Threats Sybil Attack Poses To Blockchain Technology Training Ppt
These slides cover the adverse impact of the Sybil attack on a blockchain, such as security and privacy risks and reverse transactions. These also include information about strategies to preventive to avoid the Sybil attack.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Threats Sybil Attack Poses to Blockchain Technology. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1
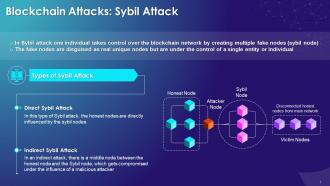
This slide illustrates the concept of sybil attack on blockchain network. It explains that in Sybil attack, one individual takes control over the blockchain network by creating multiple fake nodes (sybil nodes). It highlights the multiple types of sybil attacks such as: the direct sybil attack and indirect sybil attack. In direct attack, the honest node gets influenced by the sybil node and in the indirect attack hackers manipulate a middle node, which is in communication with an honest node to achieve his/her own ends.
Slide 2
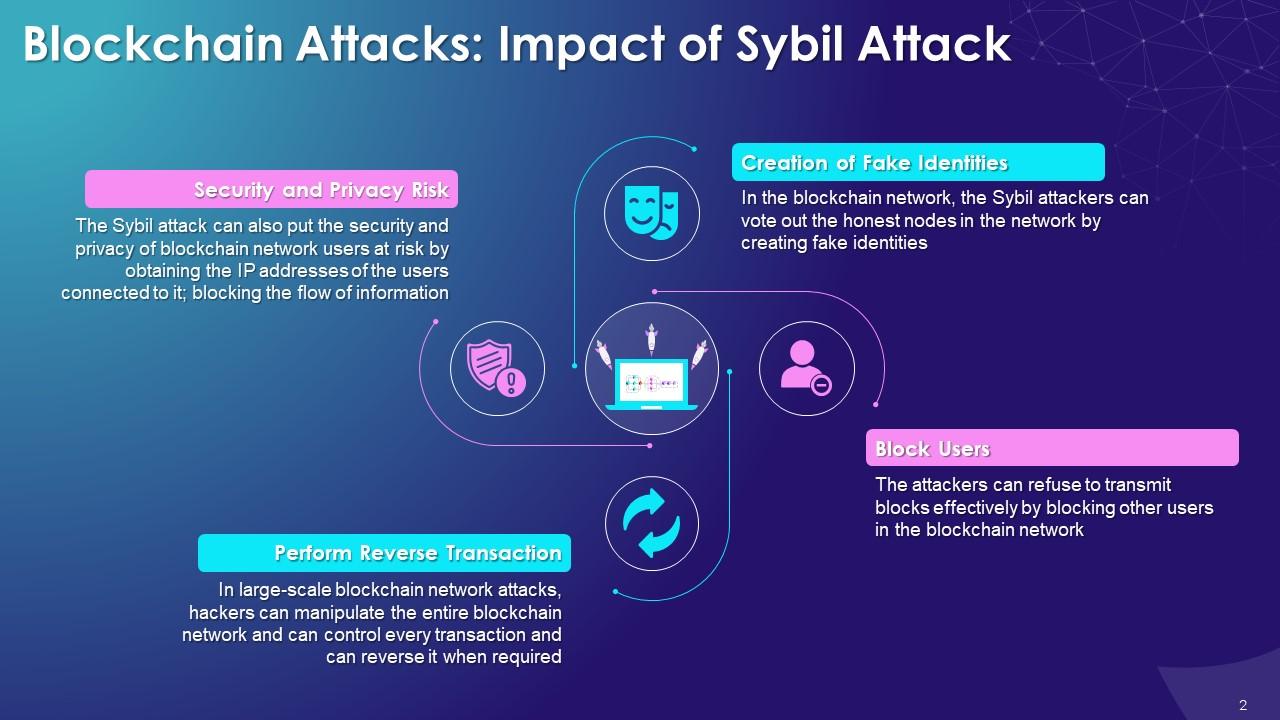
This slide showcases the multiple impacts of sybil attack on blockchain network. The multiple impacts of sybil attack such as creation of fake identities, blocking users, performing reverse transaction, and security and privacy risk. It explains that the hacker in the network after conducting the attack can vote out any request from an honest user. The attacker can conduct a large-scale attack and manipulate the entire blockchain network by purchase transactions or reversing some of these are per his/her own motive. It can also put user security at risk by controlling the information about their IP address.
Slide 3
This slide showcases the multiple ways by which blockchain networks can be prevented from Sybil attacks. The different prevention measures are: use different consensus algorithms, set up cost to create new identity, and validation of identity before anyone joins the network.
Threats Sybil Attack Poses To Blockchain Technology Training Ppt with all 19 slides:
Use our Threats Sybil Attack Poses To Blockchain Technology Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Great product with highly impressive and engaging designs.
-
Thank you for showering me with discounts every time I was reluctant to make the purchase.