How Blockchain DDoS Attacks Work Training Ppt
This set of slides covers the damaging consequence of Distributed Denial of Service attack on the blockchain, such as node failures and bloated ledger. It also includes information on how a DDoS attack happens, recent prominent attacks, and preventative measures to avoid it.
This set of slides covers the damaging consequence of Distributed Denial of Service attack on the blockchain, such as node ..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting How Blockchain DDoS Attacks Work. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1
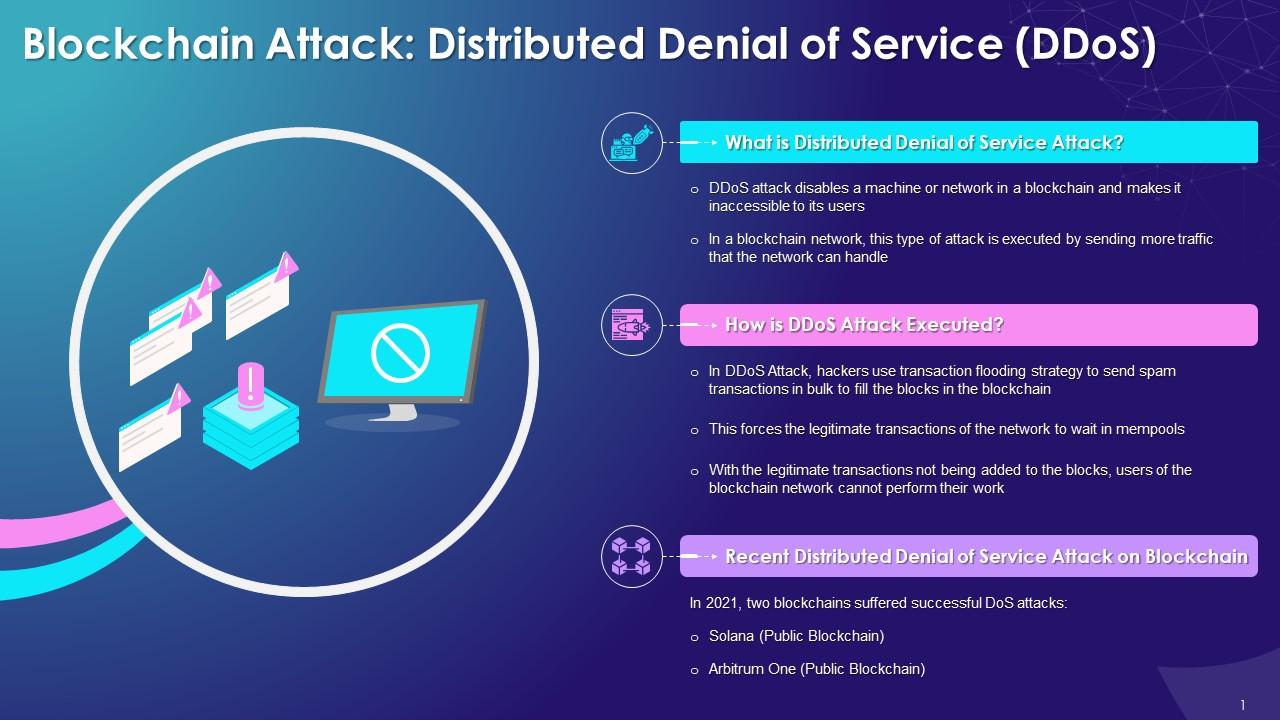
This slide highlights the concept of denial-of-service attack on blockchain. Further It also contains information on how DDoS attack is conducted using transaction flooding approach. It also contains details of recent DDoS attacks on Solana and Arbitrum One public blockchains.
Slide 2
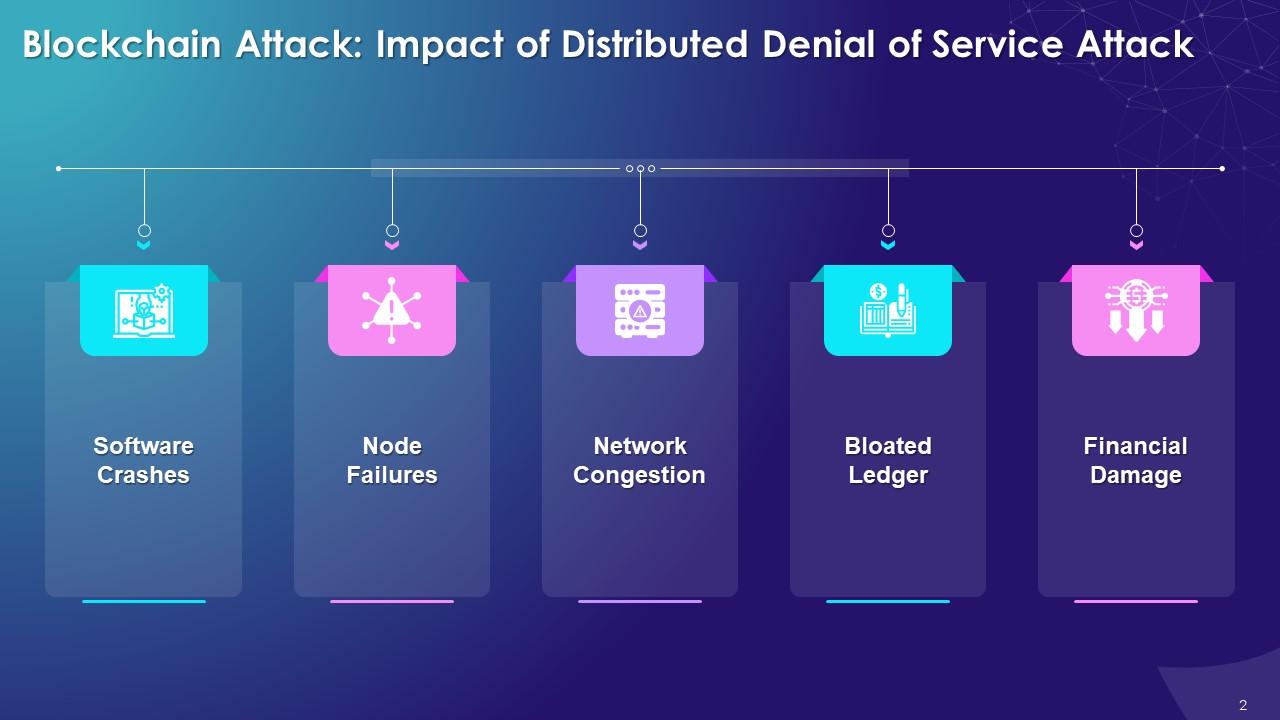
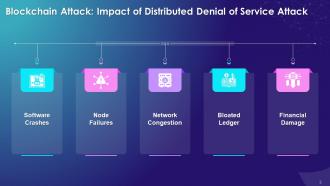
This slide showcases information about the aftermath of distributed denial of service attacks on blockchain. It explains how a blockchain network is subjected to software crashes, node failure, network congestion, bloated ledger, and financial damages when under this kind of attack.
Instructor’s Notes:
Impact of DDoS attacks on blockchain network are as follows:
Software Crashes:
- Blockchain software can perform a limited number of transactions
- Also, they have predefined mempool storage capacity
- Transaction flooding tests this limit, resulting in the crashing of the software in crashing of software
Node Failures:
- DDoS attack can force a node to run out of memory ; this can make it go offline unless the system is restarted
Network Congestion:
- When under a DDoS attack, nodes receive multiple copies of the same transaction, causing congestion. It also results in consumption of more bandwidth
Bloated Ledger:
- A ledger stuffed with spam transactions permanently impacts blockchain technology
Financial Damage:
- Users cannot access blockchain networks because of DDoS attacks and are unable to perform important business transactions. Financial damages are the end-result.
Slide 3
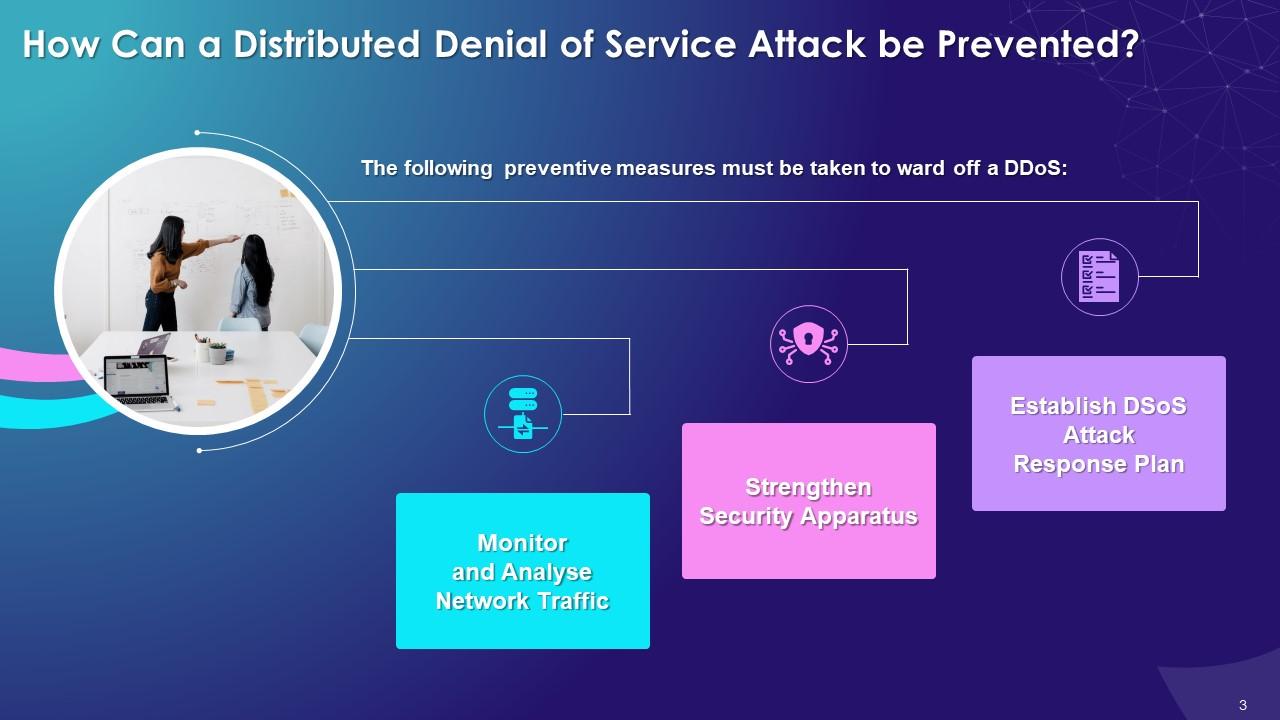
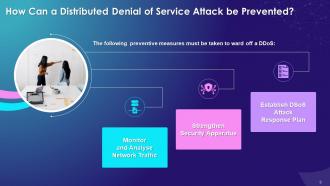
This slide illustrates the multiple prevention measures that can be taken to prevent the distributed denial of service attack in blockchain technology such as to monitor and analyze network traffic, strengthen security apparatus, and establishing an attack response plan.
Instructor’s Notes:
Different methods used to prevent and protect from DDoS attack are as follows:
Monitor and analyze network traffic:
- It is important to install an intrusion detection system in the blockchain network system to supervise network traffic
- This type of detection system will help inform all members in the network about any unusual traffic
- Enhances security of any blockchain system and ensure blocks are free of unwanted traffic
Strengthen security apparatus:
- Every system that is being used for blockchain technology needs to be secure against malicious attackers
- Strength different internet devices. Installation and maintenance of antivirus software and establishing firewalls configured to prevent DDoS attacks are a must-do
Establish a DDoS attack response plan:
- Create and practice a disaster recovery plan to prevent DDoS attacks on a blockchain network
How Blockchain DDoS Attacks Work Training Ppt with all 19 slides:
Use our How Blockchain DDoS Attacks Work Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Love how there are no boring templates here! The design is fresh and creative, just the way I like it. Can't wait to edit and use them for my extended projects!
-
Very unique, user-friendly presentation interface.