Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing
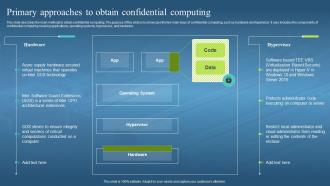
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing. Dispense information and present a thorough explanation of Operating System, Hypervisor, Restrict Local Administrator, Cloud Administrator using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
People who downloaded this PowerPoint presentation also viewed the following :
Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing with all 10 slides:
Use our Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
I had them make a presentation for an office retirement party. They were very helpful in understanding what we wanted and delivered the perfect presentation. Highly recommended!
-
Very unique and reliable designs.