Deploying Computer Security Incident Management Powerpoint Presentation Slides
Protecting against cyber threats is crucial in todays digital age, and the ability to quickly identify, record, and analyze such incidents is essential. Our professionally designed Deploying computer security incident management deck offers a comprehensive view of the security challenges faced by organizations and provides a roadmap for managing cyber attacks. It covers a range of topics, including the roles and responsibilities of the cybersecurity team, budgetary considerations, and the impact of cyber attacks on business operations. Our Computer issues management deck includes a response checklist, best practices for managing risks, and an events flow diagram, all of which are essential for maintaining effective cybersecurity. It also features a detailed incident response plan and shares critical lessons learned by incident management teams after dealing with cyber incidents. Additionally, our Phishing Attack Administration module provides insights into the techniques used by cybercriminals and ways to protect against them. With our powerful template, you can stay one step ahead of cyber threats and safeguard your organizations valuable data.
Protecting against cyber threats is crucial in todays digital age, and the ability to quickly identify, record, and analyze..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Deploying Computer Security Incident Management Powerpoint Presentation Slides V is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the seventy slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Deploying Computer Security Incident Management. Commence by stating Your Company Name.
Slide 2: This slide depicts the Agenda of the presentation.
Slide 3: This slide includes the Table of contents.
Slide 4: This slide highlights the Title for the Topics to be covered further.
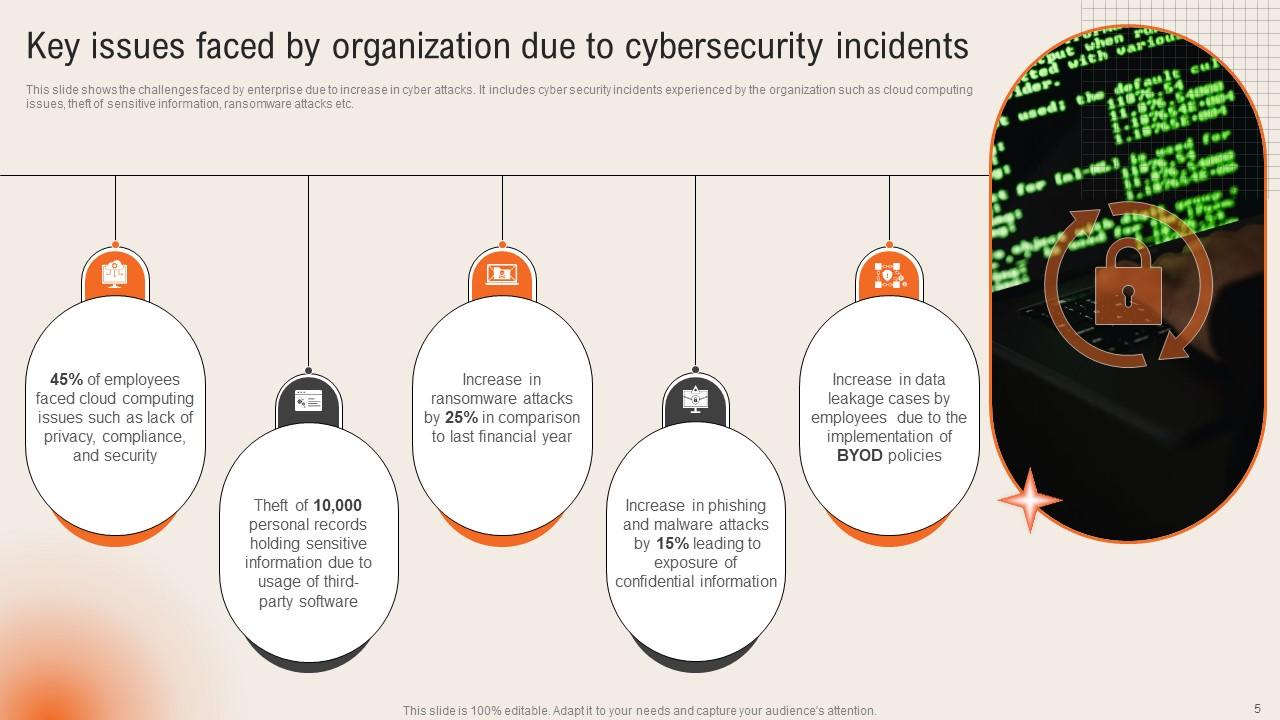
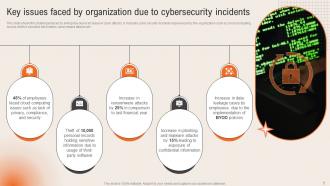
Slide 5: This slide highlights the Key issues faced by organization due to cybersecurity incidents.
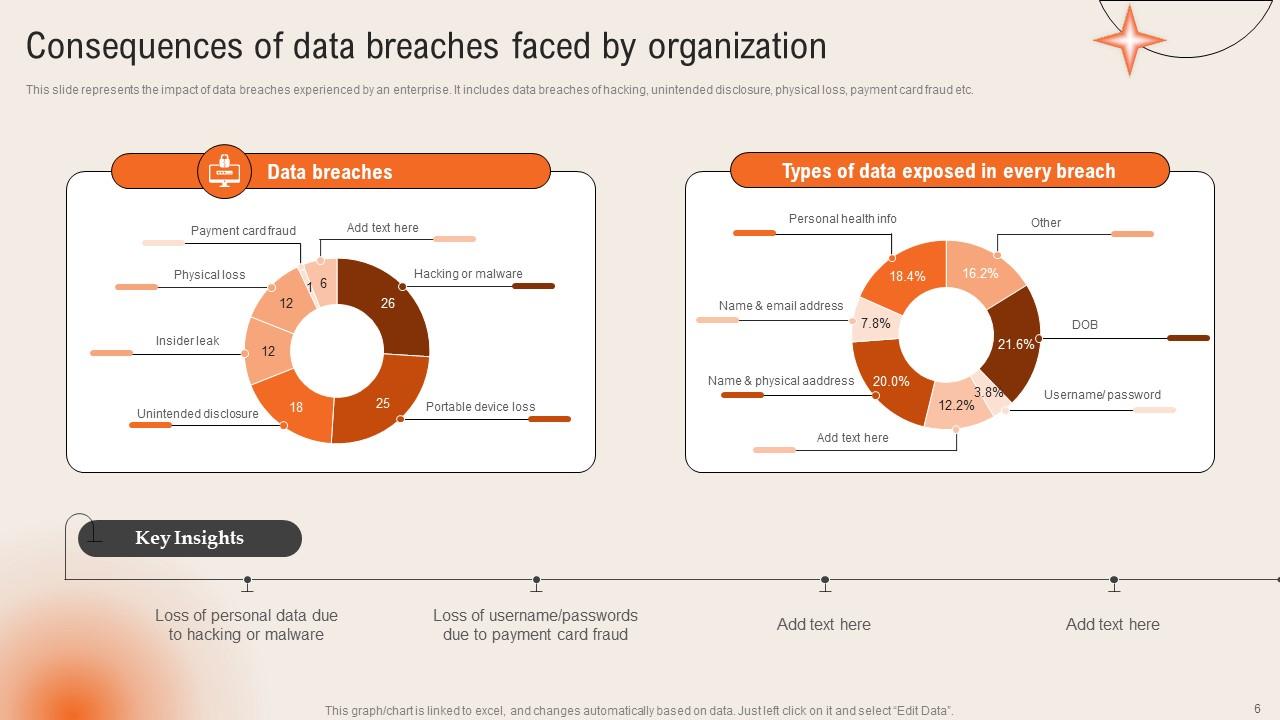
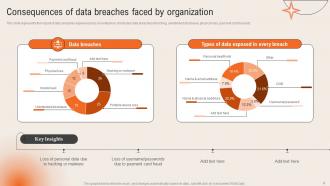
Slide 6: This slide reveals the Consequences of data breaches faced by organization.
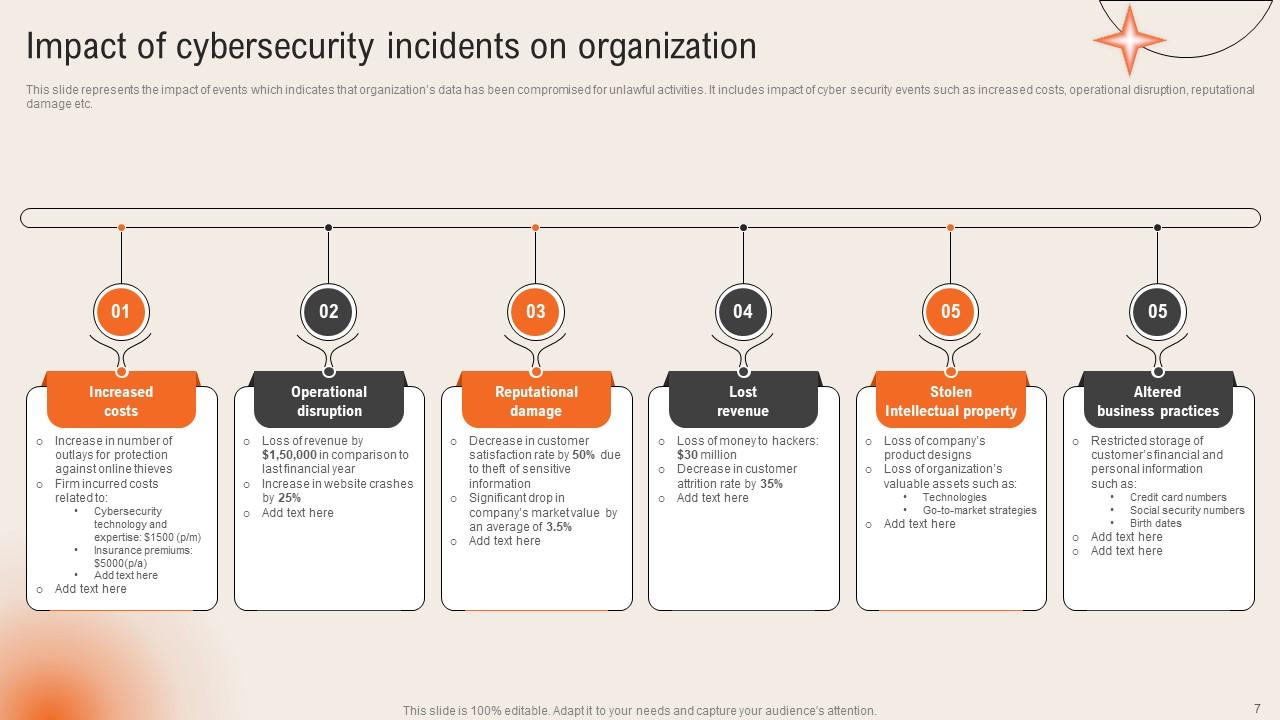
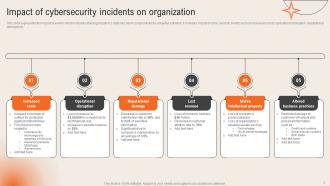
Slide 7: This slide displays the Impact of cybersecurity incidents on organization.
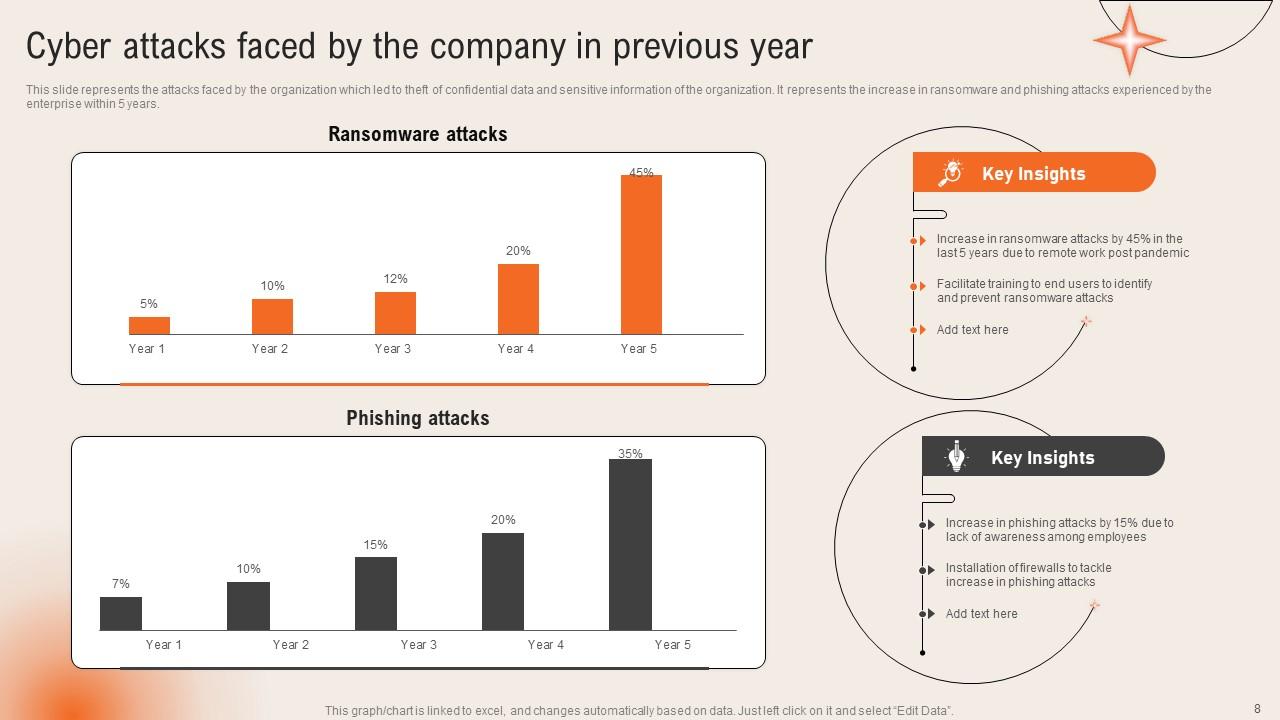
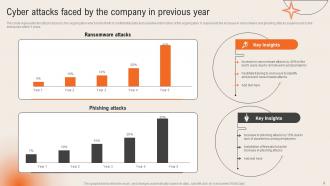
Slide 8: This slide talks about the Cyber attacks faced by the company in previous year.
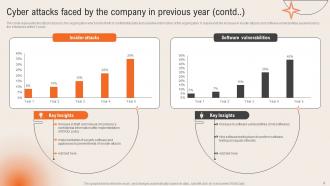
Slide 9: This slide continues the Cyber attacks faced by the company in previous year.
Slide 10: This slide reveals the Gap analysis representing current situation of cybersecurity incident management.
Slide 11: This slide portrays the Heading for the Contents to be discussed next.
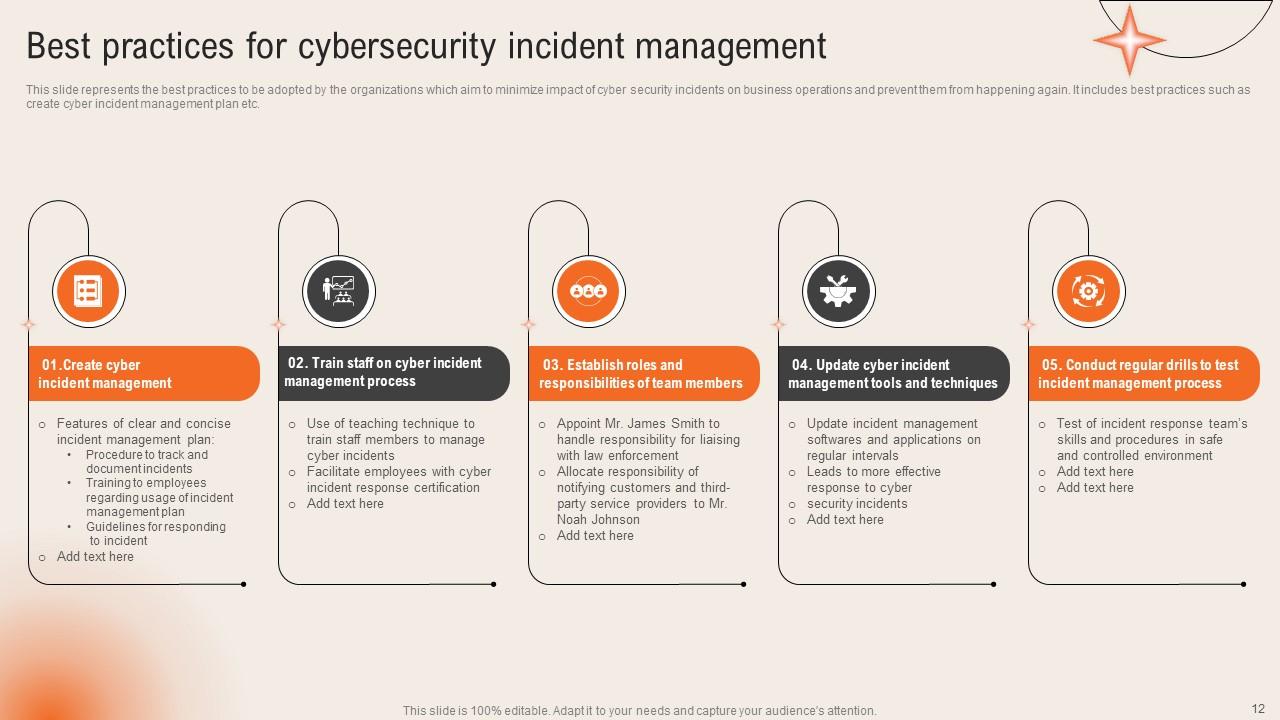
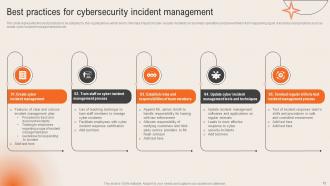
Slide 12: This slide exhibits the Best practices for cybersecurity incident management.
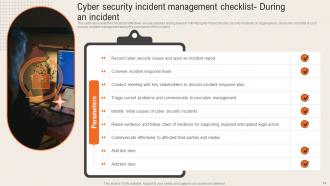
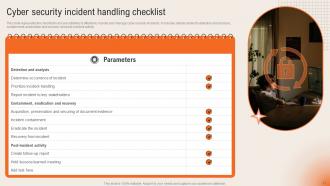
Slide 13: This slide shows the Cyber security incident management checklist- Before an incident.
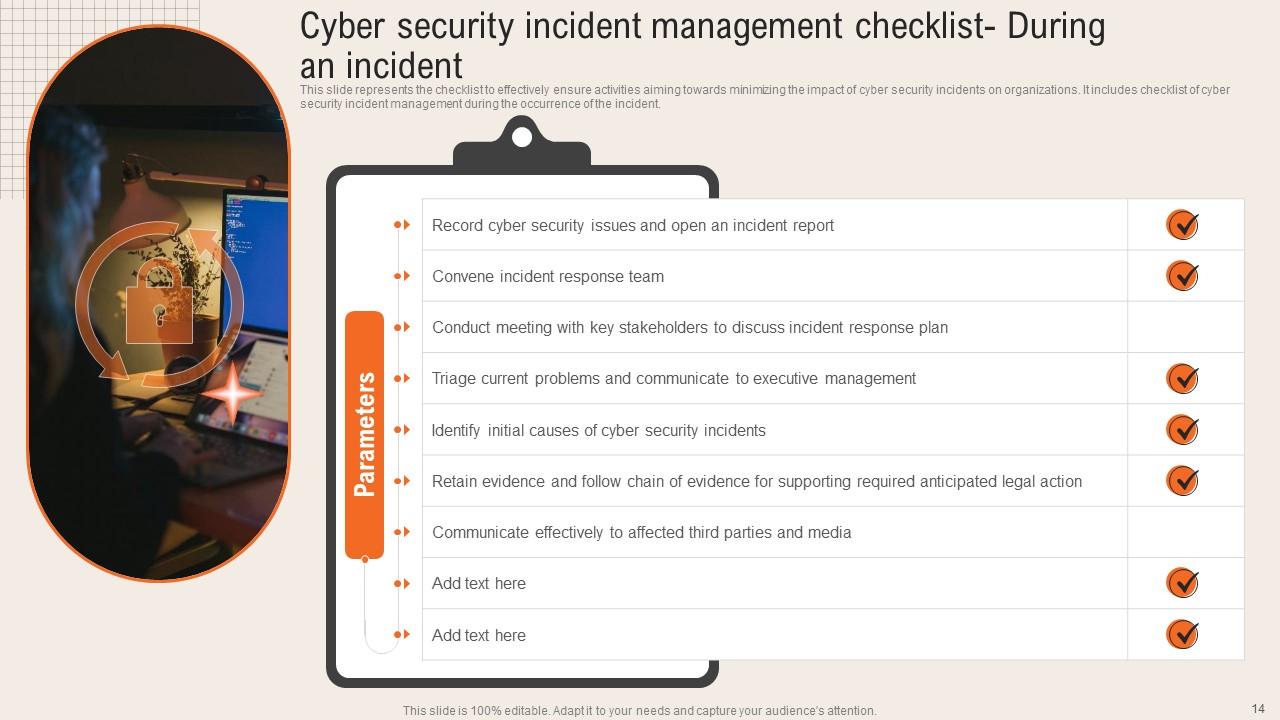
Slide 14: This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents.
Slide 15: This slide shows the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations.
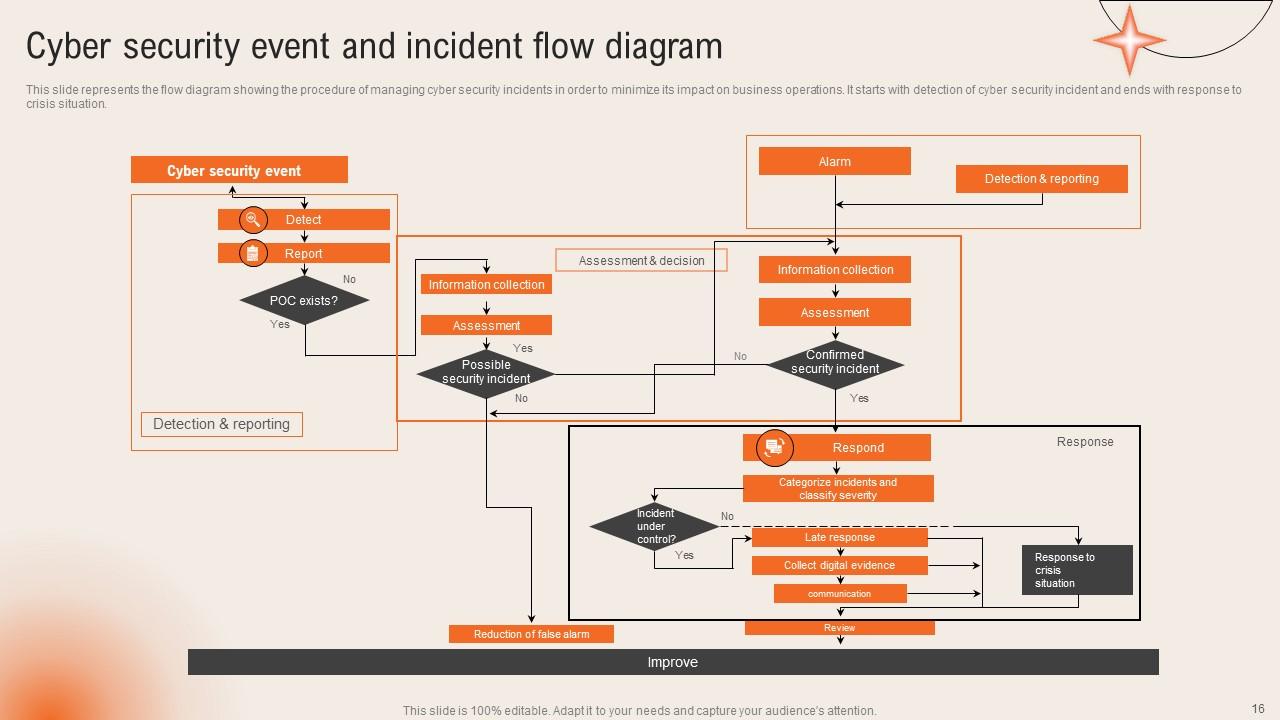
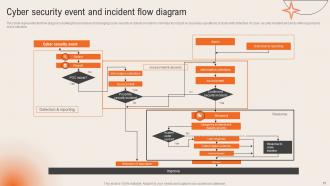
Slide 16: This slide displays the Cyber security event and incident flow diagram.
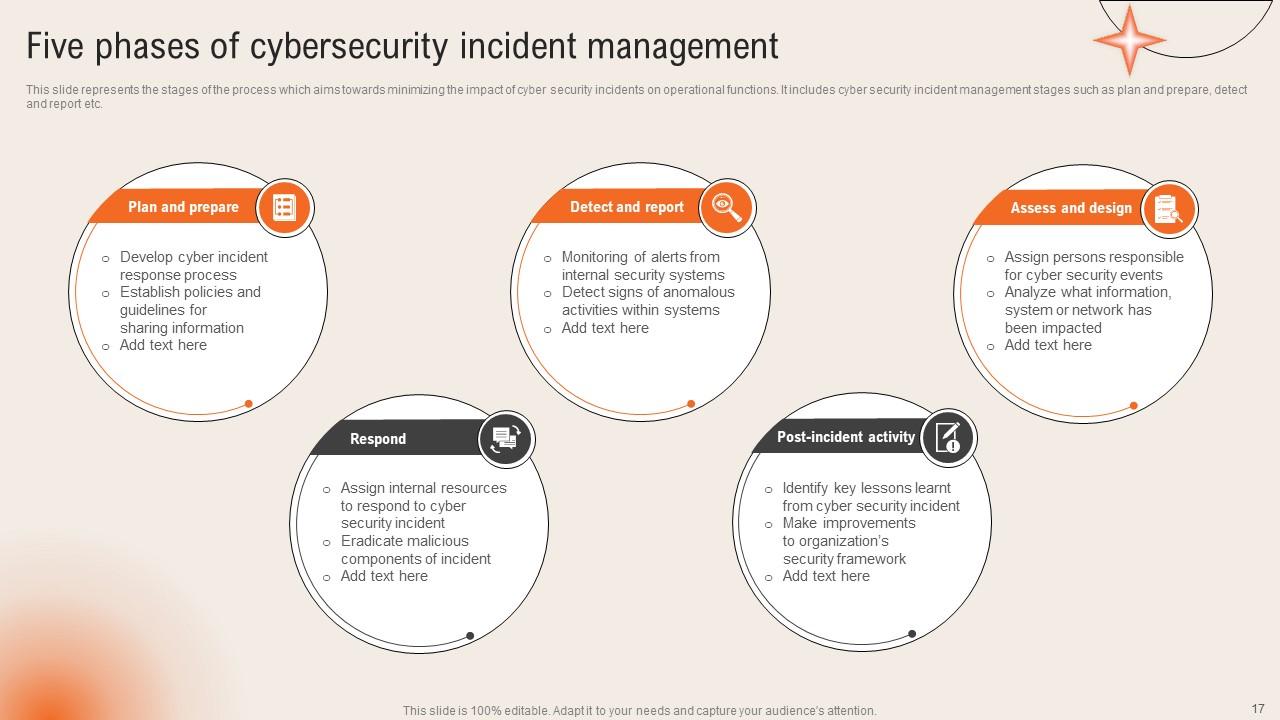
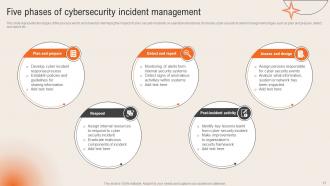
Slide 17: This slide highlights the Five phases of cybersecurity incident management.
Slide 18: This slide includes the Title for the Ideas to be covered in the forthcoming template.
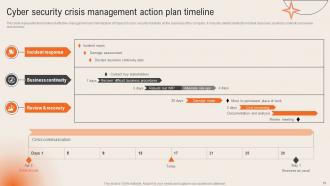
Slide 19: This slide indicates the Cyber security crisis management action plan timeline.
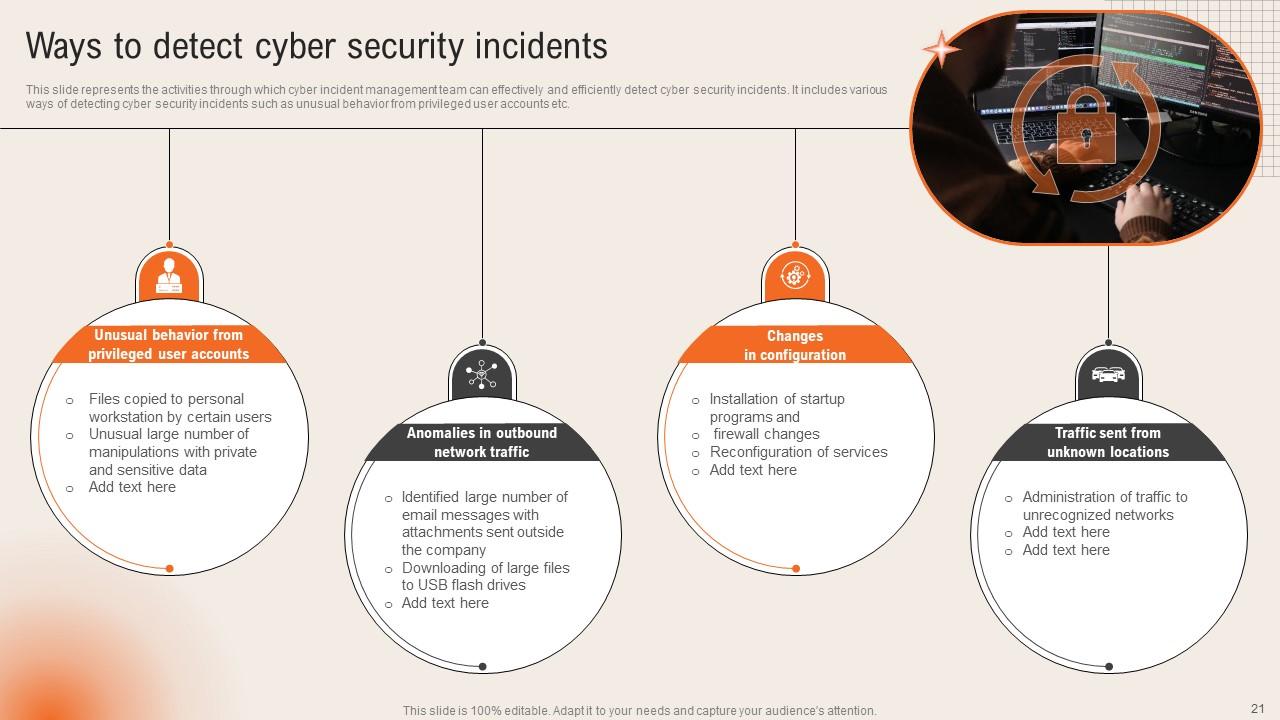
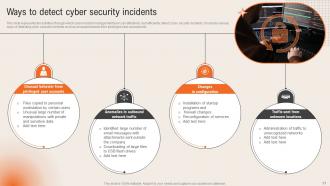
Slide 21: This slide states the Ways to detect cyber security incidents.
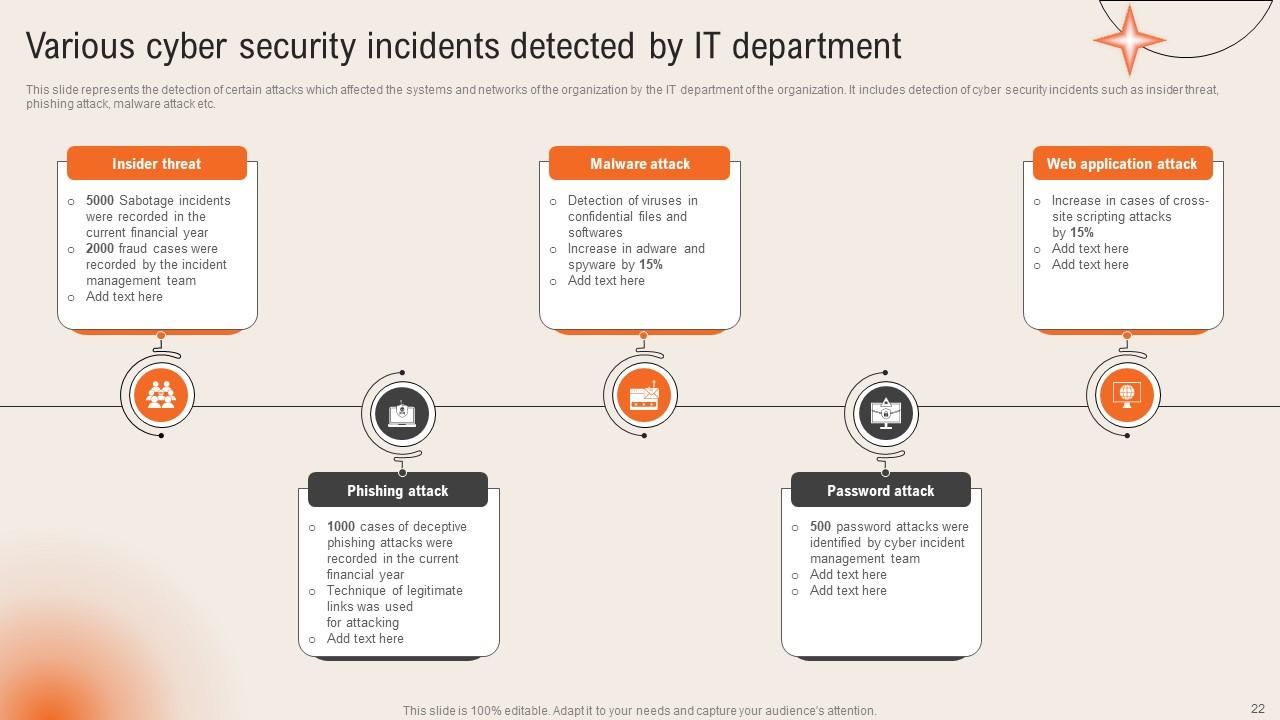
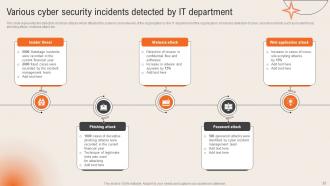
Slide 22: This slide displays the Various cyber security incidents detected by IT department.
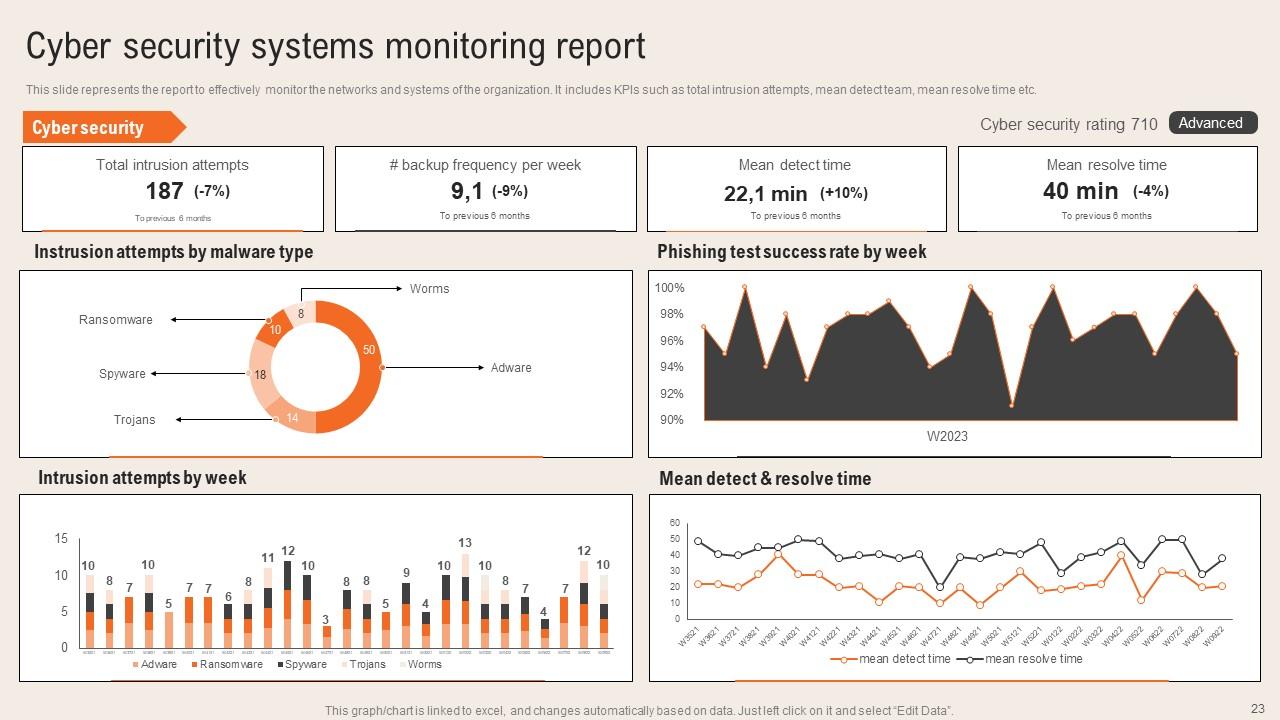
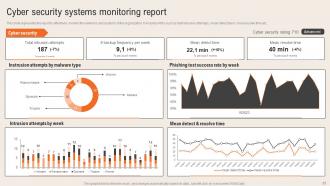
Slide 23: This slide illustrates the Cyber security systems monitoring report.
Slide 24: This slide includes the Heading for the Ideas to be discussed in the following template.
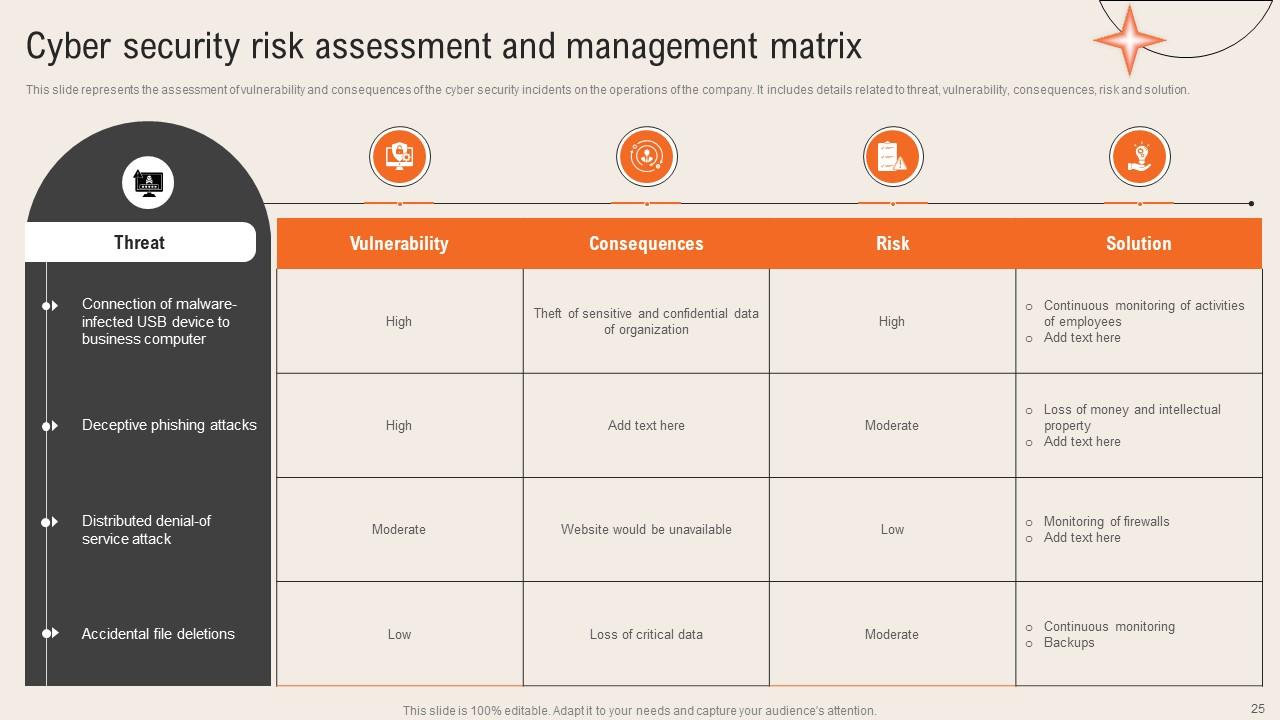
Slide 25: This slide shows the assessment of vulnerability and consequences of the cyber security incidents on the company operations.
Slide 26: This slide contains the Title for the Contents to be covered in the next template.
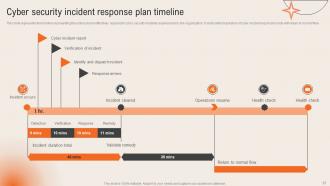
Slide 27: This slide highlights the Cyber security incident response plan timeline.
Slide 28: This slide depicts the Heading for the Topics to be further discussed.
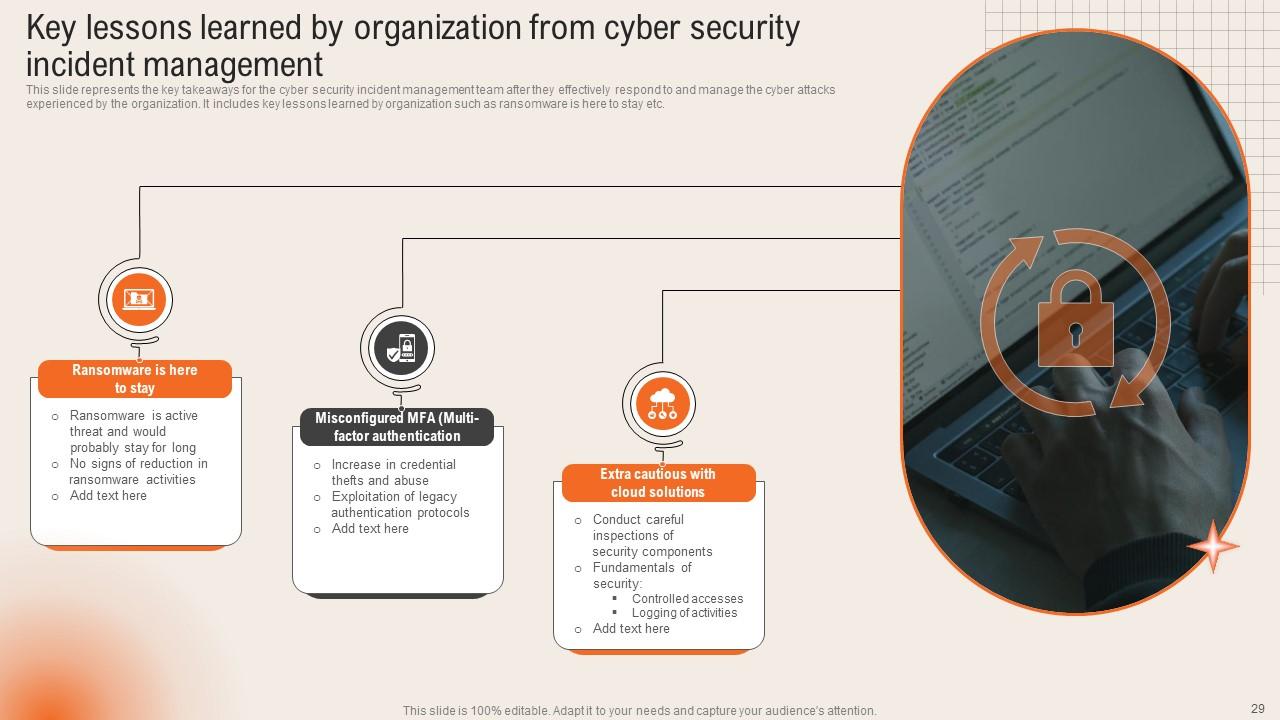
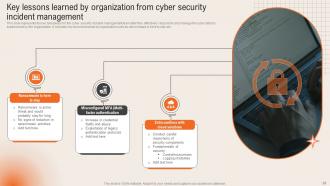
Slide 29: This slide reveals the Key lessons learned by organization from cyber security incident management.
Slide 30: This slide showcases the Title for the Topics to be covered next.
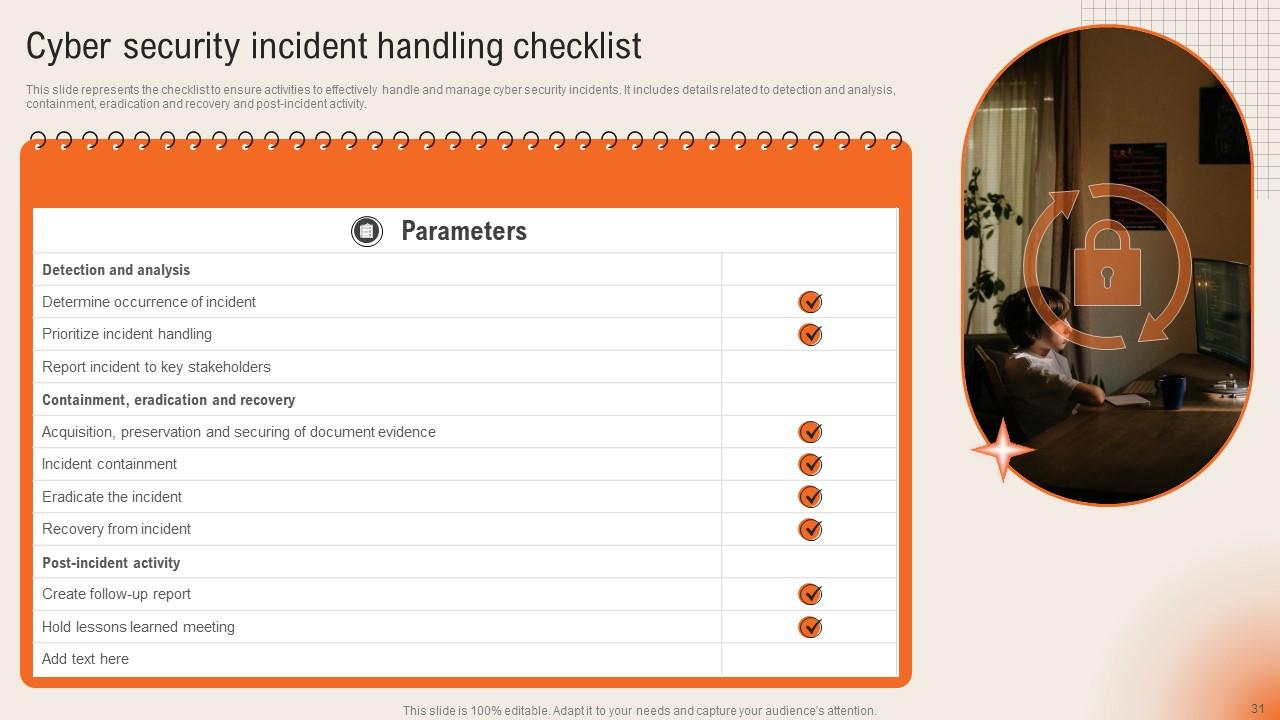
Slide 31: This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents.
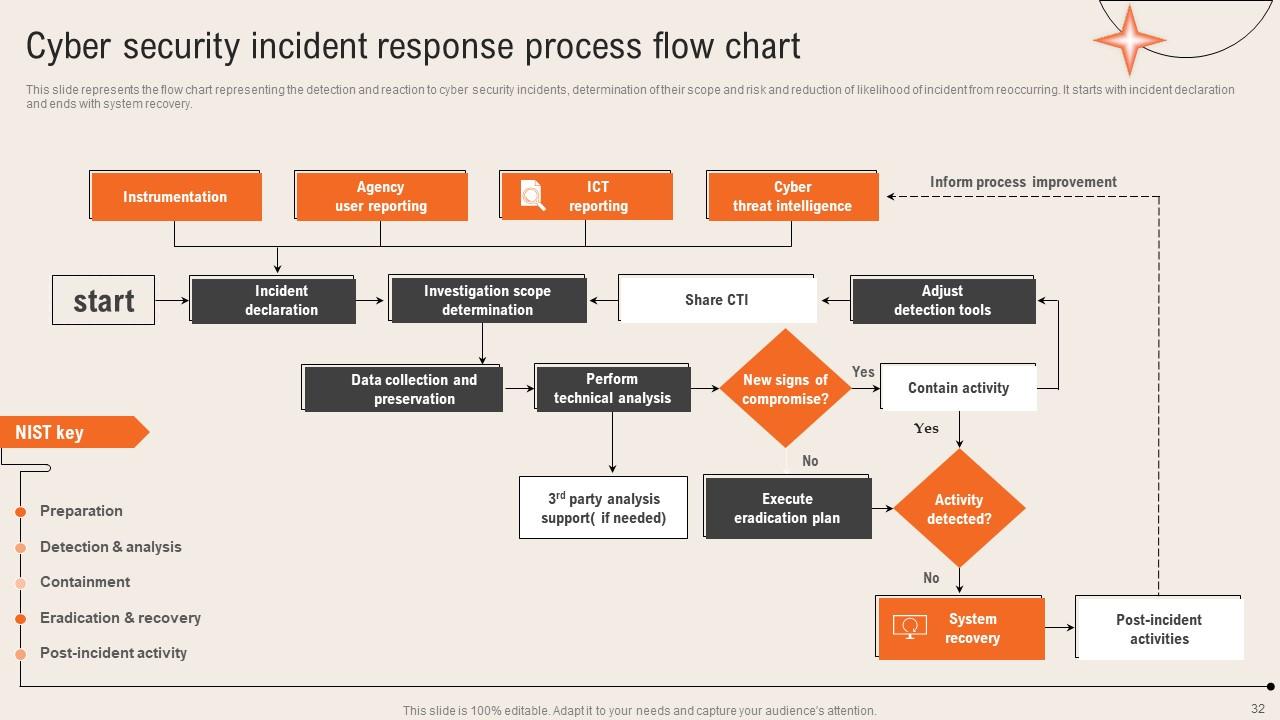
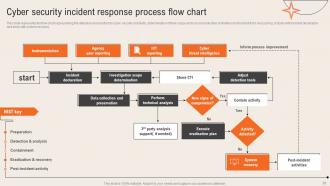
Slide 32: This slide dipslays the Cyber security incident response process flow chart.
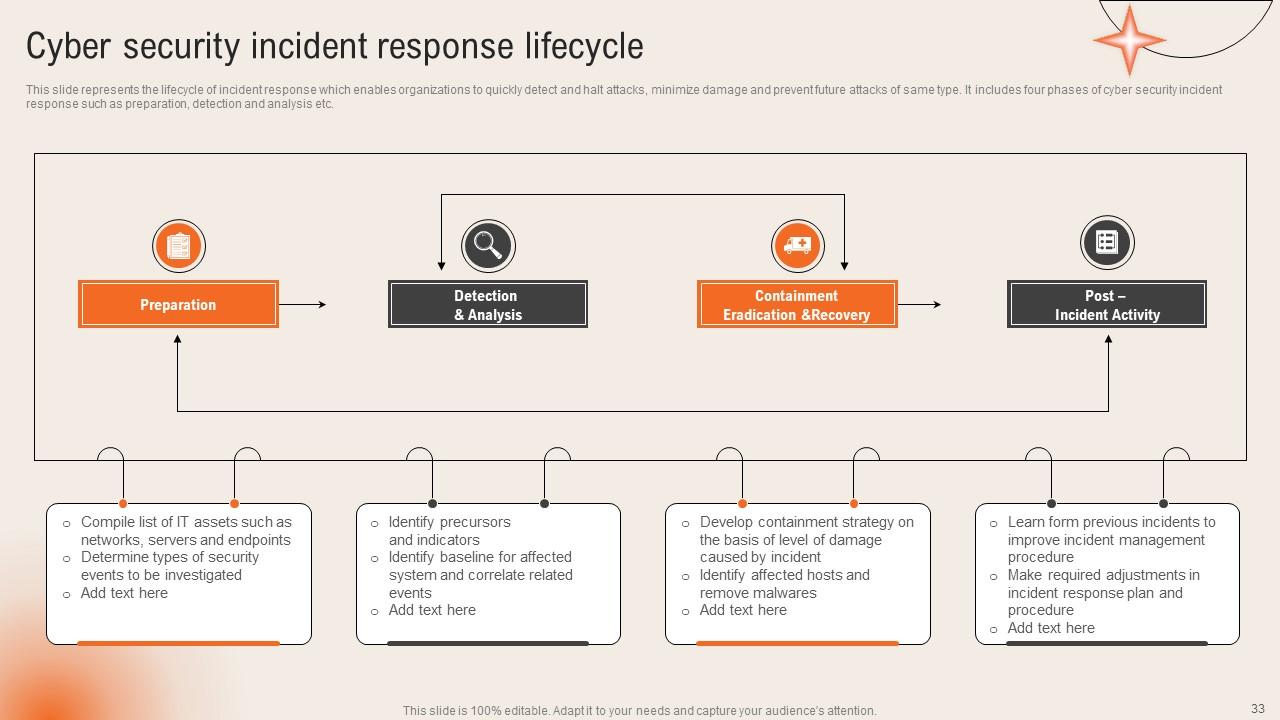
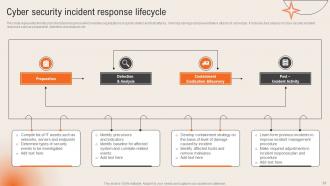
Slide 33: This slide highlights the Cyber security incident response lifecycle.
Slide 34: This slide contains the Heading for the Contents to be discussed further.
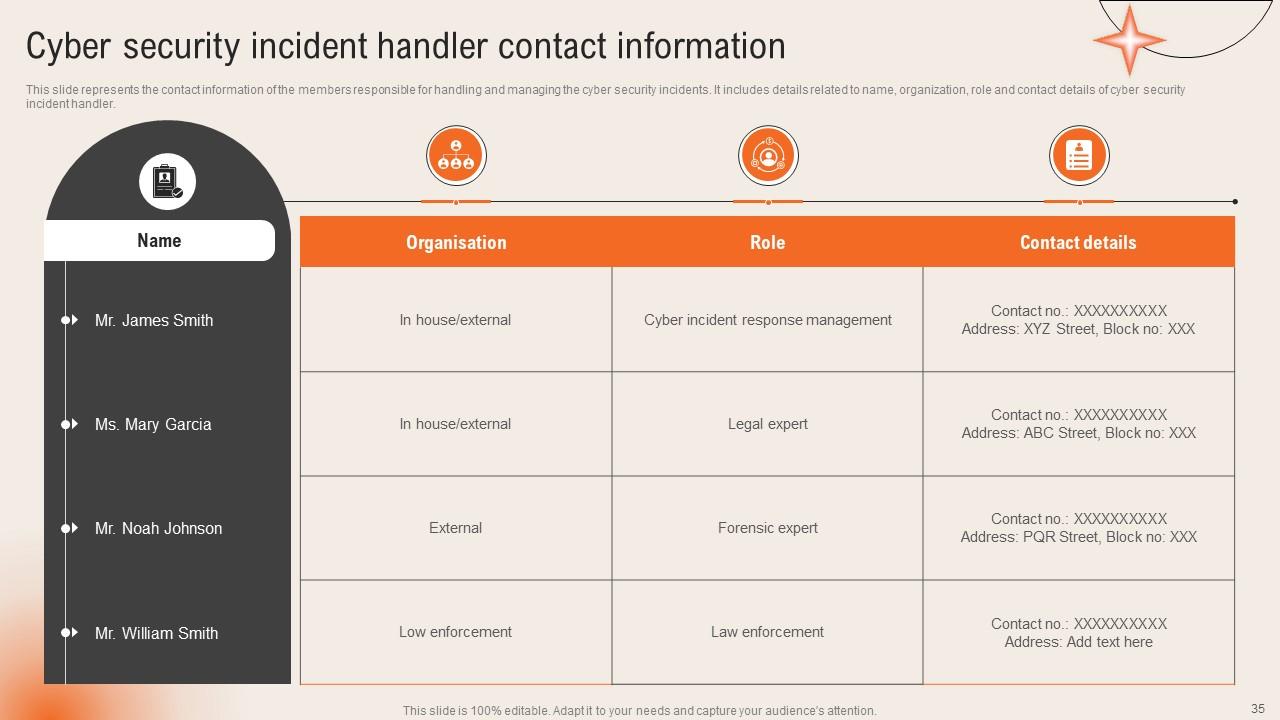
Slide 35: This slide represents the contact information of the members responsible for handling and managing the cyber security incidents.
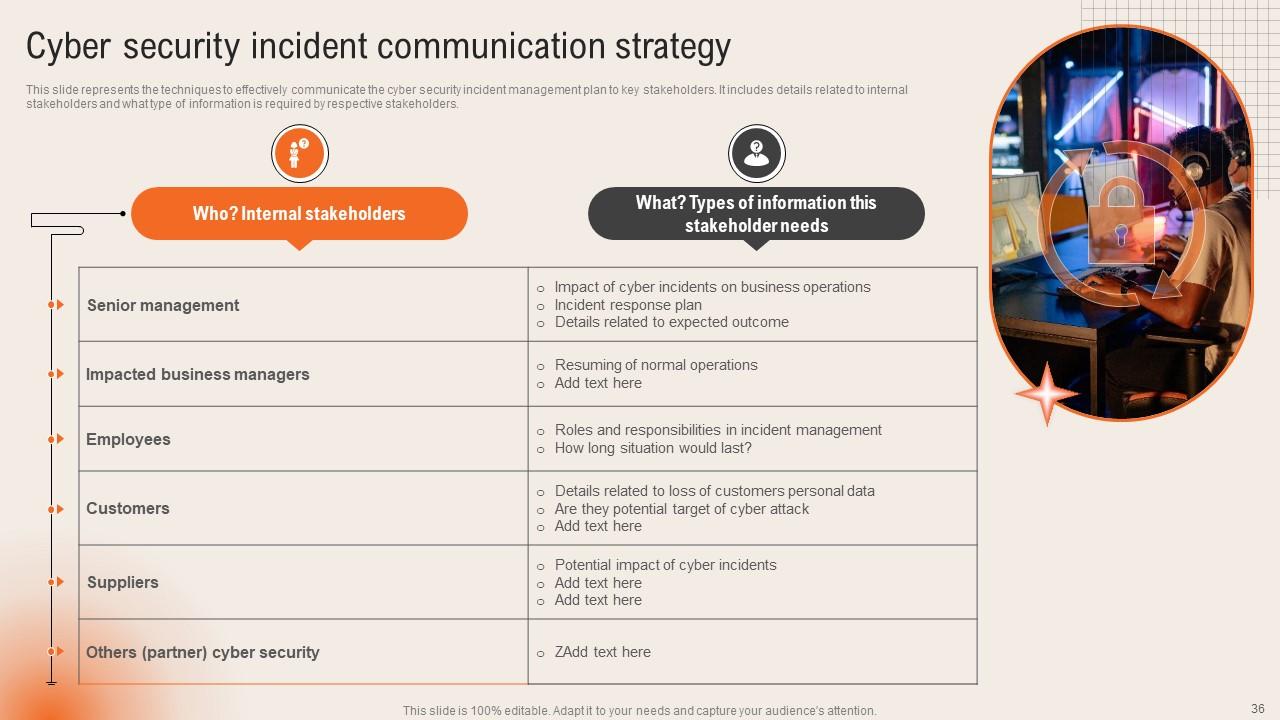
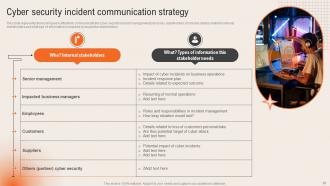
Slide 36: This slide reveals the Cyber security incident communication strategy.
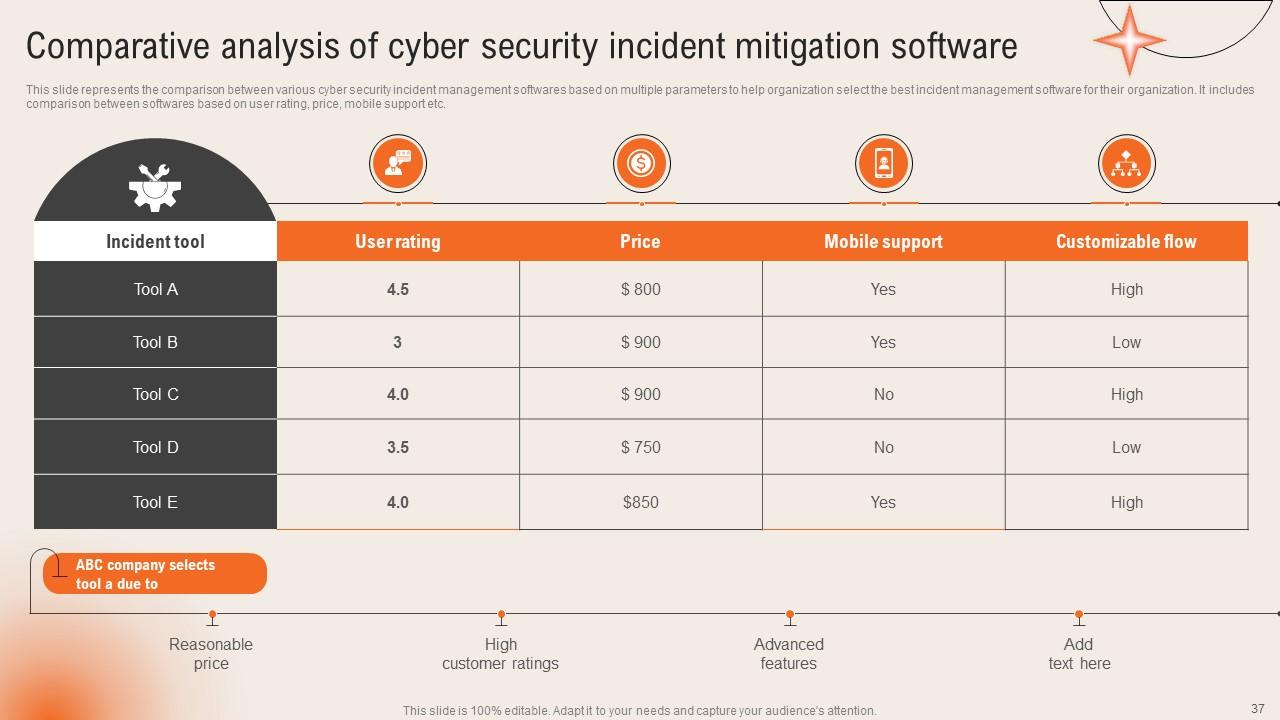
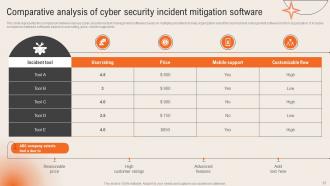
Slide 37: This slide mentions the Comparative analysis of cyber security incident mitigation software.
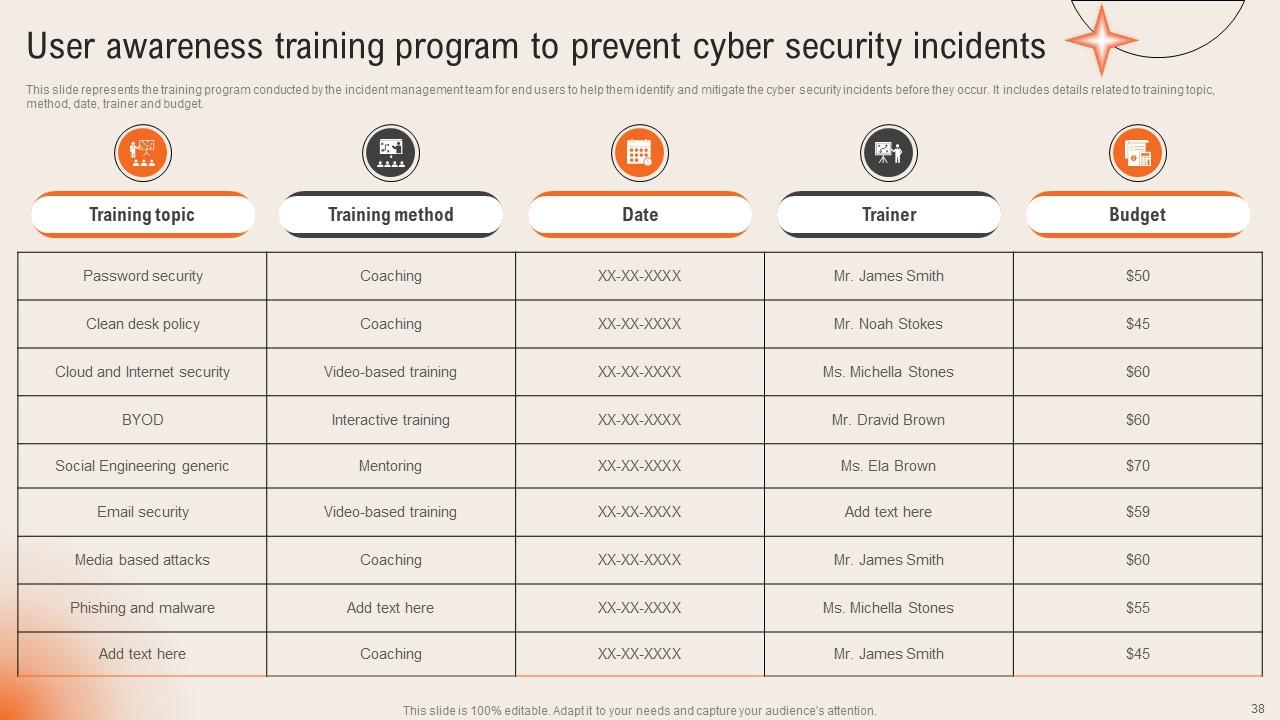
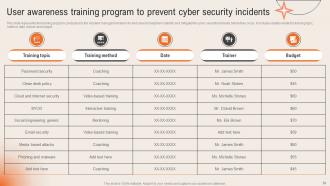
Slide 38: This slide talks about User awareness training program to prevent cyber security incidents.
Slide 39: This slide contains the Title for the Ideas to be covered next.
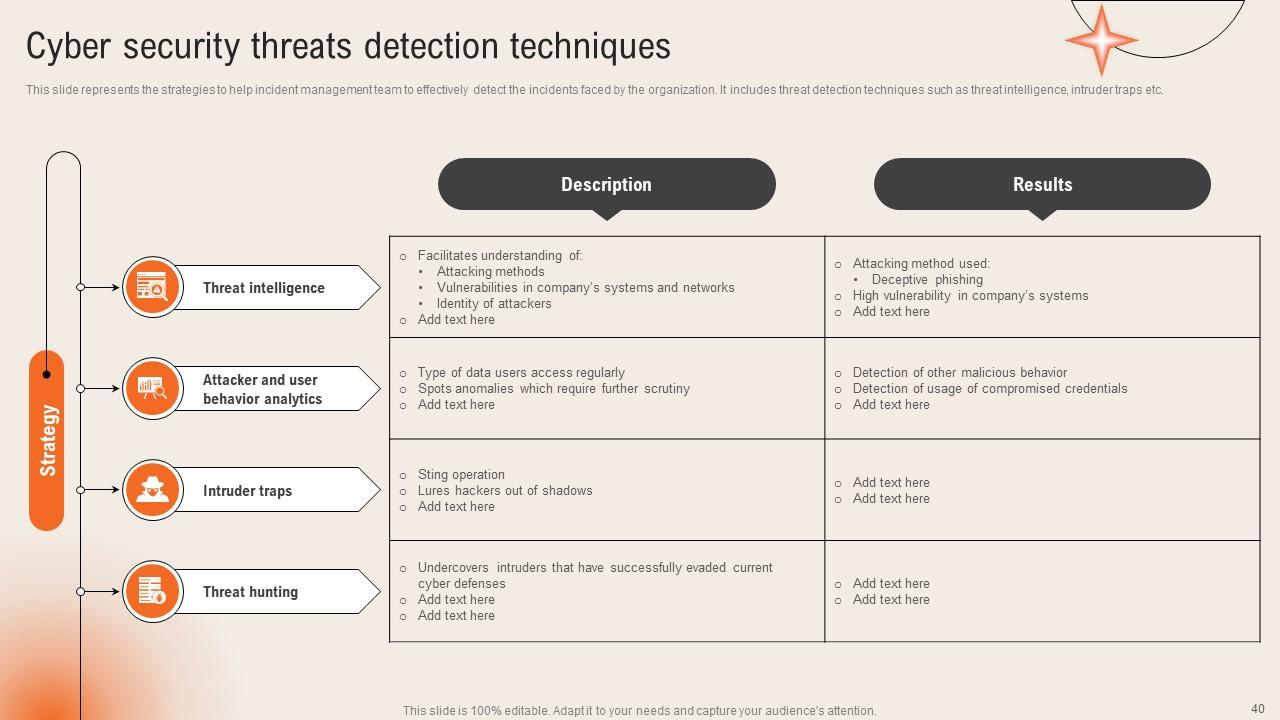
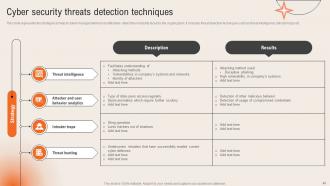
Slide 40: This slide highlights the Cyber security threats detection techniques.
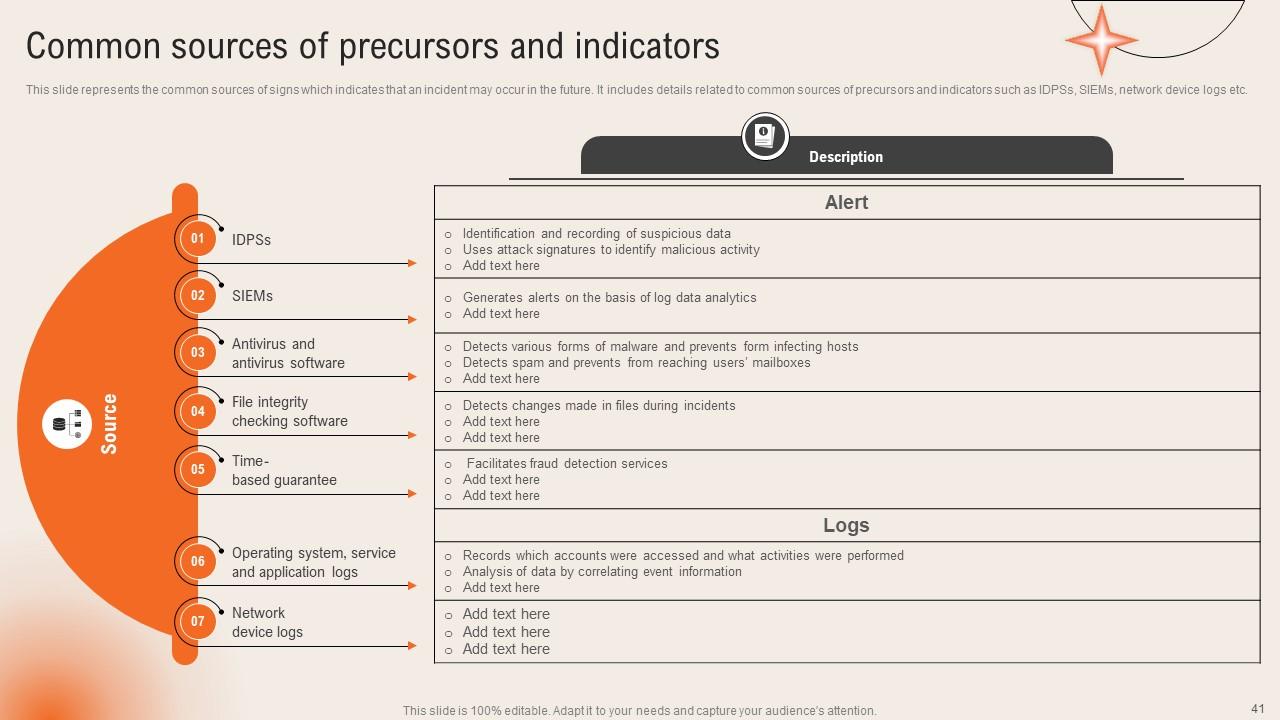
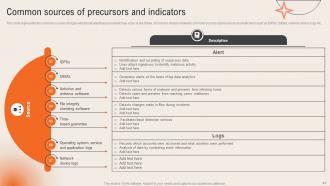
Slide 41: This slide depicts the Common sources of precursors and indicators.
Slide 42: This slide reveals the Strategies to analyze cyber security incidents.
Slide 43: This slide incorporates the Heading for the Ideas to be discussed further.
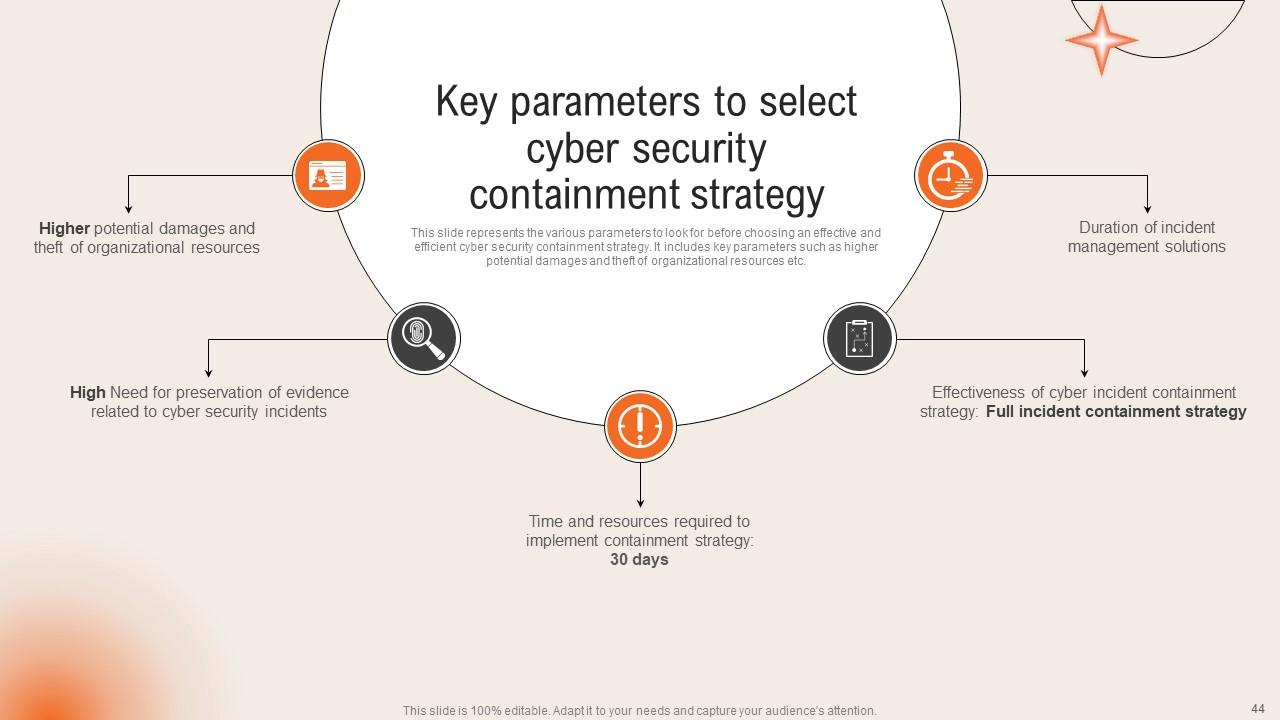
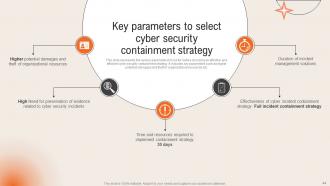
Slide 44: This slide states the Key parameters to select cyber security containment strategy.
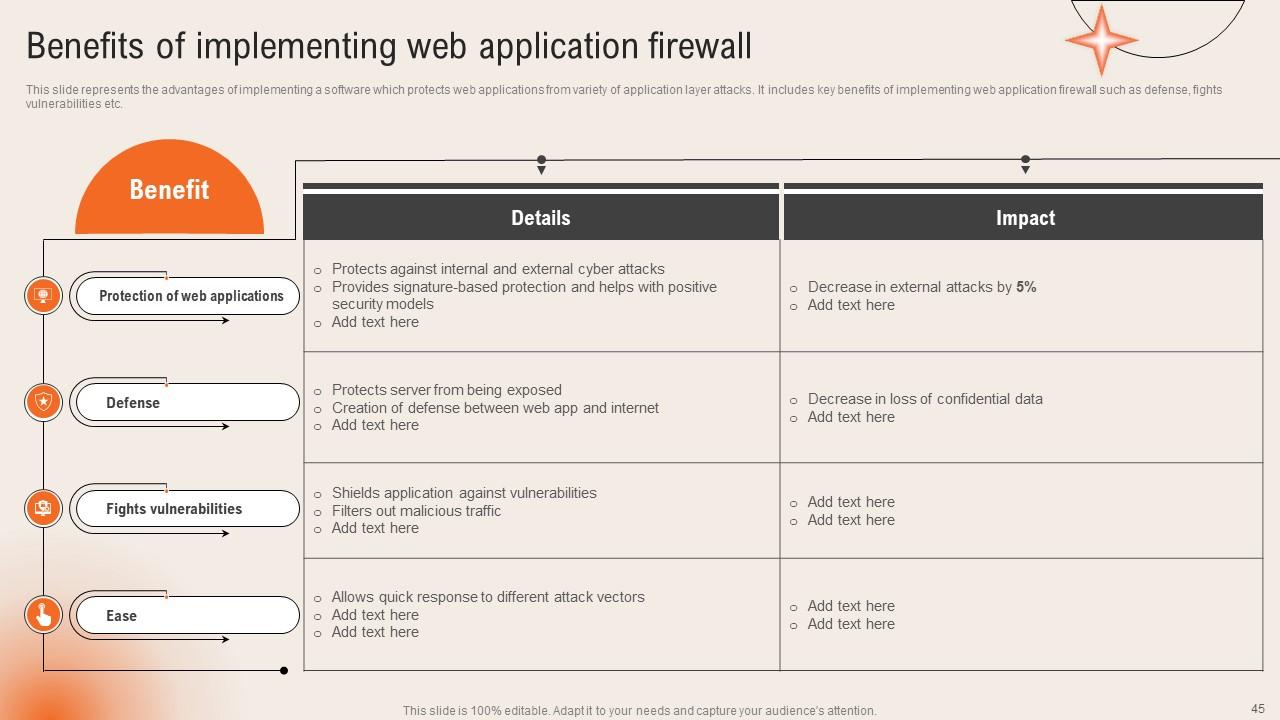
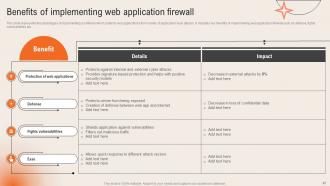
Slide 45: This slide exhibits the Benefits of implementing web application firewall.
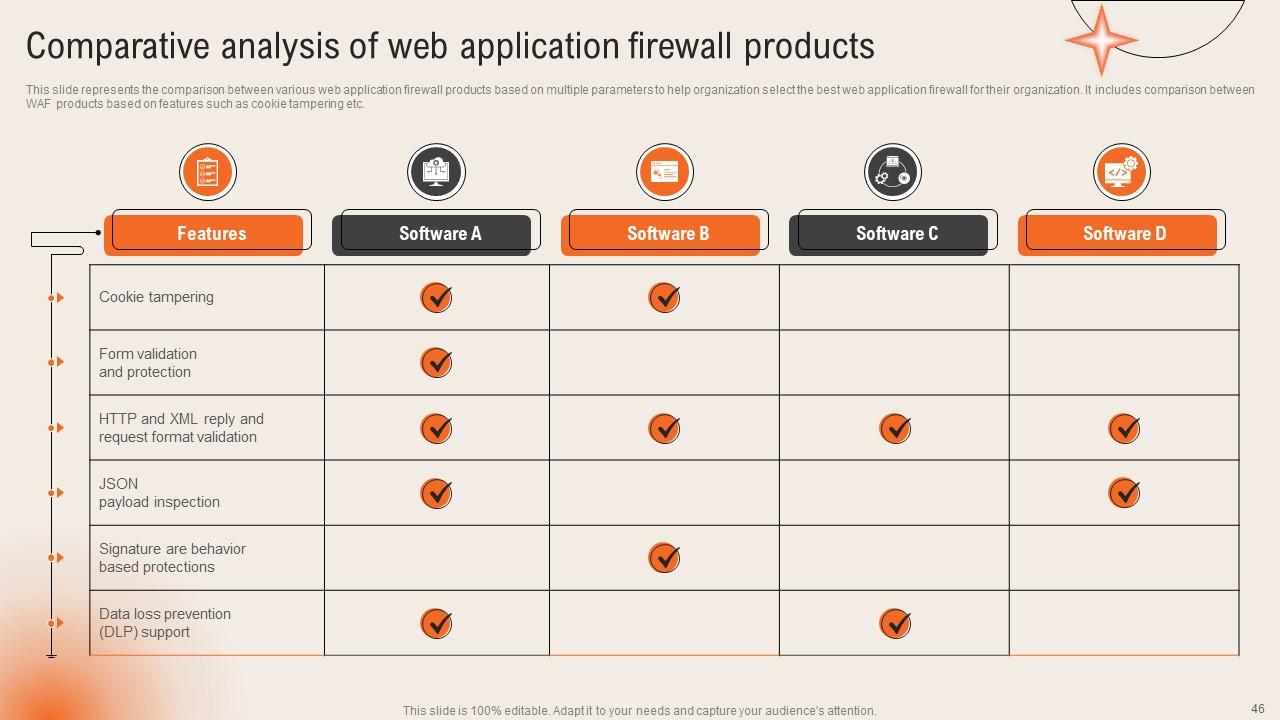
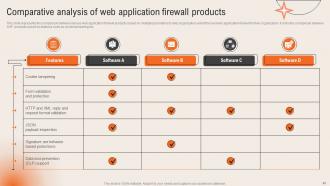
Slide 46: This slide presents the Comparative analysis of web application firewall products.
Slide 47: This slide mentions the Title for the Contents to be covered next.
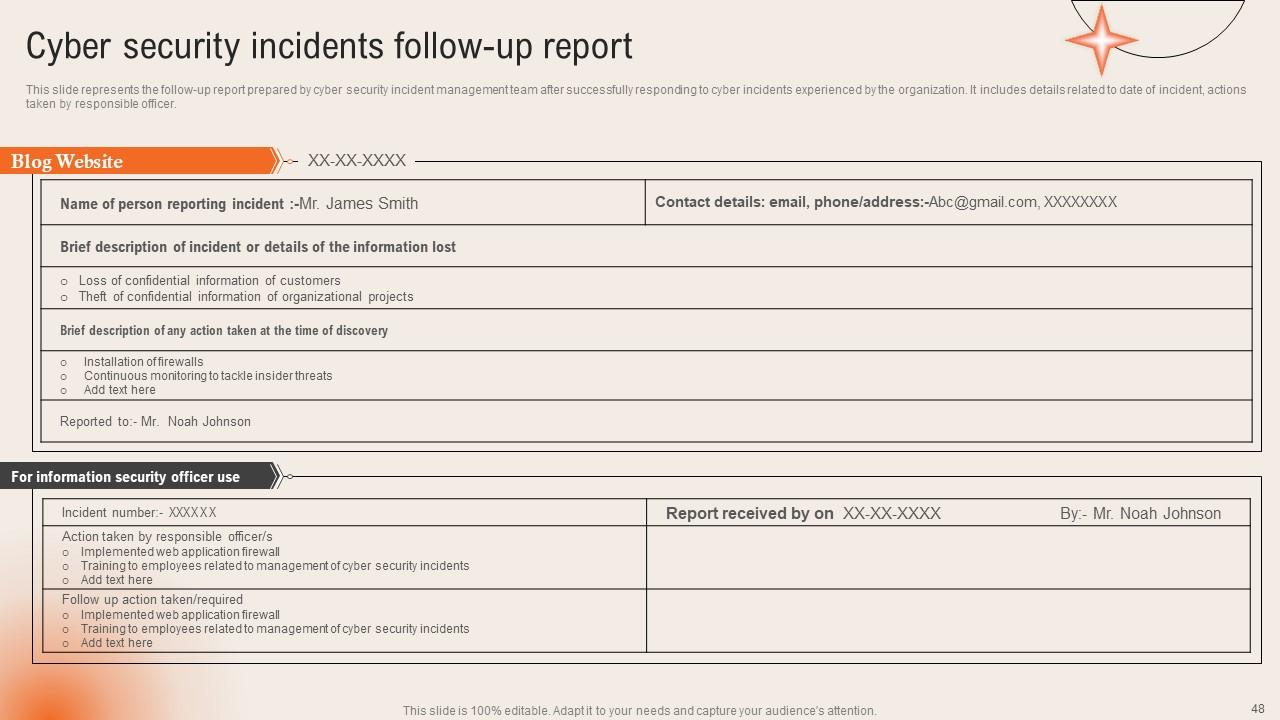
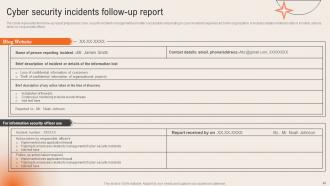
Slide 48: This slide represents the follow-up report prepared by cyber security incident management team.
Slide 49: This slide depicts the Heading for the Topics to be discussed further.
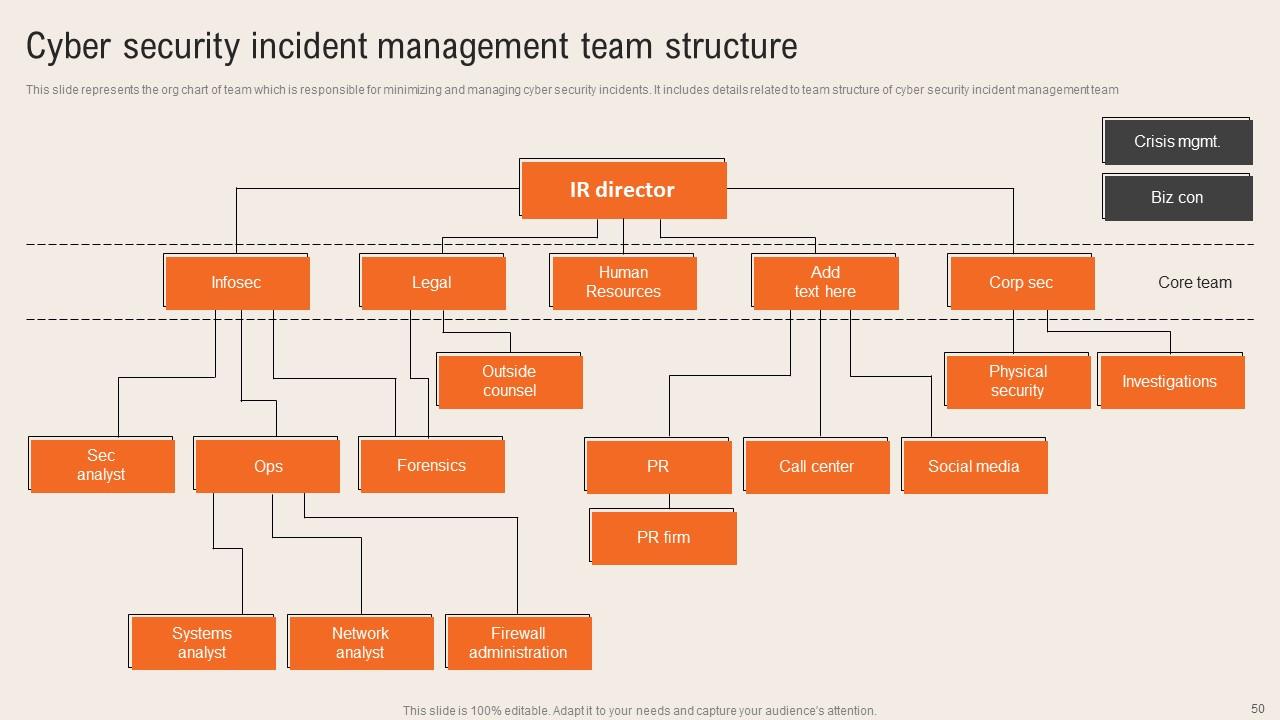
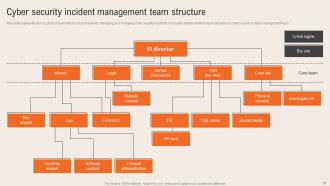
Slide 50: This slide reveals the org chart of team which is responsible for minimizing and managing cyber security incidents.
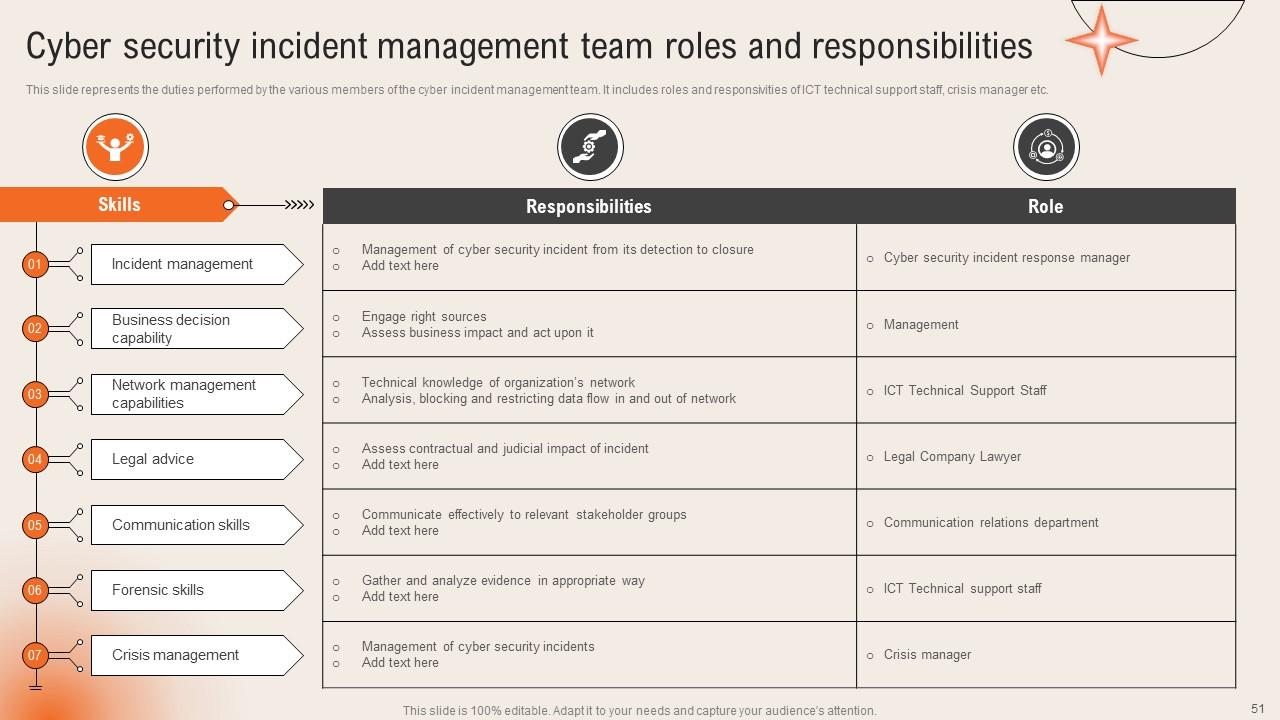
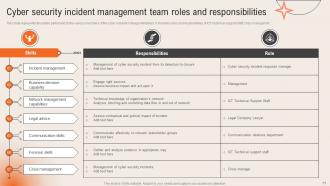
Slide 51: This slide highlights the duties performed by the various members of the cyber incident management team.
Slide 52: This slide includes the Title for the Topics to be covered next.
Slide 53: This slide highlights the Impact of implementing cyber security incident management on organization.
Slide 54: This slide incorporates the Heading for the Contents to be discussed further.
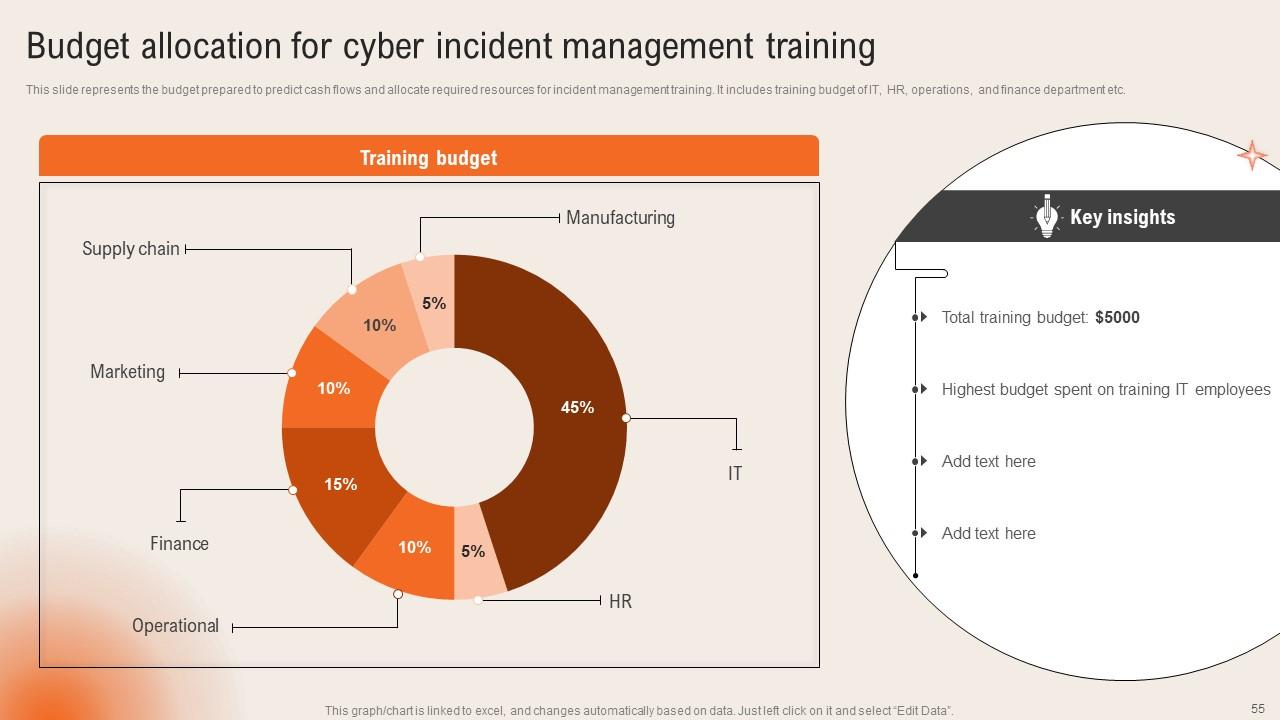
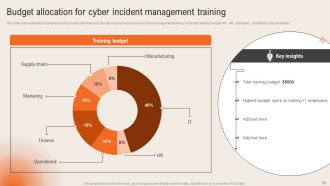
Slide 55: This slide reveals the budget prepared to predict cash flows and allocate required resources for incident management training.
Slide 56: This slide indicates the Title for the Ideas to be covered in the following template.
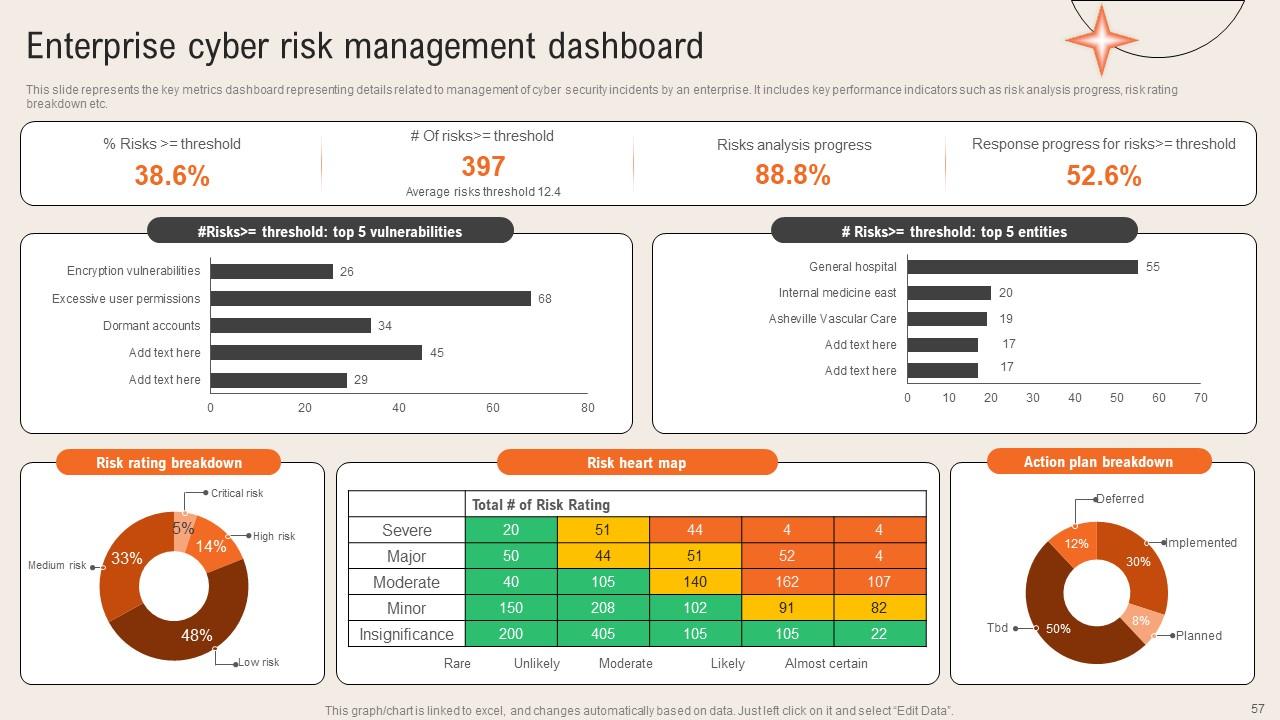
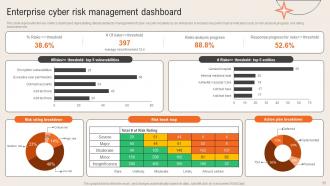
Slide 57: This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise.
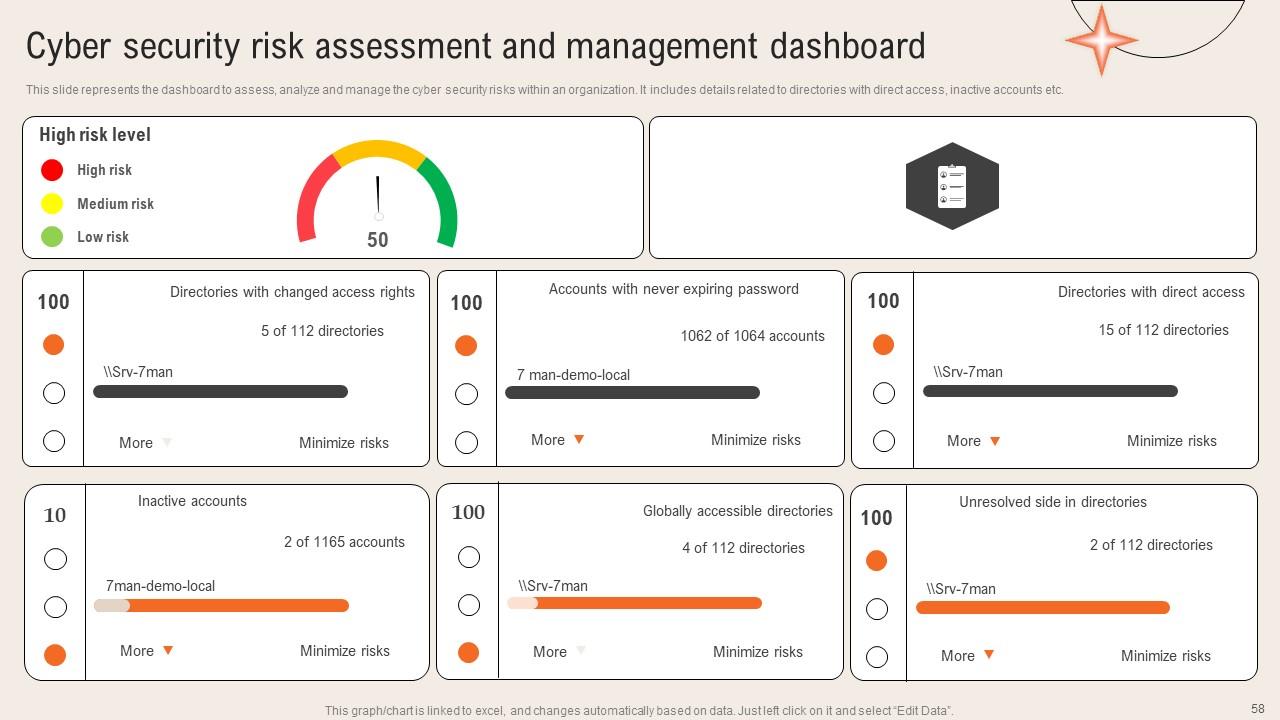
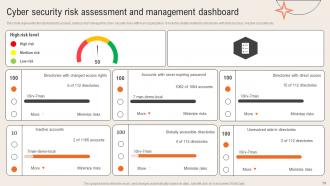
Slide 58: This slide shows the Cyber security risk assessment and management dashboard.
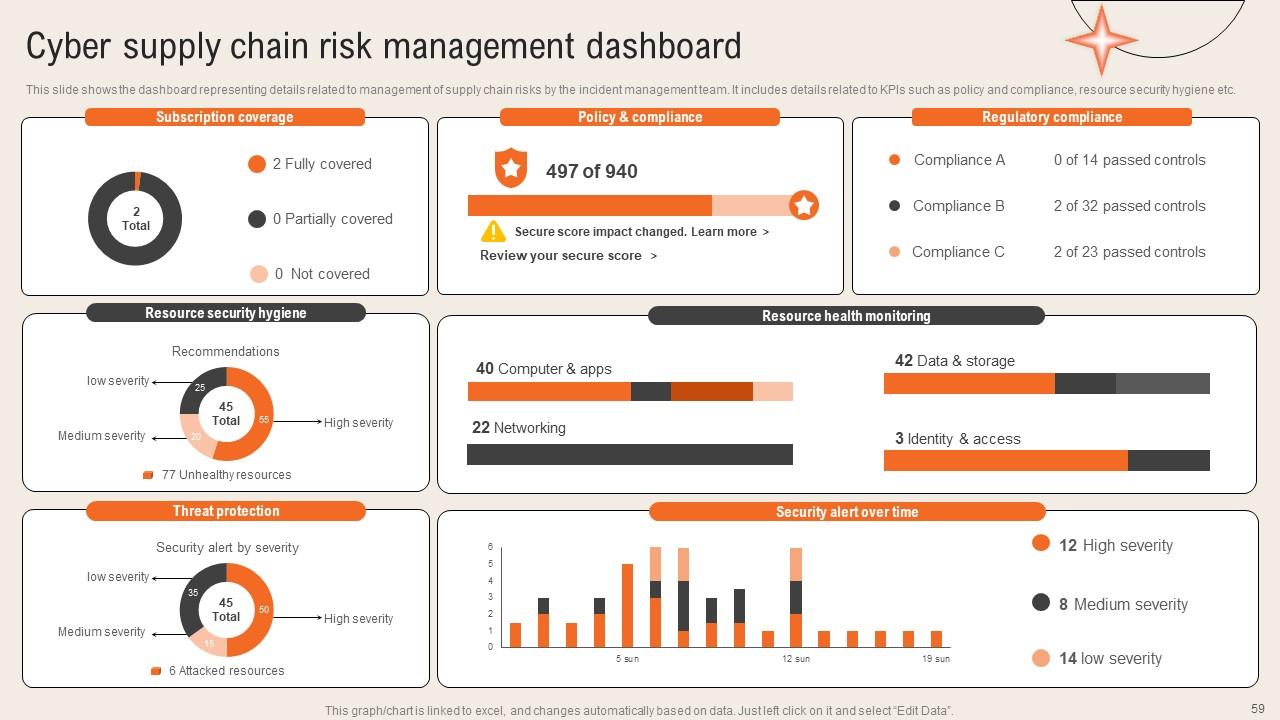
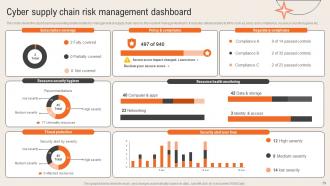
Slide 59: This slide presents the Cyber supply chain risk management dashboard.
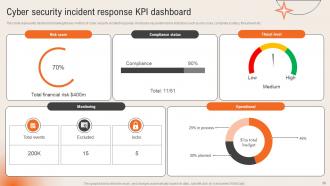
Slide 60: This slide displays the Cyber security incident response KPI dashboard.
Slide 61: This is the Icons slide containing all the Icons used in the plan.
Slide 62: This slide is used for depicting some Additional information.
Slide 63: This slide includes the comapny's Mission, vision, and goals.
Slide 64: This is the About Us slide for stating the organziation-related information.
Slide 65: This slide exhibits the firm's Timeline.
Slide 66: This slide represents the SWOT analysis.
Slide 67: This is the 30 60 90 days plan slide for effective planning.
Slide 68: This is the Puzzle slide with related imagery.
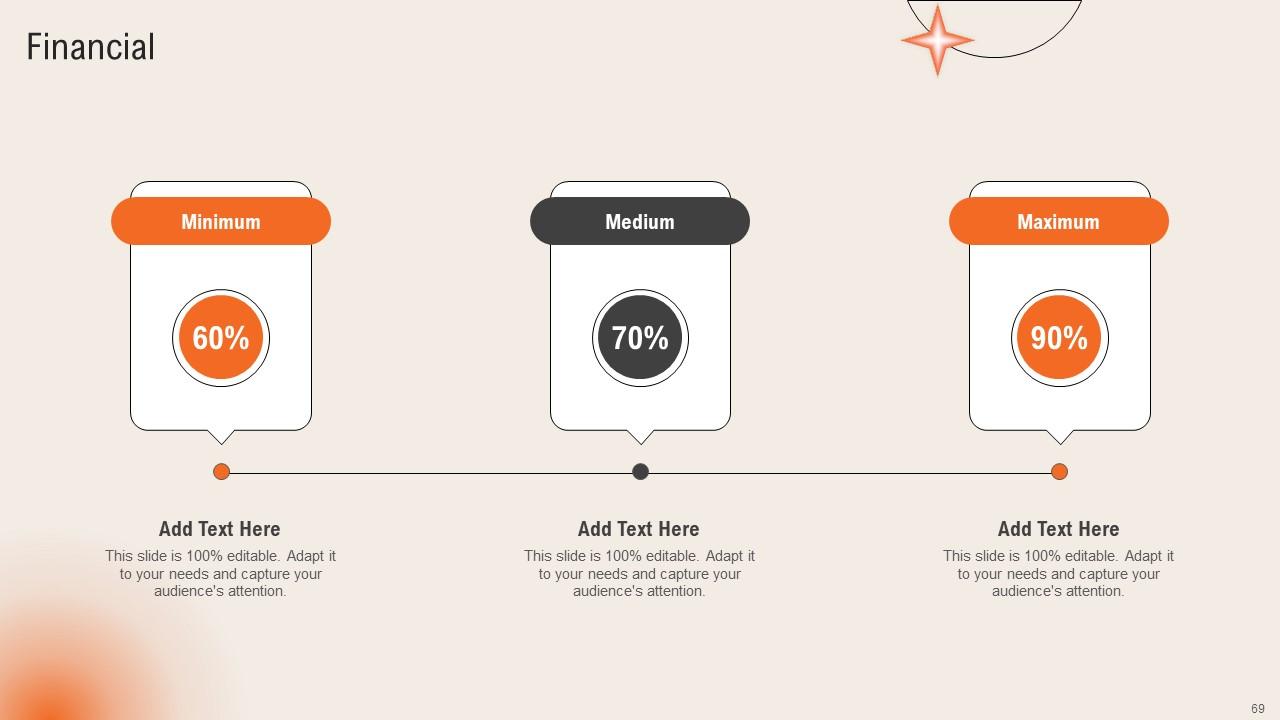
Slide 69: This slide elucidates information related to the Financial topic.
Slide 70: This is the Thank You slide for acknowledgement.
Deploying Computer Security Incident Management Powerpoint Presentation Slides with all 75 slides:
Use our Deploying Computer Security Incident Management Powerpoint Presentation Slides V to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Informative and engaging! I really like the design and quality of the slides.
-
Illustrative design with editable content. Exceptional value for money. Highly pleased with the product.