Malware Attack In Cyber Security Training Ppt
This set of PPT slides covers malware attacks in cybersecurity. It explains how these affect the system and how they are carried out popularly using emails. Further, it covers types such as viruses, adware, rootkits, spyware, ransomware, trojan horses, and more.
This set of PPT slides covers malware attacks in cybersecurity. It explains how these affect the system and how they are ca..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Malware Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 2
This slide introduces malware. Malware is any software intentionally created to disrupt a computer, server, client, or computer network, etc.
Slide 3
This slide tells us how malware is harmful to your devices. Malware can infect devices and networks and is designed with the intention of harming these networks, devices, and/or their users.
Slide 4
This slide gives information on how malwares are spread. Threat actors use physical and virtual means to spread malware that infects networks and devices.
Slide 5
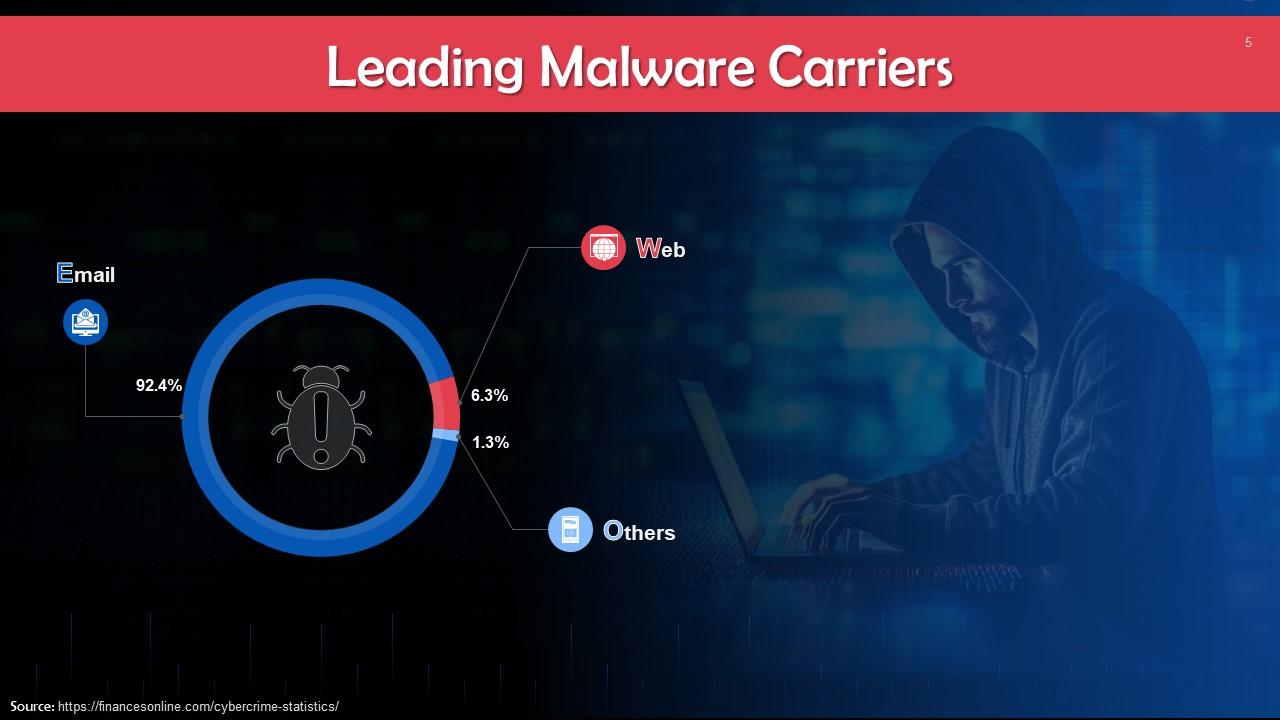
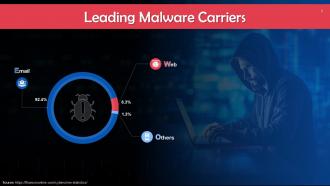
This slide depicts leading malware carriers. Emails account for the majority (about 92%) of the spread of malwares.
Slide 6
This slide highlights types of malware. These are viruses, adware, rootkit, spyware, ransomware, etc.
Instructor’s Notes:
- Virus: A virus is the most prevalent form of malware that executes itself and spreads by infecting other files or programs
- Adware: Adware keeps track of a user's download history and browsing habits, intending to display pop-up or banner ads that tempt the users to make a purchase. For instance, an advertiser may use cookies to track the web pages a user visits to target advertising
- Rootkit: A rootkit gains system administrator privileges for the victim's system. After it is installed, the program provides threat actors the root or privileged access to the user's system
- Spyware: Spyware gathers information and data about the device and user and observes the user's activity without their knowledge
- Ransomware: When ransomware infects a user's system, it encrypts its data. The victim is then told to pay a ransom to the cybercriminals to have the data on the system decrypted
- Trojan Horse: A Trojan Horse is made to seem like a legitimate software program so as to gain access to a system. Trojans can execute malicious functions once activated following installation
- Remote Access: Remote Access Trojan (RAT), or a backdoor virus, discreetly creates a backdoor into an infected computer system that allows threat actors to access it remotely without warning the user or the system's security programs
- Worm: A worm is able to self-replicate without a host program and spreads without interacting with the malware authors
- Keylogger: Keyloggers, or system monitors, track almost everything a user does on their computer, including emails, opened web pages, programs, and keystrokes
Slide 7
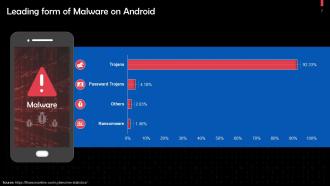
This slide depicts leading types of malware infecting android. The most common type are trojans that account for about 92% of the attacks or infections.
Slide 8
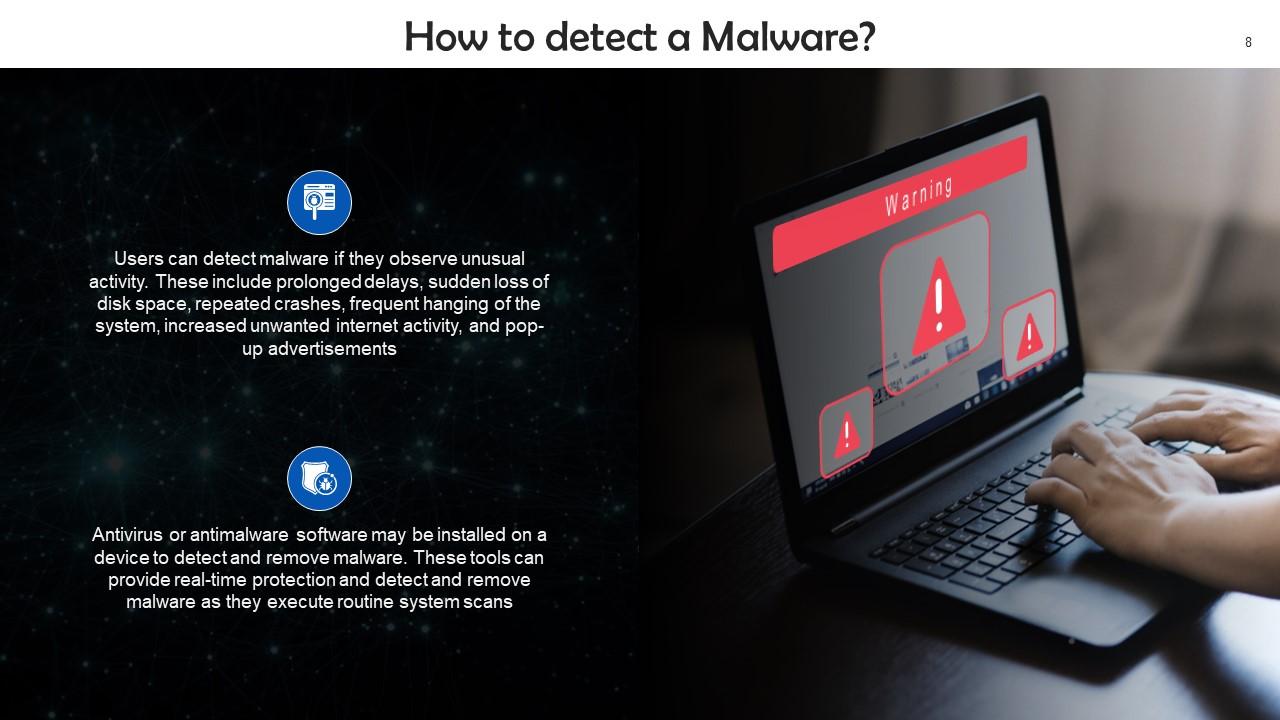
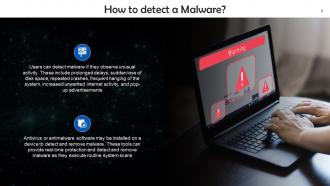
This slide gives information about how to detect a malware. Users can detect malware if they observe unusual activity, such as prolonged delays, sudden loss of disk space, repeated crashes, frequent hanging of the system, increased unwanted internet activity, and pop-up advertisements
Slide 9
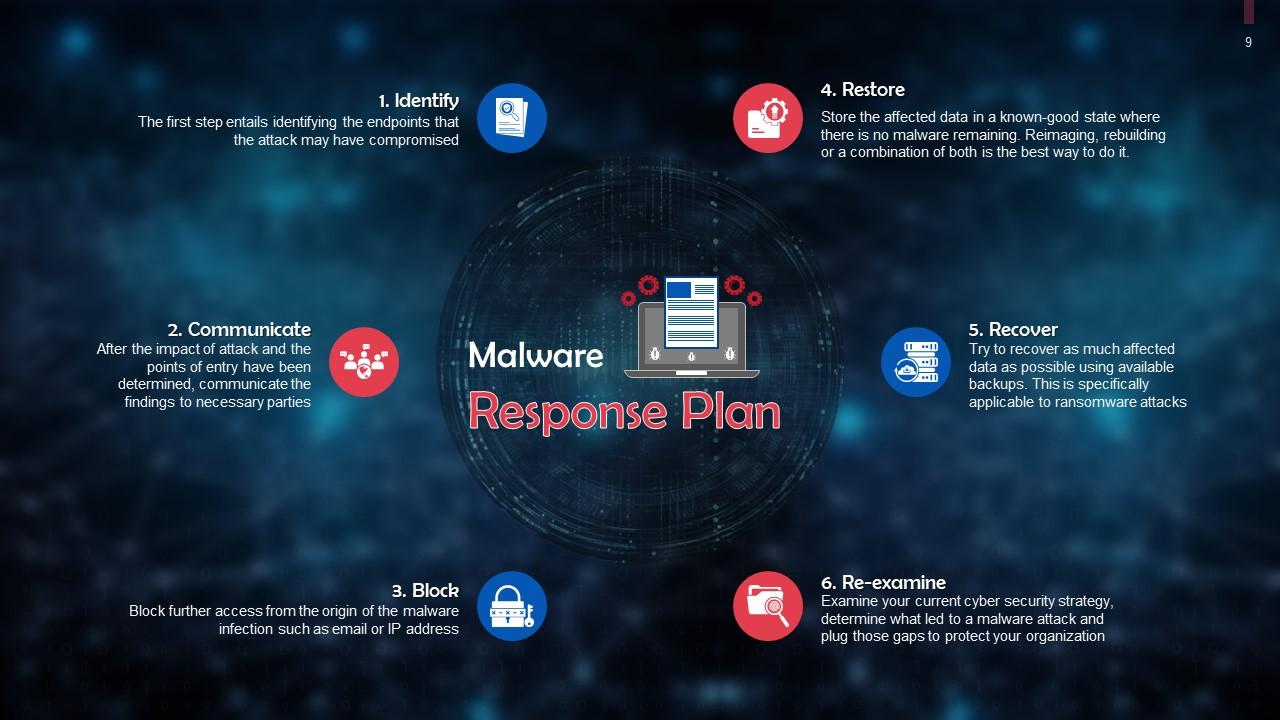
This slide highlights a six-step response plan for malwares. These steps are: Identify, communicate, block, restore, recover, and re-examine.
Slide 10
This slide tells us ways to remove a malware. Many security software products are designed to detect, prevent and remove malware from infected systems.
Slide 11
This slide talks about the ways to prevent a malware infection. Companies should implement dual approval for business-to-business (B2B) transactions and second-channel verification for business-to-consumer (B2C) transactions.
Slide 12
This slide discusses malware infections on mobile devices. Malware can infect mobile phones and provide access to a device's components, such as the microphone, camera, GPS, etc.
Malware Attack In Cyber Security Training Ppt with all 32 slides:
Use our Malware Attack In Cyber Security Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Very well designed and informative templates.
-
Fantastic collection. Loved how we can personalize these templates as per the requirements.