Ransomware Attacks In Cyber Security Training Ppt
This set of PPT slides in detail covers the working and prevention strategies to avoid ransomware attacks in cyber security.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
Presenting Ransomware Attacks in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 2
This slide gives an introduction to ransomware attacks. Ransomware is a type of malware created to deny a user or organization access to files on their computer.
Slide 3
This slide discusses how ransomware attacks work. The first step in a ransomware attack is to infect the target system, followed by data encryption, and lastly the ransom demand.
Slide 4
This slide gives information about infection and distribution vectors in ransomware attacks. Ransomware can gain access to an organization’s systems by phishing emails or specific infection vectors that use services such as Remote Desktop Protocol.
Slide 5
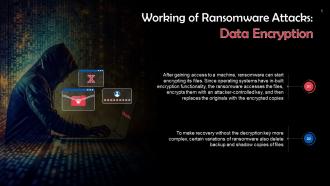
This slide talks about data encryption in ransomware attacks. After gaining access to a machine, ransomware can start encrypting its files. Since operating systems have in-built encryption functionality, the ransomware accesses the files, encrypts them with an attacker-controlled key, and then replaces the originals with the encrypted copies.
Slide 6
This slide gives information about ransom demand in ransomware attacks. After all the files have been encrypted, the ransomware makes a ransom demand. This is usually done by changing the display background to a ransom note or adding text files (with the ransom note) to each encrypted directory.
Slide 7
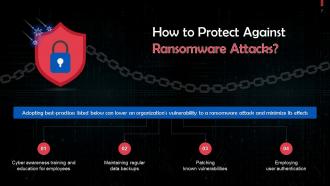
This slide highlights best practices for protection against ransomware attacks. These are: Regular cyber awareness training, maintaining regular data backups, etc.
Slide 8
This slide talks about reducing the attack surface to protect against ransomware attacks. To reduce the attack surface, address the following: Phishing messages, mobile malware, unpatched vulnerabilities, and, remote access solutions.
Slide 9
This slide discusses how deploying anti-ransomware solutions can help in mitigating ransomware attacks.
Slide 10
This slide illustrates steps that active ransomware infection. Most ransomware attacks are detected only after data encryption is done ; however, some steps must be taken immediately.
Instructor’s Notes:
- Quarantine the system: Some ransomware strains attempt to spread to other computers and associated drives. You can control its spread by blocking access to other potential recipients
- Leave the PC on: A computer may become unstable if files are encrypted, and you can lose volatile memory when a computer is turned off can happen. Keep the computer running to increase the likelihood of recovery
- Create a backup: For some ransomware versions, decrypting files is possible without paying the ransom. Create a backup of any encrypted files on a removable drive in case a solution is available in the future. Files are damaged during an unsuccessful decryption attempt
- Check for decryptors: Check with the No More Ransom Project to check if a free decryptor is available. If so, run it on a copy of the encrypted data to see if it can restore the files
- Ask for help: Computers sometimes keep backup copies of files stored on them. A digital forensics expert may be able to recover these copies if the malware has not deleted them
- Wipe and restore: Restore the system from a clean backup or operating system installation. This ensures that the malware is completely deleted from the device
Slide 11
This slide depicts key statistics on ransomware attacks.
Ransomware Attacks In Cyber Security Training Ppt with all 31 slides:
Use our Ransomware Attacks In Cyber Security Training Ppt to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Helpful product design for delivering presentation.
-
Great designs, really helpful.