Social Engineering Attacks Prevention For Businesses Powerpoint Presentation Slides
This social engineering attacks prevention for businesses PPT discusses the signs, goals, methods, and important traits of a social engineering attack. In addition, behavioral exploitation in cyber security PPT demonstrates the components of the social engineering lifecycle, ontological model of social engineering attack, and sciences involved in targeting humans. Furthermore, the social manipulation threats in the cyber security module discusses the several social engineering techniques, such as impersonation, tailgating, baiting, pretexting, scareware, quid pro quo, reverse social engineering, phishing, smishing, dumpster diving etc. Moreover, this social engineering impact mitigation strategies for organizations Outline the types and benefits of different anti-phishing solutions providers and best practices for social engineering awareness campaigns. It represents a training program for organizations to protect their employees from the risk of social engineering scams and phishing attacks. Lastly, this social engineering attacks prevention for businesses deck comprise a checklist, roadmap, 30-60-90 plan, and timeline for implementing different security measures in organizations to stay safe from social engineering attacks. Download our 100 percent editable and customizable template, which is also compatible with Google Slides.
This social engineering attacks prevention for businesses PPT discusses the signs, goals, methods, and important traits of ..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Social Engineering Attacks Prevention For Businesses Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty eight slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Social Engineering Attacks Prevention for Businesses. State your company name and begin.
Slide 2: This is an Agenda slide. State your agendas here.
Slide 3: This slide shows Table of Content for the presentation.
Slide 4: This slide shows title for topics that are to be covered next in the template.
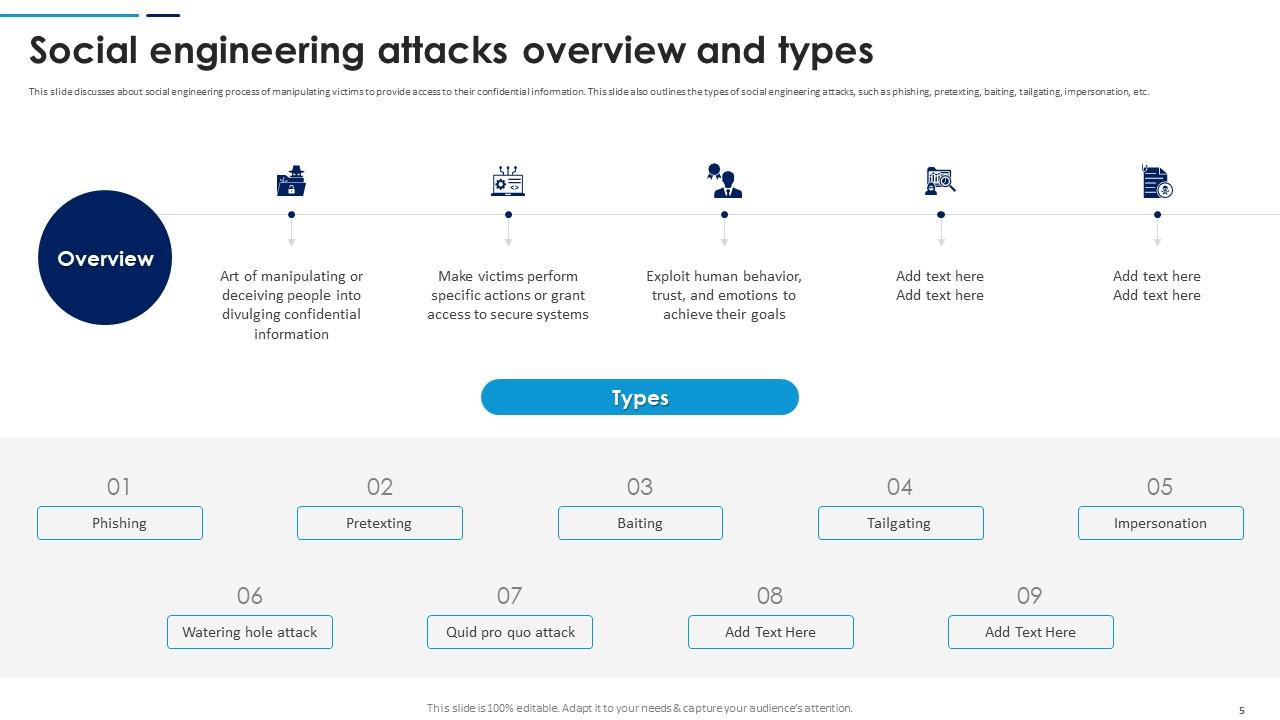
Slide 5: This slide discusses about social engineering process of manipulating victims to provide access to their confidential information.
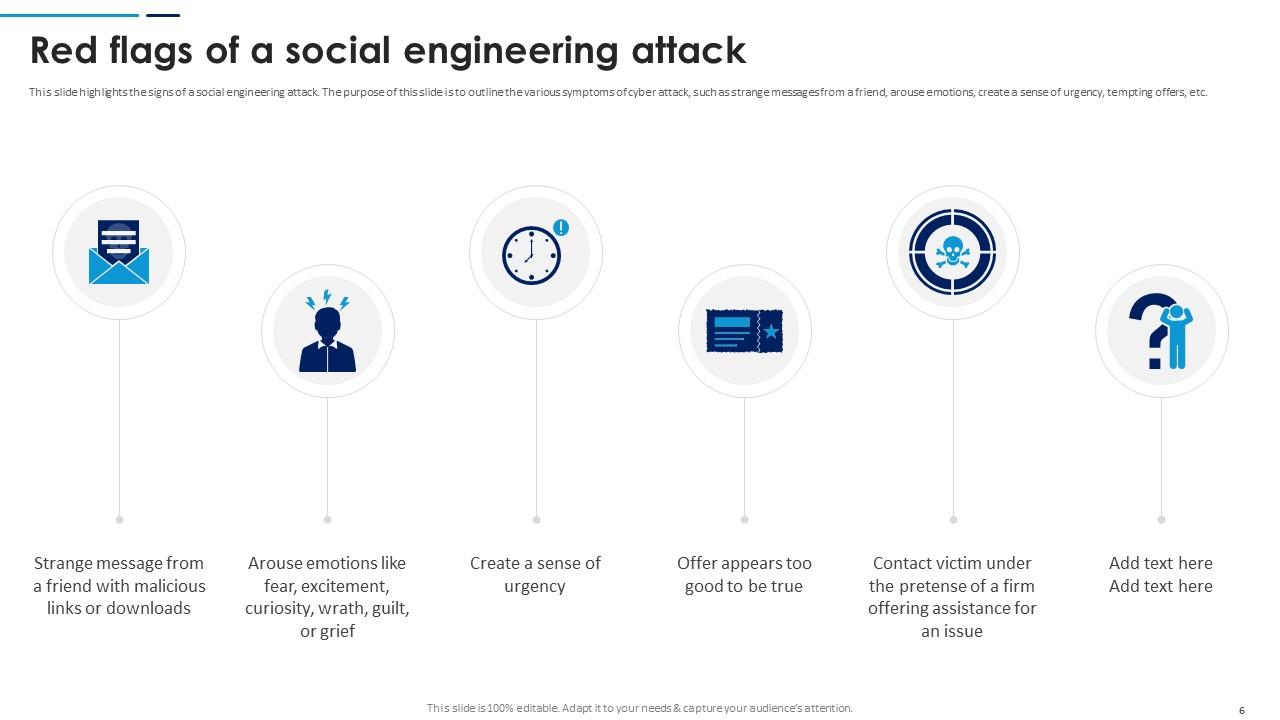
Slide 6: This slide highlights the signs of a social engineering attack. The purpose of this slide is to outline the various symptoms of cyber attacks.
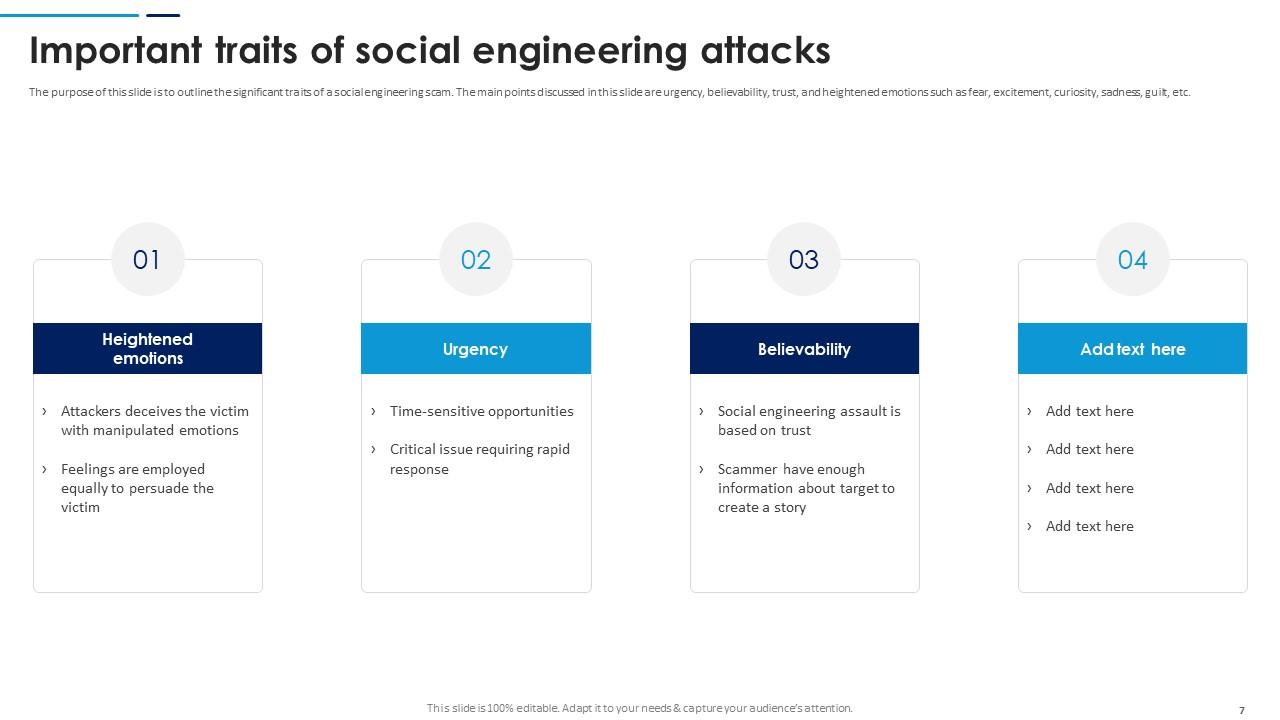
Slide 7: This slide outlines the significant traits of a social engineering scam. The main points discussed in this slide are urgency, believability, trust etc.
Slide 8: This slide demonstrates the popular procedures for conducting social engineering scams. These methods of performing social engineering attacks are phone calls, in-person interactions etc.
Slide 9: This slide highlights the motive of the scammers behind the social engineering attacks. The two primary goals discussed in this slide are disruption and theft.
Slide 10: This slide shows title for topics that are to be covered next in the template.
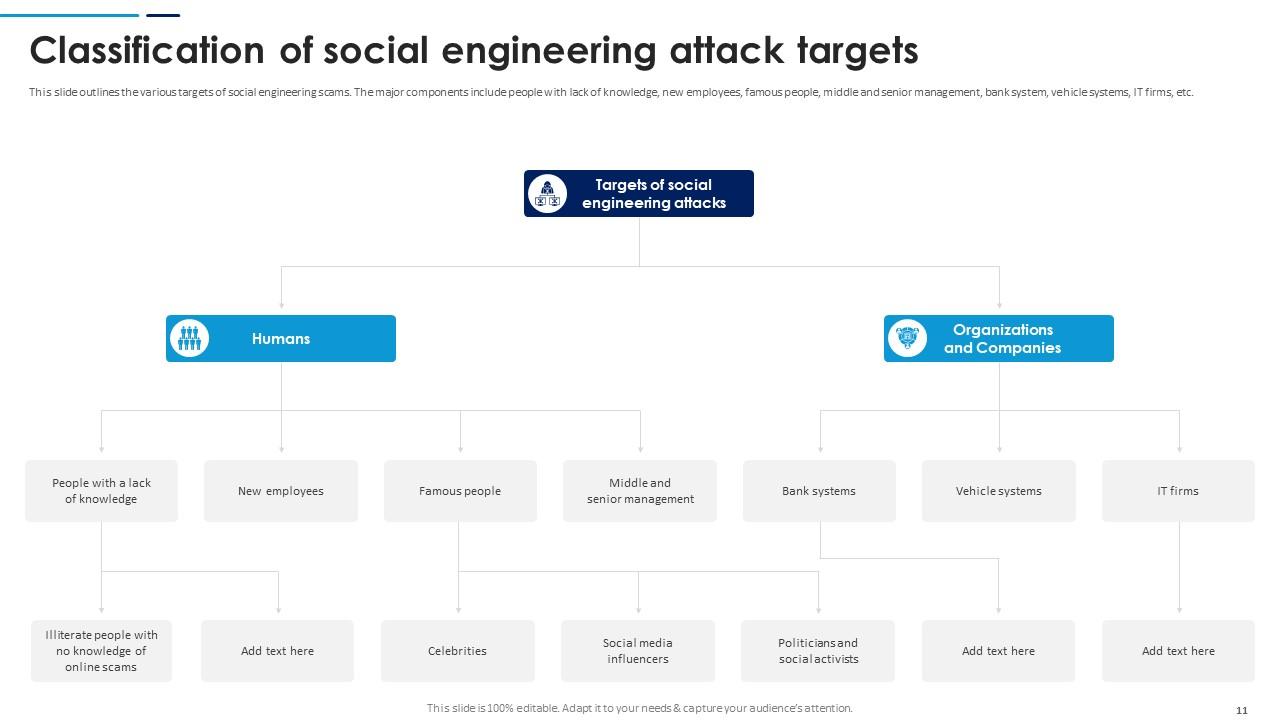
Slide 11: This slide outlines the various targets of social engineering scams. The major components include people with lack of knowledge, new employees, famous people etc.
Slide 12: This slide explains the major targets of social engineering attacks. The targeted groups discussed in this slide are high net worth individuals, well-known internet personas etc.
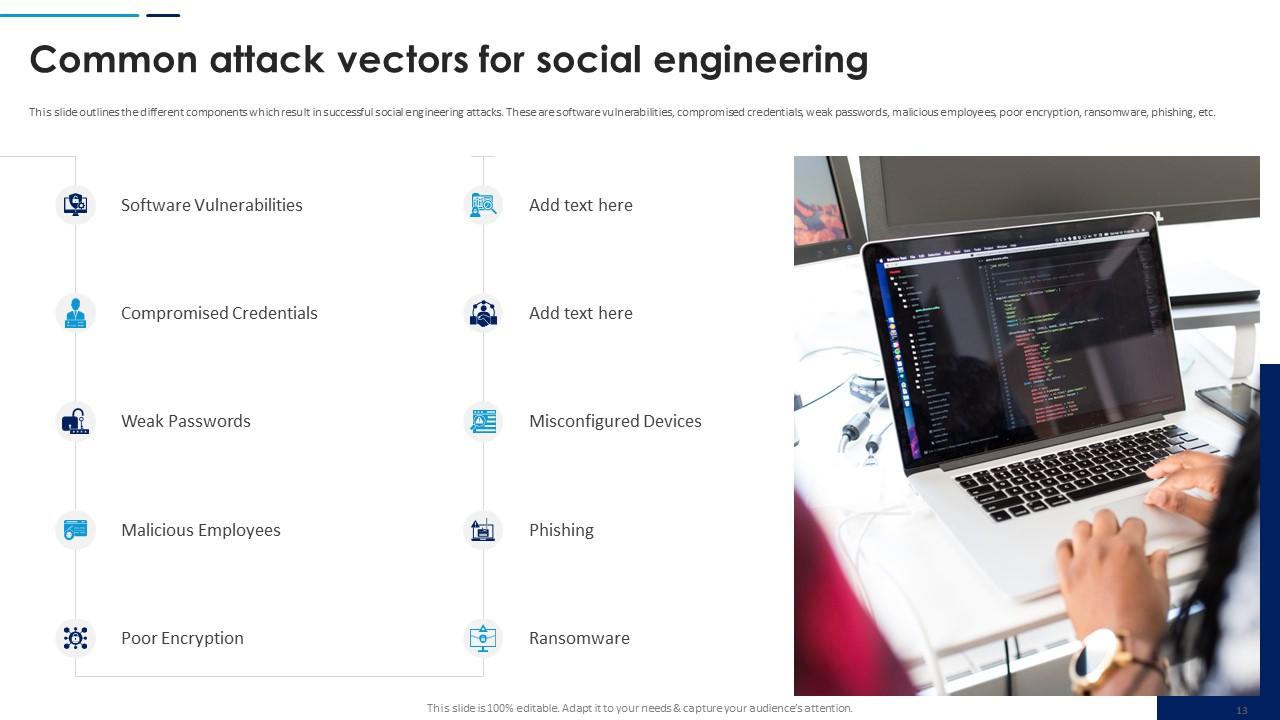
Slide 13: This slide outlines the different components which result in successful social engineering attacks. These are software vulnerabilities, compromised credentials etc.
Slide 14: This slide shows title for topics that are to be covered next in the template.
Slide 15: This slide represents the statistics of most targeted industries of social engineering scams and outlines the various sectors which are more prone to such attacks.
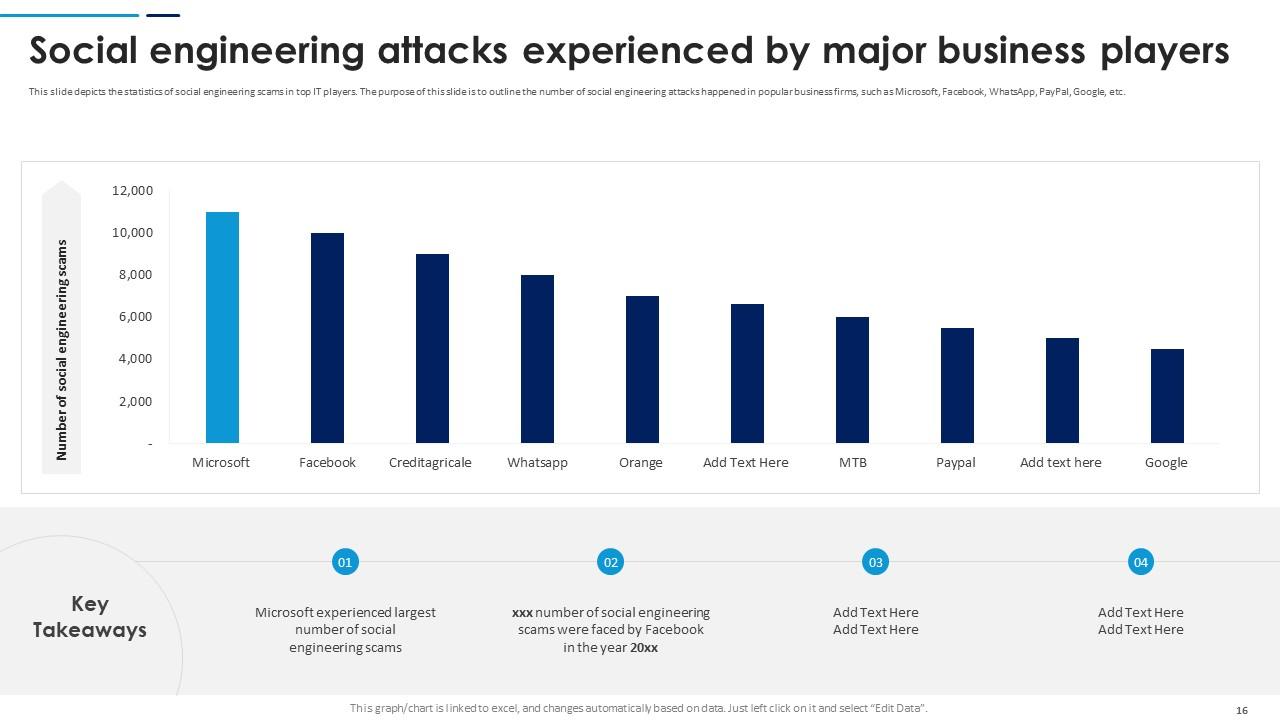
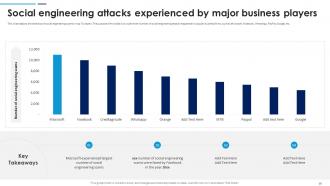
Slide 16: This slide depicts the statistics of social engineering scams in top IT players. The purpose of this slide is to outline the number of social engineering attacks.
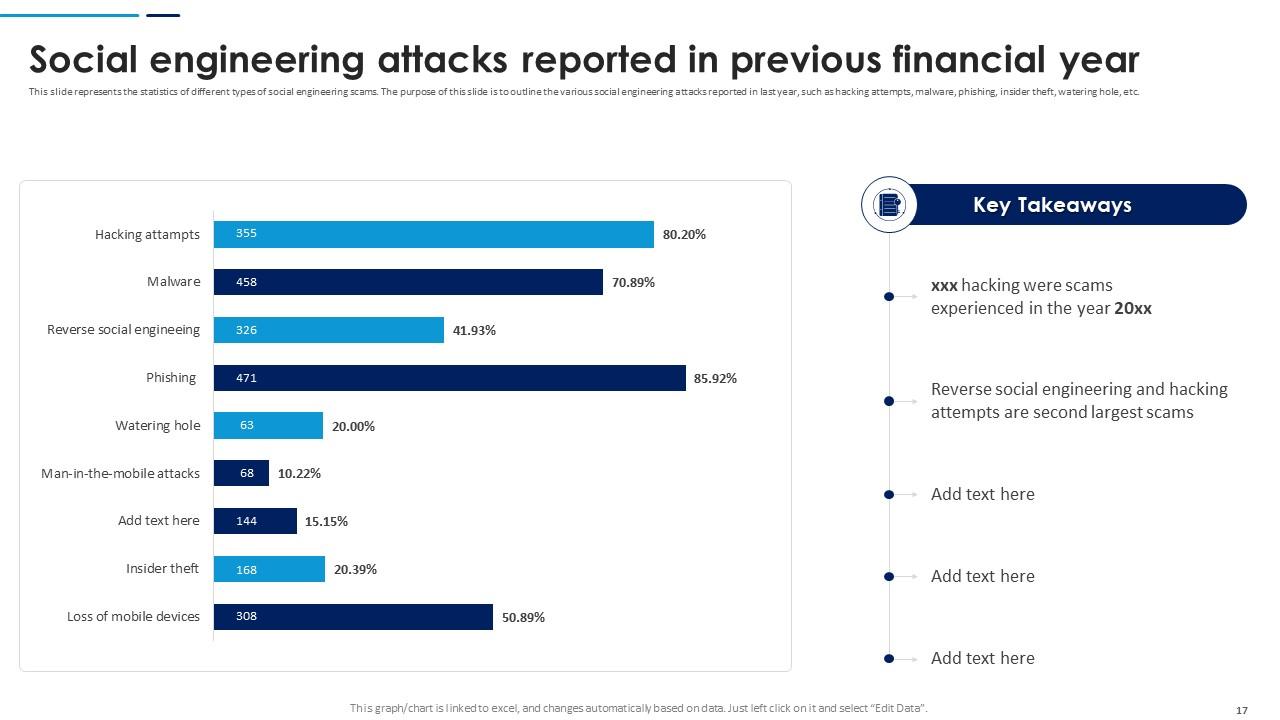
Slide 17: This slide represents the statistics of different types of social engineering scams. The purpose of this slide is to outline the various social engineering attacks.
Slide 18: This slide shows title for topics that are to be covered next in the template.
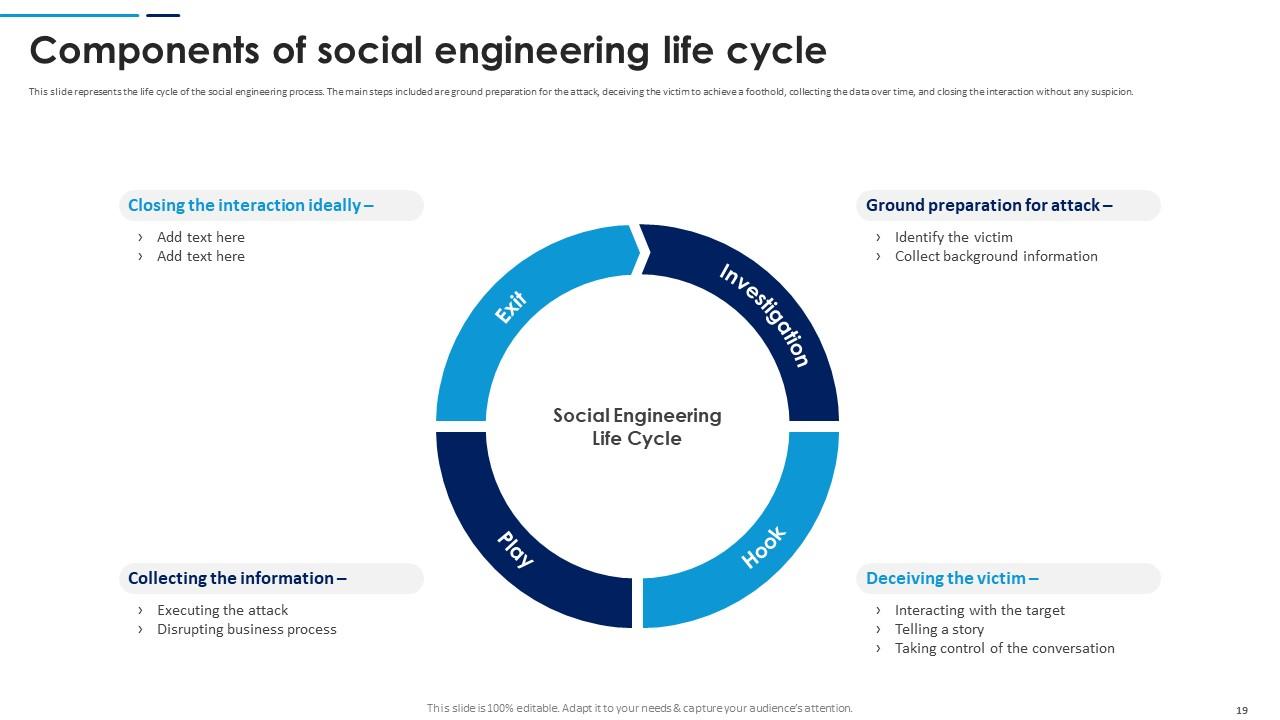
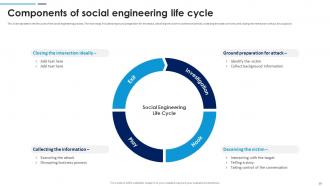
Slide 19: This slide represents the life cycle of the social engineering process. The main steps included are ground preparation for the attack and more.
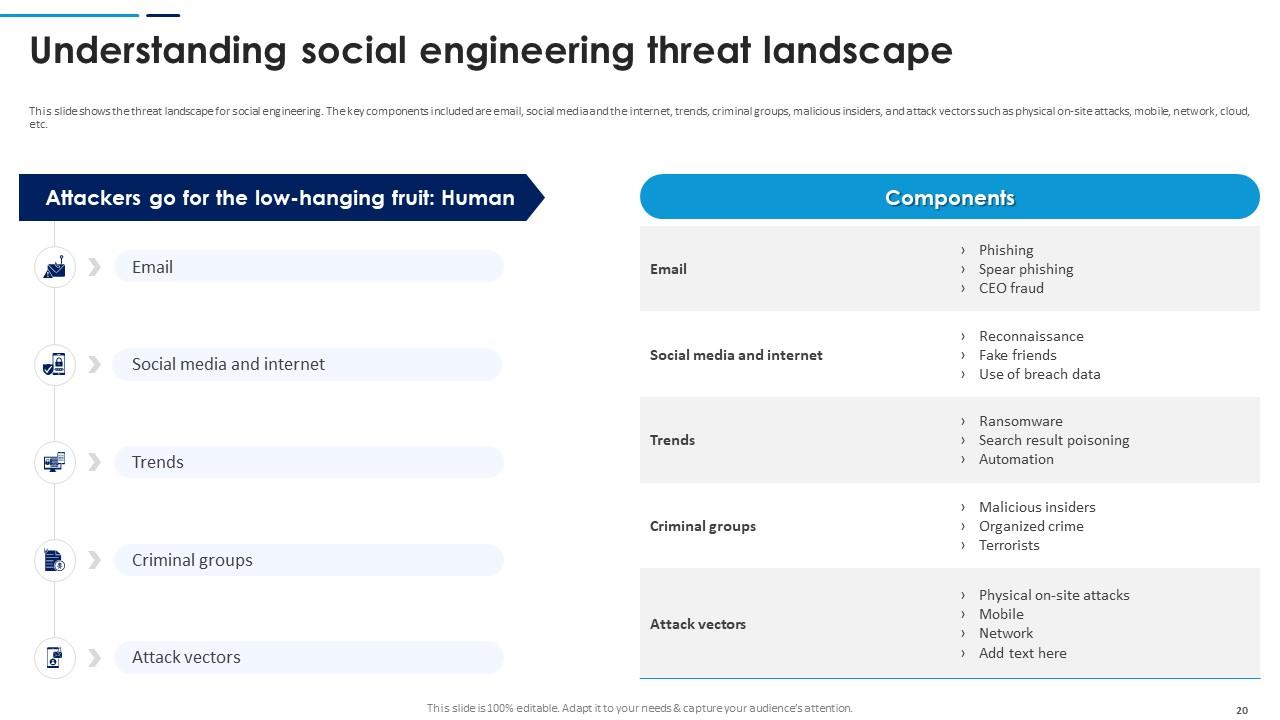
Slide 20: This slide shows the threat landscape for social engineering. The key components included are email, social media and the internet, trends, criminal groups etc.
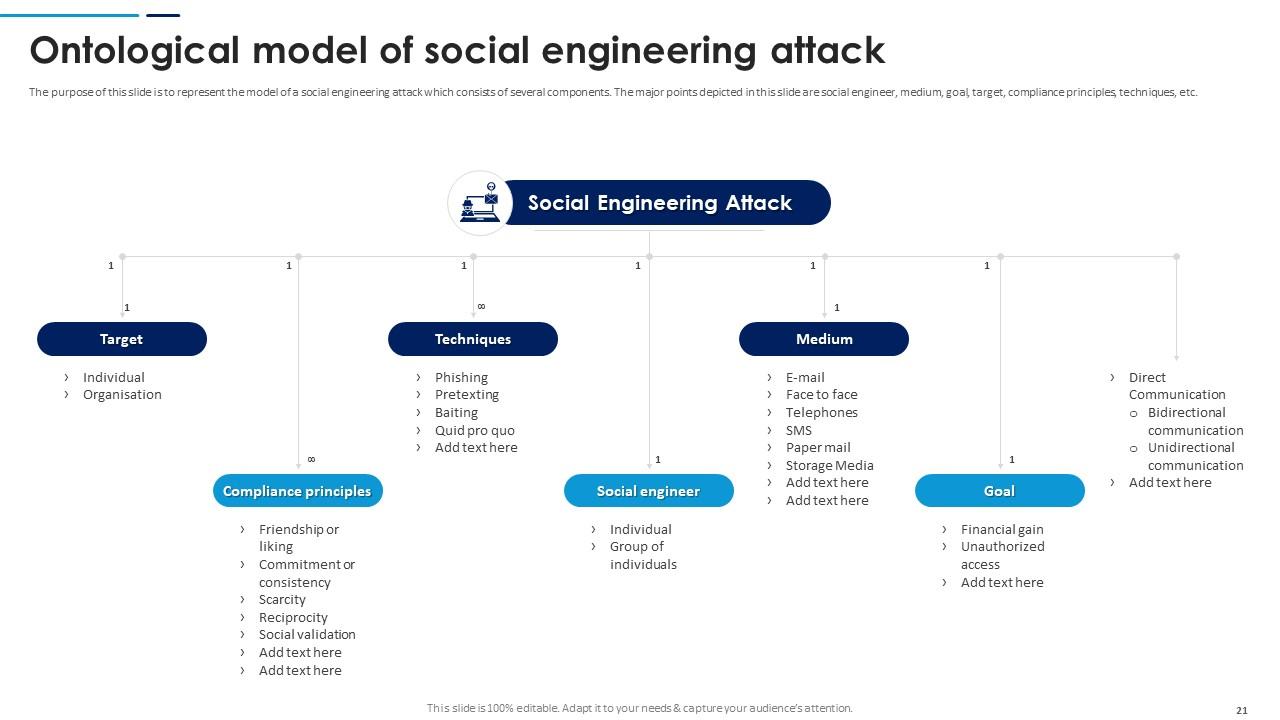
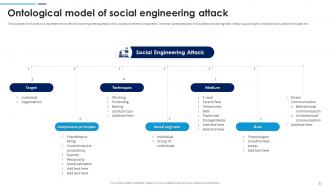
Slide 21: This slide is to represent the model of a social engineering attack which consists of several components. The major points depicted in this slide are social engineer, medium etc.
Slide 22: This slide highlights the key sciences involved in the process of modern social engineering. These are psychology, pedagogy, cognitive sciences, psychiatry etc.
Slide 23: This slide shows title for topics that are to be covered next in the template.
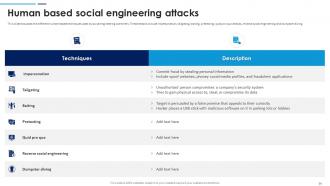
Slide 24: This slide discusses the different human-based techniques used by social engineering scammers. These attacks include impersonation, tailgating, baiting, pretexting etc.
Slide 25: This slide displays the different technology-based techniques used by social engineering scammers. These attacks include phishing, vishing, smishing etc.
Slide 26: This slide shows title for topics that are to be covered next in the template.
Slide 27: This slide discusses several social engineering mitigation techniques. These include avoid clicking on links in emails and texts, use multi-factor authentication etc.
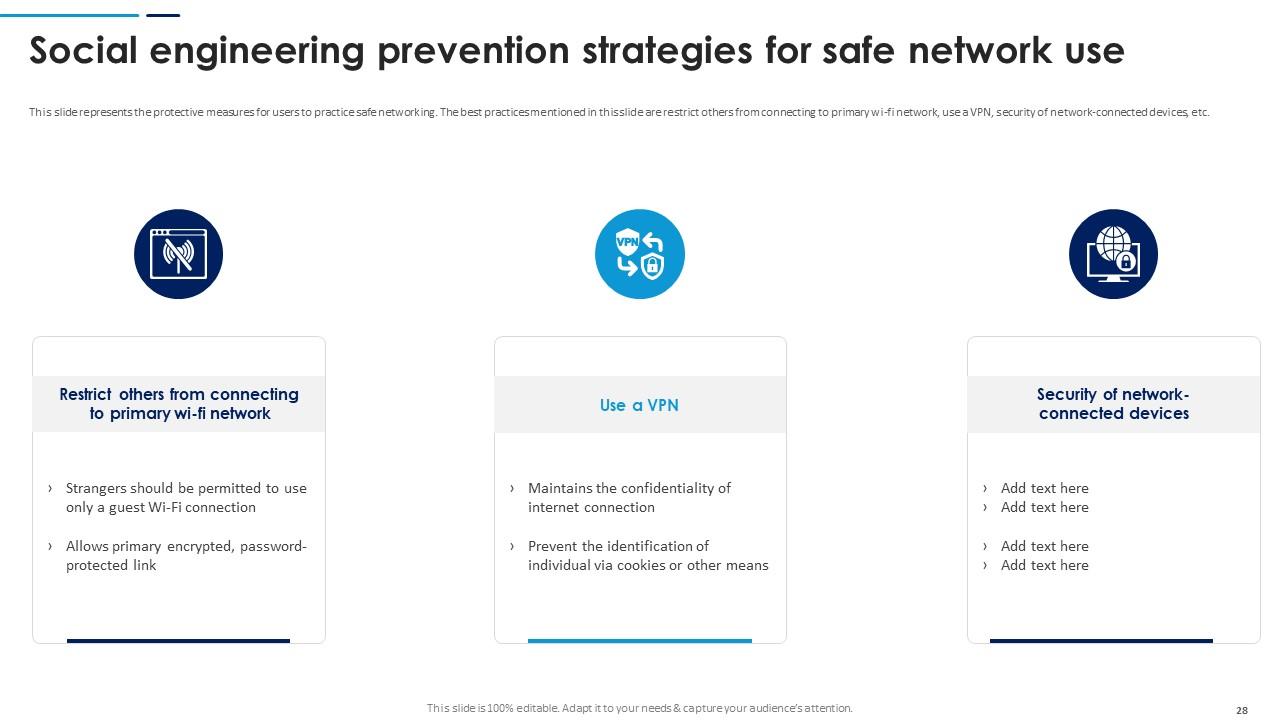
Slide 28: This slide represents the protective measures for users to practice safe networking. The best practices are mentioned in this slide.
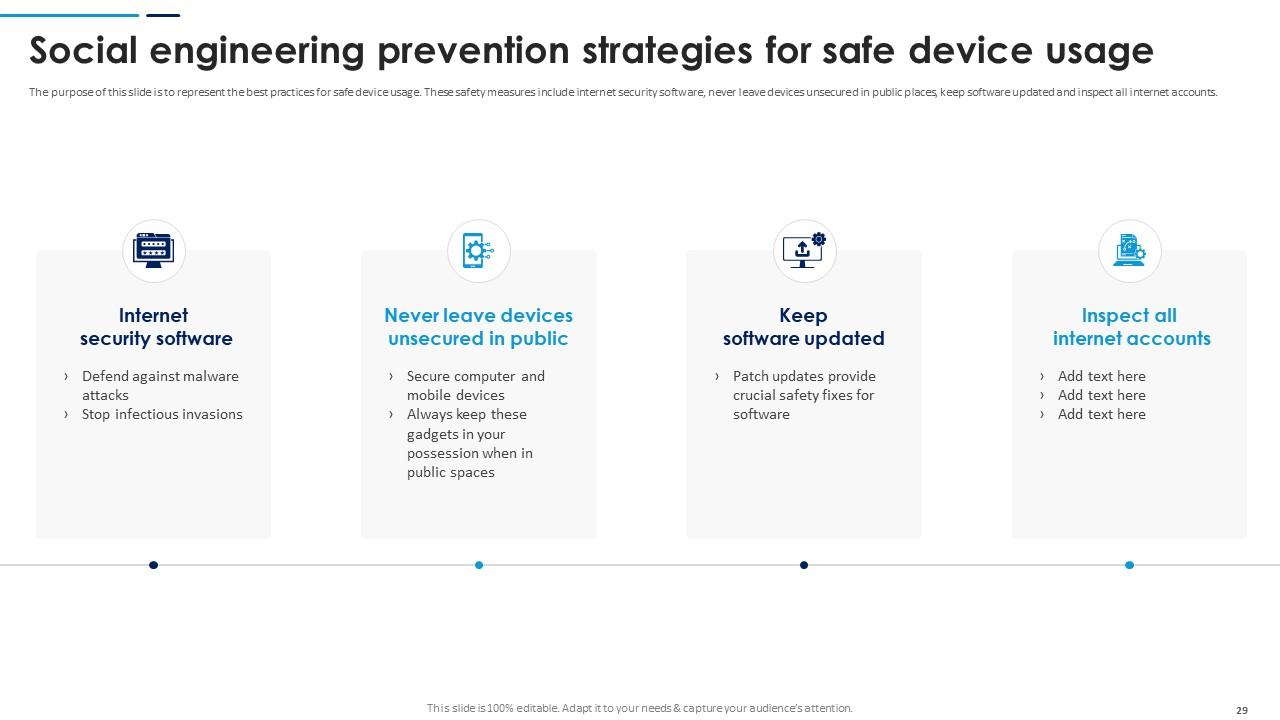
Slide 29: This slide represents the best practices for safe device usage. These safety measures include internet security software, never leave devices unsecured in public places etc.
Slide 30: This slide shows title for topics that are to be covered next in the template.
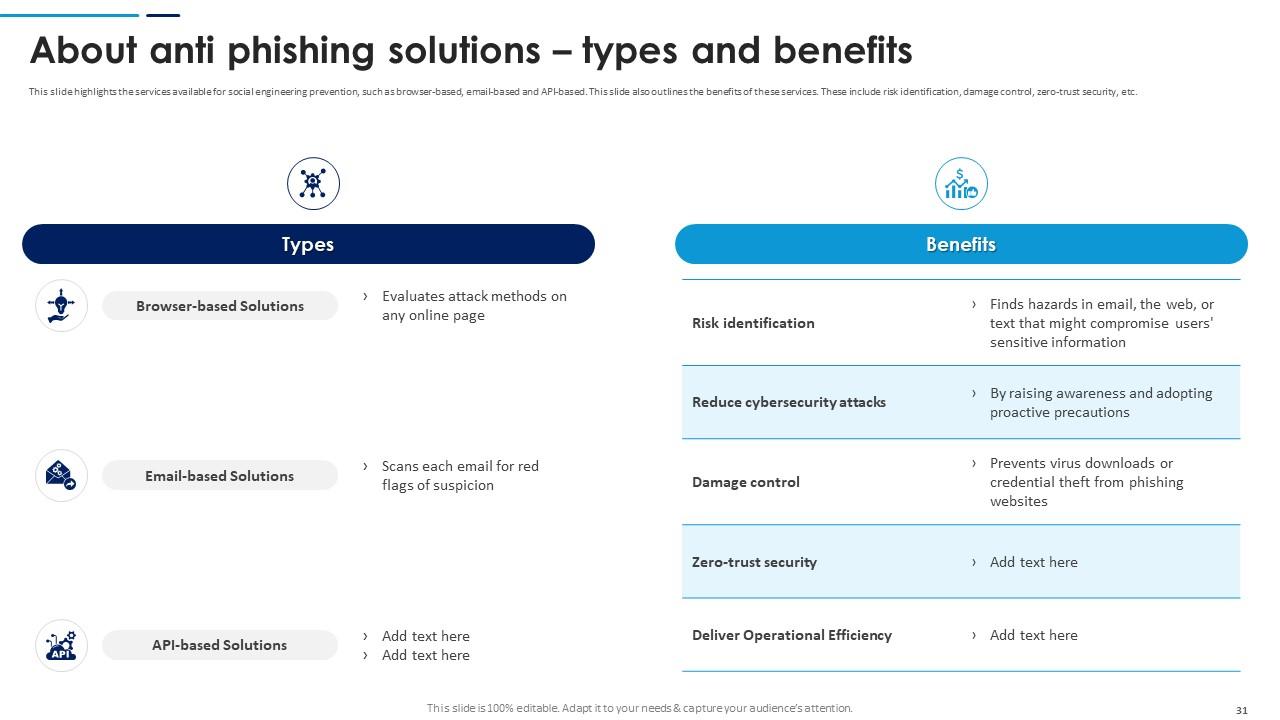
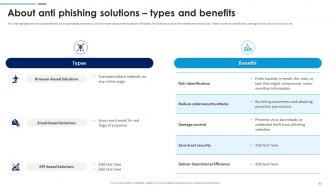
Slide 31: This slide highlights the services available for social engineering prevention, such as browser-based, email-based and API-based.
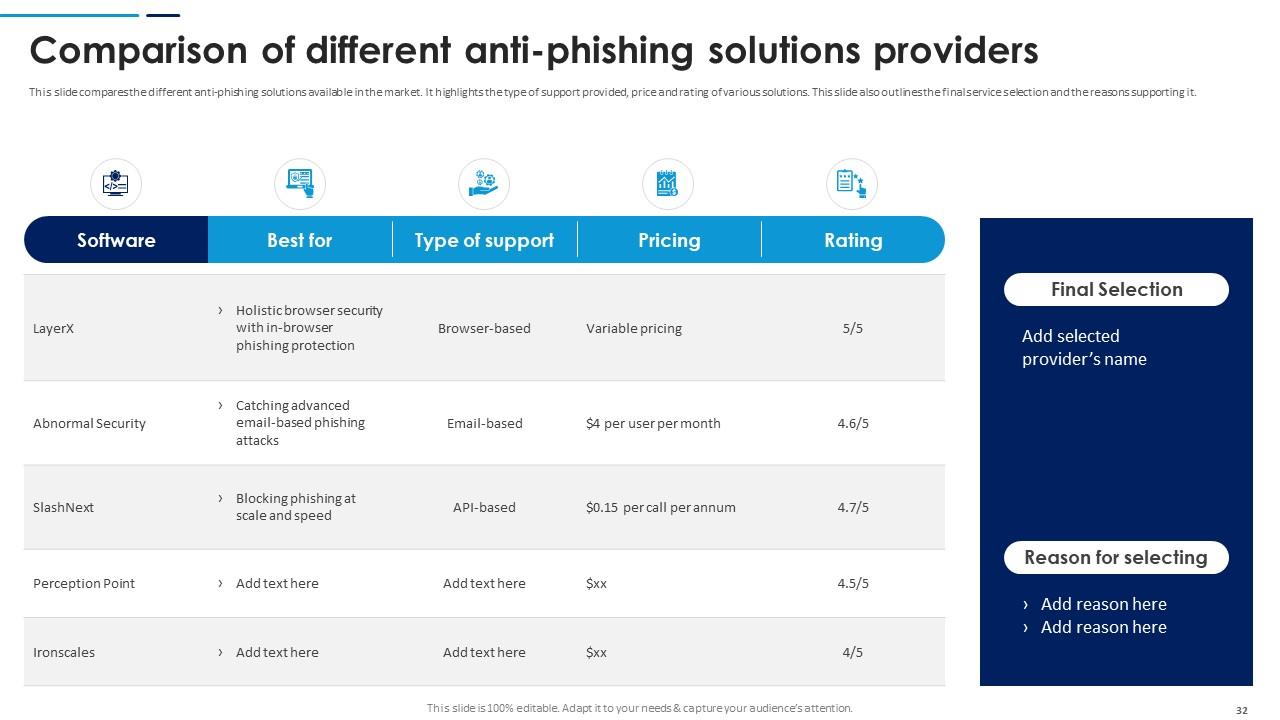
Slide 32: This slide compares the different anti-phishing solutions available in the market. It highlights the type of support provided, price and rating of various solutions.
Slide 33: This slide shows title for topics that are to be covered next in the template.
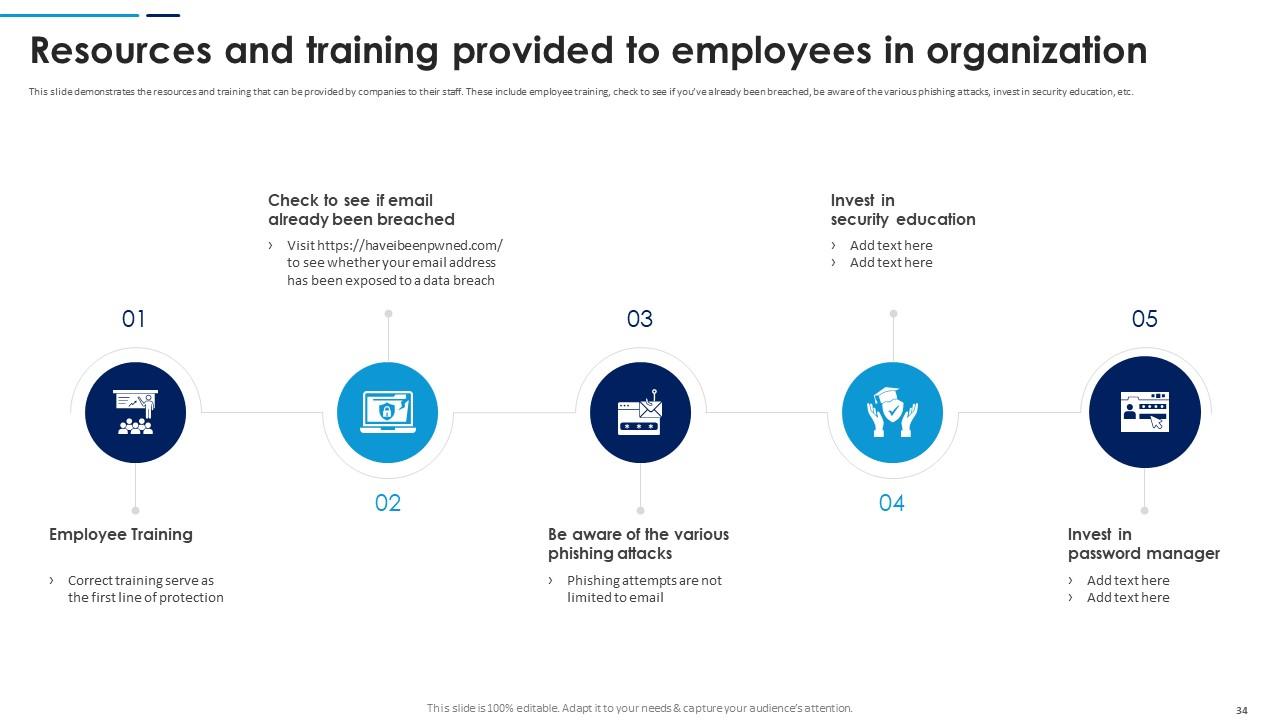
Slide 34: This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training etc.
Slide 35: This slide represents the training program for employees which will help them to prevent various cyber security scams in business.
Slide 36: This slide shows the cost breakup of social engineering awareness training program. The purpose of this slide is to highlight the estimated cost of various training components.
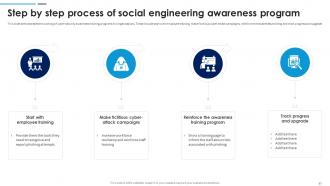
Slide 37: This slide demonstrates the working of cyber security awareness training programs for organizations. These include start with employee training and more.
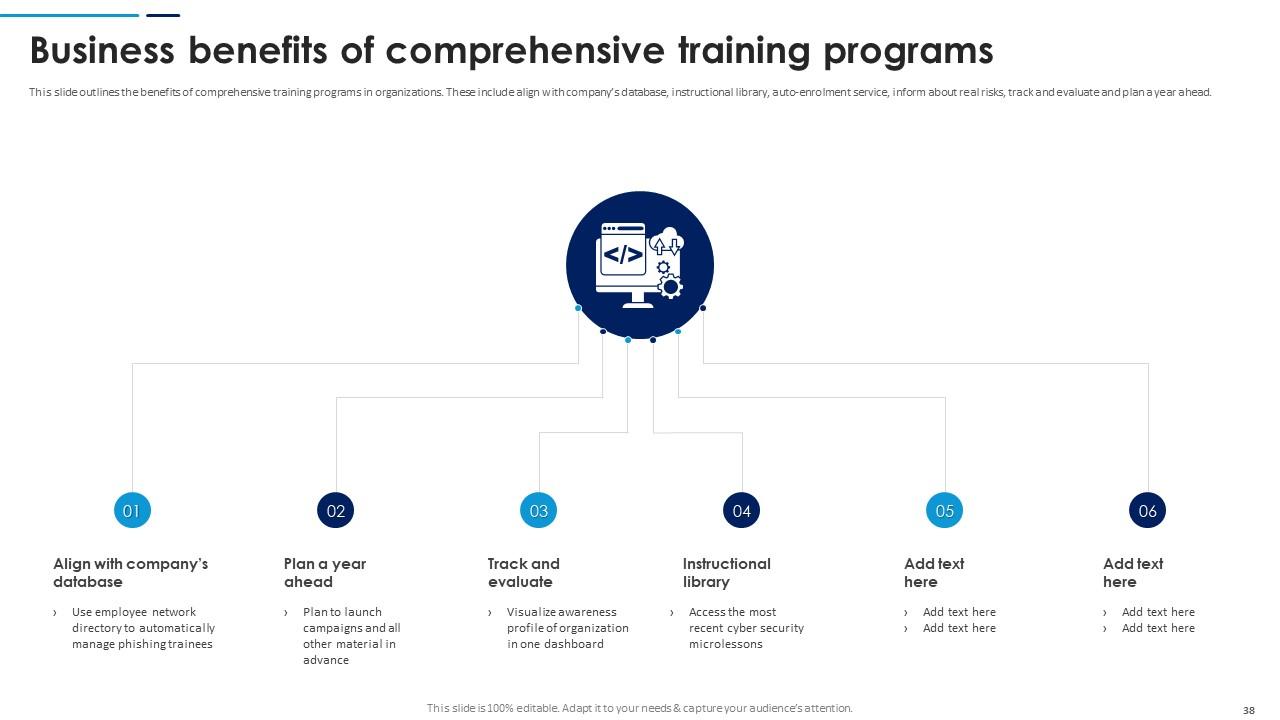
Slide 38: This slide outlines the benefits of comprehensive training programs in organizations. These include align with company’s database, instructional library etc.
Slide 39: This slide talks about the measures for successful social engineering awareness campaign. These include recognize phish, train staff while keeping their individual needs in mind etc.
Slide 40: This slide shows title for topics that are to be covered next in the template.
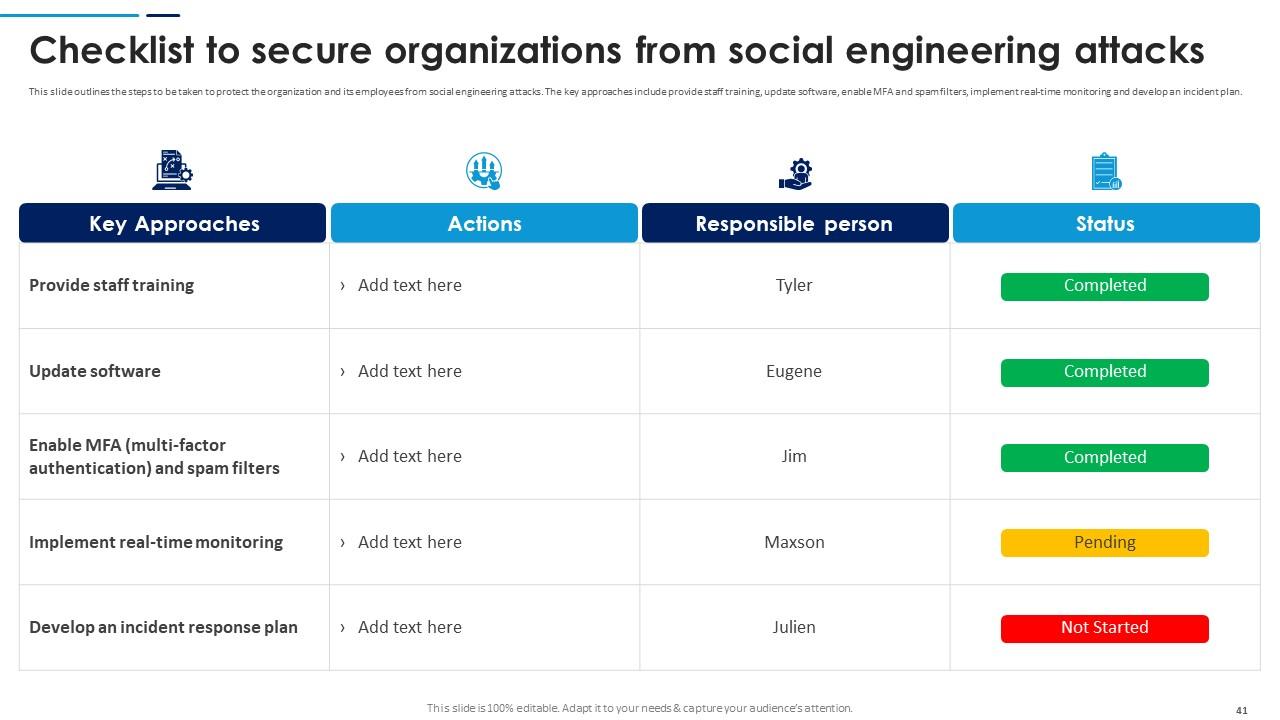
Slide 41: This slide outlines the steps to be taken to protect the organization and its employees from social engineering attacks.
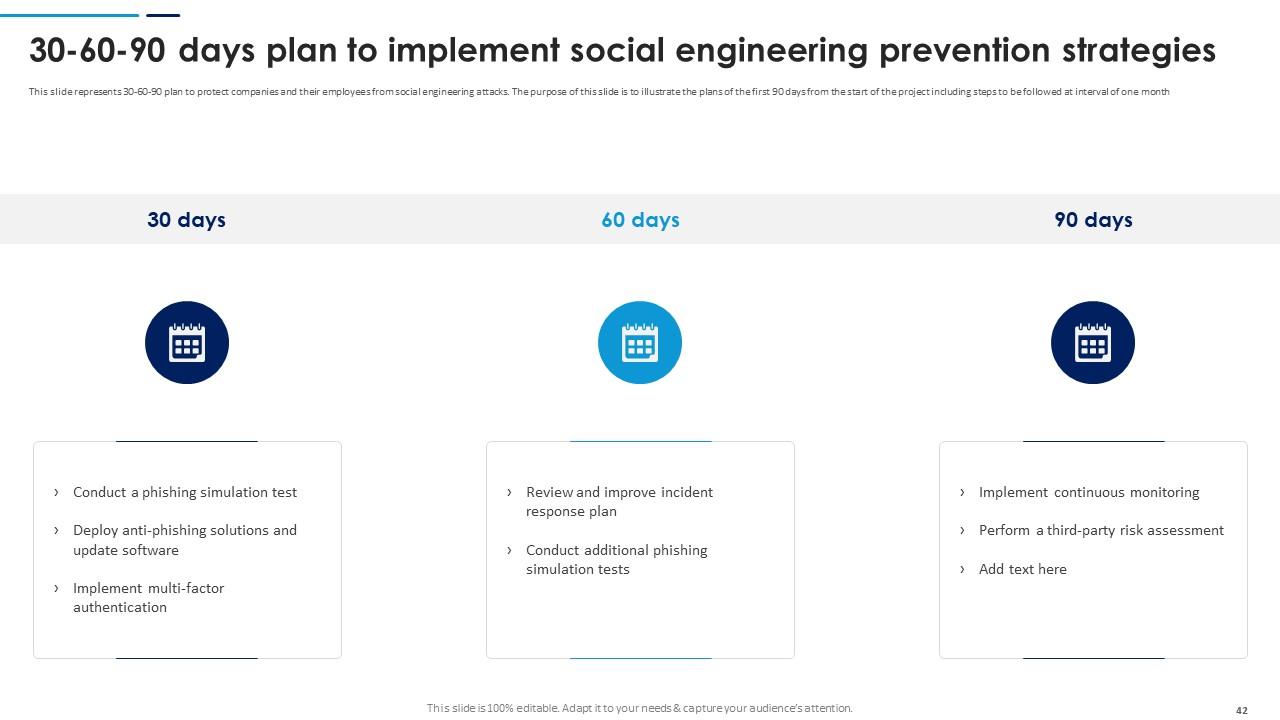
Slide 42: This slide represents 30-60-90 plan to protect companies and their employees from social engineering attacks and illustrates the plans of the first 90 days from the start of the project.
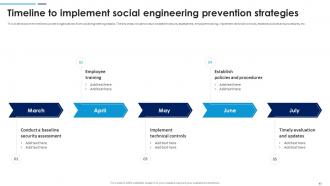
Slide 43: This slide shows the timeline to protect organizations from social engineering attacks. The key steps include conduct a baseline security assessment, employee training etc.
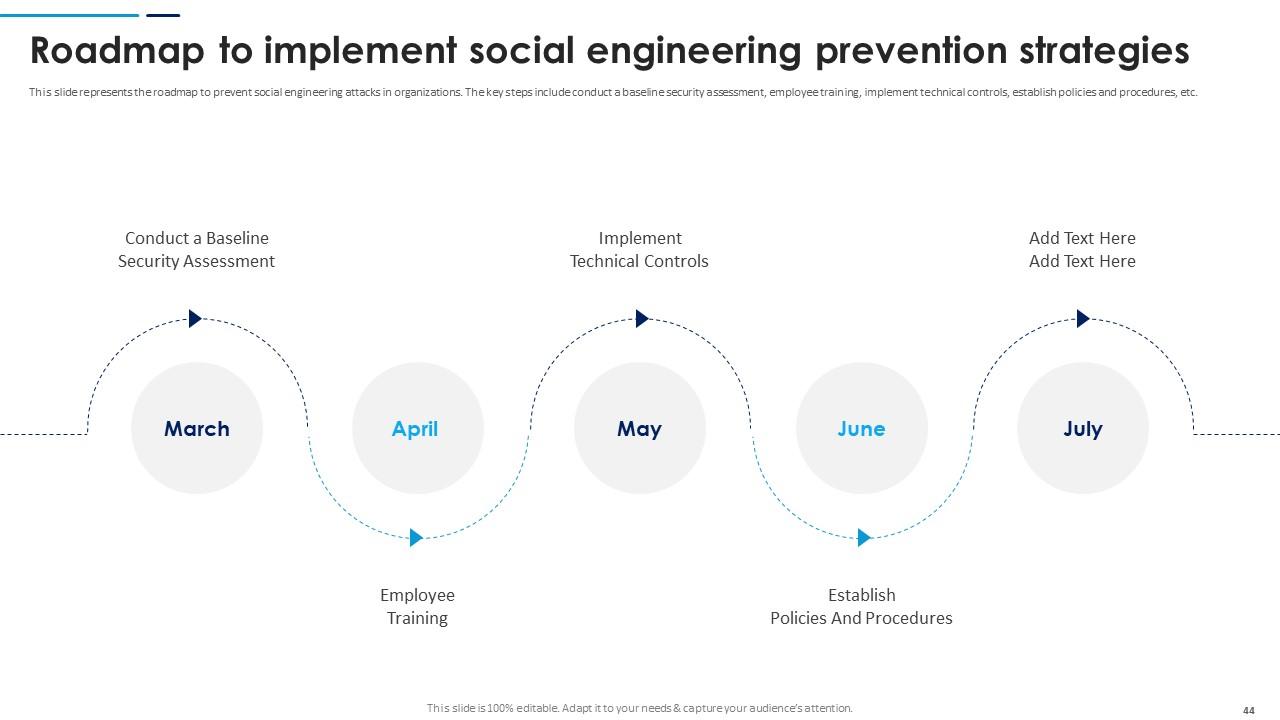
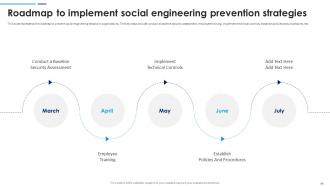
Slide 44: This slide represents the roadmap to prevent social engineering attacks in organizations. The key steps include conduct a baseline security assessment, employee training etc.
Slide 45: This slide shows title for topics that are to be covered next in the template.
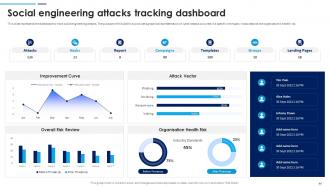
Slide 46: This slide represents the dashboard to track social engineering attacks. The purpose of this slide is to provide a graphical representation of cyber attacks.
Slide 47: This slide shows all the icons included in the presentation.
Slide 48: This slide is titled as Additional Slides for moving forward.
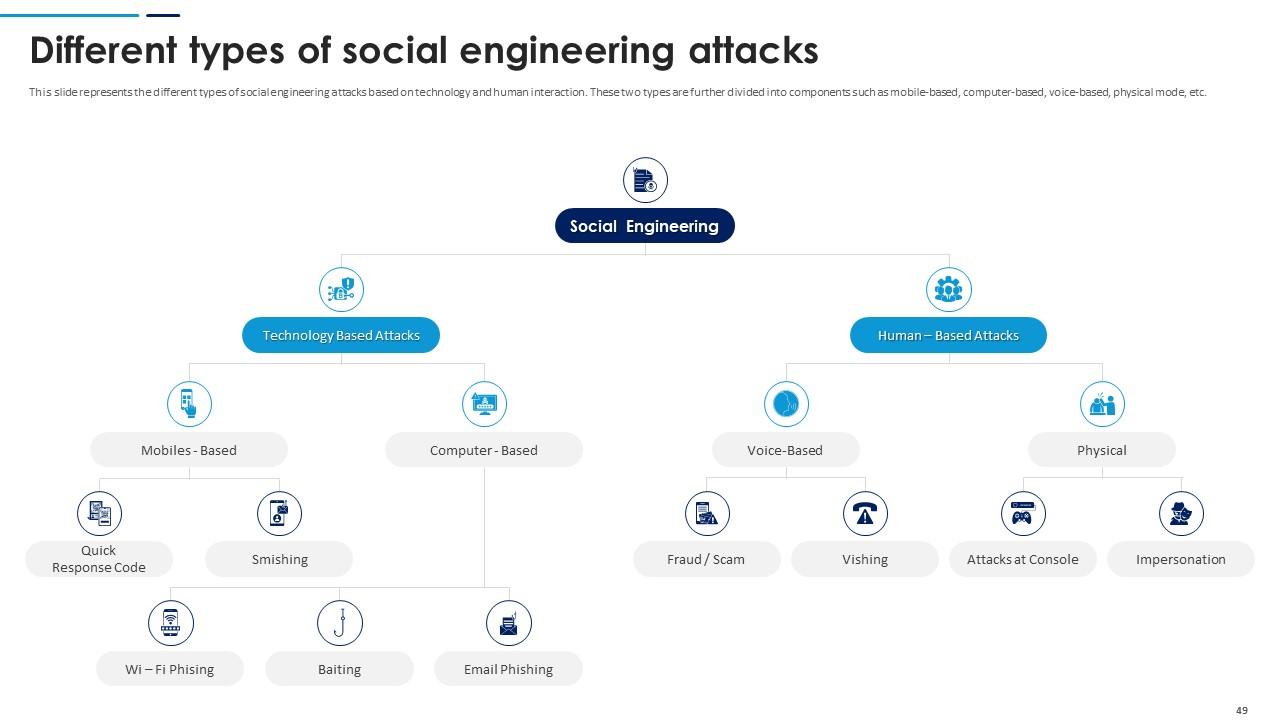
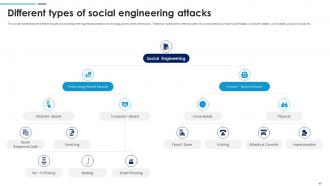
Slide 49: This slide represents the different types of social engineering attacks based on technology and human interaction.
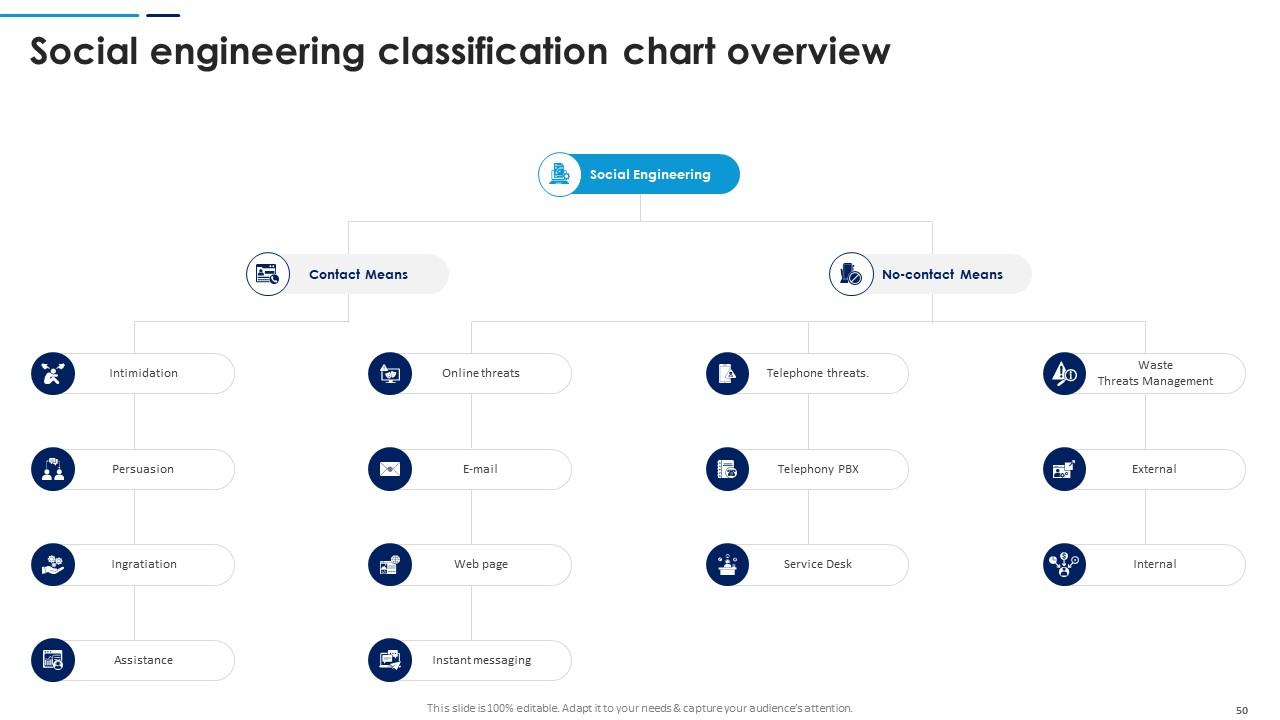
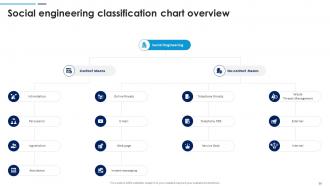
Slide 50: This slide showcases Social engineering classification chart overview with related icons and text.
Slide 51: This slide provides 30 60 90 Days Plan with text boxes.
Slide 52: This slide contains Puzzle with related icons and text.
Slide 53: This slide depicts Venn diagram with text boxes.
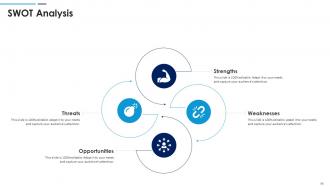
Slide 54: This slide shows SWOT analysis describing- Strength, Weakness, Opportunity, and Threat.
Slide 55: This slide shows Post It Notes for reminders and deadlines. Post your important notes here.
Slide 56: This is Our Vision, Mission & Goal slide. Post your Visions, Missions, and Goals here.
Slide 57: This is Our Team slide with names and designation.
Slide 58: This is a Thank You slide with address, contact numbers and email address.
Social Engineering Attacks Prevention For Businesses Powerpoint Presentation Slides with all 67 slides:
Use our Social Engineering Attacks Prevention For Businesses Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Thanks to SlideTeam, we have an ideal template to present all the info we need to cover. Their slides give our numbers and projections a more clear and enchanting look.
-
Great quality product.