End User Security A Cybersecurity Component Training Ppt
These slides, in detail, cover the end user security, a component of cybersecurity. It covers endpoint protections importance, working, protection strategies, components, and core functionalities.
These slides, in detail, cover the end user security, a component of cybersecurity. It covers endpoint protections importan..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting End User Security a Cybersecurity Component. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 2
This slide gives information about end-user security. End-user security, also known as endpoint security, refers to the protection of devices that users work with and users themselves.
Slide 3
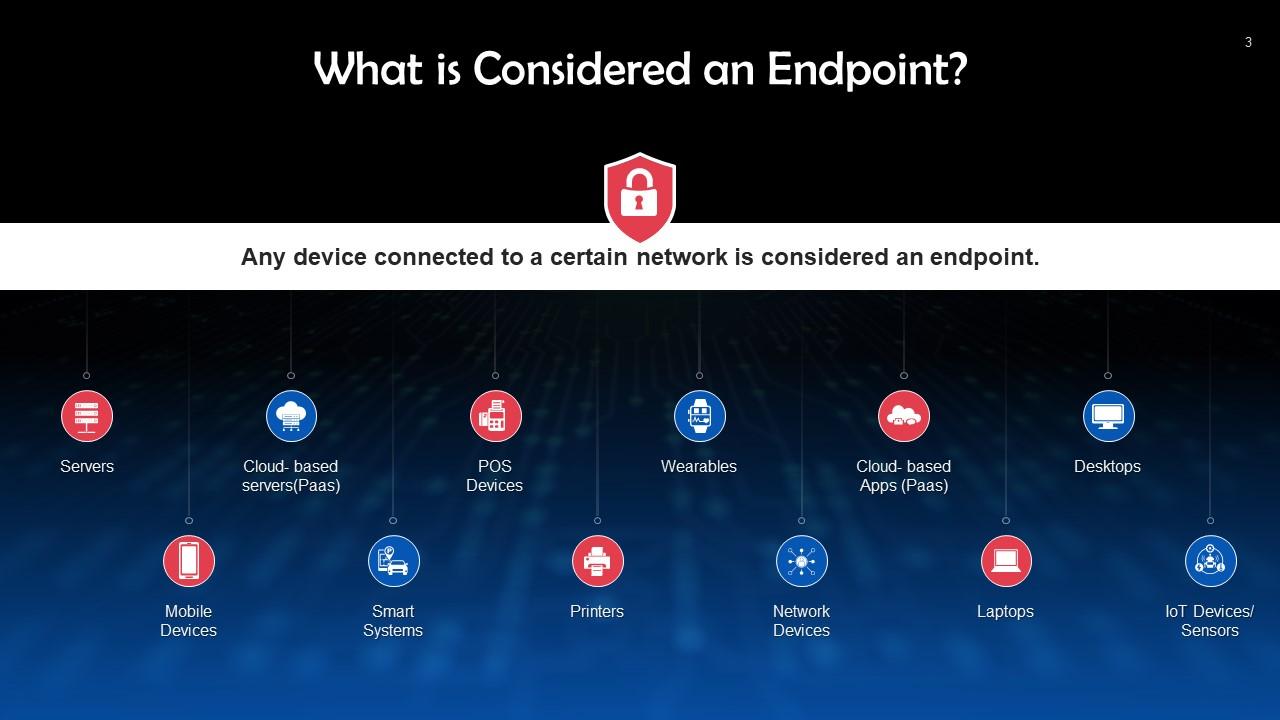
This slide depicts the working of endpoint security. Any device connected to a certain network is considered an endpoint. These include desktops, laptops, servers, printers, etc.
Slide 4
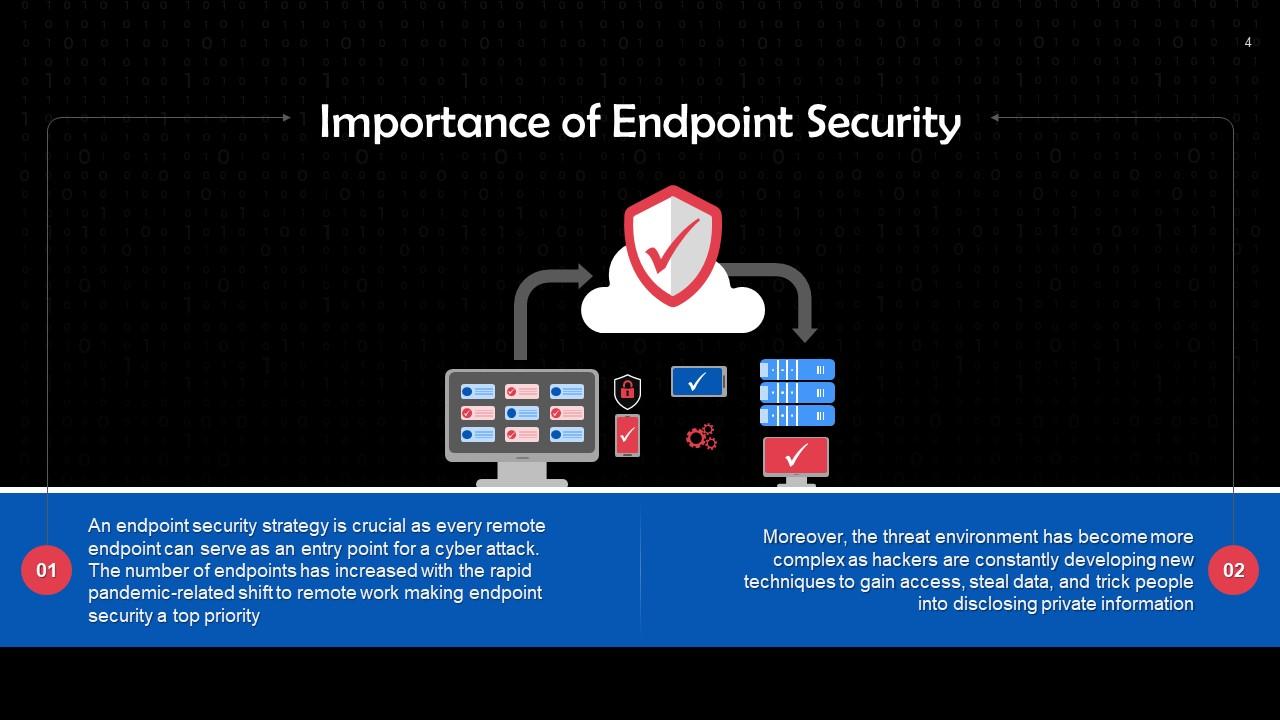
This slide shows the importance of endpoint security. An endpoint security strategy is crucial as every remote endpoint can serve as an entry point for a cyber attack as the number of endpoints is increasing with the rapid pandemic-related shift to remote work.
Slide 5
This slide depicts the working of endpoint security. Endpoint Protection Platforms, or EPPs, work by examining files as they enter the network.
Slide 6
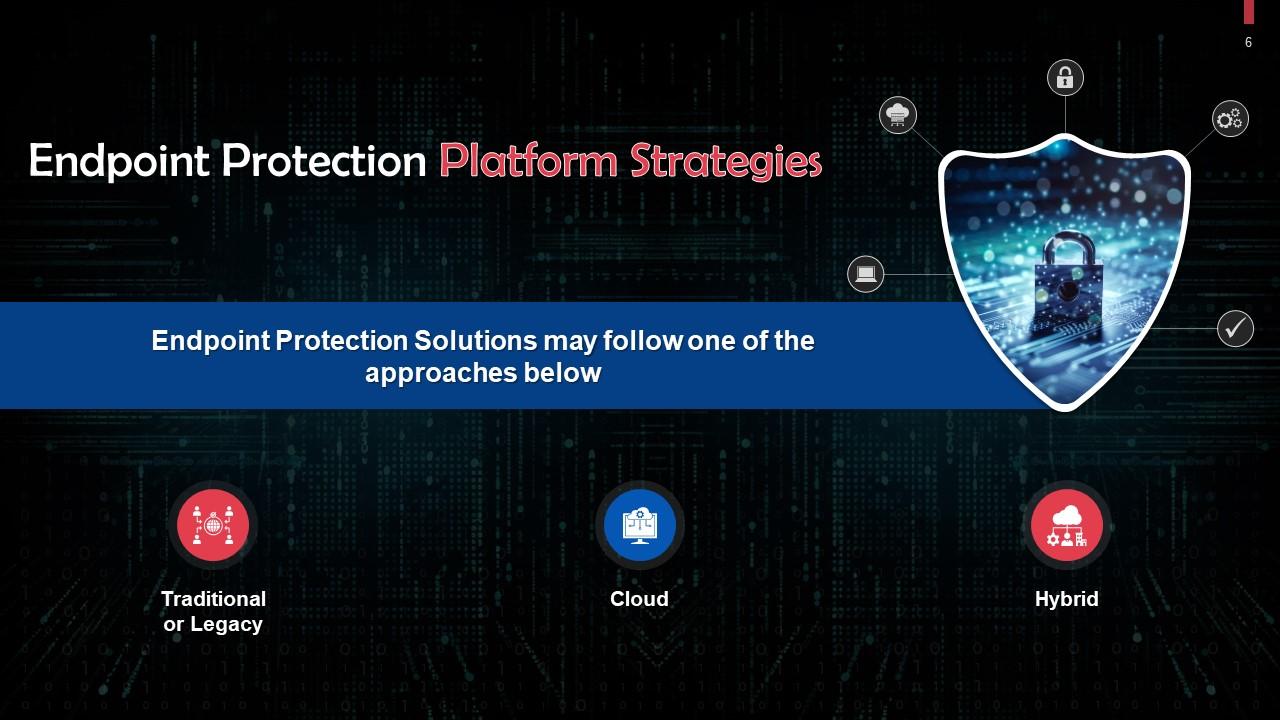
This slide tells us about strategies used in endpoint protection solutions. These are either traditional or legacy, cloud, or hybrid approach.
Slide 7
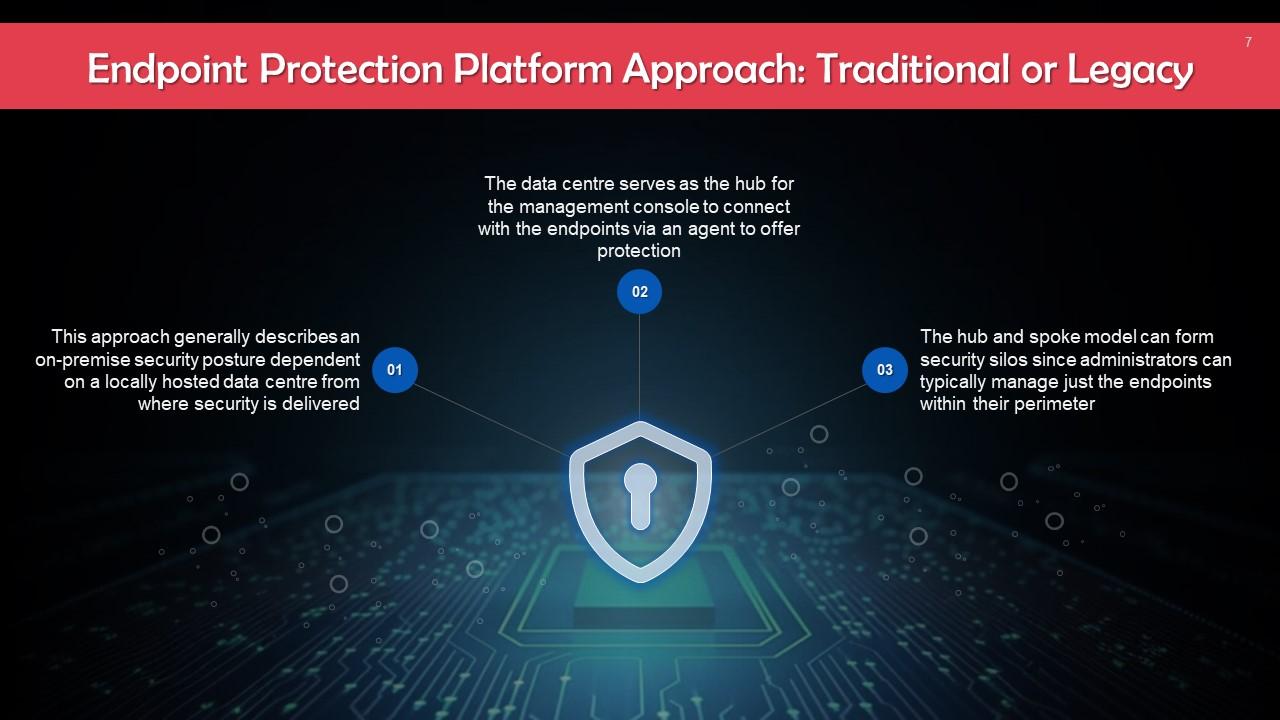
This slide talks about the traditional or legacy approach for endpoint protection platforms. This approach describes an on-premise security posture dependent on a locally hosted data center from which security is delivered.
Slide 8
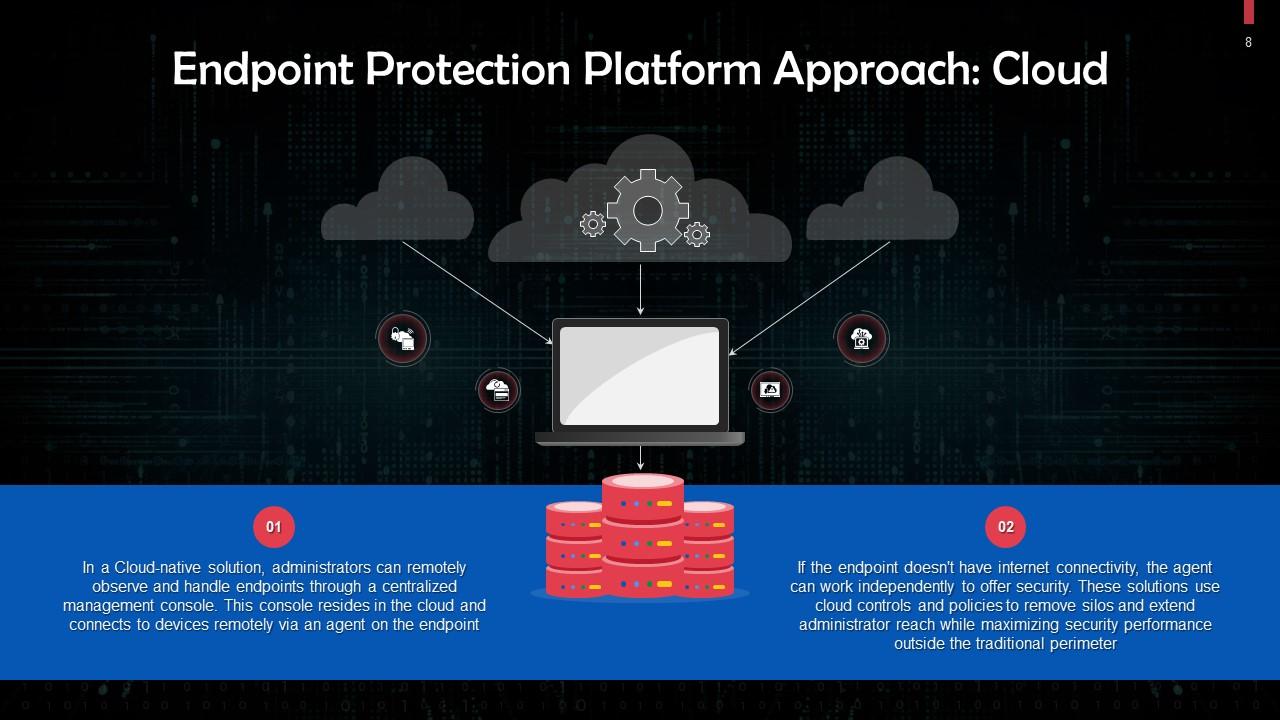
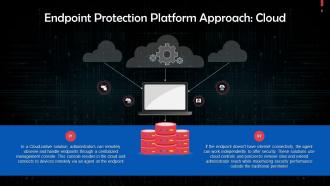
This slide talks about the cloud approach for endpoint protection platforms. In a Cloud-native solution, administrators can remotely observe and handle endpoints through a centralized management console that resides in the cloud. It connects to devices remotely via an agent on the endpoint.
Slide 9
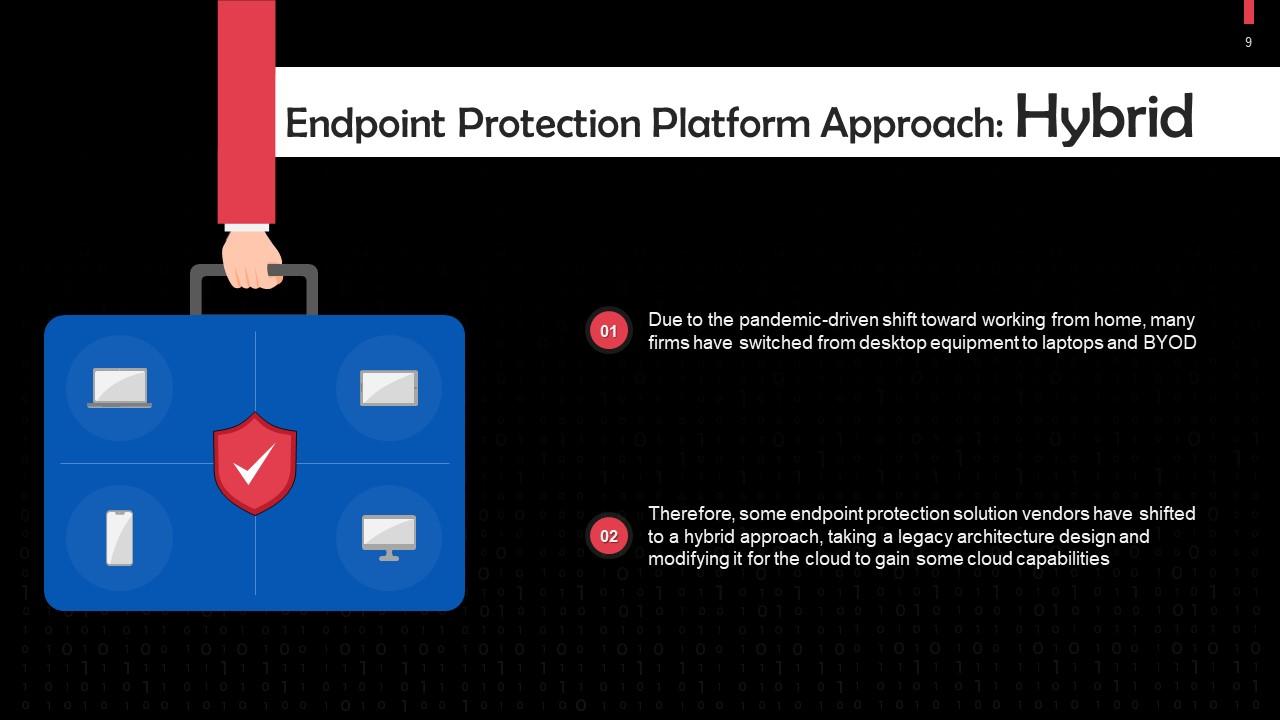
This slide discusses the hybrid approach for endpoint protection platforms. Some endpoint protection solution vendors have shifted to it. This involves taking a legacy architecture design and modifying it for the cloud to gain some cloud capabilities.
Slide 10
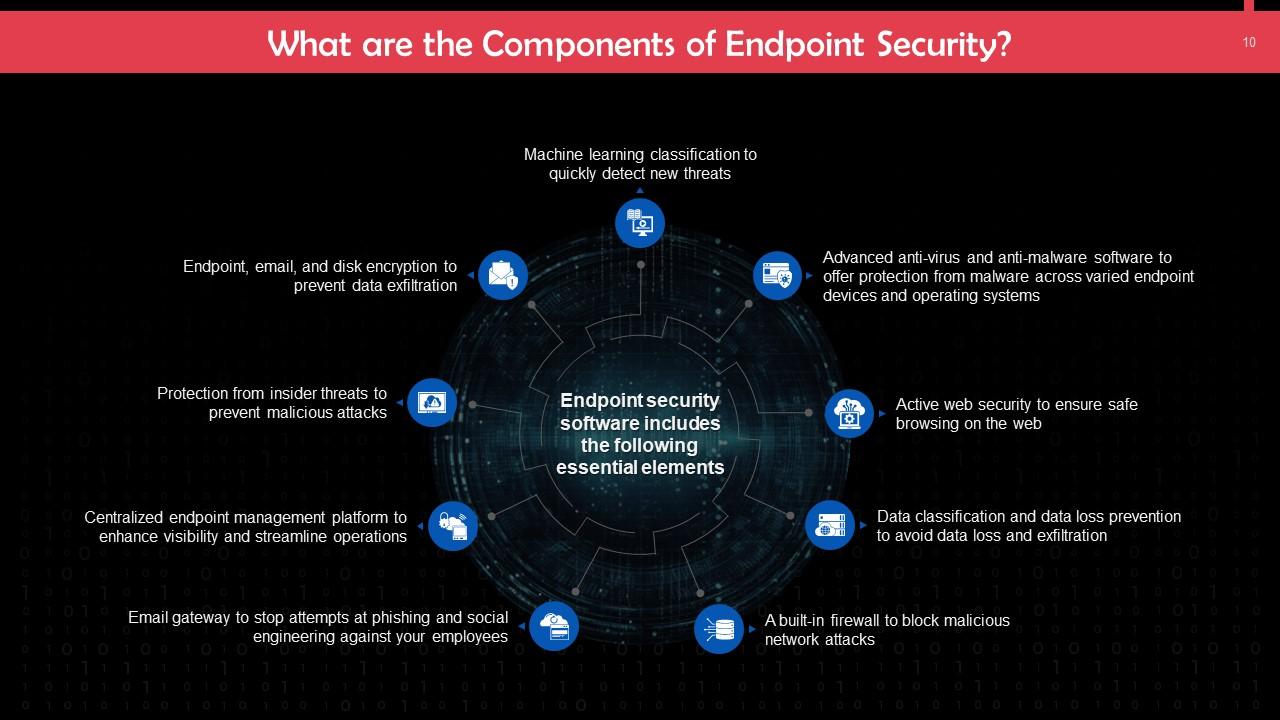
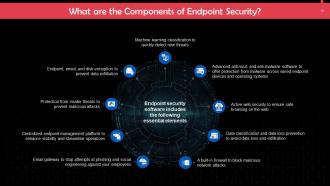
This slide lists the key components of endpoint security. These include: machine learning classification to quickly detect new threats, a built-in firewall to block malicious network attacks, etc.
Slide 11
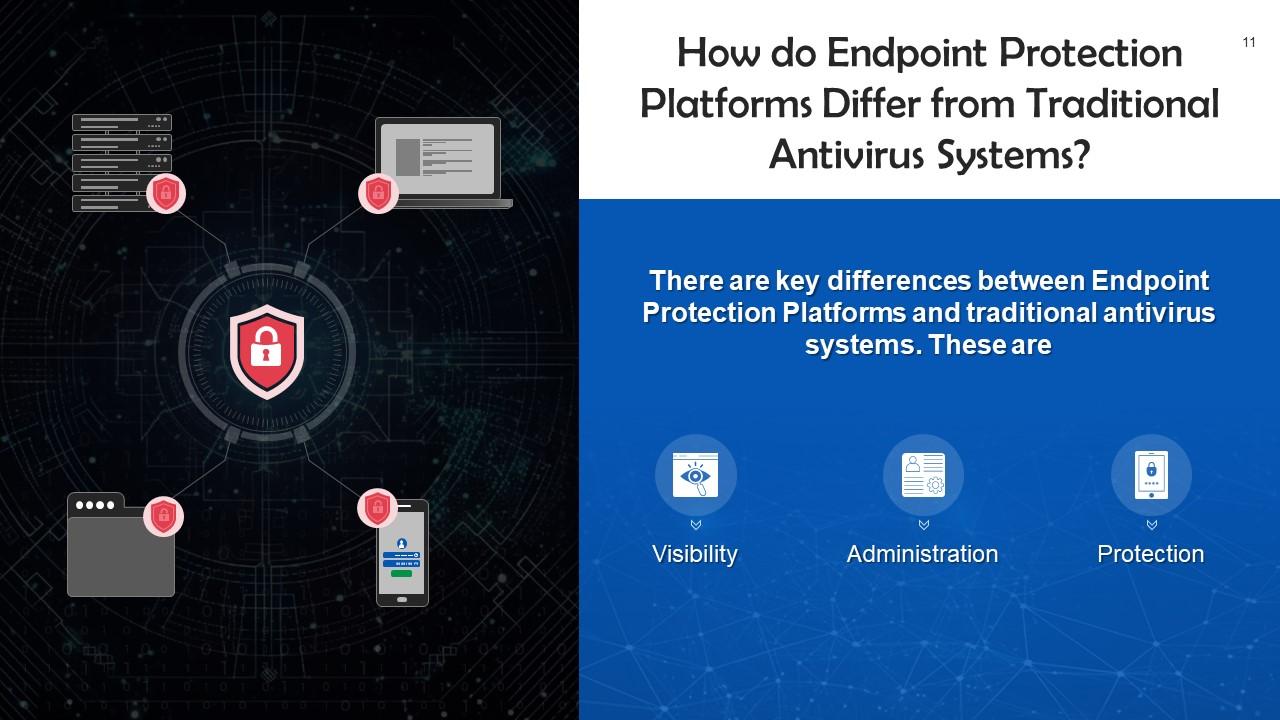
This slide highlights difference between endpoint protection and traditional antivirus systems. These are visibility, administration, and protection.
Slide 12
This slide highlights the difference between endpoint security and network security. Endpoint security software takes a holistic approach toward the company network and can provide visibility of every connected endpoint from a single location.
Slide 13
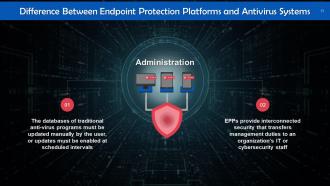
This slide discusses administration as a key difference between endpoint protection and anti-virus solutions. The databases of traditional anti-virus programs must be updated manually by the user, or updates must be enabled at scheduled intervals.
Slide 14
This slide talks about protection as a key difference between endpoint protection and anti-virus solutions. Traditional anti-virus solutions use signature-based detection to find viruses. This means that you could still be at risk if your users haven't recently updated their anti-virus software. Today's EPP solutions are automatically updated.
Slide 15
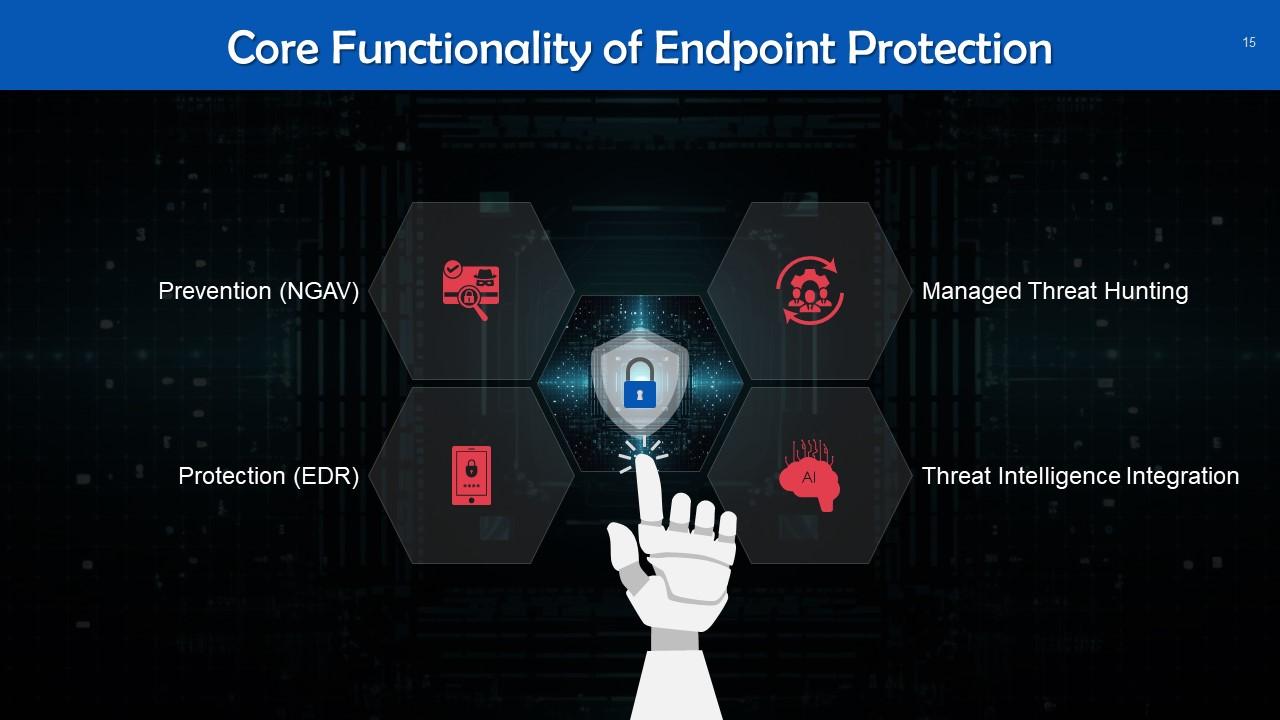
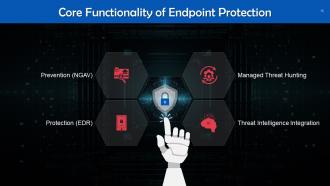
This slide lists key elements of endpoint protection. These are: Prevention, protection, managed threat hunting, and threat intelligence integration.
Slide 16
This slide discusses protection as an element of endpoint protection. Next-Generation Antivirus (NGAV) employs evolved endpoint protection technologies, such as AI and ML, to identify new malware by examining more elements like file hashes, URLs, and IP addresses.
Slide 17
This slide talks about detection in endpoint protection. An Endpoint Detection and Response (EDR) solution offers continuous and detailed visibility into what is happening on endpoints in real-time.
Slide 18
This slide talks about managed threat hunting in endpoint protection. Automation alone cannot identify every attack. The ability of security experts is crucial to identify today's complex threats.
Slide 19
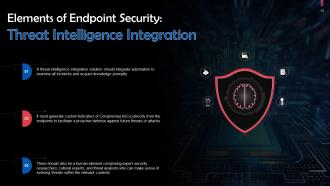
This slide talks about threat intelligence integration in endpoint protection. A threat intelligence integration solution should integrate automation to examine all incidents and acquire knowledge promptly.
End User Security A Cybersecurity Component Training Ppt with all 39 slides:
Use our End User Security A Cybersecurity Component Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
The designs are very attractive and easy to edit. Looking forward to downloading more of your PowerPoint Presentations.
-
Nice and innovative design.