Man In The Middle Attack In Cyber Security Training Ppt
This set of PPT slides in depth covers Man-in-the-Middle Attack in Cyber Security. It covers its types, such as IP Spoofing, HTTP spoofing, SSL hijacking, session hijacking, cache poisoning, and Wi-Fi eavesdropping, and tips to prevent such attacks.
This set of PPT slides in depth covers Man-in-the-Middle Attack in Cyber Security. It covers its types, such as IP Spoofing..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Man in the Browser Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 2
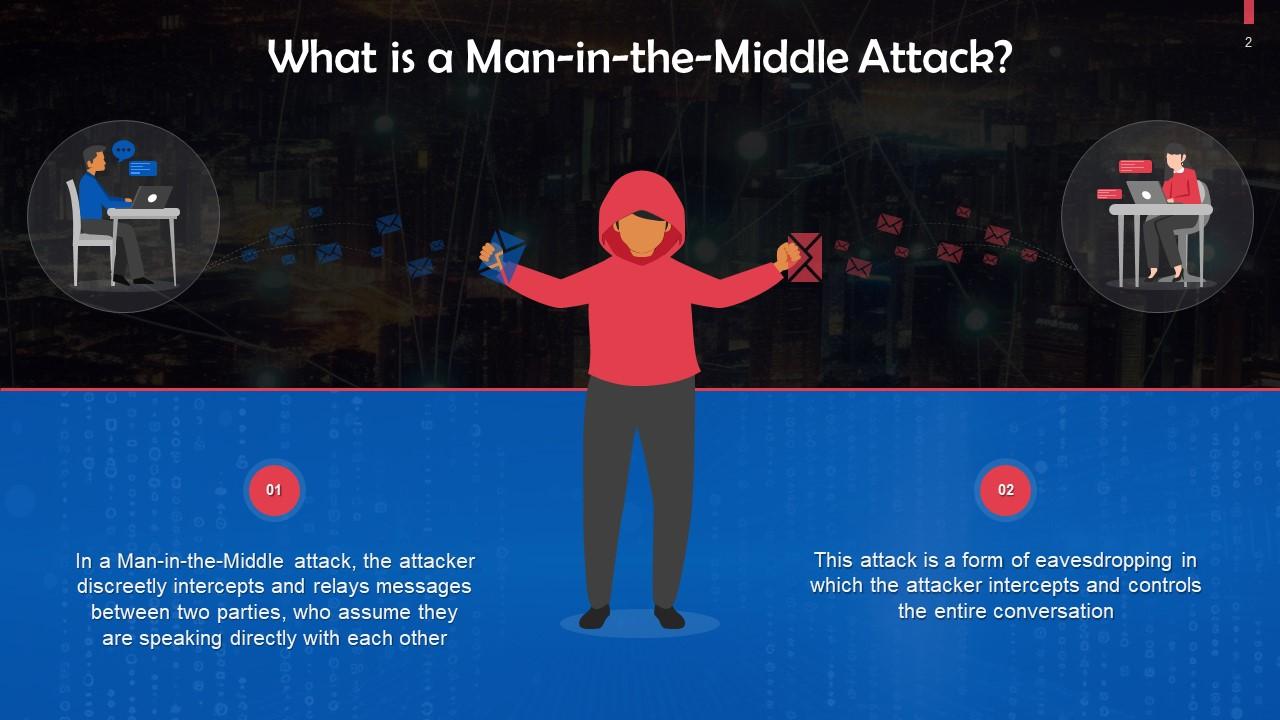
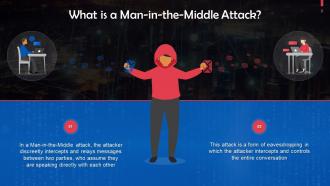
This slide talks about man-in-the-middle attacks. In a Man-in-the-Middle attack, the attacker discreetly intercepts and relays messages between two parties, who assume they are speaking directly with each other.
Slide 3
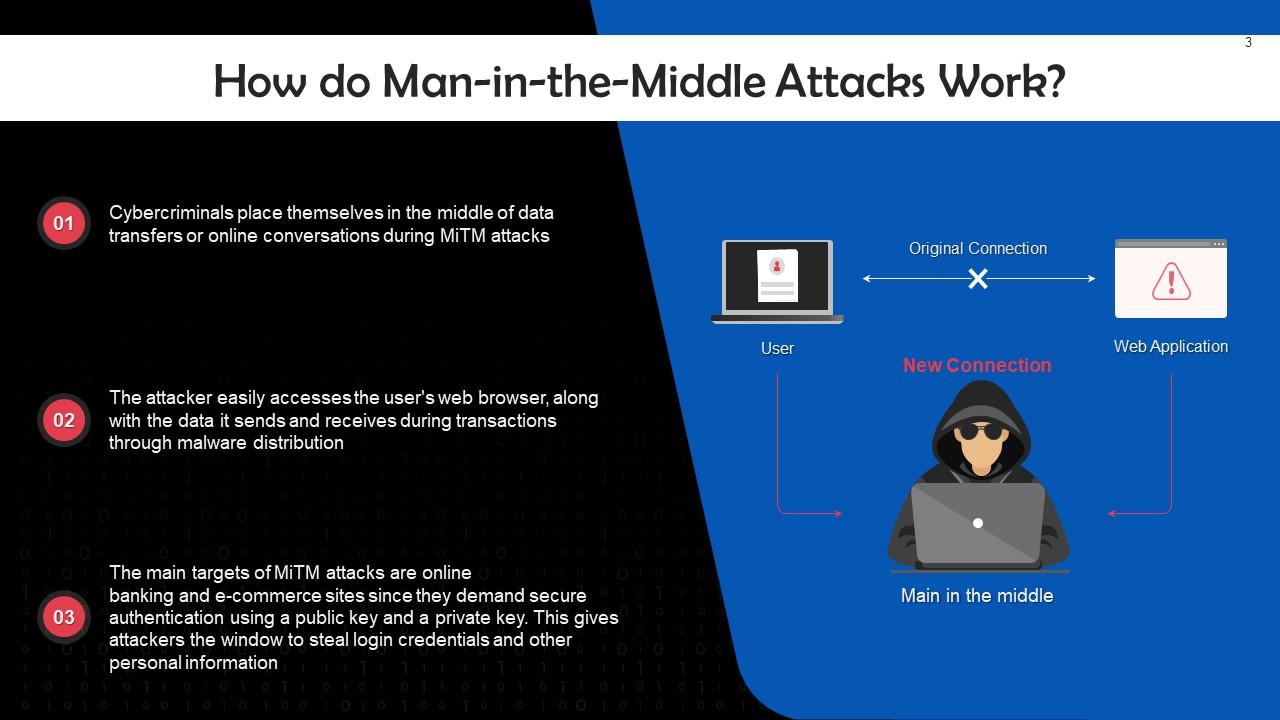
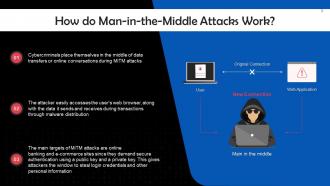
This slide depicts the working of Man-in-the-Middle (MiTM). Cybercriminals place themselves in the middle of data transfers or online conversations during MiTM attacks.
Slide 4
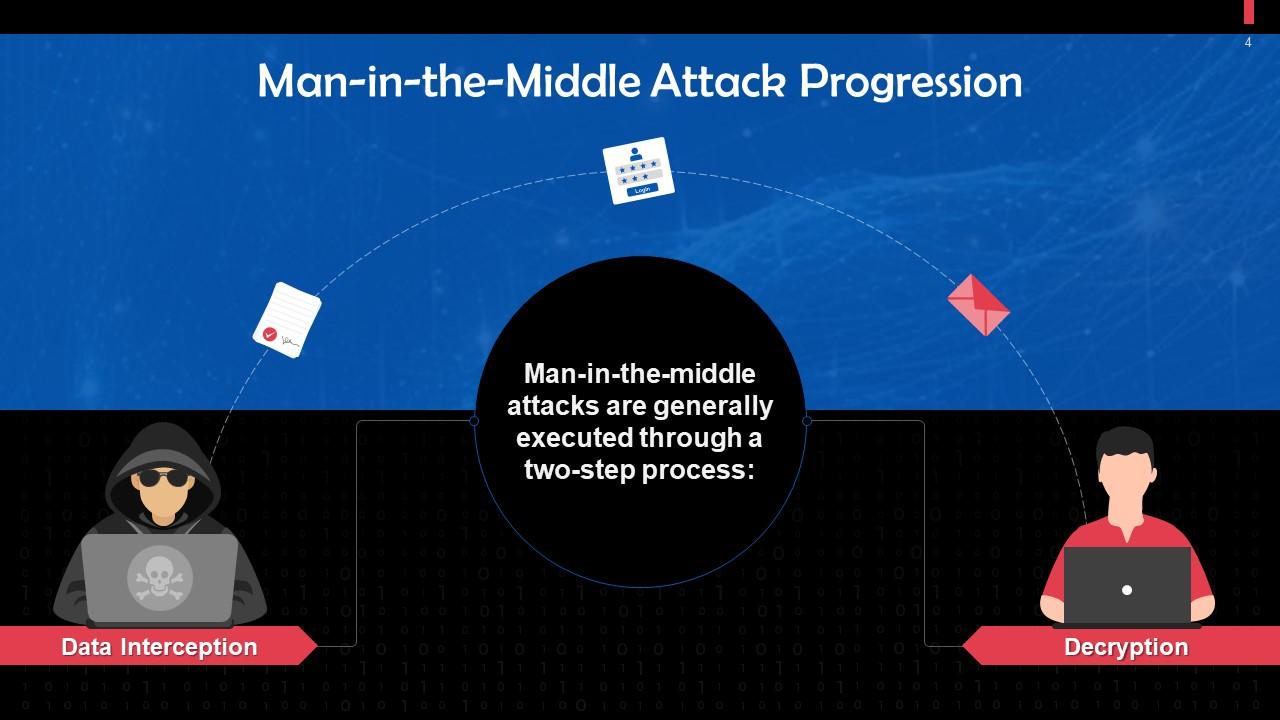
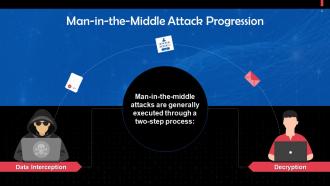
This slide highlights a two-step process of executing a MiTM attack. The steps are data interception and decryption.
Slide 5
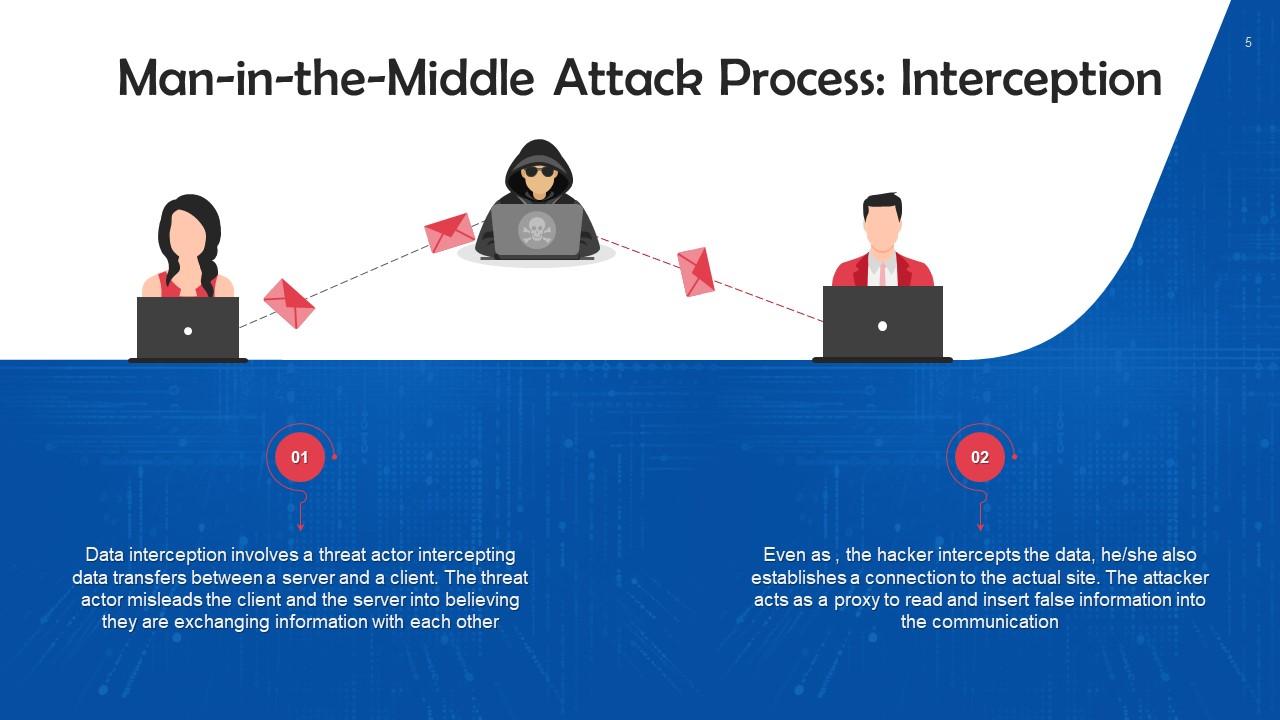
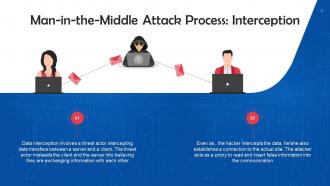
This slide discusses the first step, i.e. Interception, for executing MiTM attacks. Data interception involves a threat actor intercepting data transfers between a server and a client. The threat actor misleads the client and the server into believing they are exchanging information with each other.
Slide 6
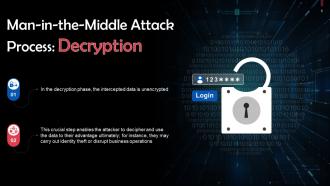
This slide discusses the second step, i.e. decryption, for executing MITM attacks. In the decryption phase, the intercepted data is unencrypted.
Slide 7
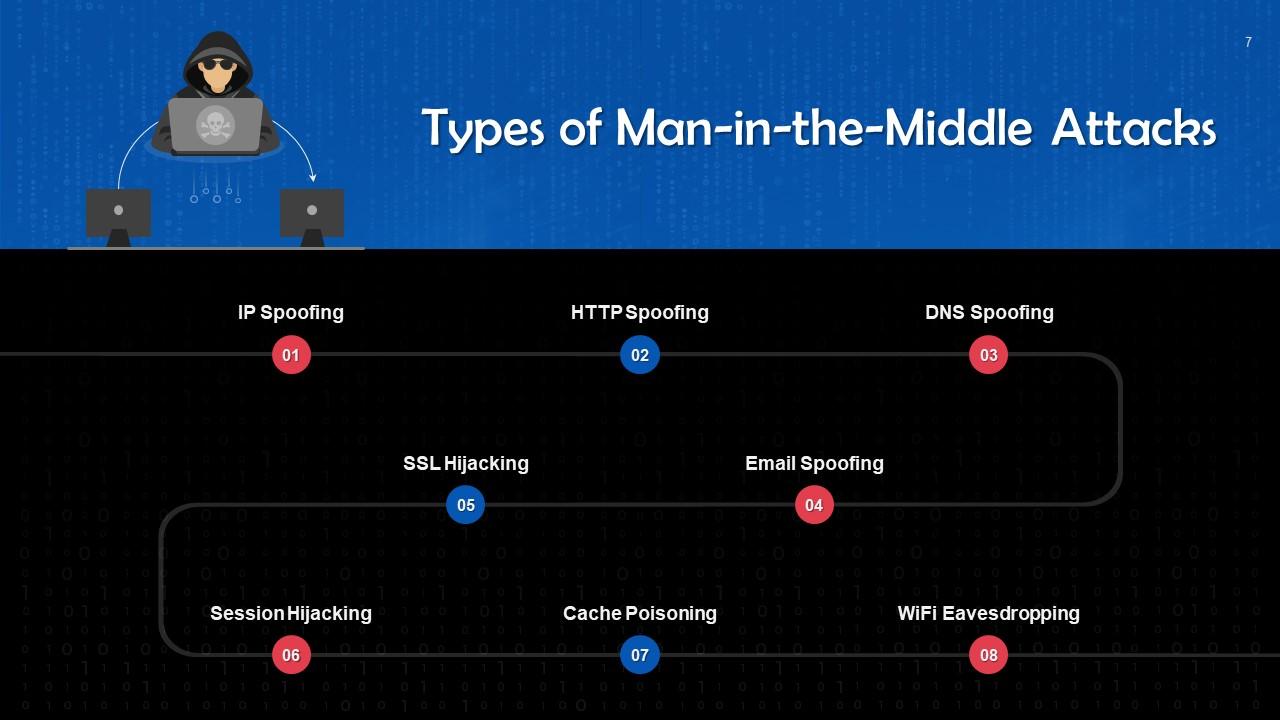
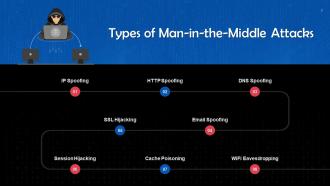
This slide depicts the working of man-in-the-middle attacks. These are: IP Spoofing, HTTP spoofing, DNS spoofing, email spoofing, SSL hijacking, session hijacking, cache poisoning, and WiFi eavesdropping.
Slide 8
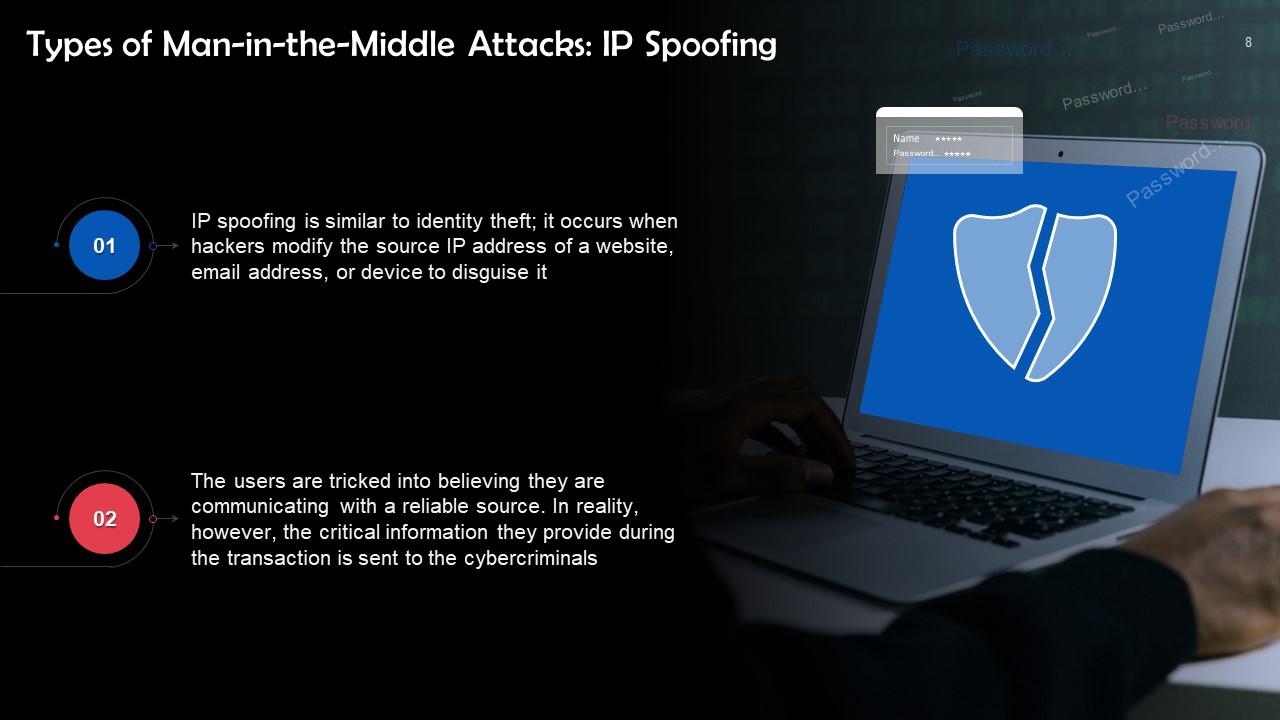
This slide talks about IP Spoofing. IP spoofing is similar to identity theft; it occurs when hackers modify the source IP address of a website, email address, or device to disguise it.
Slide 9
This slide discusses HTTP Spoofing. It involves redirecting a browser session to an unsecured or HTTP-based web page without the user's knowledge or consent. This also easy stealing of sensitive information to cybercriminals.
Slide 10
This slide talks about DNS Spoofing. Cybercriminals change domain names in this man-in-the-middle attack to divert traffic to fake websites.
Slide 11
This slide discusses Email Spoofing. This type of MiTM attack allows cybercriminals to take over the email accounts of banks and other financial organizations and track all user transactions.
Slide 12
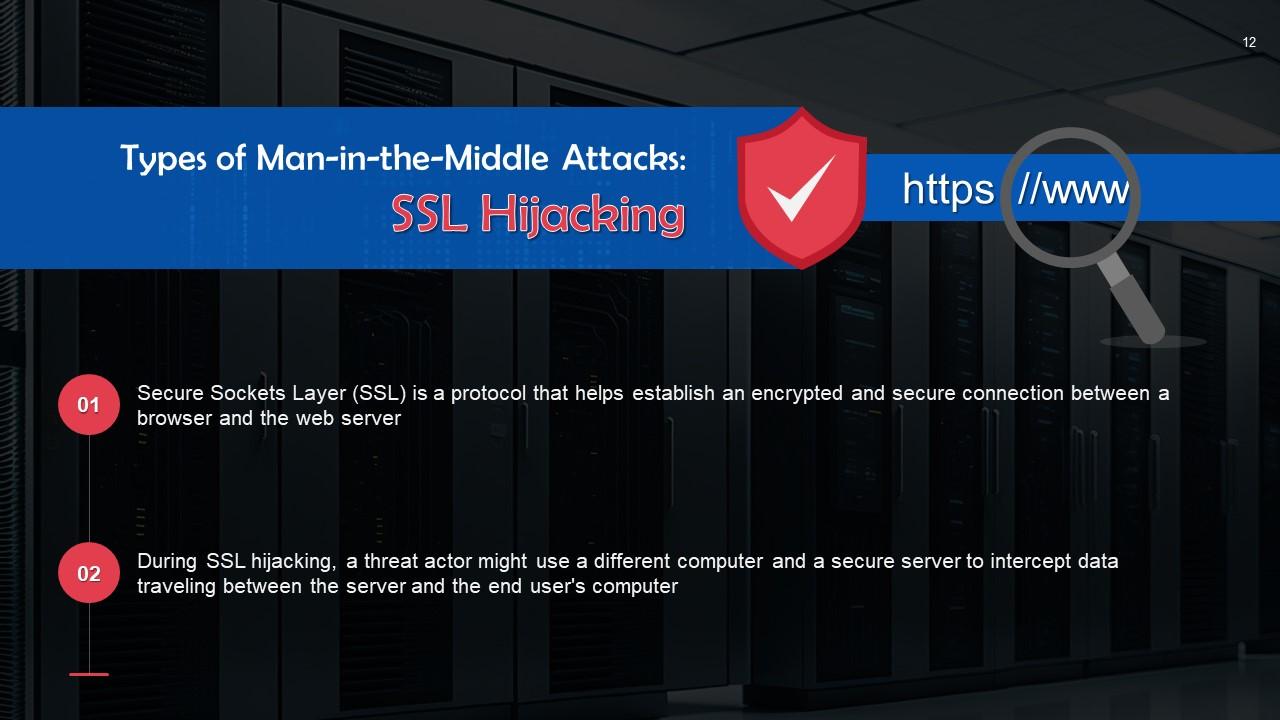
This slide talks about SSL (Secure Sockets Layer) Hijacking. SSL is a protocol that helps establish an encrypted and secure connection between a browser and the web server.
Slide 13
This slide discusses Session Hijacking. Session hijacking, or stealing browser cookies, is a malicious practice that takes place when hackers steal personal information and passwords stored in the cookies of a user's browsing session.
Slide 14
This slide talks about Cache Poisoning. It enables threat actors on the same subnet as the victims’ to eavesdrop on traffic being routed between them.
Slide 15
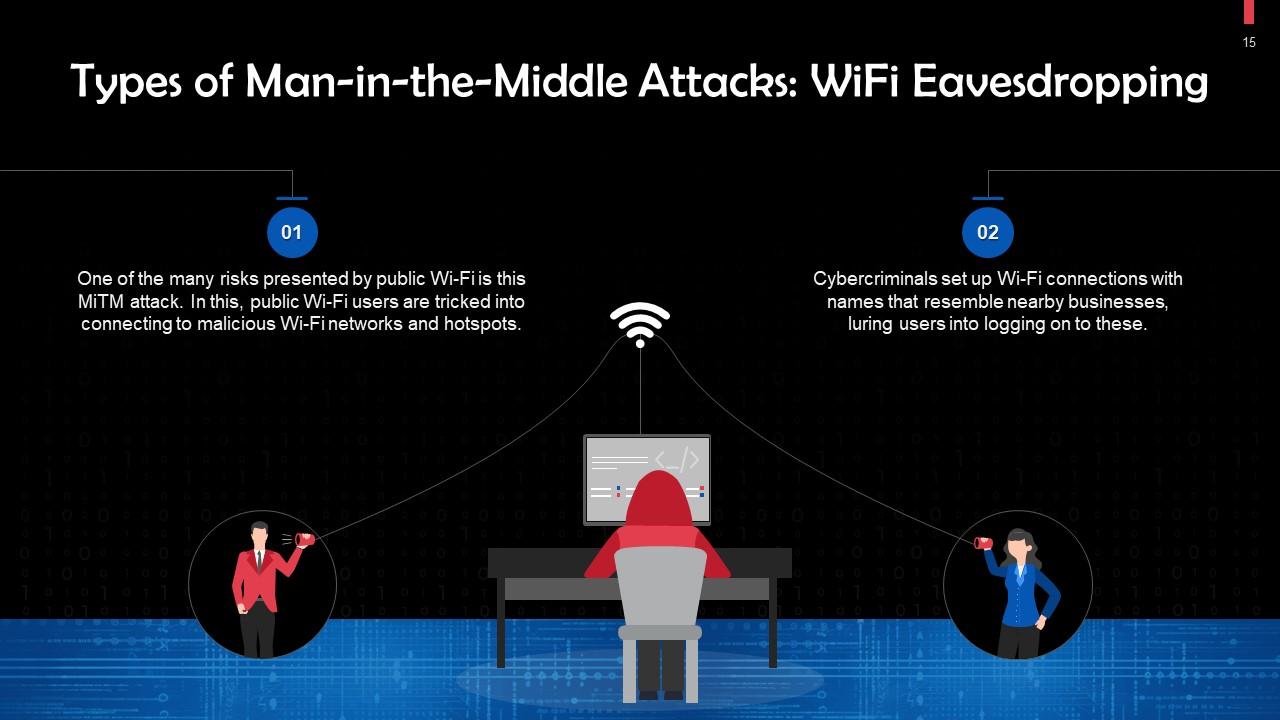
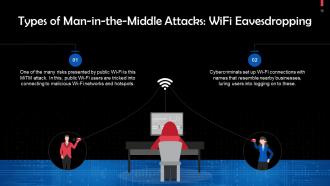
This slide discusses WiFi Eavesdropping. During this attack, public Wi-Fi users are tricked into connecting to malicious Wi-Fi networks and hotspots.
Slide 16
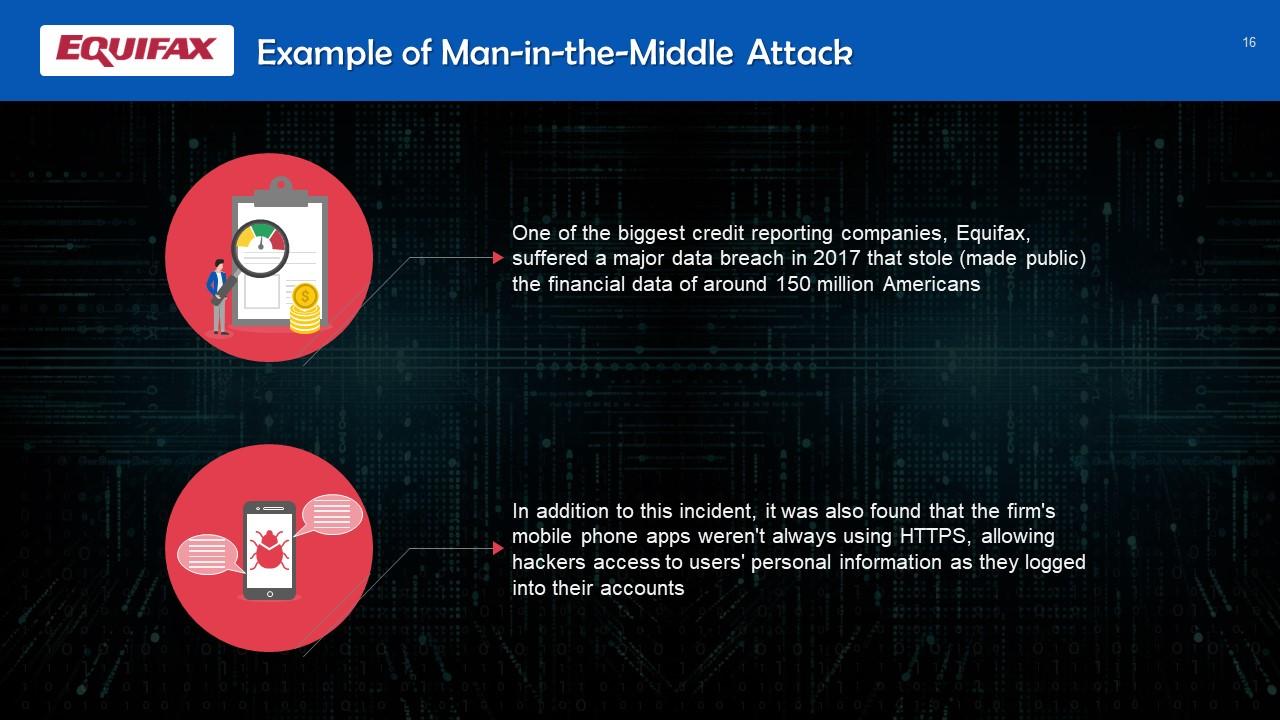
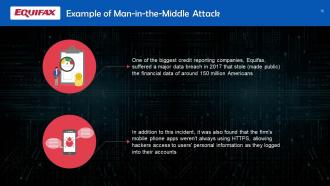
This slide depicts an example of a man-in-the-middle attack. One of the biggest credit reporting companies, Equifax, suffered a major data breach in 2017 that revealed the financial data of around 150 million Americans.
Slide 17
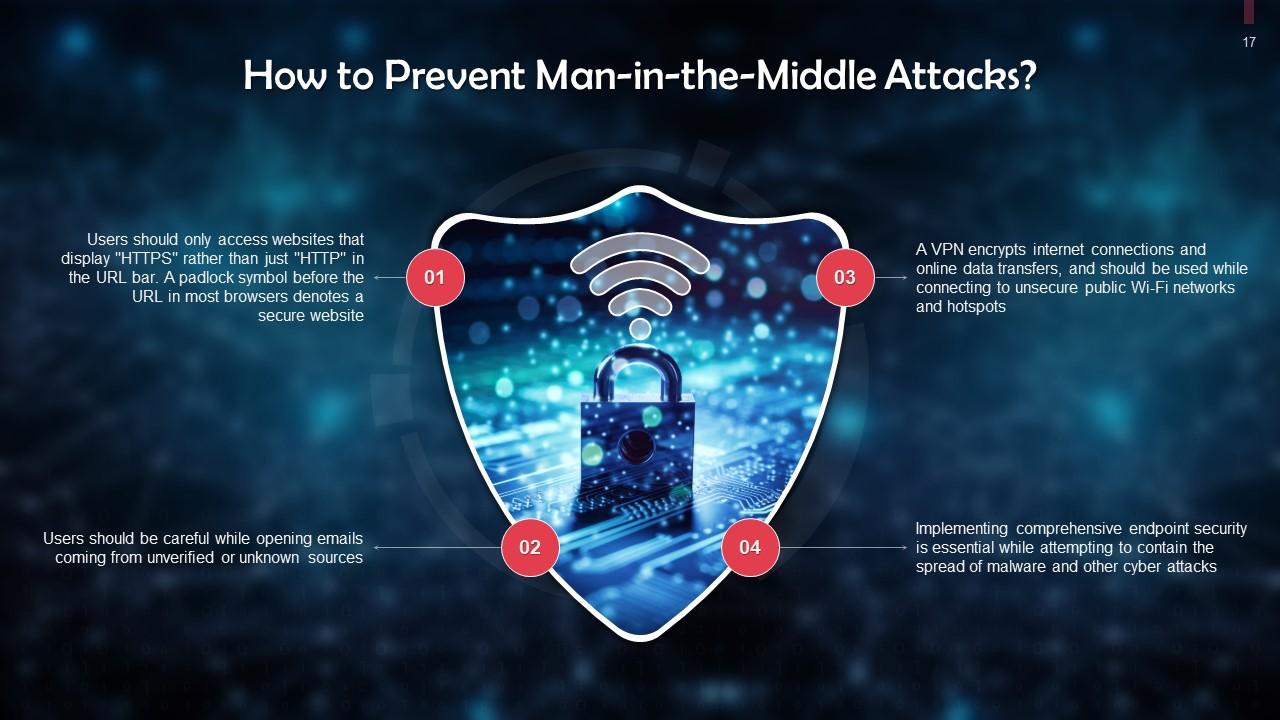
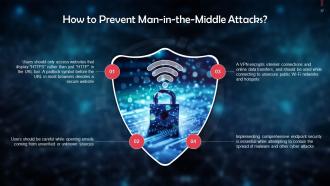
This slide gives information about the prevention of man-in-the-attacks. Users should visit secure websites that display “HTTPS” in the URL bar or a padlock symbol before the URL. A VPN should be used while connecting to public WiFi networks and hotspots.
Man In The Middle Attack In Cyber Security Training Ppt with all 37 slides:
Use our Man In The Middle Attack In Cyber Security Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Easily Editable.
-
The best collection of PPT templates!! Totally worth the money.