Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest
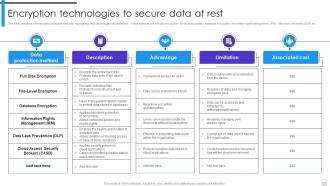
This slide compares different data protection methods, highlighting their advantages and limitations. These methods are full disk encryption, file-level encryption, database encryption, information rights management IRM, data leak prevention DLP,etc.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
This slide compares different data protection methods, highlighting their advantages and limitations. These methods are full disk encryption, file-level encryption, database encryption, information rights management IRM, data leak prevention DLP,etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Full Disk Encryption, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
People who downloaded this PowerPoint presentation also viewed the following :
Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest with all 10 slides:
Use our Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Great product with effective design. Helped a lot in our corporate presentations. Easy to edit and stunning visuals.
-
Wide collection of templates available. SlideTeam has made it easier to create presentations in just a few minutes.