Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD
Our Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Our Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD are topically designed..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
If you require a professional template with great design, then this Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty one slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Cyber Threats Management to Enable Digital Assets Security. State your company name and begin.
Slide 2: This slide shows Table of Content for the presentation.
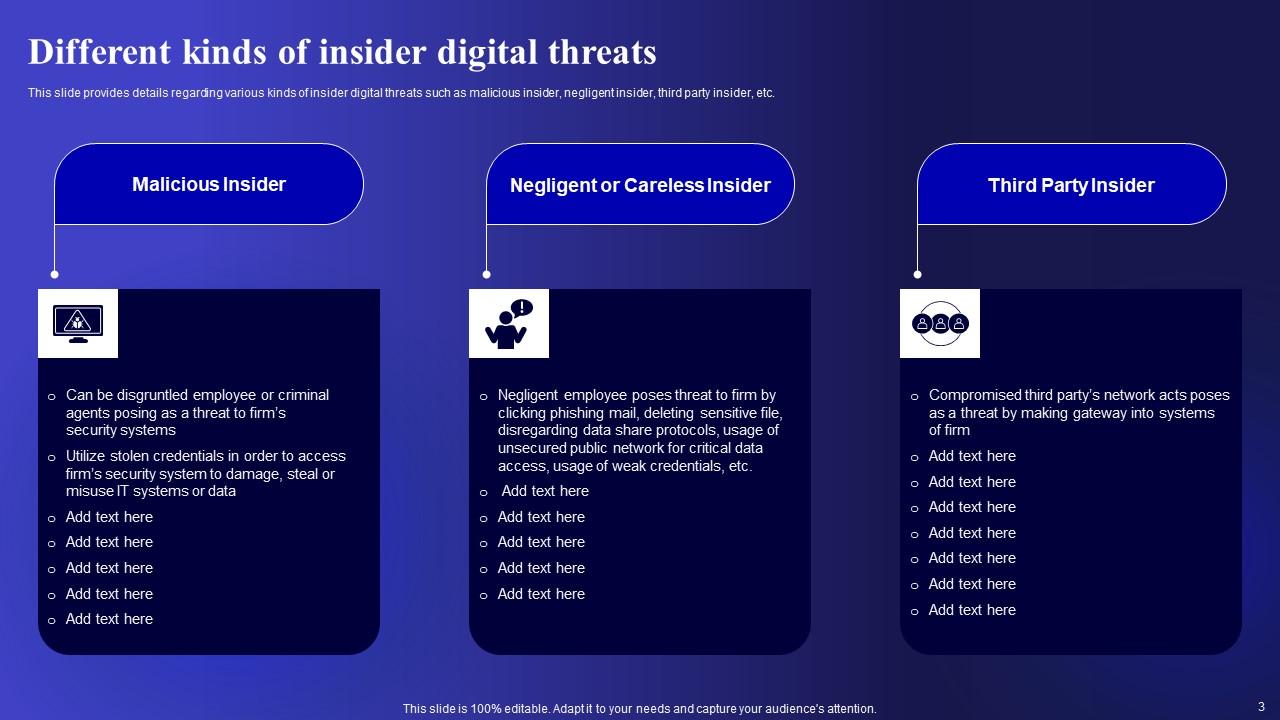
Slide 3: This slide presents Different kinds of insider digital threats.
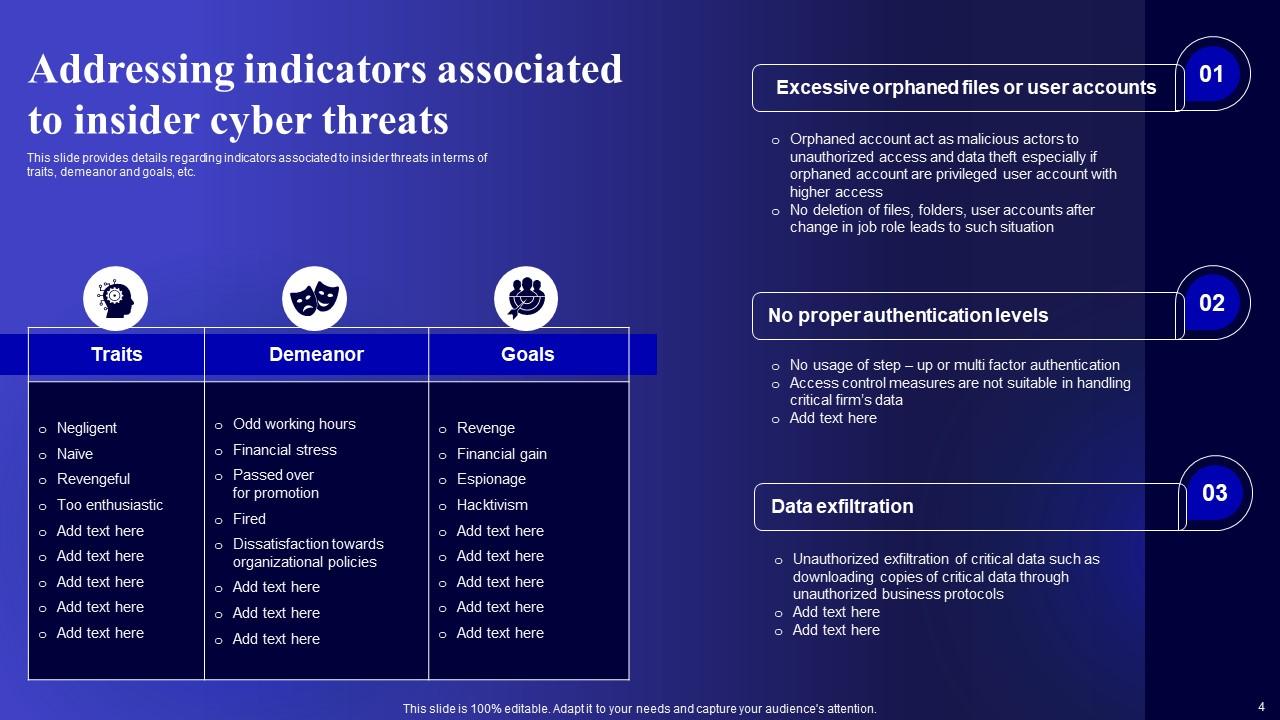
Slide 4: This slide displays Addressing indicators associated to insider cyber threats.
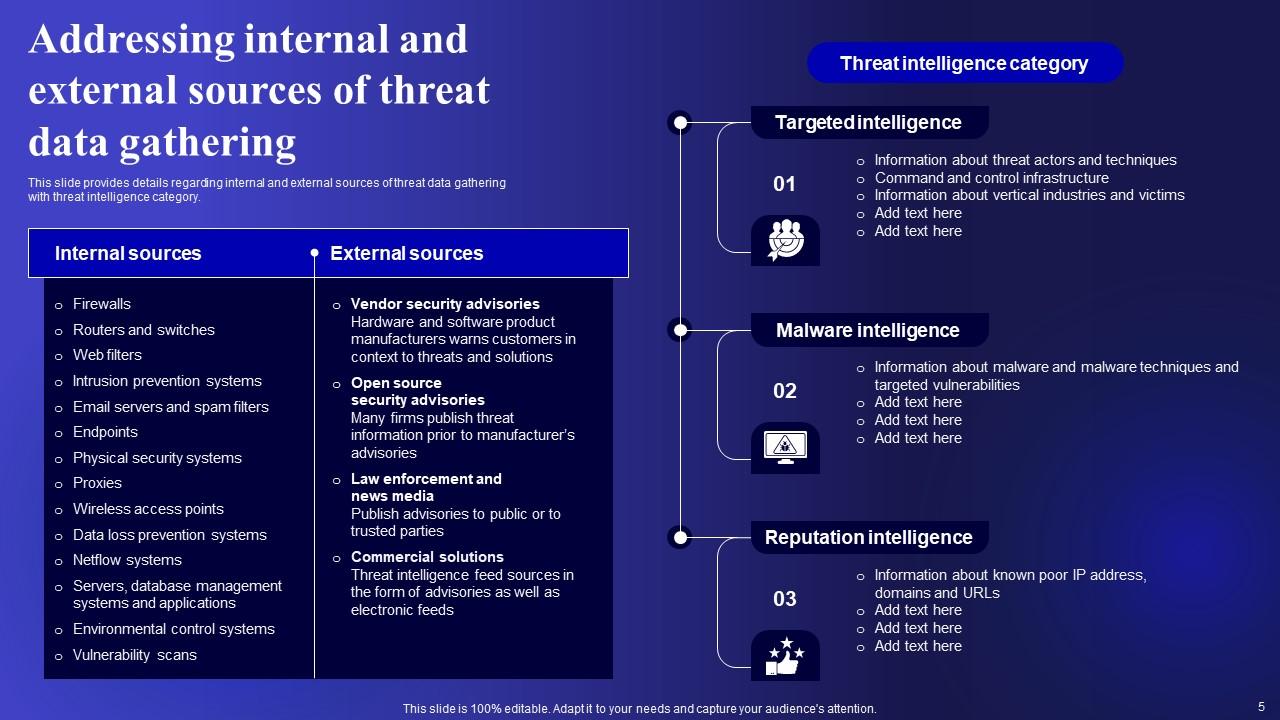
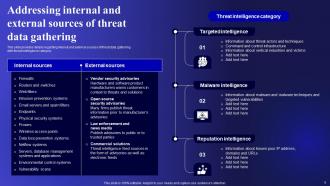
Slide 5: This slide represents Addressing internal and external sources of threat data gathering.
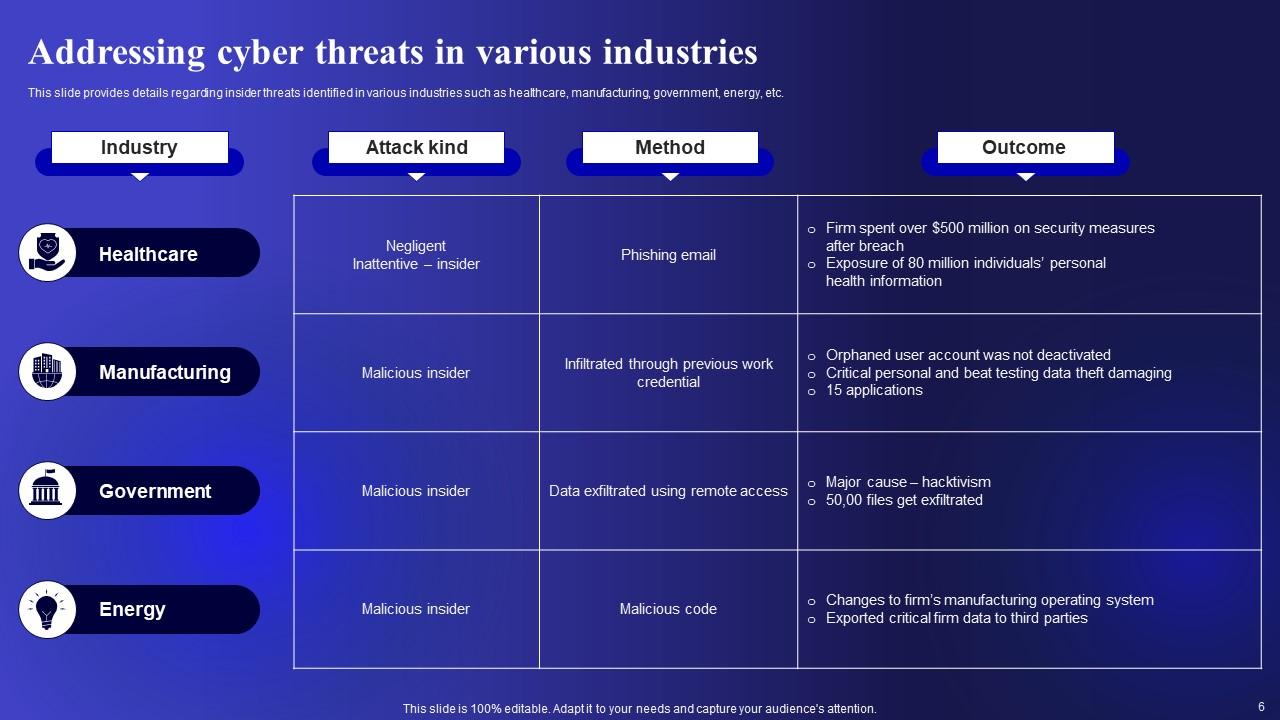
Slide 6: This slide showcases Addressing cyber threats in various industries.
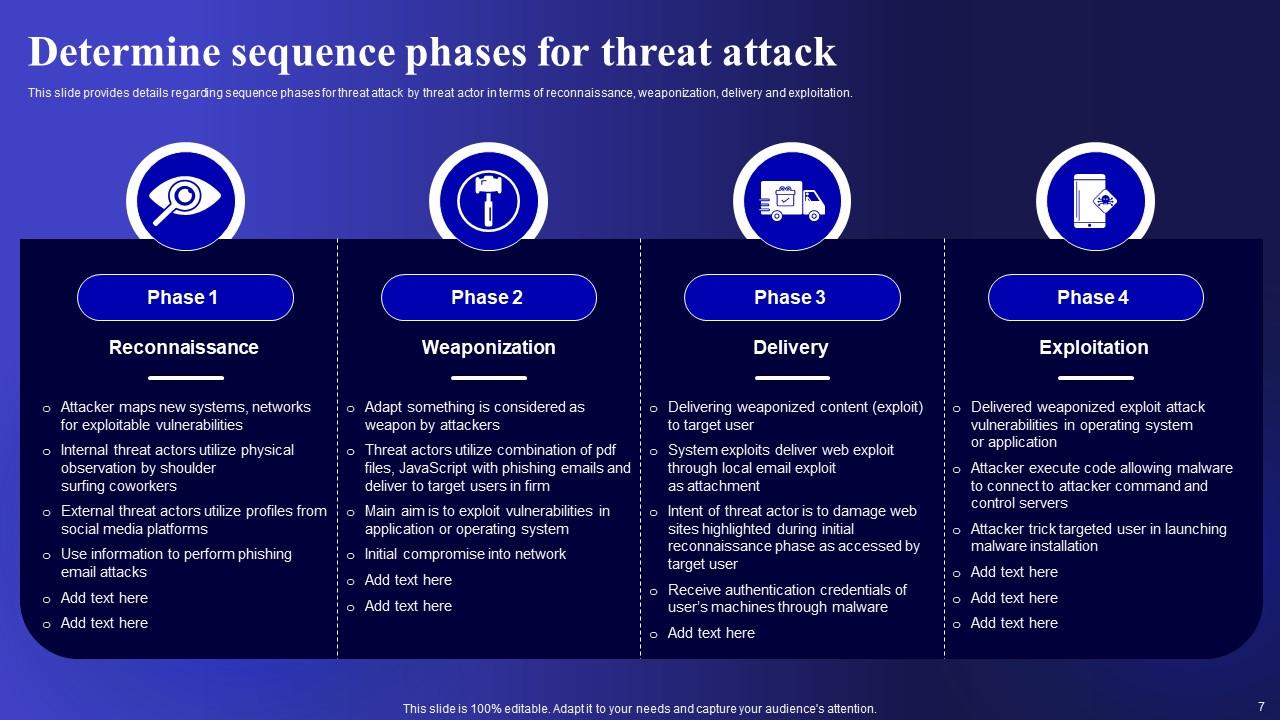
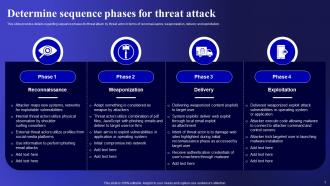
Slide 7: This slide shows Determine sequence phases for threat attack.
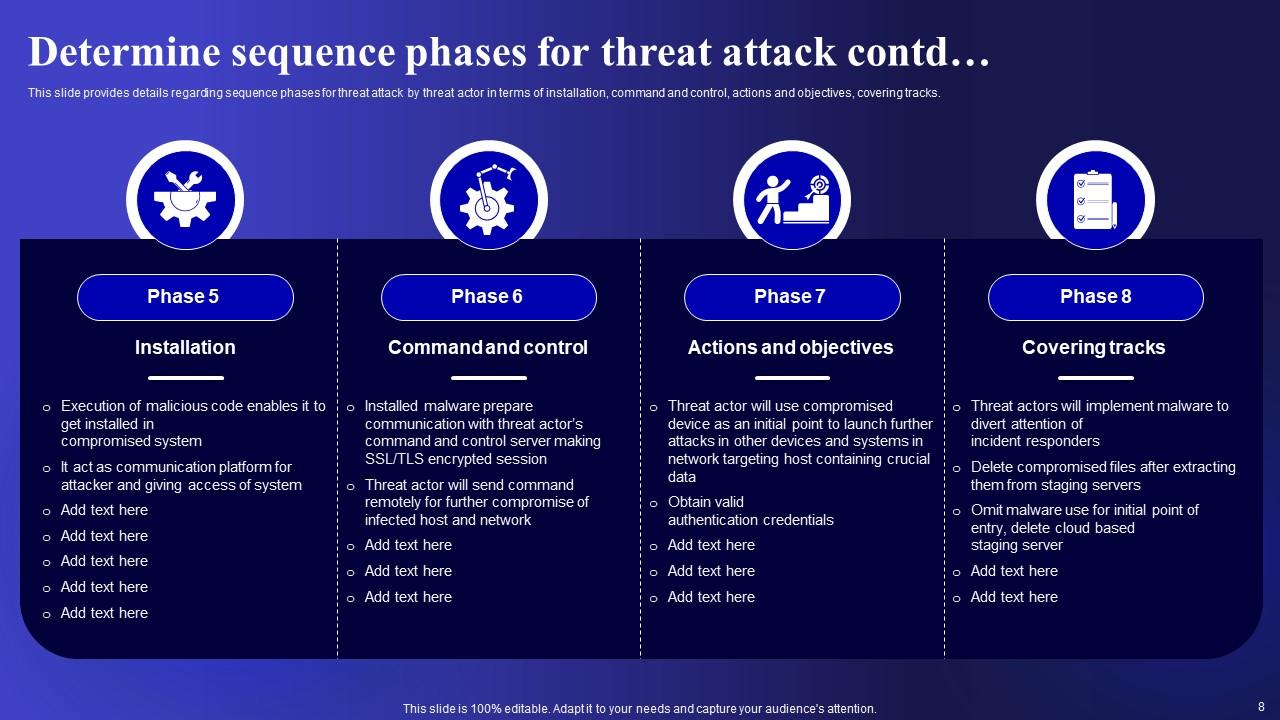
Slide 8: This is another slide continuing Determine sequence phases for threat attack.
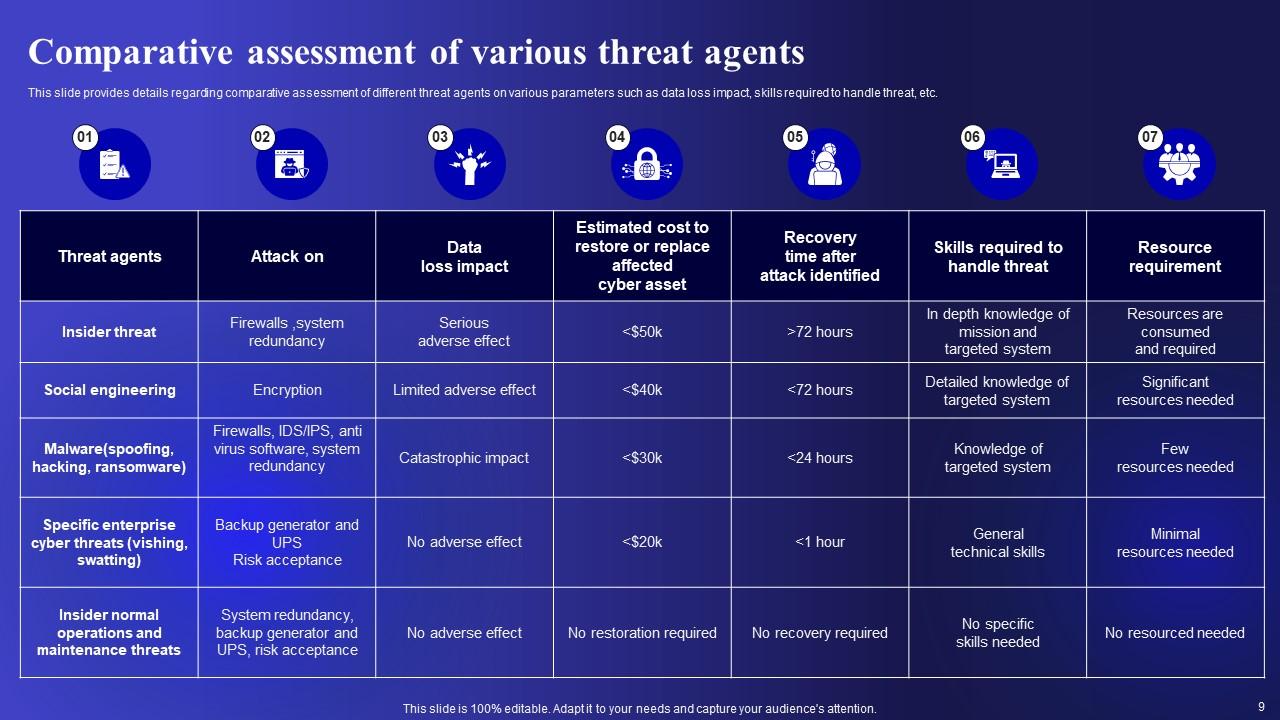
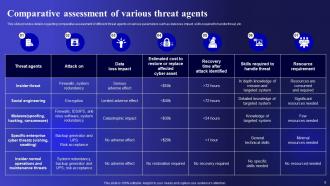
Slide 9: This slide presents Comparative assessment of various threat agents.
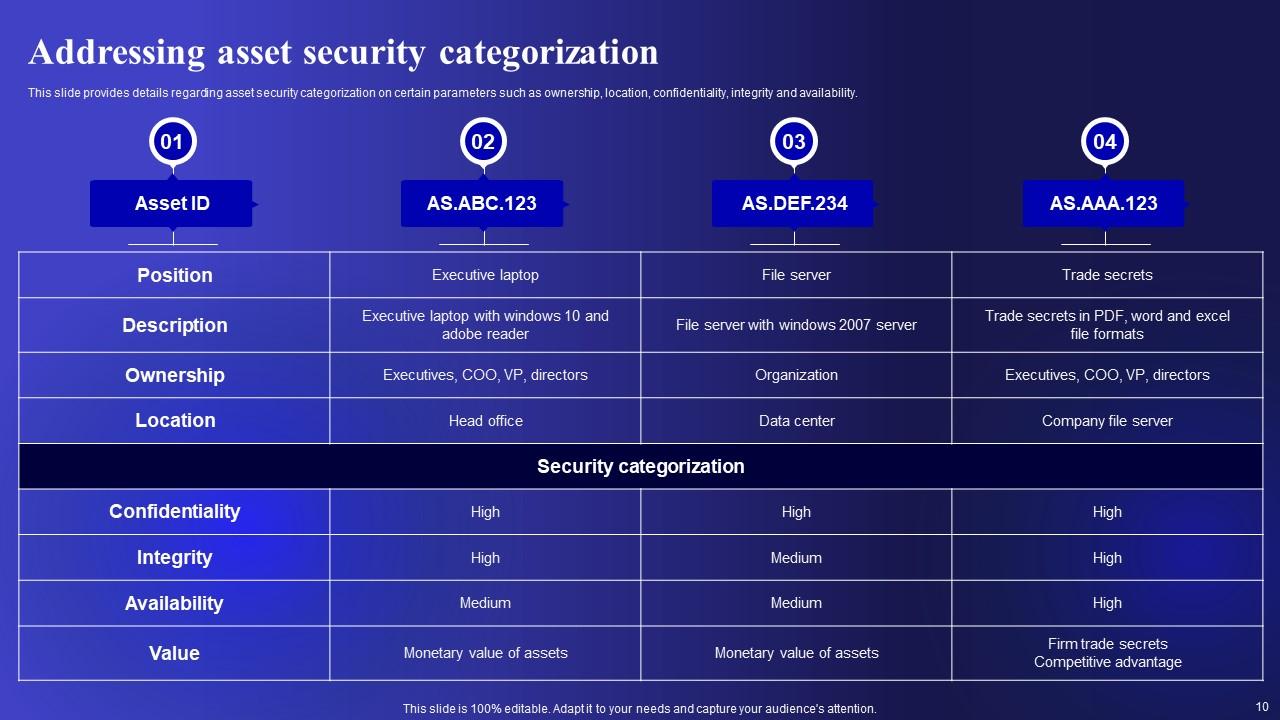
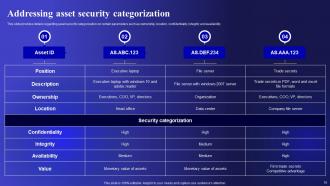
Slide 10: This slide displays Addressing asset security categorization.
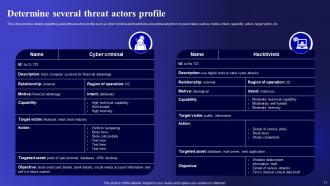
Slide 11: This slide represents Determine several threat actors profile.
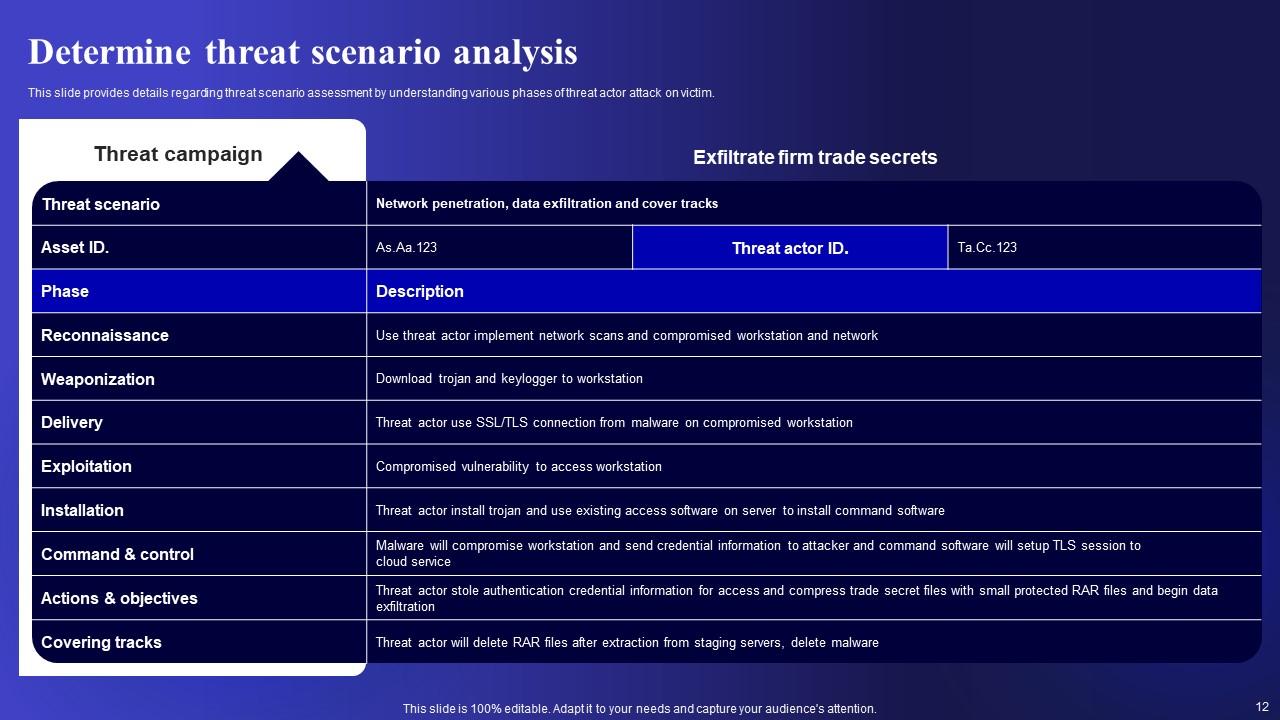
Slide 12: This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim.
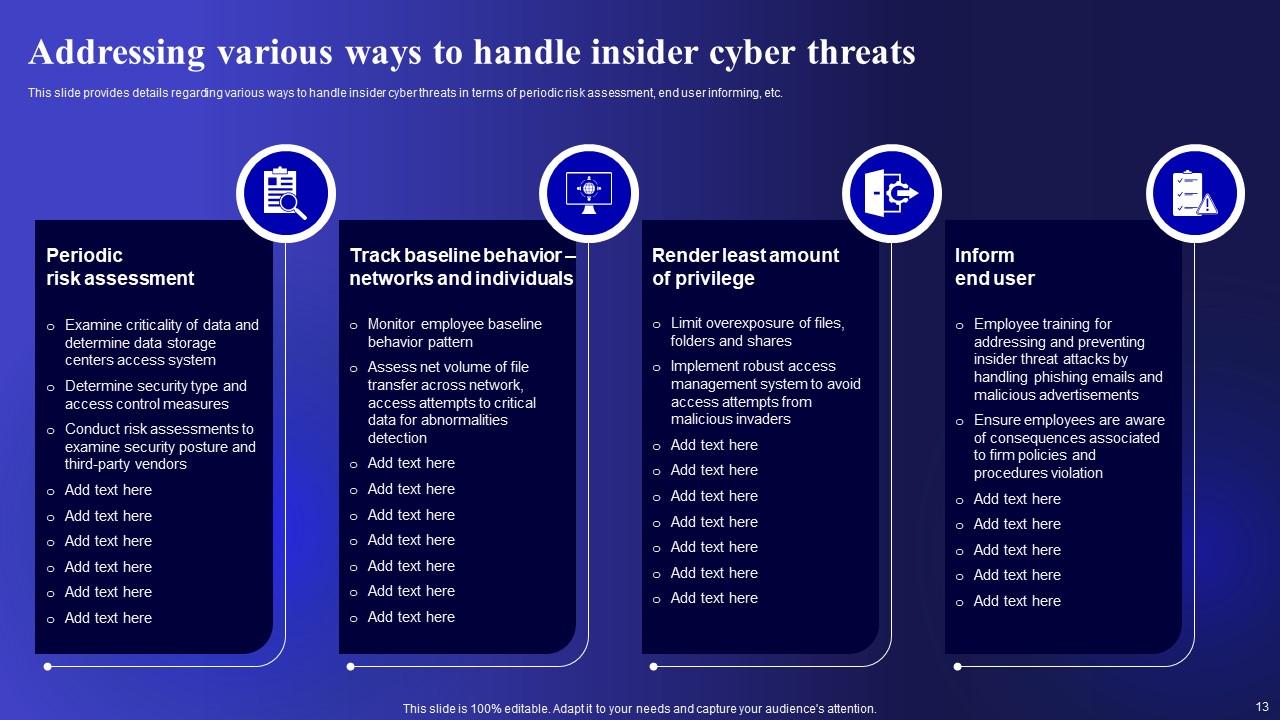
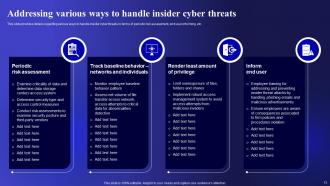
Slide 13: This slide showcases Addressing various ways to handle insider cyber threats.
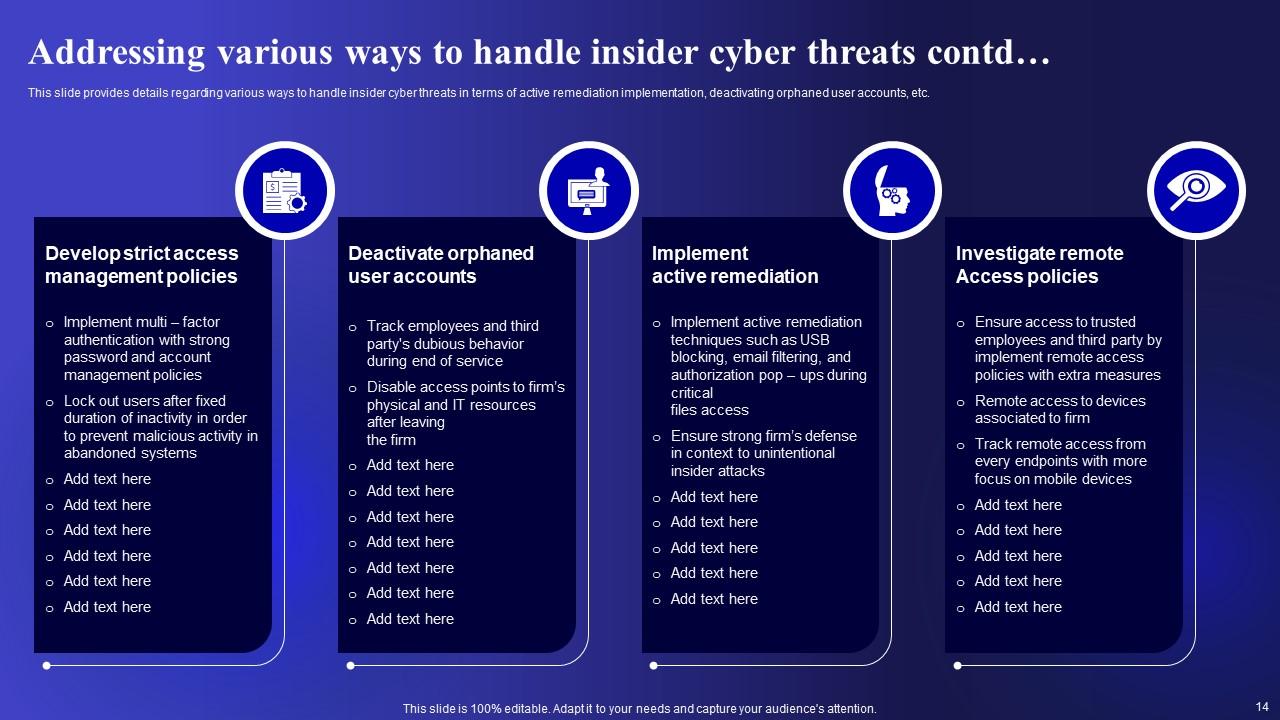
Slide 14: This is another slide continuing Addressing various ways to handle insider cyber threats.
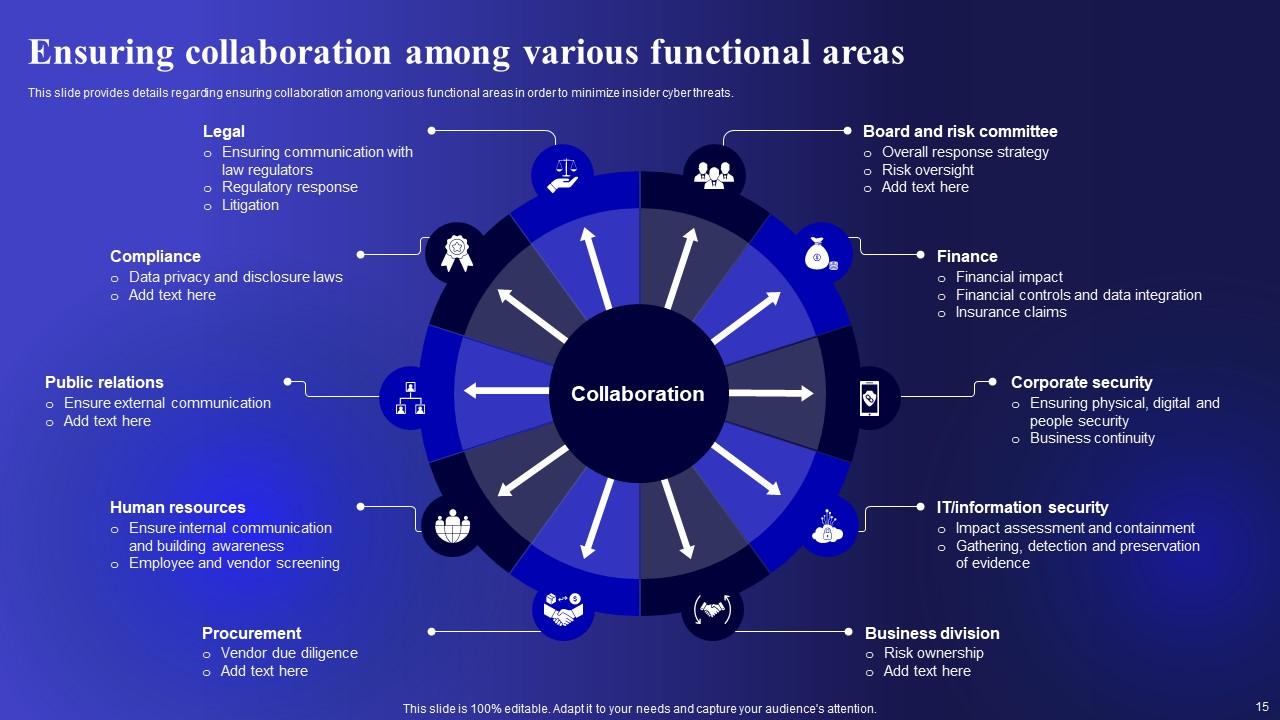
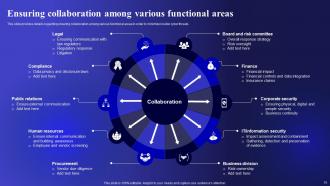
Slide 15: This slide shows Ensuring collaboration among various functional areas.
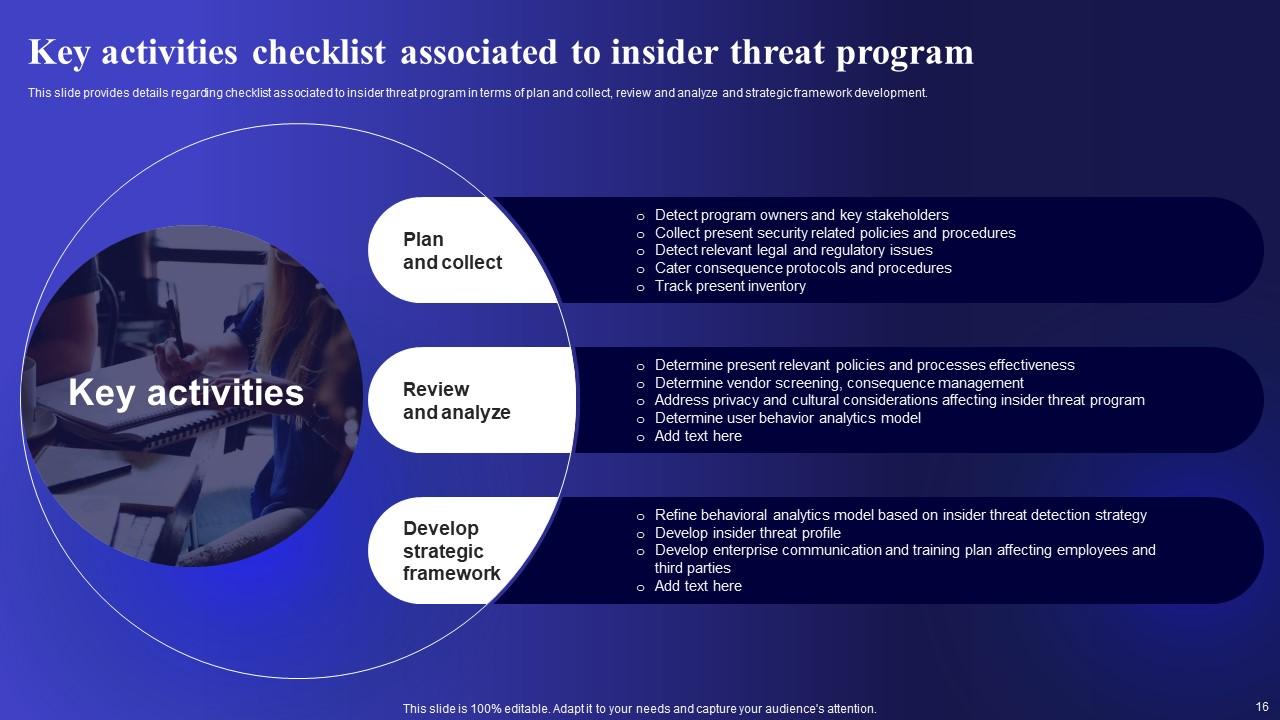
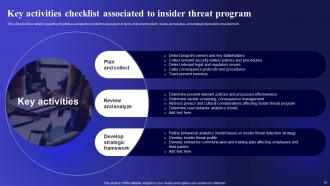
Slide 16: This slide presents Key activities checklist associated to insider threat program.
Slide 17: This slide displays Contingency plan for cyber threat handling.
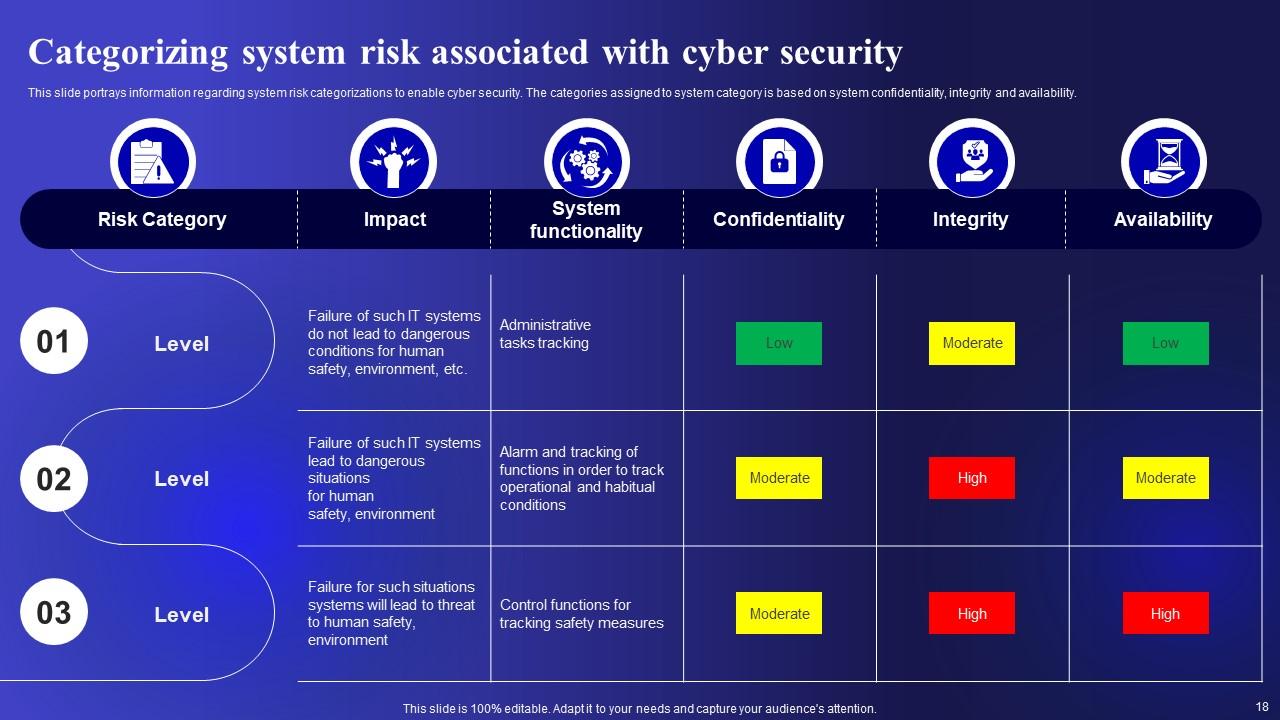
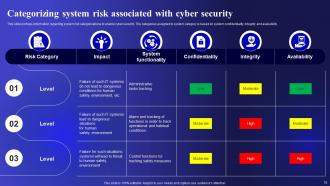
Slide 18: This slide represents Categorizing system risk associated with cyber security.
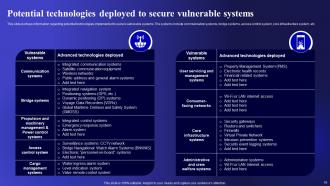
Slide 19: This slide showcases Potential technologies deployed to secure vulnerable systems.
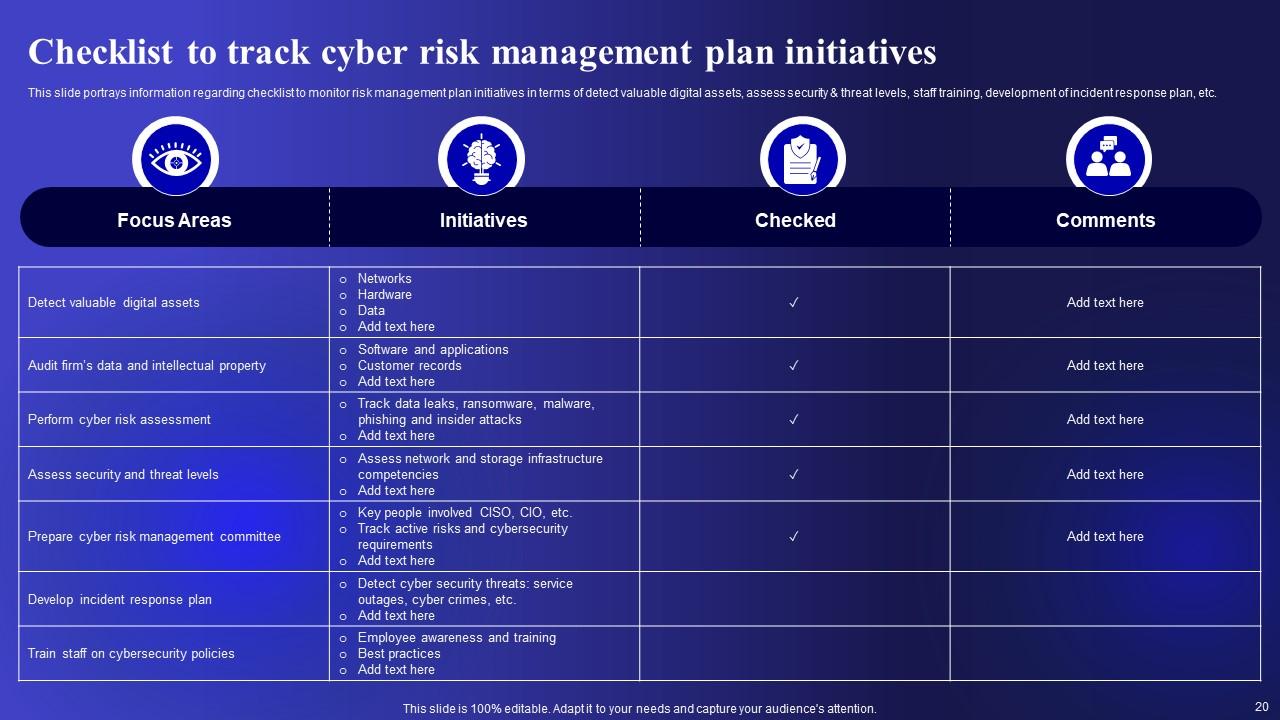
Slide 20: This slide shows Checklist to track cyber risk management plan initiatives.
Slide 21: This is a Thank You slide with address, contact numbers and email address.
Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD with all 26 slides:
Use our Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Informative presentations that are easily editable.
-
I was confident and well prepared for my presentation for the first time ever. With SlideTeam’s templates, I could deliver one of my best presentations. Will be coming back for more!