Implementing Effective Tokenization Strategies Powerpoint Presentation Slides
Explore our Implementing Effective Tokenization Strategies Presentation, which explains how to implement effective tokenization in an organization. It also includes critical challenges, performance analysis, and a project summary of tokenization. Additionally, this Platform Tokenization Deployment PPT demonstrates the various tokenization approaches, including platform, transactional, cloud-based, asset, and security tokenization. Furthermore, this Implementing Transactional Tokenization Template includes the team structure for implementing tokenization in IT. It also consists of the responsibility assignment matrix for tokenization to showcase the responsibilities. Furthermore, the Safeguarding Data through Tokenization PPT caters to scenarios after implementing tokenization in the organizational networks based on several parameters. It also includes the optimal selection of tokenization tools and platforms. Lastly, this Safeguarding Data through Tokenization Deck outlines best practices, a checklist, a training budget, a timeline, a roadmap, and the impact of tokenization. Download our 100 percent editable and customizable template, also compatible with Google Slides.
Explore our Implementing Effective Tokenization Strategies Presentation, which explains how to implement effective tokeniza..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver an informational PPT on various topics by using this Implementing Effective Tokenization Strategies Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with fifty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Implementing Effective Tokenization Strategies. State Your Company Name and begin.
Slide 2: This slide is an Agenda slide. State your agendas here.
Slide 3: This slide shows a Table of Contents for the presentation.
Slide 4: This slide is an introductory slide.
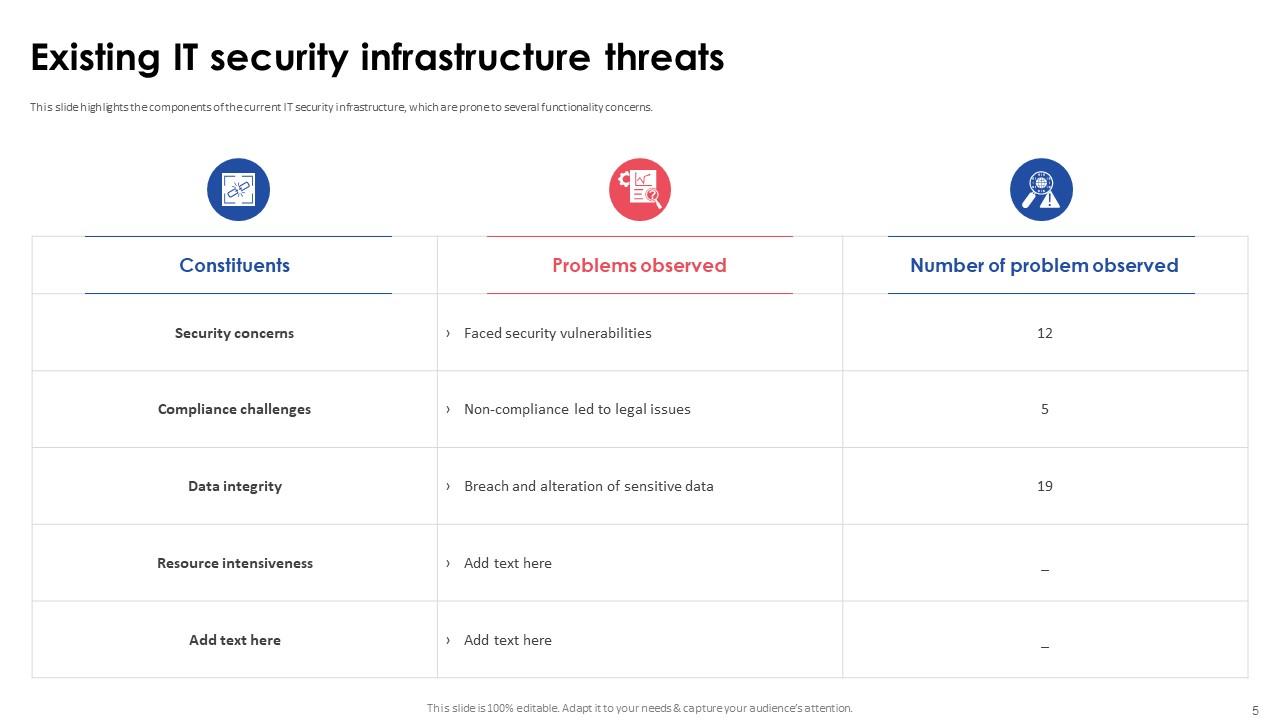
Slide 5: This slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns.
Slide 6: This slide is an introductory slide.
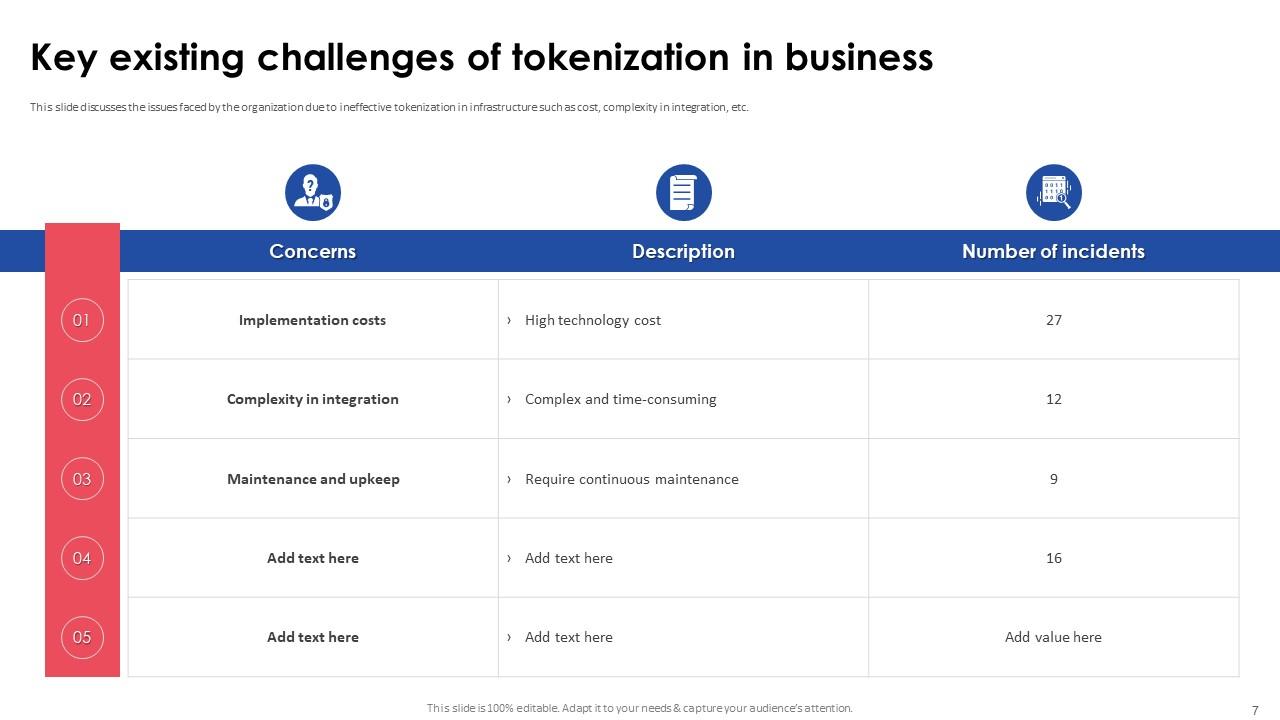
Slide 7: This slide discusses the issues faced by the organization due to ineffective tokenization in infrastructure such as cost, complexity in integration, etc.
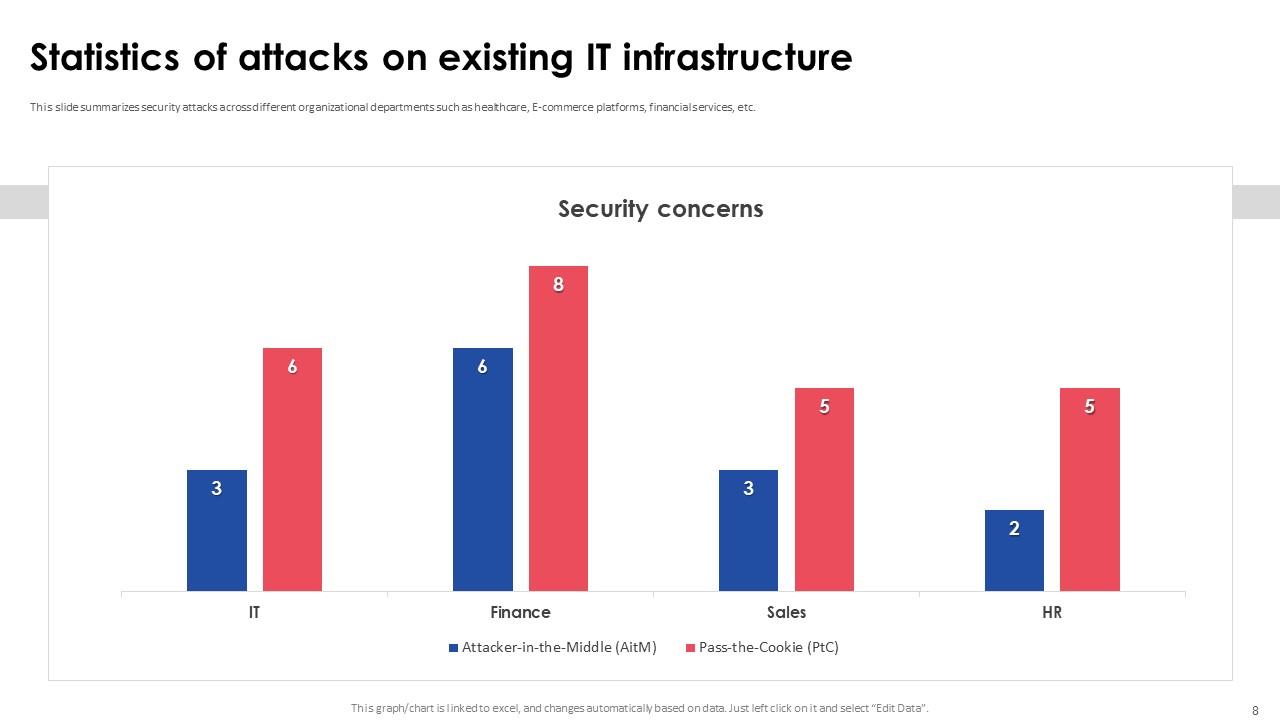
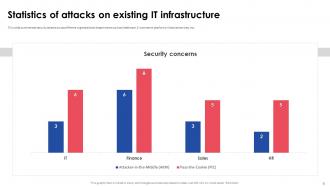
Slide 8: This slide summarizes security attacks across different organizational departments such as healthcare, E-commerce platforms, financial services, etc.
Slide 9: This slide is an introductory slide.
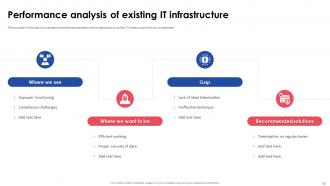
Slide 10: This slide indicates the performance analysis of the organization’s current IT infrastructure with key components.
Slide 11: This slide is an introductory slide.
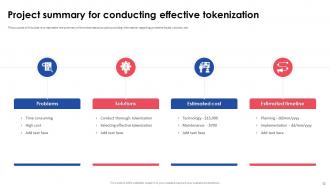
Slide 12: This slide is to represent the summary of the tokenization project providing information regarding problems faced, solution, etc.
Slide 13: This slide is an introductory slide.
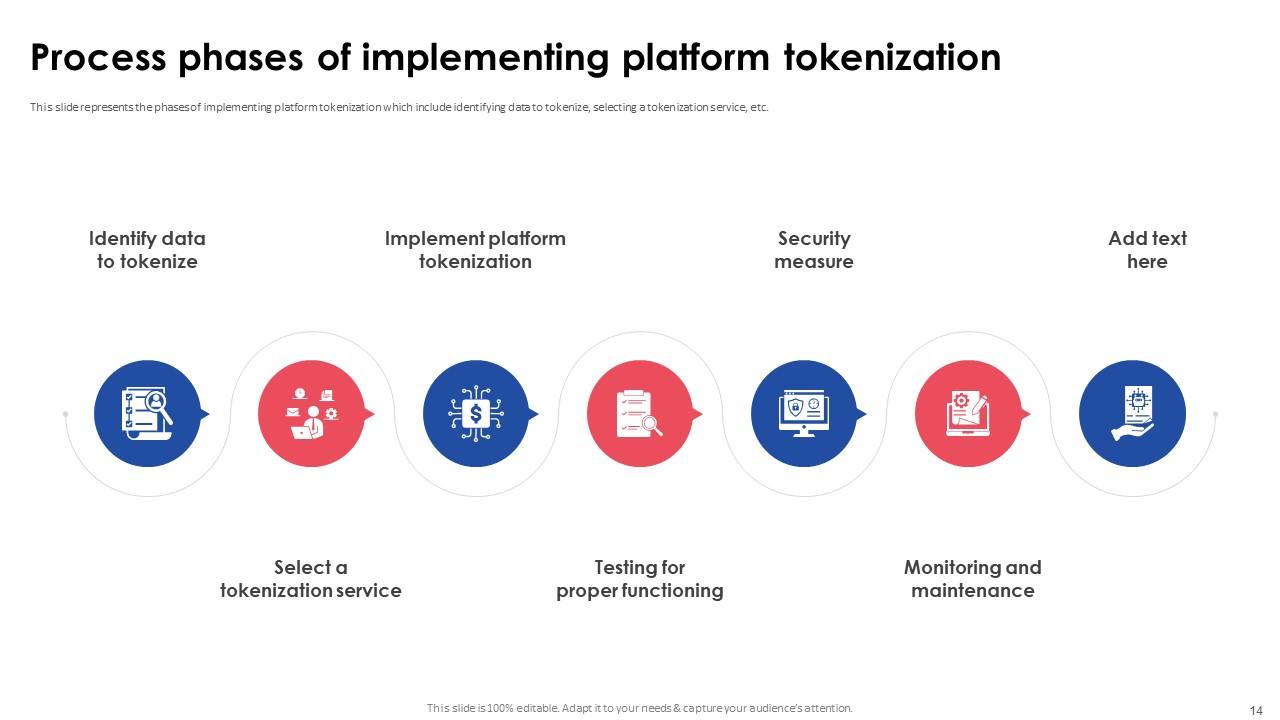
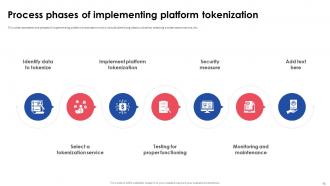
Slide 14: This slide represents the phases of implementing platform tokenization which include identifying data to tokenize, selecting a tokenization service, etc.
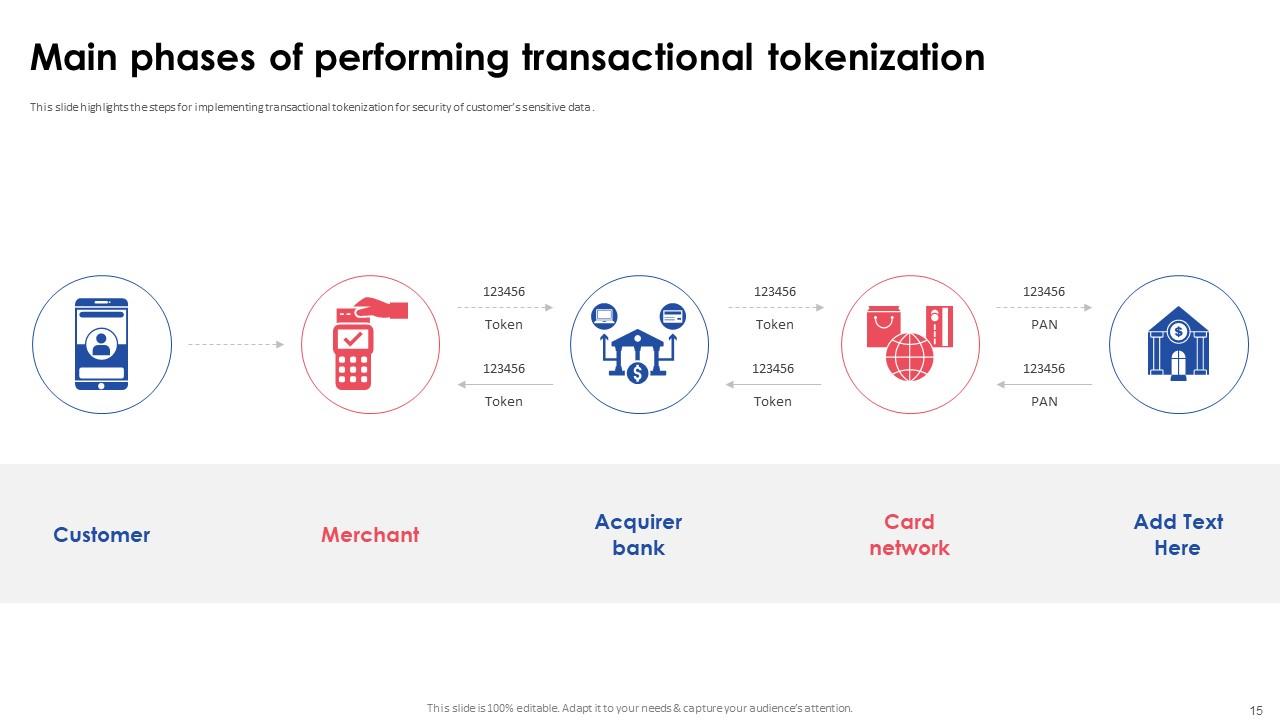
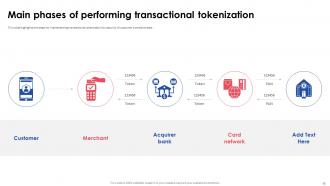
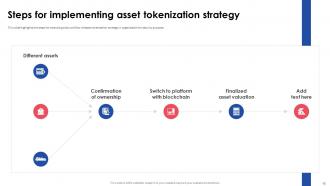
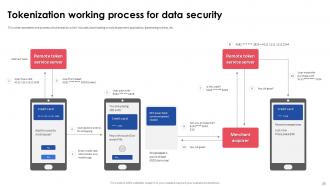
Slide 15: This slide highlights the steps for implementing transactional tokenization for security of customer’s sensitive data .
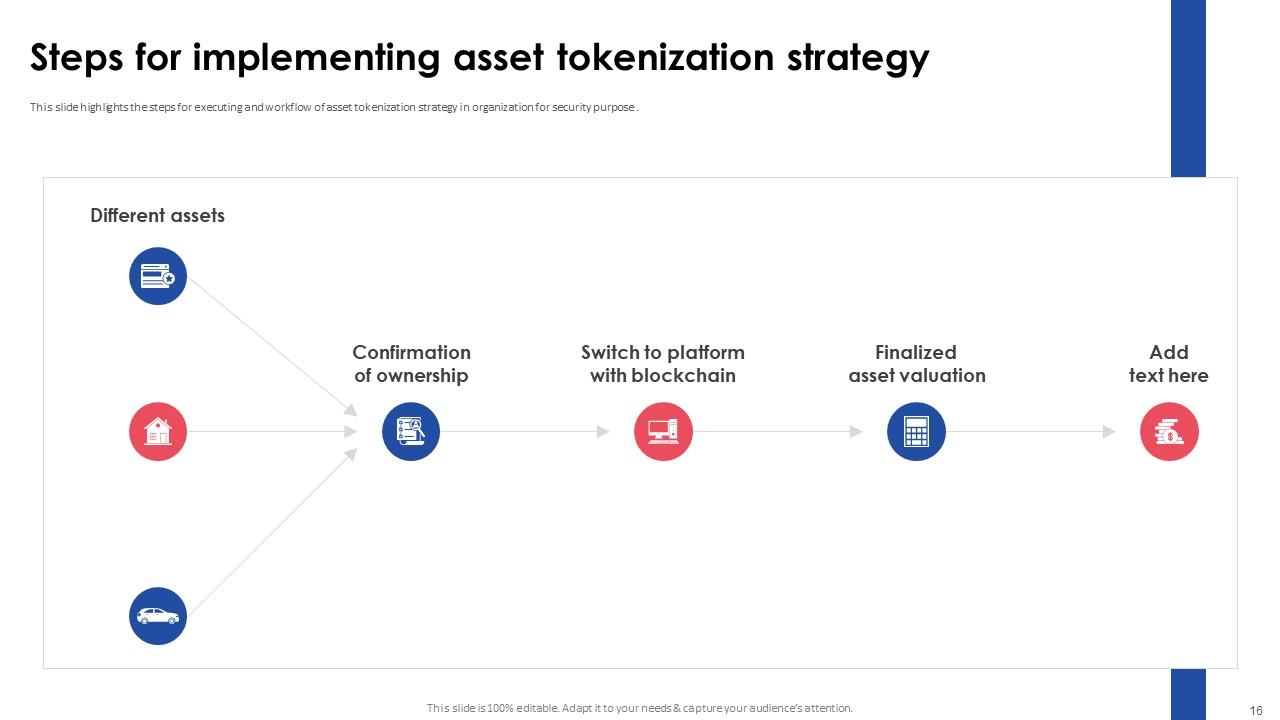
Slide 16: This slide entails the steps for executing and workflow of asset tokenization strategy in organization for security purpose .
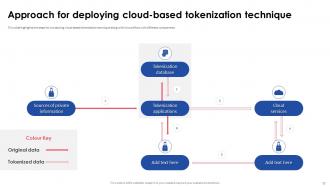
Slide 17: This slide illustrates the steps for conducting cloud-based tokenization technique along with its workflow with different components.
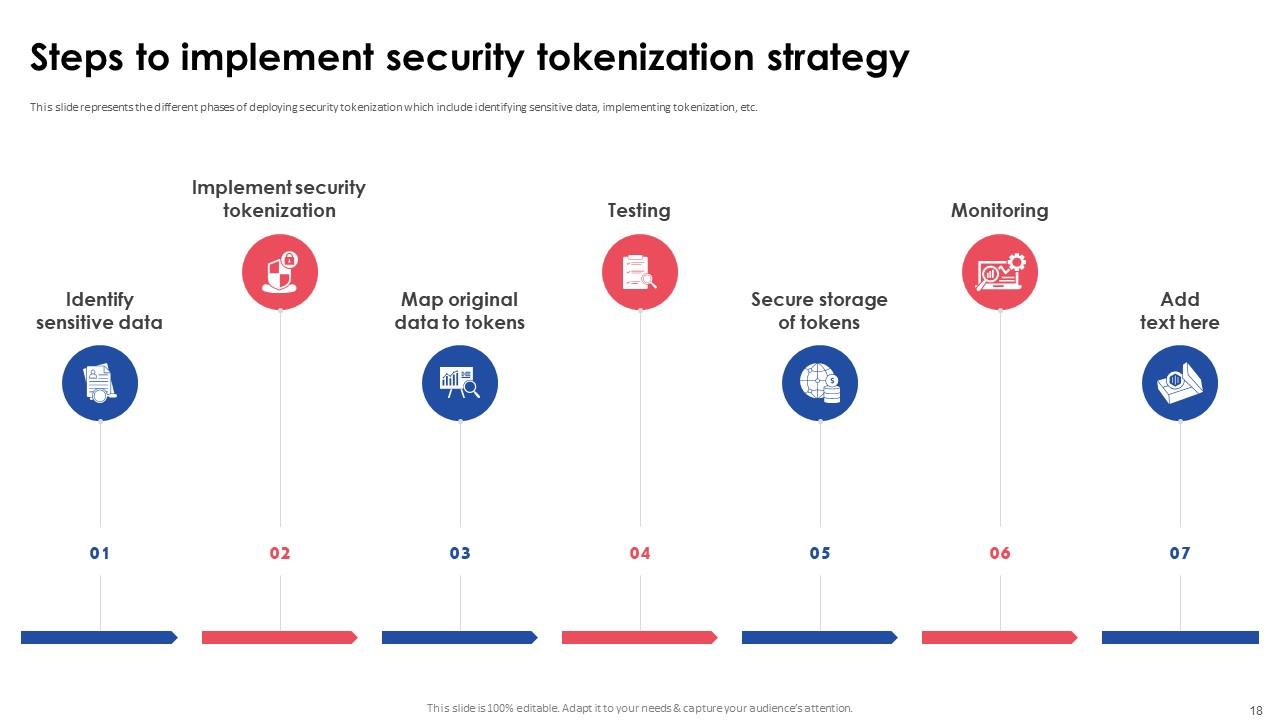
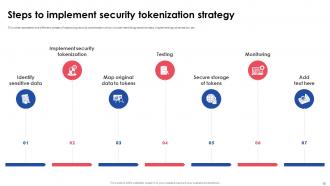
Slide 18: This slide represents the different phases of deploying security tokenization which include identifying sensitive data, implementing tokenization, etc.
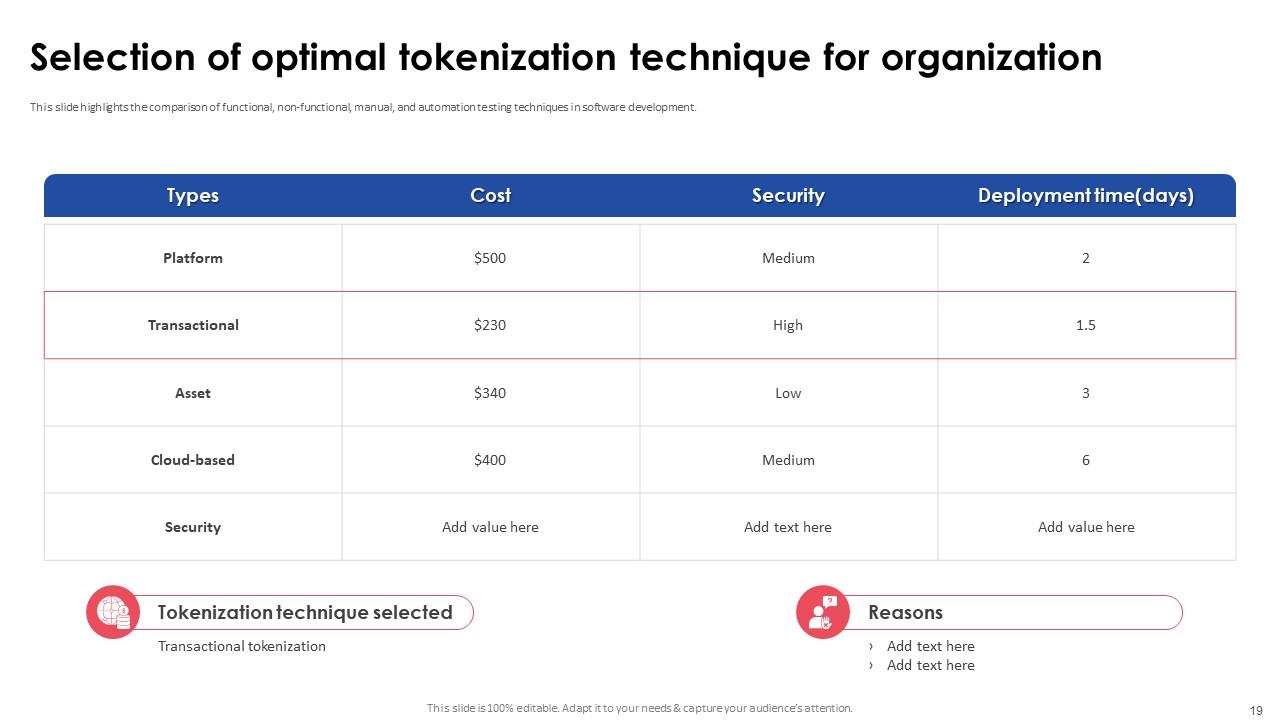
Slide 19: This slide presents the comparison of functional, non-functional, manual, and automation testing techniques in software development.
Slide 20: This slide is an introductory slide.
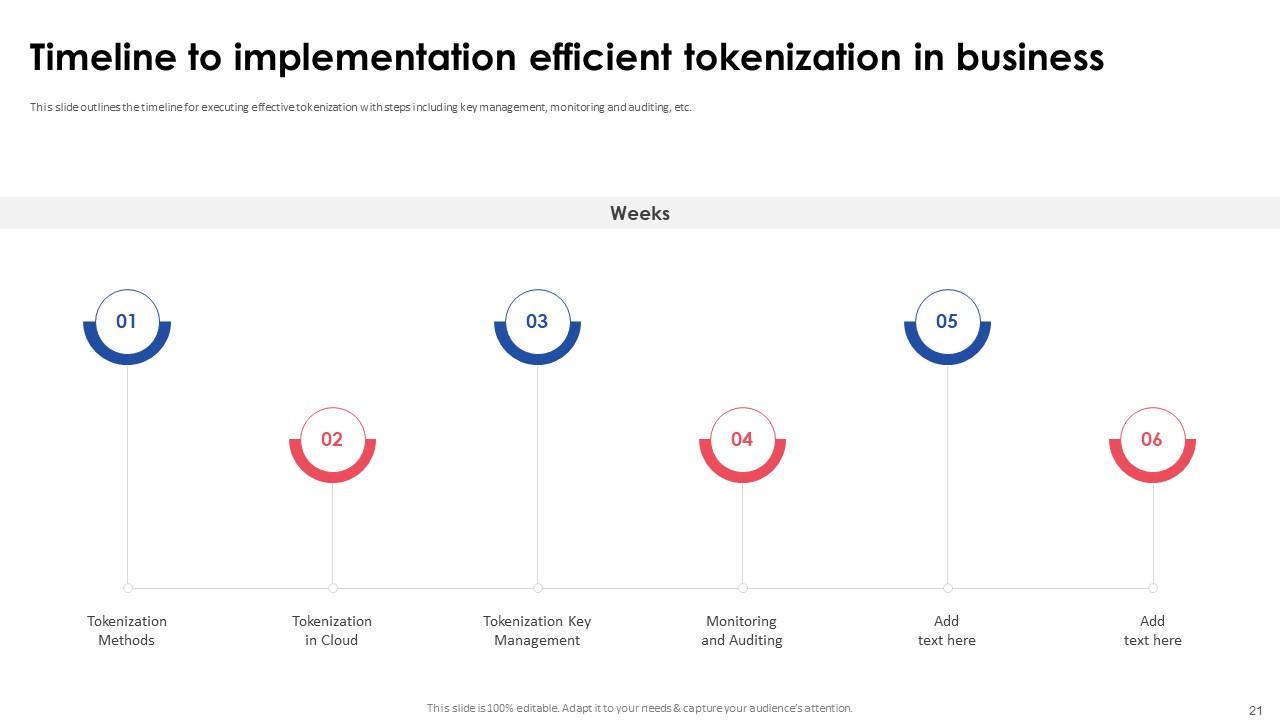
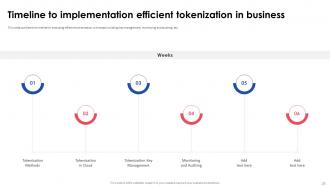
Slide 21: This slide outlines the timeline for executing effective tokenization with steps including key management, monitoring and auditing, etc.
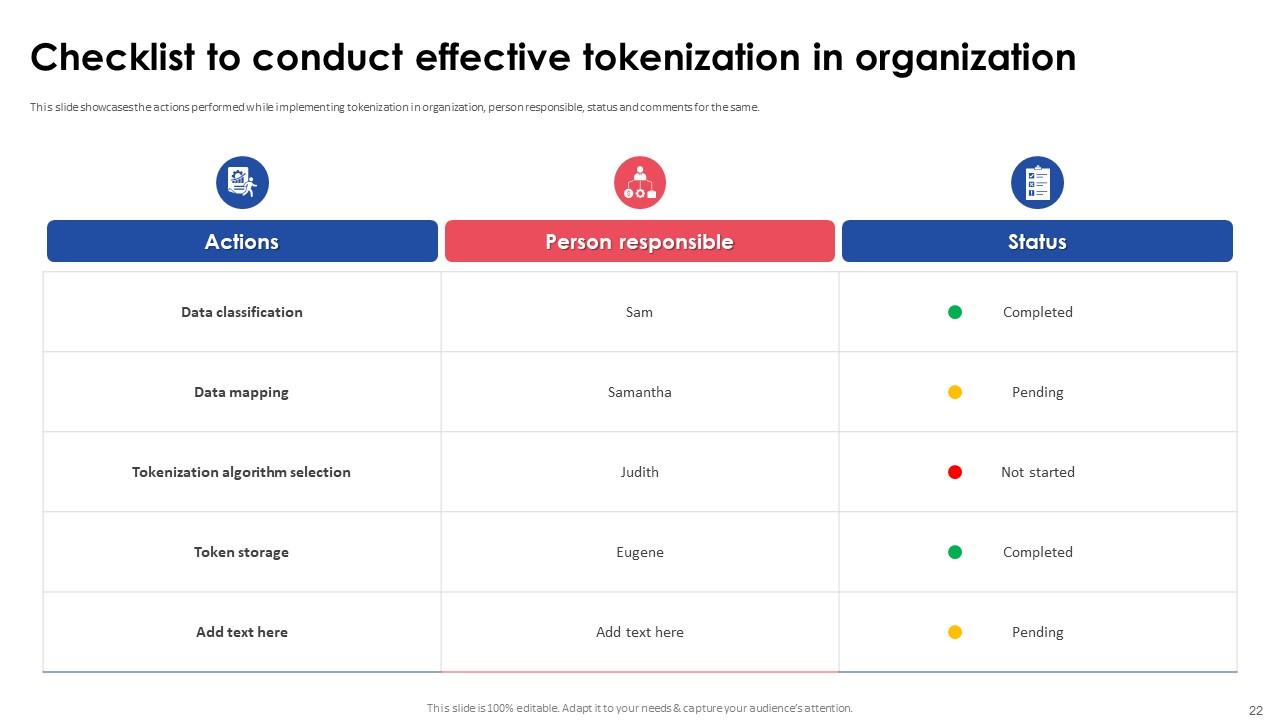
Slide 22: This slide showcases the actions performed while implementing tokenization in organization, person responsible, status and comments for the same.
Slide 23: This slide is an introductory slide.
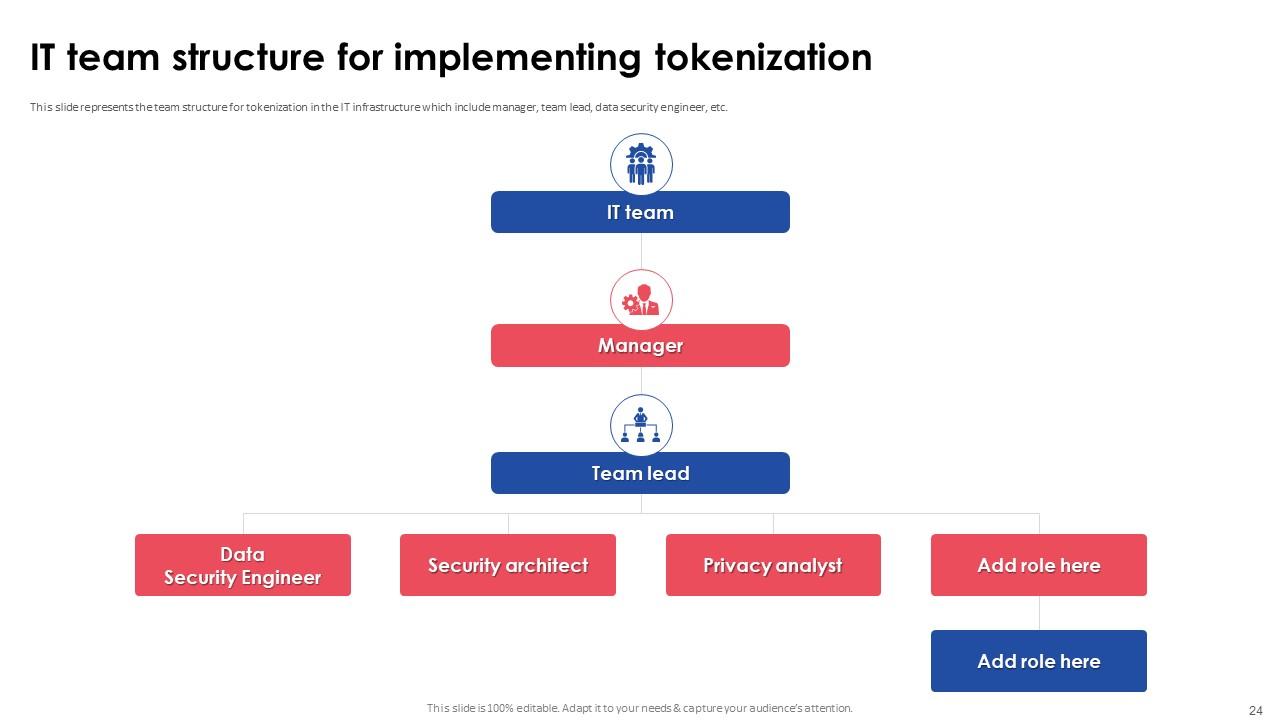
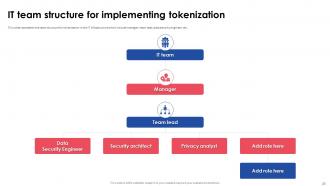
Slide 24: This slide presents the team structure for tokenization in the IT infrastructure which include manager, team lead, data security engineer, etc.
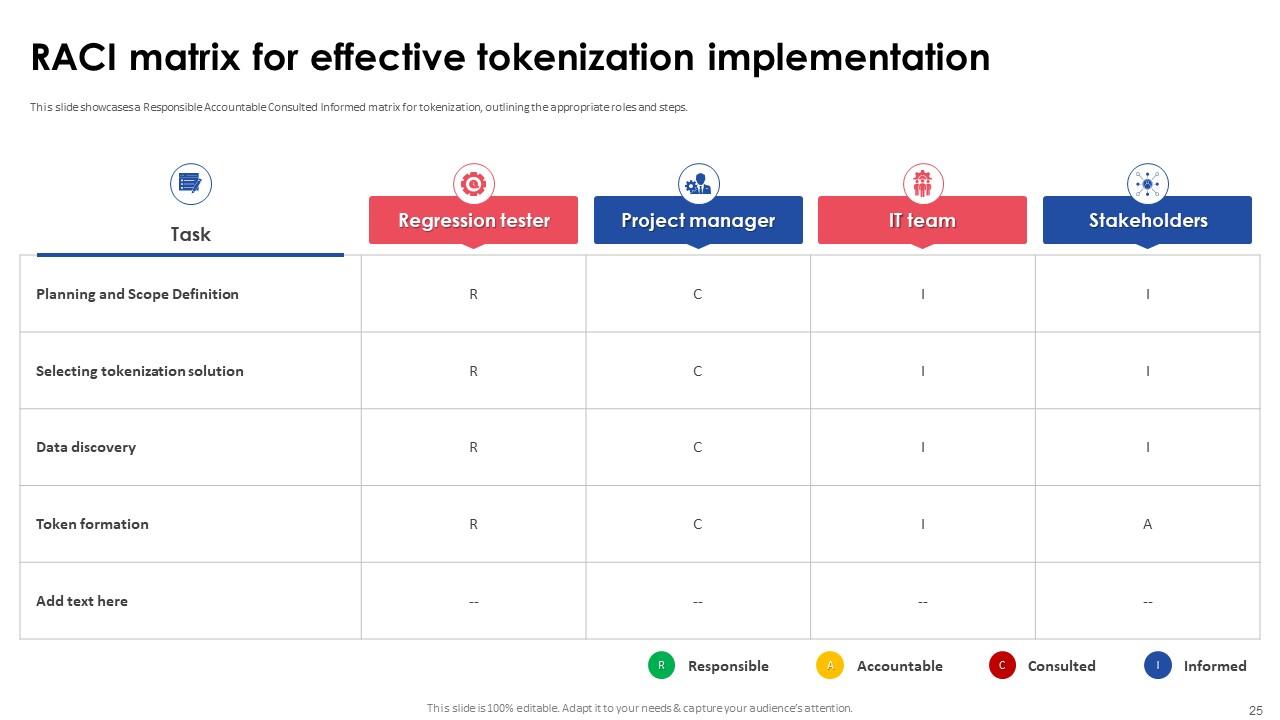
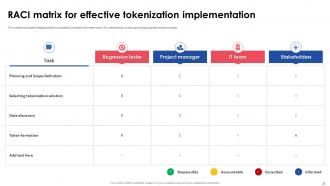
Slide 25: This slide shows a Responsible Accountable Consulted Informed matrix for tokenization, outlining the appropriate roles and steps.
Slide 26: This slide is an introductory slide.
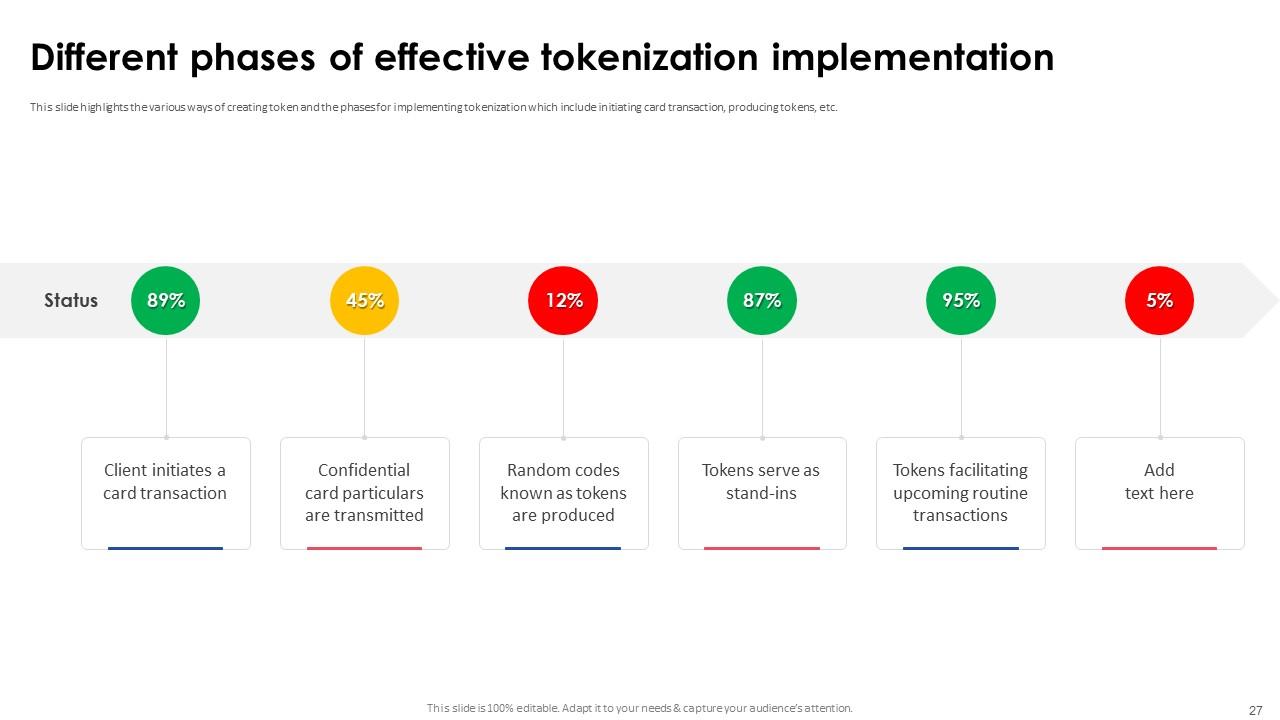
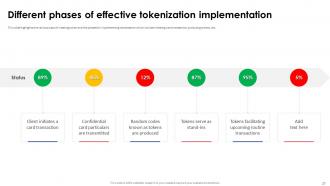
Slide 27: This slide highlights the various ways of creating token and the phases for implementing tokenization which include initiating card transaction, producing tokens, etc.
Slide 28: This slide puts the process of tokenization which includes downloading a mobile payment application, generating tokens, etc.
Slide 29: This slide is an introductory slide.
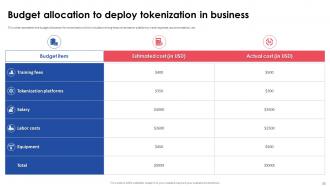
Slide 30: This slide marks the budget allocation for tokenization which includes training fees, tokenization platforms, travel expense, accommodation, etc.
Slide 31: This slide is an introductory slide.
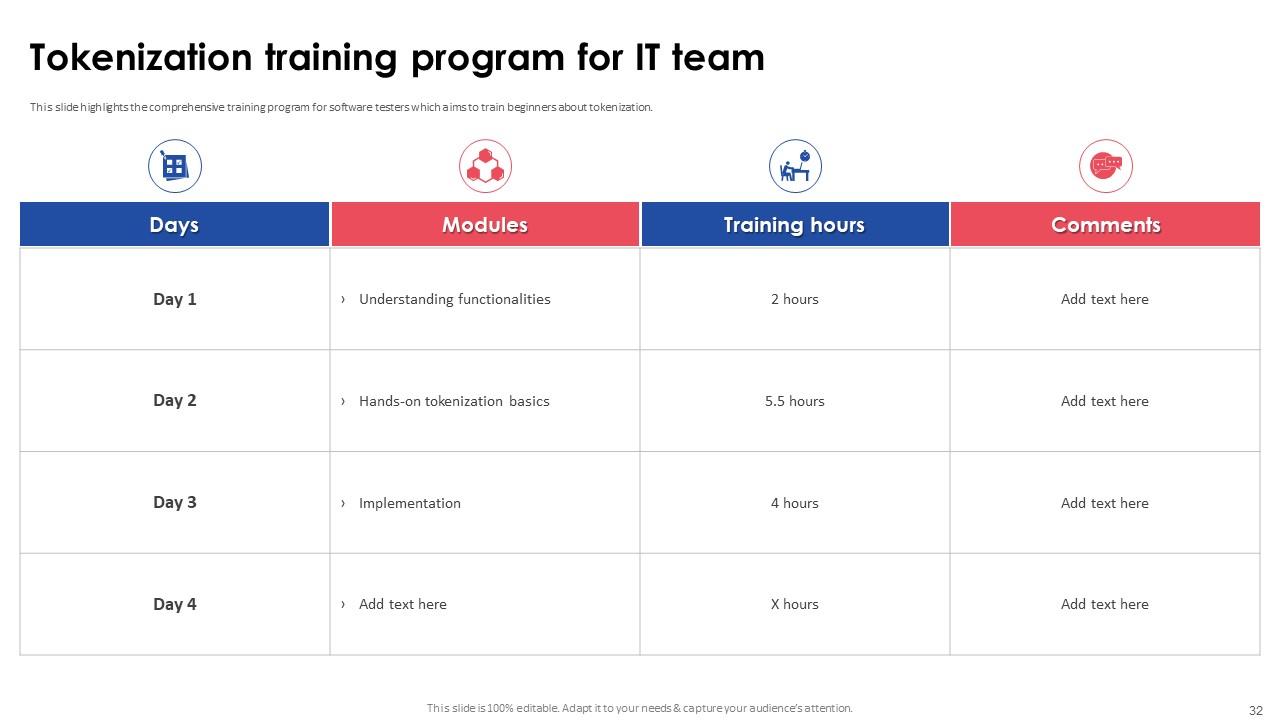
Slide 32: This slide highlights the comprehensive training program for software testers which aims to train beginners about tokenization.
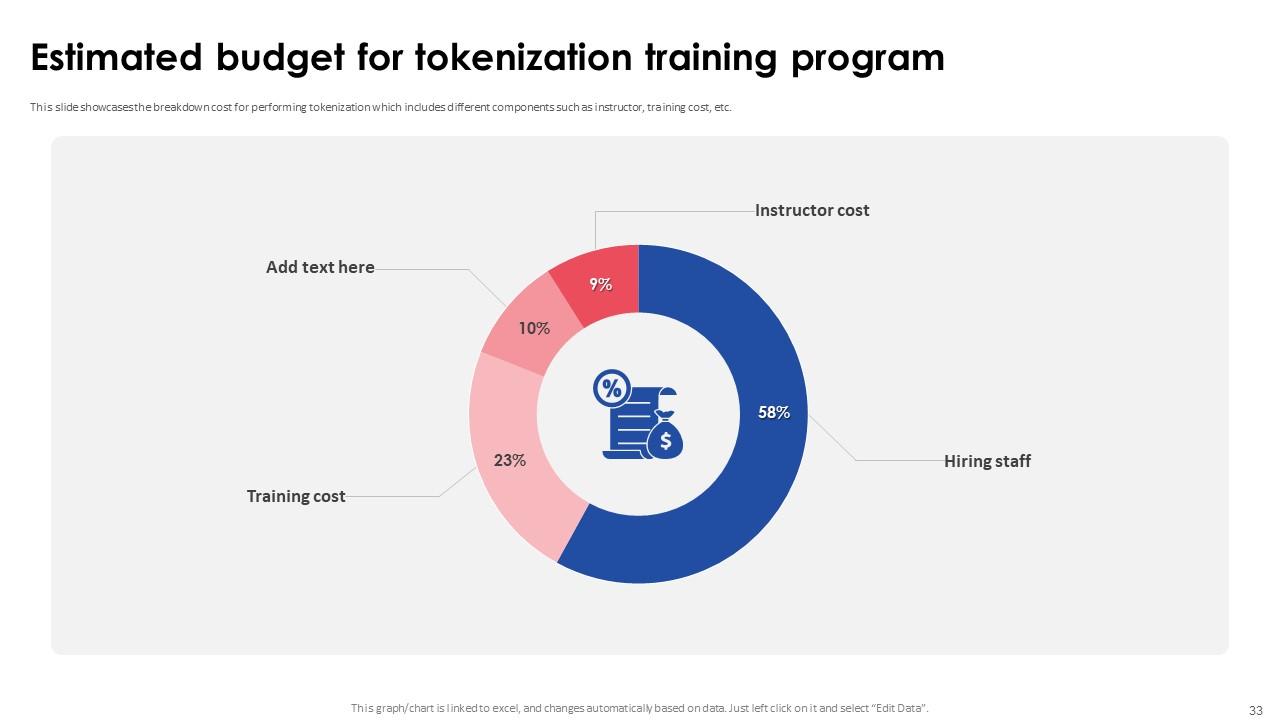
Slide 33: This slide entails the breakdown cost for performing tokenization which includes different components such as instructor, training cost, etc.
Slide 34: This slide is an introductory slide.
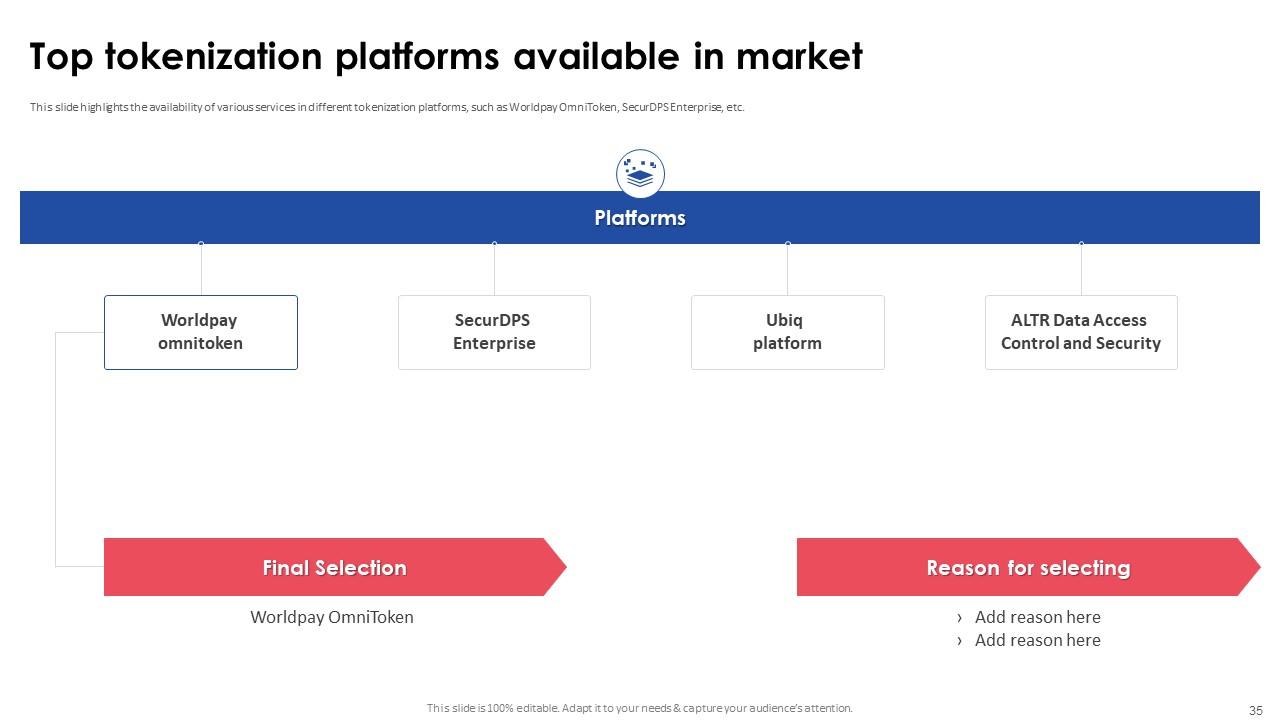
Slide 35: This slide highlights the availability of various services in different tokenization platforms, such as Worldpay OmniToken, SecurDPS Enterprise, etc.
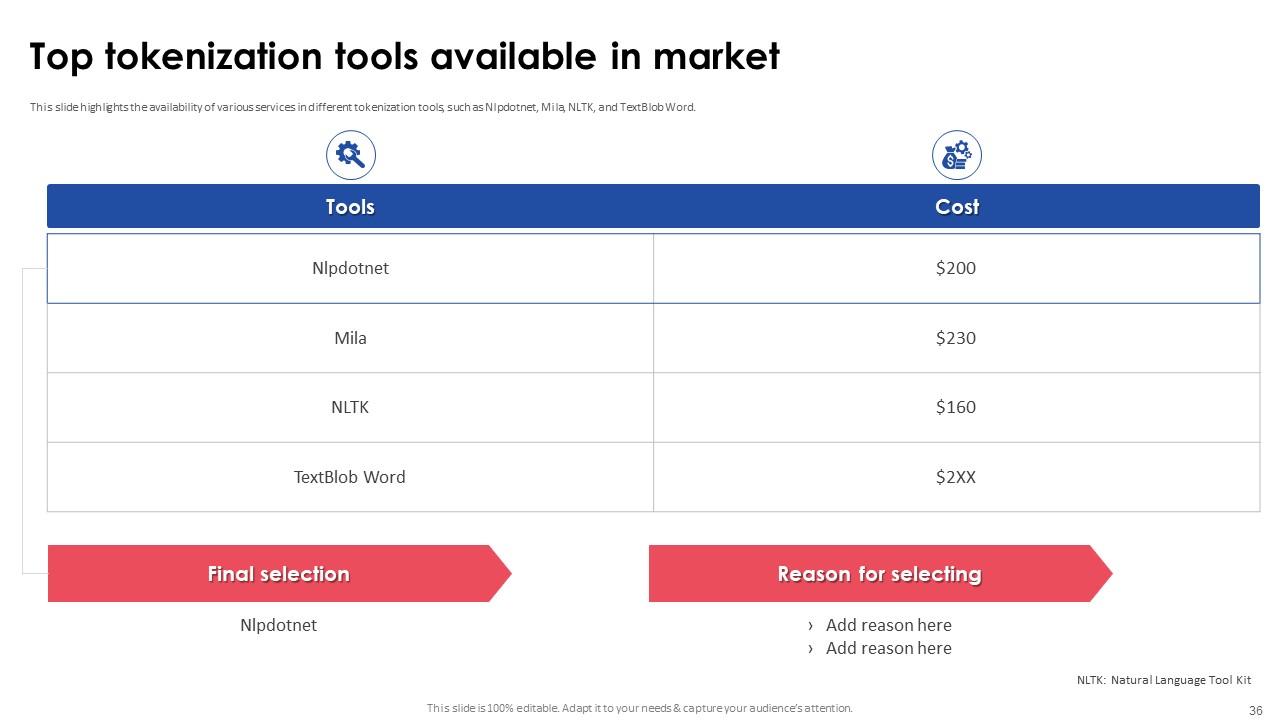
Slide 36: This slide elaborates the availability of various services in different tokenization tools, such as Nlpdotnet, Mila, NLTK, and TextBlob Word.
Slide 37: This slide is an introductory slide.
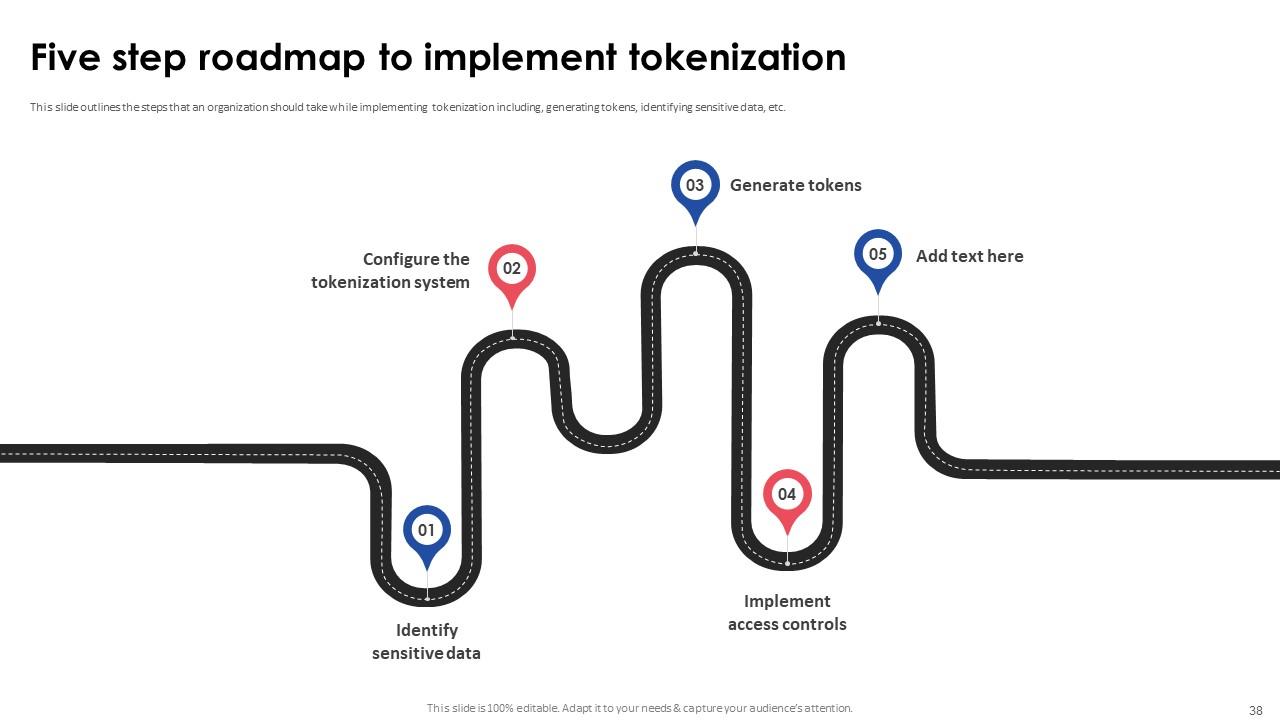
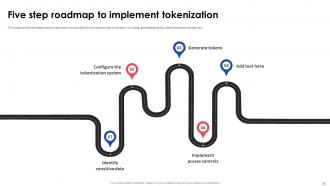
Slide 38: This slide outlines the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc.
Slide 39: This slide is an introductory slide.
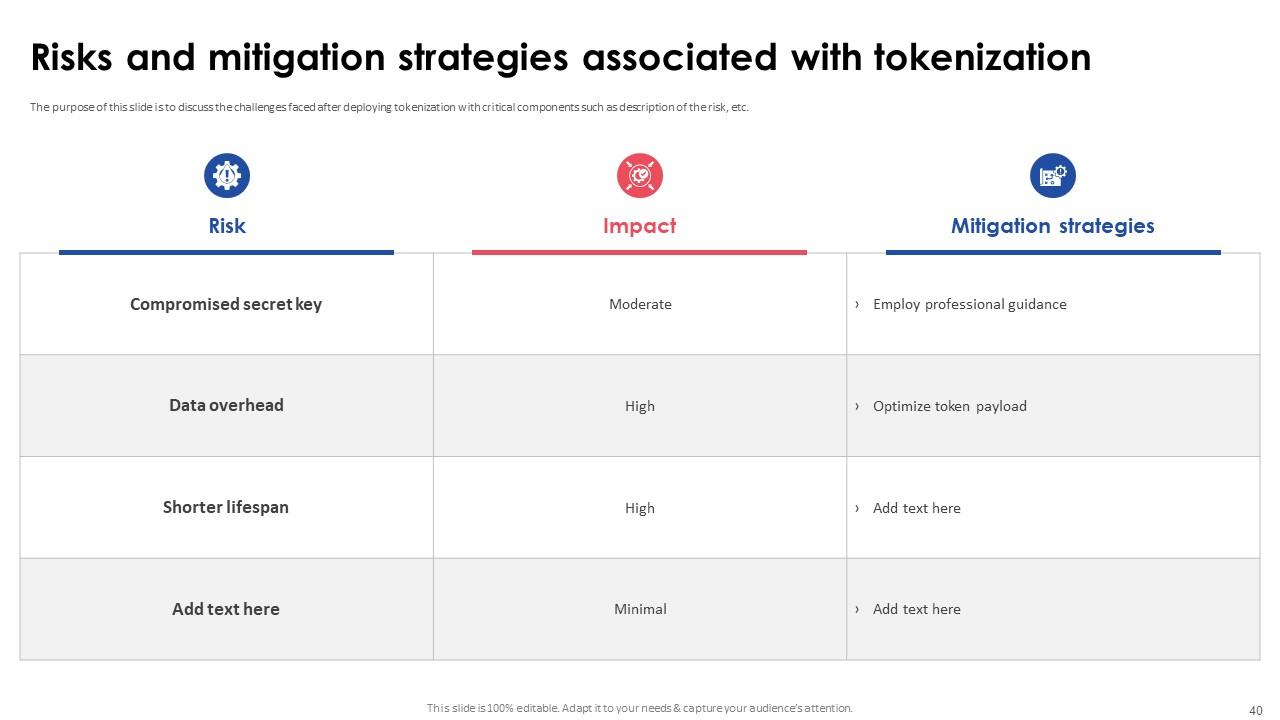
Slide 40: This slide discusses the challenges faced after deploying tokenization with critical components such as description of the risk, etc.
Slide 41: This slide is an introductory slide.
Slide 42: This slide showcases the performance tracking dashboard for tokenization by including components such as key management, crypto, tokenize, etc.
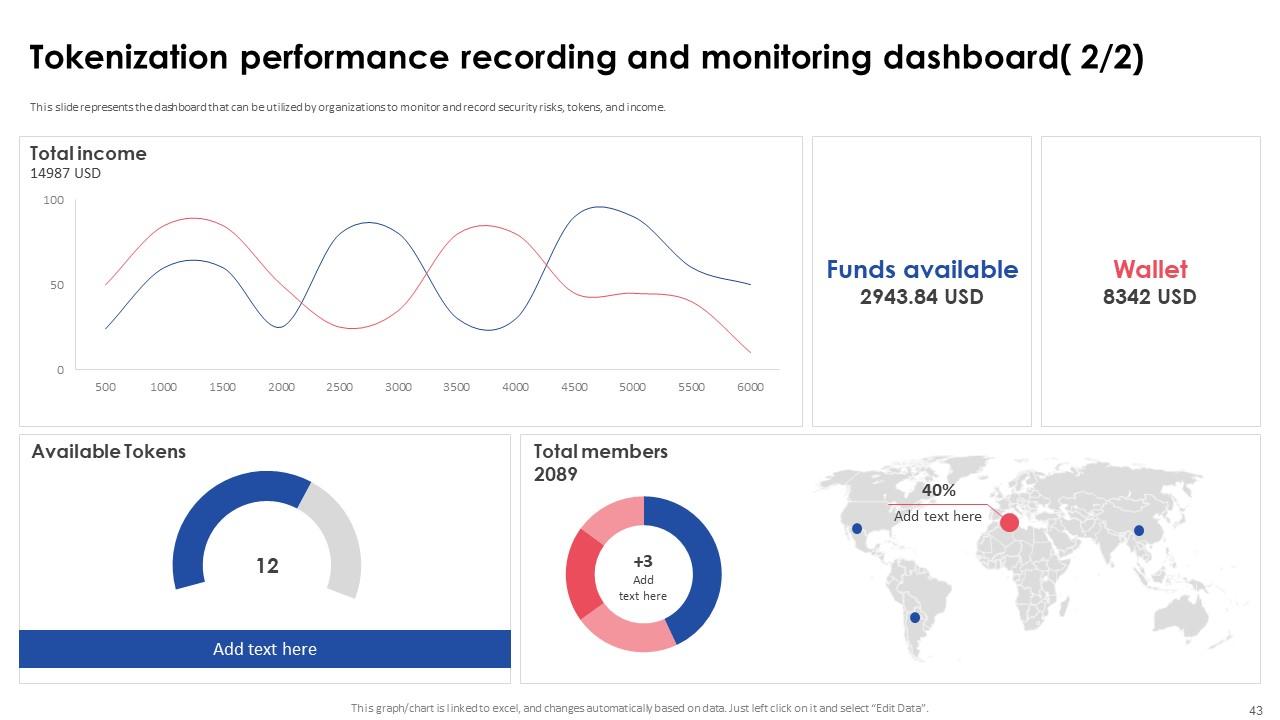
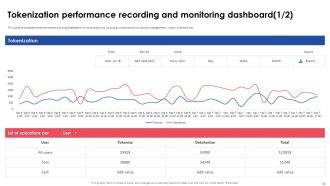
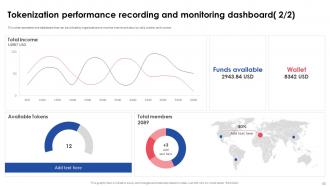
Slide 43: This slide represents the dashboard that can be utilized by organizations to monitor and record security risks, tokens, and income.
Slide 44: This slide is an introductory slide.
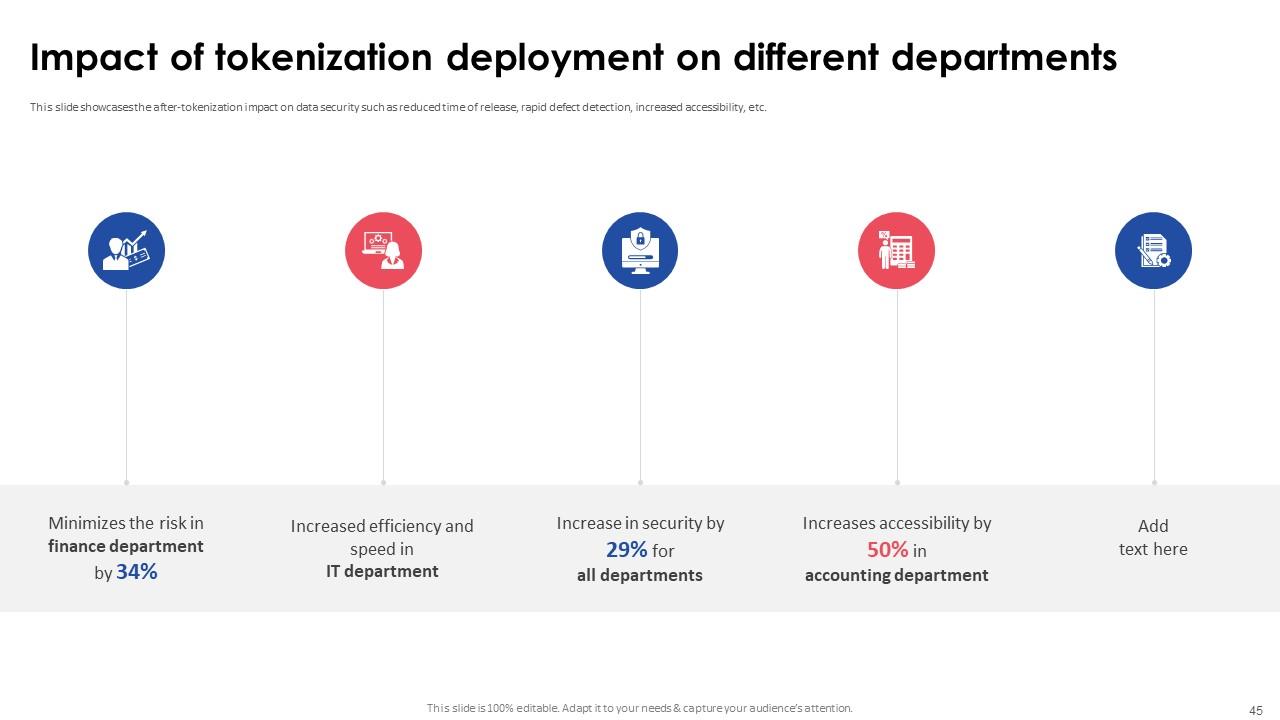
Slide 45: This slide highlights the after-tokenization impact on data security such as reduced time of release, rapid defect detection, increased accessibility, etc.
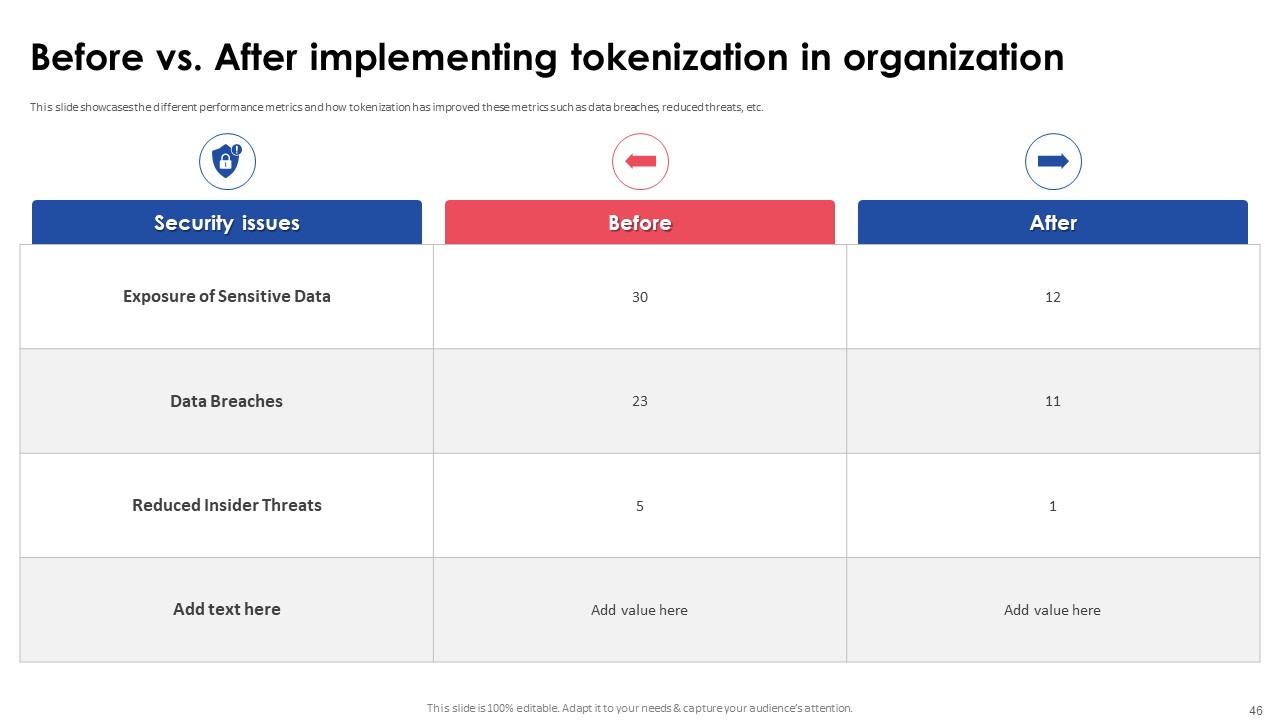
Slide 46: This slide showcases the different performance metrics and how tokenization has improved these metrics such as data breaches, reduced threats, etc.
Slide 47: This slide shows all the icons included in the presentation.
Slide 48: This slide is titled Additional Slides for moving forward.
Slide 49: This slide is an Idea Generation slide to state a new idea or highlight information, specifications, etc.
Slide 50: This slide provides a 30-60-90-day plan with text boxes.
Slide 51: This slide contains a Puzzle with related icons and text.
Slide 52: This slide is a Timeline slide. Show data related to time intervals here.
Slide 53: This slide shows SWOT describing- Strength, Weakness, Opportunity, and Threat.
Slide 54: This slide is Our Target slide. State your targets here.
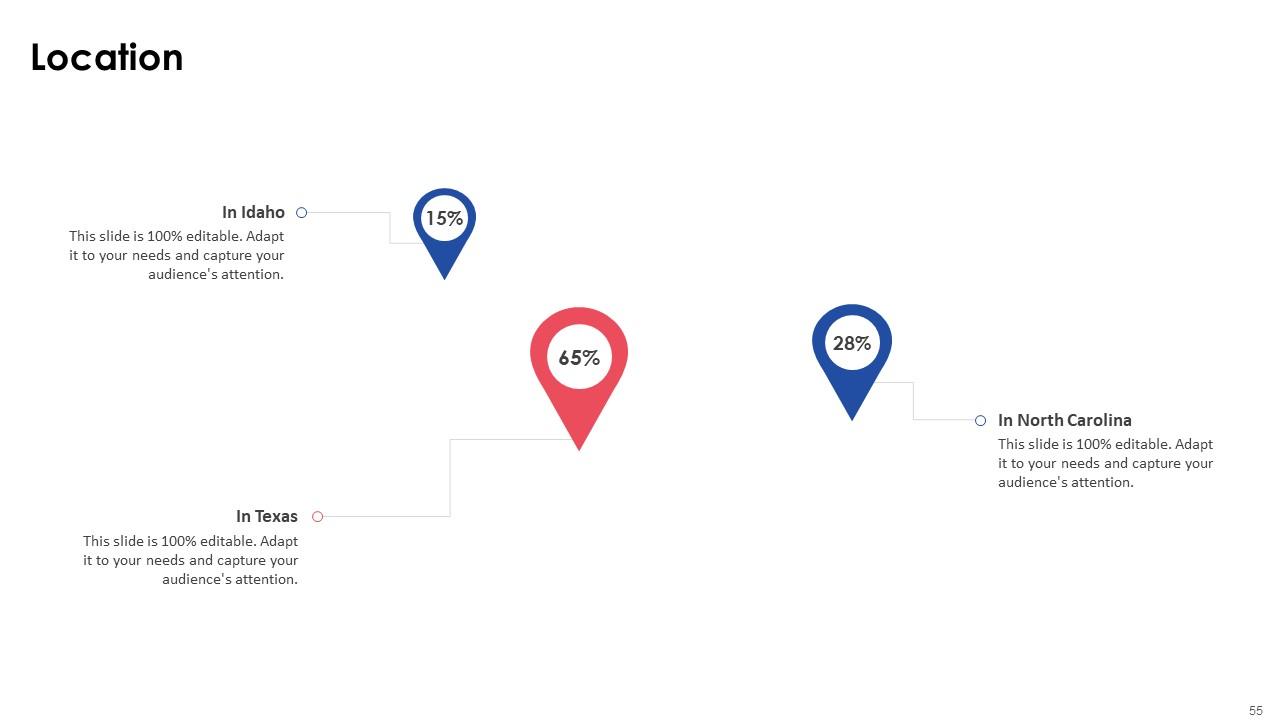
Slide 55: This slide is our location slide, mention your Company's location here.
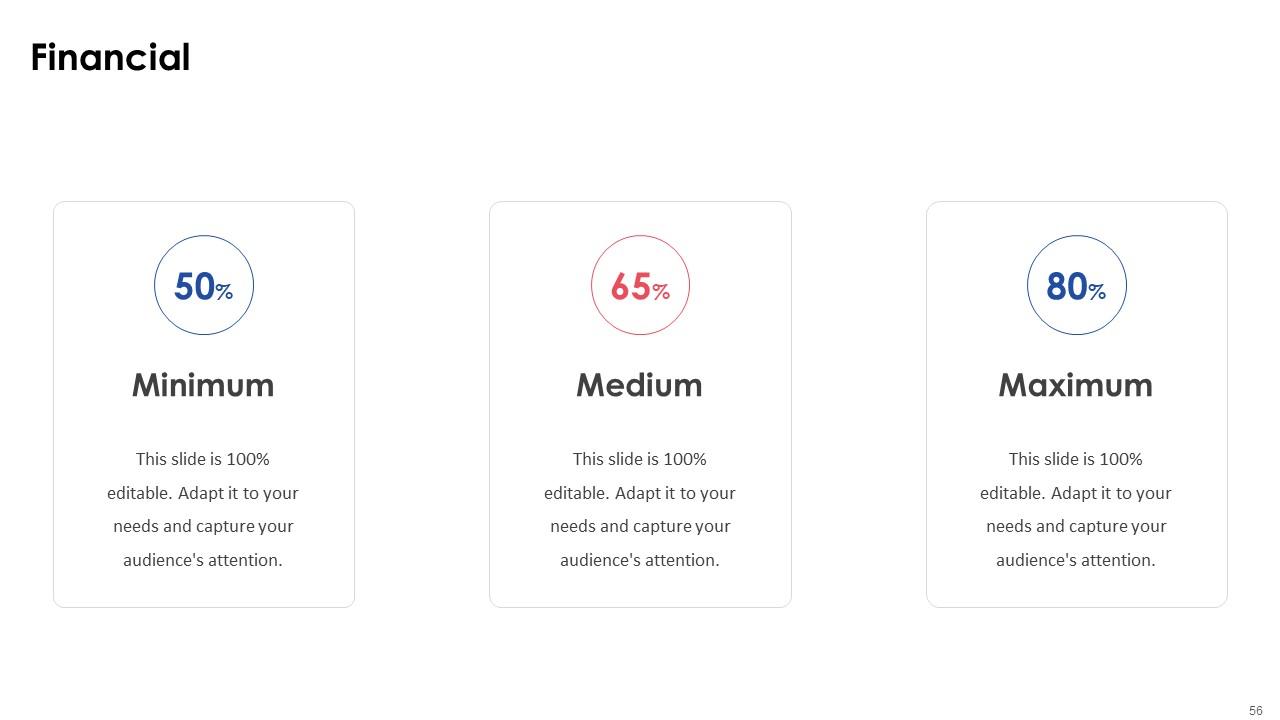
Slide 56: This slide is a financial slide. Show your finance-related stuff here.
Slide 57: This slide is a thank-you slide with address, contact numbers, and email address.
Implementing Effective Tokenization Strategies Powerpoint Presentation Slides with all 66 slides:
Use our Implementing Effective Tokenization Strategies Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
This visual representation is stunning and easy to understand. I like how organized it is and informative it is.
-
I downloaded some of the presentations for work. They were simple to modify and saved me a lot of time and effort.