ZTNA Powerpoint Presentation Slides
This comprehensive PowerPoint presentation concisely overviews the zero trust network, highlighting its main pillars, features, and functionalities. The ZTNA PowerPoint Presentation explores why businesses adopt ZTNA and demonstrates how it can enhance security and operational efficiency. Additionally, the Zero Trust Model PPT delves into the architecture of ZTNA, encompassing user and architectural workflows. The Zero Trust Architecture ZTA PPT presentation offers valuable insights into unique ZTNA software solutions and essential considerations for selecting them. Moreover, the presentations Software-defined Perimeter SDP template addresses the implementation challenges of ZTNA and provides solutions. It also presents a detailed comparison of ZTNA with other technologies. Furthermore, the Zero Trust Network Access deck includes a training program and an estimated budget plan for ZTNA implementation. Lastly, the Identity-Defined Networking IDN PowerPoint Presentation showcases practical use cases of ZTNA technology and presents a compelling case study. This fully editable and customizable template is compatible with Google Slides, ensuring convenience and flexibility for users.
This comprehensive PowerPoint presentation concisely overviews the zero trust network, highlighting its main pillars, featu..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this ZTNA Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the ninety five slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces ZTNA.
Slide 2: This is an Agenda slide. State your agendas here.
Slide 3: This slide displays Table of contents for ZTNA.
Slide 4: This slide continues Table of contents for ZTNA.
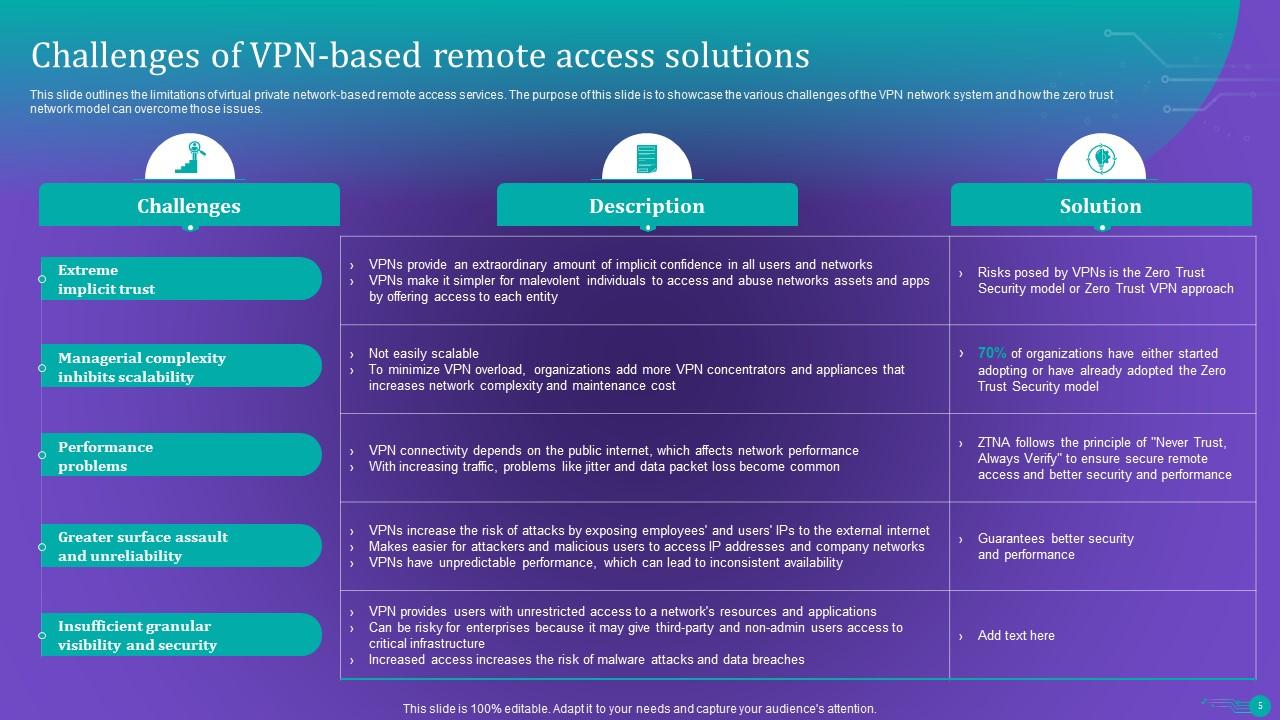
Slide 5: This slide outlines the limitations of virtual private network-based remote access services.
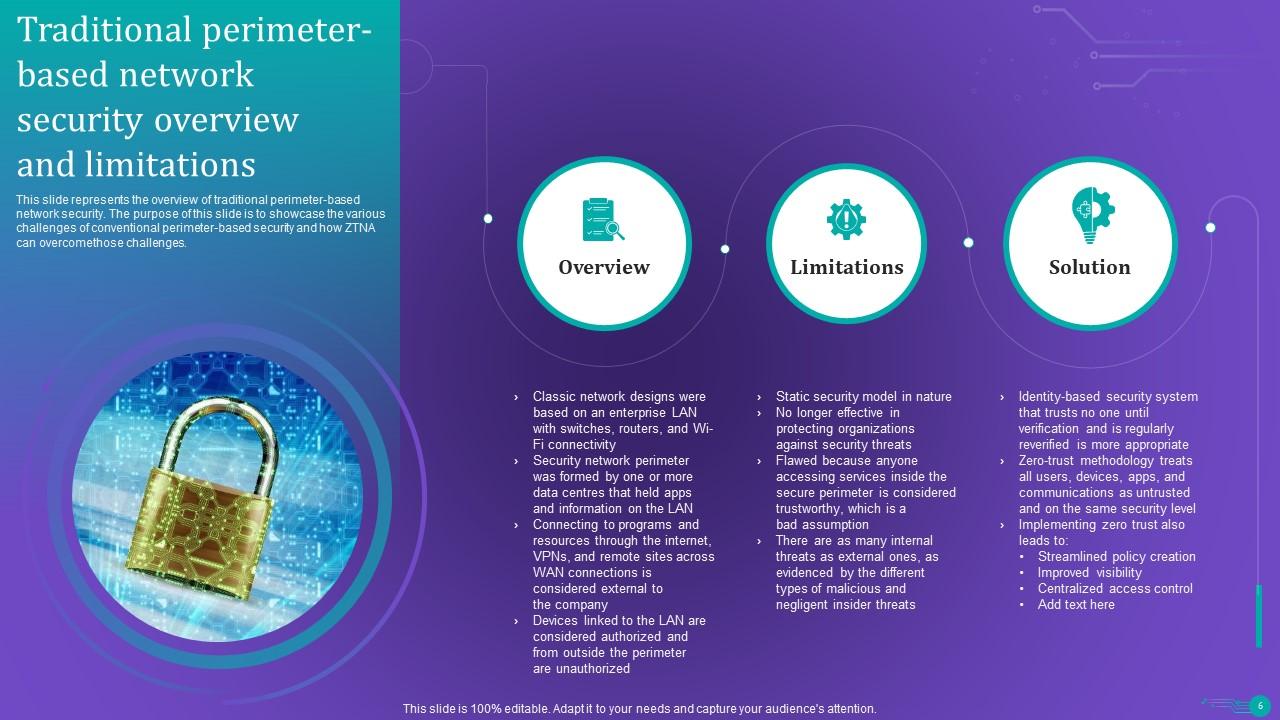
Slide 6: This slide represents the overview of traditional perimeter-based network security.
Slide 7: This slide depicts another Table of contents for ZTNA.
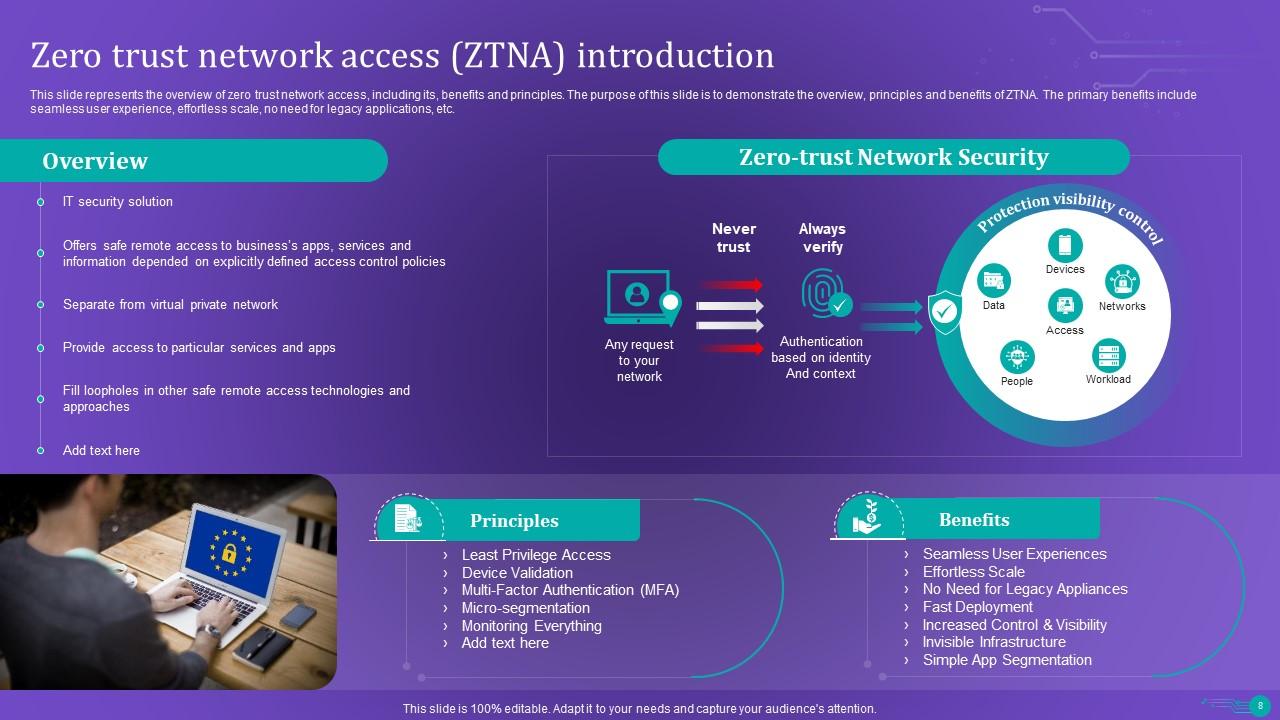
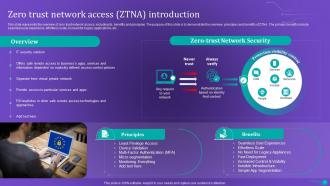
Slide 8: This slide presents the overview of zero trust network access.
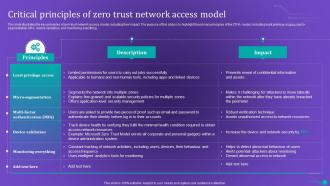
Slide 9: This slide illustrates the key principles of zero trust network access model.
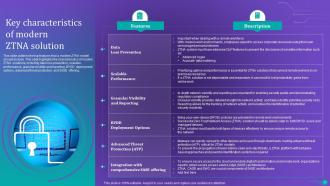
Slide 10: This slide outlines the top features that a modern ZTNA model should include.
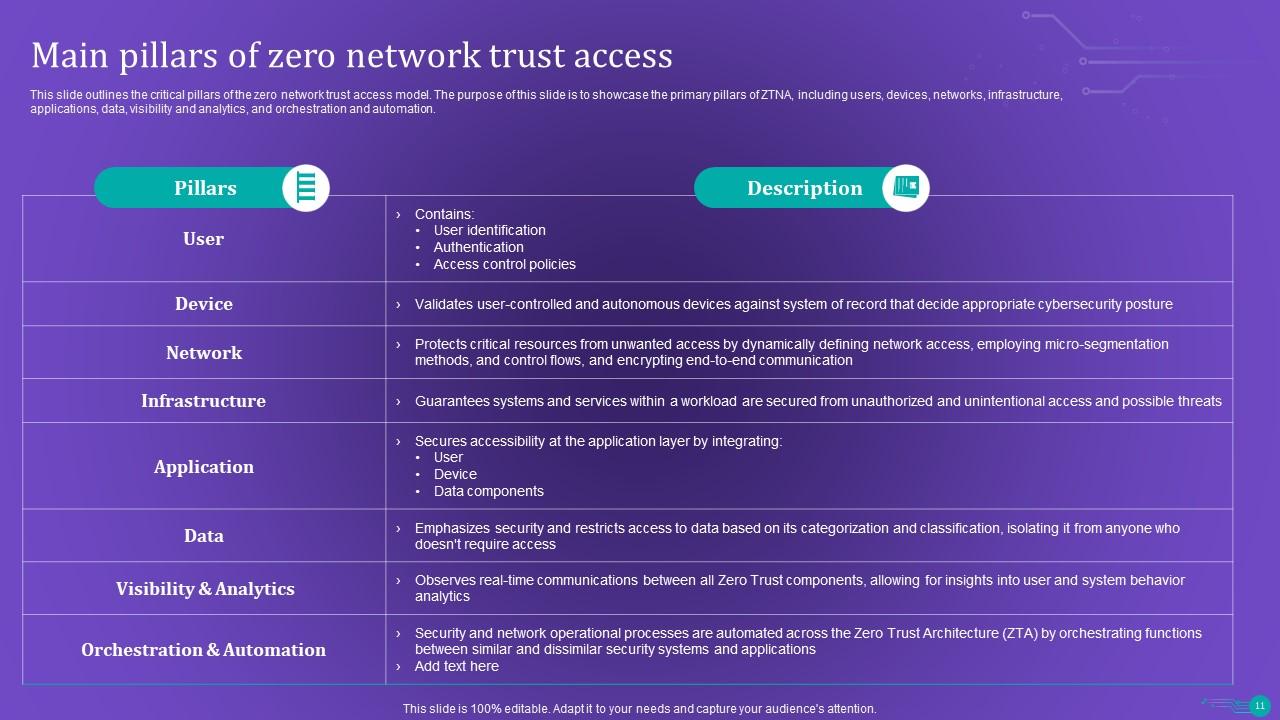
Slide 11: This slide highlights the critical pillars of the zero network trust access model.
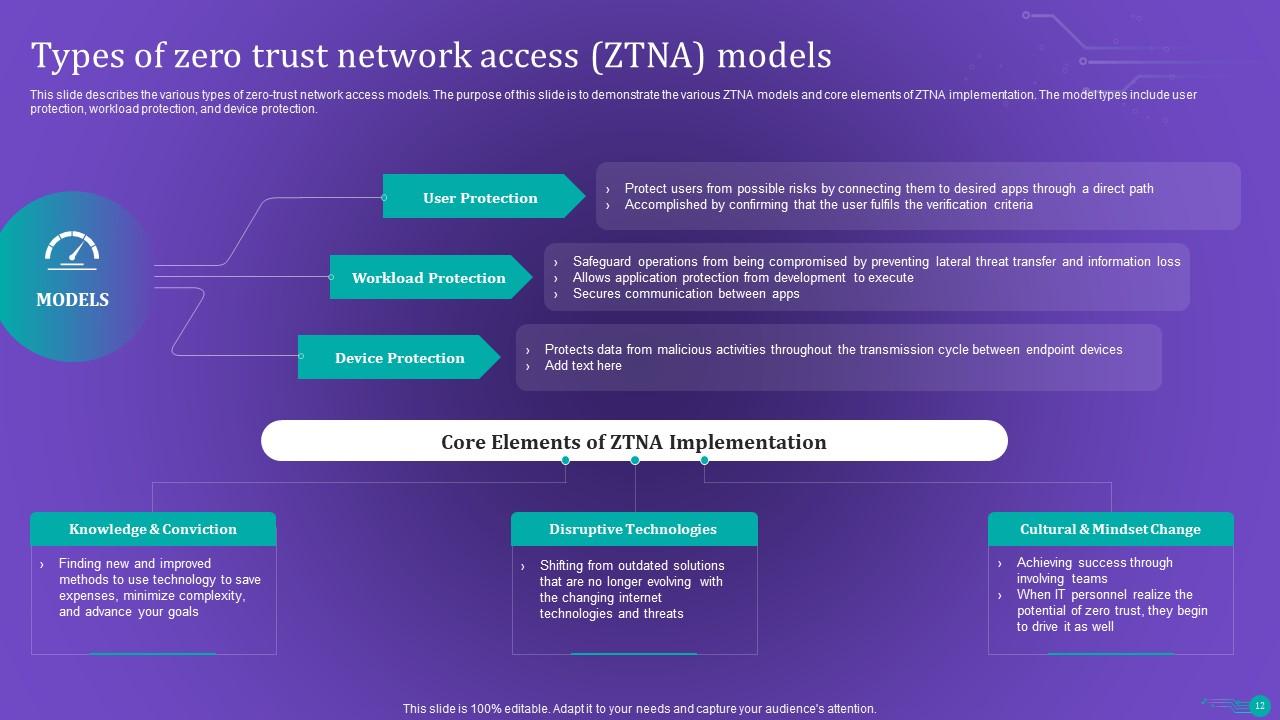
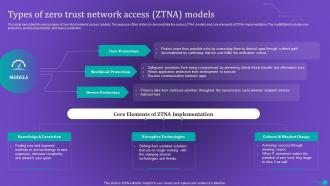
Slide 12: This slide describes the various types of zero-trust network access models.
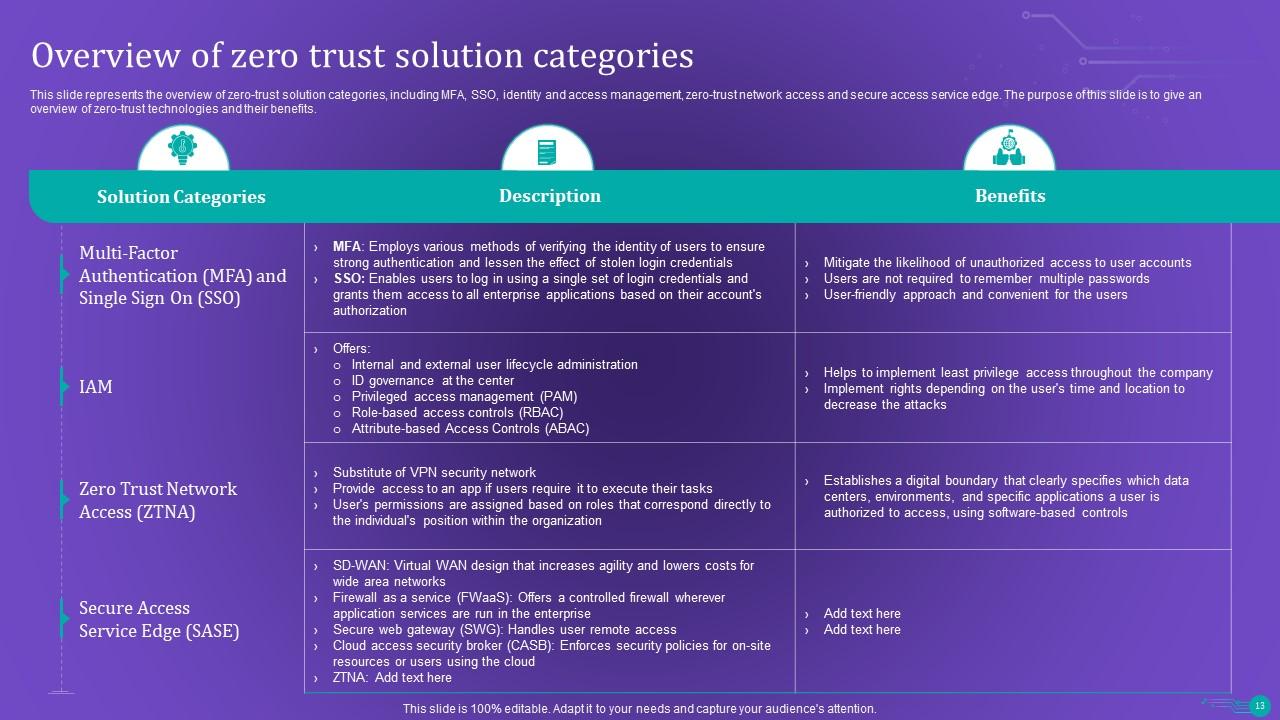
Slide 13: This slide represents the overview of zero-trust solution categories.
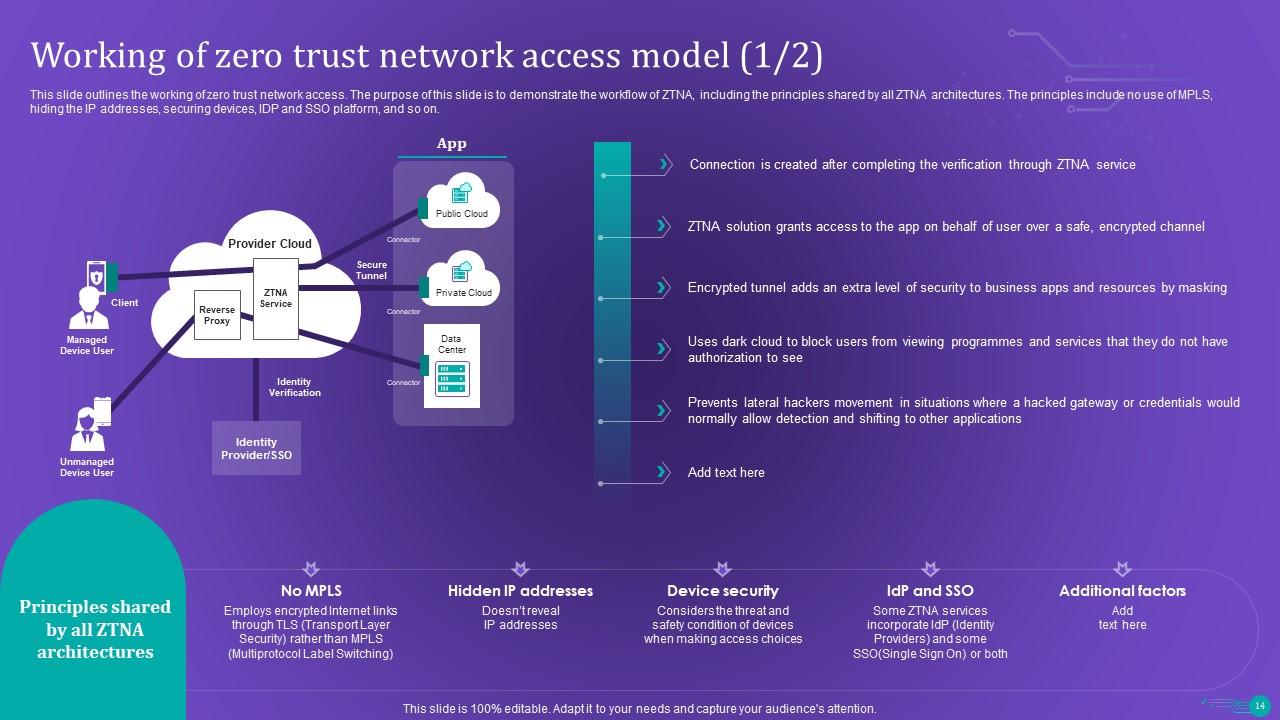
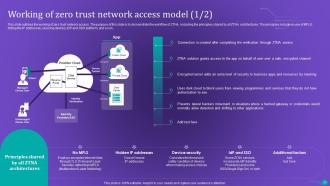
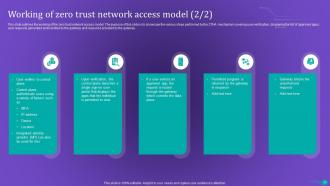
Slide 14: This slide shows the working of zero trust network access.
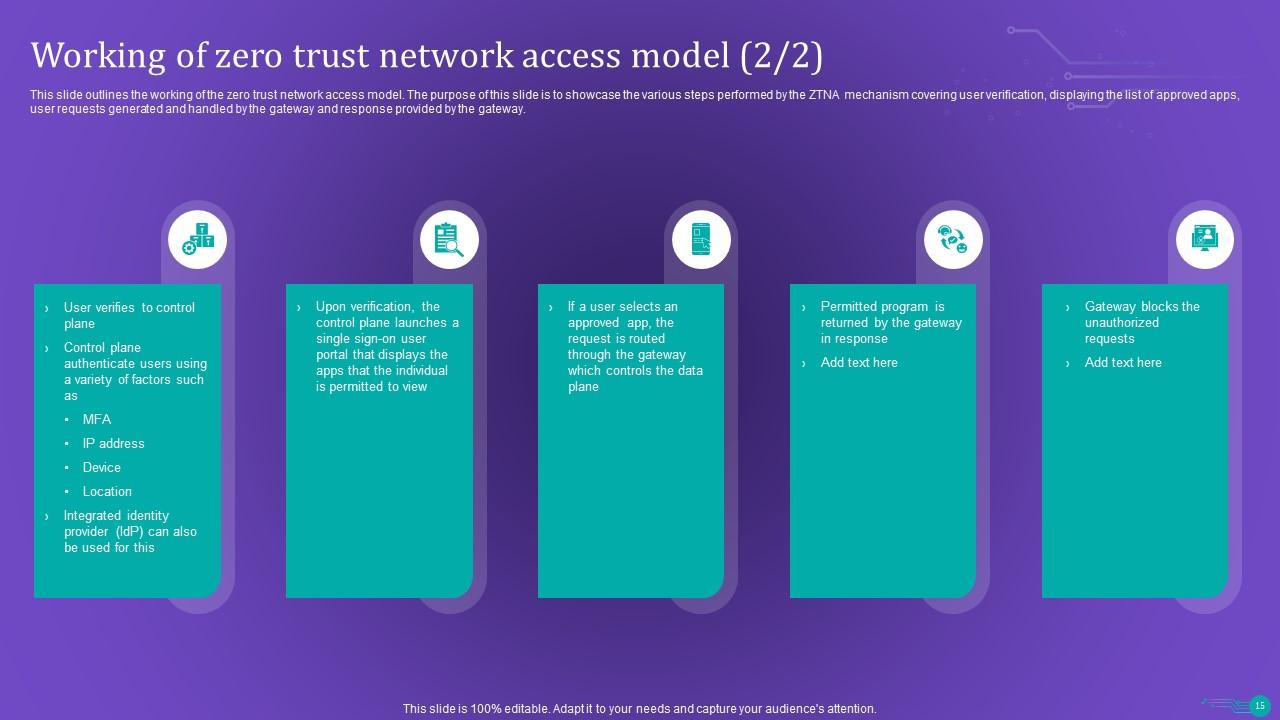
Slide 15: This slide outlines the working of the zero trust network access model.
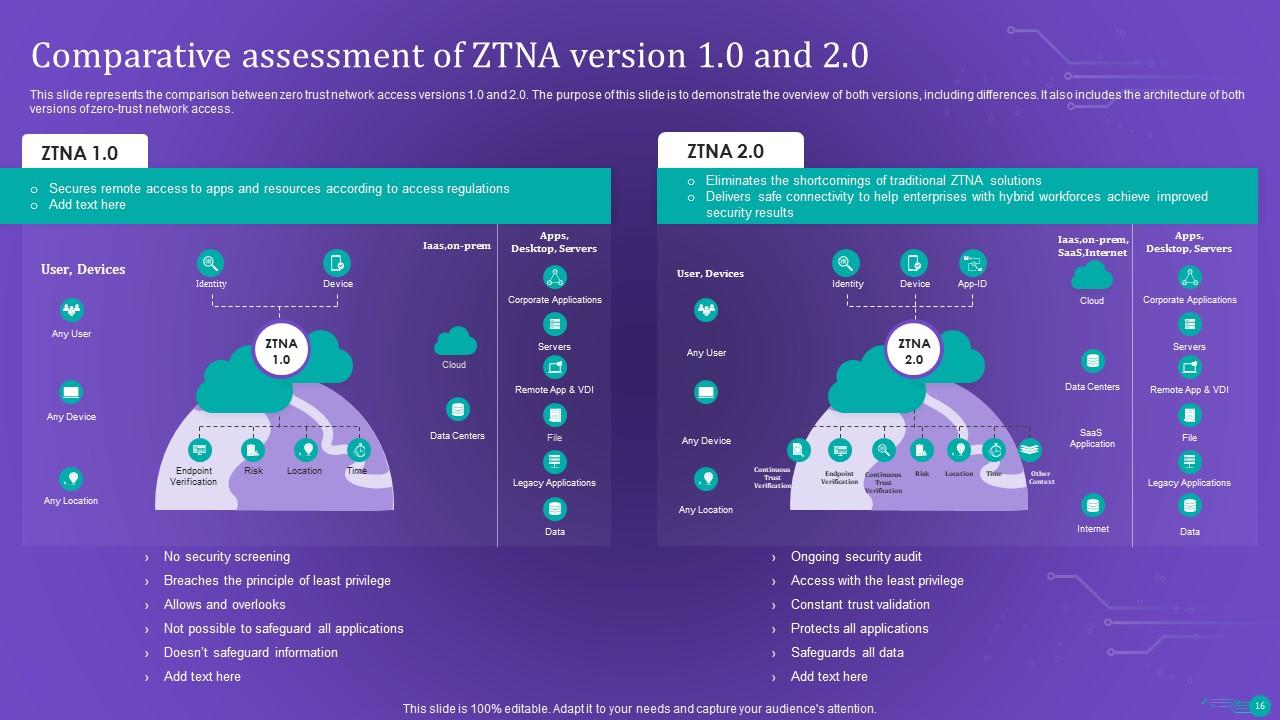
Slide 16: This slide represents the comparison between zero trust network access versions 1.0 and 2.0.
Slide 17: This slide highlights title of contents further.
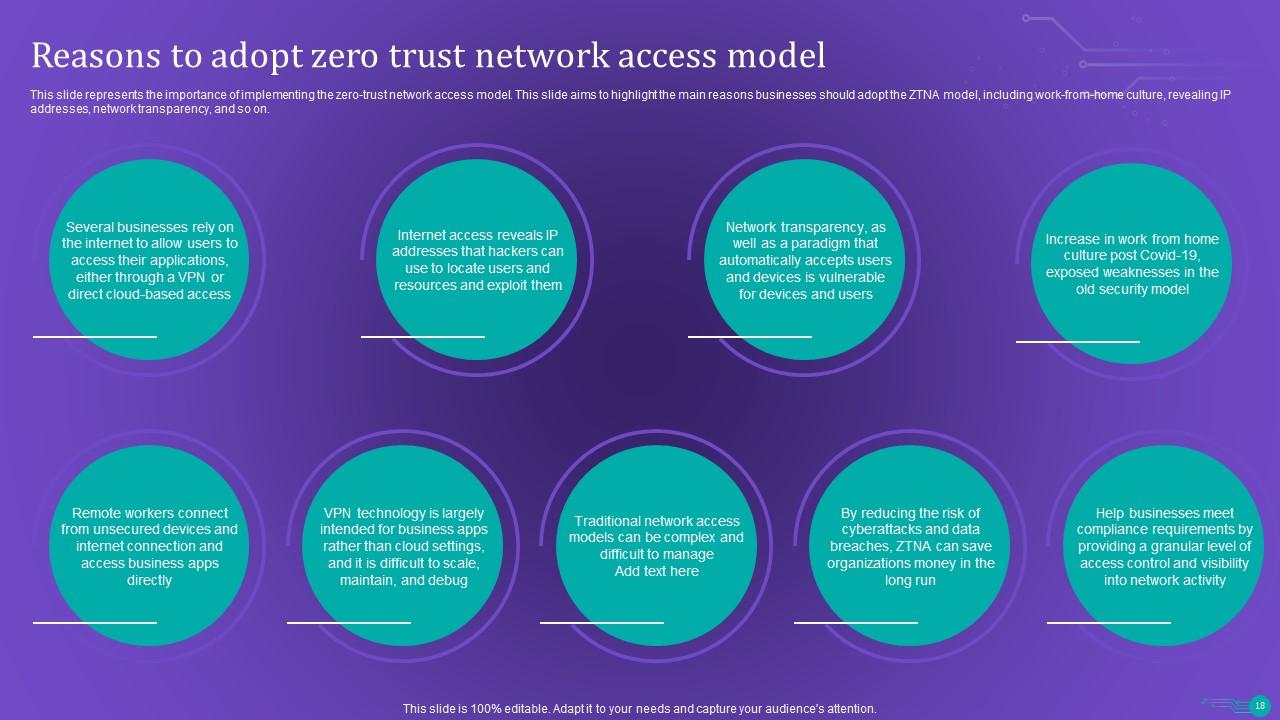
Slide 18: This slide presents the importance of implementing the zero-trust network access model.
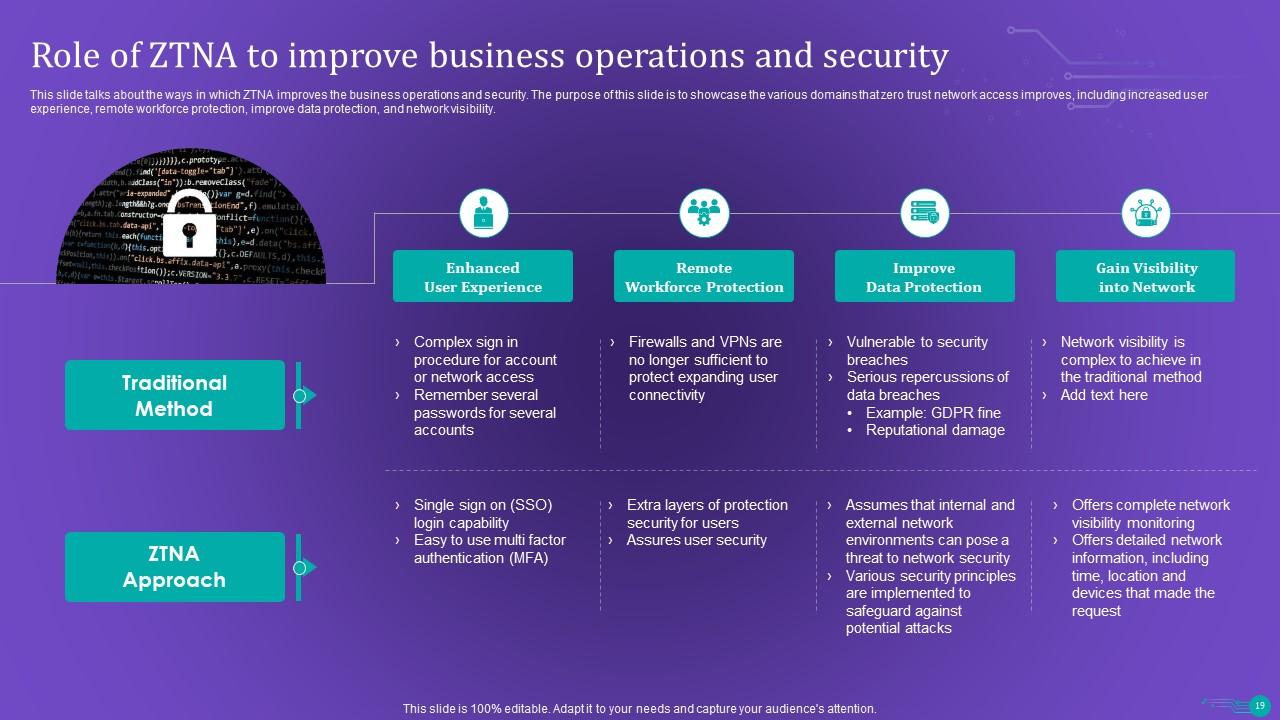
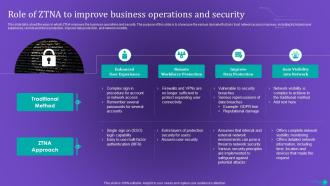
Slide 19: This slide contains the ways in which ZTNA improves the business operations and security.
Slide 20: This slide presents the main features of ZTNA.
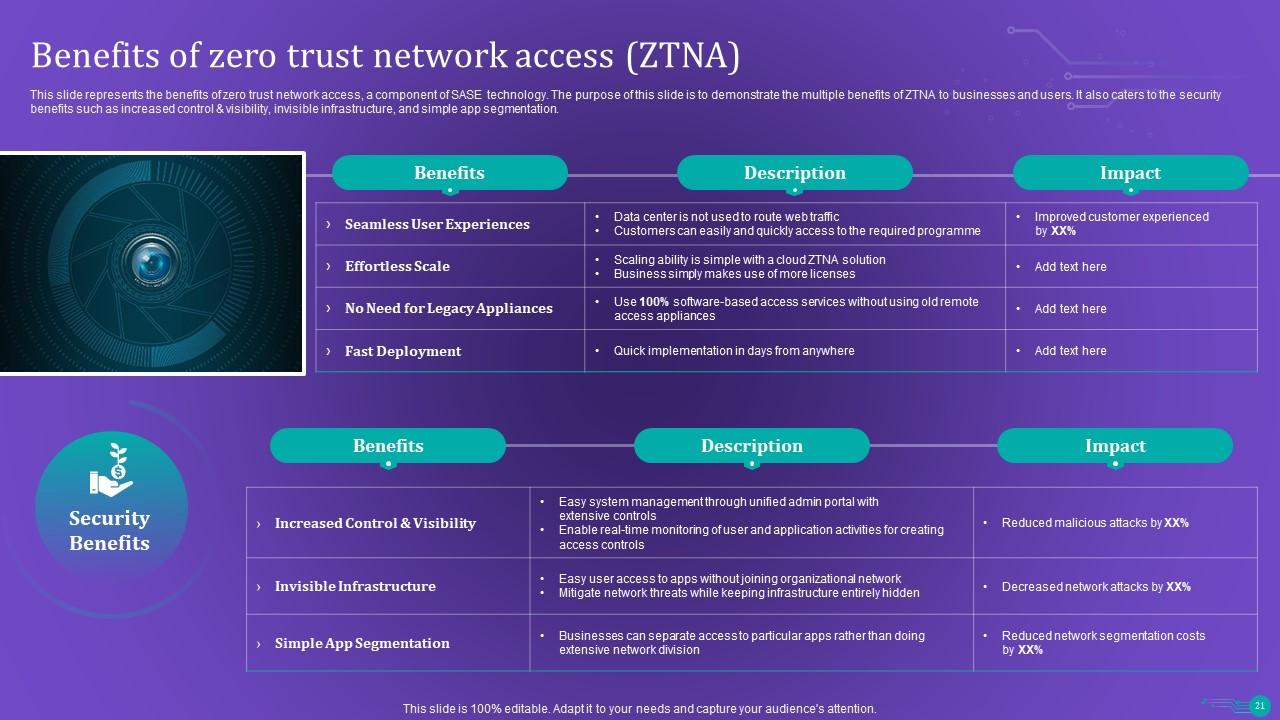
Slide 21: This slide represents the benefits of zero trust network access.
Slide 22: This slide shows another table of contents.
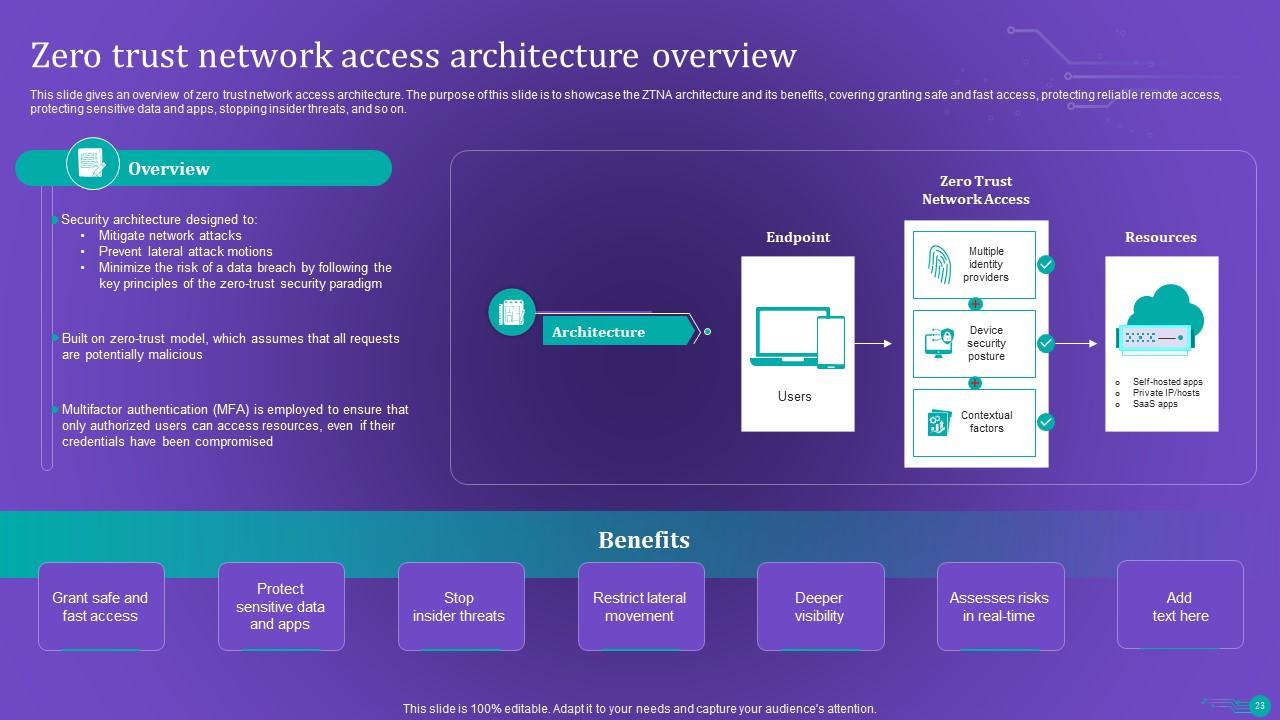
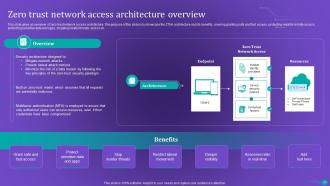
Slide 23: This slide gives an overview of zero trust network access architecture.
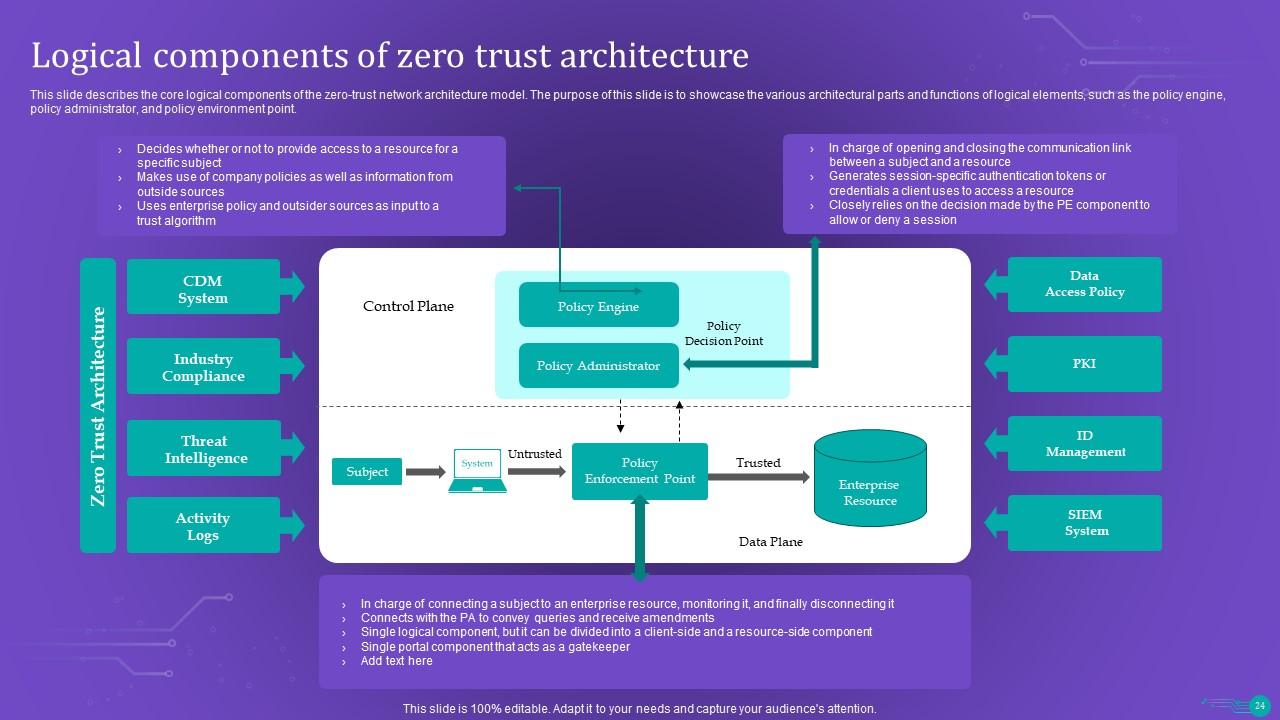
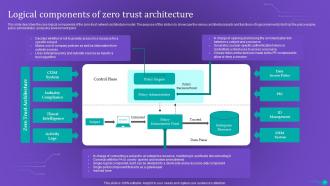
Slide 24: This slide describes the core logical components of the zero-trust network architecture model.
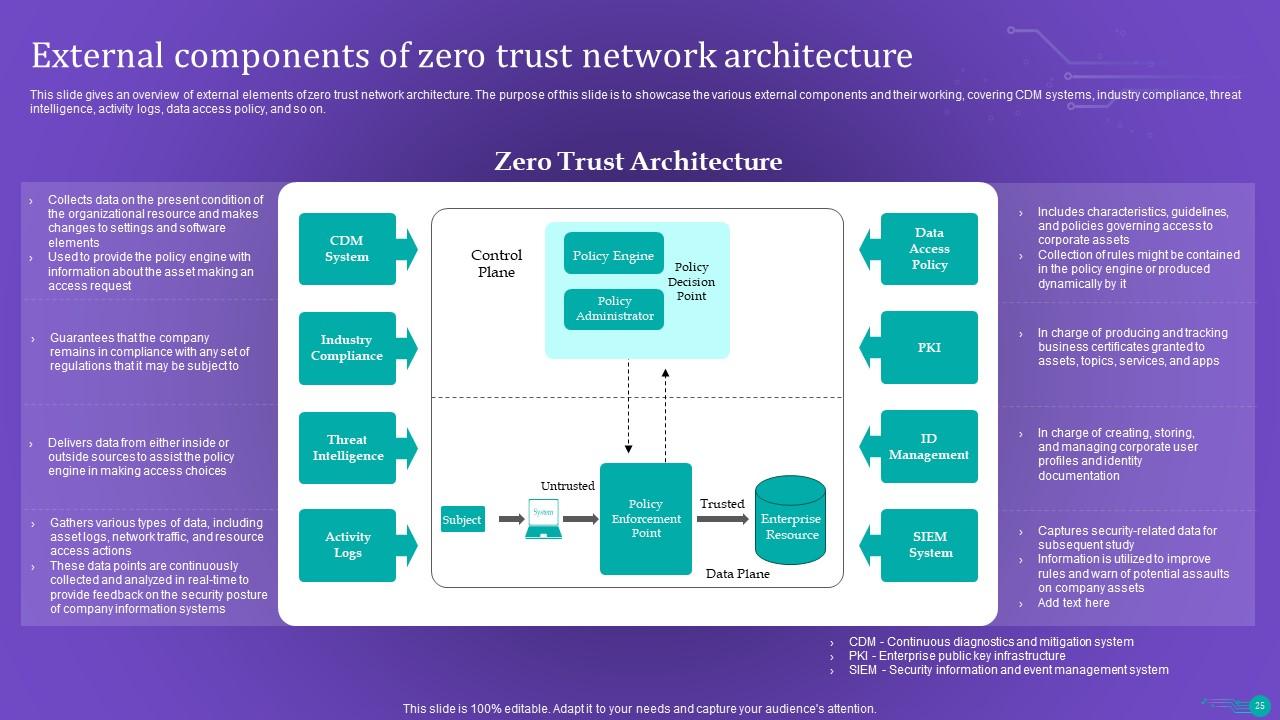
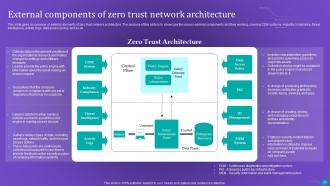
Slide 25: This slide gives an overview of external elements of zero trust network architecture.
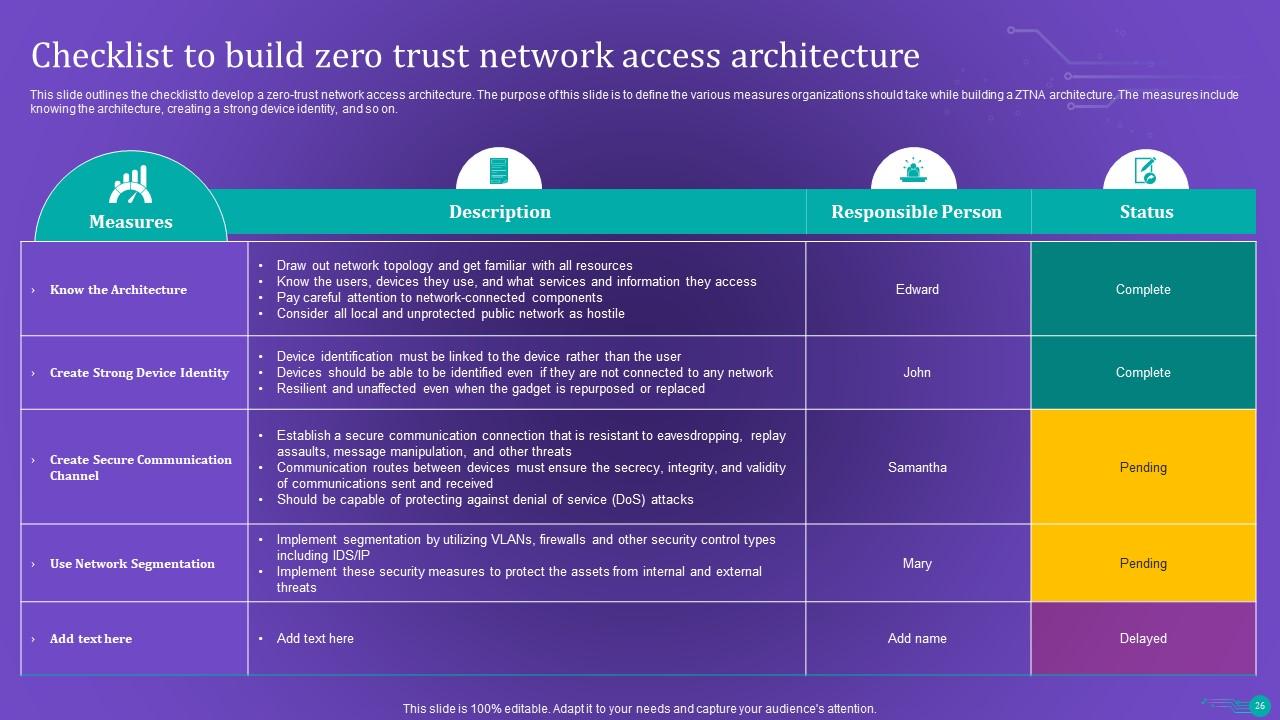
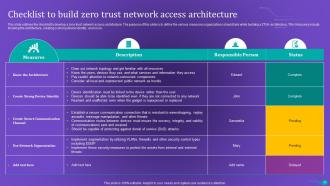
Slide 26: This slide outlines the checklist to develop a zero-trust network access architecture.
Slide 27: This slide again exhibits Table of contents for ZTNA.
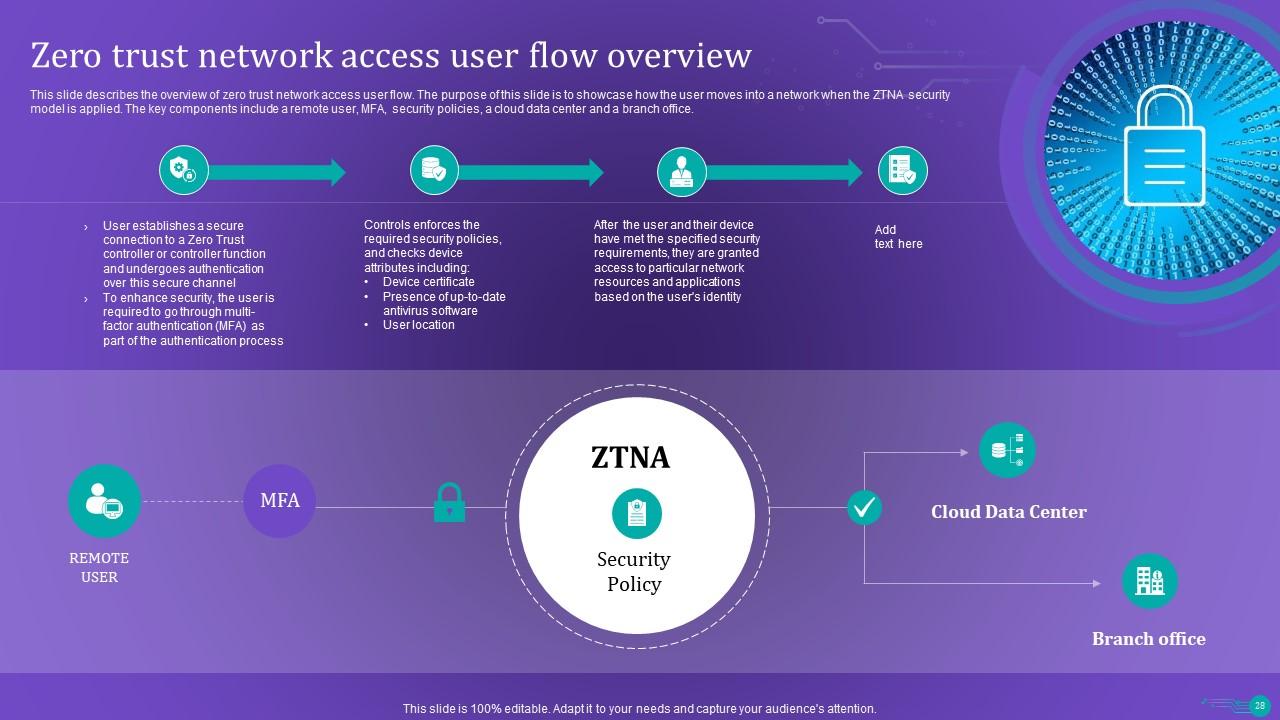
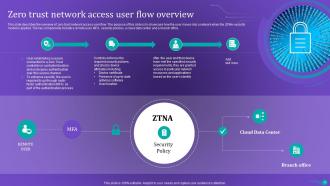
Slide 28: This slide describes the overview of zero trust network access user flow.
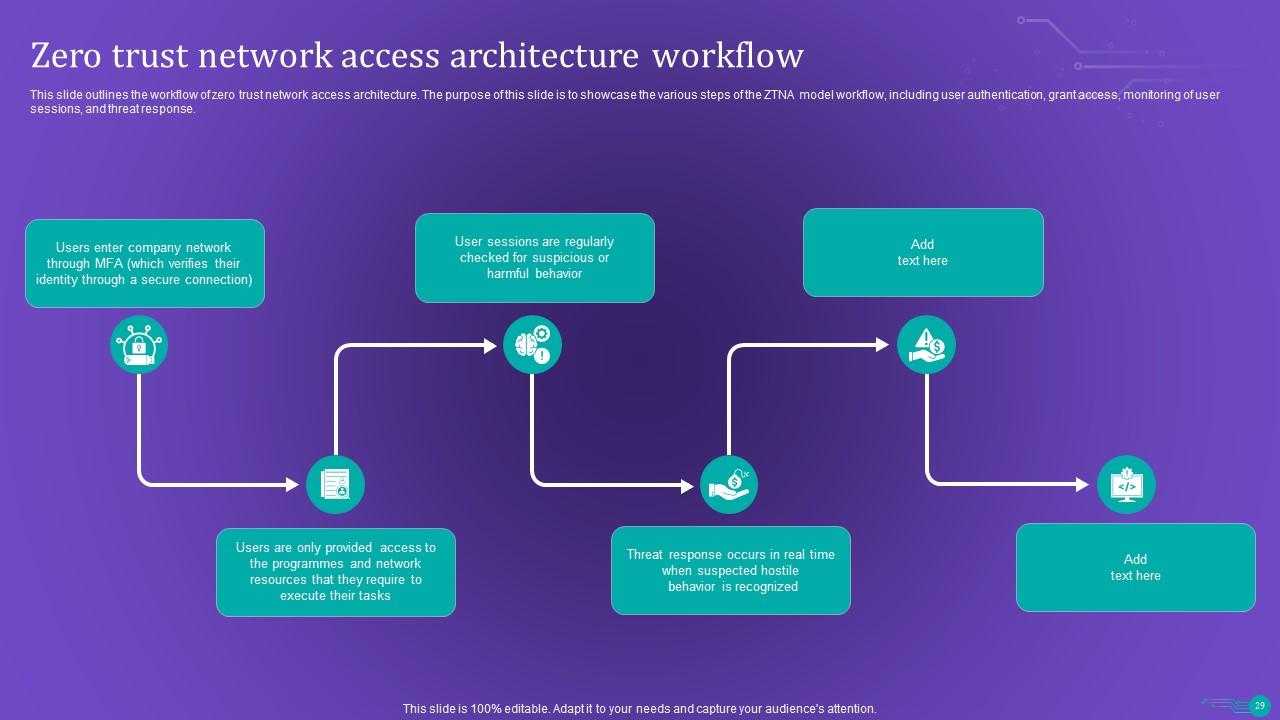
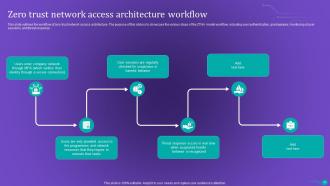
Slide 29: This slide outlines the workflow of zero trust network access architecture.
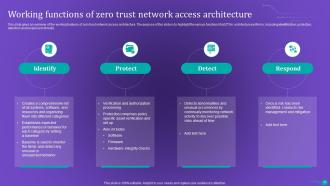
Slide 30: This slide gives an overview of the working features of zero trust network access architecture.
Slide 31: This slide shows Table of contents for ZTNA further.
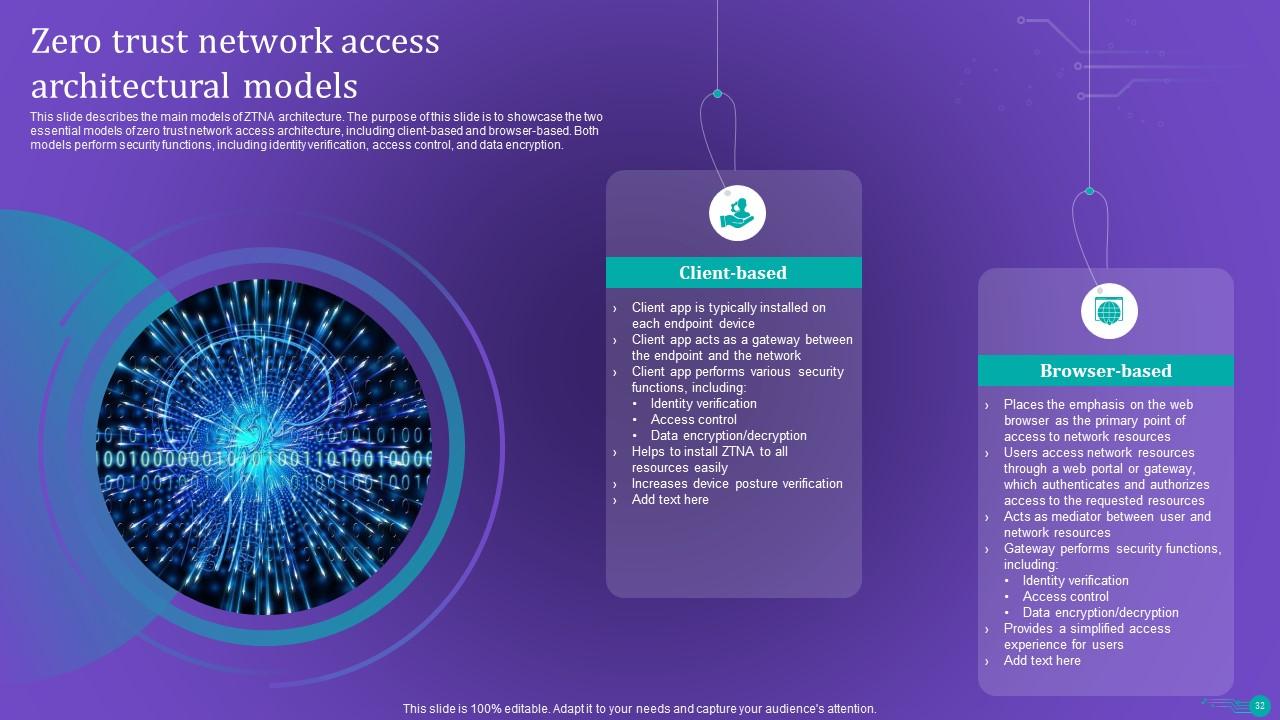
Slide 32: This slide describes the main models of ZTNA architecture.
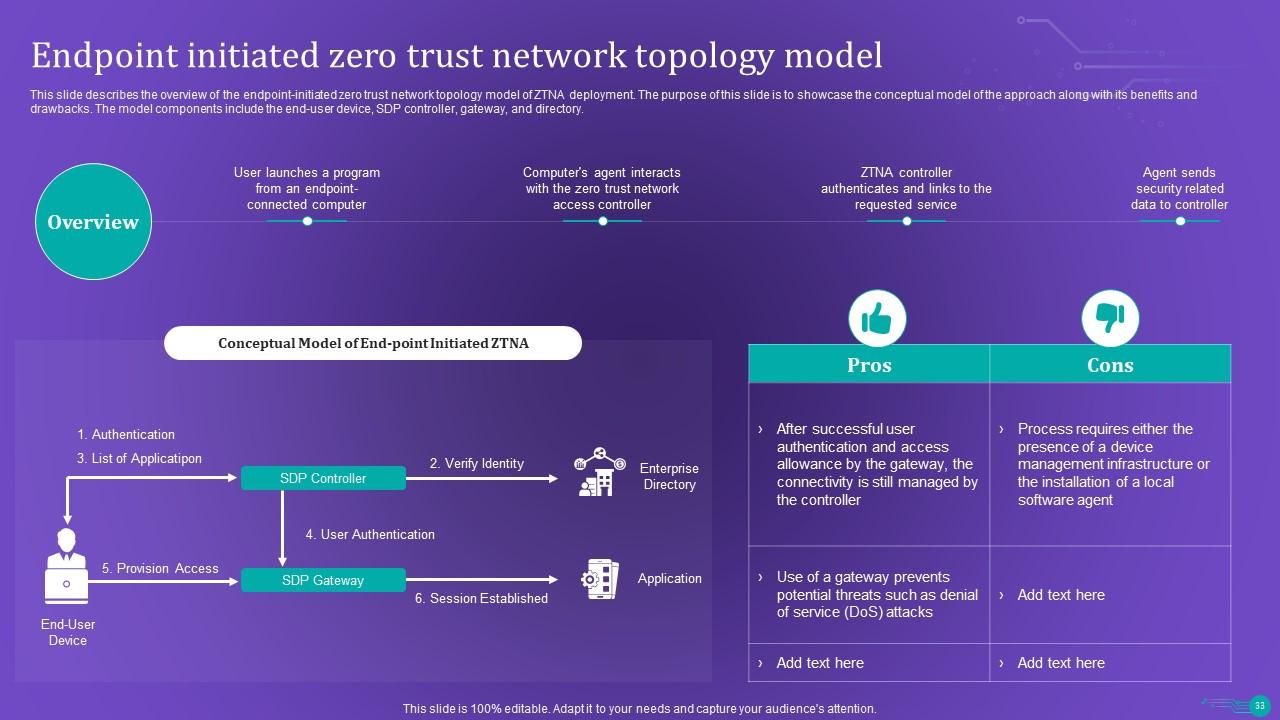
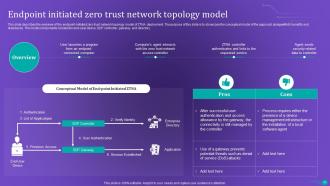
Slide 33: This slide shows the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment.
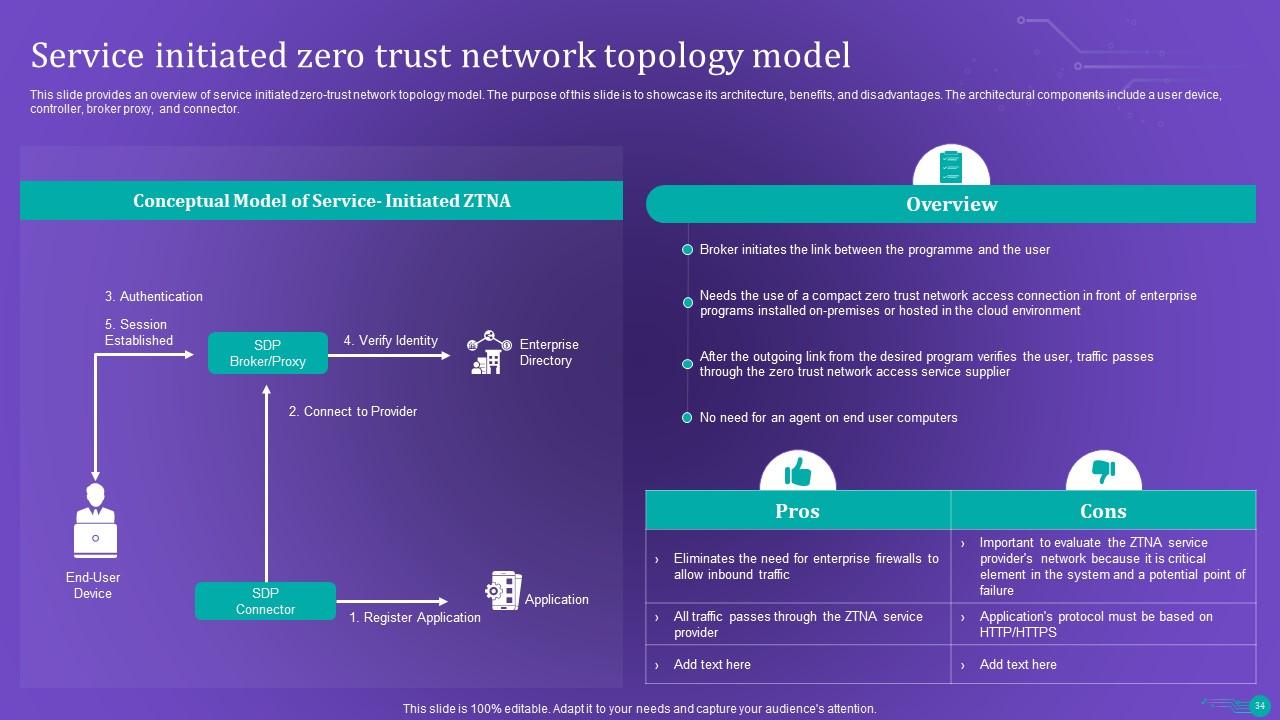
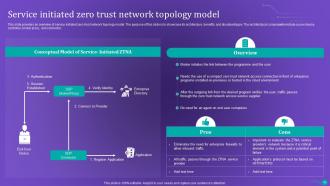
Slide 34: This slide provides an overview of service initiated zero-trust network topology model.
Slide 35: This slide highlights title of contents for presentation.
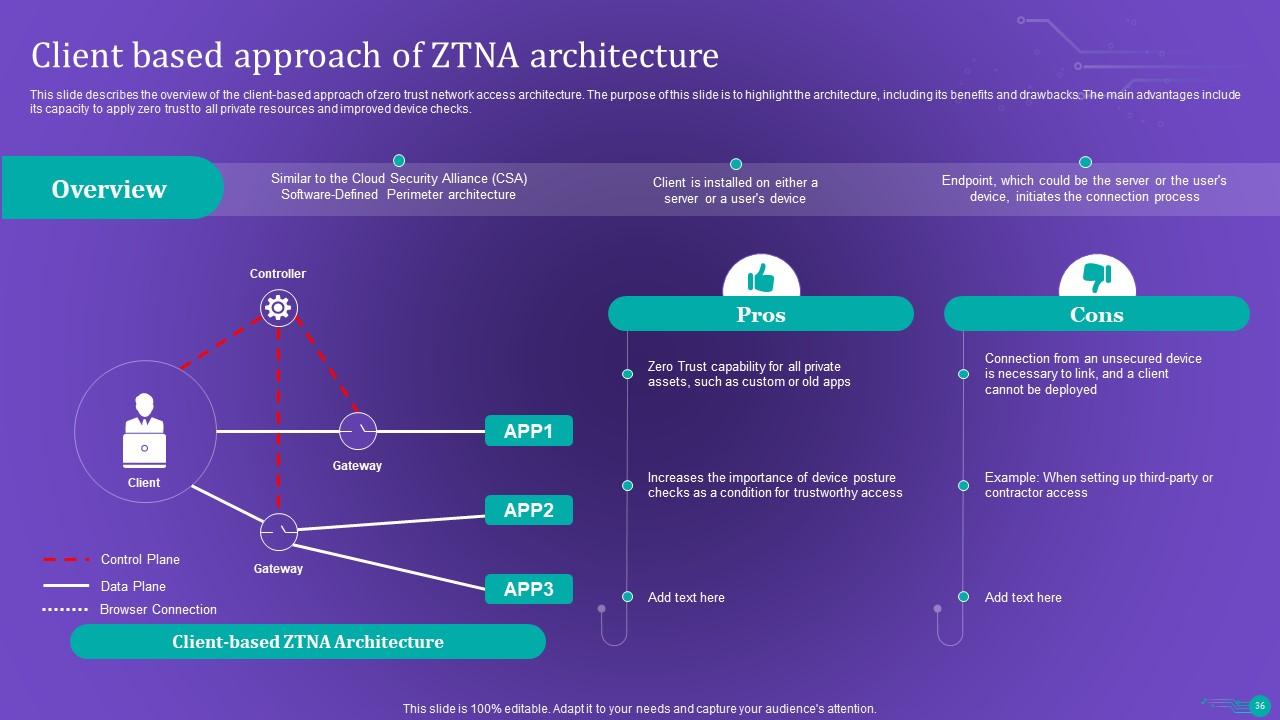
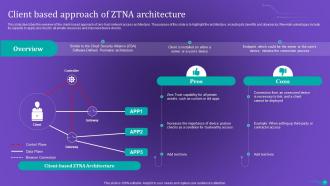
Slide 36: This slide describes the overview of the client-based approach of zero trust network access architecture.
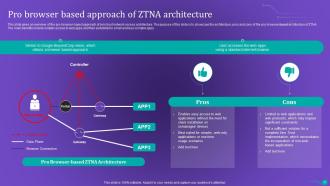
Slide 37: This slide gives an overview of the pro-browser-based approach of zero trust network access architecture.
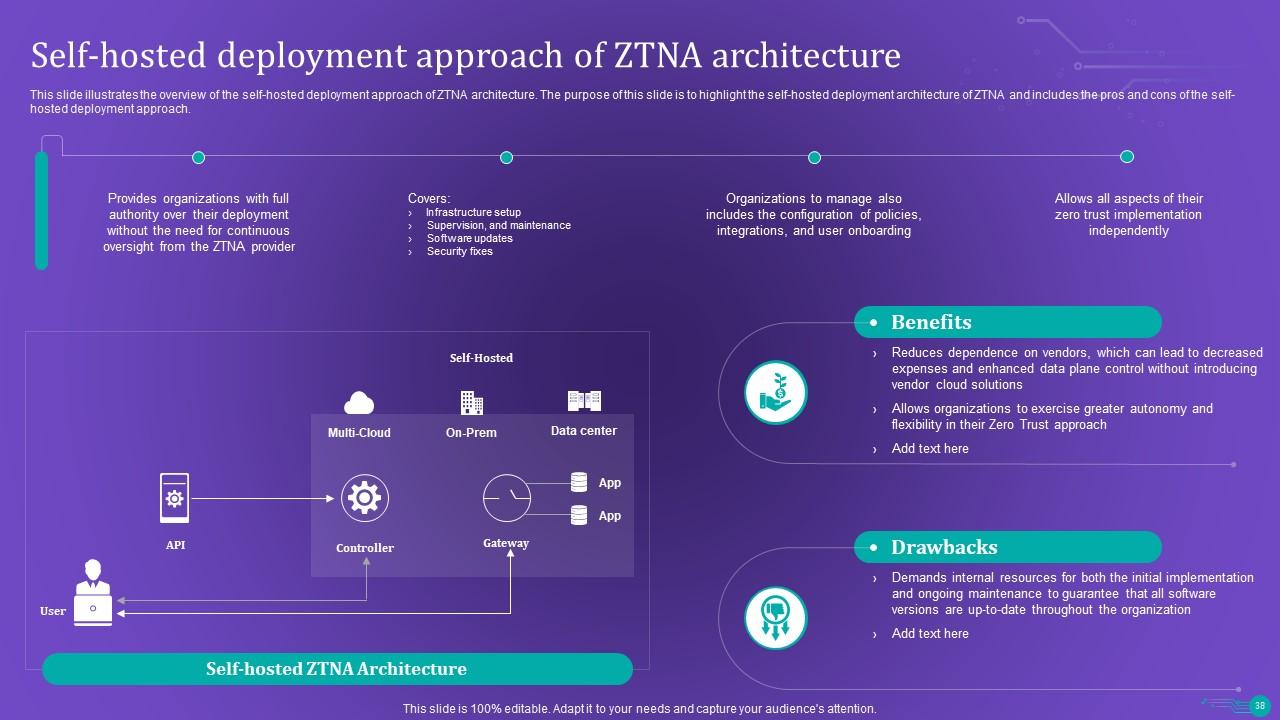
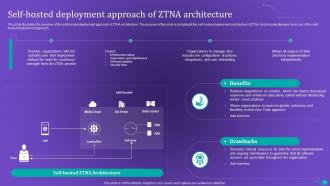
Slide 38: This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture.
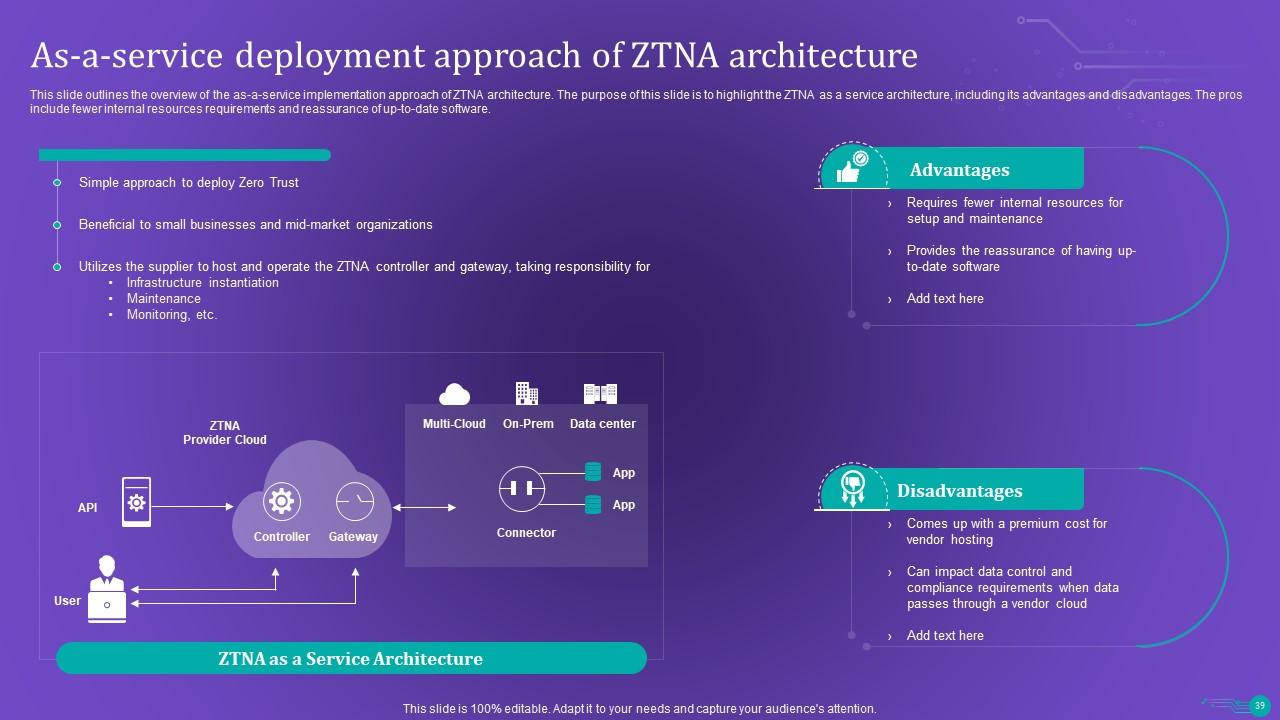
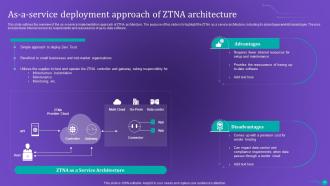
Slide 39: This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture.
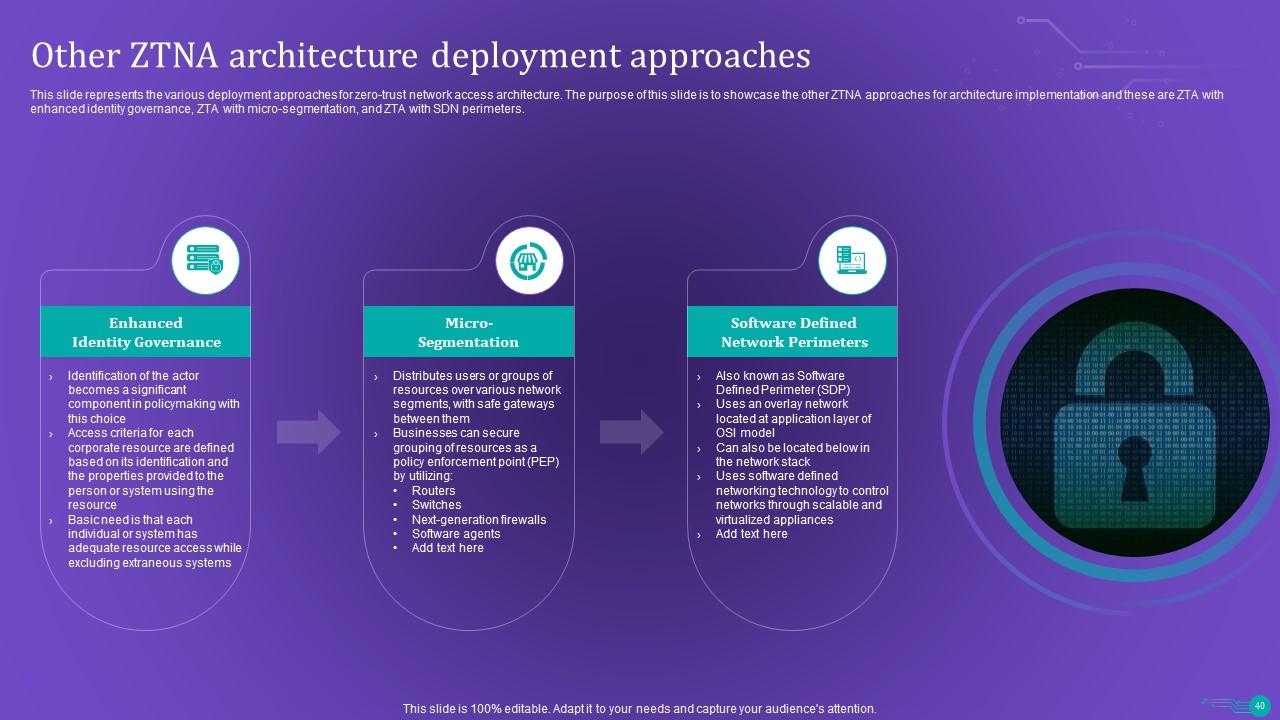
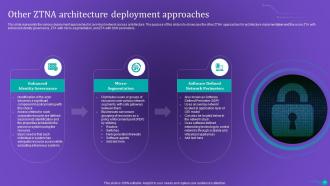
Slide 40: This slide represents the various deployment approaches for zero-trust network access architecture.
Slide 41: This slide presents Table of contents to be discussed further.
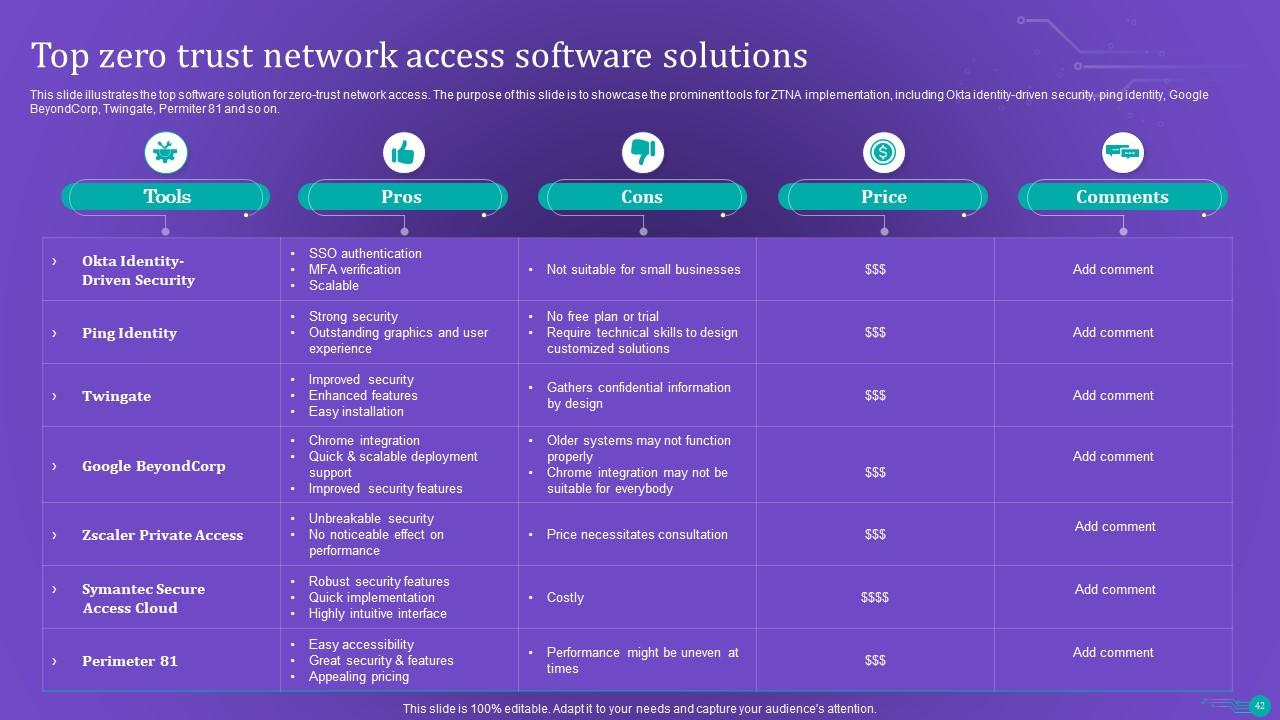
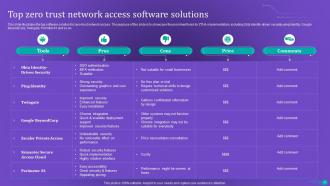
Slide 42: This slide depicts the top software solution for zero-trust network access.
Slide 43: This slide highlights the main criteria while choosing the right zero trust solution.
Slide 44: This slide represents the techniques used in the zero-trust network access model.
Slide 45: This slide contains titles for the topics to be discussed further.
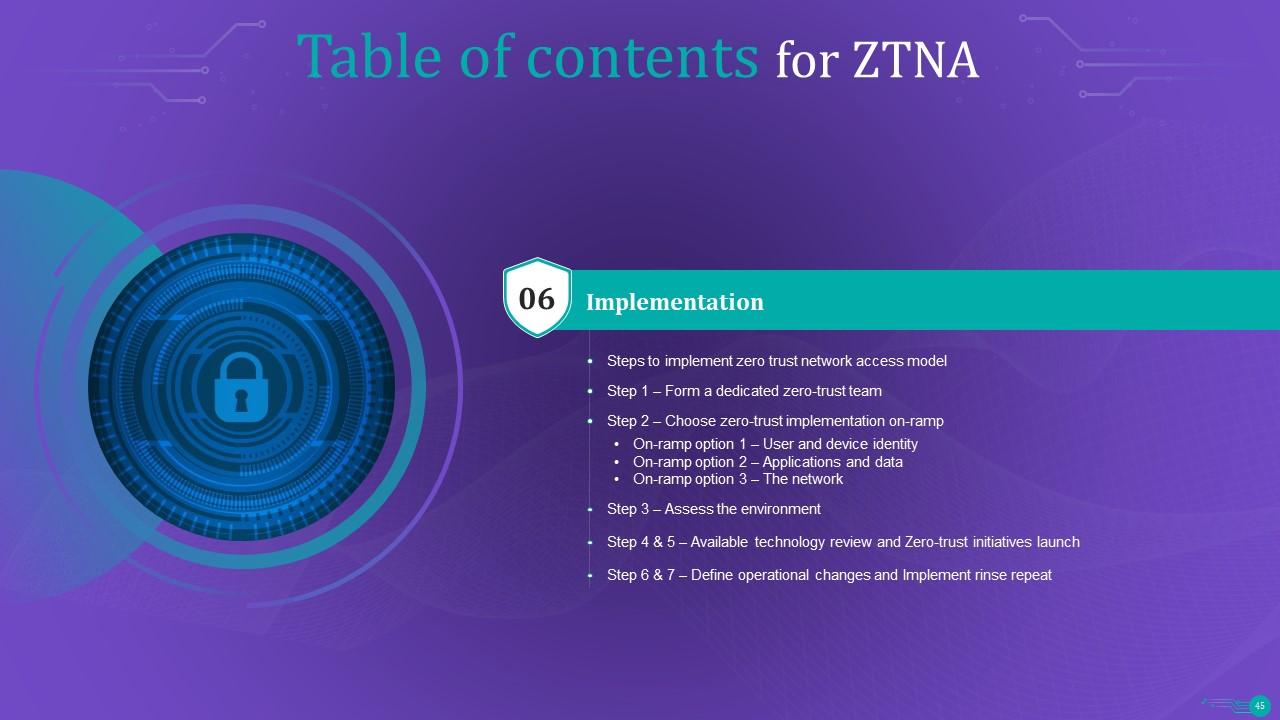
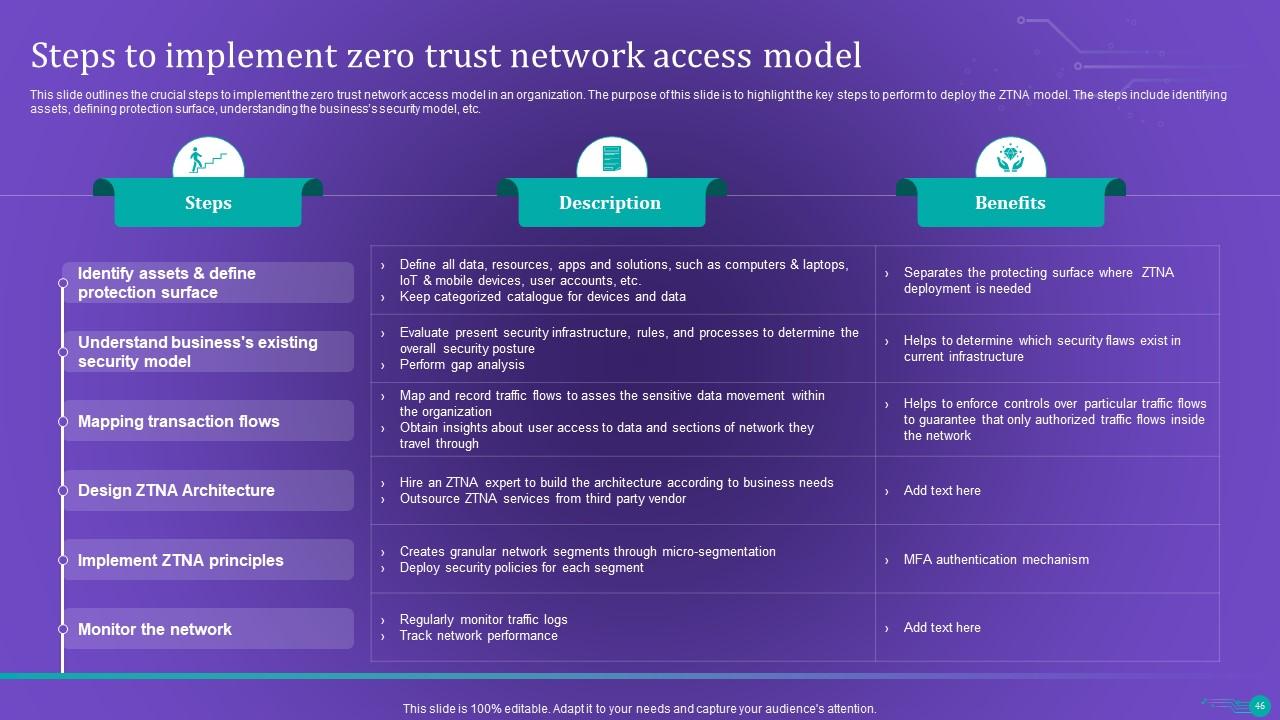
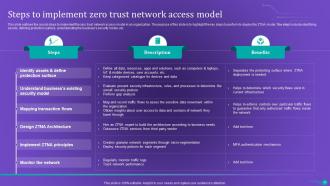
Slide 46: This slide outlines the crucial steps to implement the zero trust network access model in an organization.
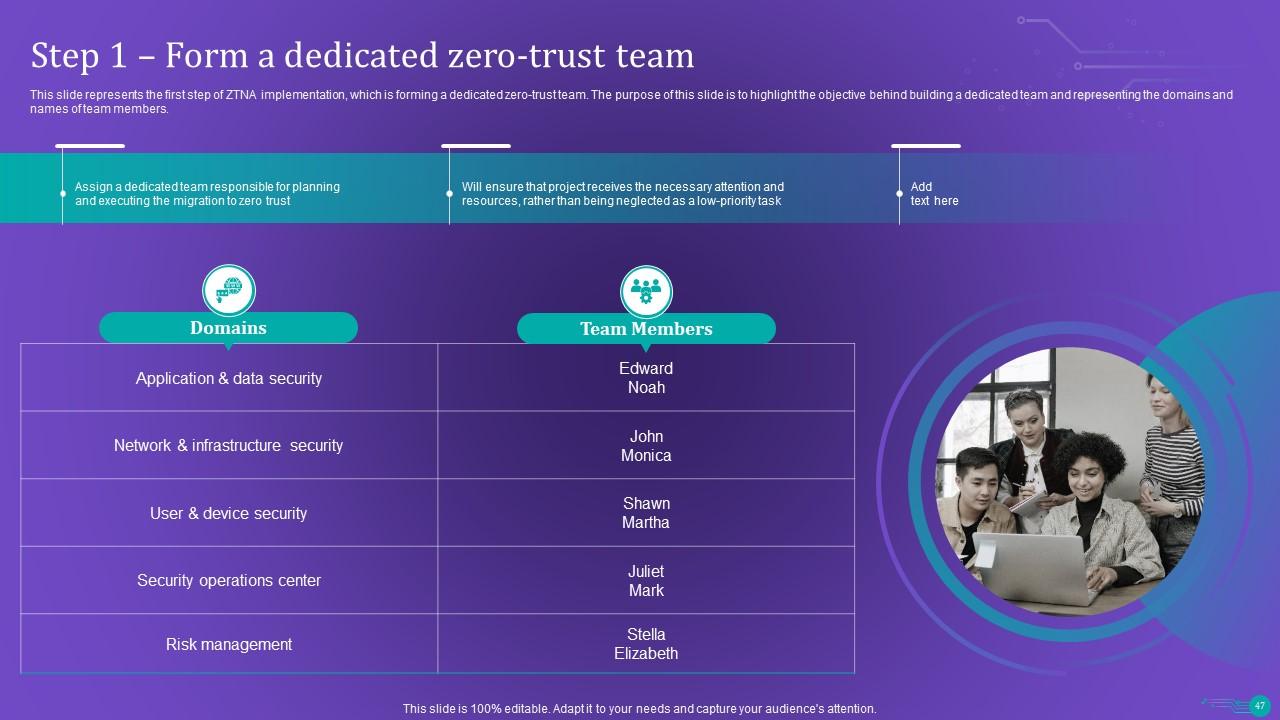
Slide 47: This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team.
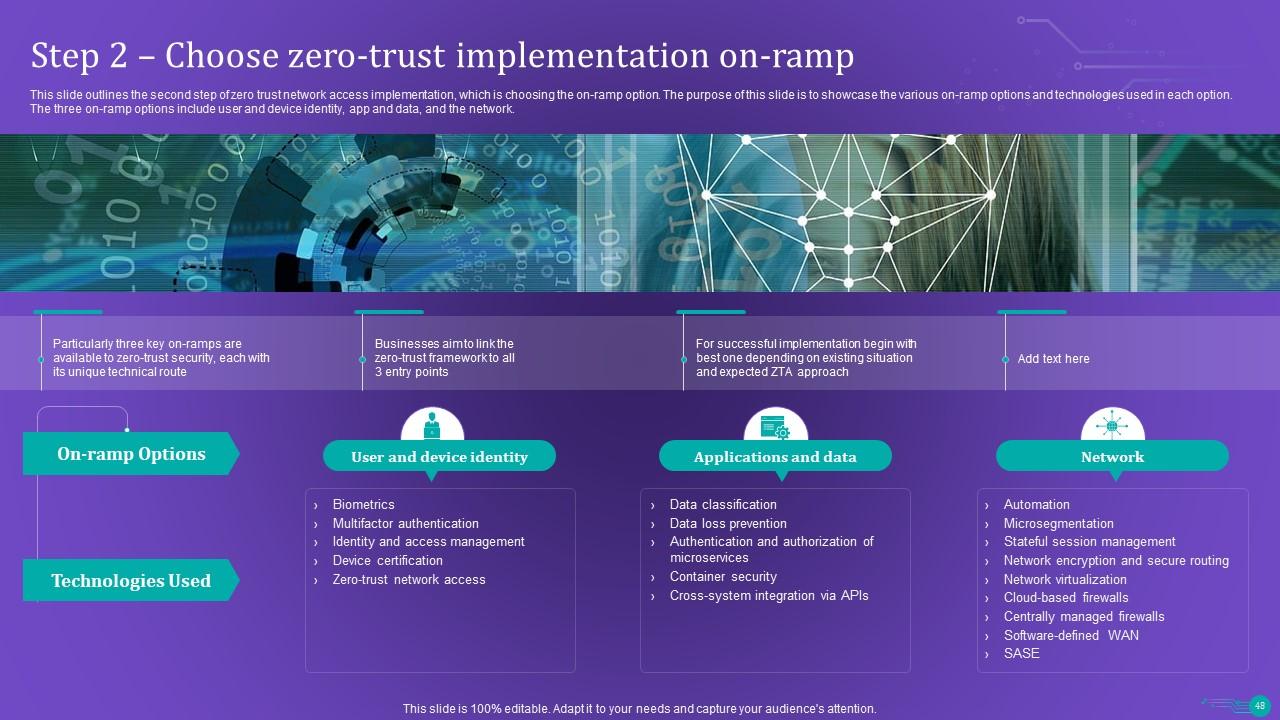
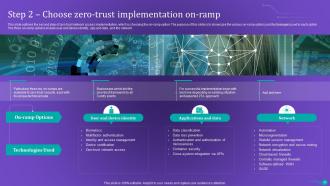
Slide 48: This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option.
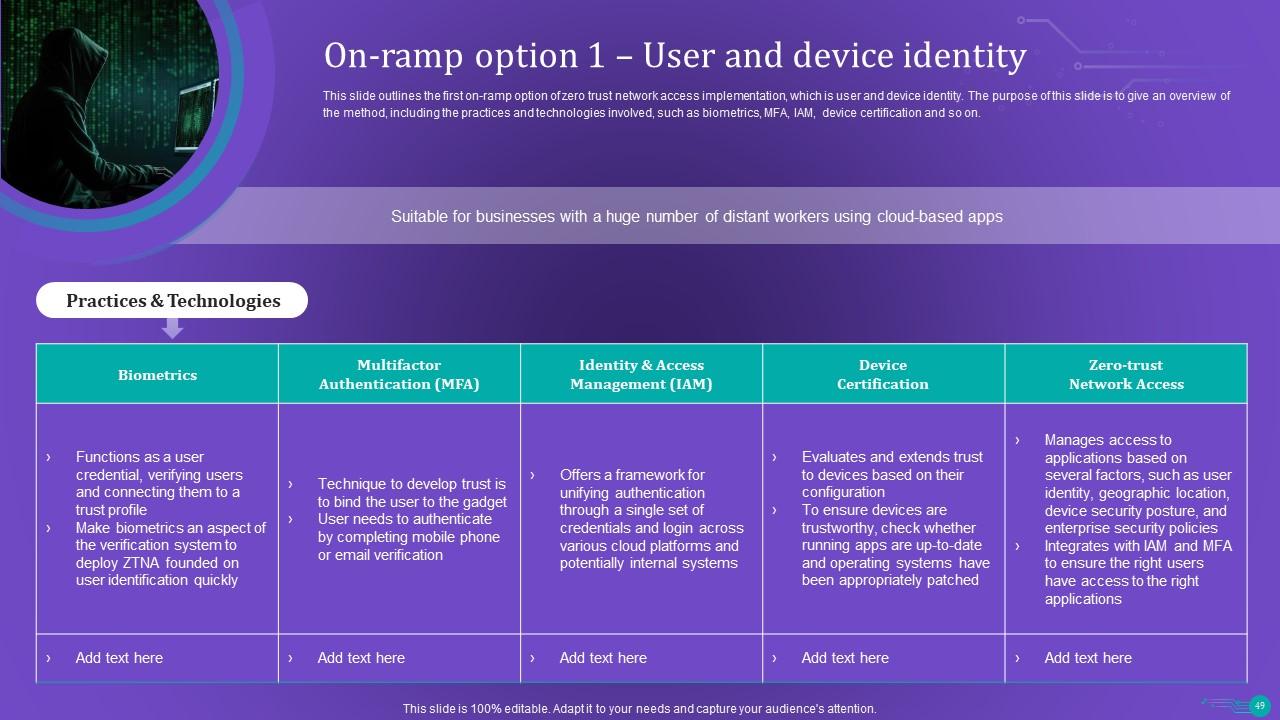
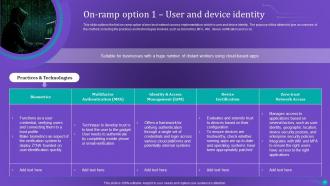
Slide 49: This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity.
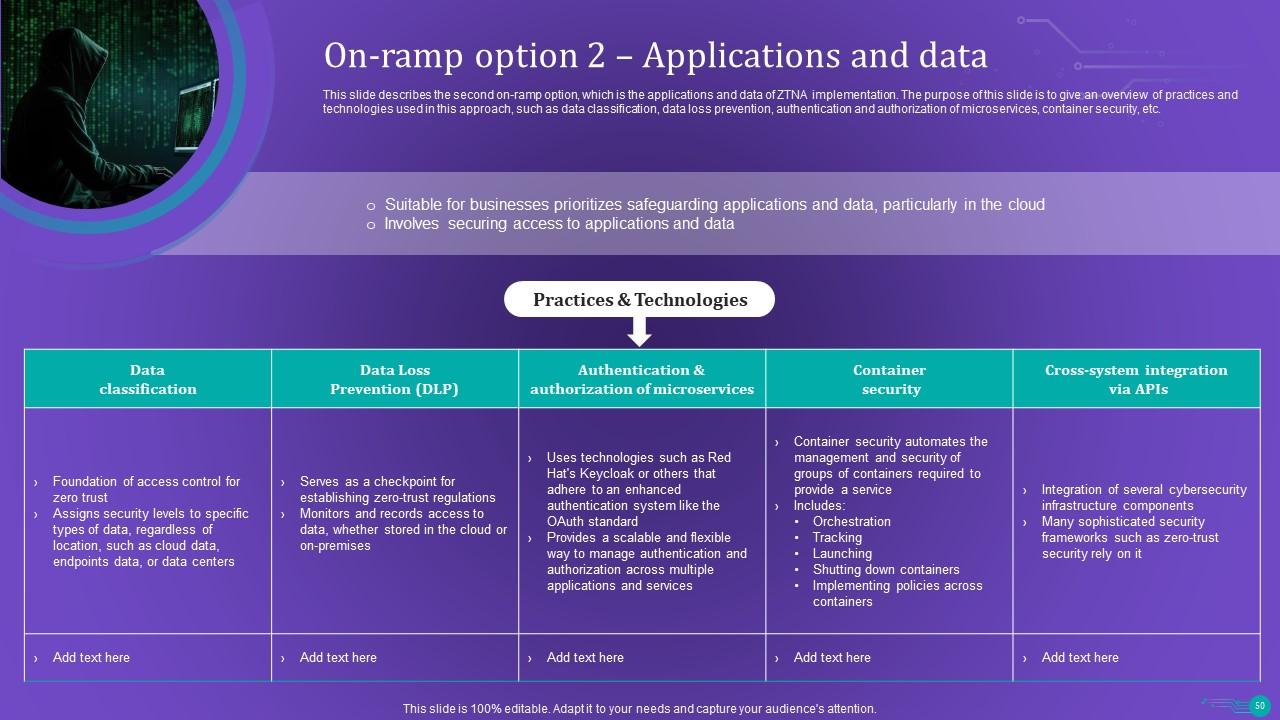
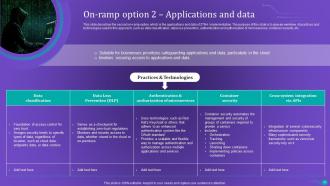
Slide 50: This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation.
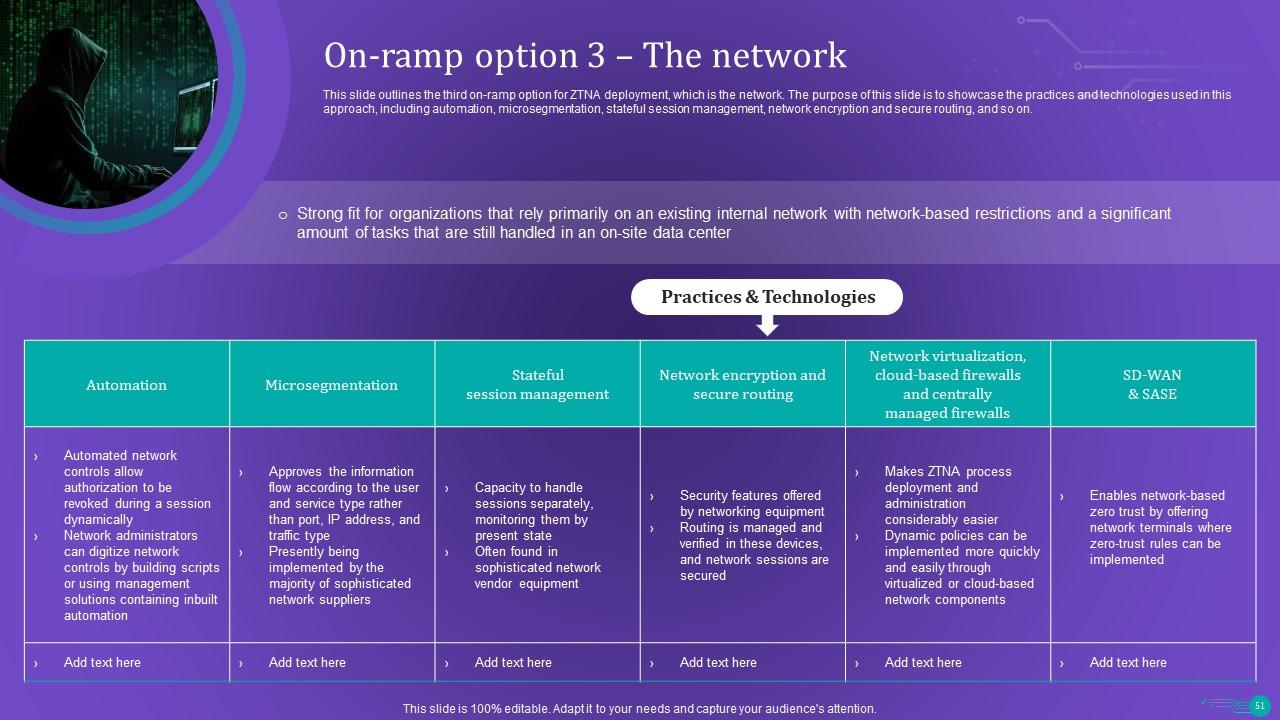
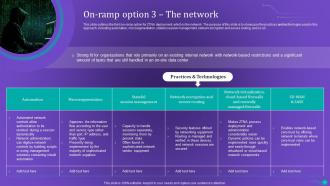
Slide 51: This slide outlines the third on-ramp option for ZTNA deployment, which is the network.
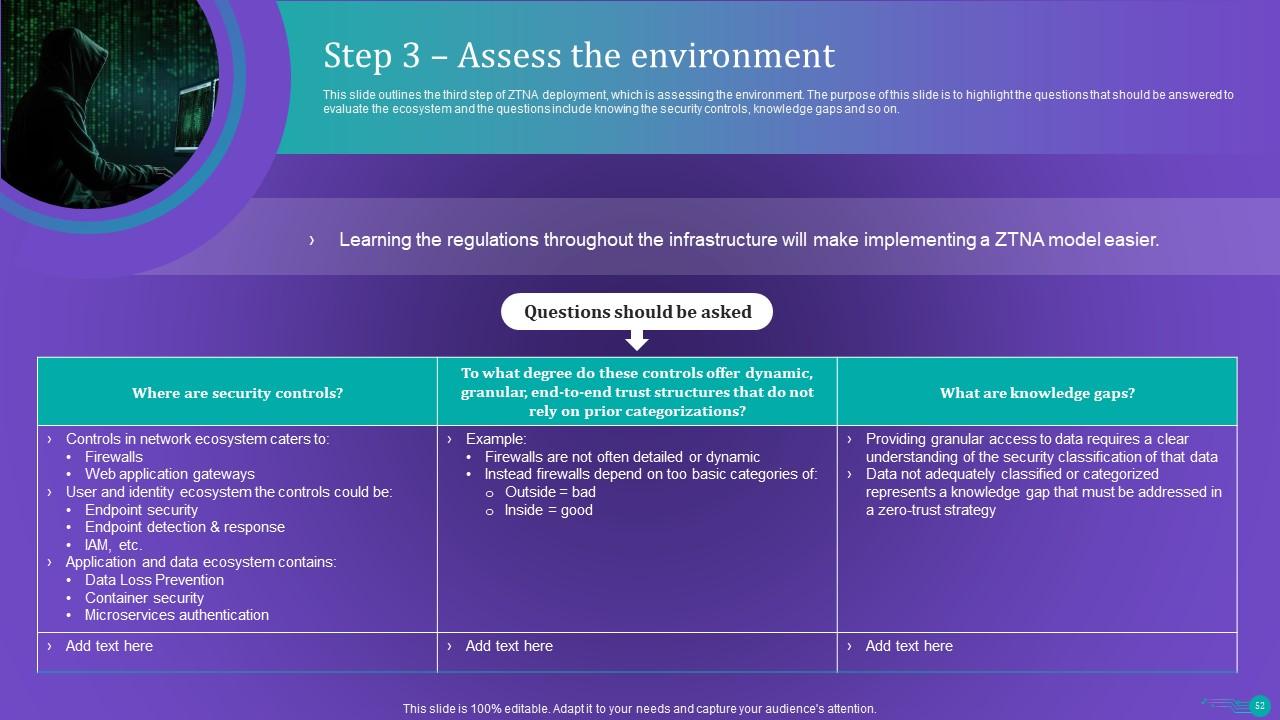
Slide 52: This slide outlines the third step of ZTNA deployment, which is assessing the environment.
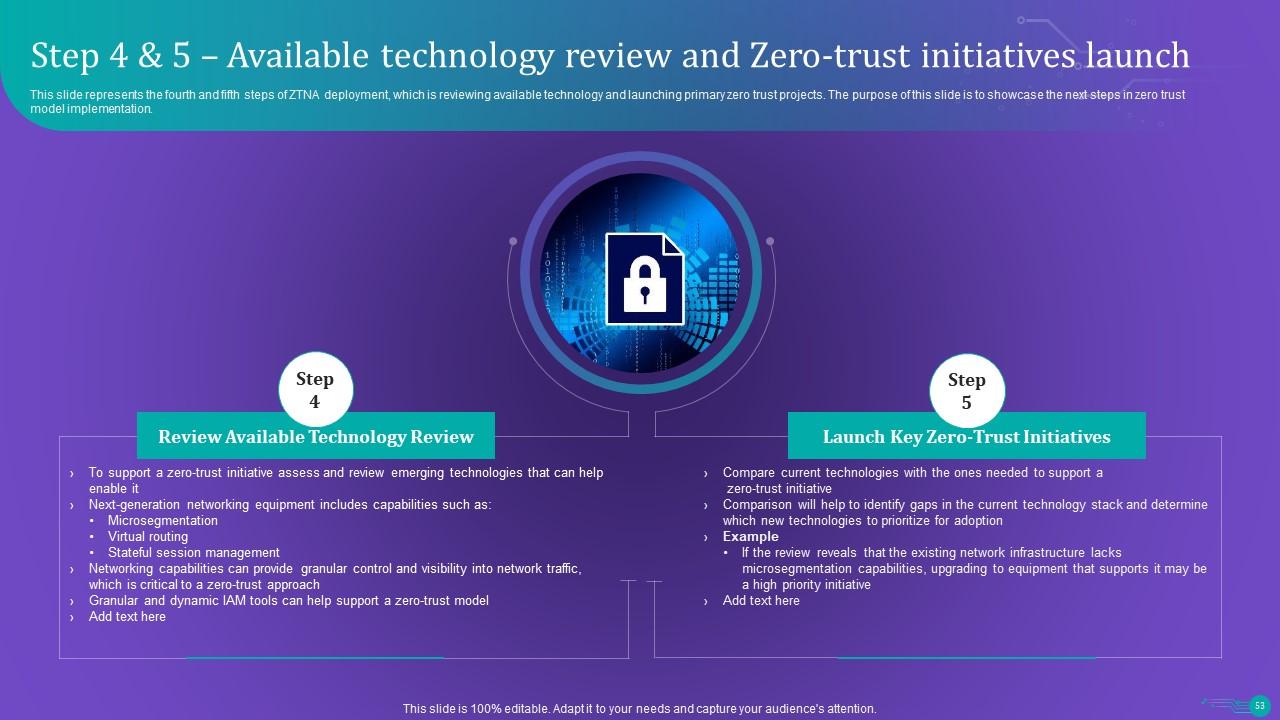
Slide 53: This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects.
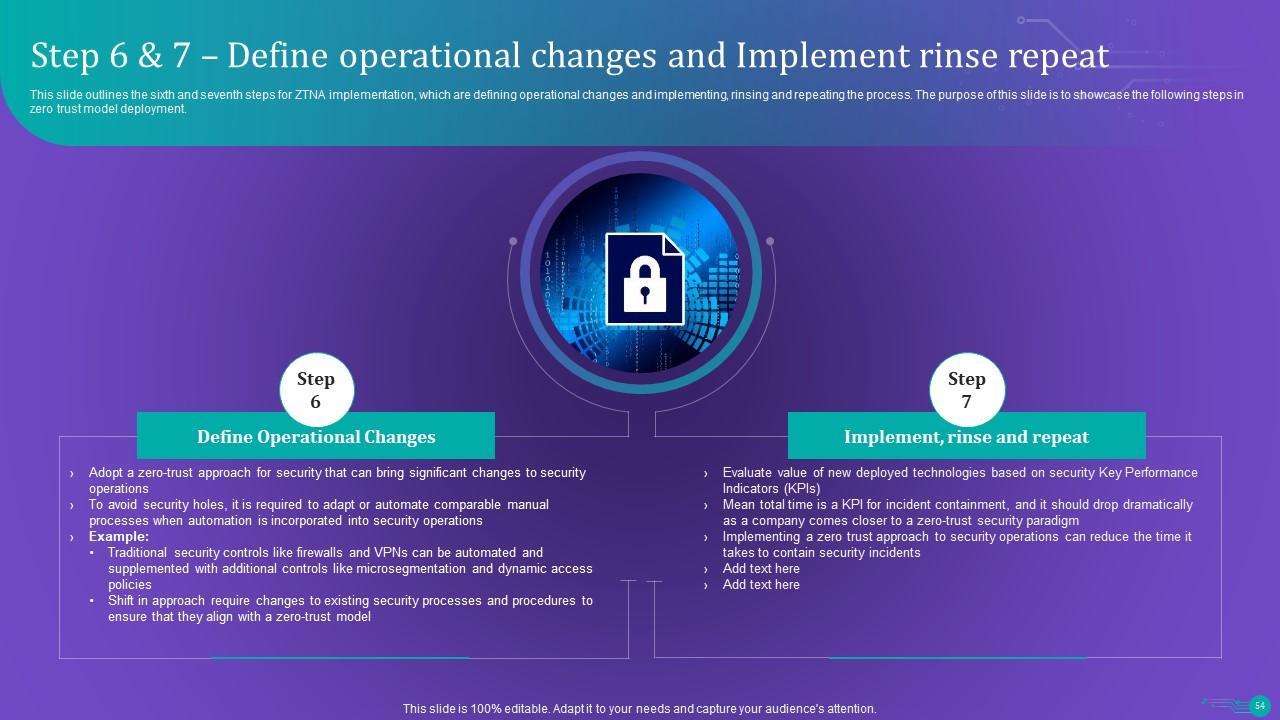
Slide 54: This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
Slide 55: This slide depicts Table of contents which is to be discussed further.
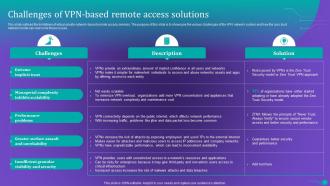
Slide 56: This slide outlines the main challenges of ZTNA implementation.
Slide 57: This slide talks about the various solutions to overcome the ZTNA deployment challenges.
Slide 58: This slide shows Title for the topics to be discussed further.
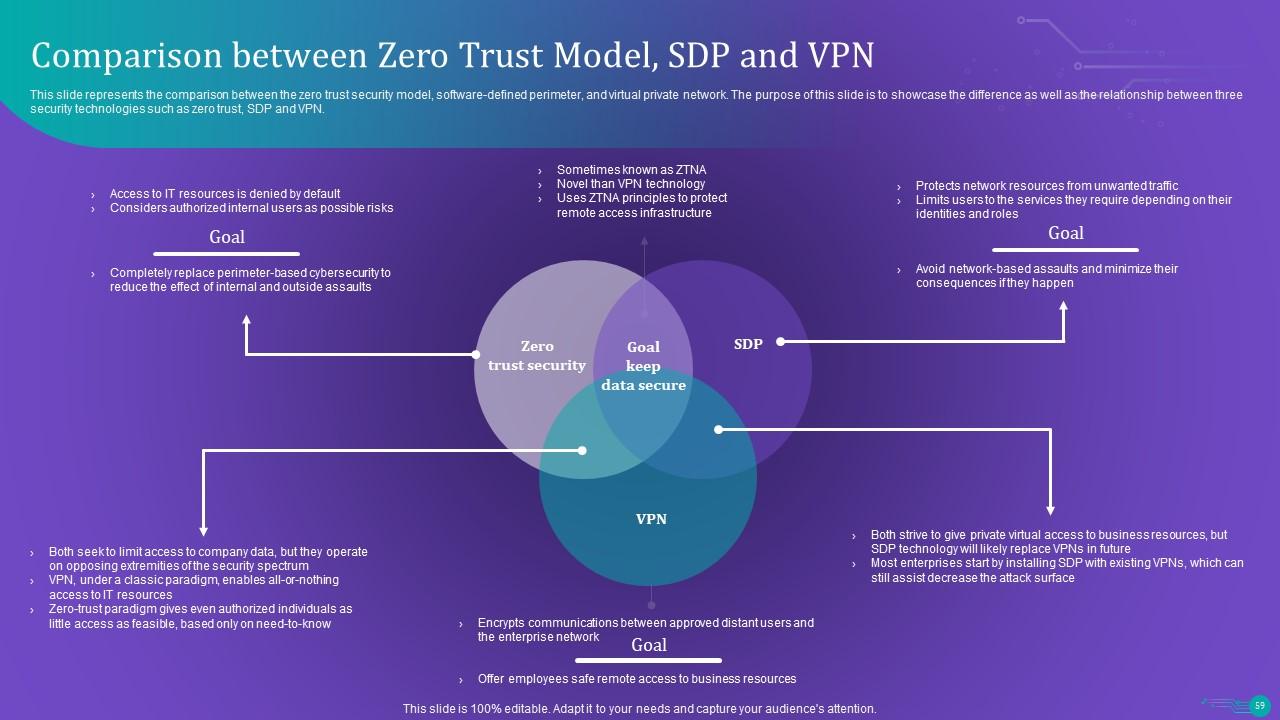
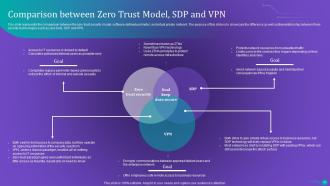
Slide 59: This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network.
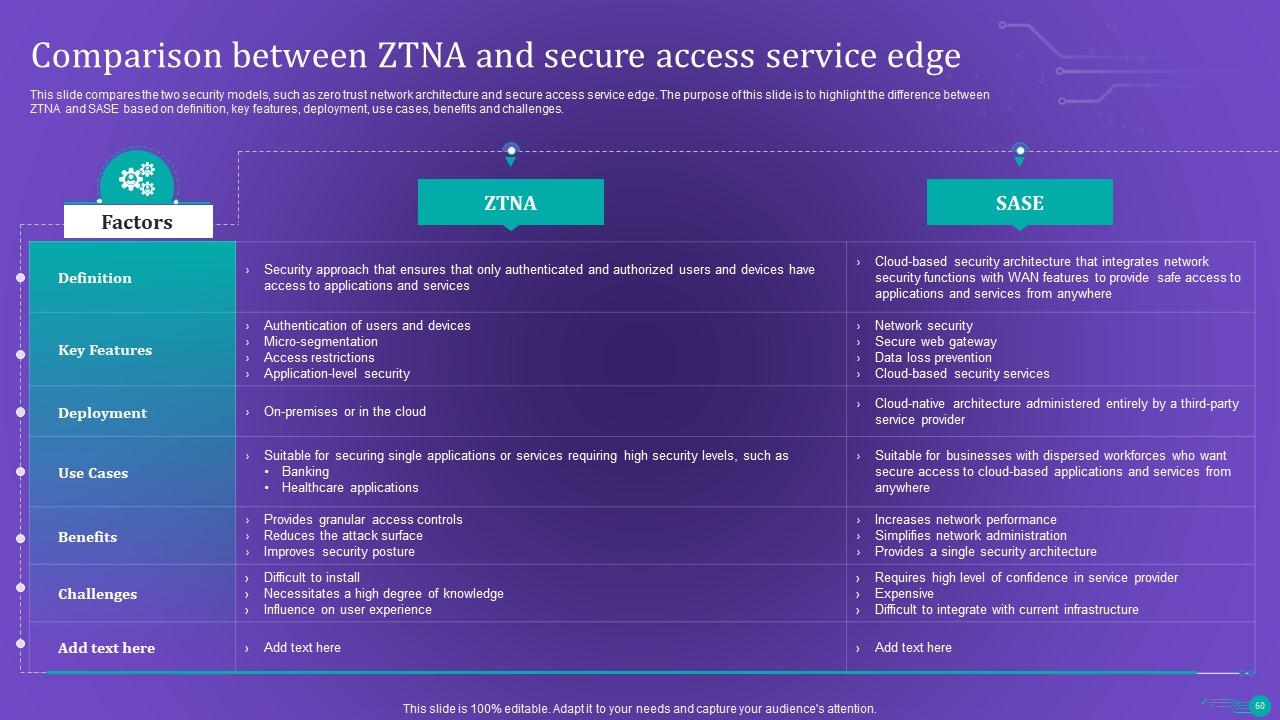
Slide 60: This slide compares the two security models.
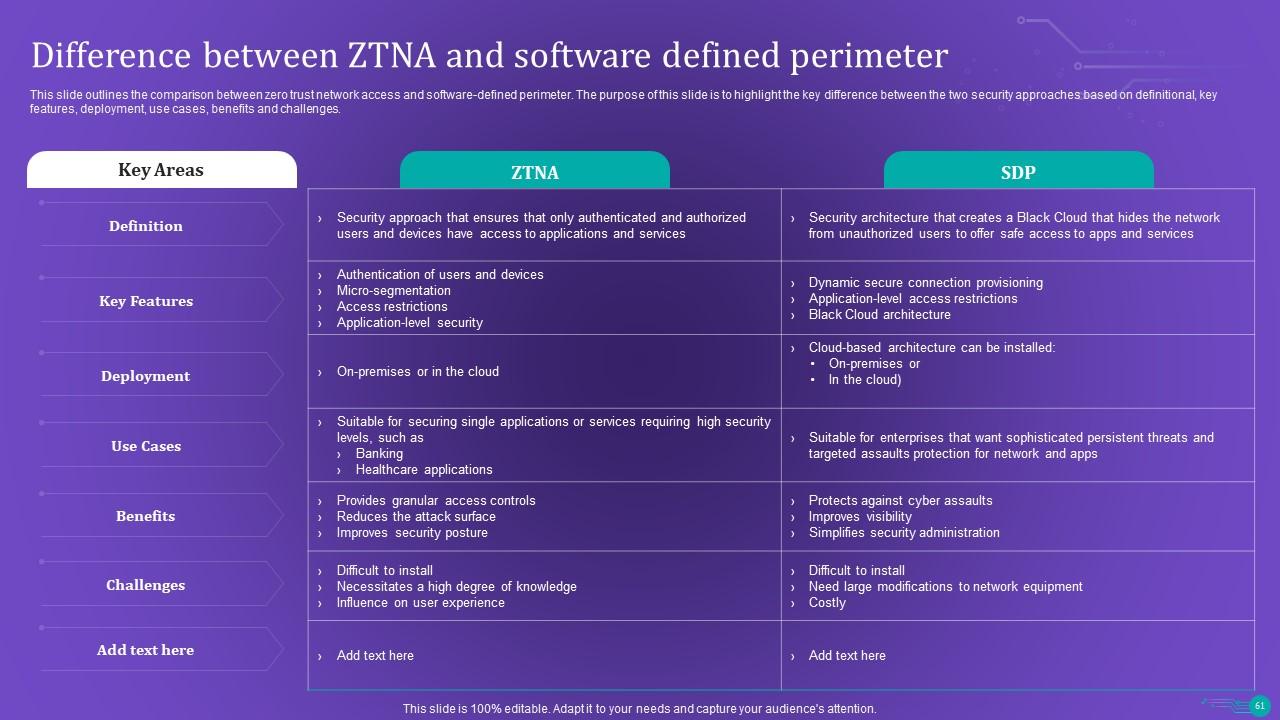
Slide 61: This slide outlines the comparison between zero trust network access and software-defined perimeter.
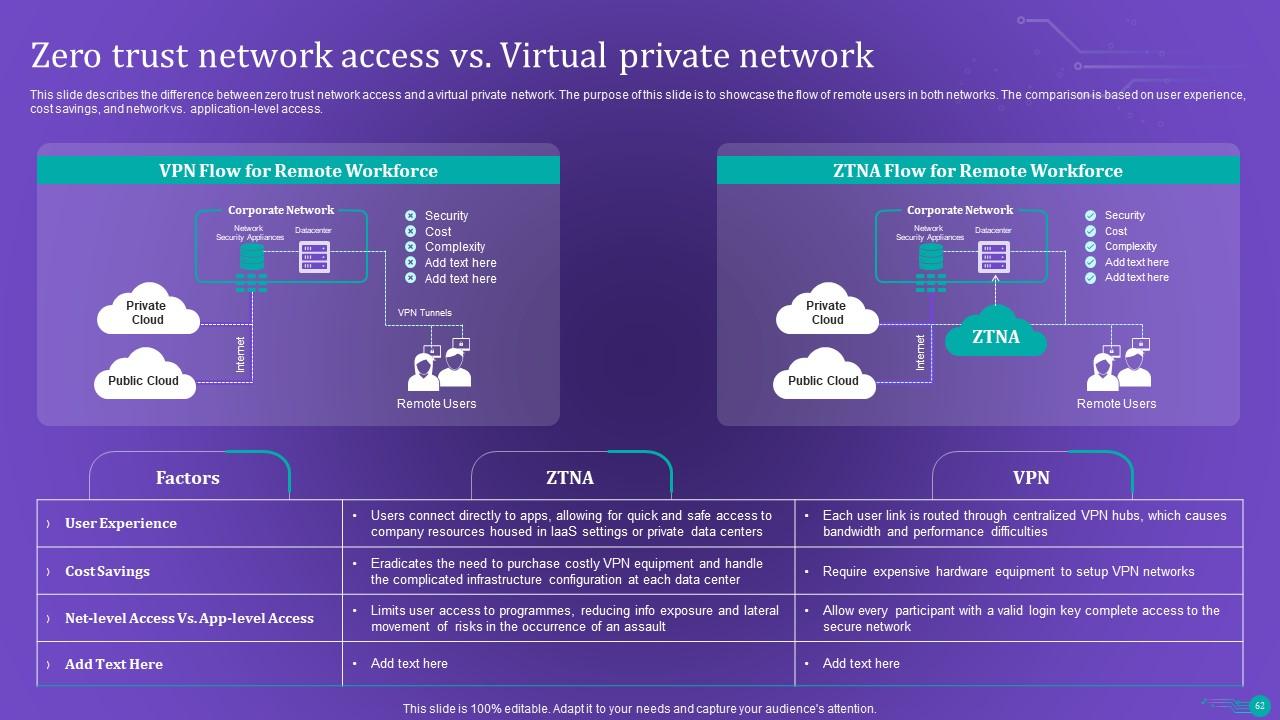
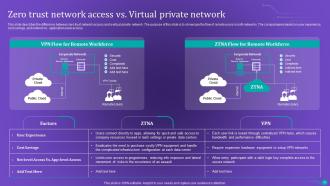
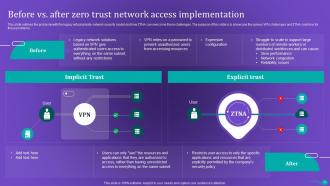
Slide 62: This slide describes the difference between zero trust network access and a virtual private network.
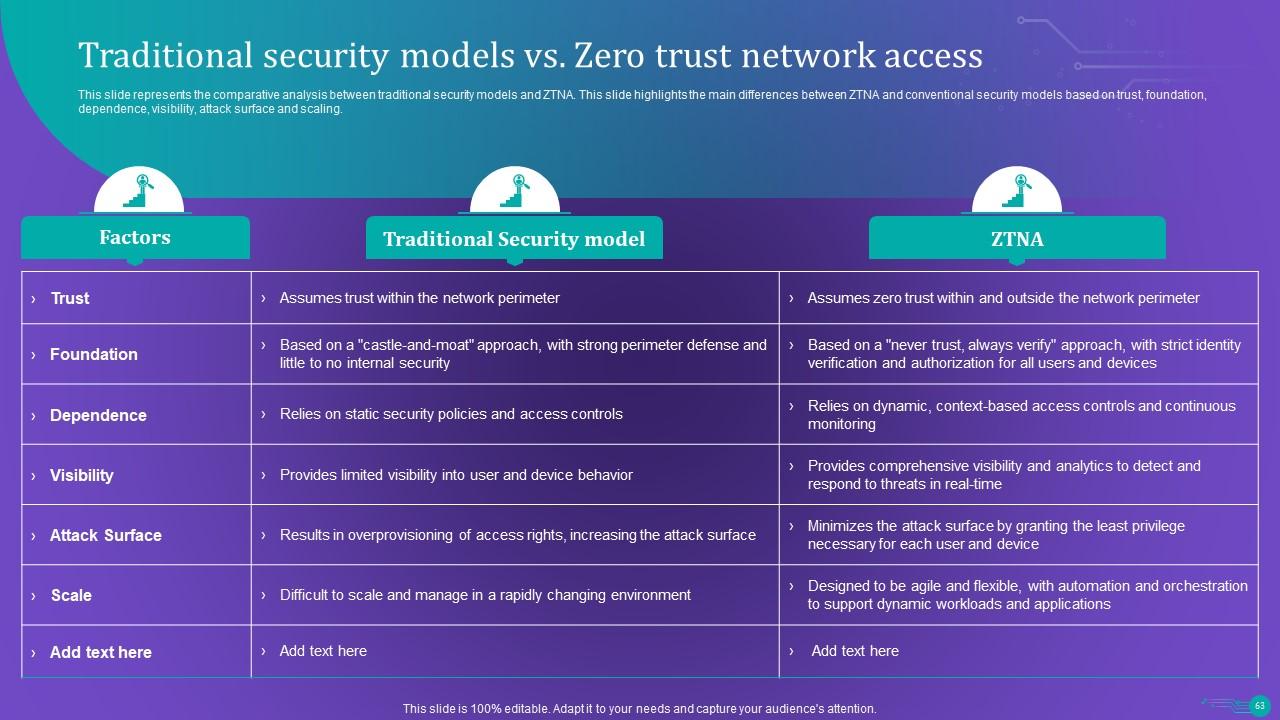
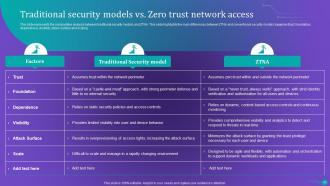
Slide 63: This slide presents the comparative analysis between traditional security models and ZTNA.
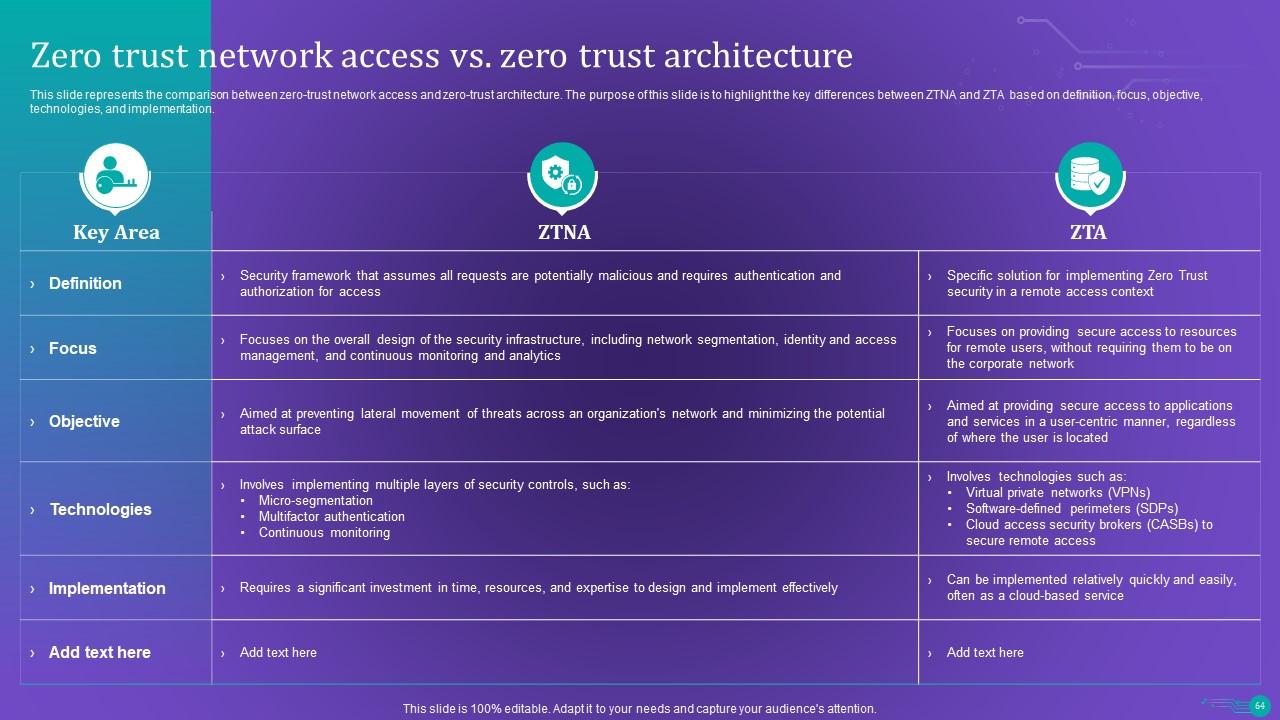
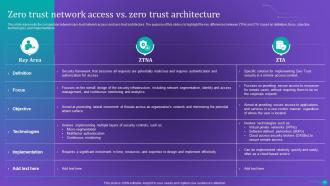
Slide 64: This slide represents the comparison between zero-trust network access and zero-trust architecture.
Slide 65: This slide depicts Table of contents for ZTNA
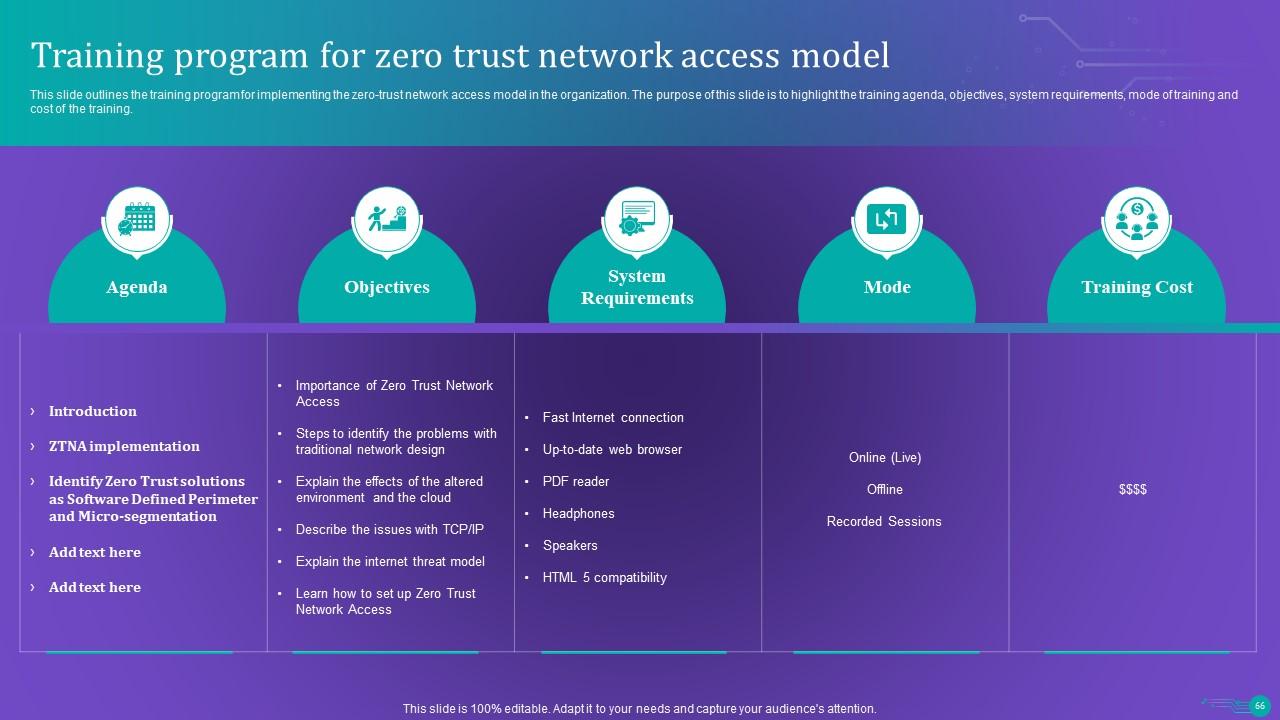
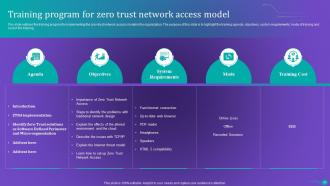
Slide 66: This slide outlines the training program for implementing the zero-trust network access model in the organization.
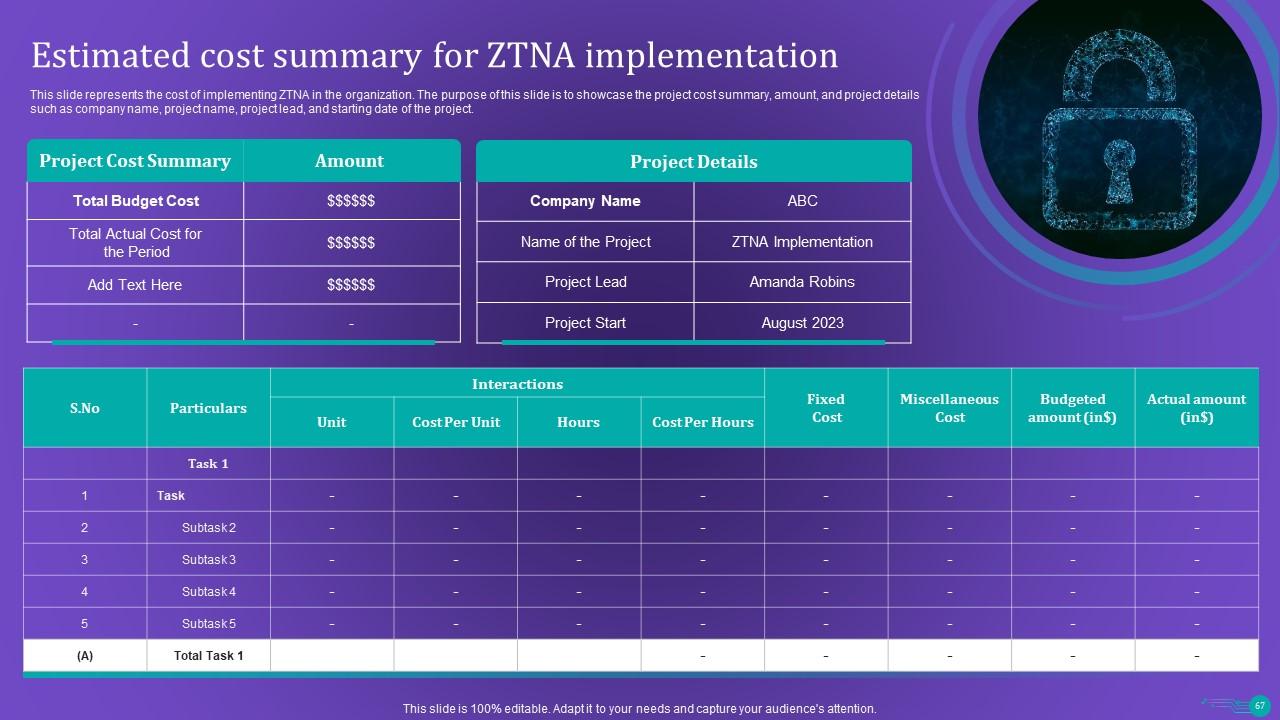
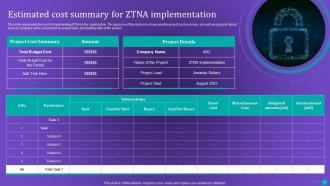
Slide 67: This slide represents the cost of implementing ZTNA in the organization.
Slide 68: This slide continues Table of contents for ZTNA.
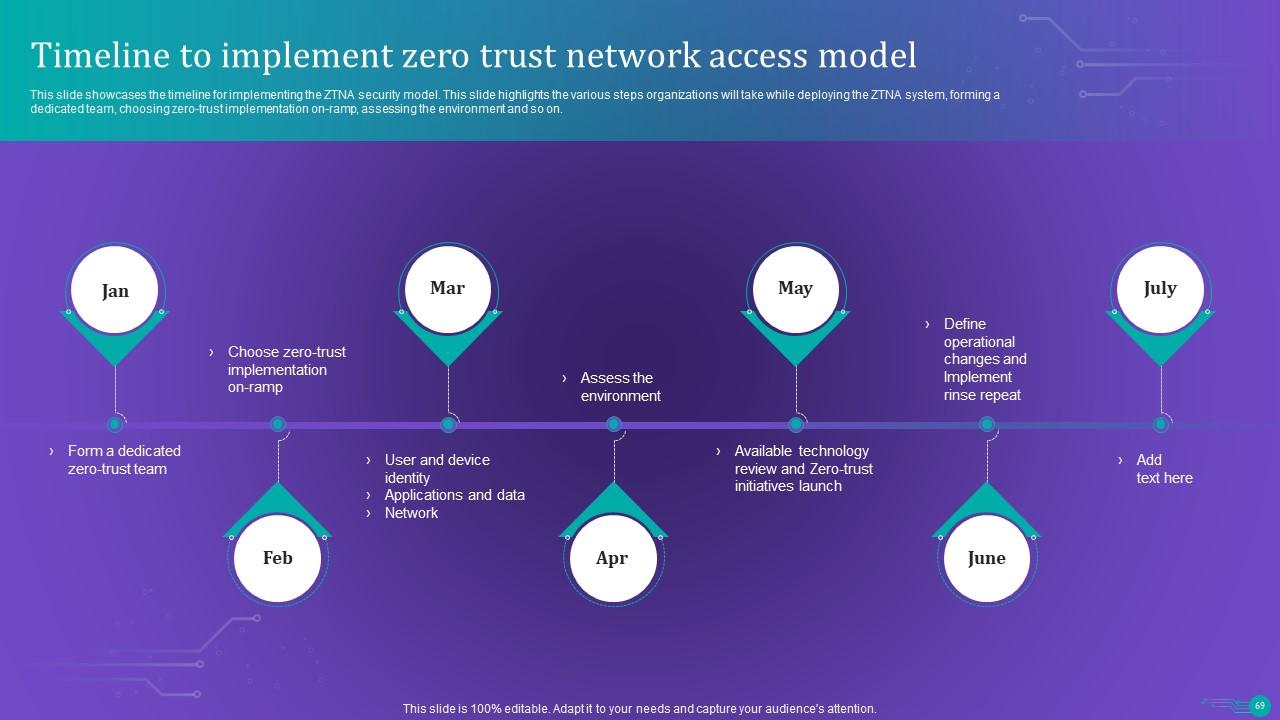
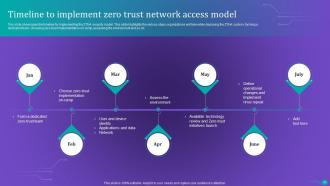
Slide 69: This slide showcases the timeline for implementing the ZTNA security model.
Slide 70: This slide shows Table of contents-Roadmap to implement zero trust network access model.
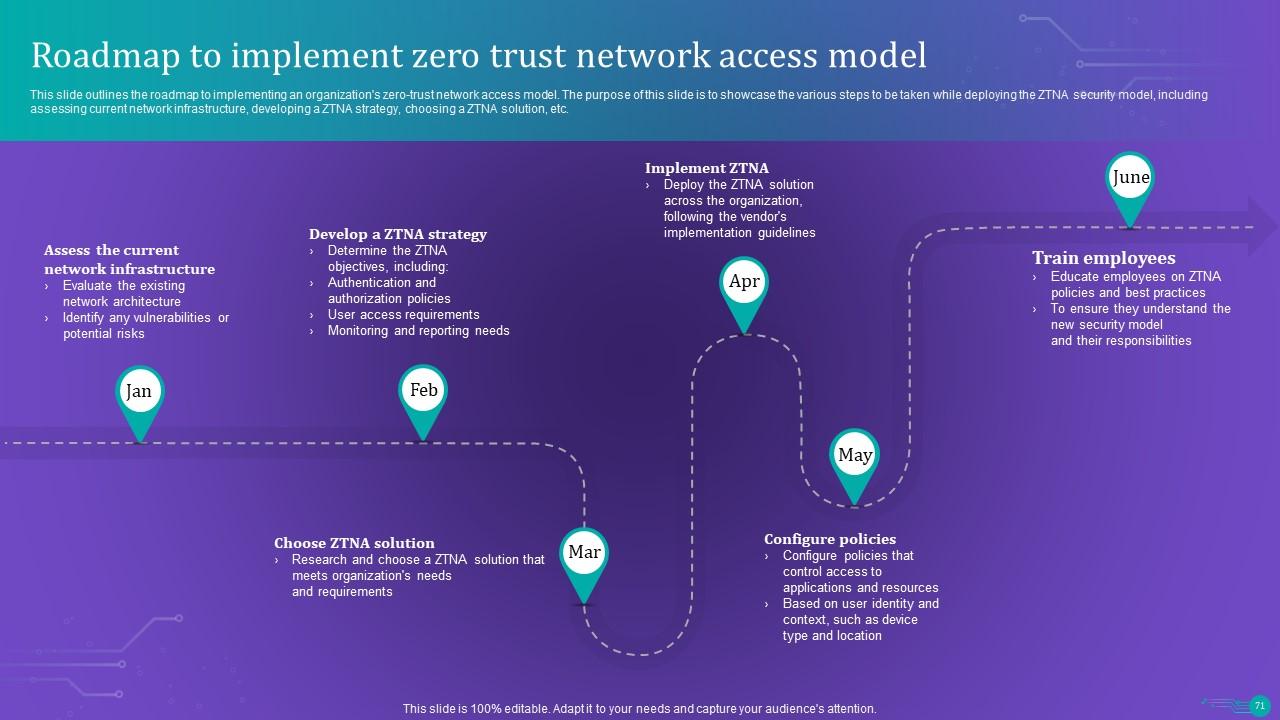
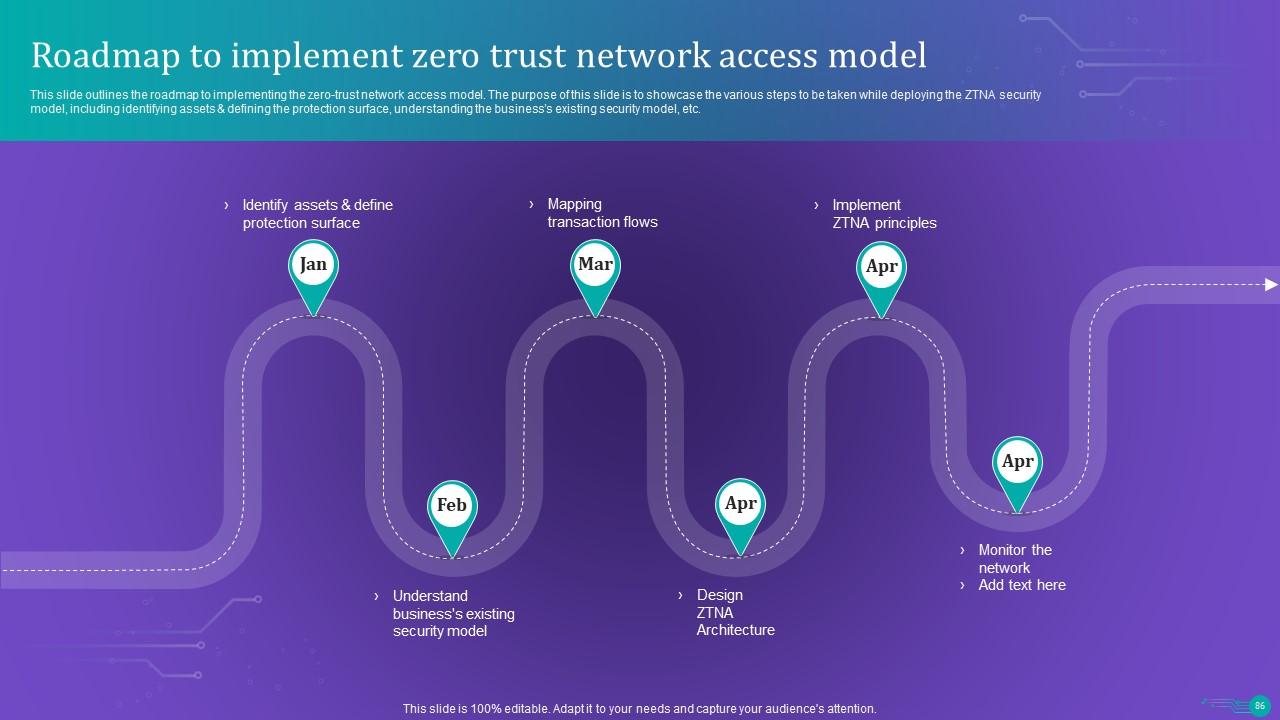
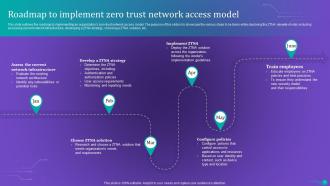
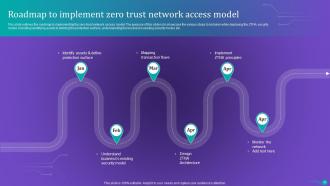
Slide 71: This slide outlines the roadmap to implementing an organization's zero-trust network access model.
Slide 72: This slide highlights Title of contents-Zero trust network access performance tracking dashboard.
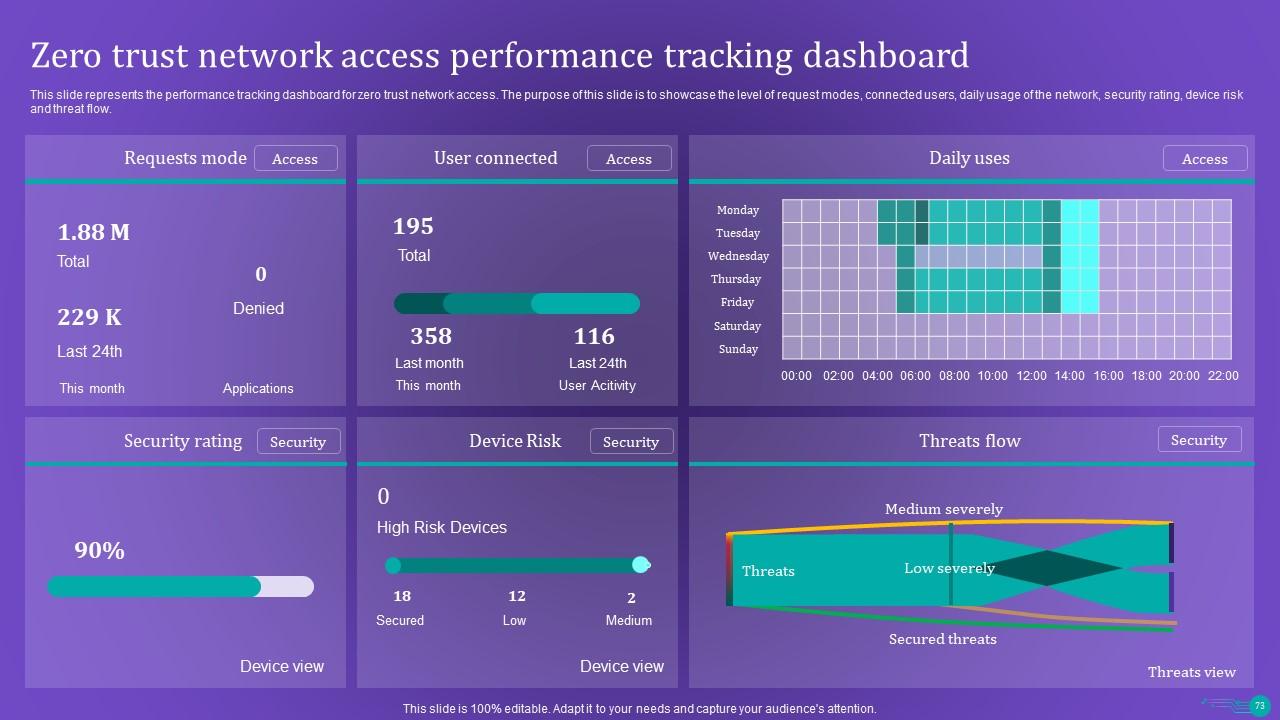
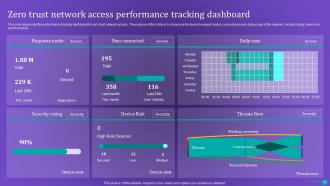
Slide 73: This slide represents the performance tracking dashboard for zero trust network access.
Slide 74: This slide showcases Table of contents for ZTNA further.
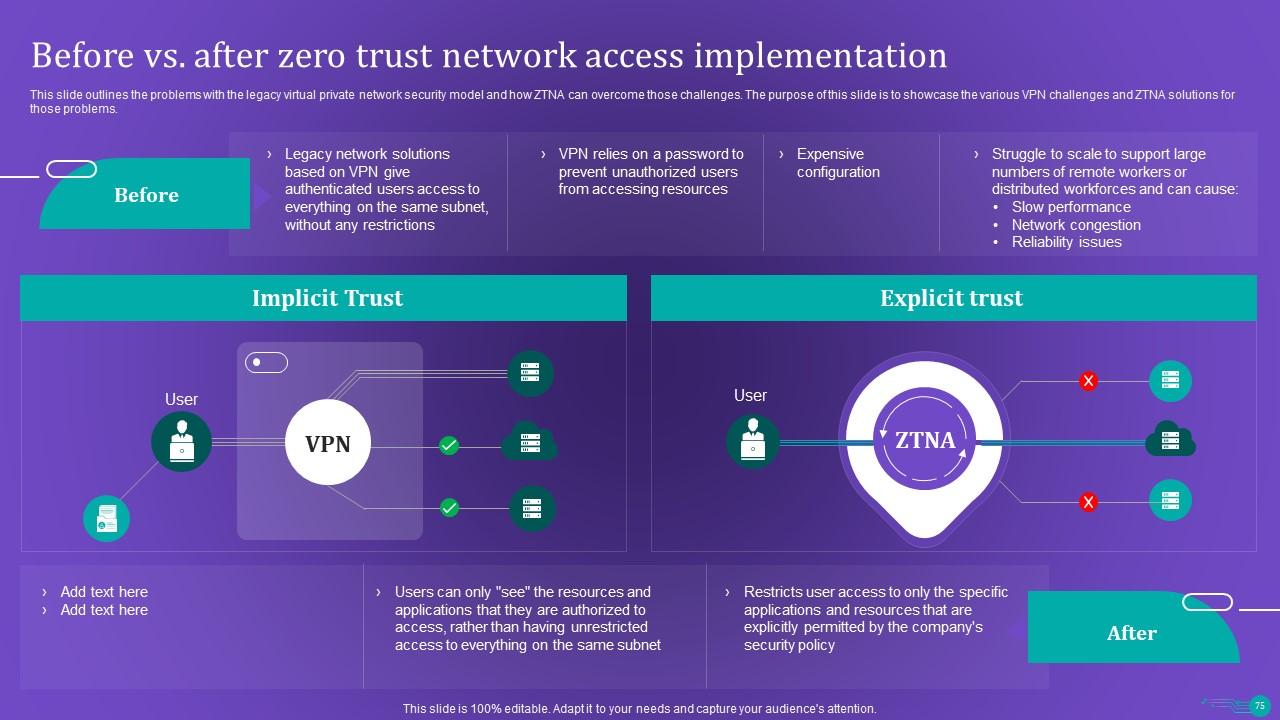
Slide 75: This slide renders the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges.
Slide 76: This slide continues Table of contents for ZTNA.
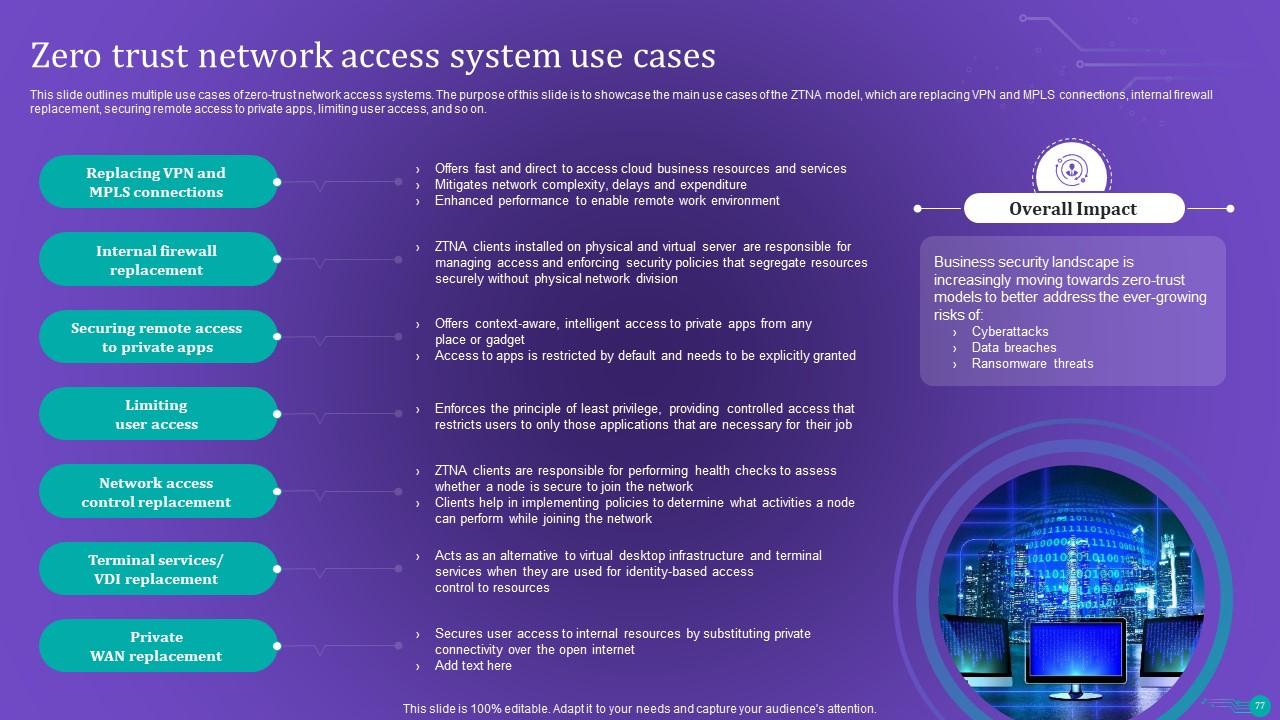
Slide 77: This slide outlines multiple use cases of zero-trust network access systems.
Slide 78: This slide represents the case study for implementing the ZTNA security model into a food and beverage organization.
Slide 79: This slide renders another Table of contents for ZTNA.
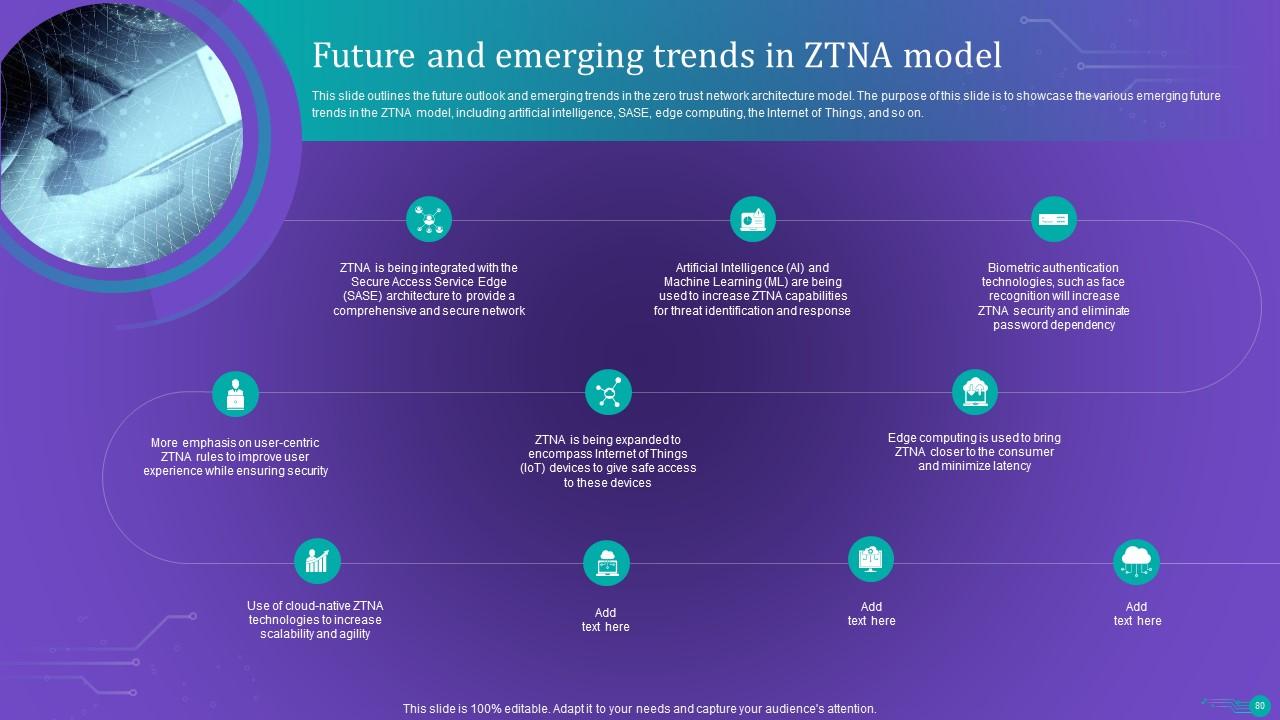
Slide 80: This slide outlines the future outlook and emerging trends in the zero trust network architecture model.
Slide 81: This slide shows all the icons included in the presentation.
Slide 82: This slide is titled as Additional Slides for moving forward.
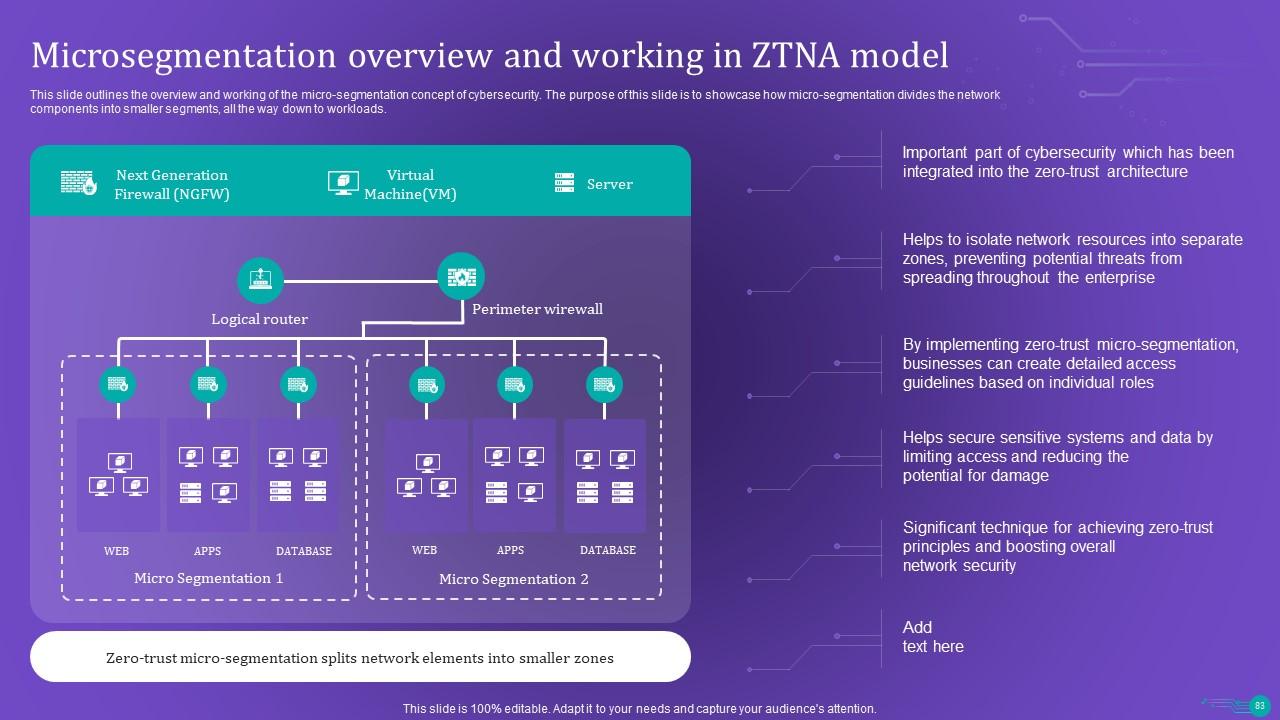
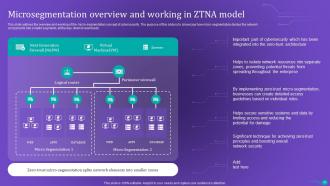
Slide 83: This slide outlines the overview and working of the micro-segmentation concept of cybersecurity.
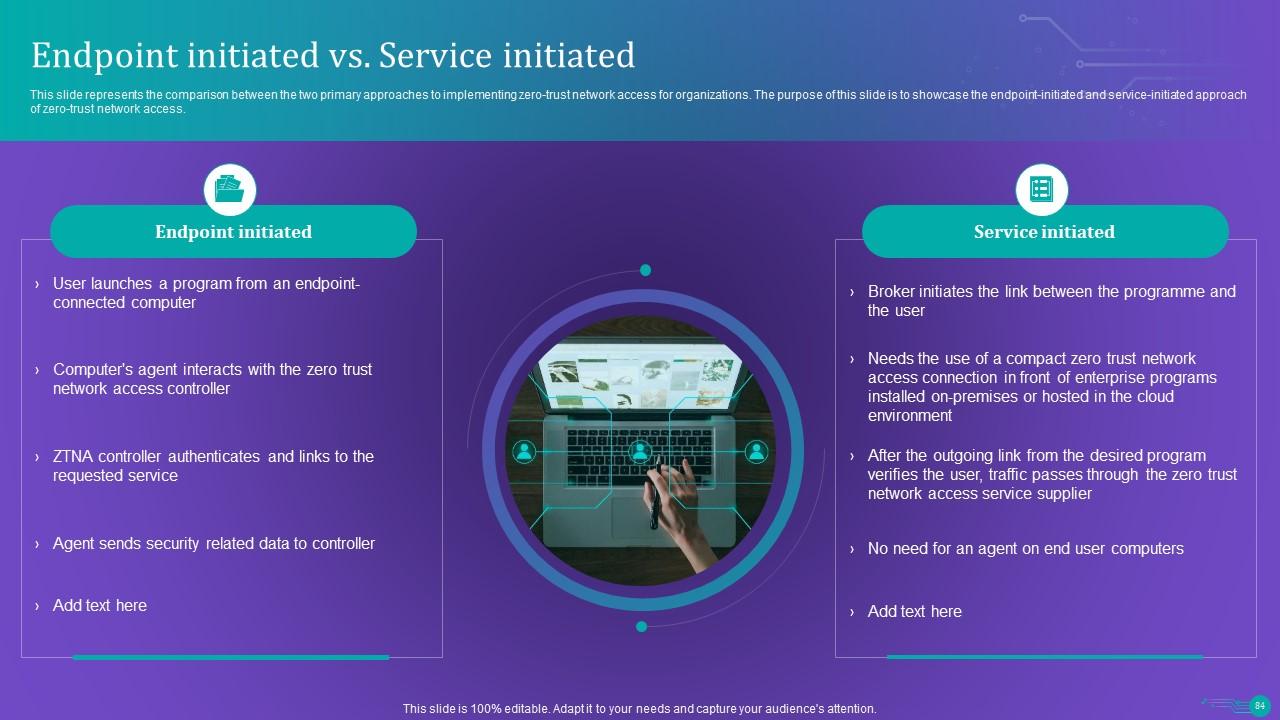
Slide 84: This slide represents the comparison between the two primary approaches to implementing zero-trust network access.
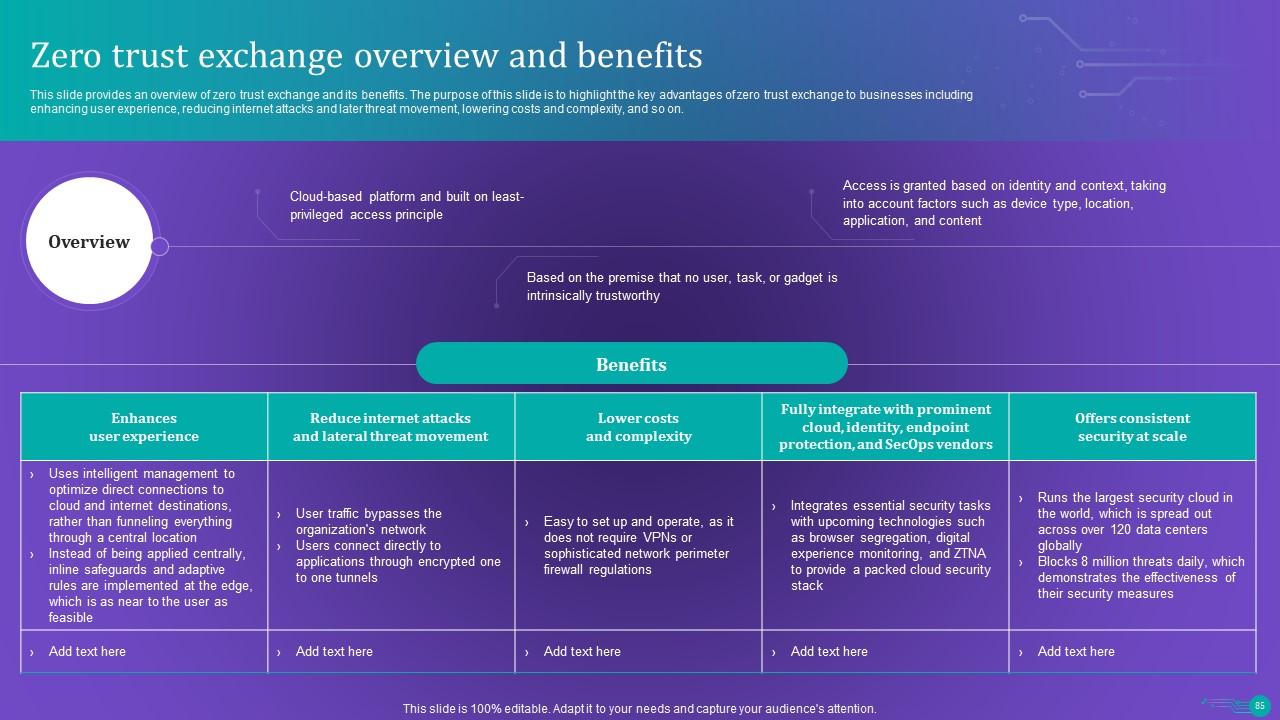
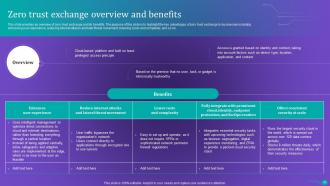
Slide 85: This slide provides an overview of zero trust exchange and its benefits.
Slide 86: This slide presents Roadmap with additional textboxes.
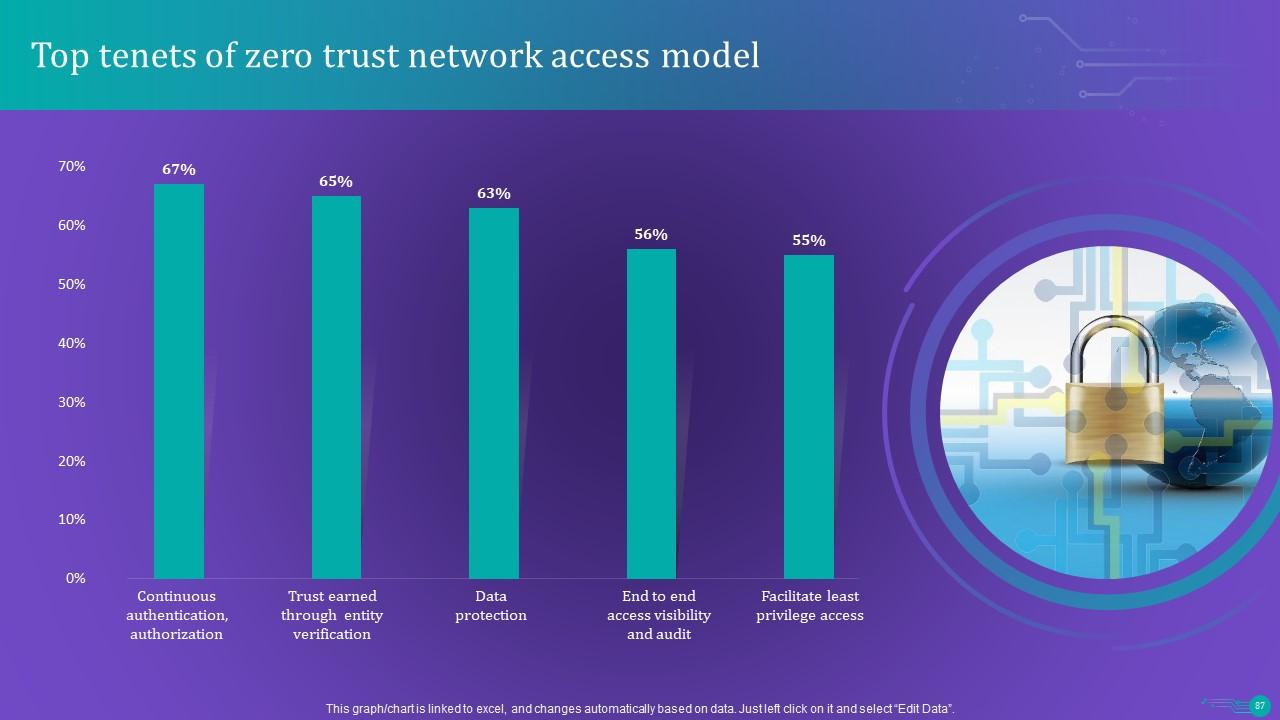
Slide 87: This slide describes Top tenets of zero trust network access model.
Slide 88: This is Our Target slide. State your targets here.
Slide 89: This is a Quotes slide to convey message, beliefs etc.
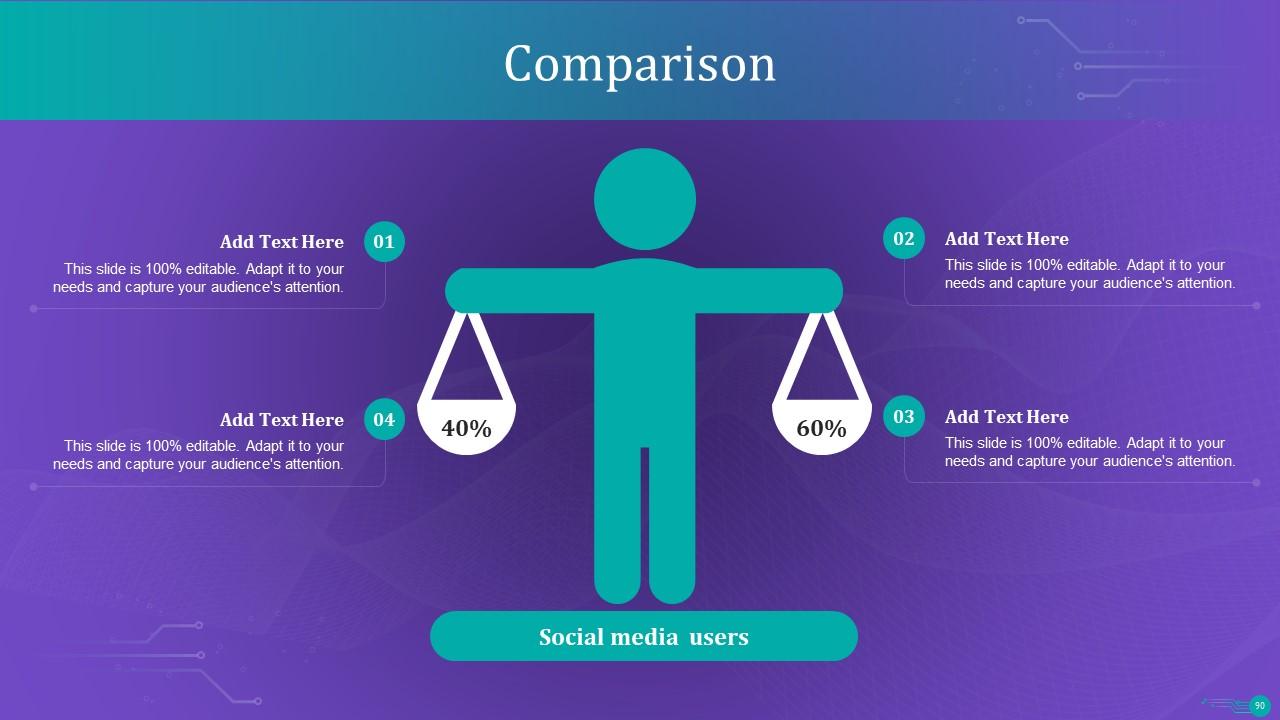
Slide 90: This slide exhibits Comparison between Social media users.
Slide 91: This slide shows Post It Notes. Post your important notes here.
Slide 92: This slide provides 30 60 90 Days Plan with text boxes.
Slide 93: This slide showcases Magnifying Glass to highlight information, specifications etc
Slide 94: This is a Financial slide. Show your finance related stuff here.
Slide 95: This is a Thank You slide with address, contact numbers and email address.
ZTNA Powerpoint Presentation Slides with all 100 slides:
Use our ZTNA Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
FAQs
Zero Trust Network Access is a security model that assumes no trust in any user or device, even if they are inside the network perimeter. It is important because traditional security models that rely on perimeter defenses are no longer sufficient in today's digital landscape. ZTNA helps protect against evolving cyber threats by ensuring strict access controls and verifying trustworthiness at every point of connection.
The key principles of ZTNA include continuous verification of user identity, strict access controls based on least privilege, micro-segmentation to limit lateral movement, encryption for data protection, and real-time monitoring and analytics for detecting and responding to threats promptly.
Implementing ZTNA provides several benefits, such as enhanced security posture, reduced attack surface, improved visibility and control over network traffic, better protection against insider threats, simplified access management, and scalability to accommodate remote and mobile users.
The main components of ZTNA architecture include Identity and Access Management (IAM) solutions, Multi-Factor Authentication (MFA), policy engines, software-defined perimeters, secure connectors, and continuous monitoring and analytics tools.
While both ZTNA and VPN provide secure access to resources, they have distinct differences. ZTNA focuses on user and device identity verification, strict access controls, and micro-segmentation, while VPNs typically establish a secure tunnel between a user's device and the corporate network. ZTNA provides a more granular and dynamic approach to access control, ensuring better security and flexibility in today's evolving threat landscape.
-
I discovered some really original and instructive business slides here. I found that they suited me well.
-
“Excellent service from the customer support team when I wanted a slide that was a bit different from those on their standard menu. Super helpful.”