Hacking it powerpoint presentation slides
Hacking is an effort to gain unauthorized access to a computer system or a private network within a computer. Here is a professionally designed Hacking IT template that provides an overview of the business current situation by describing the hacking attacks faced by the company and the impact of these attacks on the organization. This PowerPoint presentation covers the new strategies to prevent hacking, including ethical hacking, cyber security awareness among employees, backup of sensitive data, disaster recovery plan, usage of security programs, and others. Additionally, this Security Hacker PPT talks about the budget for implementing new security policies and new prevention measures. Furthermore, this template includes an implementation plan that caters to a 30-60-90 days plan, a roadmap, and a dashboard. Also, this PPT provides the impact of new security policies and preventing measures on business such as the impact of ethical hackers, benefits of ethical hackers to the company, and regaining the companys reputation. Lastly, this Hacking deck introduces hacking and ethical hacking and its purpose and legality. Download this 100 percent editable template now.
You must be logged in to download this presentation.
PowerPoint presentation slides
Enthrall your audience with this Hacking IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising fifty eight slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Hacking (IT). State Your Company Name and begin.
Slide 2: This is an Agenda slide. State your agendas here.
Slide 3: This slide presents Table of Content for the presentation.
Slide 4: This slide shows title for topics that are to be covered next in the template.
Slide 5: This slide displays Reasons and Impact of Website Hacking on Business.
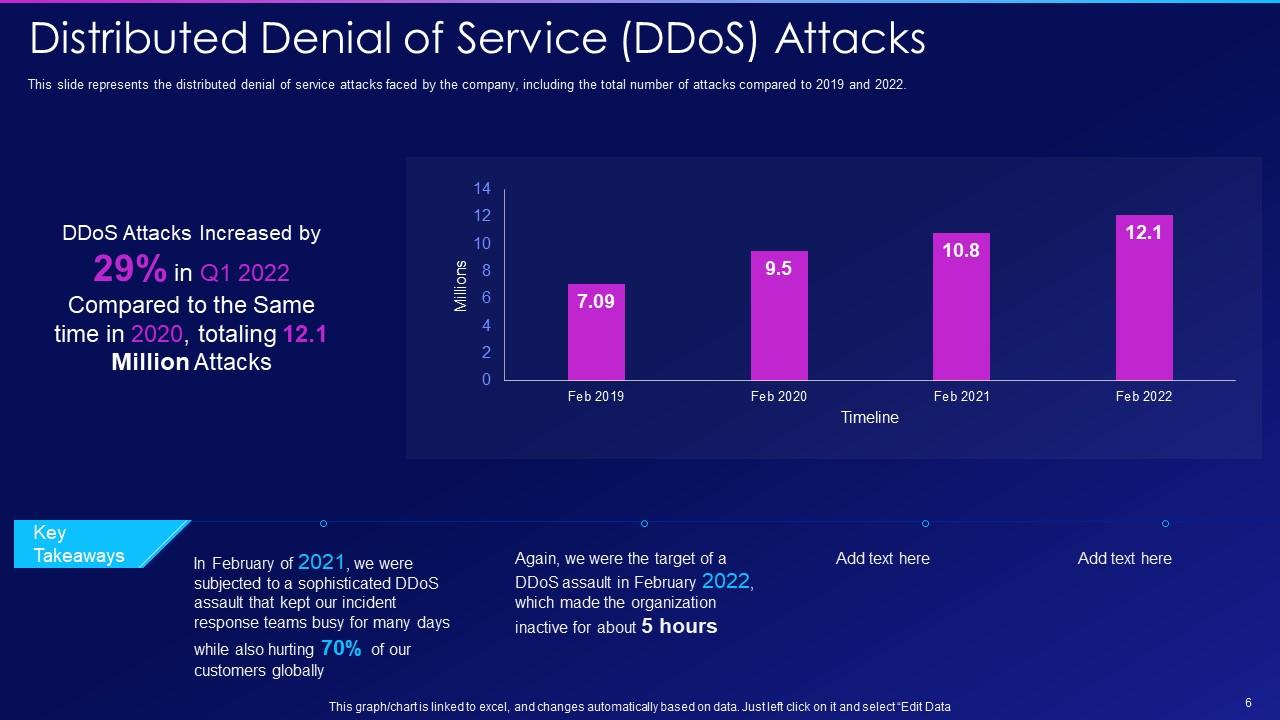
Slide 6: This slide represents the distributed denial of service attacks faced by the company.
Slide 7: This slide showcases Hacking of Our Social Media Accounts.
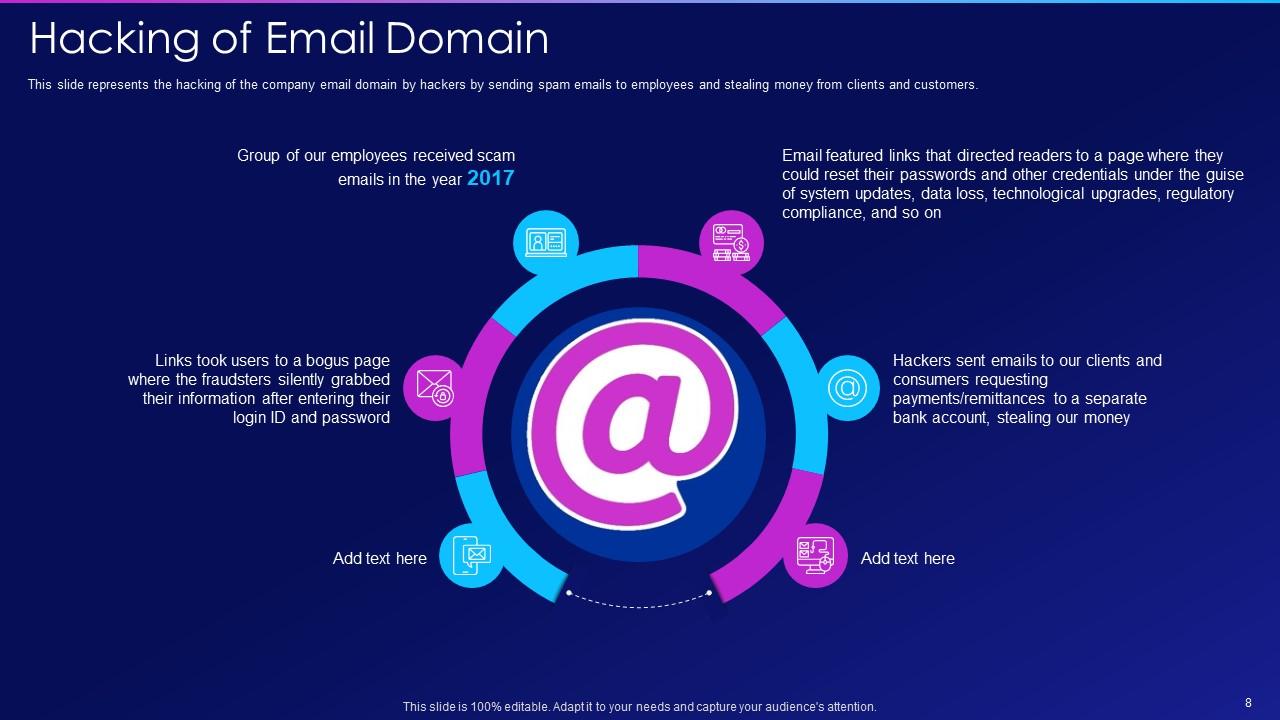
Slide 8: This slide presents hacking of the company email domain by hackers by sending spam email.
Slide 9: This slide shows title for topics that are to be covered next in the template.
Slide 10: This slide represents the different types of cyber-attacks throughout the year.
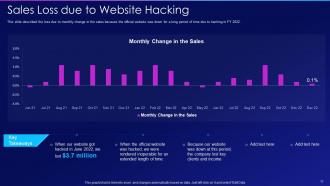
Slide 11: This slide displays Sales Loss due to Website Hacking.
Slide 12: This slide depicts the increased additional costs caused by cyber-attacks.
Slide 13: This slide represents Reputational Damage due to Cyberattacks.
Slide 14: This slide showcases Loss of Customers and Client Information.
Slide 15: This slide represents that hackers forced the company to alter business practices.
Slide 16: This slide shows title for topics that are to be covered next in the template.
Slide 17: This slide displays Ethical Hacker and Why We Need Ethical Hacker.
Slide 18: This slide represents Roles and Responsibilities of Ethical Hackers.
Slide 19: This slide depicts why organizations recruit ethical hackers, including effective security measures.
Slide 20: This slide shows title for topics that are to be covered next in the template.
Slide 21: This slide represents the cybersecurity awareness training program for staff.
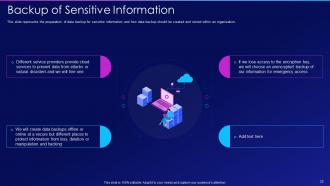
Slide 22: This slide showcases the preparation of data backup for sensitive information.
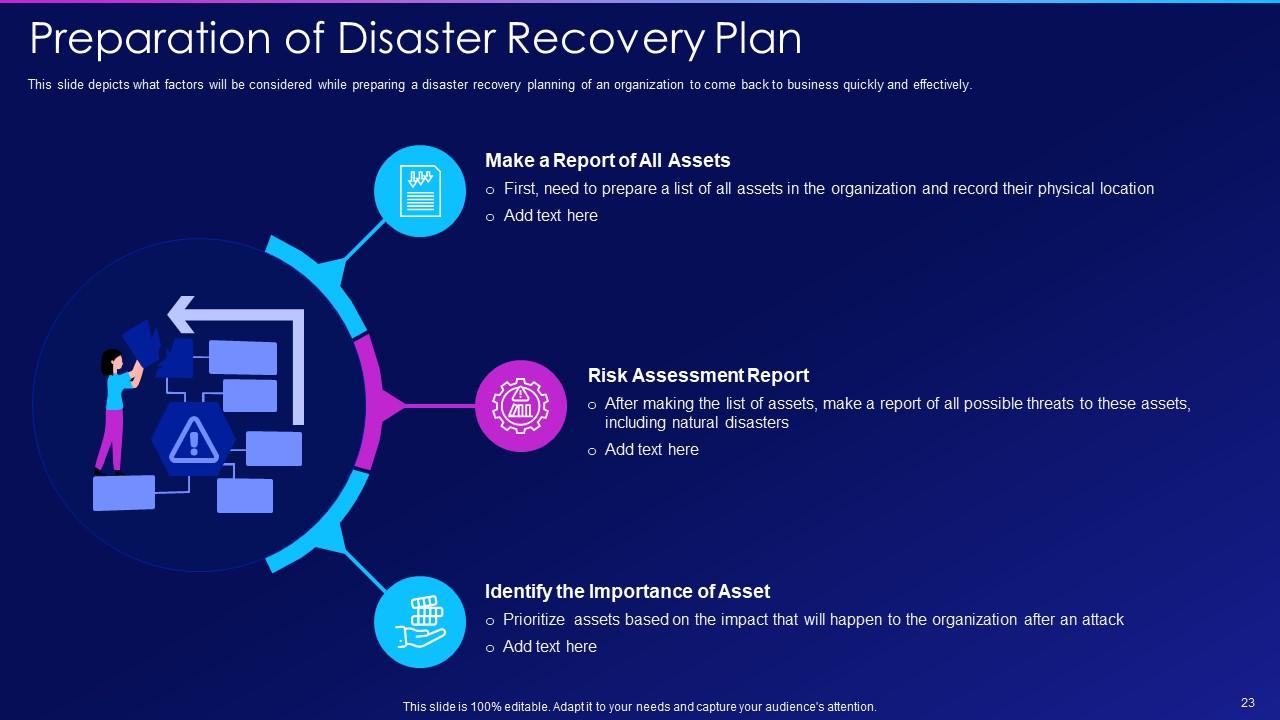
Slide 23: This slide depicts what factors will be considered while preparing a disaster recovery planning.
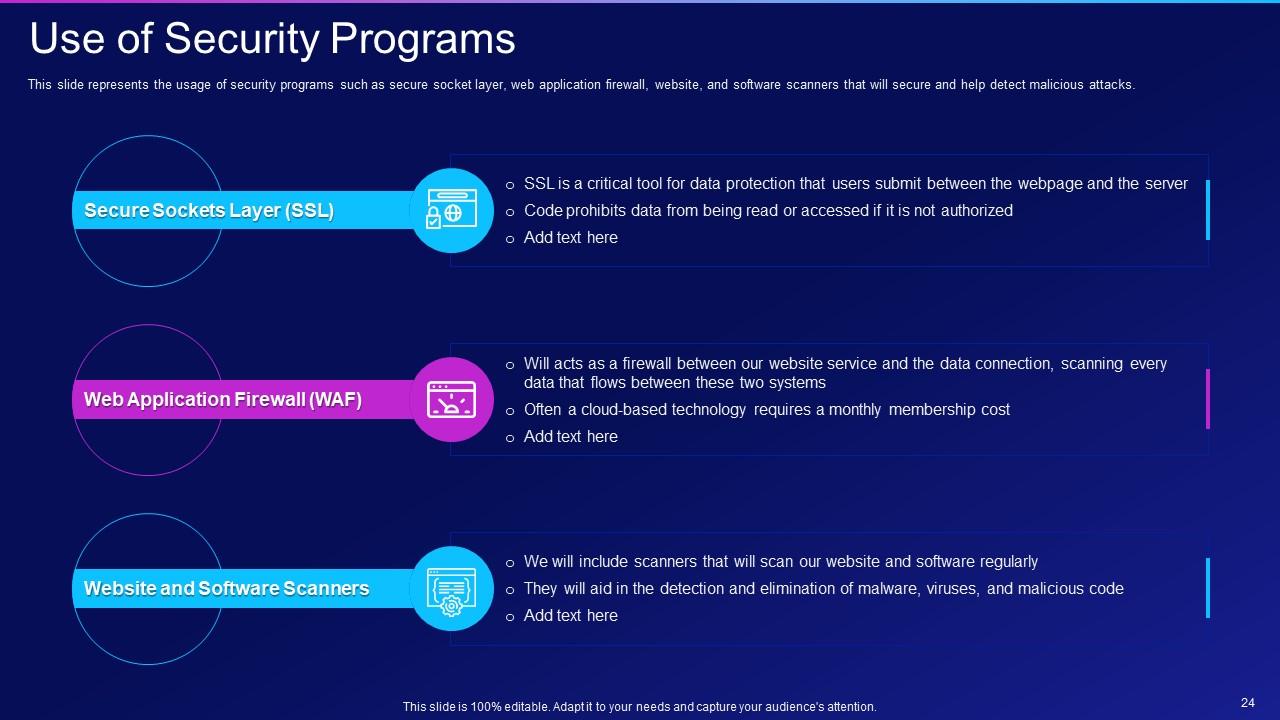
Slide 24: This slide represents the usage of security programs such as secure socket layer, web application firewall, etc.
Slide 25: This slide shows title for topics that are to be covered next in the template.
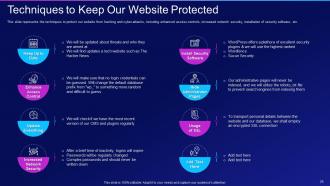
Slide 26: This slide displays Techniques to Keep Our Website Protected.
Slide 27: This slide represents Preventing Measures for Social Media Accounts.
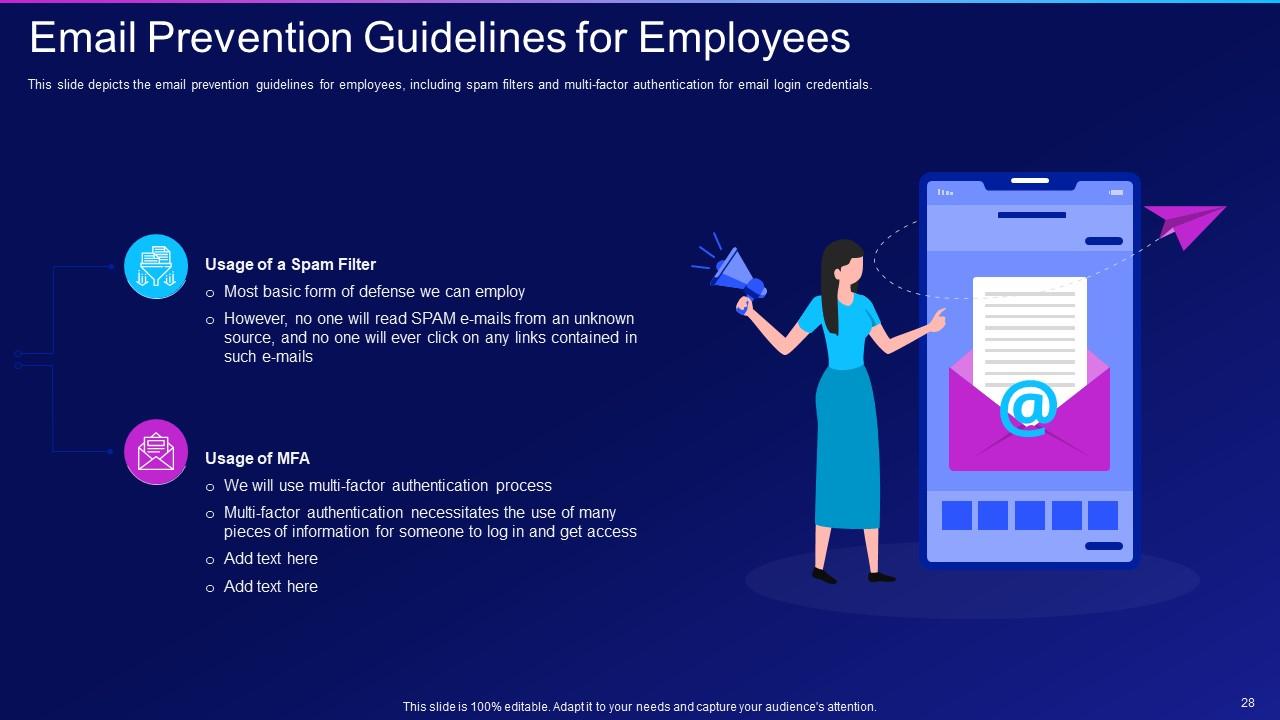
Slide 28: This slide depicts the email prevention guidelines for employees, including spam filters.
Slide 29: This slide shows title for topics that are to be covered next in the template.
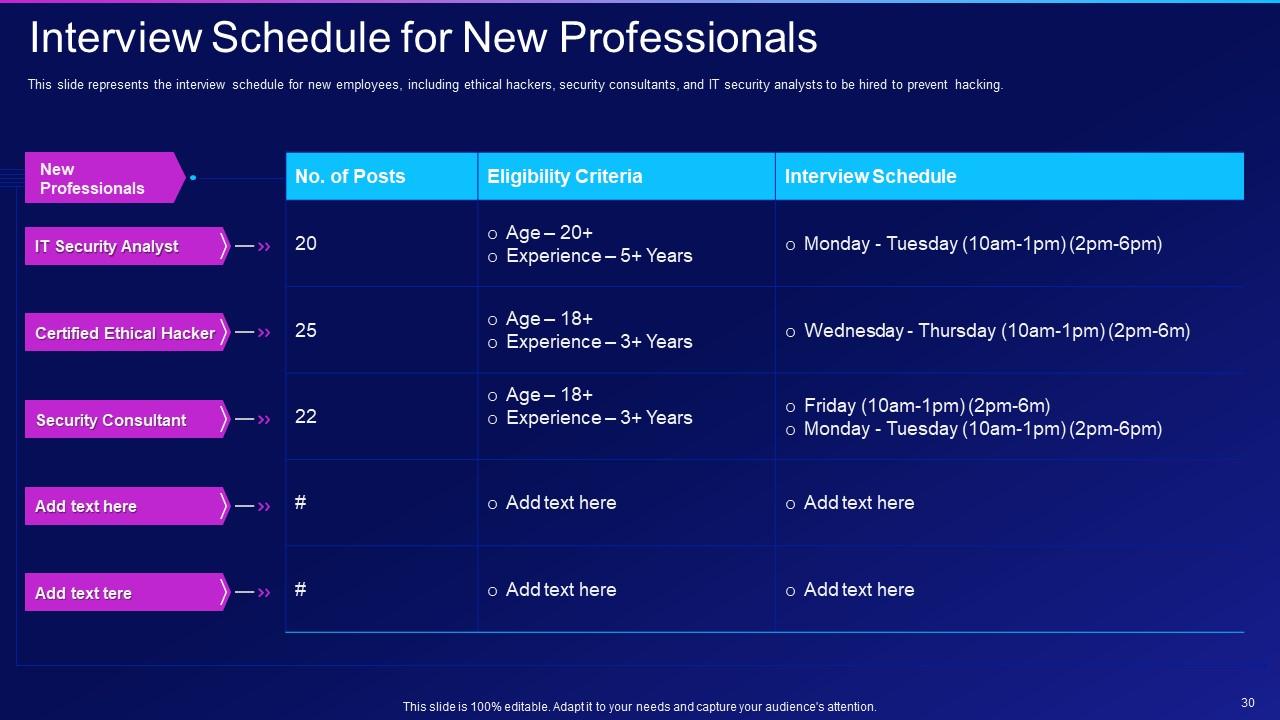
Slide 30: This slide represents the interview schedule for new employees, including ethical hackers.
Slide 31: This slide displays budget for newly recruited professionals, including new professionals.
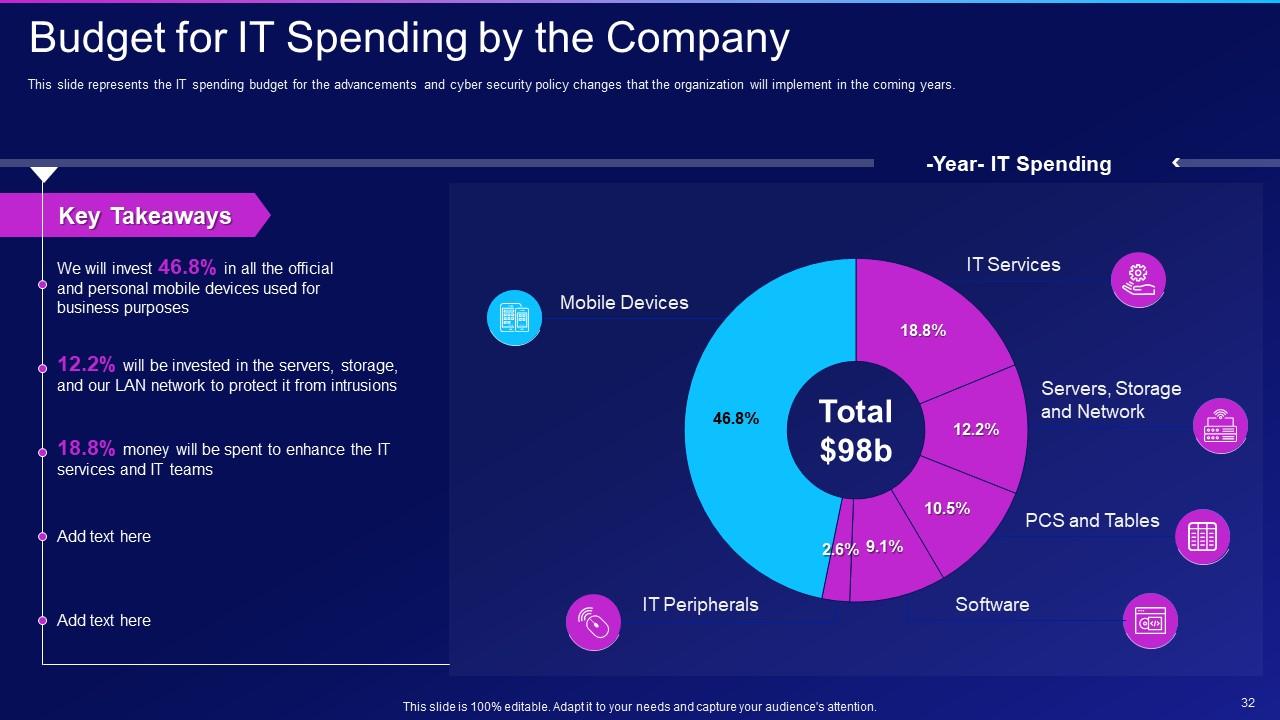
Slide 32: This slide showcases Budget for IT Spending by the Company.
Slide 33: This slide shows title for topics that are to be covered next in the template.
Slide 34: This slide presents the impact of ethical hackers on business by describing the decreased number of malicious attacks.
Slide 35: This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients.
Slide 36: This slide describes the regaining company’s reputation through regaining customers’ trust.
Slide 37: This slide shows title for topics that are to be covered next in the template.
Slide 38: This slide presents 30-60-90 Days Plan for New Strategies Implementation.
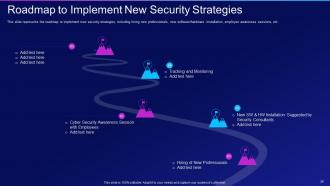
Slide 39: This slide displays Roadmap to Implement New Security Strategies.
Slide 40: This slide depicts the dashboard for threat tracking through cyber security measures.
Slide 41: This slide is titled as Additional Slides for moving forward.
Slide 42: This slide illustrates the overview of hacking and how businesses are getting affected by it every year.
Slide 43: This slide represents the phases of hacking, including reconnaissance, scanning, gaining access, etc.
Slide 44: This slide describes the common types of cybercrime such as identity theft, computer fraud, etc.
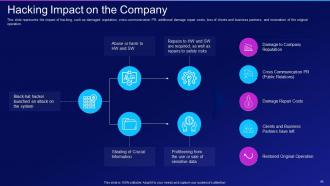
Slide 45: This slide showcases the impact of hacking, such as damaged reputation, crisis communication PR, etc.
Slide 46: This slide depicts ethical hacking and how ethical hackers could be an asset to a company.
Slide 47: This slide presents the purpose of ethical hacking, including the tools and tactics.
Slide 48: This slide displays the legality of ethical hacking, how ethical hackers work official permission.
Slide 49: This slide represents Icons for Hacking (IT).
Slide 50: This slide describes Line chart with two products comparison.
Slide 51: This is Our Mission slide with related imagery and text.
Slide 52: This slide shows Post It Notes. Post your important notes here.
Slide 53: This slide contains Puzzle with related icons and text.
Slide 54: This is a Comparison slide to state comparison between commodities, entities etc.
Slide 55: This is an Idea Generation slide to state a new idea or highlight information, specifications etc.
Slide 56: This slide depicts Venn diagram with text boxes.
Slide 57: This is a Timeline slide. Show data related to time intervals here.
Slide 58: This is a Thank You slide with address, contact numbers and email address.
Hacking it powerpoint presentation slides with all 63 slides:
Use our Hacking IT Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
FAQs
Ethical hacking is crucial as it helps organizations identify vulnerabilities in their systems before cybercriminals exploit them. Ethical hackers simulate cyber-attacks to check for weaknesses in networks, software, and systems, and then provide recommendations to improve the security posture.
Some common types of cyber-attacks include identity theft, computer fraud, privacy breach, ransomware, phishing, and malware attacks.
To become an ethical hacker, one needs to have skills in areas such as networking, programming, and computer systems. It is also essential to have certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and SANS GPEN.
Organizations recruit ethical hackers to strengthen their cybersecurity measures, protect customer information, raise security awareness, and prevent future cyber-attacks by identifying vulnerabilities in their systems.
The five phases of ethical hacking are reconnaissance, scanning, gaining access, maintaining access, and covering tracks. In the reconnaissance phase, attackers use foot printing techniques to gather information about the target system, while in the scanning phase, they use tools to scan for vulnerabilities. In the gaining access phase, attackers try to exploit the vulnerabilities found in the previous phases to gain access to the target system. The maintaining access phase involves attackers maintaining their access to the target system, while in the covering tracks phase, they try to cover their tracks to avoid detection.
-
Very unique, user-friendly presentation interface.
-
Illustrative design with editable content. Exceptional value for money. Highly pleased with the product.
-
Excellent products for quick understanding.