Overview Of Active And Passive Attacks In Cybersecurity Training PPT
This set of slides covers active and passive attacks in cybersecurity in detail. An active attack entails intercepting a communication or message and modifying it for malicious effect. A passive attack involves a hacker monitoring a system and illicitly copying data without changing it.
This set of slides covers active and passive attacks in cybersecurity in detail. An active attack entails intercepting a co..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Active and Passive Attacks in Cybersecurity. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 2
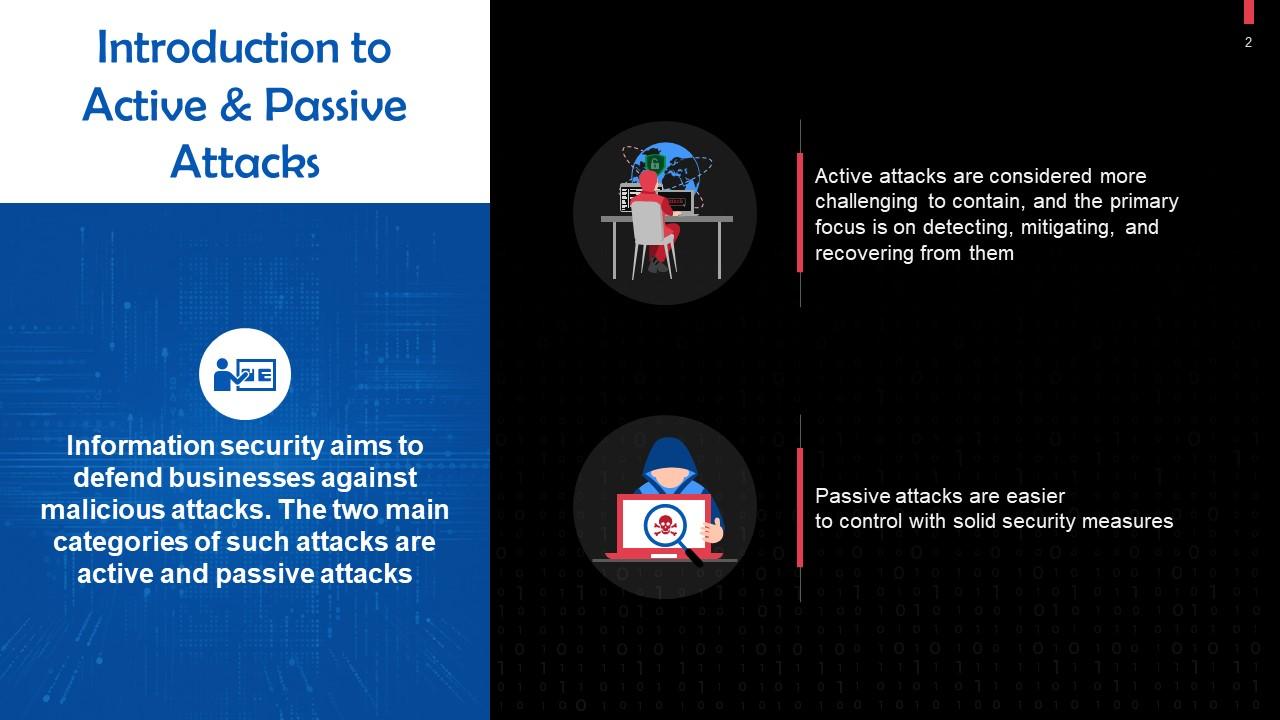
This slide introduces the concept of active and passive attacks in Information Security. Information security aims to defend businesses against malicious attacks. The two main categories of such attacks are active and passive attacks.
Slide 3
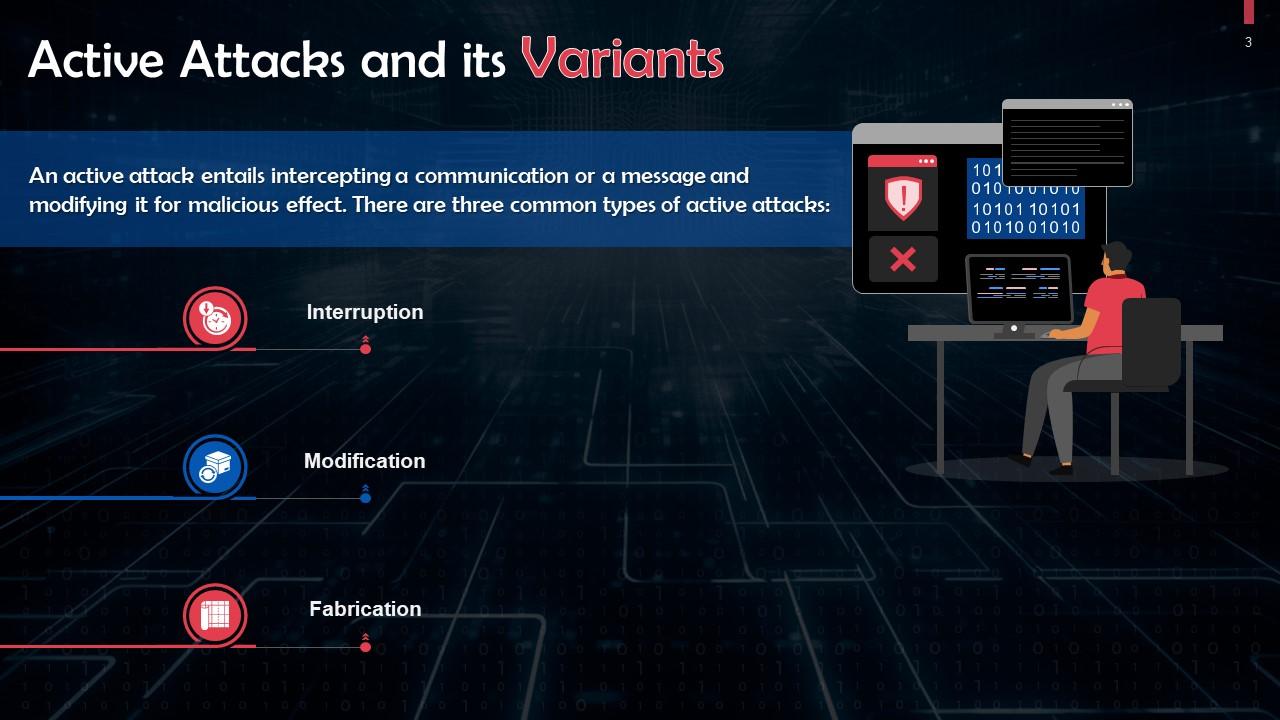
This slide provides information on active attacks and its variants. There are three common types of active attack. These are interruption, modification, and fabrication.
Instructor’s Notes:
- Interruption: The attacker interrupts the original communication and creates new, malicious messages, posing as one of the communicating parties
- Modification: The attacker uses existing communications and replays them to deceive one of the communicating parties or modifies the communication to gain an advantage
- Fabrication: Creates fake or synthetic communications, typically to achieve Denial of Service (DoS). This prevents users from accessing systems or performing routine operations
Slide 4
This slide gives us information about passive attacks. A passive attack involves a hacker monitoring a system and illicitly copying data without changing it. They then employ this information to breach target systems or disrupt networks.
Slide 5
This slide tabulates differences between active and passive attacks.
Overview Of Active And Passive Attacks In Cybersecurity Training PPT with all 25 slides:
Use our Overview Of Active And Passive Attacks In Cybersecurity Training PPT to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Attractive design and informative presentation.
-
I have just started downloading templates for my presentations and I must say this is a great design. It helped accelerate my presentation design process and made it more visually appealing.