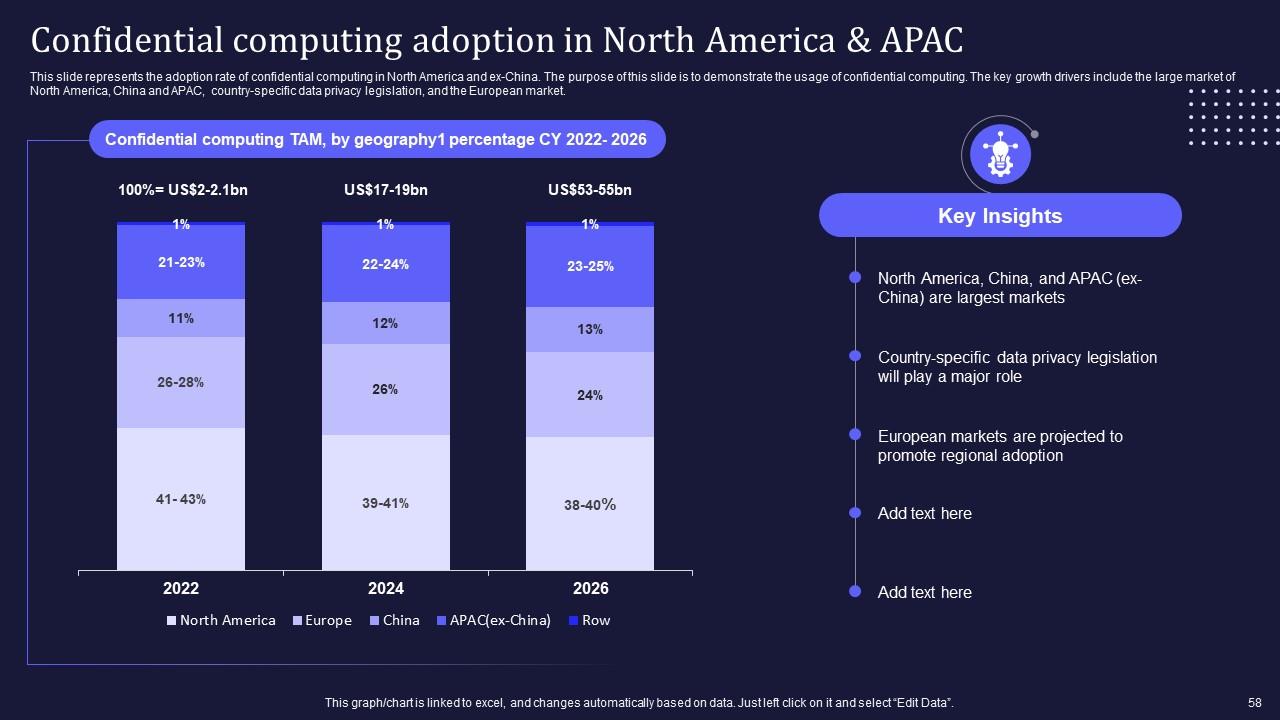
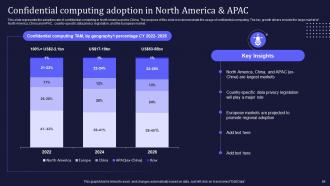
Slide 58: This slide marks the adoption rate of confidential computing in North America and ex-China.
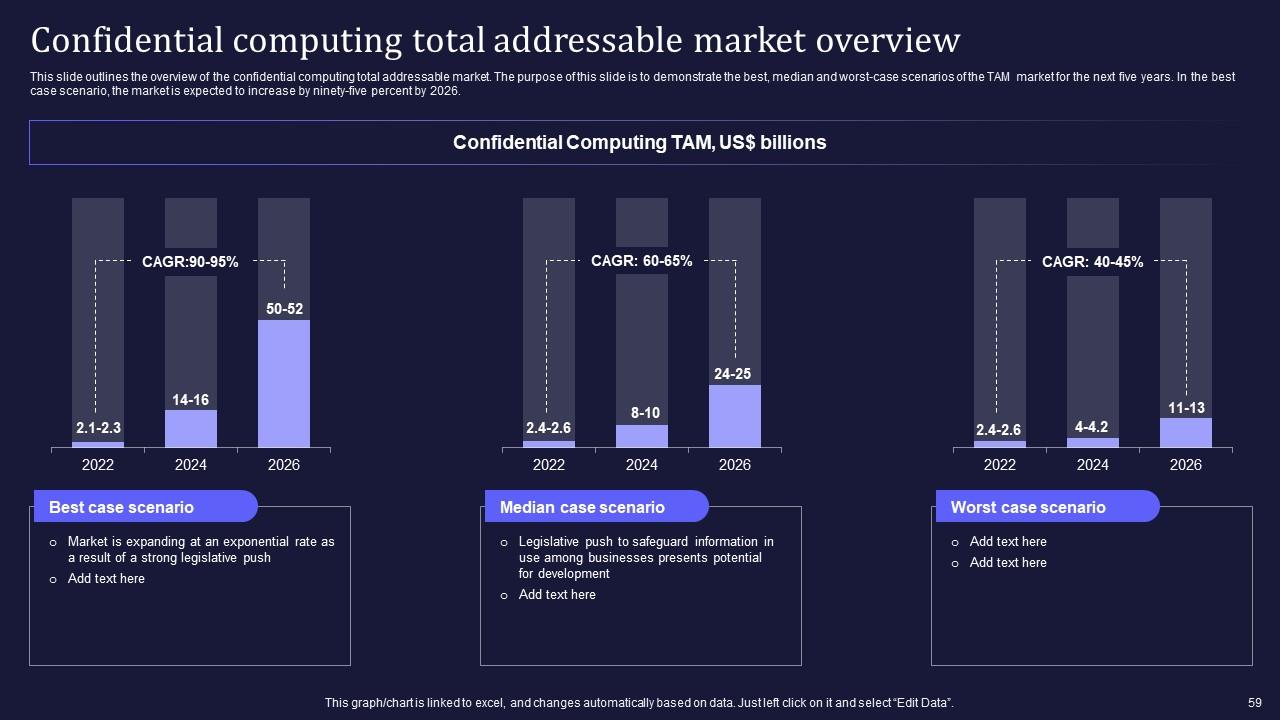
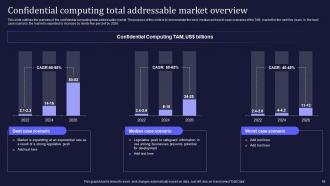
Slide 59: This slide highlights the overview of the confidential computing total addressable market.
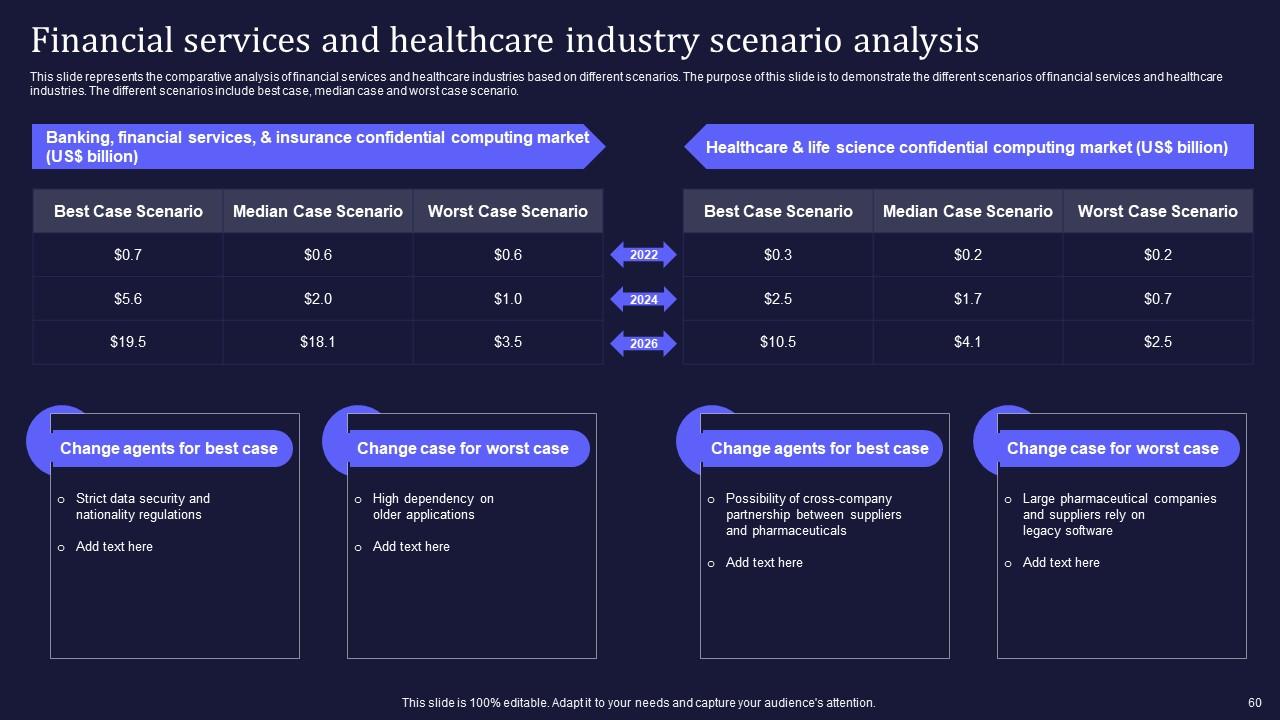
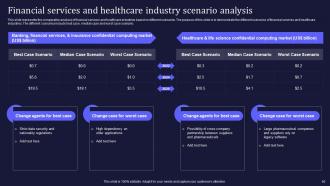
Slide 60: This slide illustrates the comparative analysis of financial services and healthcare industries based on different scenarios.
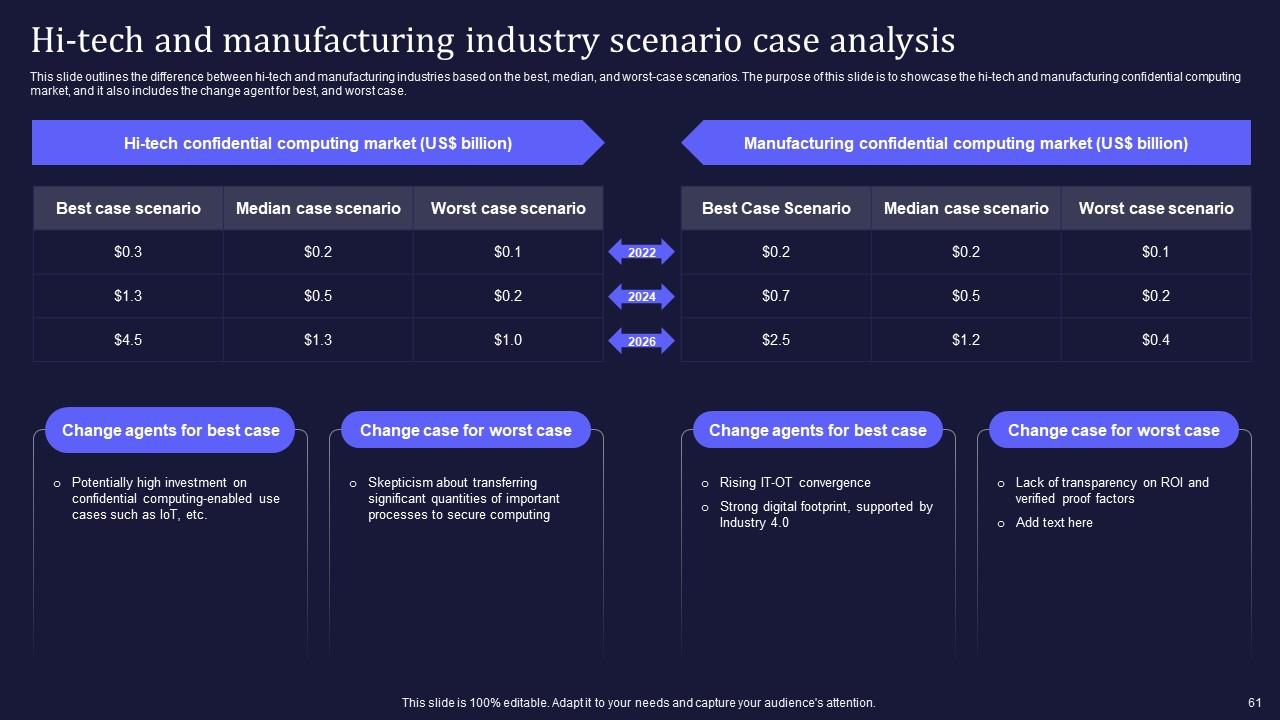
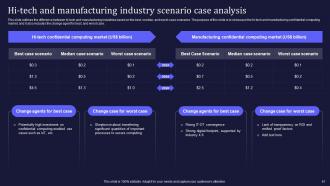
Slide 61: This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios.
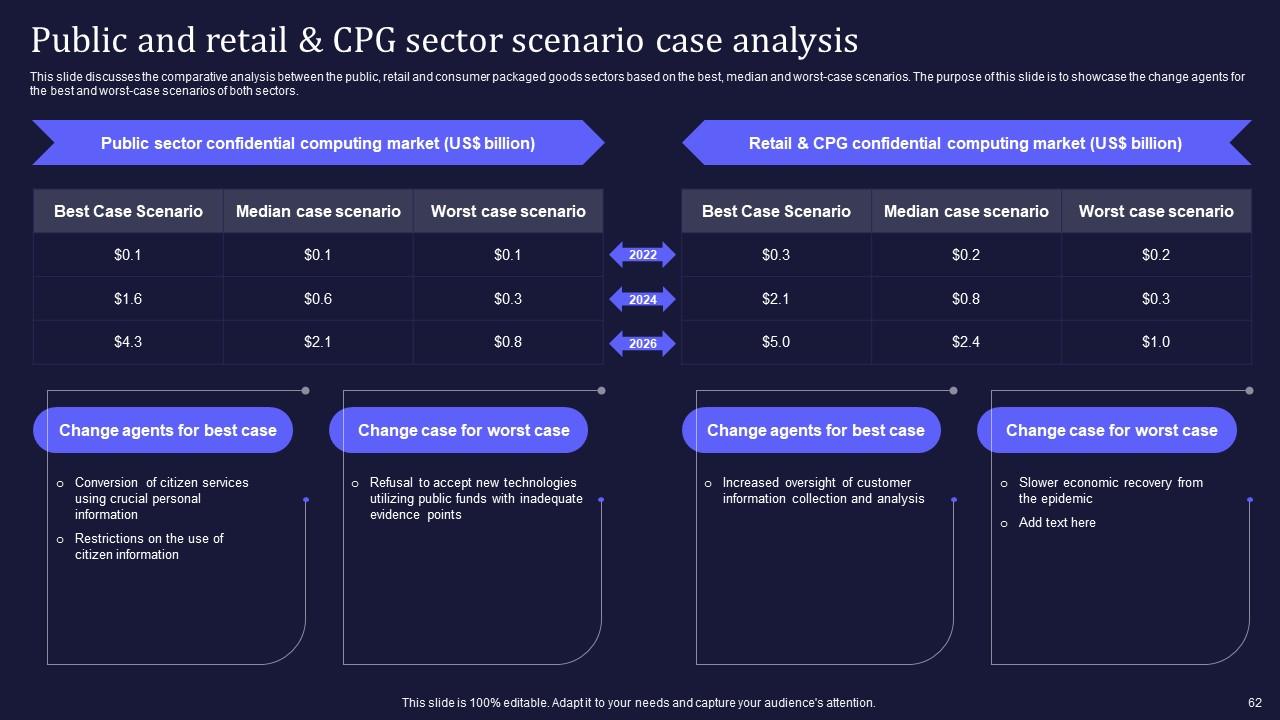
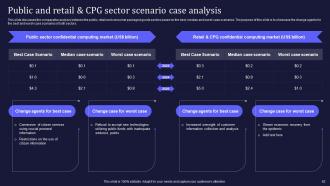
Slide 62: This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios.
Slide 63: This slide is an introductory slide.
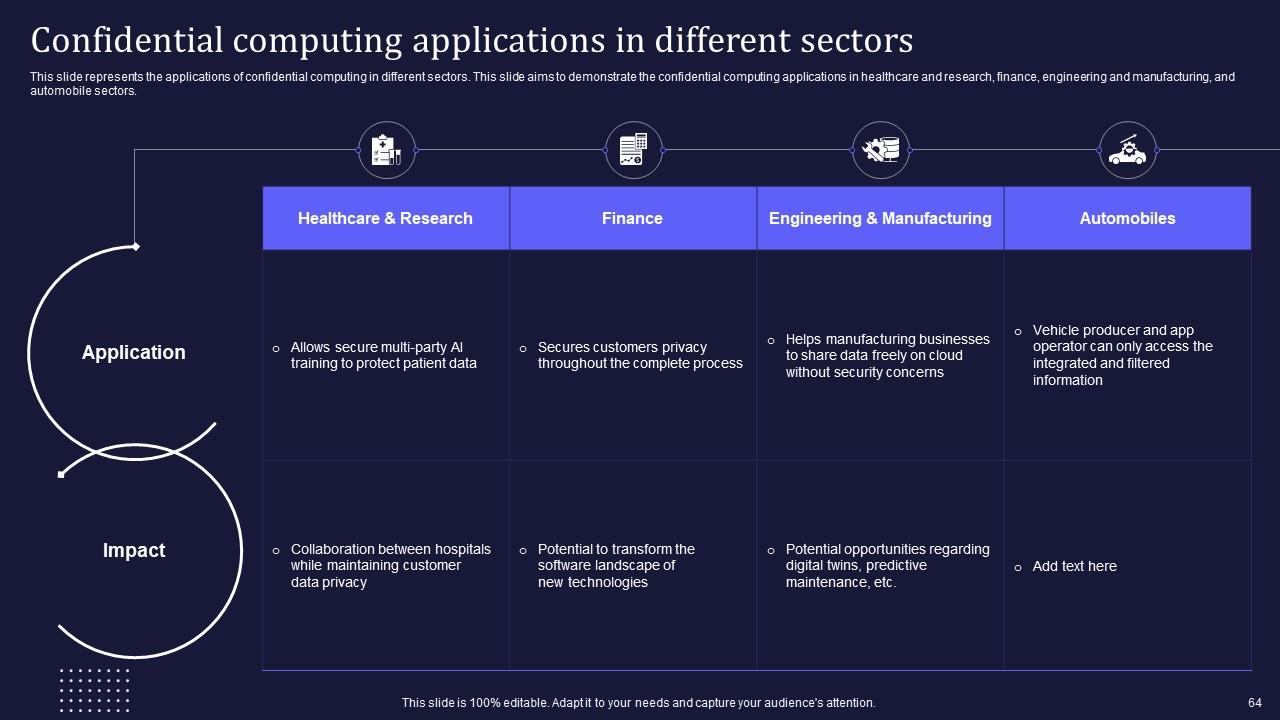
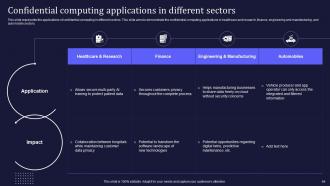
Slide 64: This slide represents the applications of confidential computing in different sectors.
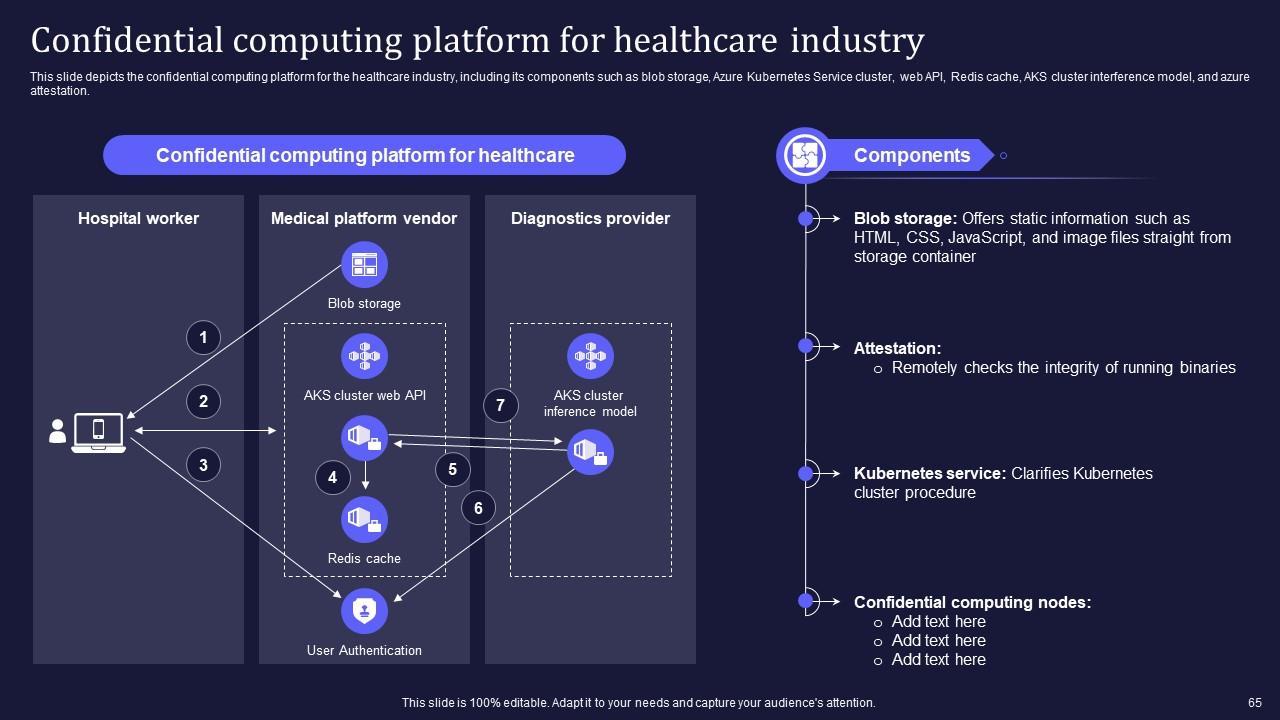
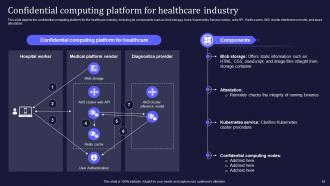
Slide 65: This slide presents the confidential computing platform for the healthcare industry.
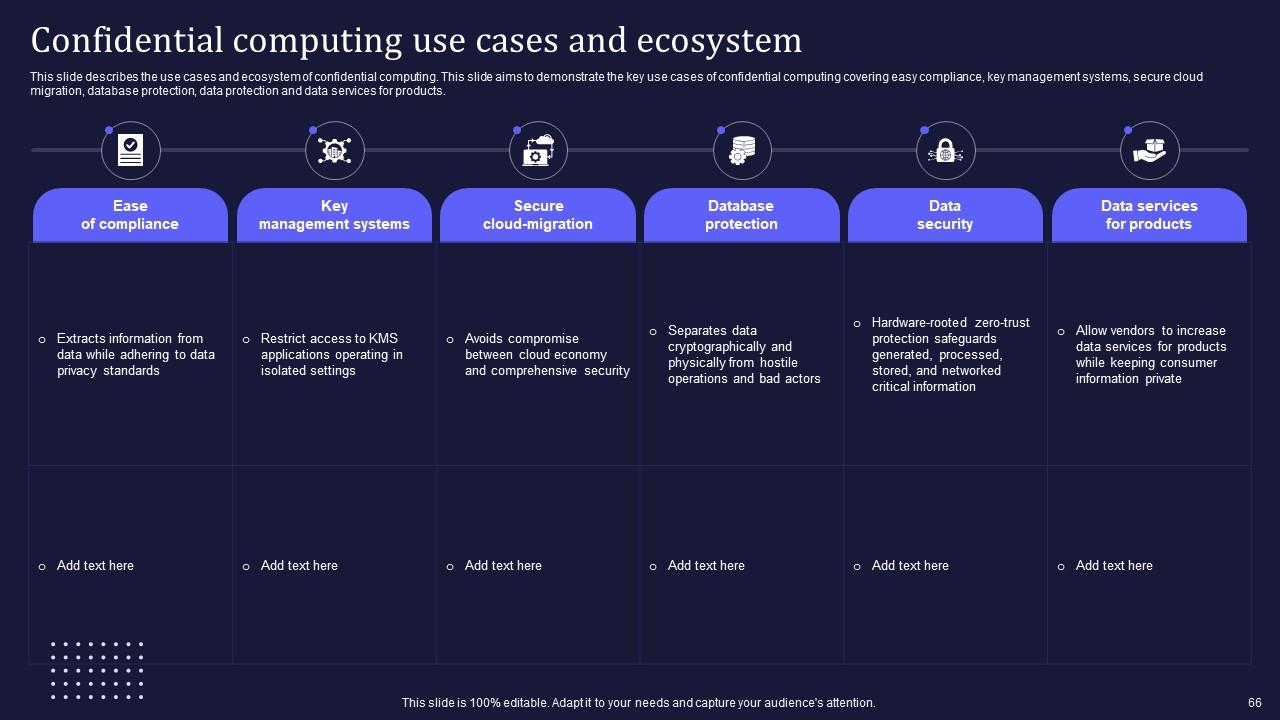
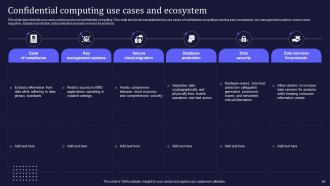
Slide 66: This slide describes the use cases and ecosystem of confidential computing.
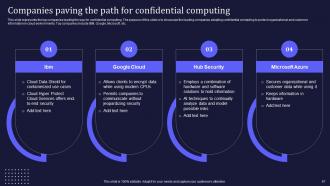
Slide 67: This slide elucidates the top companies leading the way for confidential computing.
Slide 68: This slide is an introductory slide.
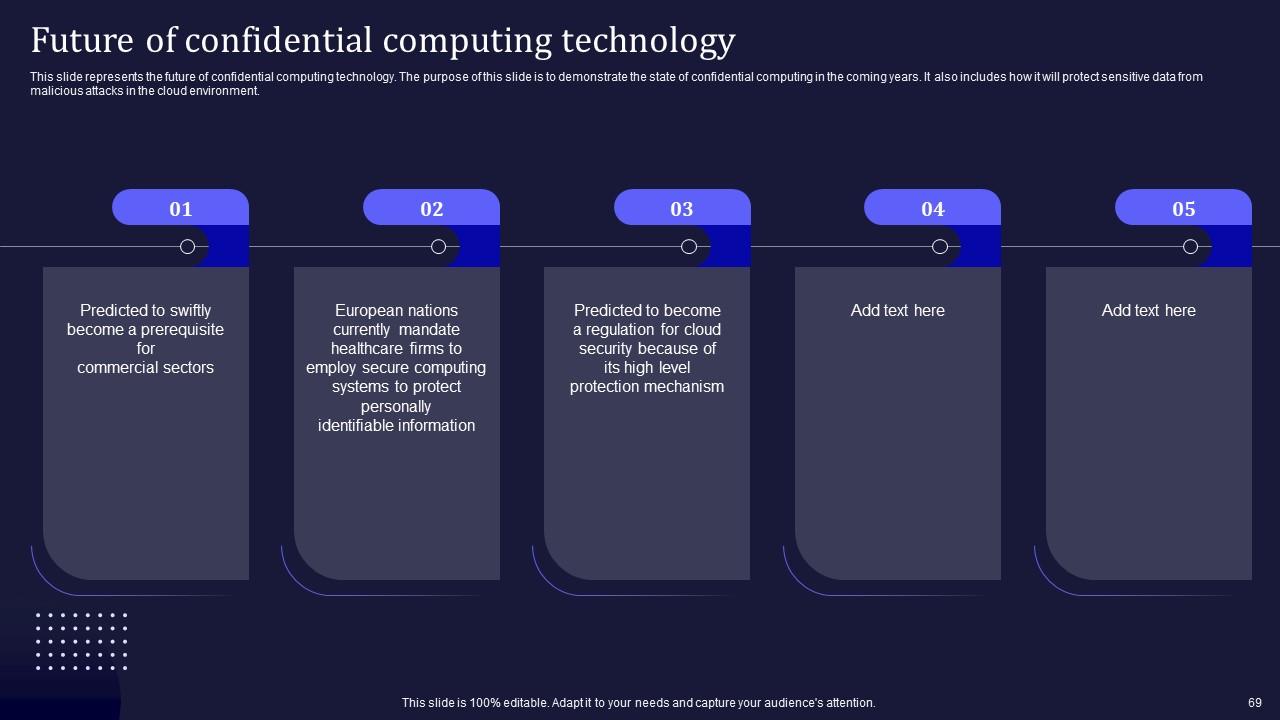
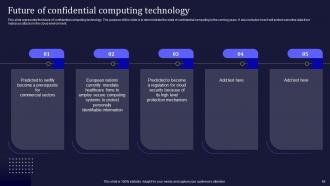
Slide 69: This slide pertains to the future of confidential computing technology.
Slide 70: This slide is an introductory slide.
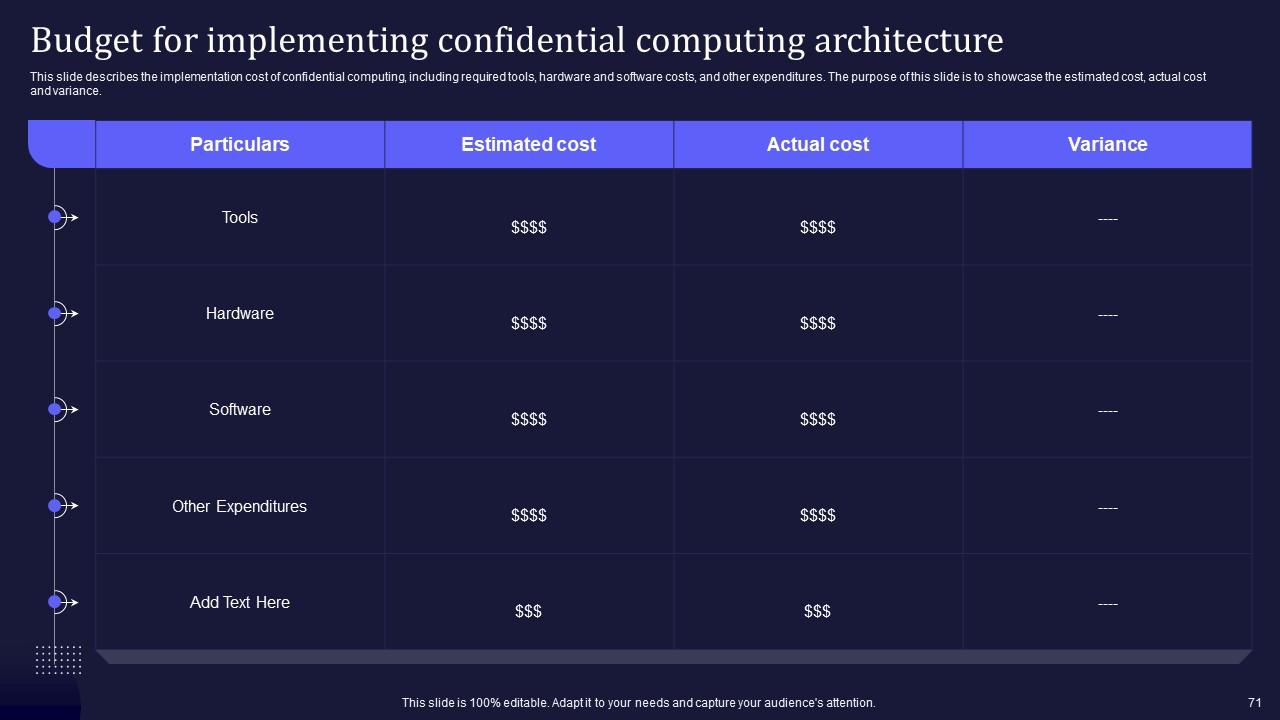
Slide 71: This slide portrays the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures.
Slide 72: This slide is an introductory slide.
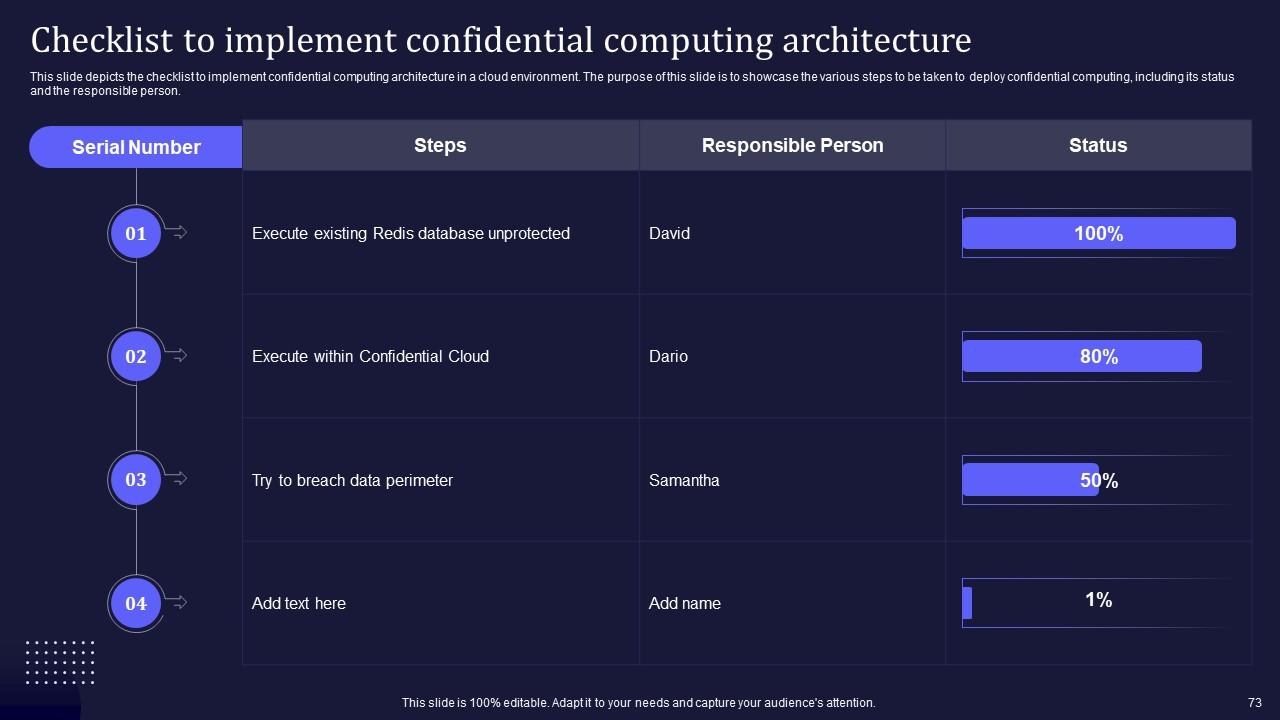
Slide 73: This slide channelises depicts the checklist to implement confidential computing architecture in a cloud environment.
Slide 74: This slide is an introductory slide.
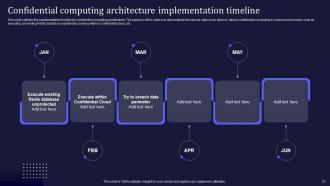
Slide 75: This slide outlines the implementation timeline for confidential computing architecture.
Slide 76: This slide is an introductory slide.
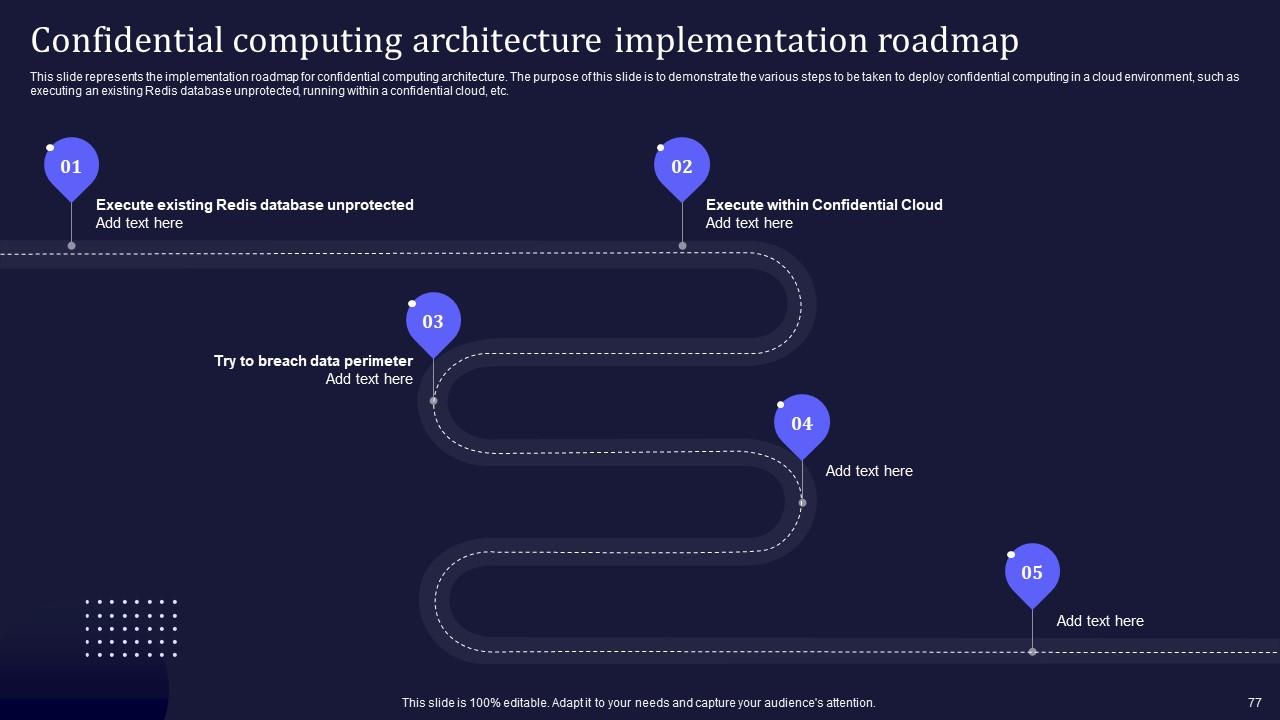
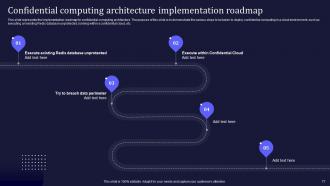
Slide 77: This slide represents the implementation roadmap for confidential computing architecture.
Slide 78: This slide is an introductory slide.
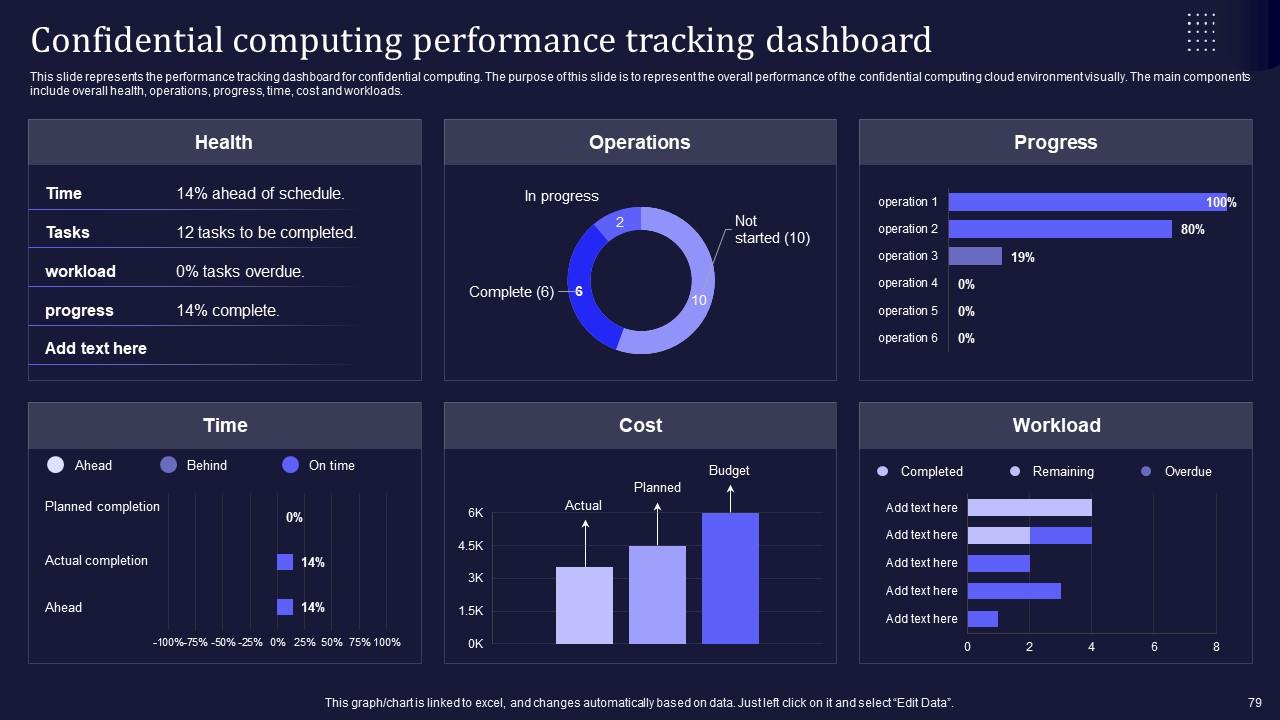
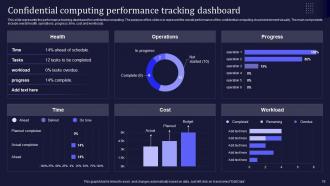
Slide 79: This slide presents the performance tracking dashboard for confidential computing.
Slide 80: This slide is an introductory slide.
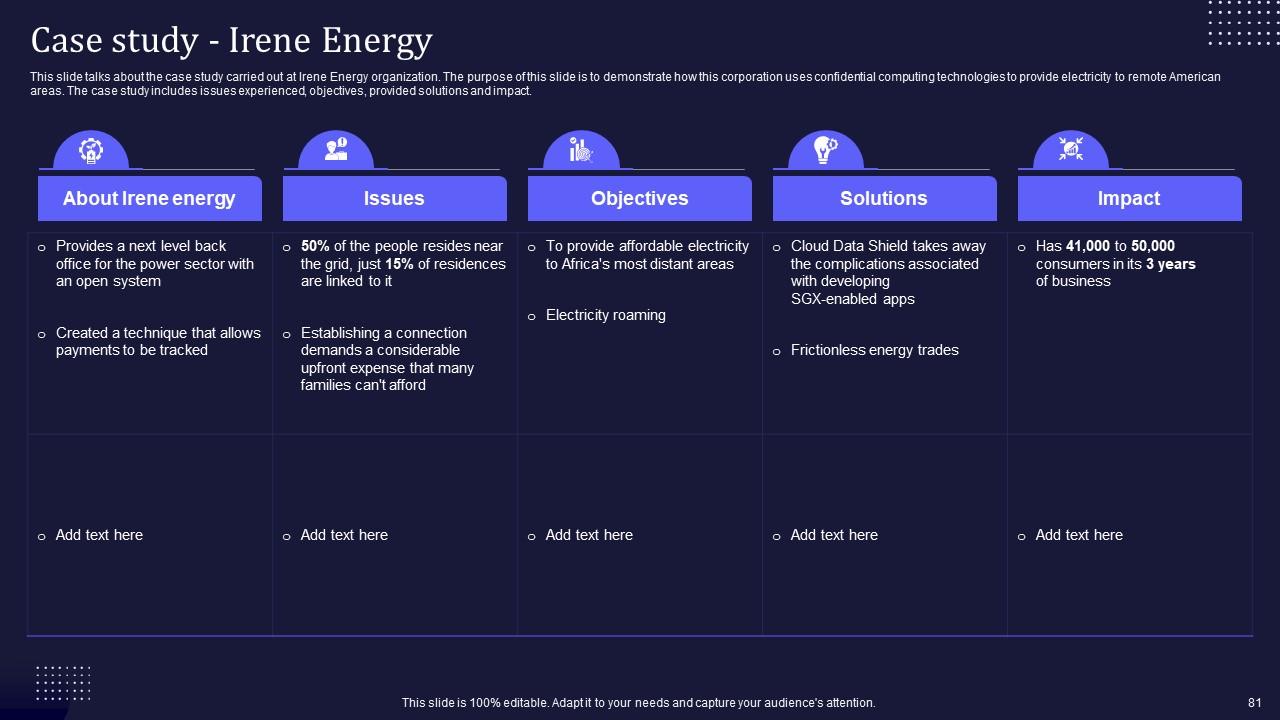
Slide 81: This slide talks about the case study carried out at Irene Energy organization.
Slide 82: This slide shows all the icons included in the presentation.
Slide 83: This slide is titled Additional Slides for moving forward.
Slide 84: This slide depicts a Venn diagram with text boxes.
Slide 85: This slide contains a Puzzle with related icons and text.
Slide 86: This slide shows Post-It Notes. Post your important notes here.
Slide 87: This slide is a financial slide. Show your finance-related stuff here.
Slide 88: This slide provides a 30-60-90-day plan with text boxes.
Slide 89: This slide is a thank-you slide with address, contact numbers, and email address.
Confidential Computing V2 Powerpoint Presentation Slides with all 98 slides:
Use our Confidential Computing V2 Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
My search for complete decks ended with SlideTeam. Such a surplus collection of HD PowerPoints. Moreover, their standard and widescreen formats have helped me in delivering bullseye presentations.
-
I discovered this website through a google search, the services matched my needs perfectly and the pricing was very reasonable. I was thrilled with the product and the customer service. I will definitely use their slides again for my presentations and recommend them to other colleagues.