Understanding Components of Cybersecurity Training Ppt
The PPT Training Module on Understanding Components of Cybersecurity offers a comprehensive guide to the various facets of cybersecurity essential for safeguarding information and systems in the digital age. It kicks off with Information Security, highlighting strategies to protect sensitive data. Next, Application Security is addressed, focusing on securing software and applications against threats. The PowerPoint Deck then shifts to Network Security, emphasizing the importance of protecting the integrity and usability of network and data. End-User Security is another critical component that educates users about safe practices. Operational Security discusses securing operations and management processes. The final component, Disaster Recovery Planning, delves into strategies for recovering data and continuing operations in the event of a cyber incident.
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Training Deck on Understanding Components of Cybersecurity. This deck comprises of 116 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content and present it with confidence.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 3
This slide gives the definition of cybersecurity. The application of technology, techniques, and controls to defend systems, networks, programs, devices, and data against cyberattacks is known as cybersecurity.
Slide 4
This slide lists the components of cybersecurity. These are: Information security, application security, network security, end-user security, operational security, and disaster recovery planning.
Slide 5
This slide talks about information security. Information security includes the protection of company data as well as the data you obtain from clients, consumers, or vendors.
Slide 6
This slide gives an overview of Information Security Policy. A set of guidelines for using IT assets is known as an Information Security Policy (ISP).
Slide 7
This slide highlights common information security threats. These are: Unsecure systems, social engineering, social media attacks, lack of encryption, security misconfiguration, and malware or endpoints.
Slide 8
This slide discusses unsecure systems as an information security threat. The rapid advancement of technology frequently causes security precautions to be compromised. In many instances, systems are created without security considerations and continue to function as legacy systems within an enterprise.
Slide 9
This slide discusses how social engineering poses a threat to information security. Attackers use social engineering to lure users into actions that could jeopardize their security or reveal confidential information.
Instructor’s Notes: Technology solutions can also be employed to stop social engineering at its source or to stop people from performing risky actions like clicking on suspicious sites or downloading unknown attachments.
Slide 10
This slide tells us about social media attacks. People who use social media frequently inadvertently disclose personal information about themselves. Attackers can carry out direct cyber-attacks using social media, such as spreading malware through social media messaging.
Slide 11
This slide discusses lack of encryption as an information security threat. Data is encrypted through encryption operations, making it accessible only to users with secret keys. It is very effective and efficient in preventing data loss or corruption in case of loss of equipment or theft; it is extremely critical in case attackers compromise organizational systems.
Slide 12
This slide talks about security misconfiguration as an information security threat. Businesses use many technological platforms and tools, particularly web applications, databases, Software as a Service (SaaS) applications, or Infrastructure as a Service (IaaS) from providers like Amazon Web Services.
Instructor’s Notes: Another issue is "configuration drift," in which, despite competent IT security employees with good IT knowledge, proper security configuration can quickly go out of date and make a system insecure.
Slide 13
This slide discusses how malware on endpoints can pose a threat to information security. Malware is the main danger to all endpoints since it can be spread through varied channels, compromise the endpoint directly, and escalate privileges to other corporate systems.
Slide 14
This slide introduces the concept of active and passive attacks in Information Security. Information security aims to defend businesses against malicious attacks. The two main categories of such attacks are active and passive attacks.
Slide 15
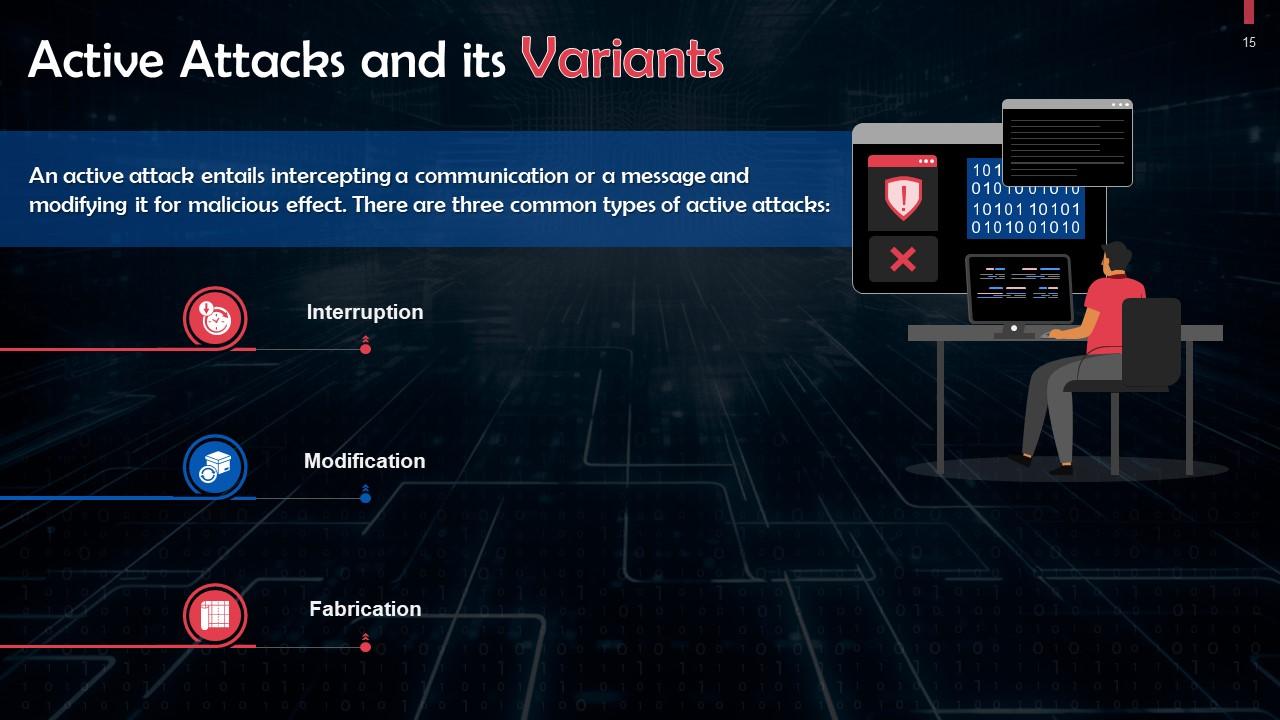
This slide provides information on active attacks and its variants. There are three common types of active attack. These are interruption, modification, and fabrication.
Instructor’s Notes:
- Interruption: The attacker interrupts the original communication and creates new, malicious messages, posing as one of the communicating parties
- Modification: The attacker uses existing communications and replays them to deceive one of the communicating parties or modifies the communication to gain an advantage
- Fabrication: Creates fake or synthetic communications, typically to achieve Denial of Service (DoS). This prevents users from accessing systems or performing routine operations
Slide 16
This slide gives us information about passive attacks. A passive attack involves a hacker monitoring a system and illicitly copying data without changing it. They then employ this information to breach target systems or disrupt networks.
Slide 17
This slide tabulates differences between active and passive attacks.
Slide 18
This slide gives information about application security. Application security is developing, adding, and testing security features in applications to prevent security vulnerabilities against threats like unauthorized access and modification.
Slide 19
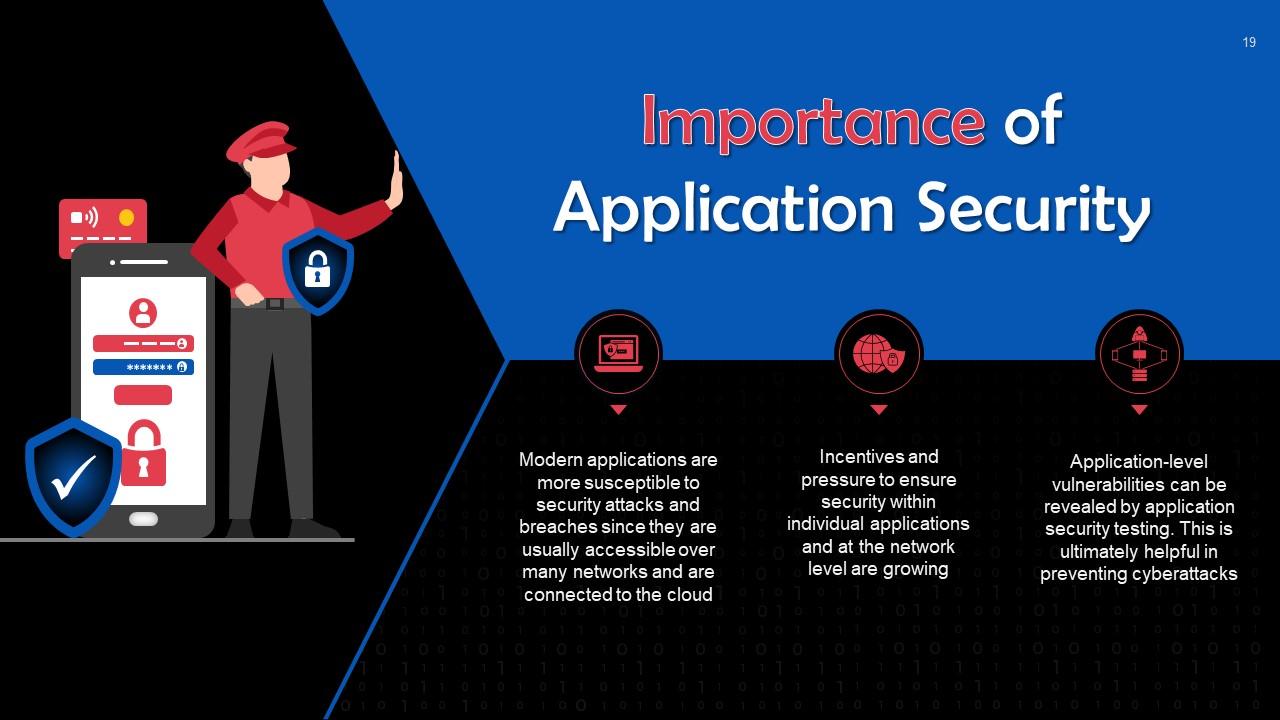
This slide discusses the importance of application security. Modern applications are more susceptible to security attacks and breaches since they are usually accessible over many networks and are connected to the cloud.
Slide 20
This slide gives information about application security controls. Application security controls strengthen an application's coding-level security, reducing its vulnerability to attackers.
Slide 21
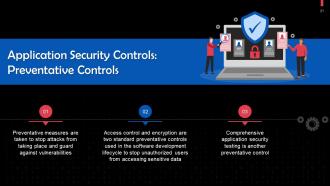
This slide tells us about preventative controls in application security. Preventative measures are taken to stop attacks from taking place and guard against vulnerabilities.
Slide 22
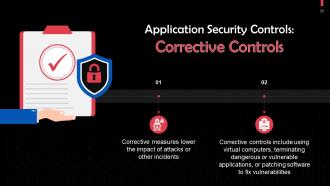
This slide discusses corrective controls in application security. Corrective controls include using virtual computers, terminating dangerous or vulnerable applications, or patching software to fix vulnerabilities.
Slide 23
This slide tells us about detective controls in application security. Detective controls are essential for a comprehensive application security architecture because these can, sometimes, be the sole means through which security experts determine an attack's occurrence
Slide 24
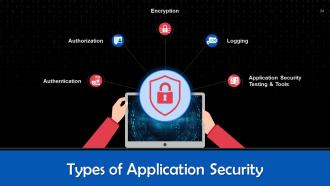
This slide highlights the types of application security. These are authentication, authorization, encryption, logging, and application security testing.
Slide 25
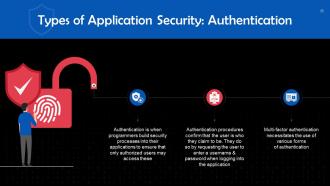
This slide talks about authentication as a type of application security. Authentication is when programmers build security procedures into their applications to guarantee that only authorized users may access these.
Slide 26
This slide discusses authorization as a type of application security. Following authentication, a user may be permitted to use the application. The system confirms that the user can use the program by comparing the user's identity to a list of authorized users
Slide 27
This slide talks about encryption as a type of application security. Sensitive data can be protected by encrypting the traffic between the end-user and the cloud in cloud-based apps.
Slide 28
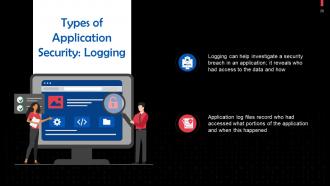
This slide discusses logging as a type of application security. Logging can help investigate a security breach in an application; it reveals who had access to the data and how.
Slide 29
This slide gives us information about application testing and tools. Application security testing ensures that all security controls are functioning efficiently and effectively.
Slide 30
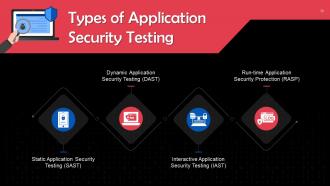
This slide highlights types of application security testing. These are Static Application Security Testing, Dynamic Application Security Testing, Interactive Application Security Testing, and Run-time Application Security Protection.
Slide 31
This slide talks about Static Application Security Testing (SAST). SAST assists in the detection of code vulnerabilities as it looks for the underlying cause in the application source files.
Slide 32
This slide talks about Dynamic Application Security Testing (DAST). DAST is a more proactive strategy, simulating security breaches on a live web application to provide precise information about exploitable vulnerabilities
Slide 33
This slide talks about Interactive Application Security Testing (IAST). IAST combines characteristics of SAST and DAST. It conducts an analysis from within the application in real-time or at any point during the development or production process
Slide 34
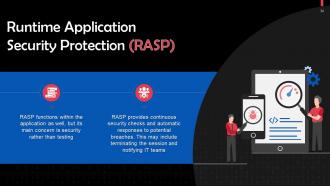
This slide talks about Runtime Application Security Protection (RASP). RASP functions within the application as well, but its main concern is security rather than testing.
Slide 35
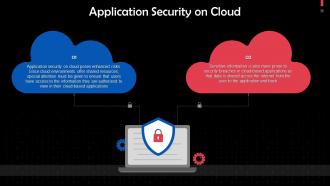
This discusses application security on cloud. Application security in the cloud poses some enhanced risks. Since cloud environments offer shared resources, special attention must be given to ensure that users have access to the information they are authorized to view in their cloud-based applications.
Slide 36
This slide tells us about mobile application security. Mobile devices are more vulnerable to attacks since they send and receive data over the internet instead of a private network.
Slide 37
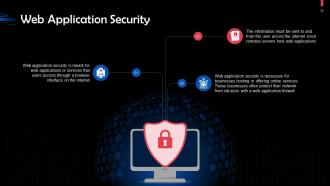
This slide discusses web application security. Web application security is meant for web applications or services that users access through a browser interface on the internet
Instructor’s Notes: A web application firewall works by inspecting and, if necessary, blocking data packets considered harmful.
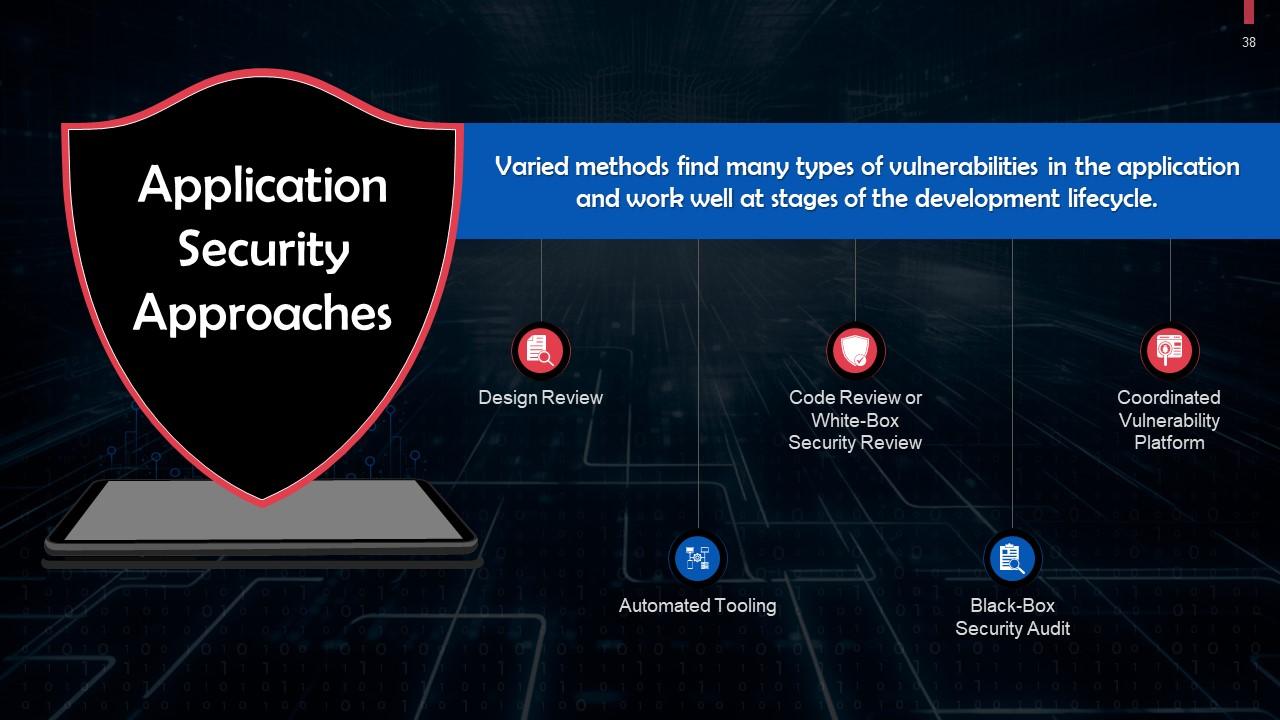
Slide 38
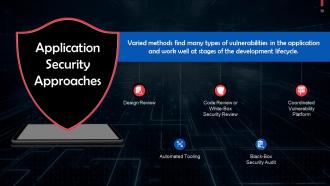
This slide highlights application security approaches. These are design review, automated tooling, code review, black-box security audit, and coordinated vulnerability platform.
Slide 39
This slide talks about design review as an application security approach. The application's architecture and design can be checked for security issues before writing the code.
Slide 40
This slide discusses Automated Tooling as an application security approach. Many security tools can be automated by incorporating them into the development or testing procedure.
Slide 41
This slide talks about Code Review or White-Box Security Review as an application security approach. A security engineer examines the application with a manual inspection of the source code and searching for security flaws.
Slide 42
This slide discusses the Black-Box Security Audit as an application security approach. This test seeks to replicate a situation in which external attackers target and try to compromise your systems in the real world.
Slide 43
This slide discusses talks about Coordinated Vulnerability Platform as an application security approach. Many websites and software providers offer hacker-powered application security solutions via which individuals can be recognized and compensated for reporting flaws or bugs.
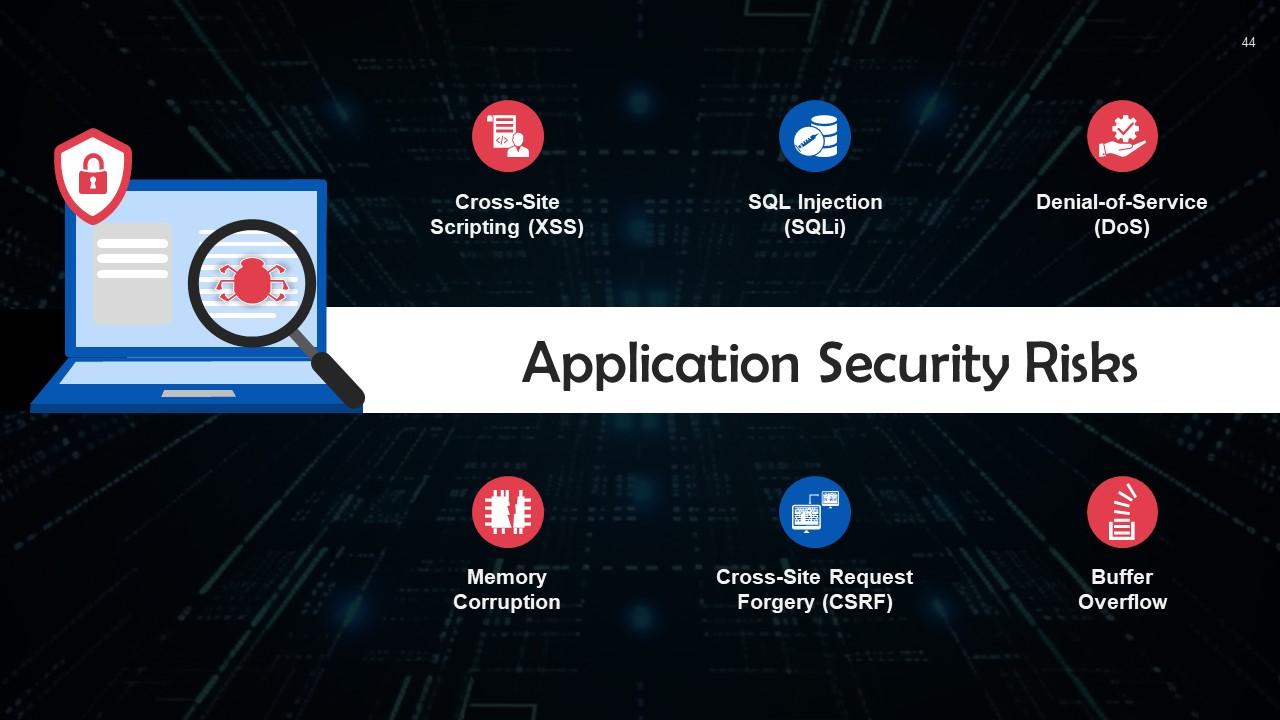
Slide 44
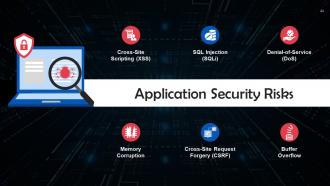
This slide lists application security risks. These are: Cross-Site Scripting (XSS), SQL injection, Denial-of-Service, memory corruption, cross-site request forgery, and buffer overflow.
Slide 45
This slide discusses cross-site scripting as a risk of application security. In Cross-Site Scripting attacks, malicious scripts are injected into benign and trustworthy websites. XSS attacks take place when an attacker sends malicious code, usually as a browser-side script, to a separate end-user using an online application.
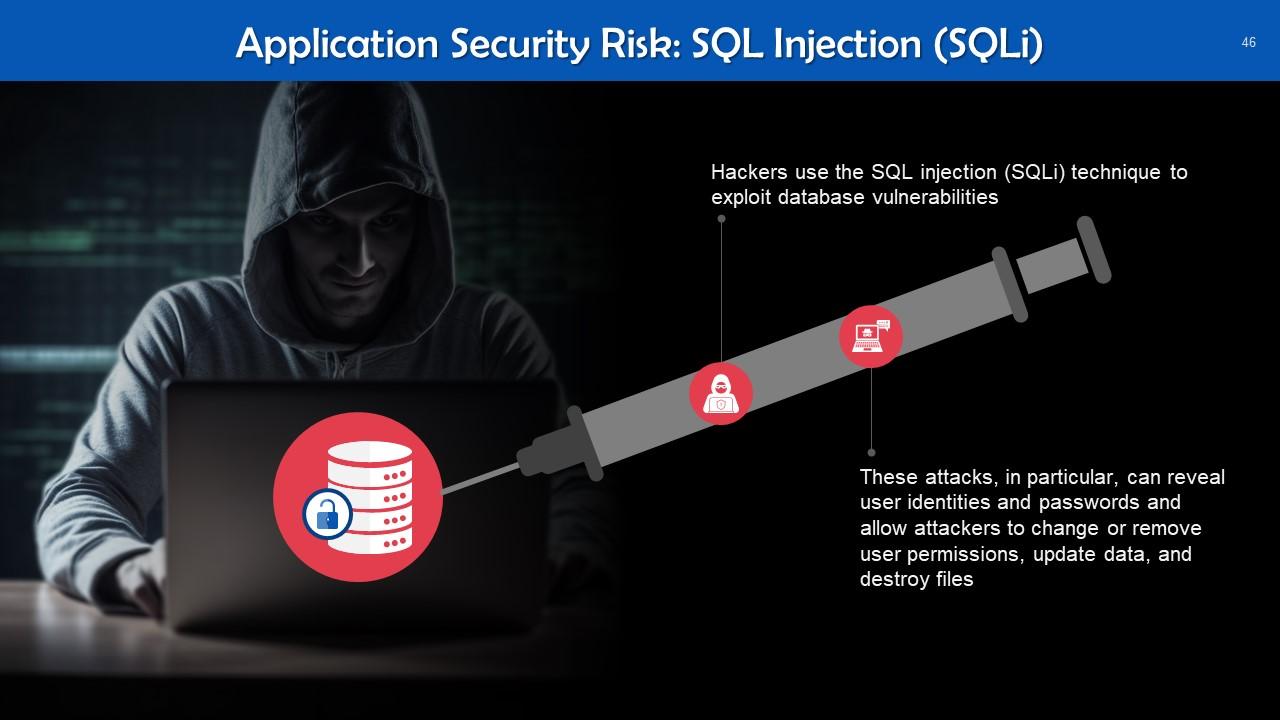
Slide 46
This slide gives information about SQL Injection as a risk of application security. Hackers employ the SQL injection (SQLi) technique to exploit database vulnerabilities.
Slide 47
This slide talks about Denial-of-Service (DoS) as a risk of application security. Remote attackers may use DoS and Distributed Denial-of-Service (DDoS) attacks to bombard a targeted server or the infrastructure that supports it with false, non-genuine traffic.
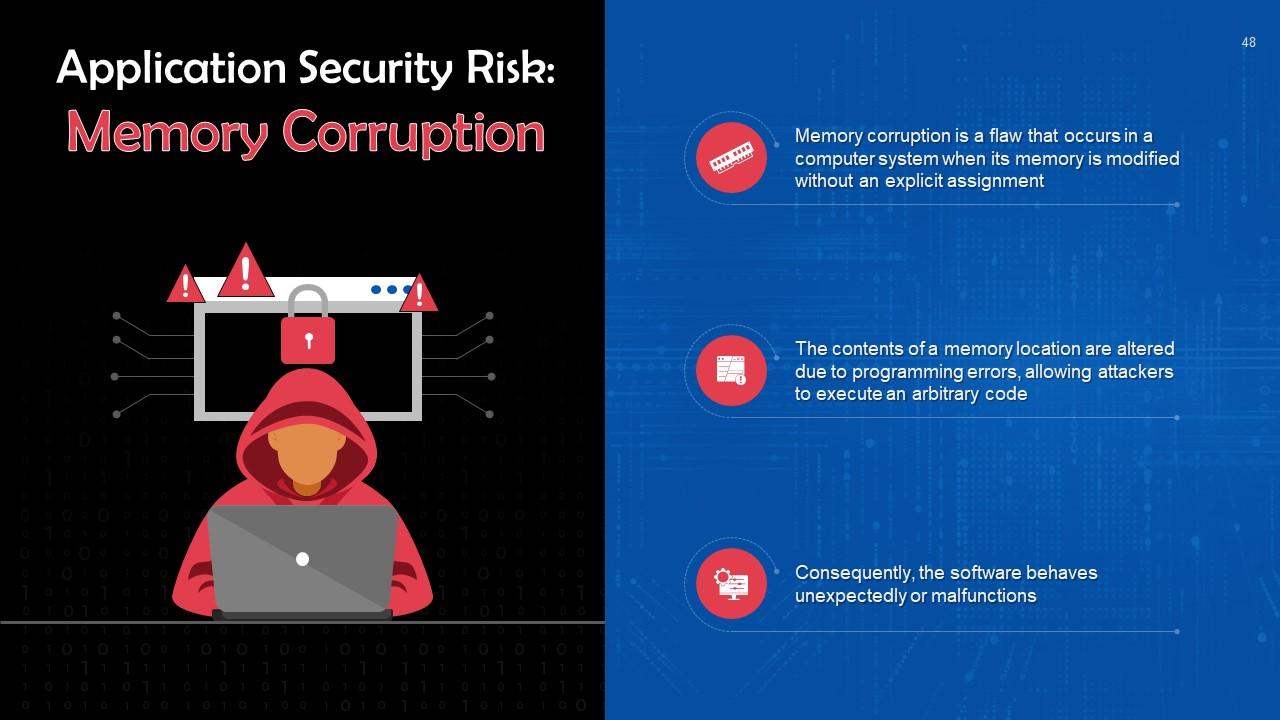
Slide 48
This slide discusses memory corruption as a risk of application security. Memory corruption is a flaw that occurs in a computer system when its memory is modified without an explicit assignment.
Slide 49
This slide talks about cross-site request forgery as a risk of application security. Hackers use Cross-Site Request Forgery (CSRF) to impersonate authorized users after tricking them into submitting an authorization request.
Slide 50
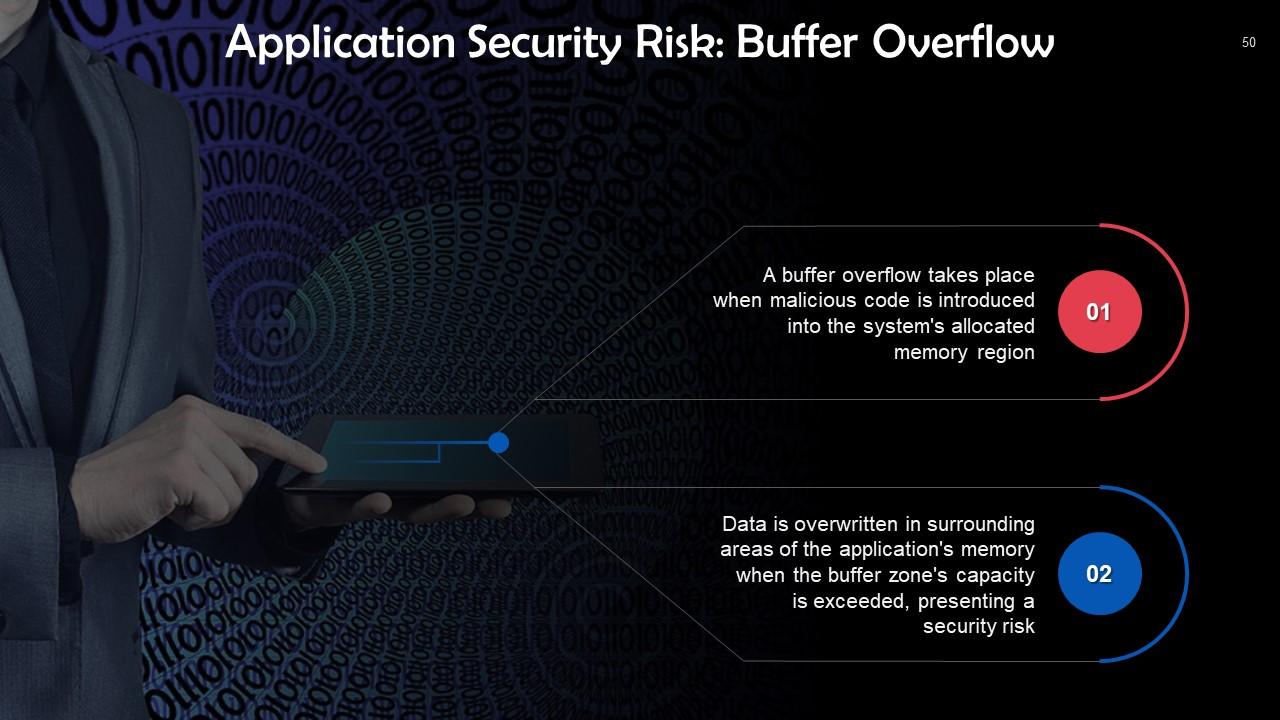
This slide talks about buffer overflow as a risk of application security. A buffer overflow takes place when malicious code is introduced into the system's allocated memory region.
Slide 51
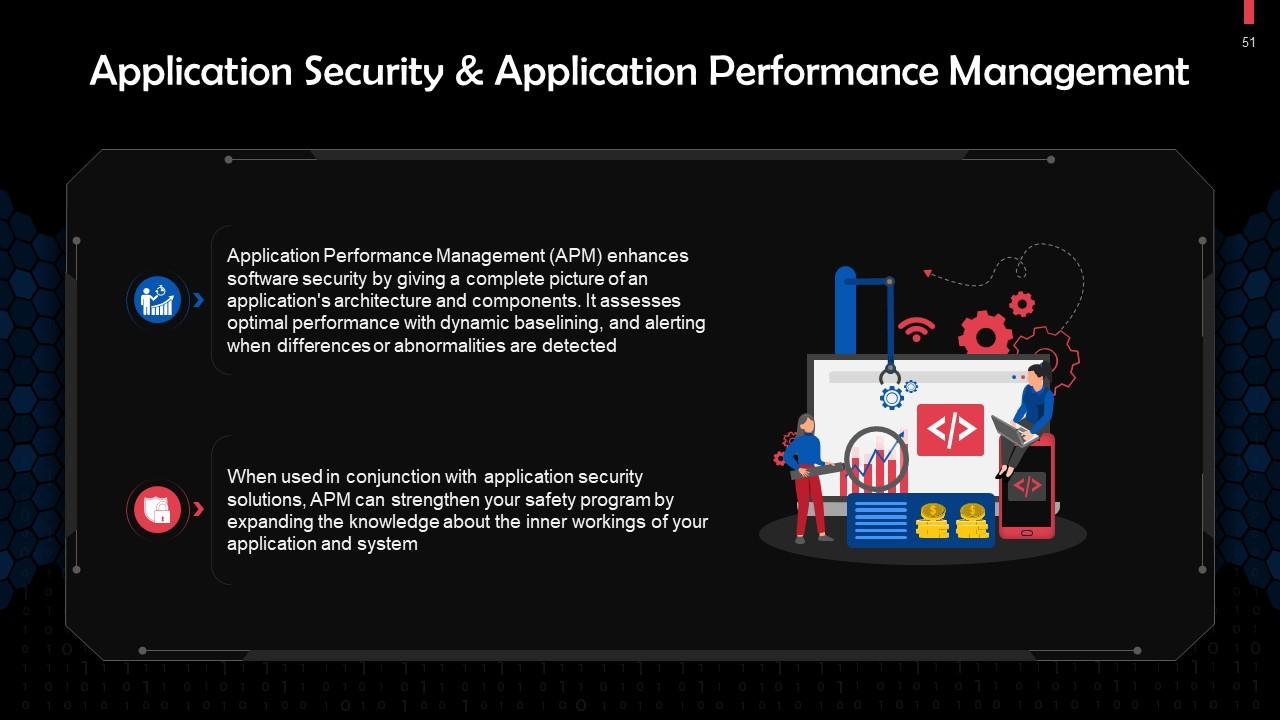
This slide gives information about Application Performance Management (APM). The APM data can help enhance software security by giving a complete picture of an application's architecture and components, assessing optimal performance with dynamic baselining, and alerting when differences or abnormalities are detected.
Slide 52
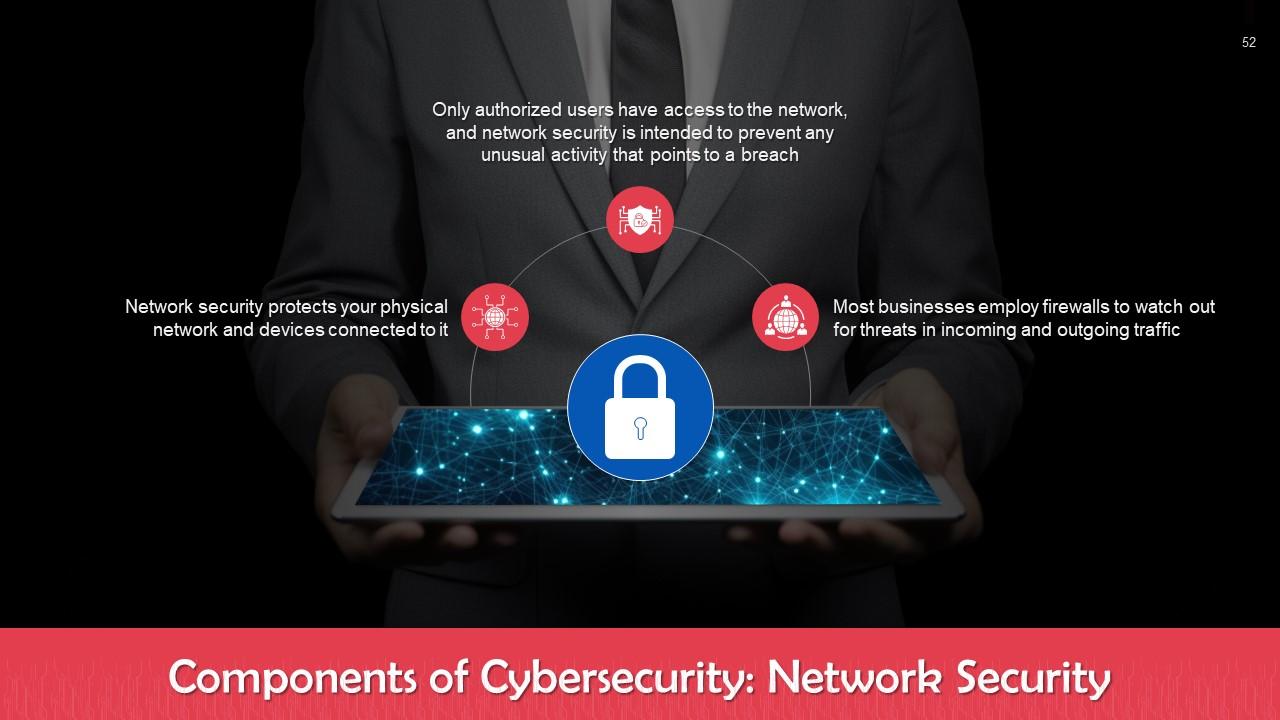
This slide talks about network security. Network security protects your physical network and devices connected to it.
Slide 53
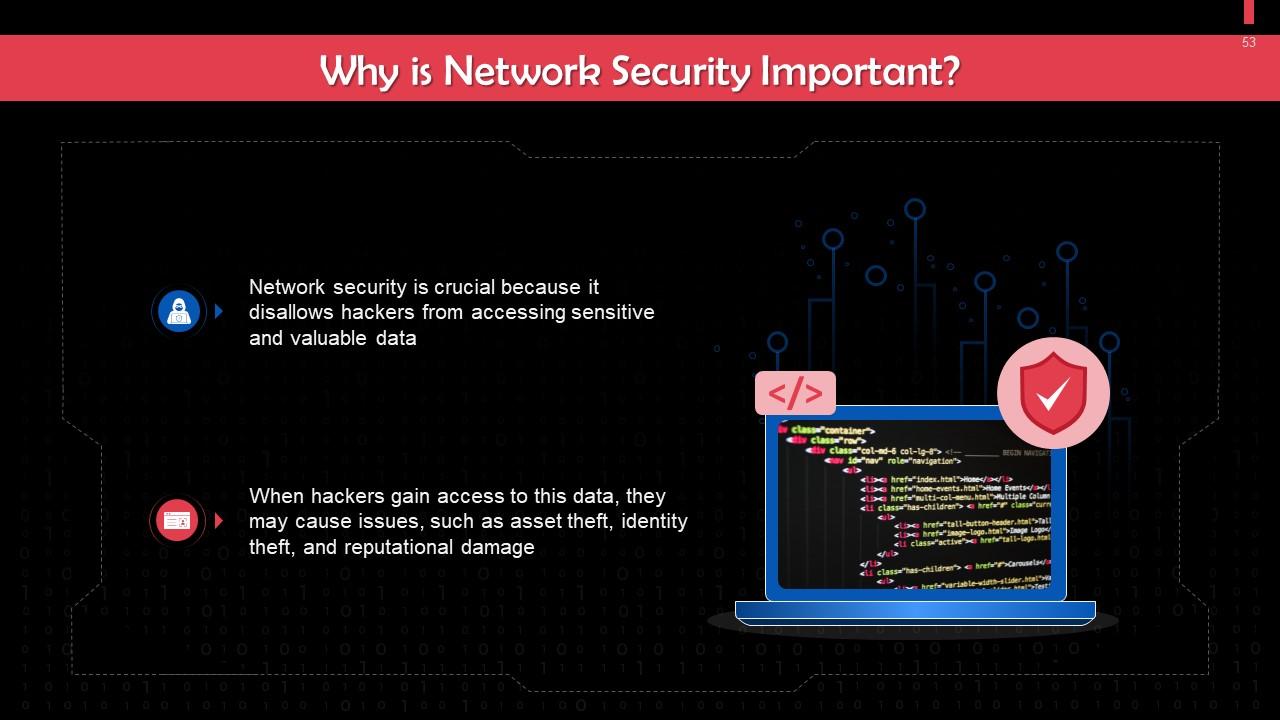
This slide discusses the importance of network security. Network security is crucial because it prevents hackers from accessing sensitive and valuable data.
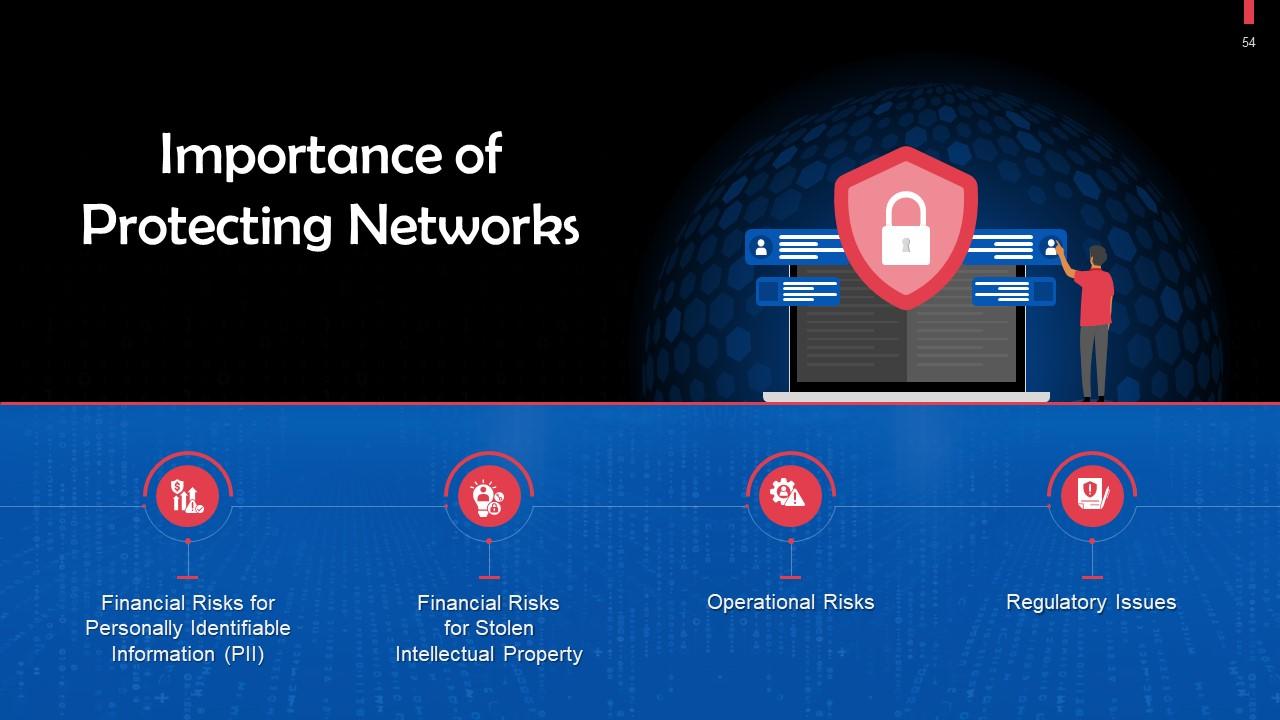
Slide 54
This slide highlights reasons for protecting networks. These are: Financial risks for Personally Identifiable Information (PII), or stolen intellectual property, operational risks, and regulatory issues.
Instructor’s Notes:
- Financial Risks for Personally Identifiable Information: Both individuals and corporations may incur costs as a result of data breaches. Companies that handle PII, such as passwords and Social Security numbers, must keep data secure. The victims of exposure may incur expenses like fines, restitution, and repairs for compromised devices
- Financial Risks for stolen Intellectual Property: It is expensive for businesses to have their intellectual property stolen. Loss of business and competitive advantages can result from losing a company's ideas, inventions, and products
- Operational Risks: Companies use networks for the majority of internal and external communication. Without sufficient network security, a company runs the danger of having its activities interrupted. Businesses and home networks rely on hardware and software that cannot function properly when infected with malware, viruses, or other cyberattacks.
- Regulatory Issues: Many governments have laws governing network security and data security that firms must follow. Breaking these rules may result in fines, bans, and even jail time
Slide 55
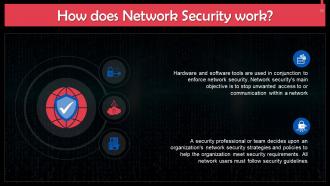
This slide gives information about the working of network security. Hardware and software tools are used in conjunction to enforce network security. Network security's main objective is to stop unwanted access to or communication within a network.
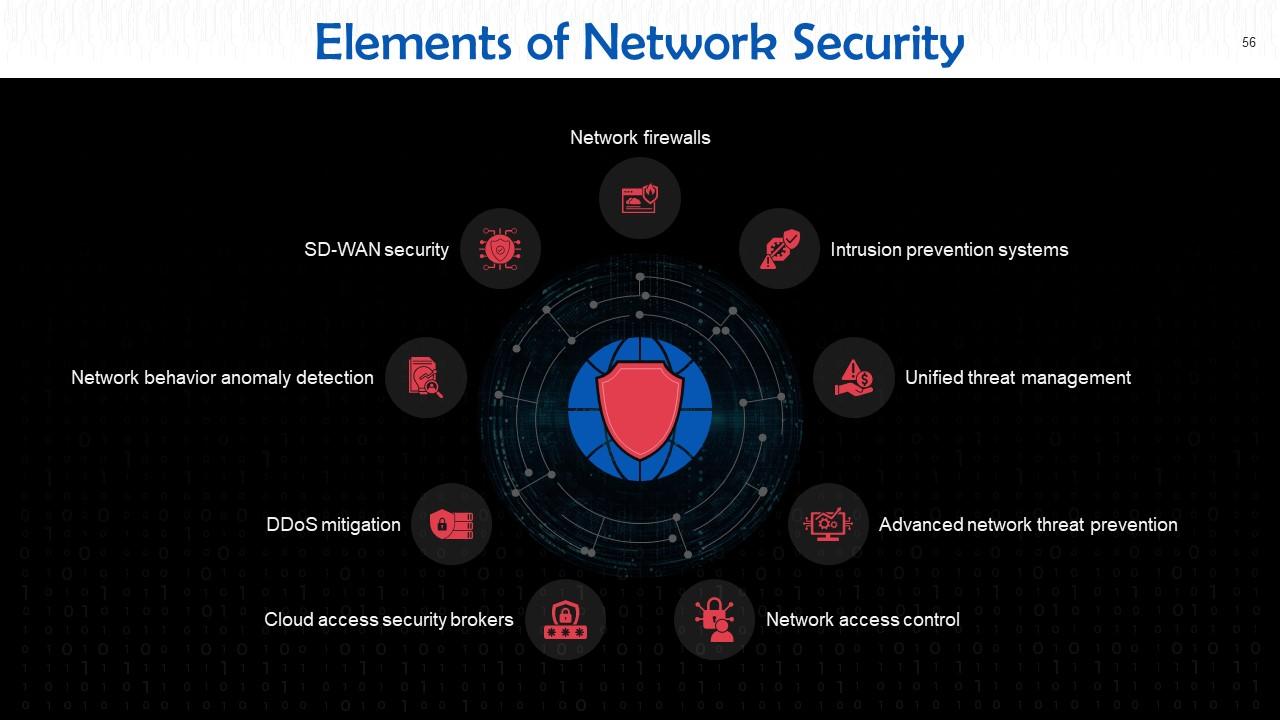
Slide 56
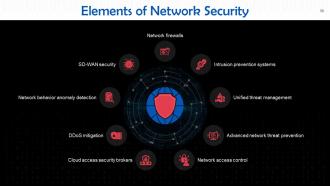
This slide highlights the nine elements of network security. These are: Network firewalls, intrusion prevention systems, unified threat management, advanced network threat prevention, network access control, cloud access security brokers, DDoS mitigation, network behavior anomaly detection, and SD-WAN security.
Slide 57
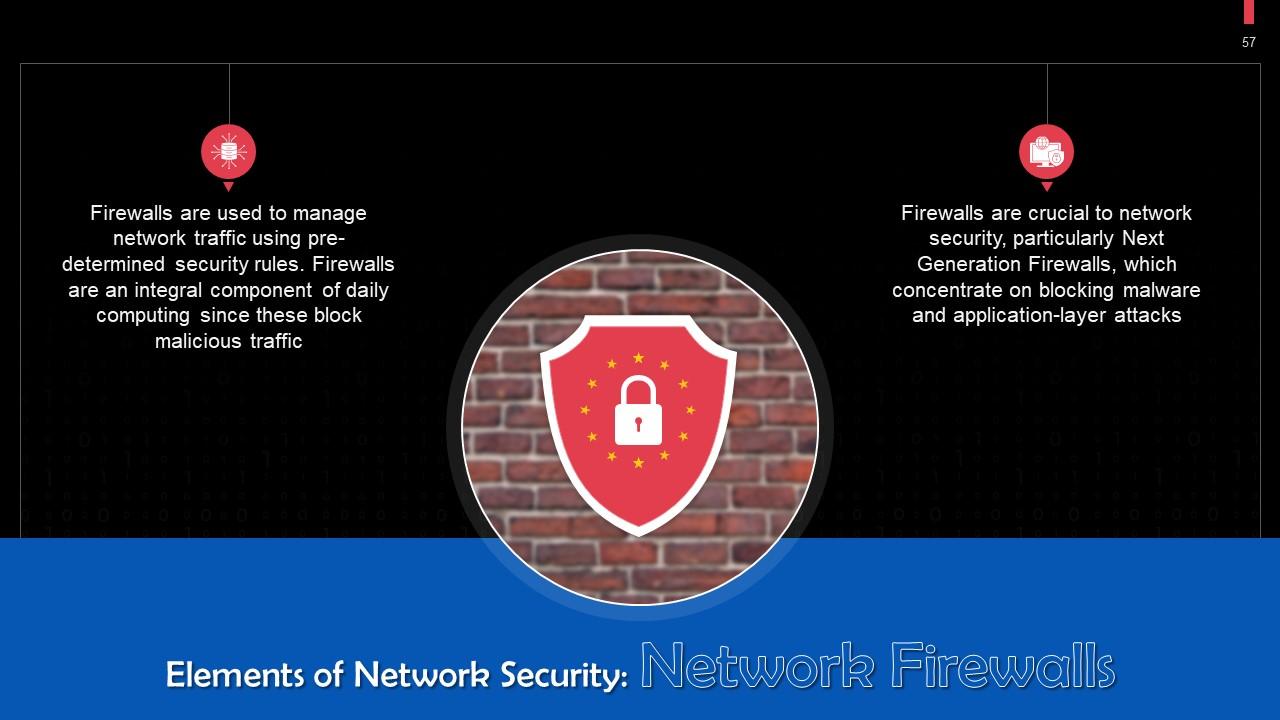
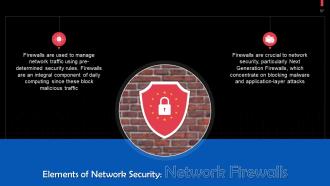
This slide tells us about network firewalls. Firewalls are used to manage network traffic using pre-established security rules. Firewalls are an essential component of daily computing since they block malicious traffic.
Slide 58
This slide gives information about Intrusion Prevention Systems. Network security attacks like brute force attacks, DoS attacks, and exploits of known vulnerabilities can be found or prevented by technologies based on Intrusion Prevention Systems (IPS).
Slide 59
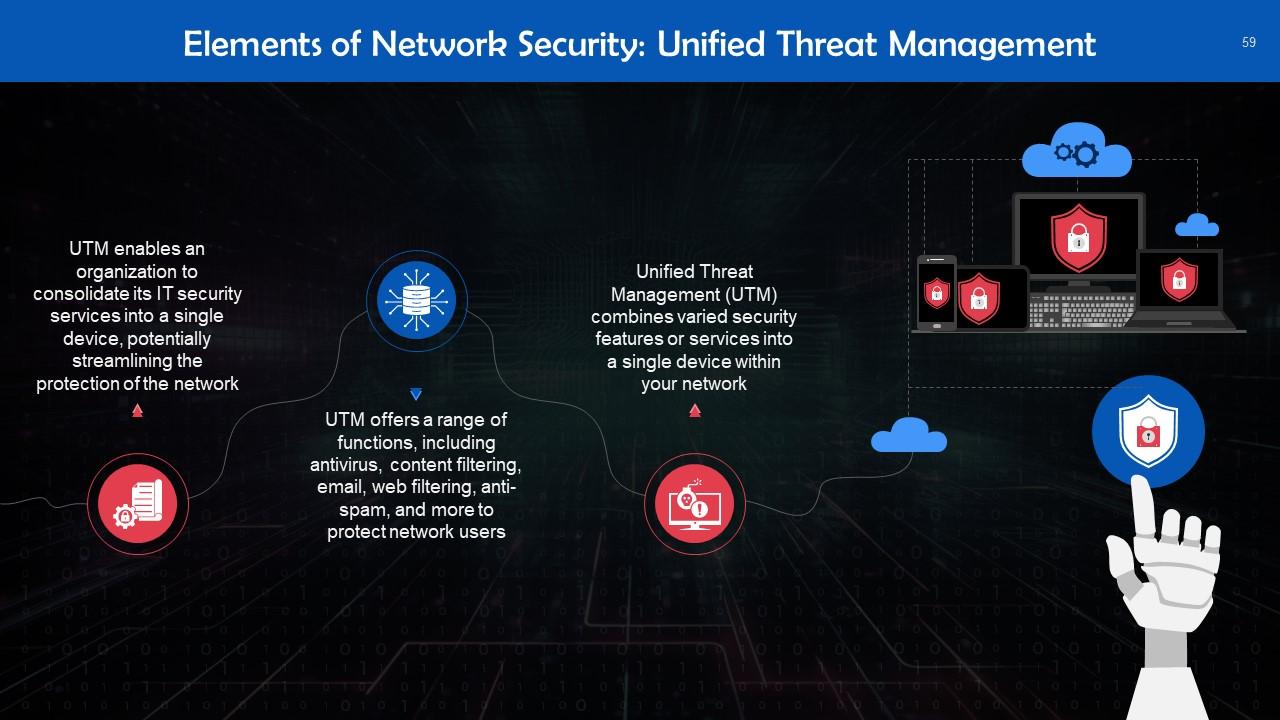
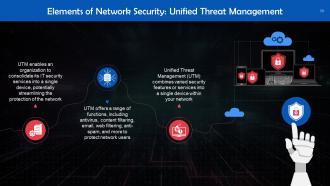
This slide tells us about Unified Threat Management (UTM), which combines several security features or services into a single device within your network.
Slide 60
This slide tells us about Advanced Network Threat Perception (ATP), which combines analysis tools to defend against advanced threats that employ known and unknown attack vectors.
Slide 61
This slide gives information about network access control. Network access control assists in ensuring that unauthorized users and devices are kept out of a private network.
Slide 62
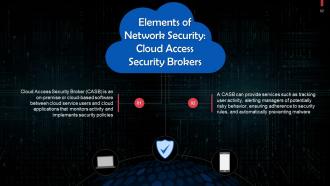
This slide tells us about Cloud Access Security Brokers. Cloud Access Security Broker is an on-premise or cloud-based software between cloud service users and cloud applications that monitors activity and implements security policies.
Slide 63
This slide tells us about Distributed Denial of Service (DDoS) Mitigation. The process of successfully defending a targeted server or network from a DDoS attack is known as DDoS mitigation.
Slide 64
This slide gives information about Network Behavior Anomaly Detection. It uses Artificial Intelligence (AI) and Machine Learning (ML) to detect hidden threats in parts of network infrastructure that other security tools cannot reach. It also notifies the IT team of those threats.
Slide 65
This slide tells us about SD-WAN Security. As businesses increasingly employ cloud-hosted SaaS apps to support digital transformation initiatives, they are deploying Software-Defined Wide Area Network (SD-WAN) solutions to ensure they have the required high-performance and reliable network connectivity.
Slide 66
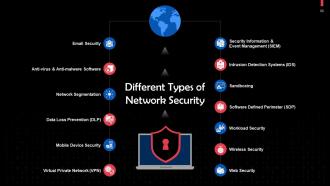
This slide lists types of network security. Some of these include email security, network segmentation, Security Information and Event Management (SIEM), Sandboxing, etc.
Slide 67
This slide discusses the importance of email security. Email is one of the most vulnerable areas in a network. Clicking on email links that covertly download harmful software makes employees targets of phishing and malware attacks.
Slide 68
This slide talks about anti-virus and anti-malware software for network security. Malicious software or malware includes viruses, worms, trojans, ransomware, and spyware. Malware can infect a network and remain inactive for days or weeks.
Slide 69
This slide discusses the importance of network segmentation. Network segmentation is a technique that companies with large networks and network traffic use to divide a network into smaller, manageable sections.
Slide 70
This slide talks about Data Loss Prevention (DLP) as a type of network security. These tools help in monitoring data in use, in motion, and at rest to identify and stop data breaches.
Slide 71
This slide discusses the importance of mobile device security. Business applications for smartphones and other mobile devices have made such devices a crucial component of network security.
Slide 72
This slide talks about Virtual Private Network (VPN) for network security. Remote access VPN provides remote and protected access to an organization network's individual hosts or clients, such as mobile users, telecommuters, and extranet consumers.
Slide 73
This slide discusses the importance of Security Information & Event Management (SIEM). This security management strategy records information from network hardware and application logs while being extremely watchful for unusual activity.
Slide 74
This slide talks about Intrusion Detection Systems (IDS) for network security. An IDS watches network traffic for suspicious activity and sends an alert when it is found.
Slide 75
This slide discusses sandboxing as a type of network security. Sandboxing is a cybersecurity technique that allows you to run programs or access files on a host computer in a secure, isolated environment that closely resembles end-user operating environments.
Instructor’s Notes: For instance, malware in Microsoft Word, Excel, PowerPoint, and PDF files can be safely detected and prevented before the files are downloaded by an unsuspecting end user.
Slide 76
This slide talks about Software Defined Perimeter (SDP) for network security. SDP is a technique to hide Internet-connected infrastructure (servers, routers, etc.) so that external parties and attackers are unable to see it, whether it is hosted on-premise or in the cloud.
Slide 77
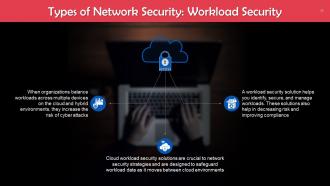
This slide talks about workload security as a type of network security. When organizations balance workloads across multiple devices on the cloud and hybrid environments, they increase the risk of cyber-attacks.
Slide 78
This slide discusses the importance of wireless security. Wireless networks are one of the most vulnerable parts of a system and require rigorous security measures and monitoring.
Slide 79
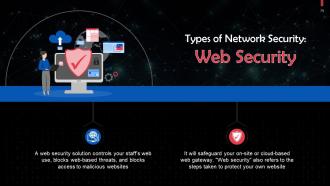
This slide talks about web security as a type of network security. A web security solution controls your staff’s web use, blocks web-based threats, and blocks access to malicious websites.
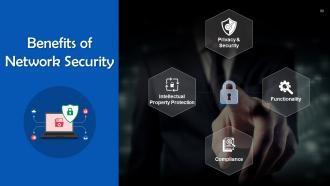
Slide 80
This slide lists benefits of network security. These include: privacy & security, functionality, compliance, and intellectual property protection.
Instructor’s Notes:
- Privacy & Security: Organizations must protect the privacy, integrity, and accessibility of network data since it contains sensitive user data. Network security guards against lapses that could reveal PII and other sensitive data, harm a company's reputation, and cause financial losses
- Functionality: Network security ensures that organizations and individuals continue to operate efficiently
- Compliance: Many nations have laws requiring compliance with data security and privacy, and secure networks are crucial for adhering to these mandates
- Intellectual Property Protection: The capacity of many businesses to compete depends on their intellectual property. Securing access to intellectual property helps organizations retain their competitive edge
Slide 81
This slide lists challenges to network security. These are: Remote & mobile access, user adherence, third-party partners, and evolving network attack actors.
Instructor’s Notes:
- Remote & Mobile Access: As more businesses implement Bring Your Own Device (BYOD) policies, there will be extensive and complicated network of devices for firms to secure. Since users are more likely to access business networks over a personal or public network, wireless security is becoming even more crucial
- User Adherence: Every network user is accountable for maintaining security. It can be challenging for organizations to ensure that everyone follows the best practices while simultaneously evolving those strategies to address the newest threats
- Third-Party Partners: A company's network is frequently accessed by cloud service providers, managed security service providers, and security product suppliers, creating additional potential security flaws
- Evolving Network Attack Actors: As technology advances, threat actors and their techniques also become more sophisticated. For instance, emerging technologies like blockchain have given rise to new malware attacks like cryptojacking. Network security defensive tactics must evolve to counter these new threats
Slide 82
This slide gives information about end-user security. End-user security, also known as endpoint security, refers to the protection of devices that users work with and users themselves.
Slide 83
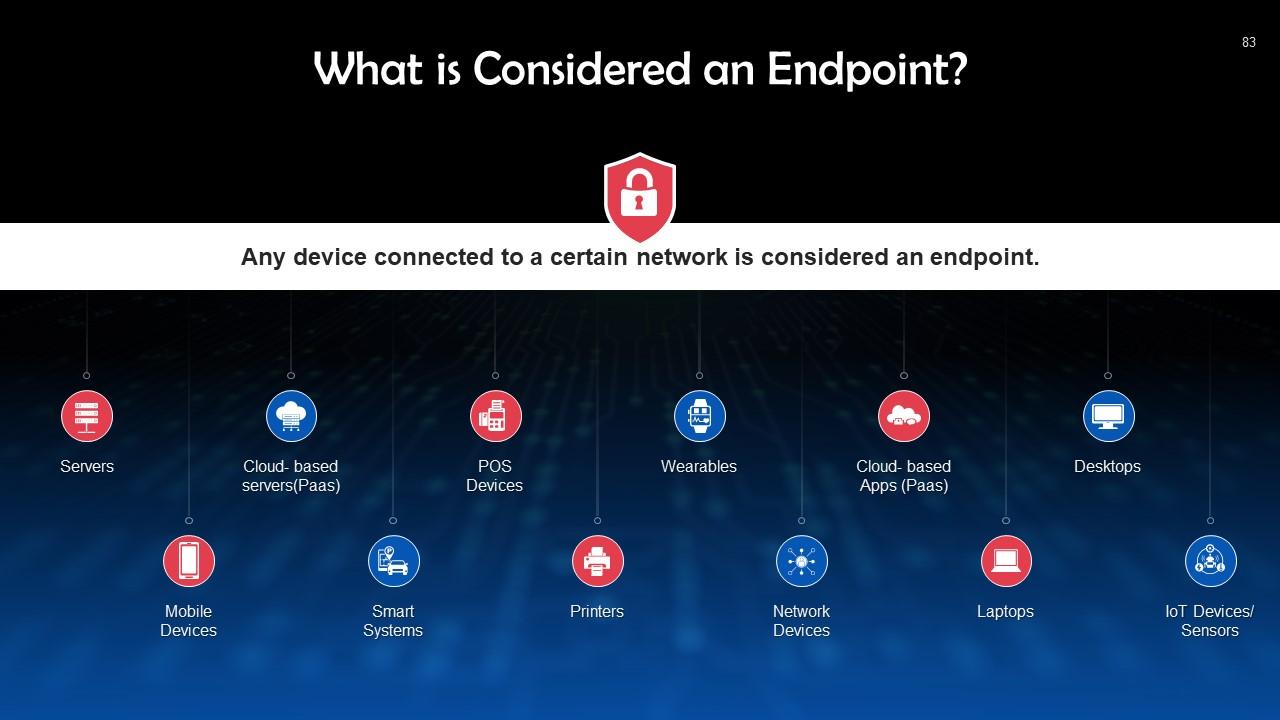
This slide depicts the working of endpoint security. Any device connected to a certain network is considered an endpoint. These include desktops, laptops, servers, printers, etc.
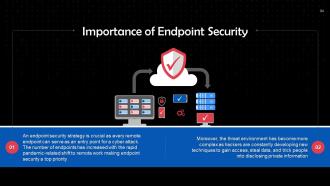
Slide 84
This slide shows the importance of endpoint security. An endpoint security strategy is crucial as every remote endpoint can serve as an entry point for a cyber attack as the number of endpoints is increasing with the rapid pandemic-related shift to remote work.
Slide 85
This slide depicts the working of endpoint security. Endpoint Protection Platforms, or EPPs, work by examining files as they enter the network.
Slide 86
This slide tells us about strategies used in endpoint protection solutions. These are either traditional or legacy, cloud, or hybrid approach.
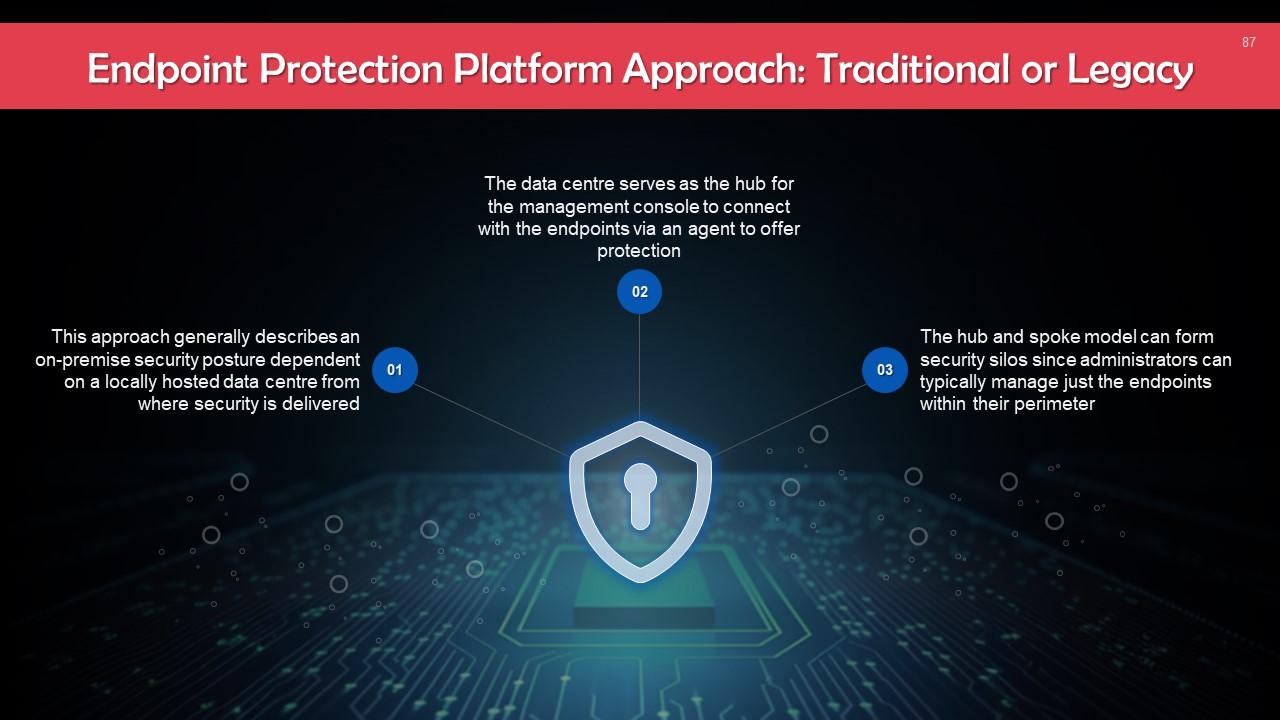
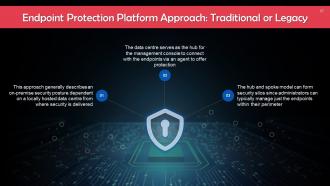
Slide 87
This slide talks about the traditional or legacy approach for endpoint protection platforms. This approach describes an on-premise security posture dependent on a locally hosted data center from which security is delivered.
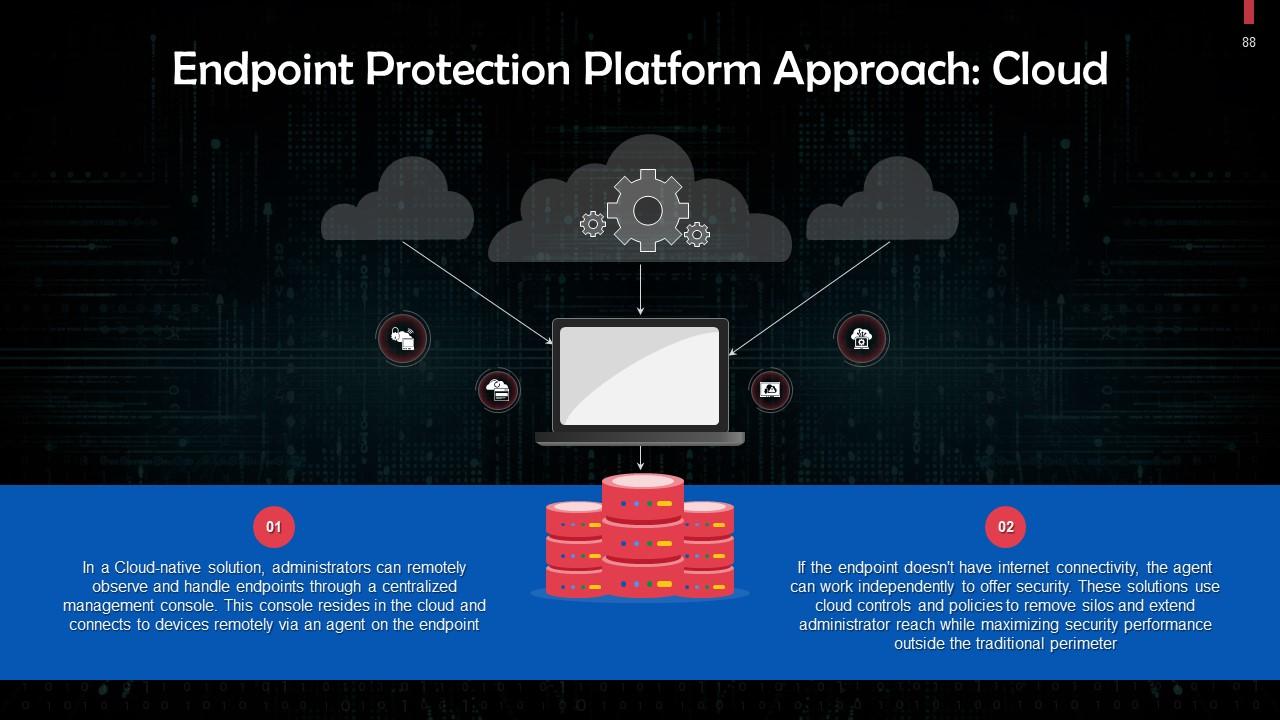
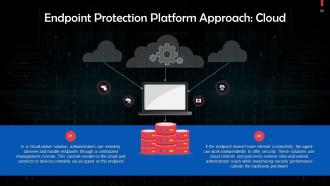
Slide 88
This slide talks about the cloud approach for endpoint protection platforms. In a Cloud-native solution, administrators can remotely observe and handle endpoints through a centralized management console that resides in the cloud. It connects to devices remotely via an agent on the endpoint.
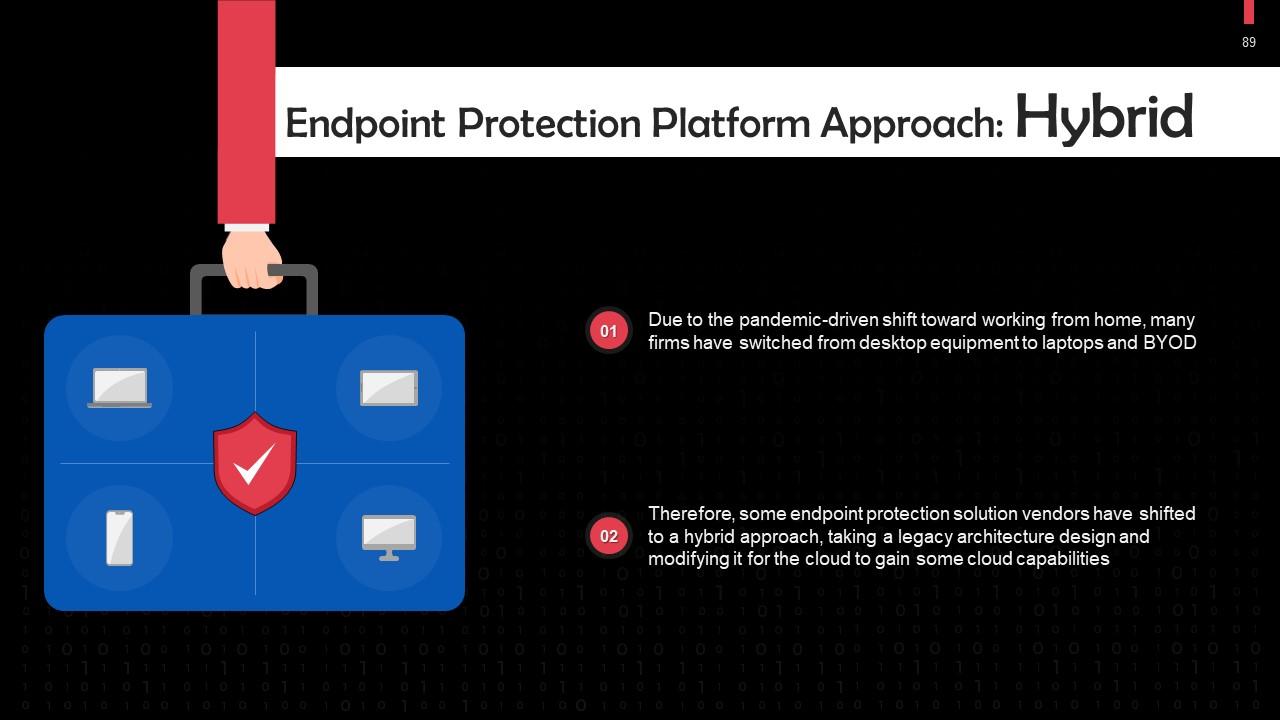
Slide 89
This slide discusses the hybrid approach for endpoint protection platforms. Some endpoint protection solution vendors have shifted to it. This involves taking a legacy architecture design and modifying it for the cloud to gain some cloud capabilities.
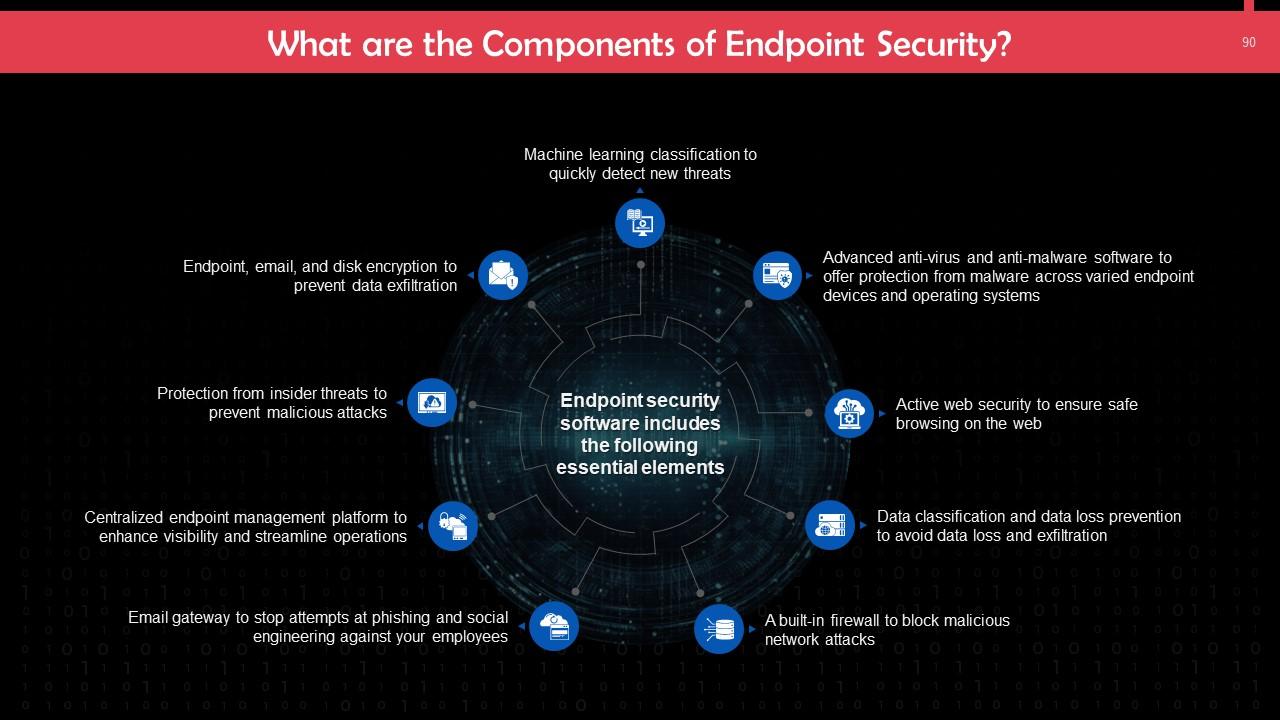
Slide 90
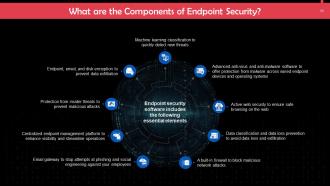
This slide lists the key components of endpoint security. These include: machine learning classification to quickly detect new threats, a built-in firewall to block malicious network attacks, etc.
Slide 91
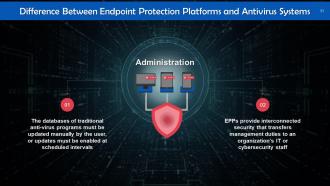
This slide highlights difference between endpoint protection and traditional antivirus systems. These are visibility, administration, and protection.
Slide 92
This slide highlights the difference between endpoint security and network security. Endpoint security software takes a holistic approach toward the company network and can provide visibility of every connected endpoint from a single location.
Slide 93
This slide discusses administration as a key difference between endpoint protection and anti-virus solutions. The databases of traditional anti-virus programs must be updated manually by the user, or updates must be enabled at scheduled intervals.
Slide 94
This slide talks about protection as a key difference between endpoint protection and anti-virus solutions. Traditional anti-virus solutions use signature-based detection to find viruses. This means that you could still be at risk if your users haven't recently updated their anti-virus software. Today's EPP solutions are automatically updated.
Slide 95
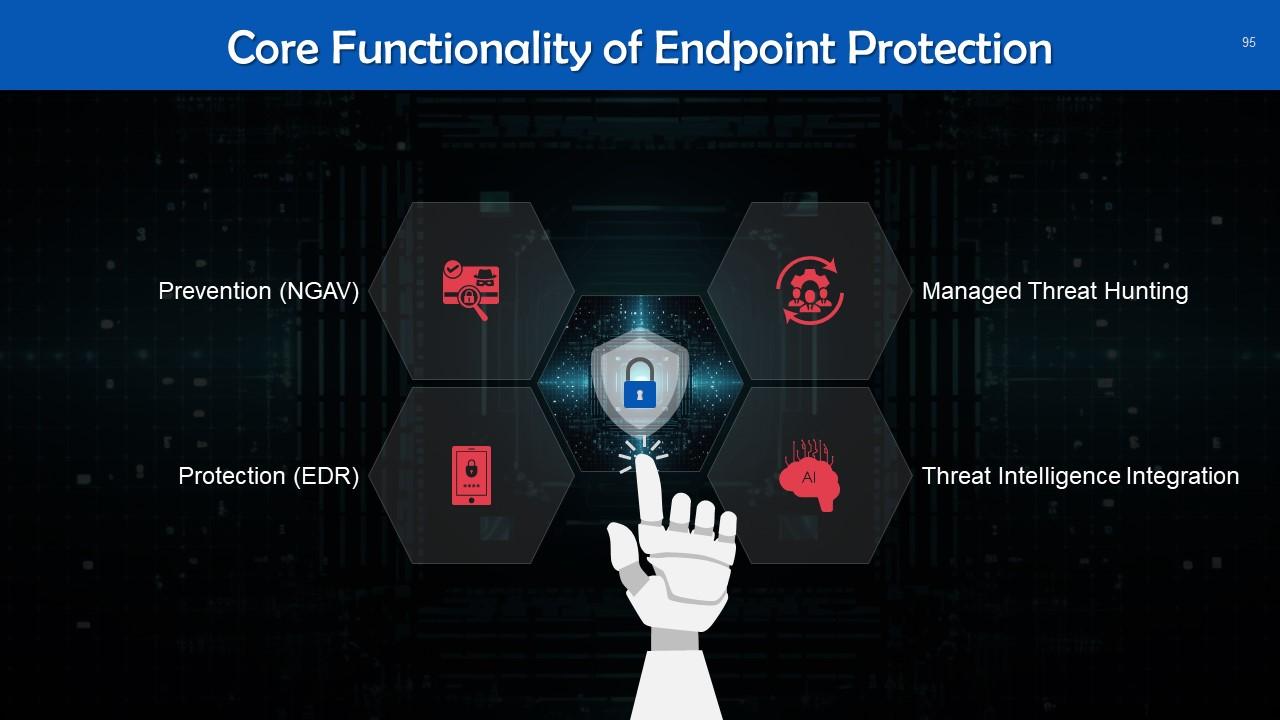
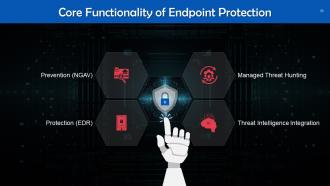
This slide lists key elements of endpoint protection. These are: Prevention, protection, managed threat hunting, and threat intelligence integration.
Slide 96
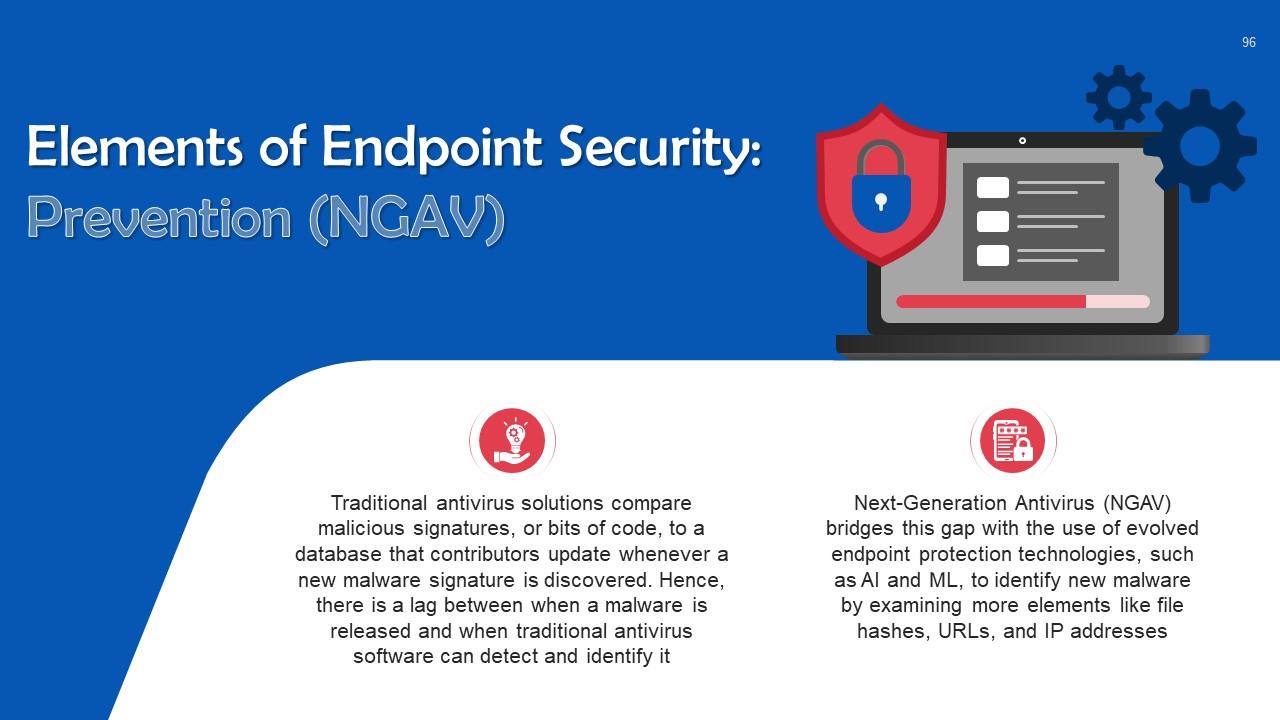
This slide discusses protection as an element of endpoint protection. Next-Generation Antivirus (NGAV) employs evolved endpoint protection technologies, such as AI and ML, to identify new malware by examining more elements like file hashes, URLs, and IP addresses.
Slide 97
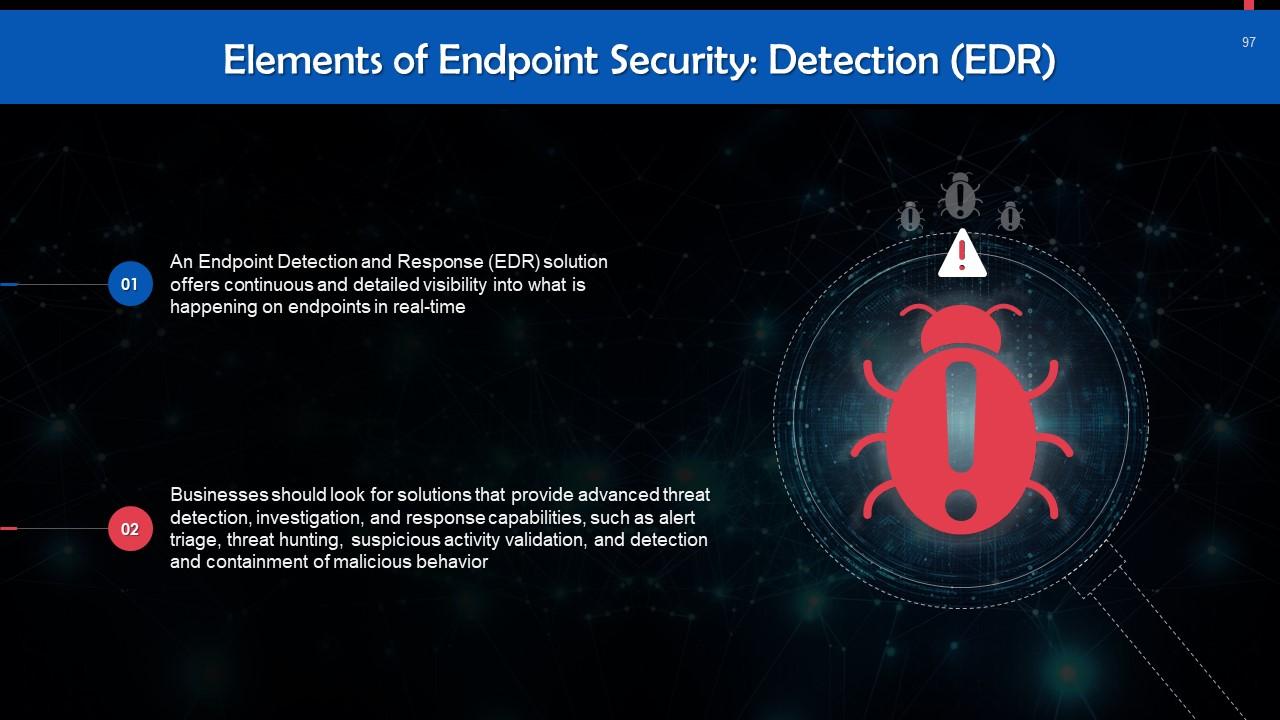
This slide talks about detection in endpoint protection. An Endpoint Detection and Response (EDR) solution offers continuous and detailed visibility into what is happening on endpoints in real-time.
Slide 98
This slide talks about managed threat hunting in endpoint protection. Automation alone cannot identify every attack. The ability of security experts is crucial to identify today's complex threats.
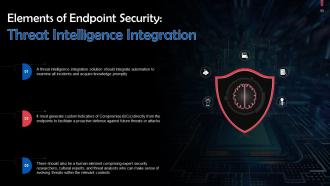
Slide 99
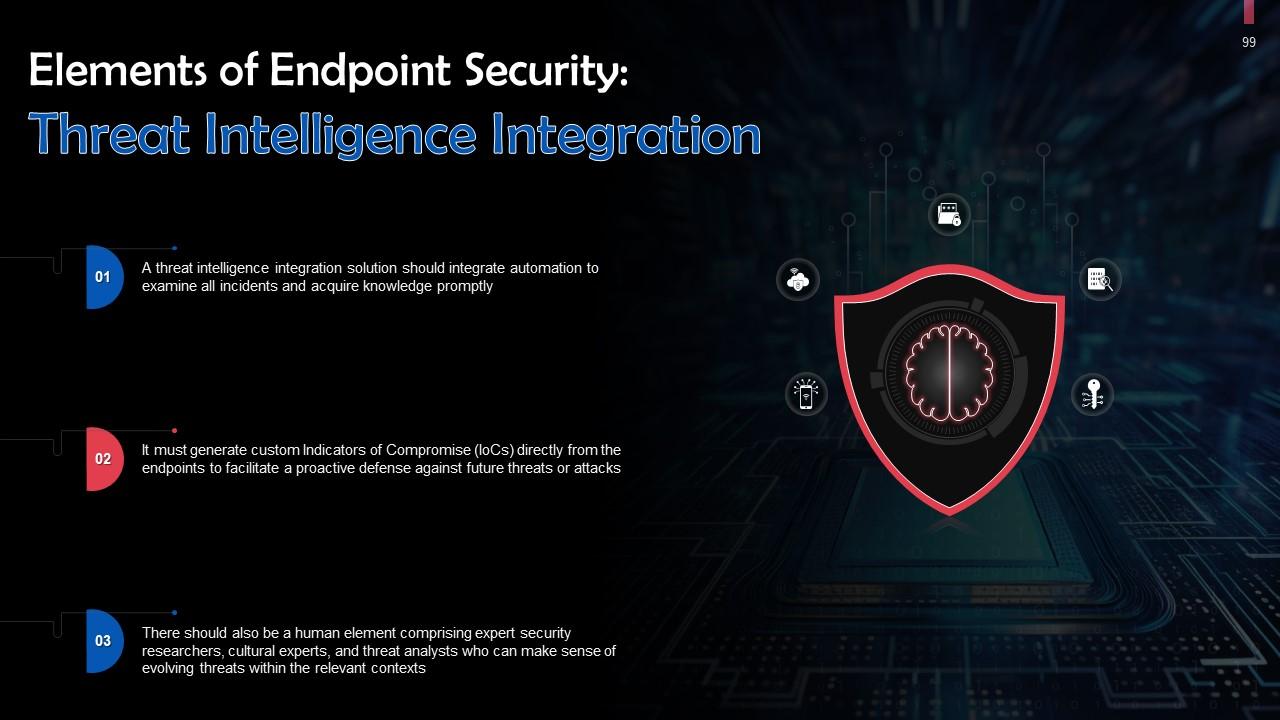
This slide talks about threat intelligence integration in endpoint protection. A threat intelligence integration solution should integrate automation to examine all incidents and acquire knowledge promptly.
Slide 100
This slide talks about operational security. Operational security entails looking at the entire security strategy to ensure that all measures are working effectively throughout all operations and that none conflict with one another.
Slide 101
This slide discusses the importance of operational security. OPSEC employs the risk management approach to identify potential threats and vulnerabilities before they're exploited; this method can shield your organization against potential business disruptions that could be financially crippling.
Slide 102
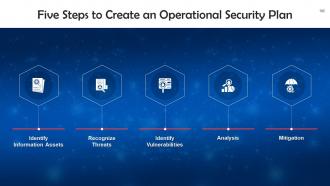
This slide lists steps to create an operational security plan. These are: Identifying information assets, threats, vulnerabilities, performing analysis, and mitigation.
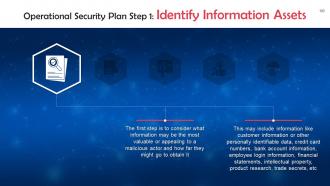
Slide 103
This slide discusses the first step of an operational security plan: Identifying Information Assets. The first step is to consider what information may be the most valuable or appealing to a malicious actor and how far they might go to obtain it.
Slide 104
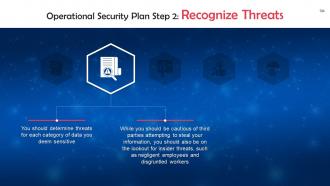
This slide talks about the second step of an operational security plan: Recognize Threats. You should determine the threats for each category of data you deem sensitive.
Slide 105
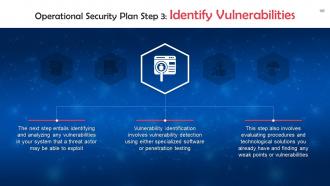
This slide discusses the third step of an operational security plan: Identifying Vulnerabilities. Vulnerability identification involves vulnerability detection using either specialized software or penetration testing.
Slide 106
This slide talks about the fourth step of an operational security plan: Analysis. In this step, rank your security flaws using factors like the likelihood of an attack, the extent of damage you may suffer, and the amount of work and time you'd need to recover.
Slide 107
This slide discusses the last step of an operational security plan: Mitigation. This may include updating your hardware, devising new policies concerning sensitive data, or training employees on security procedures and company policies.
Slide 108
This slide lists best practices for operational security or OPSEC. These are: Implementing identity & access management, disaster recovery & incident response plan, and automation.
Slide 109
This slide gives information about implementing identity and access management for operational security. IAM ensures that only individuals with authorization can access your technological resources.
Slide 110
This slide talks about disaster recovery and incident response plan for operational security. A DRP will assist you in regaining access and functionality of your IT infrastructure after a cyberattack.
Slide 111
This slide discusses the importance of automation for operational security. Humans make mistakes and behave maliciously, something technology doesn't do on its own. To eliminate such errors, organizations are turning to automation.
Slide 112
This slide gives information about disaster recovery planning. A disaster recovery plan outlines the steps to restart regular business operations and procedures following an organizational crisis.
Slide 113
This slide gives an overview of the working of Disaster Recovery Planning. Disaster recovery depends on replicating data and computer processing in an off-premises location.
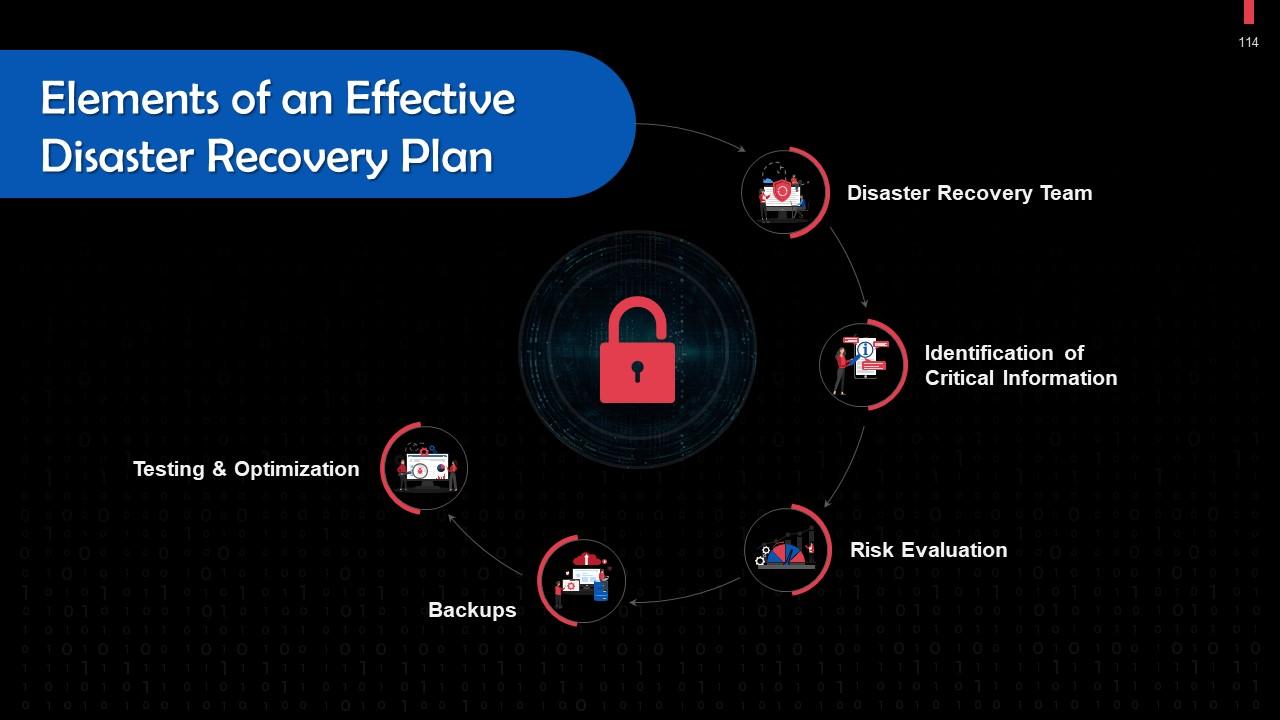
Slide 114
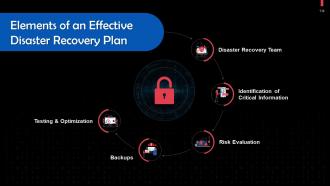
This slide lists important elements in an effective disaster recovery plan. These are: Disaster recovery team, identification of critical information, risk evaluation, backups, and testing & optimization.
Instructor’s Notes:
- Disaster Recovery Team: A designated team of experts should develop, implement, and manage the disaster recovery plan. The roles and duties of each team member should be specified. The team must be able to communicate with one another, staff members, vendors, and clients in case of a cyberattack
- Identification of Critical Information: A solid disaster recovery plan outlines the systems, applications, data, and other resources that are most important for maintaining company operations. The plan also documents measures that must be taken to recover data
- Risk Evaluation: Analyze any potential risks to your organization. Plan the steps and resources necessary to restore operations based on the type of incident
- Backups: Determine what needs a backup, who should perform backups, and how these should be implemented. Include a Recovery Point Objective (RPO) that specifies the frequency of backups along with a Recovery Time Objective (RTO) that states the maximum permissible downtime permitted after a security breach
- Testing & Optimization: The recovery team should regularly evaluate its strategy to address ever-evolving threats and business needs. In planning how to respond to a cyber attack, it’s critical that organizations test and optimize their security and data protection strategies.
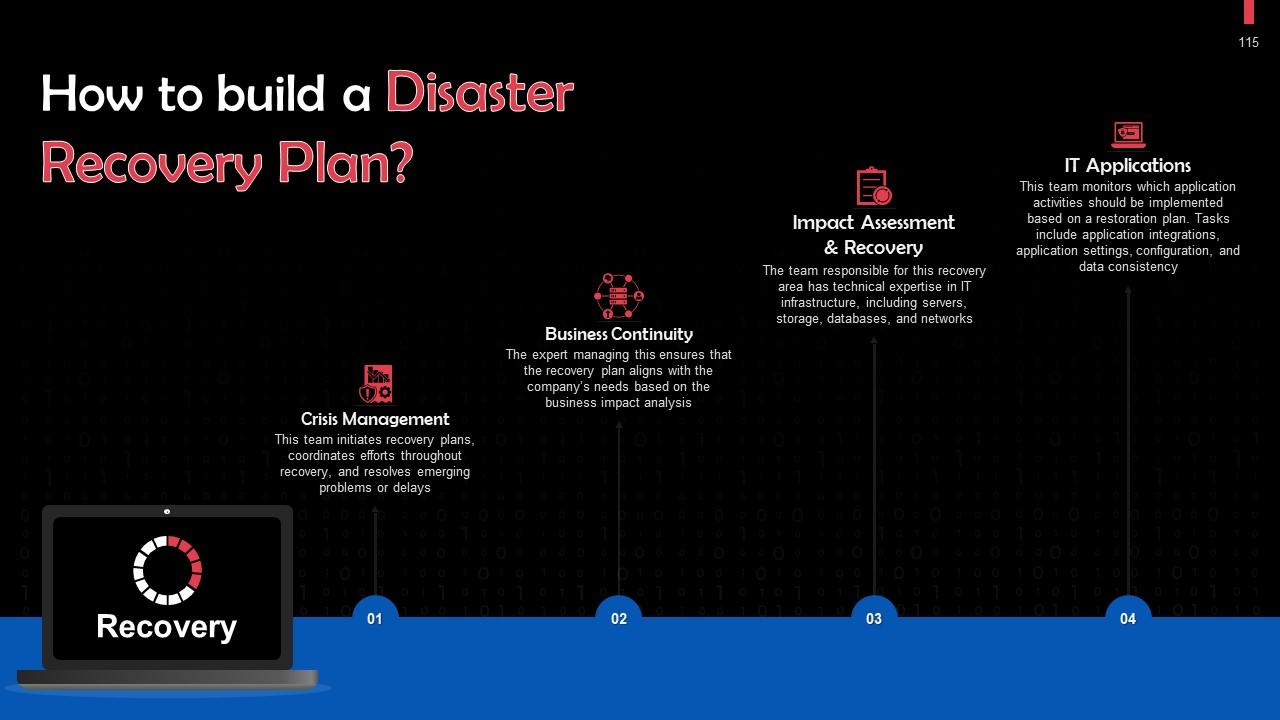
Slide 115
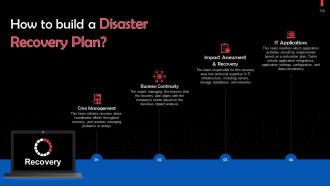
This slide discusses the building of a disaster recovery plan. This includes, crisis management, business continuity, impact assessment & recovery, and IT applications.
Slide 116
This slide lists types of disaster recovery. These are backups, hot sites, cold sites, backup as a service, disaster recovery as a service (DRaaS), point in time copies, virtualization, instant recovery.
Understanding Components of Cybersecurity Training Ppt with all 126 slides:
Use our Understanding Components of Cybersecurity Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Thrilled to see several customizable templates catering various verticals and industries.
-
Design layout is very impressive.