Confidential Computing V2 Process Of Using Intel SGX Based Trusted Applications
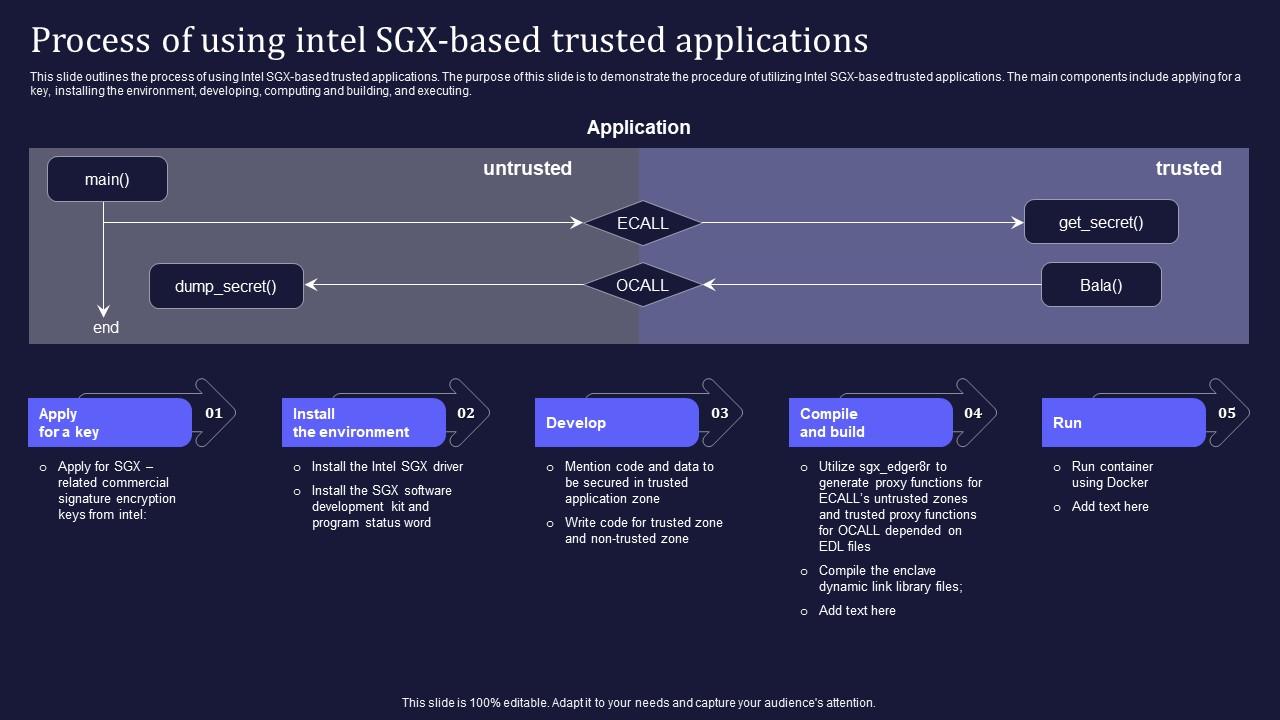
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate ..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Introducing Confidential Computing V2 Process Of Using Intel SGX Based Trusted Applications to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Installing The Environment, Developing, Computing And Building, Signature Encryption, using this template. Grab it now to reap its full benefits.
People who downloaded this PowerPoint presentation also viewed the following :
Confidential Computing V2 Process Of Using Intel SGX Based Trusted Applications with all 10 slides:
Use our Confidential Computing V2 Process Of Using Intel SGX Based Trusted Applications to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
SlideTeam is very efficient when it comes to saving time. I am happy that I chose them for my presentation.
-
Love how there are no boring templates here! The design is fresh and creative, just the way I like it. Can't wait to edit and use them for my extended projects!