Phishing Attack Types In Cyber Attack Training Ppt
This set of PPT slides in detail covers the types of phishing attacks which are spear, whaling, vishing, smishing, email, and search engine phishing.
This set of PPT slides in detail covers the types of phishing attacks which are spear, whaling, vishing, smishing, email, a..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Phishing Attack Types in Cyber Attack. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 2
This slide lists types of phishing attacks. These are spear phishing, whaling, vishing, smishing, email phishing, and search engine phishing.
Slide 3
This slide talks about spear phishing. Spear phishing seeks to gain illegal access to confidential data by targeting specific organizations or individuals.
Slide 4
This slide gives information about whaling. A whaling phishing attack targets CEOs or CFOs to steal sensitive information from a company. Many whaling phishing attempts aim to trick the victim into approving high-value wire transfers to the attacker
Slide 5
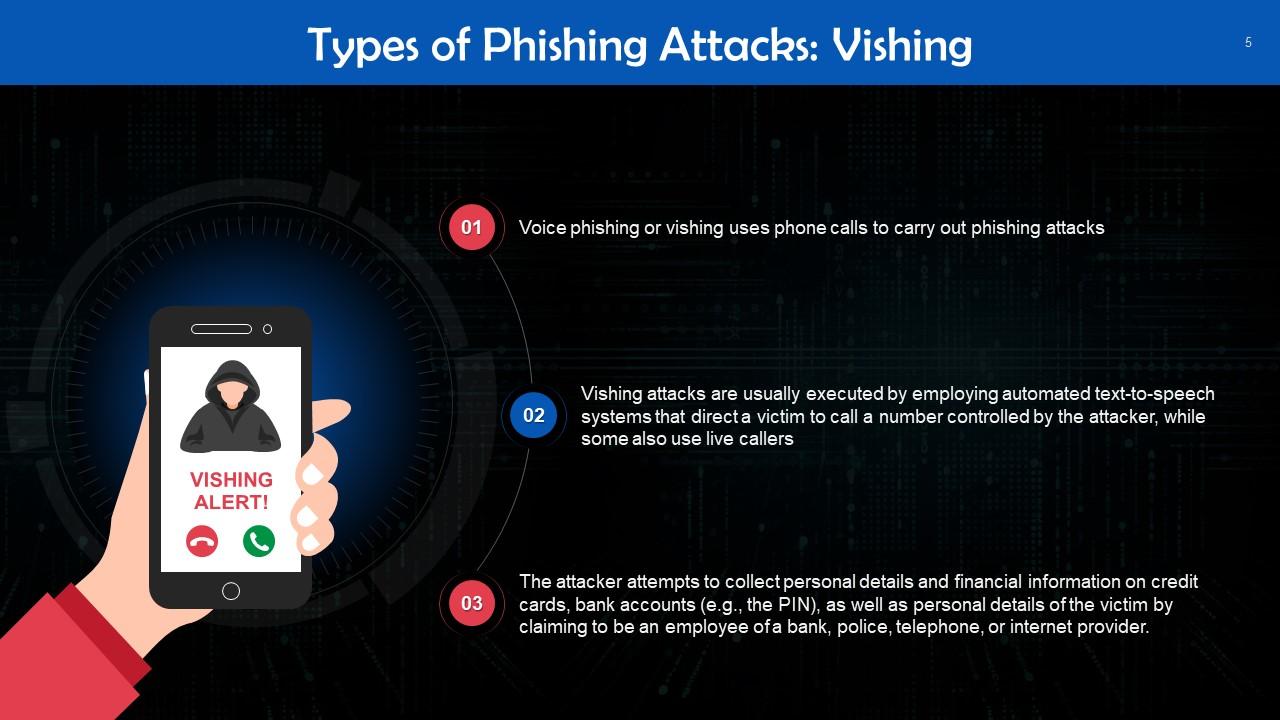
This slide talks about vishing. Voice phishing or vishing uses phone calls to carry out phishing attacks. Vishing attacks are usually conducted using automated text-to-speech systems that direct a victim to call a number that the attacker controls, while some also use live callers.
Slide 6
This slide talks about smishing. Smishing uses text messaging or short message service (SMS) to carry out the attack. These messages usually contain clickable links or a return phone number.
Slide 7
This slide cautions against email phishing. Email phishing is the most prevalent form of phishing, where hackers send emails to any email address they can obtain.
Slide 8
This slide talks about search engine phishing. In search engine phishing or SEO poisoning, hackers work to become the top hit on a search engine using Search Engine Optimization.
Phishing Attack Types In Cyber Attack Training Ppt with all 28 slides:
Use our Phishing Attack Types In Cyber Attack Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Loved the collection. Editing the presentation was seamless with their templates.
-
The presentations are very helpful. I am always able to get appropriate templates for the different topics related to my profession.