IoT Security And Privacy Safeguarding The Digital Ecosystem Powerpoint Presentation Slides IoT CD
IoT security refers to the implementation of solutions to alleviate cyber threats and preserve the integrity of IoT devices and networks. This deck IoT Security and Privacy Safeguarding the Digital Ecosystem covers the introduction, key principles, architecture and potential vulnerabilities and explains the need for effective IoT security and data privacy management. It also includes various types of security attacks such as physical, network, encryption and software security. It further addresses concerns related to devices, communication protocol and gateway. Furthermore, This presentation explores mitigation strategies such as best practices, IoT device management process and the relevance of regulatory guidelines. It also covers emerging technologies such as blockchain, AI machine learning and edge computing to enhance IoT security. It also includes case studies to illustrate the practical implications. Download it now.
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this IoT Security And Privacy Safeguarding The Digital Ecosystem Powerpoint Presentation Slides IoT CD is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the seventy six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide showcase the title IoT Security and Privacy Safeguarding the Digital Ecosystem. State Your Company Name.
Slide 2: This slide showcase the title AGENDA.
Slide 3: This slide exhibit Table of Content.
Slide 4: This slide exhibit Table of Content.
Slide 5: This slide exhibit Table of Content: Introduction to IoT security.
Slide 6: This slide presents the benefits of Internet of things devices’ security and data privacy.
Slide 7: This slide presents an overview of IoT security requirements to protect devices and vulnerable networks from unauthorised access or breaches.
Slide 8: This slide highlights security concerns in various areas of internet of things system in order to effectively address and mitigate such risks.
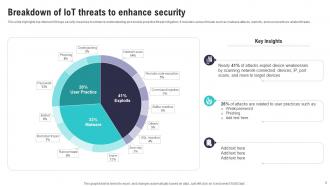
Slide 9: This slide highlights top internet of things security breaches to enhance understanding and enable proactive threat mitigation.
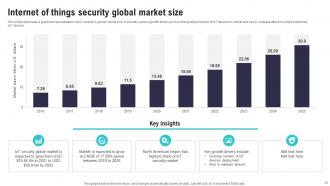
Slide 10: This slide showcases a graphical representation of IoT security’s global market size.
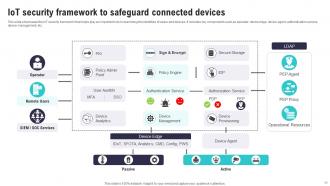
Slide 11: This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices.
Slide 12: This slide exhibit Table of Content: Need for IoT security management
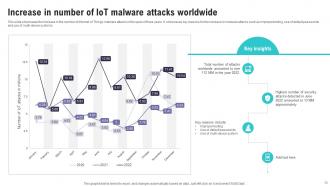
Slide 13: This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years.
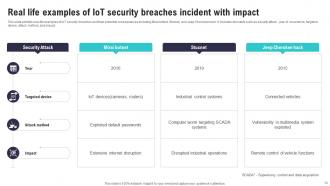
Slide 14: This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack.
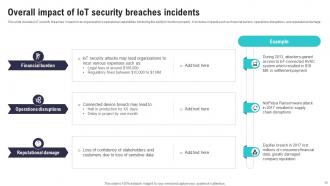
Slide 15: This slide includes IoT security breaches’ impact on an organisation’s operational capabilities, hindering the ability to function properly.
Slide 16: This slide exhibit Table of Content: IoT Security risk and privacy concerns.
Slide 17: This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures.
Slide 18: This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations.
Slide 19: This slide exhibit Table of Content: Types of security attacks in IoT ecosystem.
Slide 20: This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation.
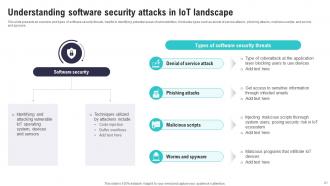
Slide 21: This slide presents an overview and types of software security threats, helpful in identifying potential areas of vulnerabilities.
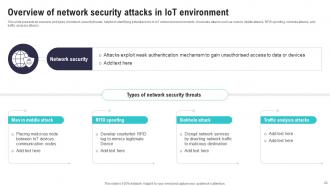
Slide 22: This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments.
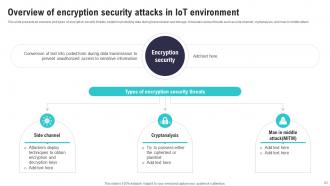
Slide 23: This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage.
Slide 24: This slide showcase table of content that is to be discuss further.
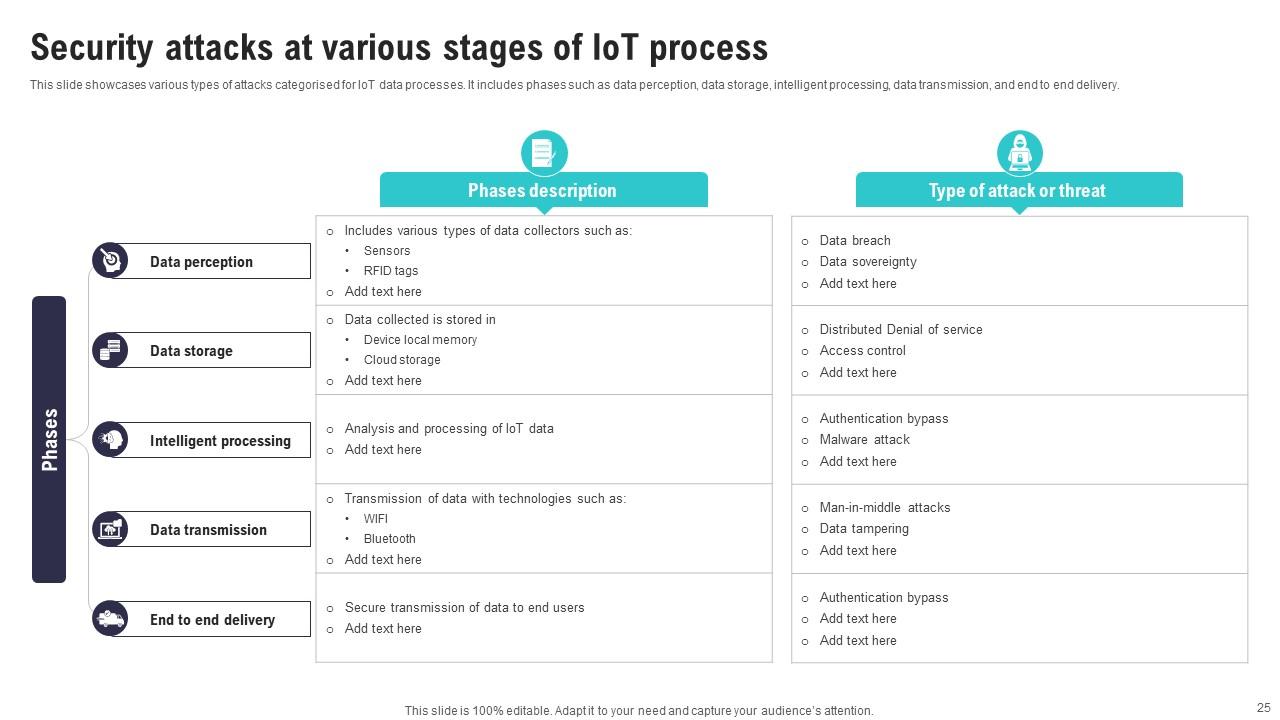
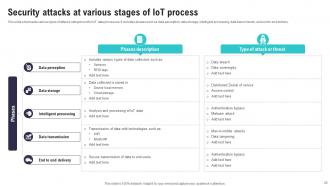
Slide 25: This slide showcases various types of attacks categorised for IoT data processes.
Slide 26: This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework.
Slide 27: This slide showcase table of content that is to be discuss further.
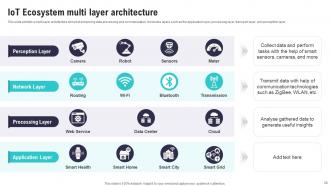
Slide 28: This slide exhibits a multi-layer architecture aimed at enhancing data processing and communication.
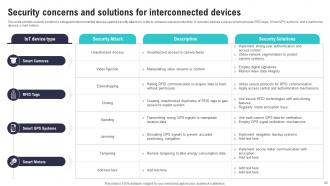
Slide 29: This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity.
Slide 30: This slide outlines key communication protocols that facilitate data exchange within IoT devices.
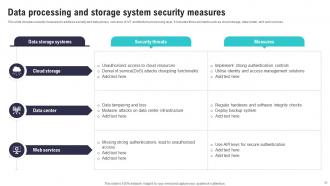
Slide 31: This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer.
Slide 32: This slide exhibits emerging trends in IoT gateway security challenges along with best practices to mitigate such risks effectively.
Slide 33: This slide showcase table of content: IoT ecosystem security concerns.
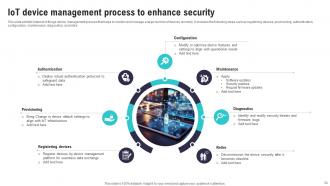
Slide 34: This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely.
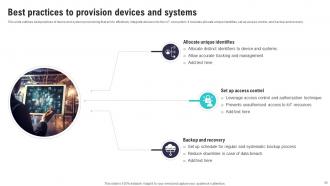
Slide 35: This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem.
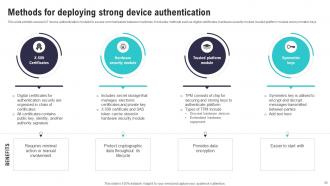
Slide 36: This slide exhibits several IoT device authentication models for secure communication between machines.
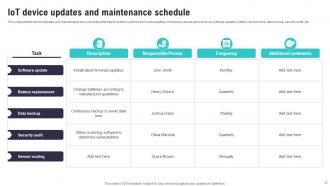
Slide 37: This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities.
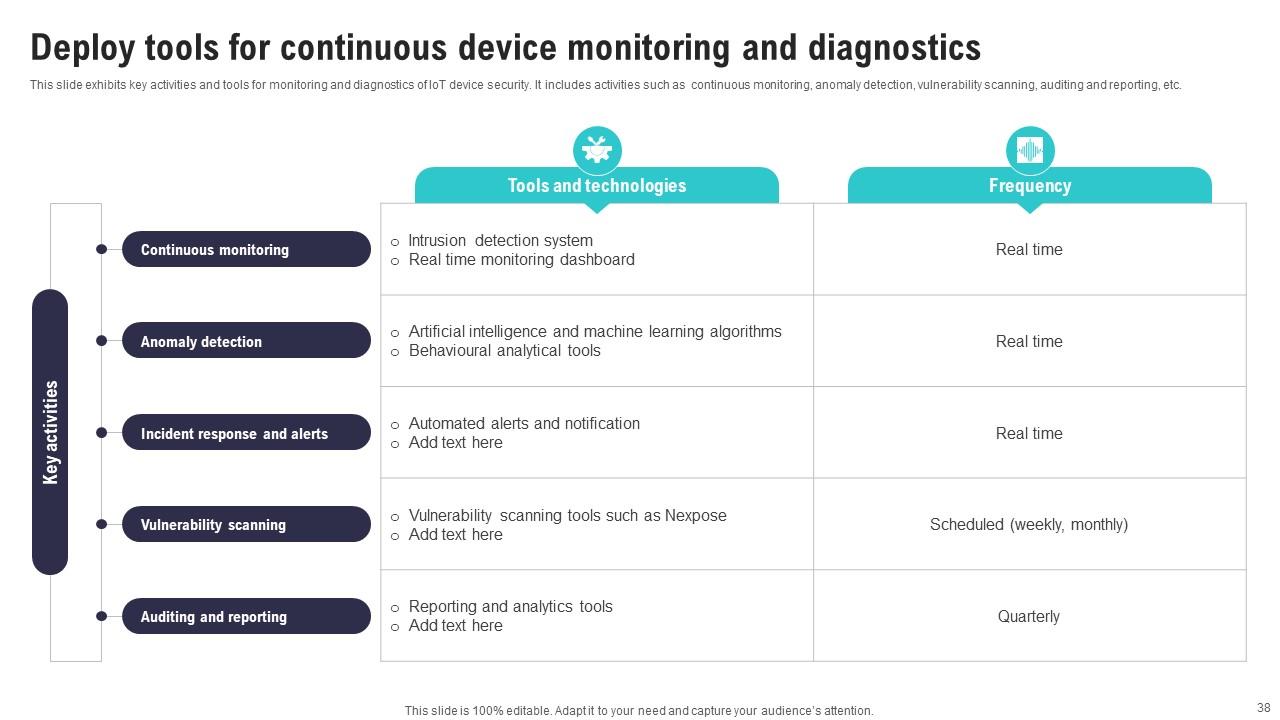
Slide 38: This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security.
Slide 39: This slide showcase table of content: IoT security best practices.
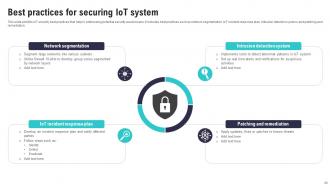
Slide 40: This slide exhibits IoT security best practices that help in addressing potential security weaknesses.
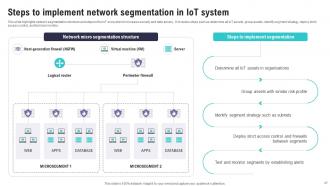
Slide 41: This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy.
Slide 42: This slide contains a checklist that helps organisations to effectively manage and recover from security incidents.
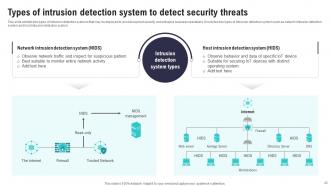
Slide 43: This slide exhibits two types of intrusion detection systems that may be deployed to provide layered security and enhance business operations.
Slide 44: This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies.
Slide 45: This slide showcase table of content: Regulatory guidelines.
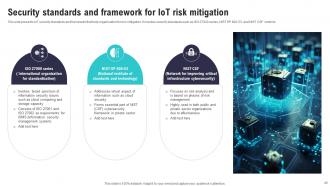
Slide 46: This side presents IoT security standards and framework that help organisation for risk mitigation.
Slide 47: This slide exhibits personal data handling regulations for organisations across various regions.
Slide 48: This slide showcase table of content: IoT security tools and platforms
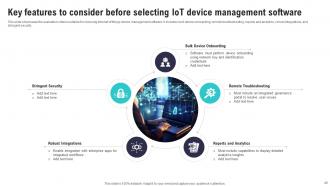
Slide 49: This slide showcases the evaluation criteria suitable for choosing internet of things device management software.
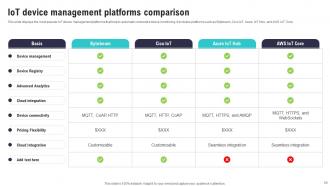
Slide 50: This slide displays the most popular IoT device management platforms that help to automate connected device monitoring.
Slide 51: This slide showcase table of content: Emerging technologies.
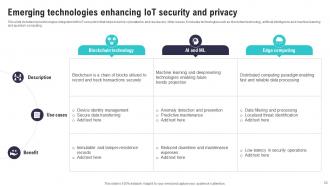
Slide 52: This slide includes key technologies integrated with IoT ecosystem that helps to tackle cyberattacks and resolve any other issues.
Slide 53: This slide showcase table of content: Blockchain.
Slide 54: This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security.
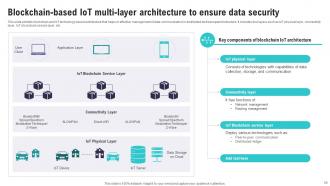
Slide 55: This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure.
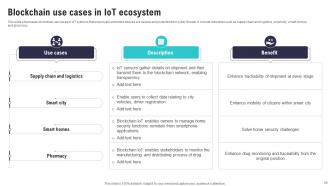
Slide 56: This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats.
Slide 57: This slide showcase table of content: AI and machine learning.
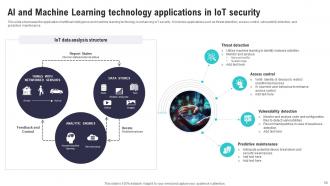
Slide 58: This slide showcases the application of artificial intelligence and machine learning technology in enhancing IoT security.
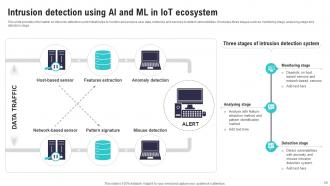
Slide 59: This slide provides information on intrusion detection system that helps to monitor and analyse user data, networks and services to detect vulnerabilities.
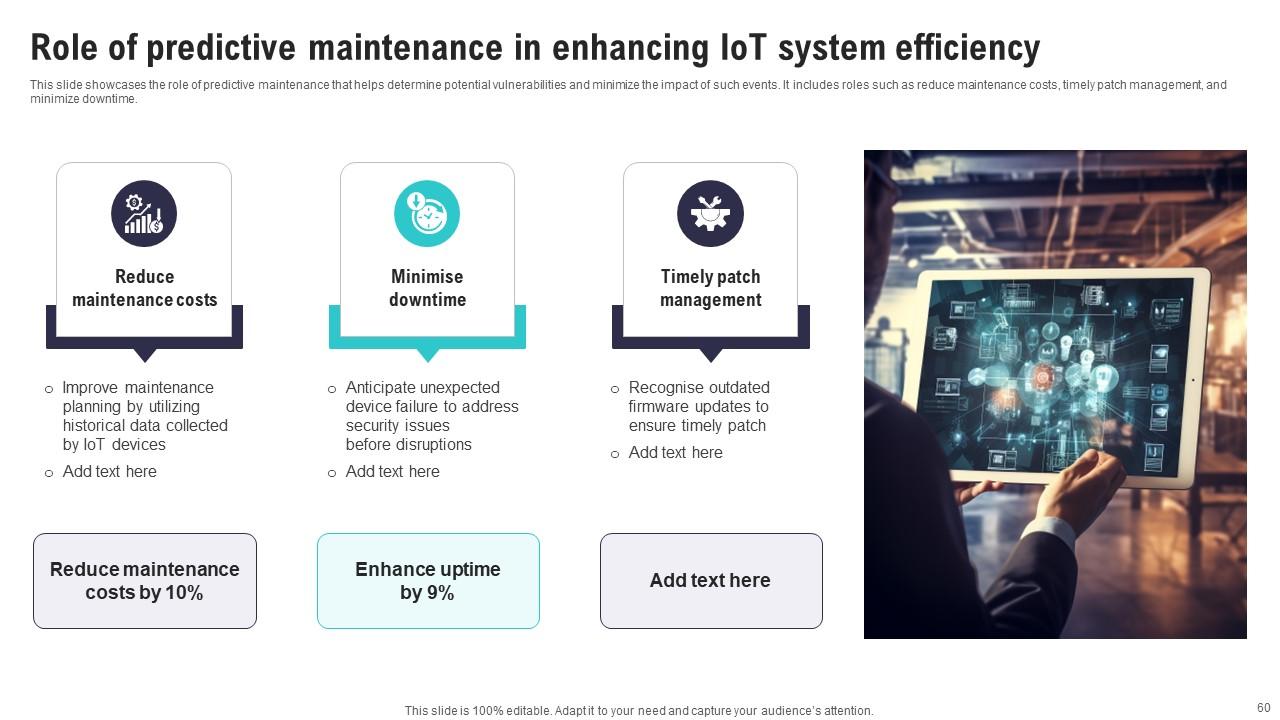
Slide 60: This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events.
Slide 61: This slide showcase table of content: Edge computing.
Slide 62: This slide showcases the significant role of edge computing in enhancing IoT data security and privacy.
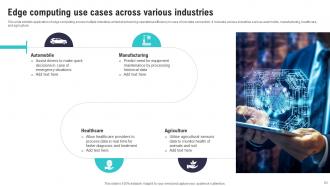
Slide 63: This slide exhibits application of edge computing across multiple industries aimed at enhancing operational efficiency in case of lost data connection.
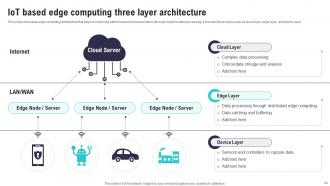
Slide 64: This slide showcases edge computing architecture that helps in improving performance and reduce latency through real time data processing.
Slide 65: This slide showcase table of content: Case study.
Slide 66: This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale.
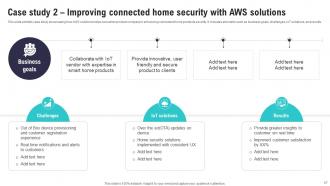
Slide 67: This slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security.
Slide 68: This slide shows all the icons included in the presentation.
Slide 69: This slide is titled as Additional Slides for moving forward.
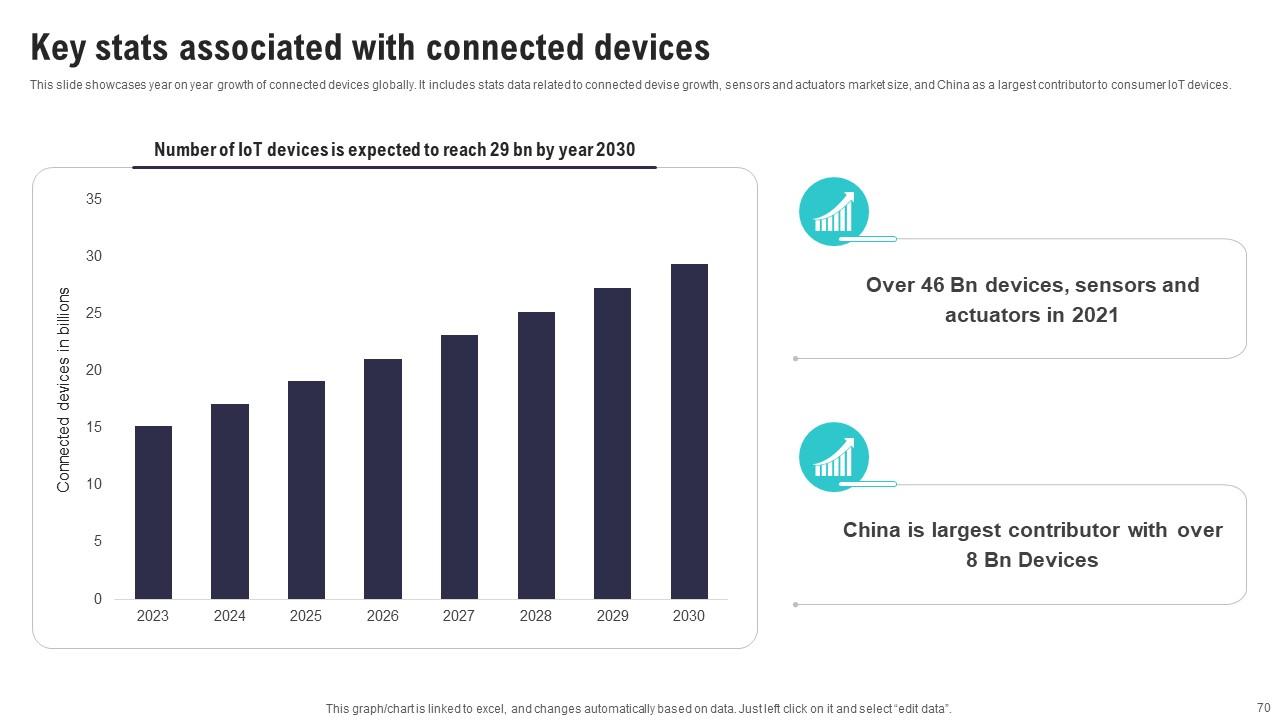
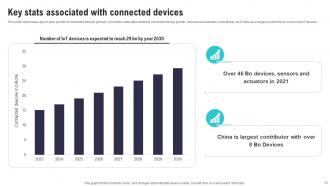
Slide 70: This slide showcases year on year growth of connected devices globally.
Slide 71: This slide showcase Venn diagram.
Slide 72: This is a Timeline slide. Show data related to time intervals here.
Slide 73: This slide contains Puzzle with related icons and text.
Slide 74: This slide displays Mind Map with related imagery.
Slide 75: This is Our Goal slide. State your firm's goals here.
Slide 76: This is a Thank You slide with address, contact numbers and email address.
IoT Security And Privacy Safeguarding The Digital Ecosystem Powerpoint Presentation Slides IoT CD with all 85 slides:
Use our IoT Security And Privacy Safeguarding The Digital Ecosystem Powerpoint Presentation Slides IoT CD to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
The best collection of PPT templates!! Totally worth the money.
-
Best Representation of topics, really appreciable.