Comprehending Cyber Threats Training Ppt
The PowerPoint Training Module on Comprehending Cyber Threats offers an insightful overview of various cyber threats, each posing unique risks in the digital realm. It starts with Spyware, detailing software that secretly gathers user information. It then moves to Social Engineering, highlighting how deception manipulates individuals into divulging confidential information. Ransomware Attacks are covered next, focusing on malware that encrypts data and demands ransom for access. Trojan Horses are discussed, revealing malicious programs disguised as legitimate software. Cryptojacking, a newer threat, is explained as the unauthorized use of someones computer to mine cryptocurrency. The section on Malvertising Attacks delves into the use of online advertising for spreading malware. Finally, Adware is examined, emphasizing software automatically displaying or downloading advertising material. It also has Key Takeaways and Discussion Questions related to the topic to make the training session more interactive. The deck contains PPT slides on About Us, Vision, Mission, Goal, 30-60-90 Days Plan, Timeline, Roadmap, Training Completion Certificate, and Energizer Activities.
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Training Deck on Comprehending Cyber Threats. This deck comprises of 90 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 3
This slide gives an overview of spyware attacks. Spyware is malicious software installed on a computing device without the end user's knowledge.
Slide 4
This slide depicts the working of spyware. Spyware can infect a device without the end user's knowledge through an app install package, malicious website, or file package.
Instructor’s Notes: Spyware may also track web browsing history, passwords, and other private information, such as email addresses, credit card numbers, personal identification numbers, or banking information.
Slide 5
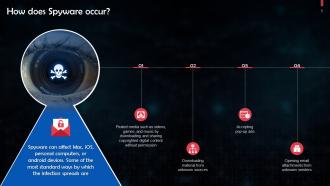
This slide discusses how spyware infections occur. Some common ways are: Users accepting pop-up ads and opening email attachments from unknown senders.
Slide 6
This slide highlights types of spyware. These are: Adware, keyboard loggers, trojans, and mobile spyware.
Slide 7
This slide lists common types of spyware. These are: CoolWeb Search, Emotet, Zlob, DarkHotel, and Gator.
Slide 8
This slide discusses ways to prevent spyware. You can do so by enabling 2FA, downloading software only from reliable sources.
Slide 9
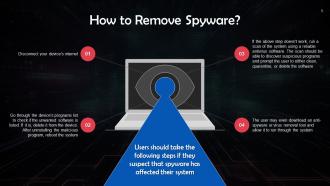
This slide lists steps to be followed in case a user detects spyware on their device. They must disconnect the device’s internet connection and check the programs list to delete any suspicious software.
Slide 10
This slide introduces anti spyware tools. While some anti-spyware programs operate only when the scan is manually performed, others monitor computer activity continuously to make sure spyware cannot record the user's information.
Slide 11
This slide gives an overview of social engineering cyber attacks. Social engineering is used to describe a wide range of malicious activities carried out through human interactions.
Slide 12
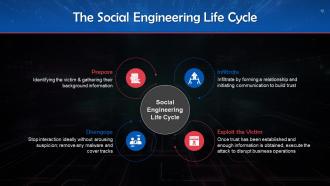
This slide depicts the social engineering lifecycle. The steps are as follows: Prepare, infiltrate, exploit the victim, and disengage.
Slide 13
This slide lists types of social engineering techniques. These are baiting, pretexting, scareware, phishing, watering hole attacks, and access tailgating.
Slide 14
This slide talks about baiting, a social engineering technique. Baiting attacks use a fake promise to pique a victim’s curiosity or greed. They trick users into falling for a trap that steals their confidential information or inflicts their devices with malware.
Slide 15
This slide discusses pretexting which is a social engineering technique. Pretexting uses a false identity as the “pretext” for building trust, such as directly impersonating a vendor or a facility employee.
Slide 16
This slide talks about scareware which is a social engineering technique. Scareware is a type of malware designed to scare you into taking action. This malicious malware sends warnings that report fake malware infections or claim that one of your accounts has been compromised.
Slide 17
This slide revisits phishing which can be considered as a social engineering technique. Phishing scams are email or text message campaigns devised to trick people into divulging sensitive or financial information about themselves.
Slide 18
This slide talks about watering hole attacks. These attacks target popular websites with malware to affect multiple users simultaneously.
Slide 19
This slide gives information about access tailgating which is a social engineering technique. Tailgating, also known as piggybacking, is following an authorized employee into an area with limited access.
Slide 20
This slide highlights two unusual techniques of social engineering. These are traditional mail malware distribution and fax-based phishing.
Slide 21
This slide talks about fax-based phishing to execute a social engineering attack. Cybercriminals sometimes use unusual methods such as fax instead of the usual email or internet routes to mislead people into revealing their private information.
Slide 22
This slide discusses traditional mail malware distribution as a type of social engineering technique. Cybercriminals once used a home-delivery service in Japan to distribute CDs infected with Trojan spyware.
Slide 23
This slide highlights questions to ask yourself if you suspect a social engineering attack.
Slide 24
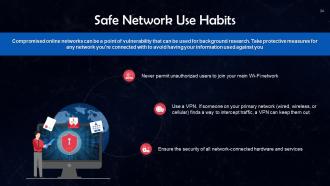
This slide lists safe network use habits. Compromised online networks can be a point of vulnerability that can be used for background research. To avoid having your information used against you, take protective measures in any network you’re connected to.
Slide 25
This slide lists safe communication and account management habits. It is essential to be careful while communicating online, as social media, email, and text messages are common targets.
Slide 26
This slide lists safe device use habits. Keeping your devices safe is just as important as all your other online habits.
Slide 27
This slide gives an introduction to ransomware attacks. Ransomware is a type of malware created to deny a user or organization access to files on their computer.
Slide 28
This slide discusses how ransomware attacks work. The first step in a ransomware attack is to infect the target system, followed by data encryption, and lastly the ransom demand.
Slide 29
This slide gives information about infection and distribution vectors in ransomware attacks. Ransomware can gain access to an organization’s systems by phishing emails or specific infection vectors that use services such as Remote Desktop Protocol.
Slide 30
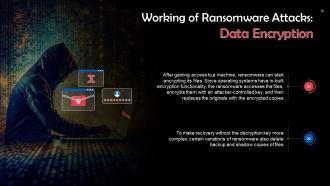
This slide talks about data encryption in ransomware attacks. After gaining access to a machine, ransomware can start encrypting its files. Since operating systems have in-built encryption functionality, the ransomware accesses the files, encrypts them with an attacker-controlled key, and then replaces the originals with the encrypted copies.
Slide 31
This slide gives information about ransom demand in ransomware attacks. After all the files have been encrypted, the ransomware makes a ransom demand. This is usually done by changing the display background to a ransom note or adding text files (with the ransom note) to each encrypted directory.
Slide 32
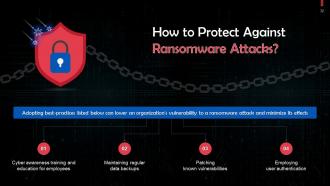
This slide highlights best practices for protection against ransomware attacks. These are: Regular cyber awareness training, maintaining regular data backups.
Slide 33
This slide talks about reducing the attack surface to protect against ransomware attacks. To reduce the attack surface, address the following: Phishing messages, mobile malware, unpatched vulnerabilities, and, remote access solutions.
Slide 34
This slide discusses how deploying anti-ransomware solutions can help in mitigating ransomware attacks.
Slide 35
This slide illustrates steps that active ransomware infection. Most ransomware attacks are detected only after data encryption is done ; however, some steps must be taken immediately.
Instructor’s Notes:
- Quarantine the system: Some ransomware strains attempt to spread to other computers and associated drives. You can control its spread by blocking access to other potential recipients
- Leave the PC on: A computer may become unstable if files are encrypted, and you can lose volatile memory when a computer is turned off can happen. Keep the computer running to increase the likelihood of recovery
- Create a backup: For some ransomware versions, decrypting files is possible without paying the ransom. Create a backup of any encrypted files on a removable drive in case a solution is available in the future. Files are damaged during an unsuccessful decryption attempt
- Check for decryptors: Check with the No More Ransom Project to check if a free decryptor is available. If so, run it on a copy of the encrypted data to see if it can restore the files
- Ask for help: Computers sometimes keep backup copies of files stored on them. A digital forensics expert may be able to recover these copies if the malware has not deleted them
- Wipe and restore: Restore the system from a clean backup or operating system installation. This ensures that the malware is completely deleted from the device
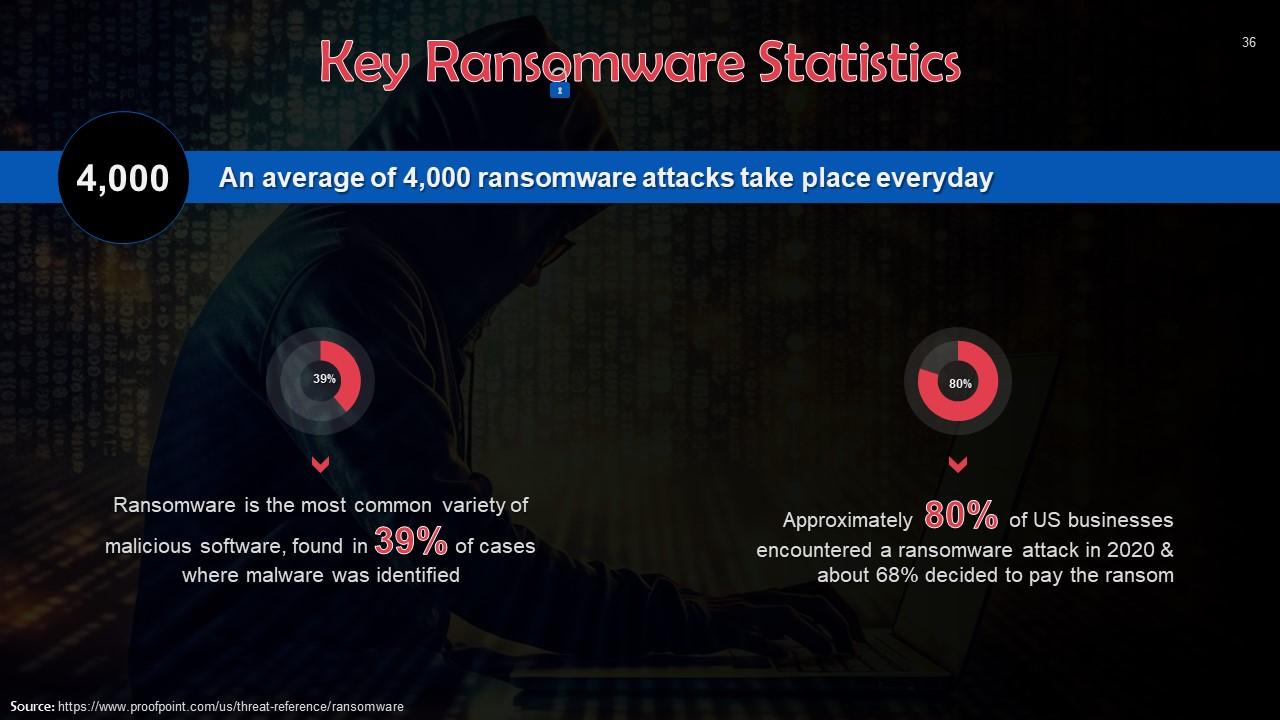
Slide 36
This slide depicts key statistics on ransomware attacks.
Slide 37
This slide gives an overview of Trojan Horses. A Trojan Horse is a form of malware that poses as legitimate code or software.
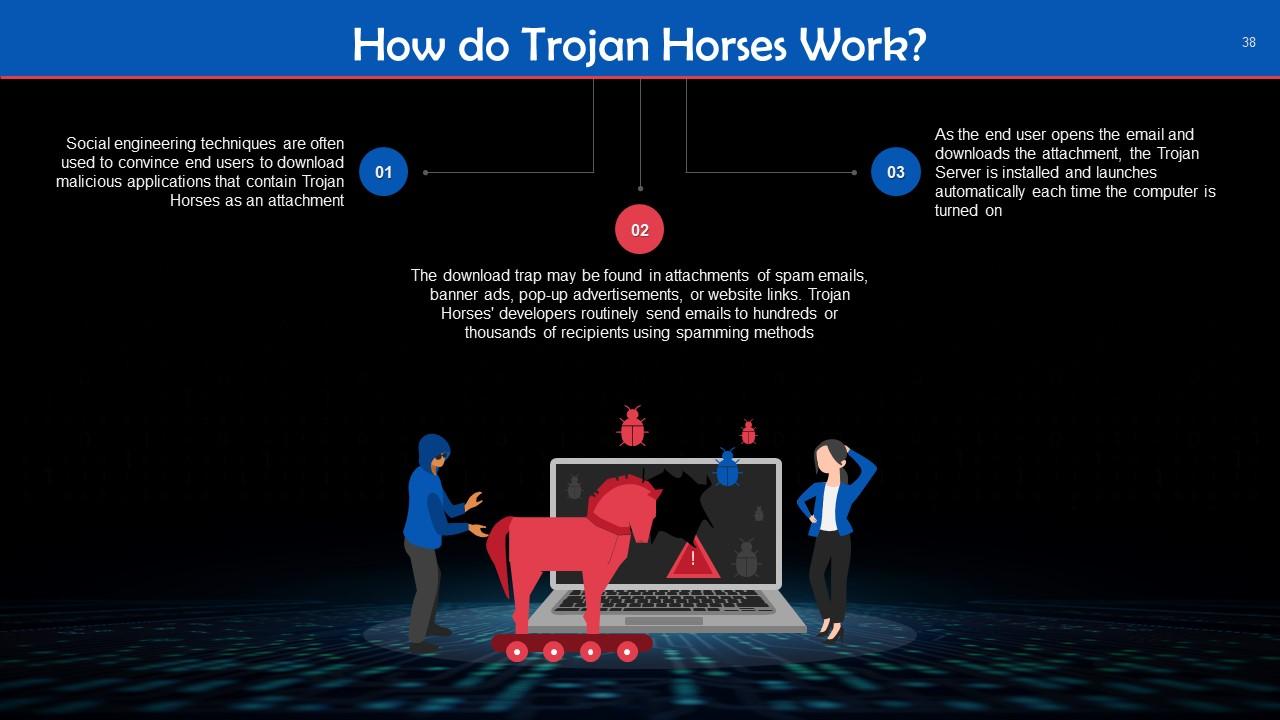
Slide 38
This slide discusses the working of Trojan Horses. Social engineering techniques are often used to convince end users to download malicious applications that contain Trojan Horses as an attachment.
Slide 39
This slide talks about how a trojan horse negatively affects a computer. Once a Trojan horse becomes active, it can negatively affect the computer's performance and put sensitive user data at risk.
Slide 40
This slide discusses whether trojan horse is a virus or a malware. To classify a trojan as a virus is incorrect because, unlike a virus or worm, Trojan malware cannot replicate itself or self-execute. It requires specific and deliberate action from the user.
Slide 41
This slide highlights types of trojan horses. These are: Ransom trojan, backdoor trojan, downloader trojan, DDoS trojan, exploit trojan, rootkit trojan, SMS trojan, fake AV trojan, trojan game thief, and banking trojan.
Instructor’s Notes:
- Ransom trojan: This Trojan malware demands ransom from users in exchange for the restoration of an infected device and its contents
- Backdoor trojan: The threat actor sets up access points to the network using this malware
- Downloader trojan: This type of trojan typically targets already compromised devices and installs a new version of malicious software on the device
- DDoS trojan: These can be deployed to multiple devices to create a botnet, or a zombie network, which can then be used to execute a DDoS attack
- Exploit trojan: As their name suggests, these Trojans identify and take advantage of vulnerabilities within software applications to gain access to the system
- Rootkit trojan: Rootkits operate close to or within the operating system's kernel, which gives them the capability to initiate commands to the computer. This trojan provides unauthorized access to threat actors. It is challenging to detect as it can conceal its presence on the infected device
- SMS trojan: This is a mobile device attack in which the Trojan malware can send and intercept text messages. It can also generate revenue by sending SMS messages to premium-rate numbers
- Fake AV trojan: Disguised as antivirus software, this trojan is ransomware that demands users to pay to detect or remove threats. The issues that the program claims to have found are usually fake
- Trojan game thief: This trojan targets online gamers and attempts to access their gaming account login information
- Banking trojan: This trojan targets financial accounts and is created to steal data related to bank accounts, credit or debit cards, or other online payment systems
Slide 42
This slide lists types of Trojan horses. These are: QakBot, Andromeda, and Night Spider’s Zloader.
Slide 43
This slide gives information about QakBot, which is a type of trojan horse. QakBot is an eCrime banking trojan which can spread throughout a network using a worm-like functionality.
Slide 44
This slide talks about Andromeda, which is a type of trojan horse. A modular trojan known as Andromeda is primarily employed as a downloader to spread additional malware payloads, such as banking Trojans
Slide 45
This slide gives information about Night Spider’s Zloader, which is a type of trojan horse. Zloader disguises itself as legitimate programs such as Zoom, Atera, Brave Browser, NetSupport, JavaPlugin, and TeamViewer installers.
Slide 46
This slide tells us how to identify trojan horses. The following signs can indicate the presence of a trojan horse on a device: A change in the computer's screen, excessive amounts of pop-up ads.
Slide 47
This slide discusses how to protect against a trojan horse attack. Adopting responsible online conduct and taking a few simple preventive steps are the best ways to safeguard against Trojan horse attacks.
Slide 48
This slide gives information about the removal of a trojan horse. A system should be immediately disconnected from the Internet if a trojan horse is identified. Suspicious files must be identified and removed using an antivirus/antimalware software or by reinstalling the operating system.
Slide 49
This slide gives an overview of cryptojacking. Cryptojacking is a cybercrime in which a hacker hijacks the computing resources of another party to mine cryptocurrency.
Slide 50
This slide discusses the working of cryptojacking. The hacker infects the website or open-source code, which enables discreet download of crypto mining software on the victim’s system. This software then surreptitiously mines cryptocurrency for the hacker using the victim’s resources.
Slide 51
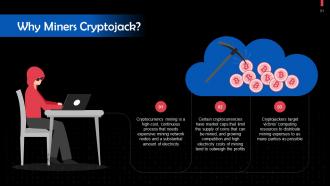
This slide highlights the reason behind cryptojacking. Cryptocurrency mining is a high-cost, continuous process that needs expensive mining network nodes and a substantial amount of electricity, which can outweigh the profits and ultimately lead miners to cryptojack. Cryptojackers target victims' computing resources to distribute mining expenses to as many parties as possible.
Slide 52
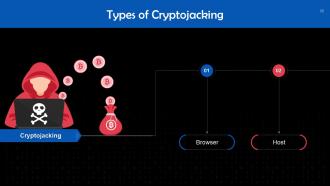
This slide depicts two types of cryptojacking. These are Browser and Host cryptojacking.
Slide 53
This slide talks about browser cryptojacking. The browser-based technique conceals code that instantly runs crypto mining software in a user's web browser when they visit the webpage hosting it.
Instructor’s Notes: Existing websites can be infected via programmatic advertising, which contains malware that automatically places ads on sites. This is done without knowledge of website owners, and they have little control over whether their site runs the software.
Slide 54
This slide gives information about Host cryptojacking. This technique functions like traditional phishing and malware attacks. Cryptojackers trick victims into clicking on links that seem harmless but that install crypto mining software onto a victim's device.
Slide 55
This slide lists signs to identify cryptojacking. These are: Poor device performance, battery overheating, higher electricity costs.
Slide 56
This slide highlights ways to prevent cryptojacking. You can do so by using strong protection against cyber attacks, blocking infected sites.
Slide 57
This slide gives information about malvertising attacks. In a malvertising attack, harmful code is injected into legitimate online advertising networks, and the code usually redirects users to malicious websites.
Slide 58
This slide depicts the effect of malvertising on users. Malvertising may carry out attacks against users viewing the malvertisement without clicking it , with the display of unwanted advertisements.
Slide 59
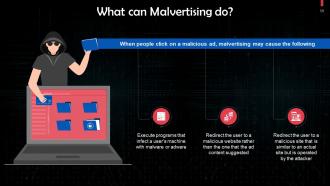
This slide discusses the harmful effects of malvertising. When people click on a malicious ad, malvertising may execute programs that infect a user's machine with malware or adware, and redirect the user to a malicious website.
Slide 60
This slide depicts the effect of malvertising on publishers. Publishers are at risk of having their reputations tarnished, losing customers and revenue, and facing legal implications because of the damage caused to users who happen to visit their sites.
Slide 61
This slide discusses how malware is inserted into ads. Attackers employ the below given delivery methods to insert harmful malware into advertisements.
Instructor’s Notes:
- Malware in ad calls: Whenever a website shows a page with an advertisement, the ad exchange pushes adverts to the user via multiple third parties. An attacker compromises one of these third-party servers and add malicious code to the ad payload
- Malware in an ad creative: A text or banner ad may contain malware. For instance, HTML5 allows for the delivery of advertisements as a combination of images and JavaScript, which may have dangerous code. Ad networks that deliver ads in Flash (.swf) format are very vulnerable to this
- Malware within a pixel: Pixels are pieces of code inserted in an ad or a landing page, which sends data to a server for tracking. A legitimate pixel only sends data. If an attacker intercepts a pixel’s delivery path, it can send a malicious code as a response to the user’s browser.
- Malware within a video: Video players do not defend against malware. For instance, third-party pixels from a standard video format called VAST may include malicious code. Videos can infect users by displaying a malicious URL at the end of the video
- Malware injected post-click: When a user clicks an advertisement, they are often redirected through several URLs before arriving at the ad landing page. Any compromised URL along this delivery chain allows the attacker to run malicious malware
- Malware on a landing page: There may be clickable elements that run malicious code even on legitimate landing pages that trustworthy websites provide. This type of malware is dangerous because users can click an ad, land on a real/legitimate landing page but still get infected by a malicious on-page element
- Malware within a flash video: Flash-based videos can inject an Iframe into the page that downloads malware, without the knowledge of the user
Slide 62
This slide discusses how users can mitigate the risk of malvertising. Antivirus software can protect against drive-by downloads or malicious code that malvertising executes.
Slide 63
This slide tells us how publishers can mitigate the risk of malvertising. Carefully examine ad networks and research ad delivery paths and security practices is the first and major step that you should take.
Slide 64
This slide gives the definition of adware. Adware or advertisement-supported software helps generate revenue for its developers by automatically displaying adverts on your screen, typically within a web browser.
Slide 65
This slide discusses the ways adware infects your computer. You may unknowingly download a free computer program or app with additional software that includes adware.
Slide 66
This slide highlights the difference between malvertising and adware. Malvertising involves malicious code initially placed on a publisher’s web page. However, adware targets only individual users.
Slide 67
This slide depicts the working of adware. Adware operates by discreetly installing itself on devices anticipating the user will click on an advertisement it shows them.
Instructor’s Notes: Adware may also track your browsing history to display ads that are relevant to you. Once developers have your location and browser history, they can generate more revenue from selling this information to third parties.
Slide 68
This slide highlights two types of adware. These are: Legitimate adware and potentially unwanted applications.
Slide 69
This slide talks about legitimate adware. Legitimate adware asks for your consent to run ads and software promos, offsetting developer costs so they can offer their software for free.
Instructor’s Notes: All developers, including reputable ones, produce legal adware, and giving away free products to clients is a legitimate and legal approach.
Slide 70
This slide talks about Potentially Unwanted Applications (PAUs). All programs you may not have chosen to install on your device are considered PUAs. .
Slide 71
This slide discusses legal deceptive adware PUA. Legal deceptive adware PUA may make it challenging to opt out of installing harmless third-party software. Legitimate adware sometimes uses this technique.
Slide 72
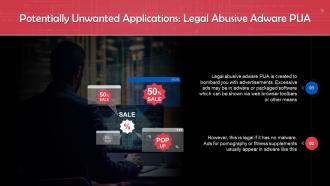
This slide gives information legal abusive adware PUA. Legal abusive adware PUA is created to bombard you with advertisements. Excessive ads may be in adware or packaged software which can be shown via web browser toolbars or other means.
Slide 73
This slide discusses Illegal malicious adware PUA. Illegal malicious adware PUA makes revenue for malicious third parties wanting to distribute malicious software such as viruses, spyware, or other malware onto devices.
Slide 74
This slide lists signs of an adware infection on a computer. Some of these include: Unexpected change(s) in your web browser home page, frequent crashing of the device, reduced internet speeds.
Slide 75
This slide gives the definition of mobile adware. Adware can also infect people's mobile phones through apps in popular categories such as gaming and entertainment. You may also fall prey to an app that spams you with ads.
Slide 76
This slide highlights signs of an adware infection on a mobile. These are: Phone gets slow, longer load time in apps.
Slide 77
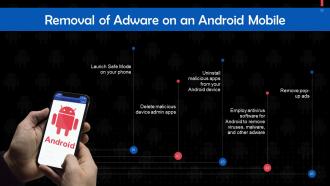
This slide discusses steps to remove adware from an android device.
Slide 78
This slide discusses steps to remove adware from an iPhone. It is seldom that the iPhone is infected with viruses, malware, or adware because of Apple's sandboxed approach and the fact that iOS apps don't interact with each other.
Slide 79
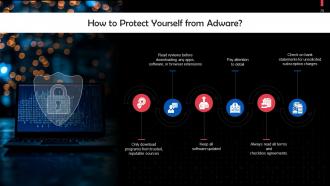
This slide lists tips to protect yourself from adware. These include: Keep all software updated, pay attention to detail.
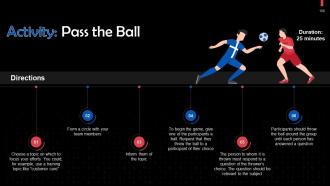
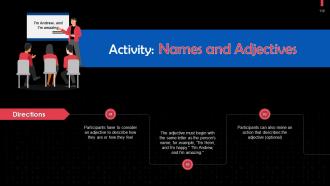
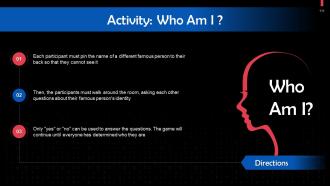
Slide 102 to 117
These slides contain energizer activities that a trainer can employ to make the training session interactive and engage the audience.
Comprehending Cyber Threats Training Ppt with all 126 slides:
Use our Comprehending Cyber Threats Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Like always a great experience with you guys. Always there on the drop of hat to help.
-
Satisfied with the way SlideTeam resolved my query regarding the right business PPTs that I was having difficulty finding. I found the perfect match with their assistance.